Attack path analysis method based on hierarchical attack graph
An attack path and analysis method technology, applied in the field of attack path analysis based on a hierarchical attack graph, can solve problems such as poor real-time performance, and achieve the effects of reducing scale, improving real-time performance, and reducing time and space consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
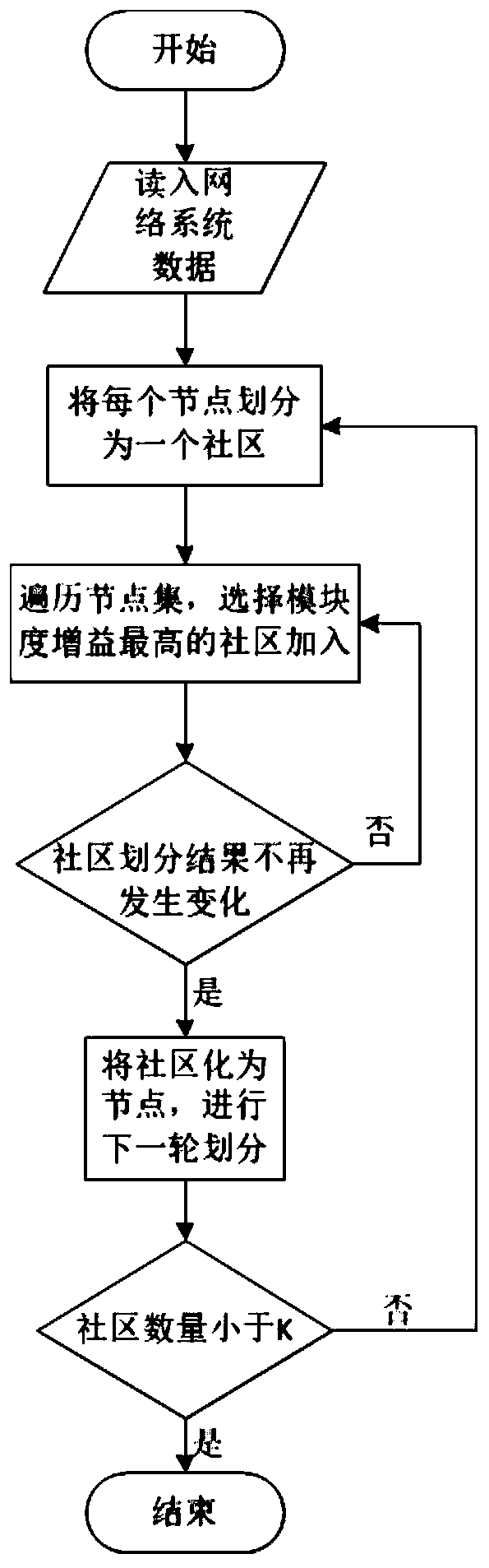
[0082] The present invention will be described in detail below in conjunction with the accompanying drawings and embodiments.
