Kerberos authentication system and based on physical unclonable function
A physical and functional technology, applied in the field of Kerberos authentication system based on physical unclonable functions, can solve problems affecting device and system availability, security system crash, key leakage, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment 1
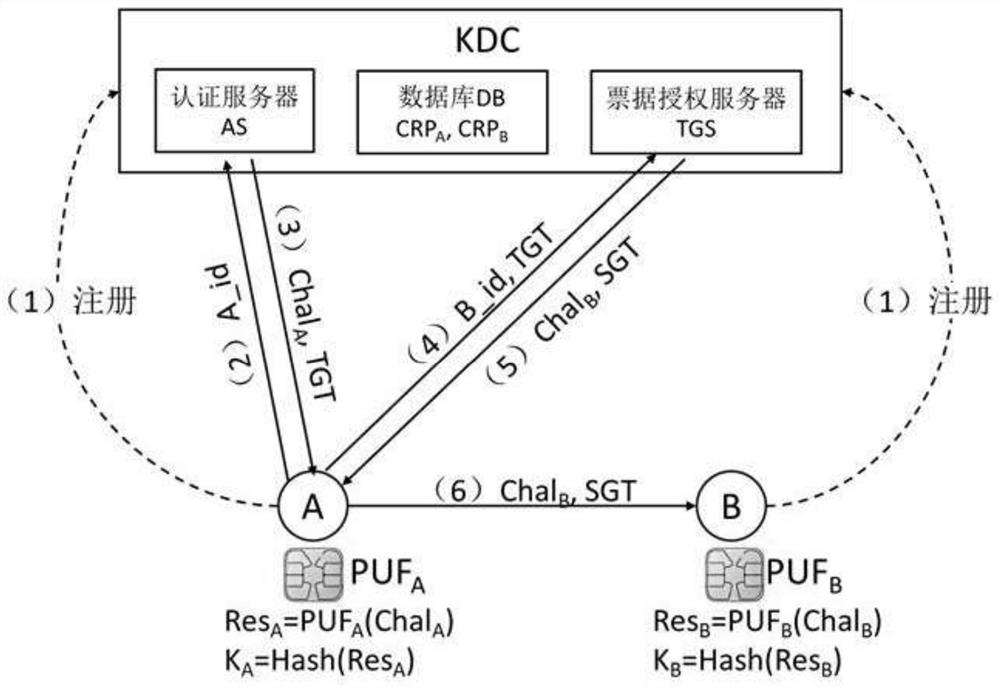
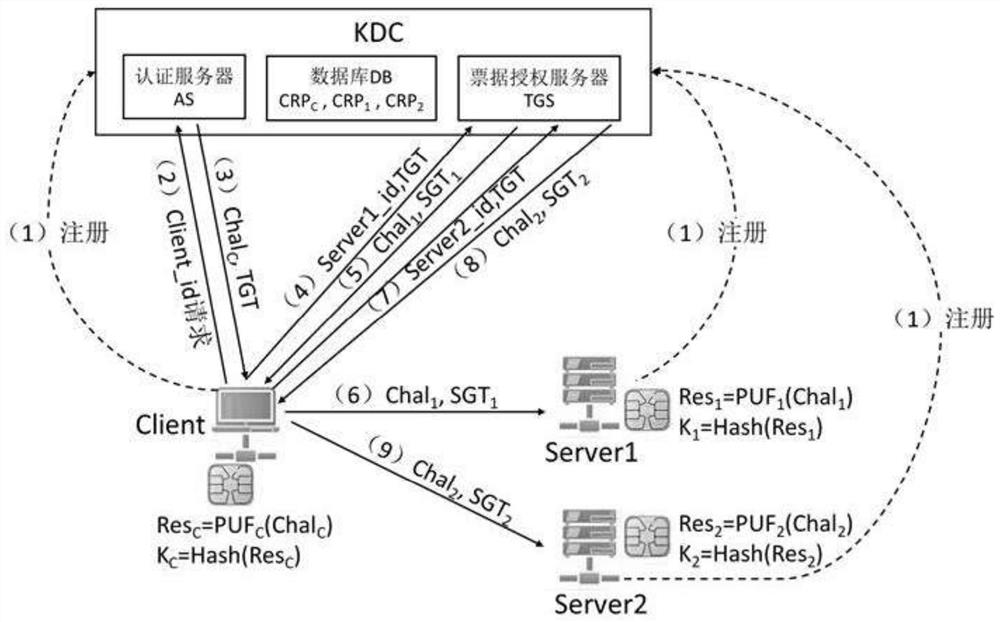
[0066] Such as figure 2 As shown, when the method of the present invention is used for single sign-on SSO, the system includes a client, an application server and a key distribution center KDC, and the key distribution center KDC includes: an authentication server AS, a ticket authorization server TGS, a database DB ;
[0067] Both the client and the application server are equipped with a PUF chip, and the database DB stores a set of stimulus-response pairs of the PUF chip; the device A and device B perform two-way authentication with the key distribution center KDC; the key distribution The central KDC distributes a symmetric session key K between devices A and B A,B .
