USB flash disk fingerprint authentication encryption method
A fingerprint authentication and encryption method technology, applied in the field of information security, can solve the problems of reduced security, effective information exposure, etc., and achieve the effect of reducing possibility, easy to use, and strong encryption performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
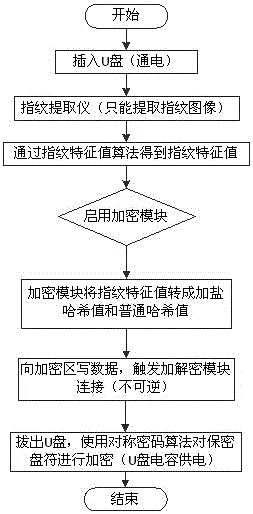
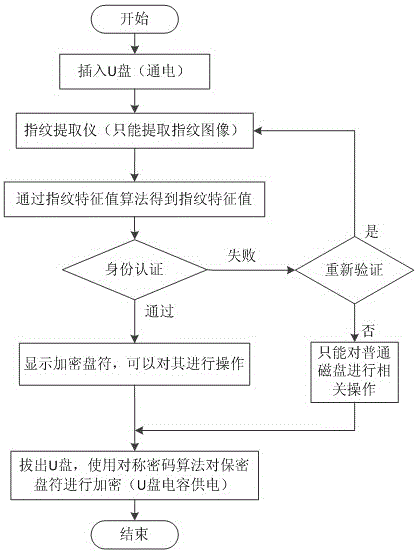
[0034] Embodiment 1: as Figure 1~Figure 3 Shown, a kind of U disk fingerprint authentication encryption method, this method comprises the following steps:
[0035] (1) Fingerprint extraction: insert the U disk, and use the fingerprint extraction device on the U disk to extract fingerprints;
[0036] (2) Generate fingerprint feature value: convert the fingerprint in step (1) into fingerprint feature value through the fingerprint feature value module;
[0037] (3) Encryption module: convert the fingerprint feature value in step (2) into a salted hash value and a normal hash value through the hash conversion module, store the salted hash value in the hidden area, and the U disk is powered on. It will write data to the encrypted area and trigger the encryption module connection;
[0038] (4) Pull out the U disk: the U disk capacitor supplies power, and uses a symmetric encryption algorithm to encrypt the confidential drive letter, and the U disk encryption is completed.
[003...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com