Internet of Things (IoT) DDoS attack defense method and device based on SDN, equipment and medium
An IoT device and IoT technology, applied in the field of network security, can solve the problems of high cost and poor DDoS attack defense effect, and achieve the effect of increasing flexibility, improving defense effect, and reducing defense cost.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
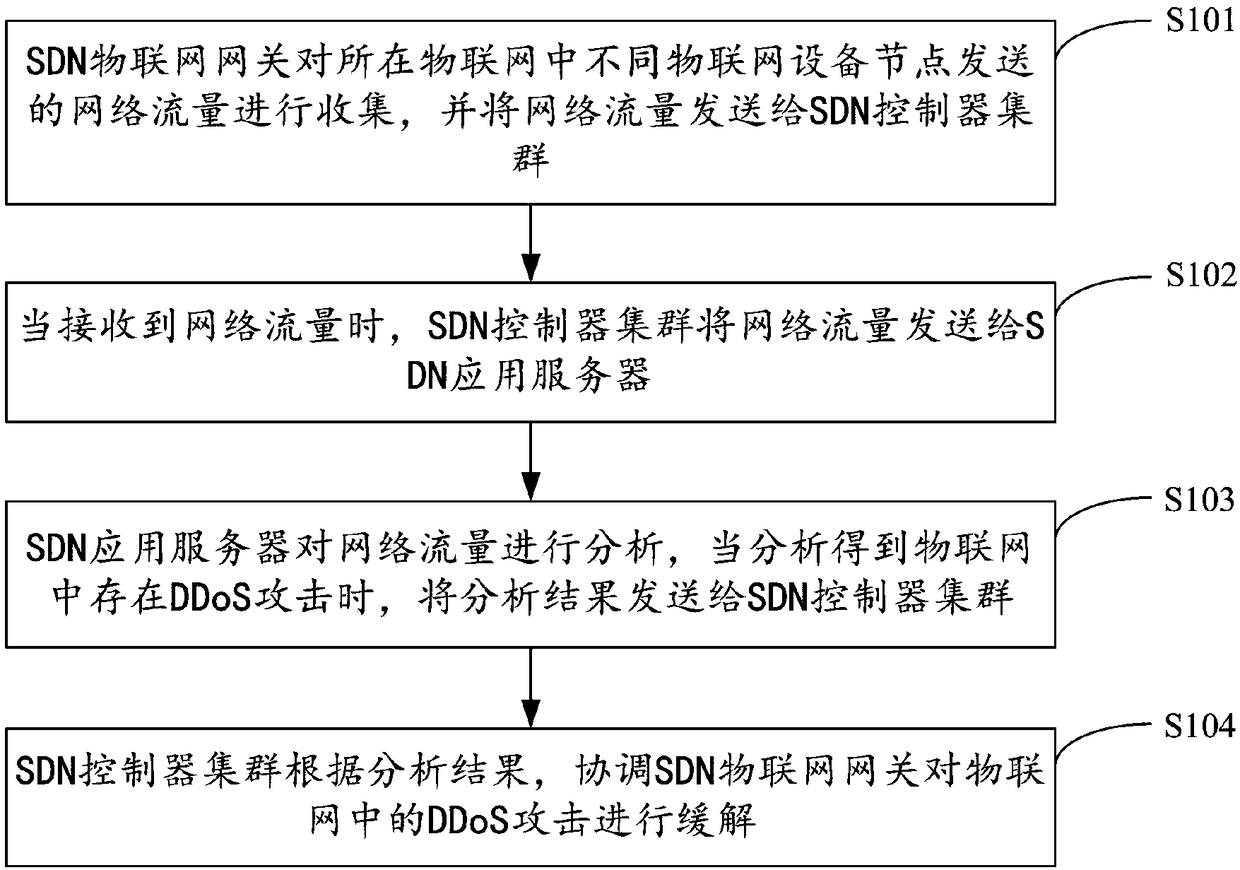
[0028] figure 1 The implementation process of the SDN-based Internet of Things DDoS attack defense method provided by Embodiment 1 of the present invention is shown. For the convenience of description, only the parts related to the embodiment of the present invention are shown, and the details are as follows:
[0029] In step S101, the SDN IoT gateway collects network traffic sent by different IoT device nodes in the IoT, and sends the network traffic to the SDN controller cluster.