[0068] The method includes the following steps:
[0069] Step S1: Register the client and the application server with the key distribution center KDC.
[0070] S11: The client and the application server respectively install a physically unclonable function PUF chip;
[0071] S12: The client and the appl...
specific Embodiment 2
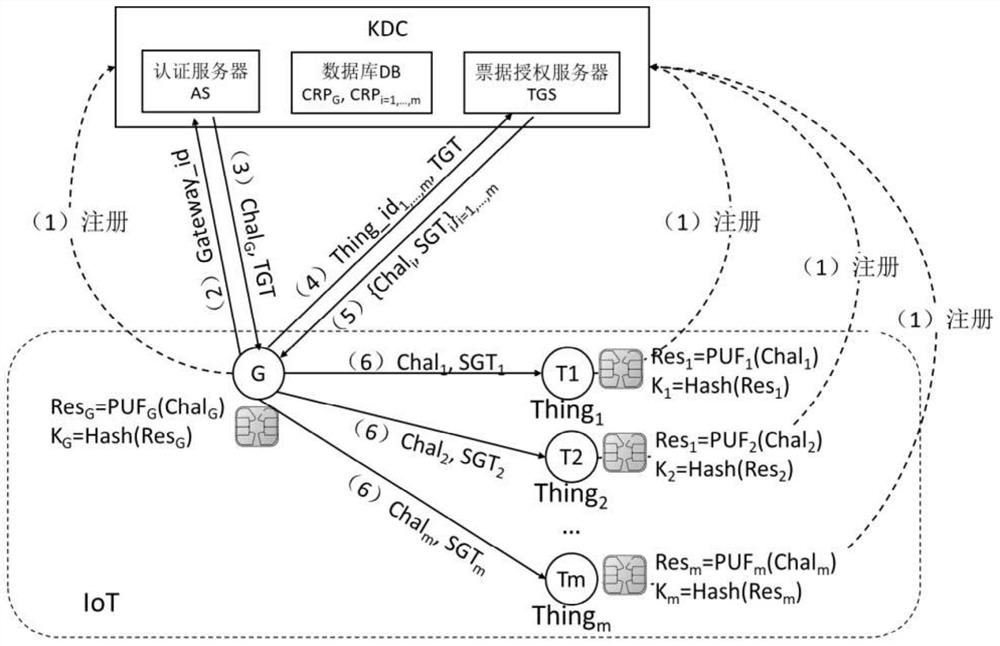
[0117] The present invention is applied to the authentication and session of gateway nodes and terminal devices in the Internet of Things, including servers, gateway nodes and terminal devices, wherein, there is only one server, which is the control center of the network; there are several gateway nodes, and the server manages several gateway nodes, each The gateway node manages several terminal devices; when the gateway node is physically connected to the terminal device, it needs to be authenticated and establish a session key.
[0118] Specific steps are as follows:
[0119] Step S1: Register the gateway and the terminal device with the key distribution center KDC.
[0120] S11: Before the network launch, all gateways and terminal devices are installed with a physical unclonable function PUF structure;
[0121] S12: The gateway and the terminal device respectively generate several random numbers as the stimulus set, and input each stimulus into the PUF chip to generate a c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com