Function parameter data transmission encryption method, system and device and readable storage medium
A technology of data transmission and encryption method, applied in the field of data transmission, can solve the problems of affecting data transmission efficiency, data change, insufficient encryption strength, etc., and achieve the effect of not affecting data transmission efficiency and fast encryption speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
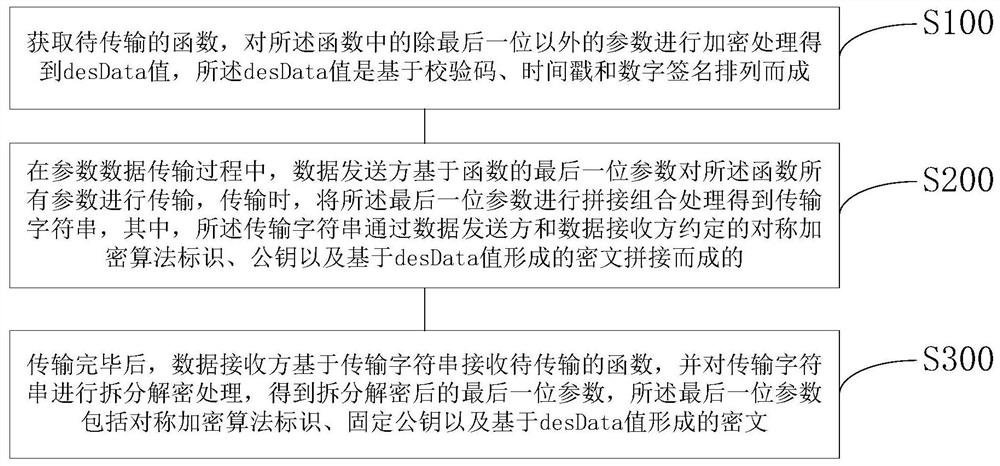
[0049] A function parameter data transmission encryption method, such as figure 1 shown, including the following steps:
[0050] S100. Obtain the function to be transmitted, and encrypt parameters in the function except the last bit to obtain a desData value, and the desData value is arranged based on a check code, a time stamp and a digital signature;
[0051] S200. In the process of parameter data transmission, the data sender transmits the function based on the last parameter of the function. When transmitting, the last parameter is concatenated and combined to obtain a transmission string, wherein the transmission The character string is concatenated by the symmetric encryption algorithm identification, public key and ciphertext formed based on the desData value agreed by the data sender and the data receiver;
[0052] S300. After the transmission is completed, the data receiver receives the function to be transmitted based on the transmission string, and splits and decrypt...
Embodiment 2
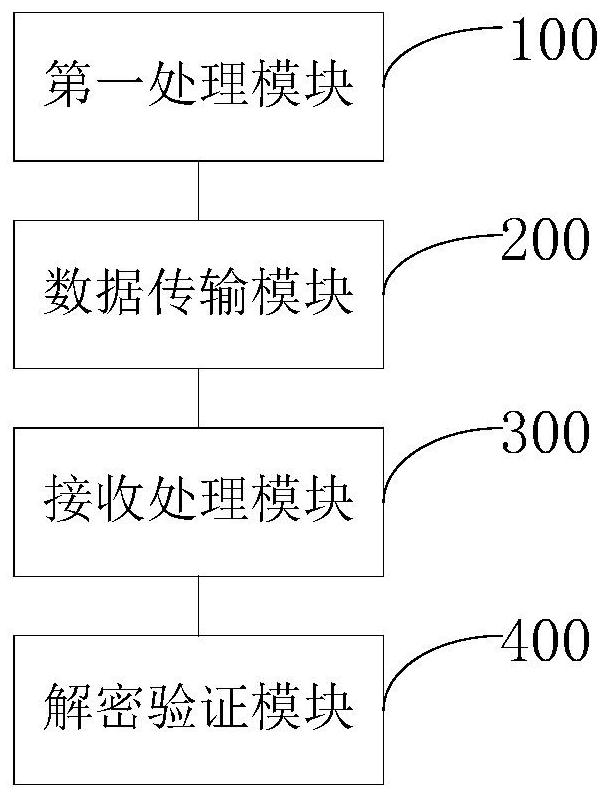
[0077] A function parameter data transmission encryption system, including a first processing module 100, a data transmission module 200 and a receiving processing module 300;
[0078] The first processing module 100 is configured to obtain the function to be transmitted, encrypt parameters in the function except the last bit to obtain a desData value, and the desData value is based on a check code, a time stamp and a digital signed by;
[0079] In the data transmission module 200, during the parameter data transmission process, the data sender transmits the function based on the last parameter of the function. When transmitting, the last parameter is concatenated and combined to obtain a transmission string. Wherein, the transmission character string is spliced by the symmetric encryption algorithm identification, public key and ciphertext formed based on the desData value agreed by the data sender and the data receiver;
[0080] The receiving processing module 300, after ...
Embodiment 3
[0094] A computer-readable storage medium, the computer-readable storage medium stores a computer program, and when the computer program is executed by a processor, the following method steps are implemented:
[0095] Obtain the function to be transmitted, and encrypt the parameters in the function except the last bit to obtain the desData value, and the desData value is arranged based on the check code, time stamp and digital signature;
[0096] In the process of parameter data transmission, the data sender transmits the function based on the last parameter of the function. When transmitting, the last parameter is concatenated and combined to obtain a transmission string, wherein the transmission string It is spliced by the symmetric encryption algorithm identification, public key and ciphertext formed based on the desData value agreed by the data sender and data receiver;
[0097] After the transmission is completed, the data receiver receives the function to be transmitte...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com