Encrypted traffic identification method and device and equipment
A traffic and algorithm technology, applied in the field of malicious traffic analysis, can solve the problems of high false alarm rate, poor interpretability, complex traffic, etc., to achieve the effect of improving prediction accuracy, reducing computing pressure, and improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
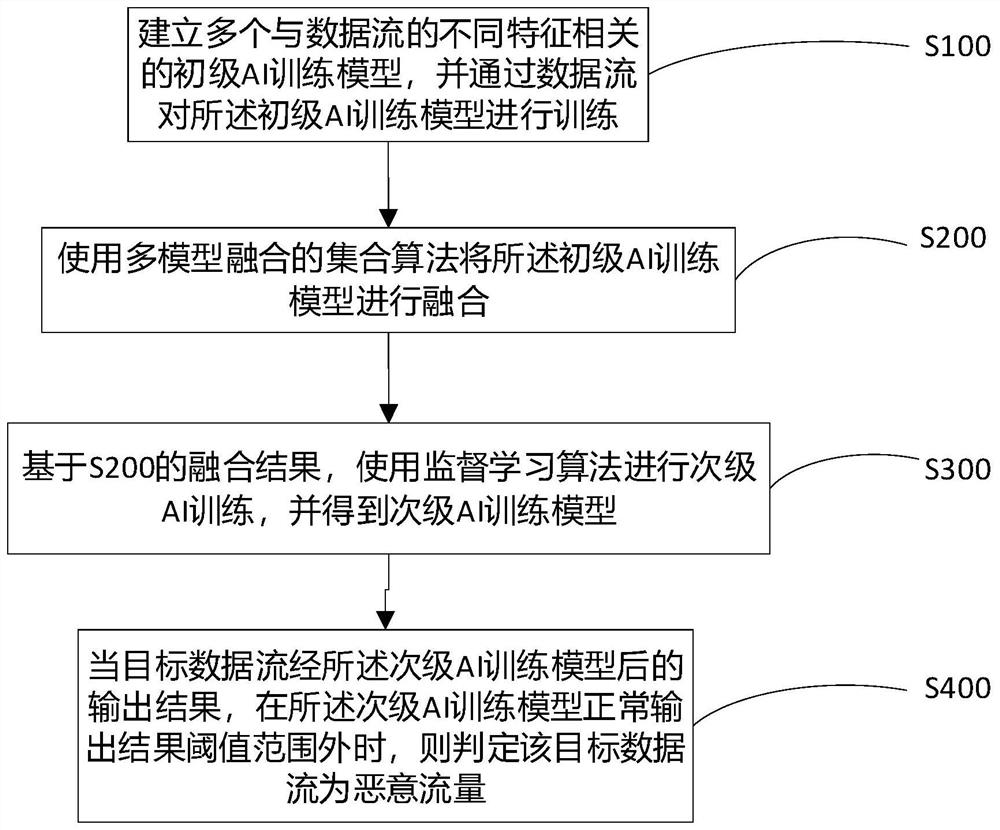
[0044] Please refer to the attached figure 1 , figure 1 A method for identifying encrypted traffic provided in an embodiment of the present application uses an AI model to identify encrypted traffic, and the training process of the AI model includes the following steps:
[0045] S100. Establish a plurality of primary AI training models related to different characteristics of the data stream, and train the primary AI training models through the data stream;
[0046] S200. Fuse the primary AI training model by using an ensemble algorithm of multi-model fusion;
[0047] S300. Based on the fusion result of S200, use a supervised learning algorithm to perform secondary AI training, and obtain a secondary AI training model;
[0048] S400. When the output result after the target data flows through the secondary AI training model is outside the normal output result threshold range of the secondary AI training model, determine that the target data flow is malicious traffic.
[004...
Embodiment 2
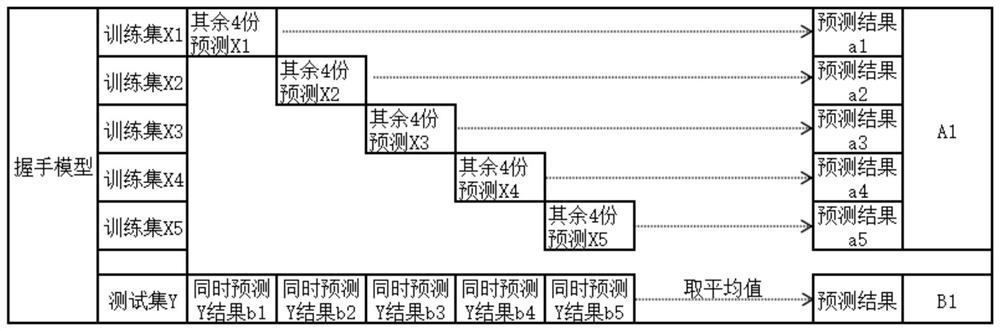
[0068] Such as Figure 5 As shown, in this embodiment, the detection process for encrypted traffic is divided into four dimensions:
[0069] 1. One-dimensional detection: extract the destination IP and associated DNS from the traffic, and match with the IP blacklist, and / or DNS blacklist, and / or IP whitelist, and / or DNS whitelist respectively, and the IP or DNS hits black The traffic on the list is malicious encrypted traffic, and the traffic whose IP and DNS both hit the white list is normal encrypted traffic;
[0070] 2. Two-dimensional detection: The SSL / TLS protocol will generate a ClientHello message during the handshake negotiation process, which includes such as: the maximum supported TLS version, acceptable ciphers, extended list, elliptic curve cipher and elliptic curve cipher format Wait. Concatenate these values together to get a specific value through the Hash function, which is the TLS fingerprint (note: different from JA3, the information granularity is finer...
Embodiment 3
[0080] This embodiment discloses an identification device for encrypted traffic such as Figure 7 As shown, the identification device of the encrypted traffic includes:
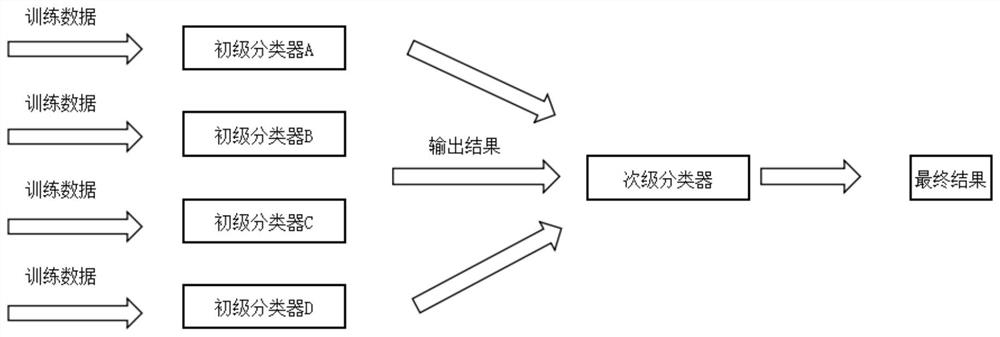
[0081] The primary AI training module 100: includes a plurality of primary AI training models related to different characteristics of the data stream, and trains the AI training primary model through the data stream;
[0082] Fusion module 200: use an ensemble algorithm to fuse the AI training primary model;
[0083] Secondary AI training module 300: based on the fusion result of the fusion module, use a supervised learning algorithm to perform secondary AI training, and obtain a secondary AI training model;
[0084] Judgment module 400: when the output result of the target data flowing through the secondary AI training model is outside the normal output result threshold range of the secondary AI training model, determine that the target data flow is malicious traffic.
[0085] The processes and methods...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com