Voice print identification portal
a voice authentication and print technology, applied in the field of voice authentication, can solve the problems of increasing the security concerns of the use of computers, the limitations of existing systems, and the difficulty of successfully achieving voice authentication over speech recognition,
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
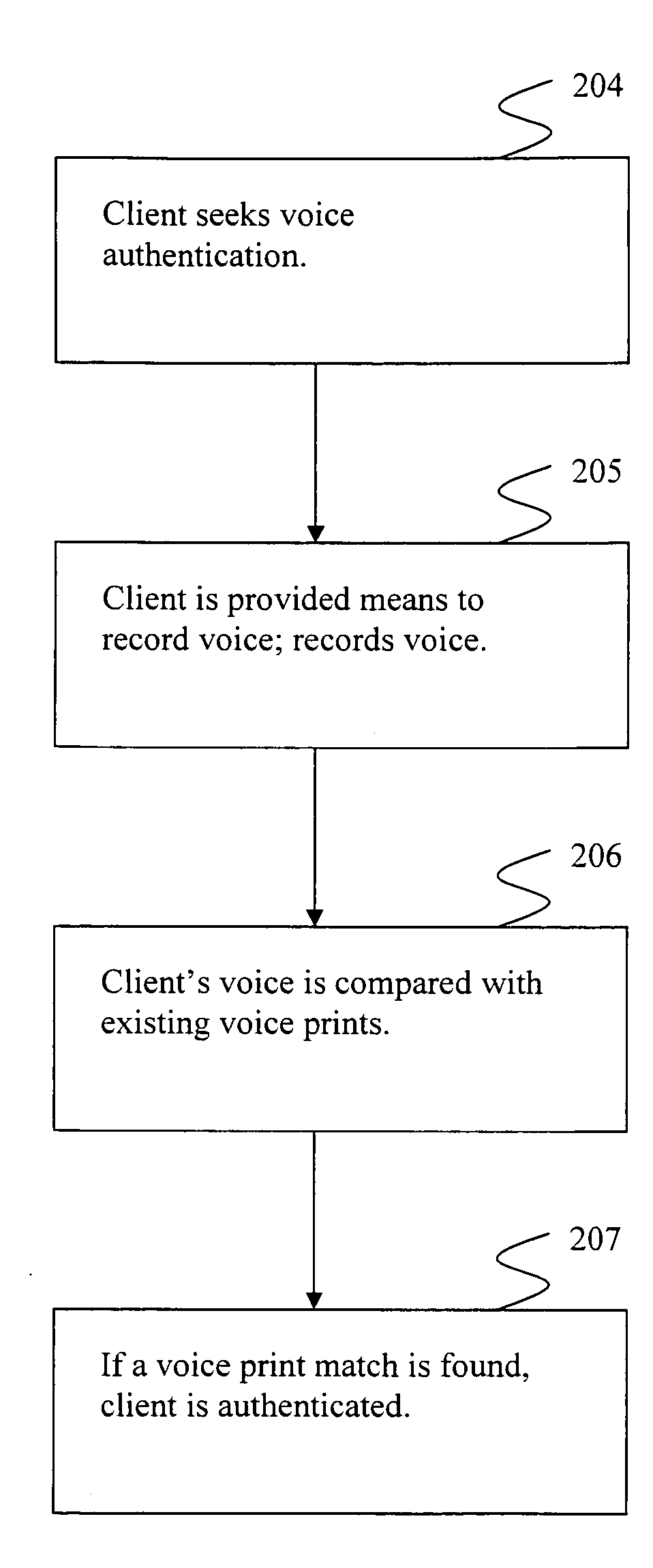
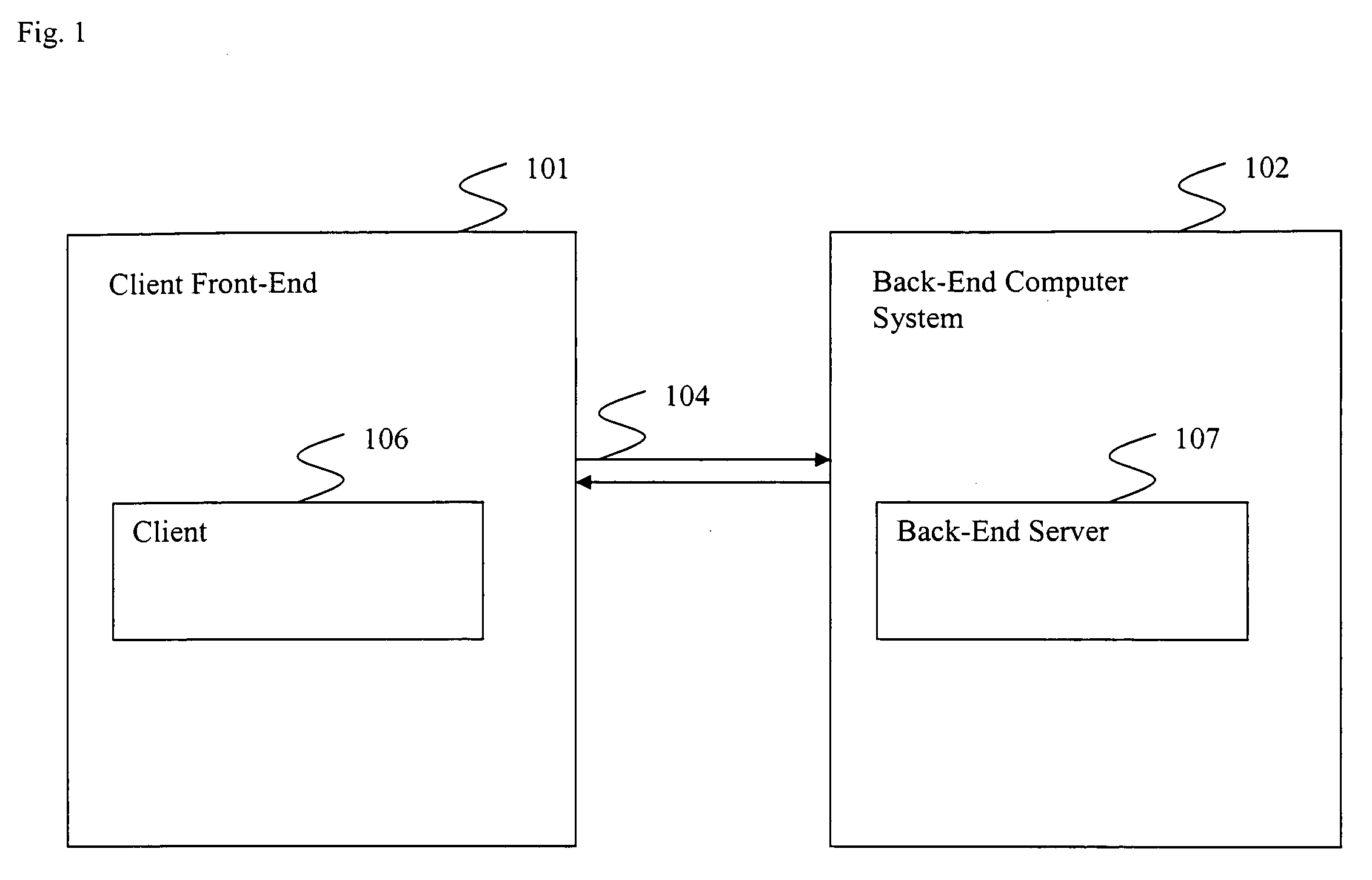
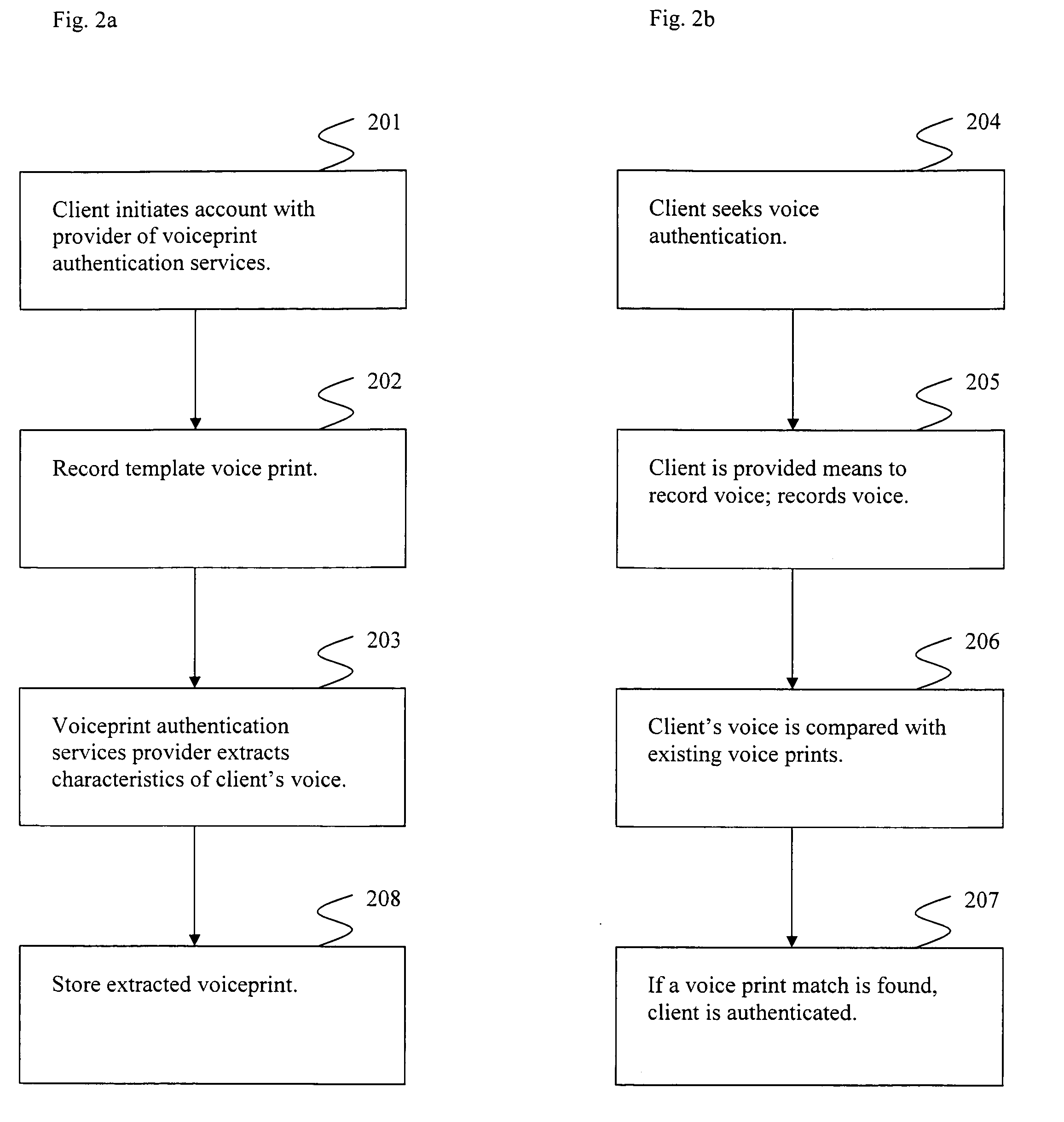
[0031]FIG. 1 illustrates generally a block diagram example of a typical transaction over a network. According to the example of FIG. 1, client 106 seeks to communicate with a business over a network such as the internet. To communicate, client 106 uses a front-end interface 101. Front-end interface 101 may be any means with which a client may access content available over a network. A client may access a front-end interface 101 through any commonly known network access device such as, but not limited to, a computer, a Smartphone, or a PDA. Client 106, through front-end interface 101, communicates with back-end computer system 102. Back-end computer system 102 may include a back-end server 107.
[0032]According to the example illustrated in FIG. 1, front-end interface 101 communicates with back-end computer system 102 through connection 104. A typical transaction usually includes authentication of client 106 by back-end computer system 102. Often, authentication is achieved through cli...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com