Systems, Methods and Computer-Readable Media for Regulating Remote Access to a Data Network
a remote access and data network technology, applied in the field of network access, can solve the problems of inability to properly configure the modem in the network, inability to ensure the integrity of the modem,
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
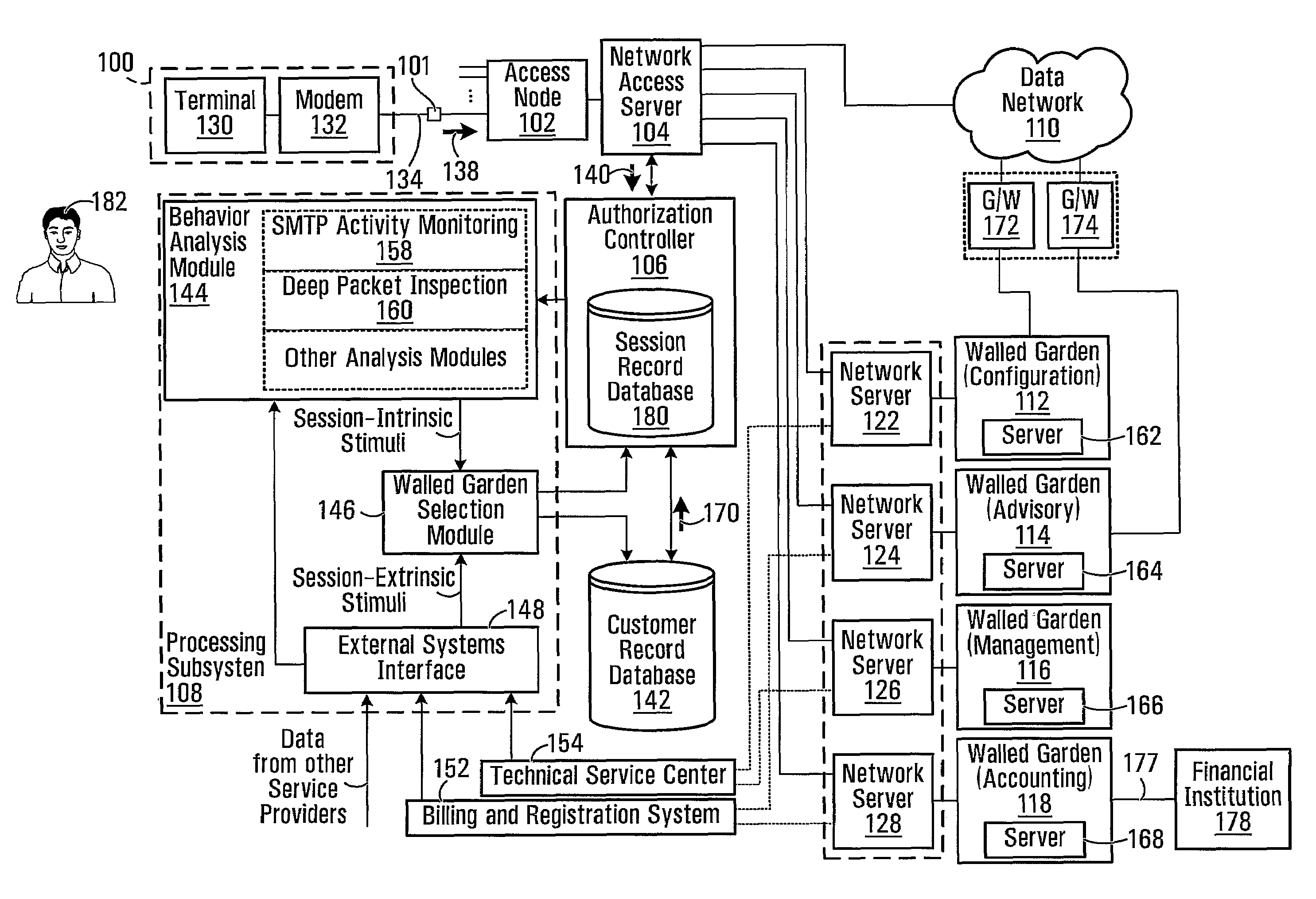
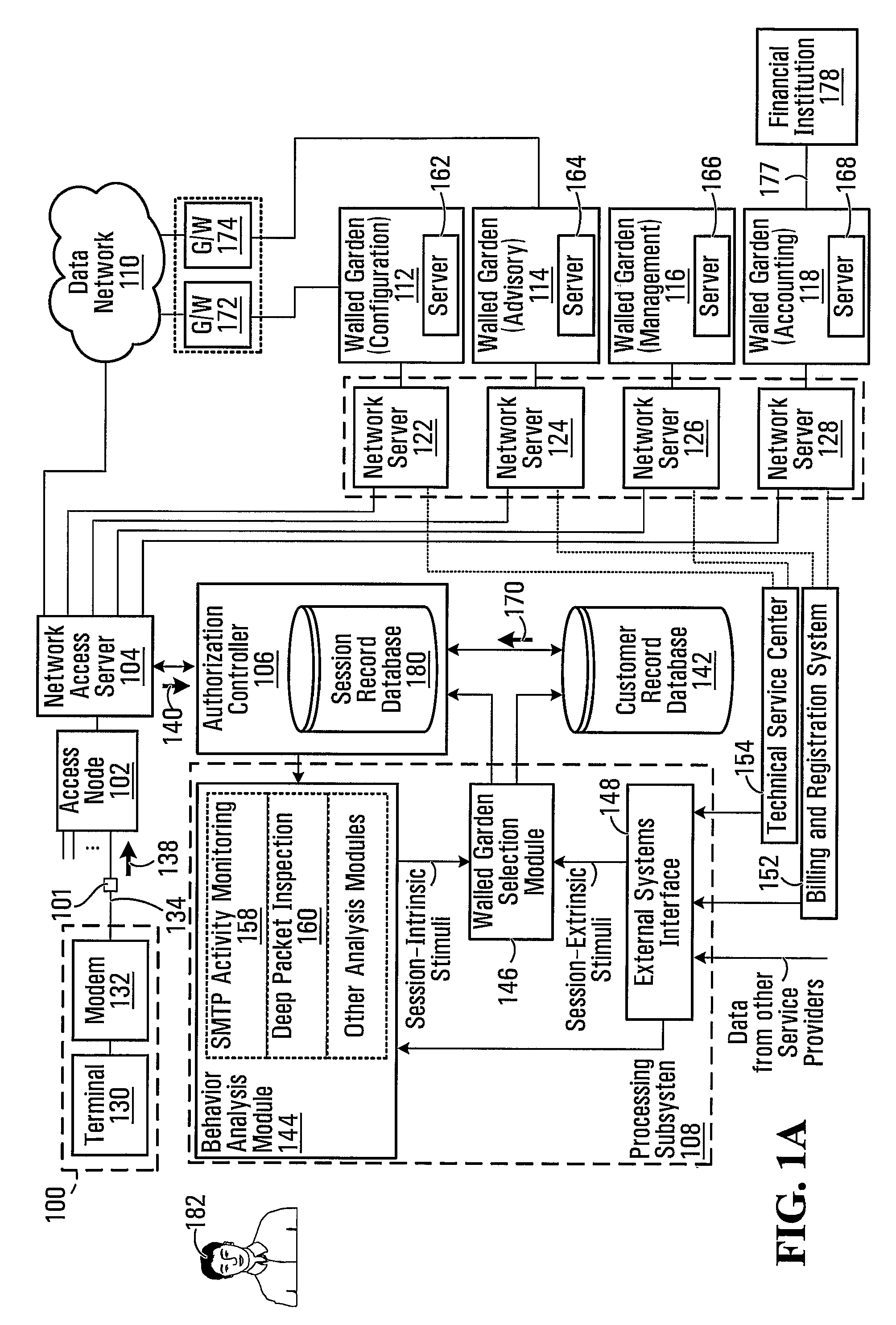
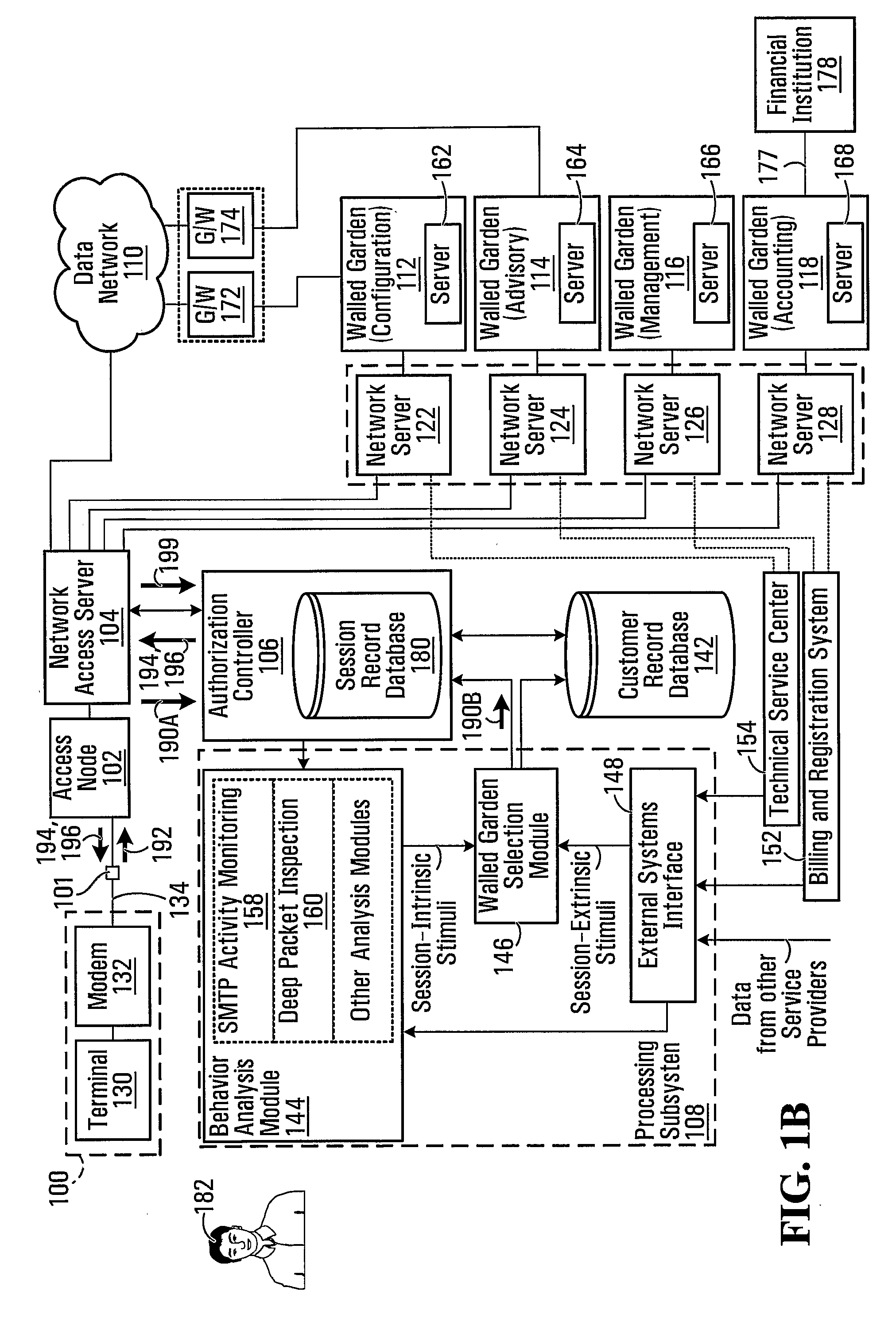
[0024]With reference to FIG. 1A, there is shown a network architecture including a customer premises 100, a splitter 101, an access node 102 (such as a digital subscriber line access multiplexer (DSLAM)), a network access server 104, an authorization controller 106, a customer record database 142 and a processing subsystem 108. In addition, there is provided a data network 110 (which may be an Intranet, the Internet, or another data network) and a plurality of walled gardens. In this case, four walled gardens 112, 114, 116, 118 are illustrated. However, it should be understood that in general, there are at least two walled gardens, while there is no upper limit on the number of walled gardens that may be provided.
[0025]The network access server 104 operates as a gateway to the data network 110 and to the walled gardens 112, 114, 116, 118, which are accessible via respective network servers. For example, in the illustrated embodiment, the network access server 104 is connected to wal...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com