Method for improving encrypted data security transmission level
A technology for safe transmission and encryption of data, applied in the field of data transmission, it can solve problems such as leakage and data ports do not have encryption performance, and achieve the effect of strong encryption performance, fast and convenient docking and compact structure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0072] The method for improving the level of secure transmission of encrypted data includes the following steps:
[0073] (1) The plug-in stage;
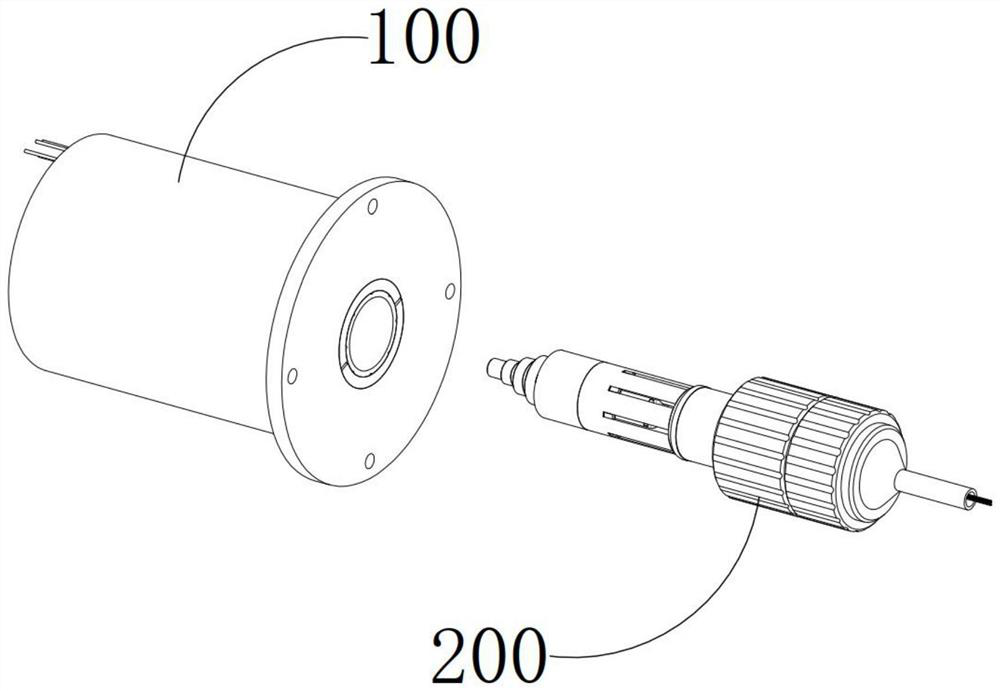
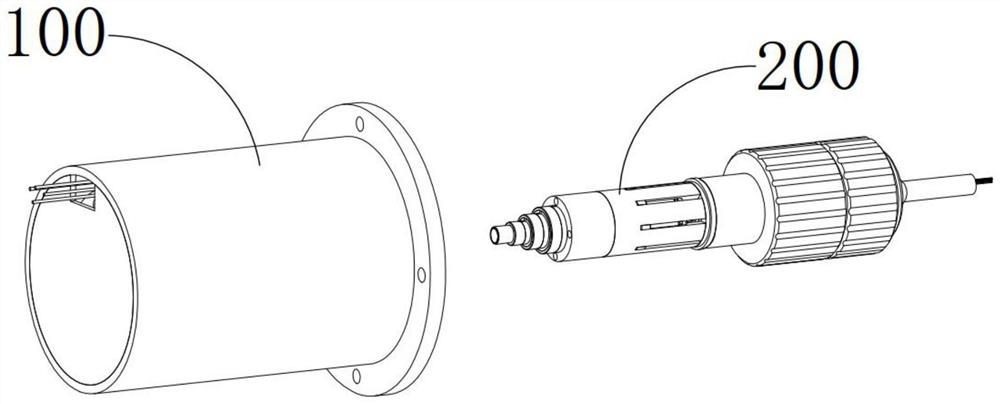
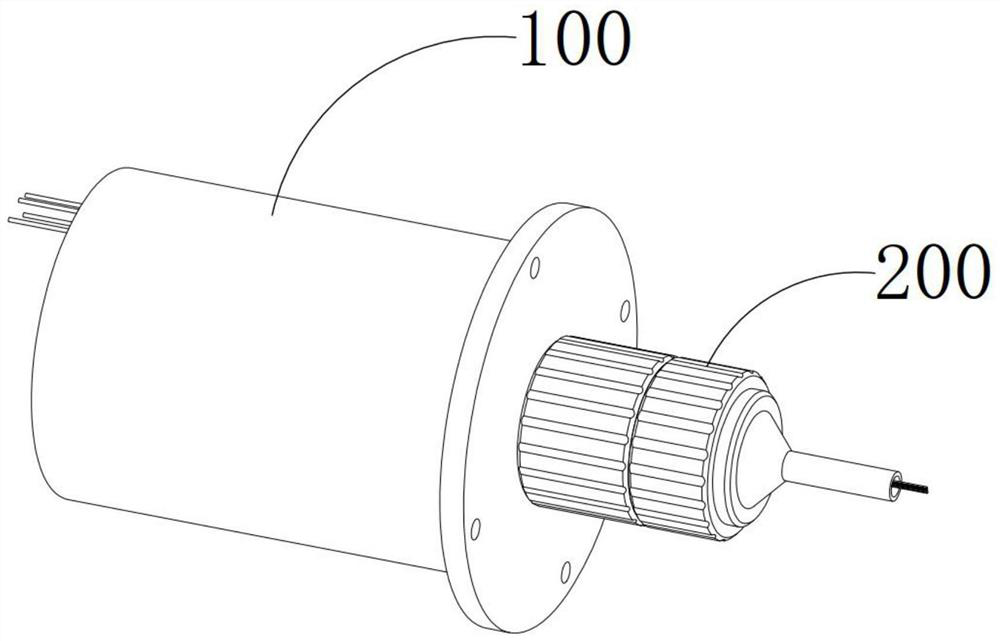
[0074] S1: Insert the decryption cylinder 210 into the installation cylinder 110 and complete the matching and docking, the output member 120 and the input member 220 will be connected to each other, and the decryption mechanism 230 and the encryption switch 130 are directly opposite;
[0075] The encryption socket 100 includes a mounting barrel 110, an output member 120, and a plurality of encryption switches 130. The output member 120 and the encryption switch 130 are both installed in the mounting barrel 110. The encryption switch 130 is connected in series with the output member 120 and a plurality of encryption switches 130 is opened at the same time for turning on the output member 120, and the encryption switch 130 is closed in the initial state;
[0076] The decryption mechanism 200 includes a decryption cylinder 210 for inserting i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com