Network access control method and system based on IP access behaviors
A network access control and behavior technology, applied in the field of computer networks, can solve the problems of cumbersome configuration, poor dynamic real-time performance, low efficiency, etc., and achieve the effect of improving service quality, enhancing stability and usability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
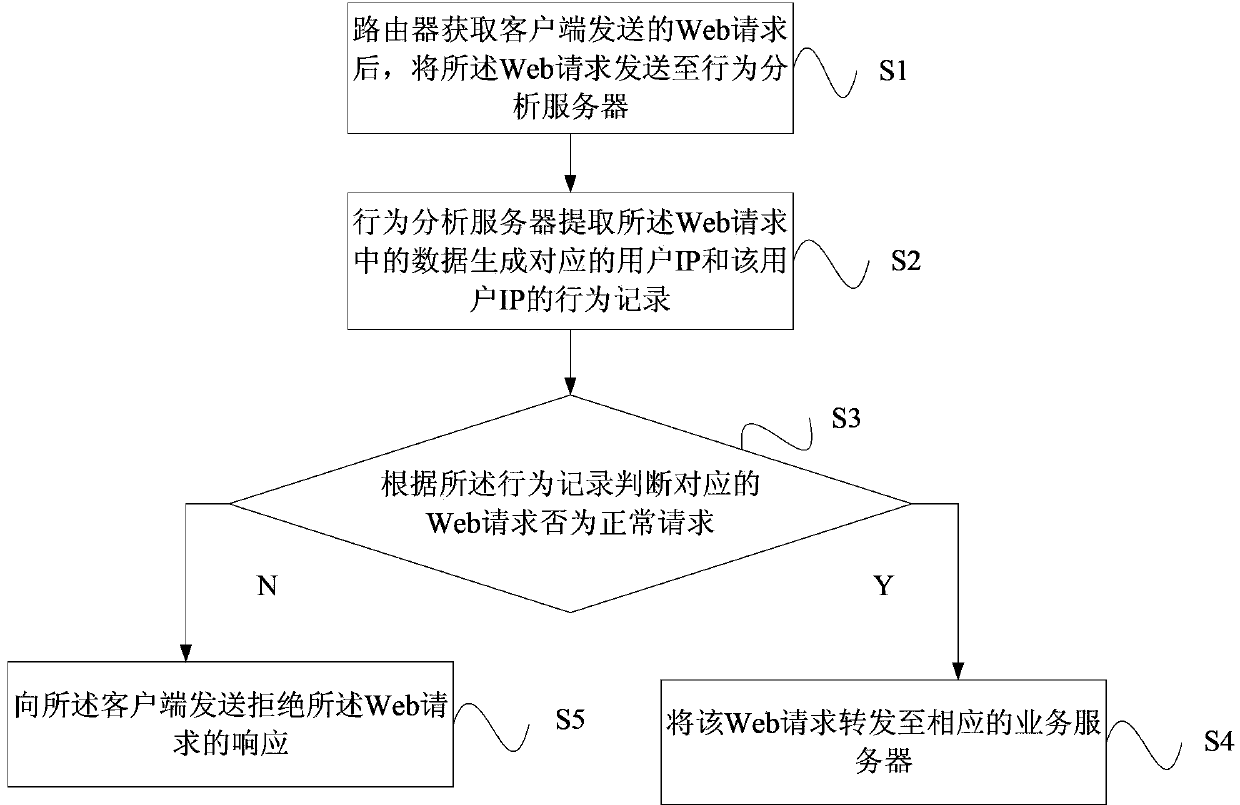
[0030] like Figures 1 to 3 As shown, the present invention provides a network access control method based on IP access behavior. The method in this embodiment is applicable to access control including websites, interfaces, WEB services, etc. The method includes steps S1 to S5.
[0031] Step S1, after the router obtains the Web request sent by the client, it sends the Web request to the behavior analysis server. Specifically, various users send Web requests through the client, and each client corresponds to an IP; The entrance of the company's business server, by configuring it, it can send Web requests to the corresponding behavior analysis server.
[0032] In an embodiment of the present invention, the Web request includes the user IP, the requested resource address, and the used browser model information.
[0033] In step S2, the behavior analysis server extracts the data in the Web request to generate the corresponding user IP and the behavior record of the user IP. Speci...
Embodiment 2
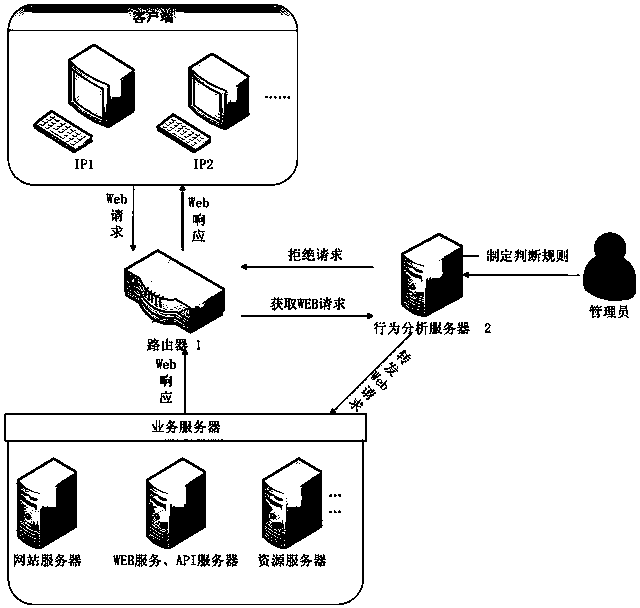
[0053] like image 3 As shown, the present invention also provides another network access control system based on IP access behavior, including a router 1 and a behavior analysis server 2 .
