Multi-step attack tracing method and system, terminal and readable storage medium
A relational and algorithmic technology, applied in the field of network security, can solve problems such as the intricate relationship between logs, achieve good scalability, improve accuracy, and reduce bad connections
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The present invention will be described in further detail below in conjunction with the accompanying drawings.
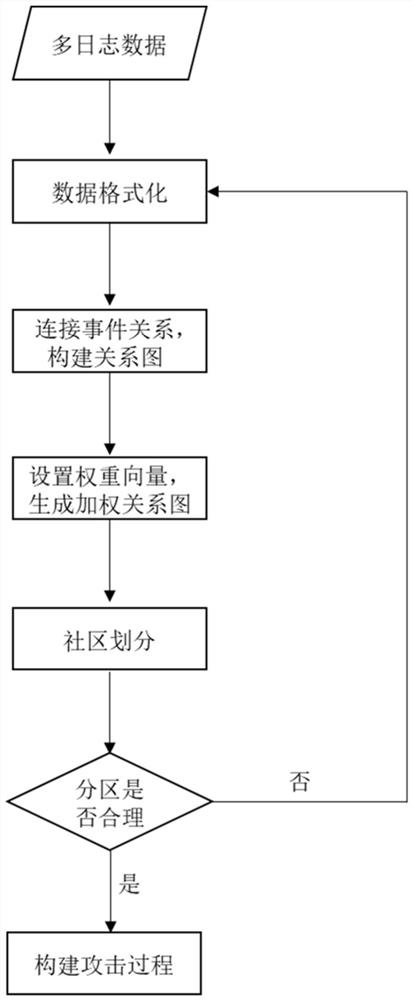
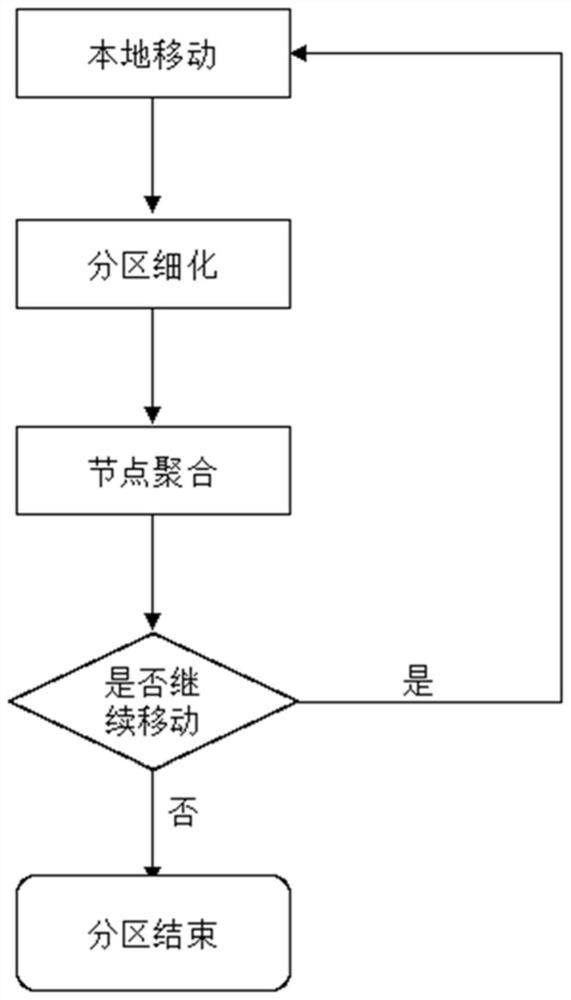
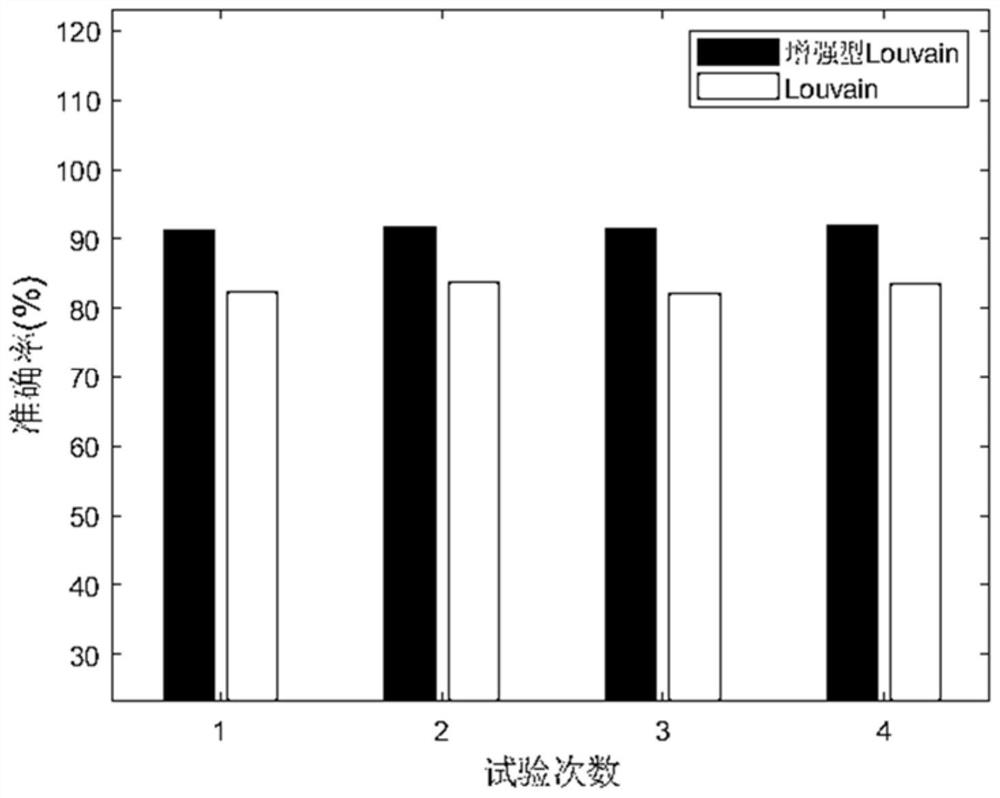
[0038] see figure 1 , the multi-step attack source tracing method of the present invention, through multi-log event correlation, uses the enhanced Louvain algorithm to divide the community, and builds the attack process based on the attack community. The main body is divided into four parts: the first part is the construction of the relationship graph, extracting event features, establishing event connections, and constructing event relationship graphs through event relationship vectors; the second part is state optimization, obtaining weight vectors through logistic regression algorithms, and using weight vectors Weight the relationship graph to solve the problem of state explosion; the third part is community division, using the enhanced Louvain algorithm to divide the weighted graph into relationship, so as to obtain the attack community that needs to be ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com