Search spam analysis and detection
a search spam and analysis technology, applied in the field of search spam analysis and detection, can solve the problems of search spam putting a burden on the web, search spam traffic can be significant, and certain consumer product sellers bear a disproportionate burden of illicit search spam activity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
lf-monitoring components.
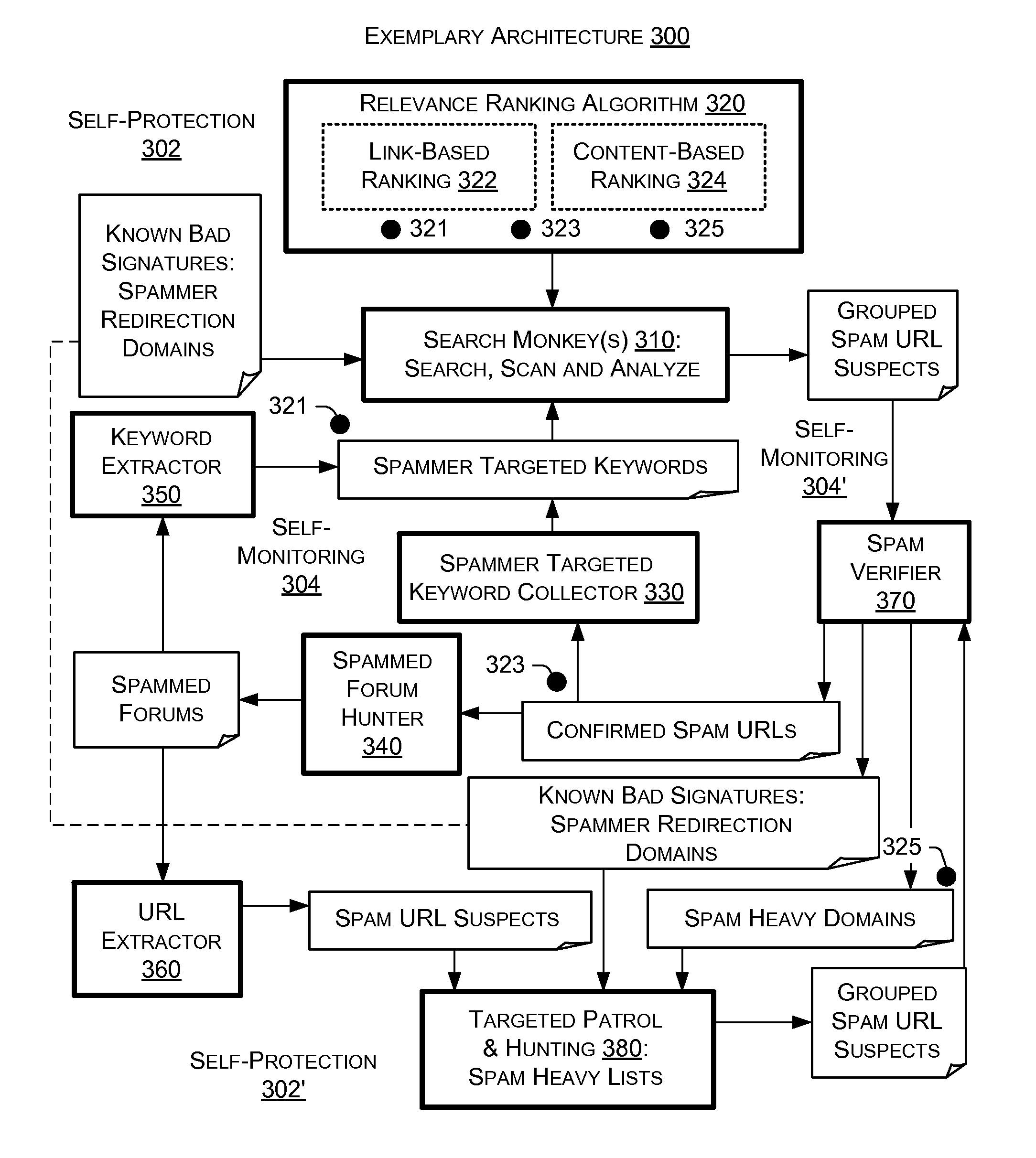
[0009]FIG. 5 is a diagram of an exemplary spam verifier component that uses one or more techniques to verify a spam URL and to optionally output one or more lists or groups of URLs.
[0010]FIG. 6 is a diagram of an exemplary search ranger system and some associated methods.
[0011]FIG. 7 is a diagram of an exemplary spam detection method.
[0012]FIG. 8 is a diagram of an exemplary method that uses an anti-cloaking technique for URLs that use click-through cloaking.
[0013]FIG. 9 is a diagram of an exemplary double-funnel model for analyzing spam and for identifying entities involved in spam.
[0014]FIG. 10 is a diagram of various components of an exemplary computing device that may be used to implement various exemplary methods discussed herein.
DETAILED DESCRIPTION
[0015]As mentioned in the background section, the problem of search spam is not new. Search spam has traditionally been modeled as an information retrieval and relevance ranking problem. For example, convent...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com