[0054] The router 1 is configured to, after acquiring the Web request sent by the client, send the Web request to the behavior analysis server.
[0055] In an embodiment of the present invention, the Web request includes the user IP, the requested resource address, and the used browser model information.
[0056] The behavior analysis server 2 is used to extract the data in the Web request to generate the corresponding user IP and the behavior record of the user IP, and judge whether the corresponding Web request is a normal request according to the behavior record, and if so, then the Web request The request is forwarded to the corresponding service server; if not, a response rejecting the Web request is sent to the client.
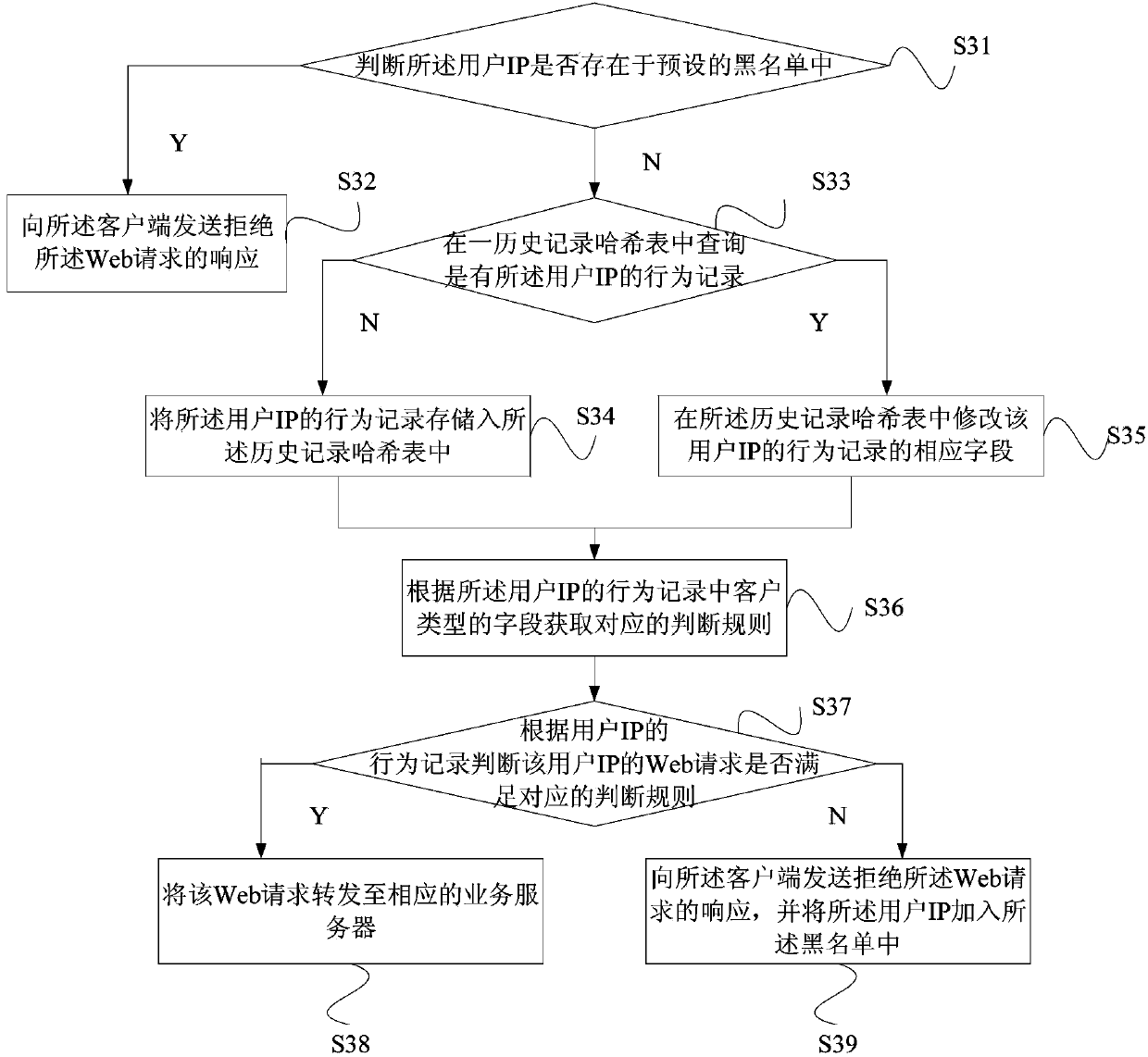
[0057] In an embodiment of the present invention, the behavi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com