Information security defense rule intelligent deployment method based on improved particle swarm optimization
A particle swarm algorithm and information security technology, applied in the field of security products, can solve problems such as lack of science and deployment of defense rules, and achieve the effect of reducing overhead, reducing load, and improving defense pertinence
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0054] Below with reference to accompanying drawing, the present invention is further described by specific embodiment:
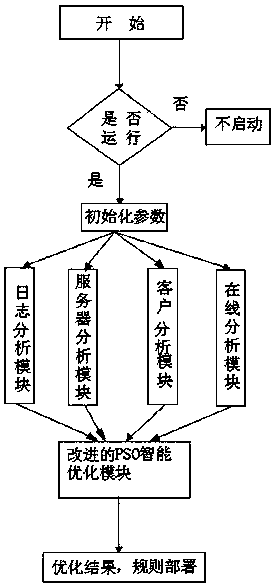
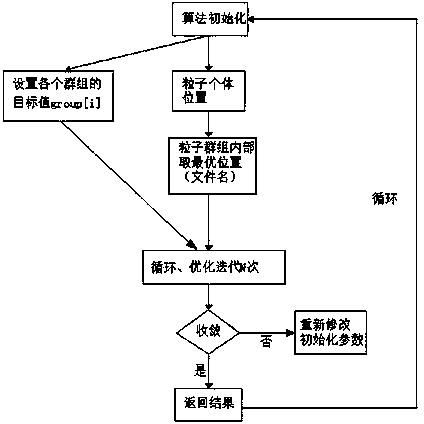
[0055] An intelligent deployment method of information security defense rules based on an improved particle swarm optimization algorithm, the method includes an intelligent learning algorithm, a deployment strategy of security rules, and optimizes the frequency, type and potential of attacks in the system log according to the improved particle swarm optimization algorithm of parameters Attacks, using intelligent learning algorithms to deploy without affecting the normal resource overhead of the security defense system, deploying rules for the actual network environment, using the ability to defend against existing attacks and gain insight into potential attacks based on network conditions, with The access log attack analysis engine capable of autonomously analyzing attacks can identify common attacks through access logs.
[0056] The method includes: an ini...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com