[0083] like Figures 1 to 7 As shown, an attack path analysis method based on hierarchical attack graph includes the following steps:
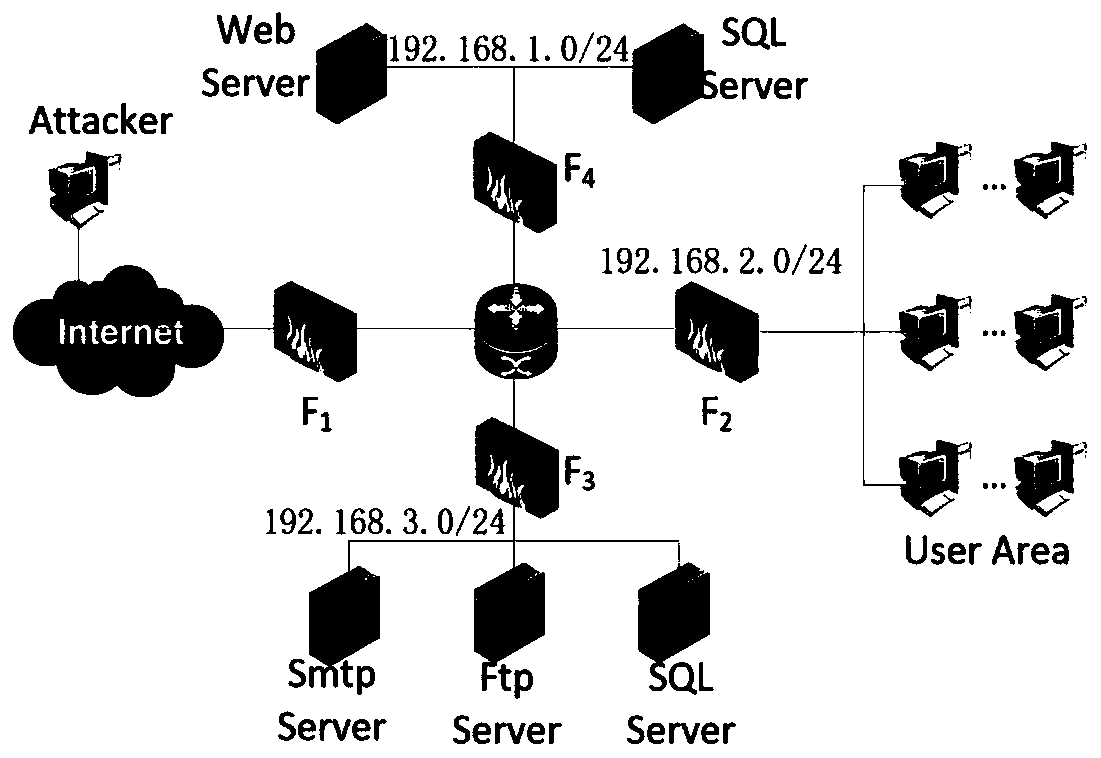
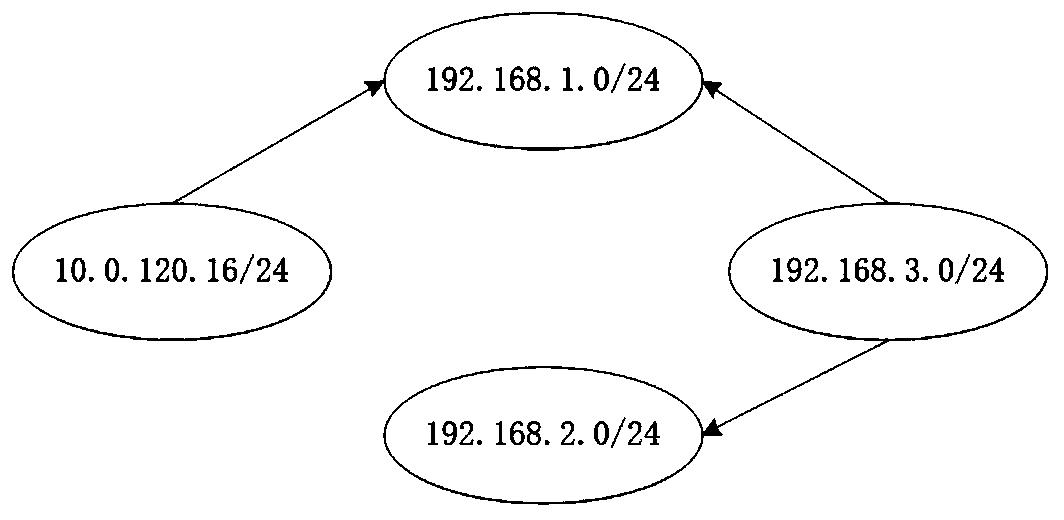
[0084] The network topology diagram of this embodiment is as follows figure 2As shown, the network has three main areas, which are external server area, internal server area, and user area. The external server area includes a web server and a SQL data server, which are used to provide external web browsing and information storage services, and are located in the 192.168.1.0 / 24 network segment; the internal server includes an smtp mail server, an ftp file server, and an SQL data server , providing internal mail communication, file transmission and information storage services, located in the 192.168.2.0 / 24 network segment. The user area is in the 192.168.3.0 / 24 network segment, including 20 hosts. The attacker is ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com