Personalized track data privacy protection method based on semantics
A trajectory data and privacy protection technology, applied in the field of communication, can solve the problems of low data utility, insufficient protection of mobile user privacy, and reduce the risk of real trajectory disclosure, and achieve the effect of high utility.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
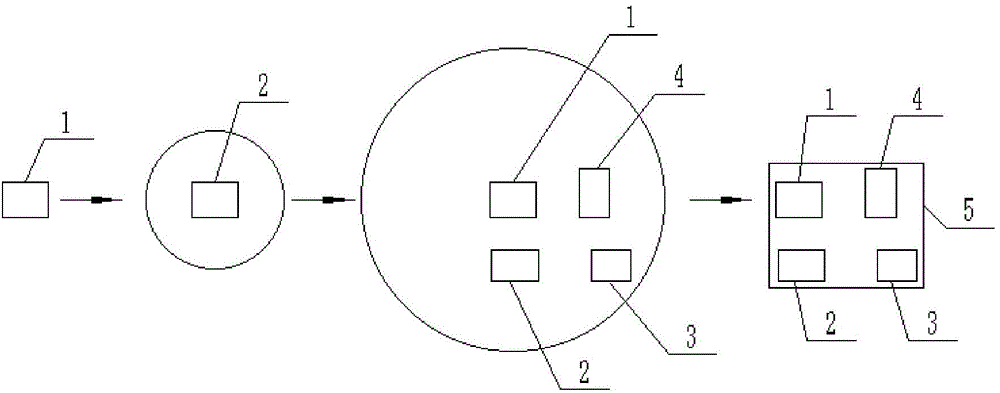
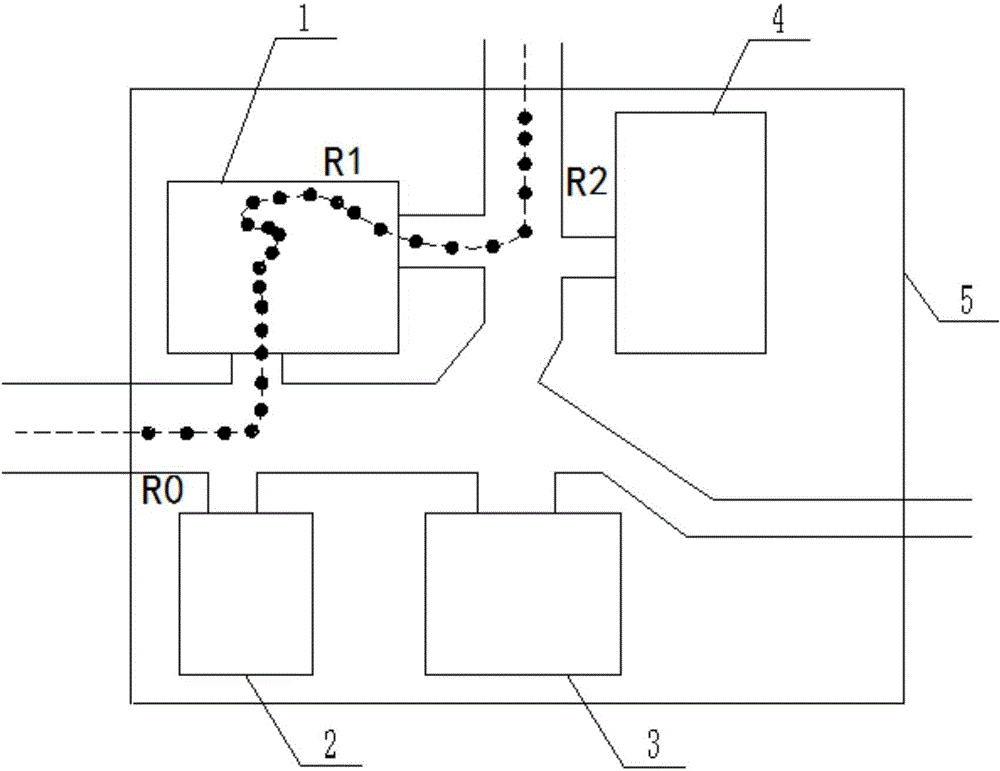
[0057] Please refer to Figure 1 to Figure 4 , Embodiment 1 of the present invention is:
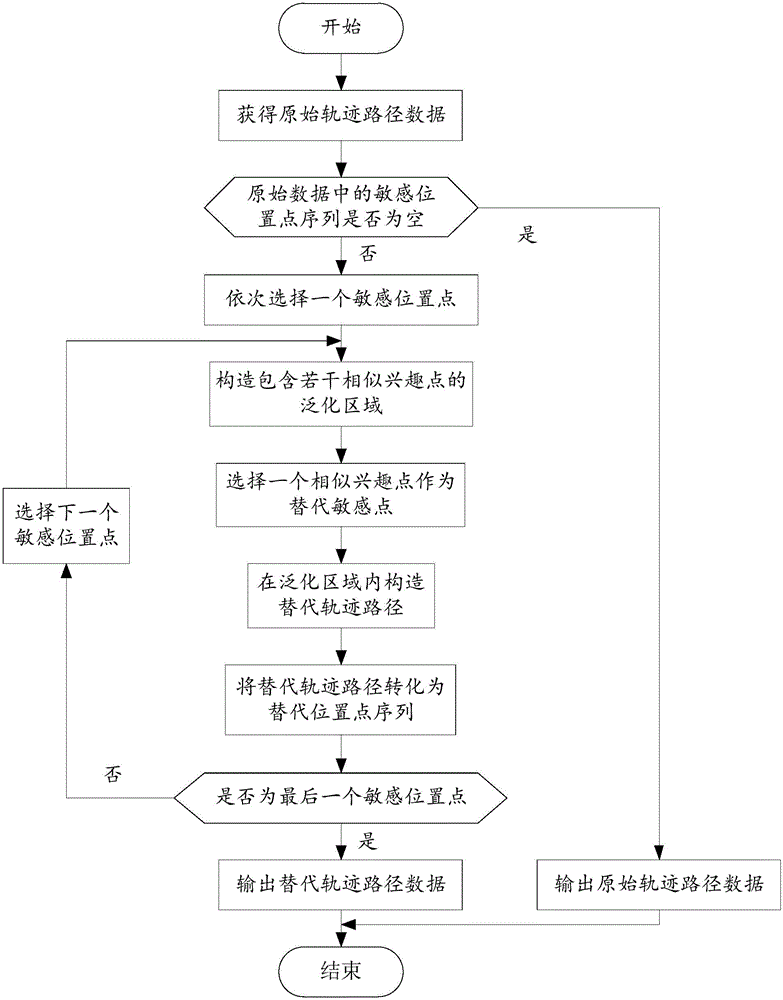
[0058] The present invention provides a semantic-based personalized track data privacy protection method, see figure 2 , the method includes the following steps:
[0059] S1 obtains the sensitive position point sequence that needs to be protected in the original trajectory path data according to the sensitive position point parameters set by the user. If the sensitive position point sequence is empty, the original trajectory path is directly output. If the sensitive position point If the sequence is not empty, proceed to the next step;
[0060] S2 Select a sensitive location point as the first sensitive point 1 according to the sequence of the sensitive location point sequence, and preset the interest threshold of the first sensitive point 1;
[0061] S3 (see figure 1 ) takes the first sensitive point 1 as the center, gradually expands the radius area in the map, and presets the num...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com