Encryption component applied to safe transmission of communication data
A communication data and security technology, applied in the direction of mechanical encryption, etc., can solve the problems of loss of confidentiality in data transmission, etc., and achieve the effect of compact structure, convenient docking and cooperation, and ingenious structure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
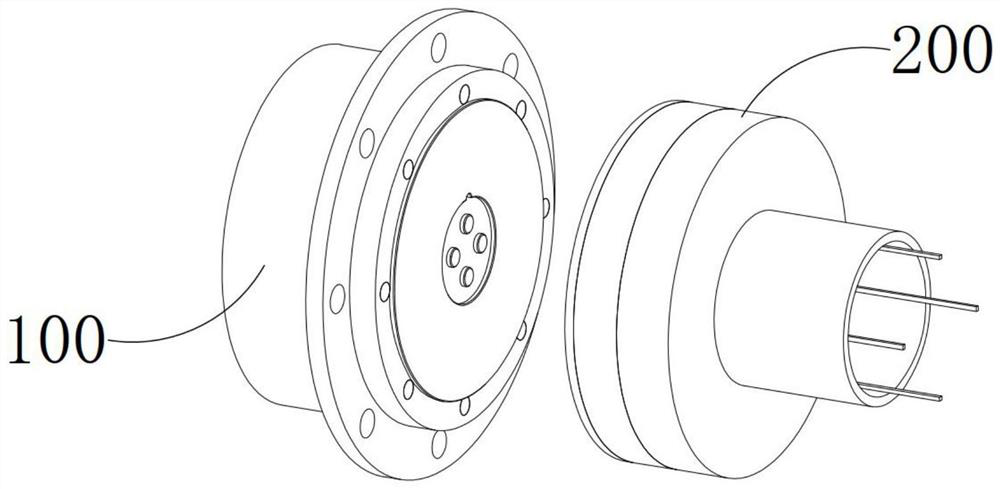
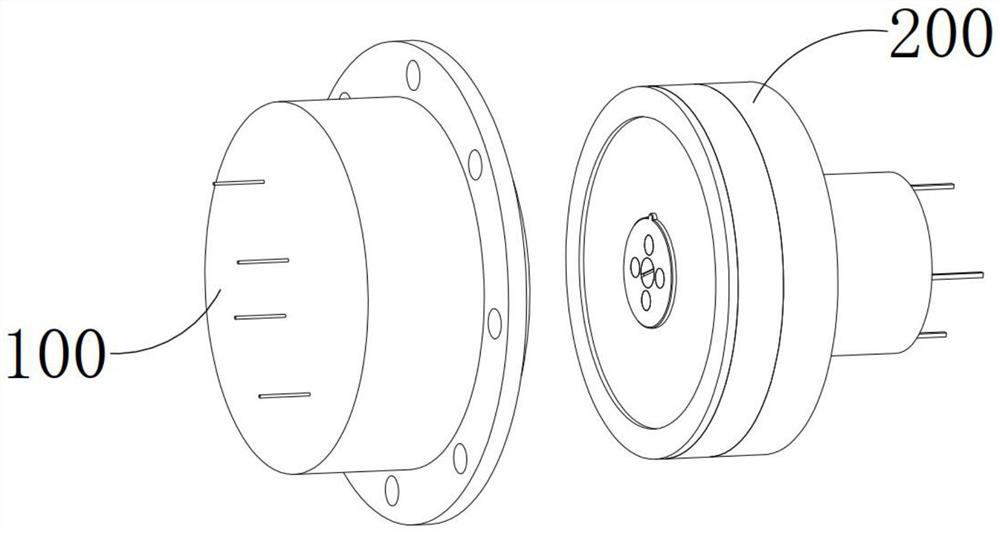
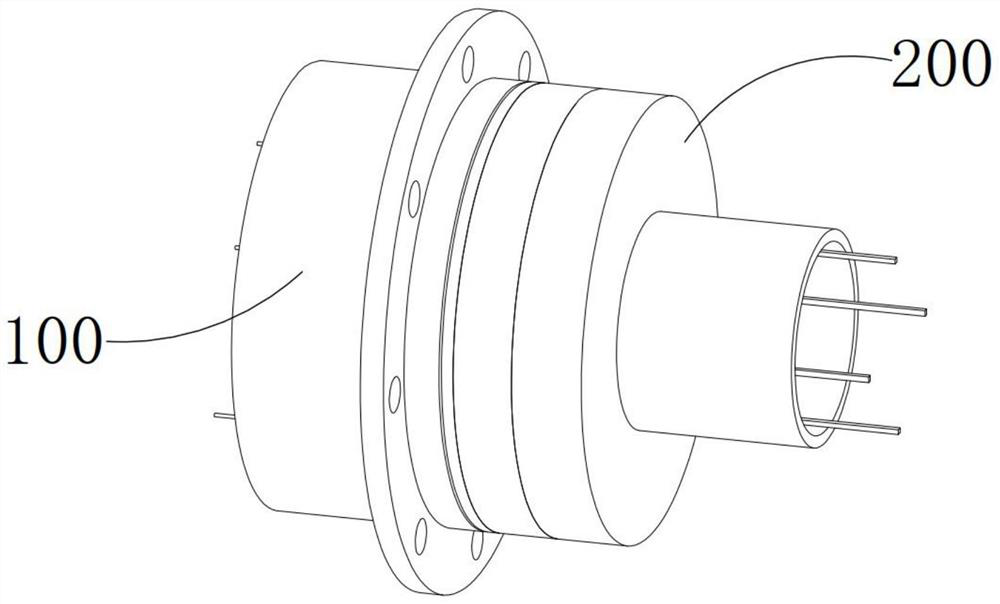
[0045] see Figure 1-20 , a magnetoelectric encryption non-porous data port, which includes an output encryption device 100 connected to a memory to directly establish a data communication channel, a docking decryption device 200 connected to a receiver to directly establish a data communication channel, and an internal communication of the output encryption device 100 itself The channel is disconnected and the internal communication channel of the docking decryption device 200 is always on. The docking decryption device 200 can be docked and connected with the output encryption device 100 and decrypt the output encryption device 100 so that the internal communication channel of the output encryption device 100 is disconnected. Switch to on, and the confidential data inside the memory can be transmitted to the receiver by the output encryption device 100 and the docking decryption device 200 after the on.
[0046] The output encryption device 100 includes a cylindrical mountin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com