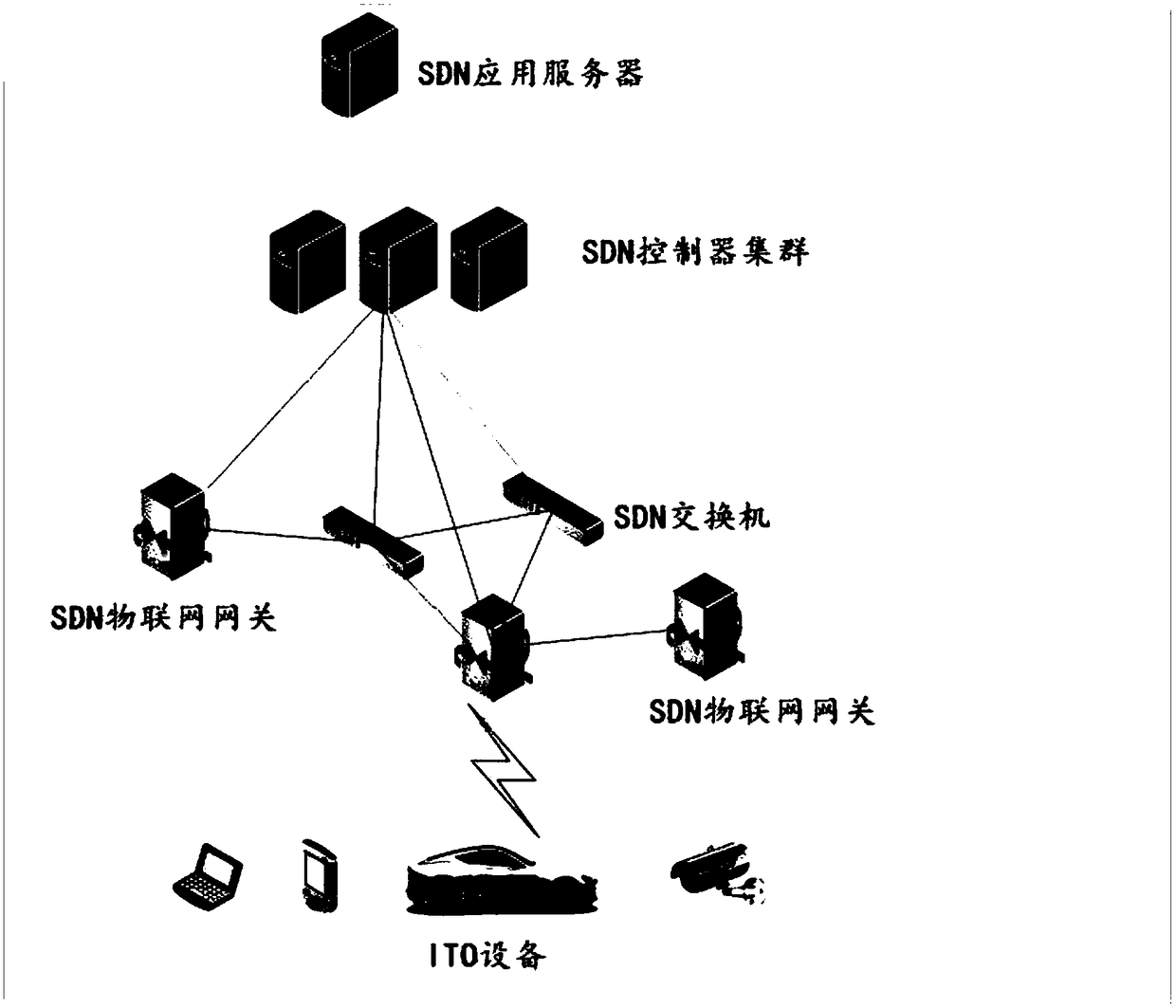
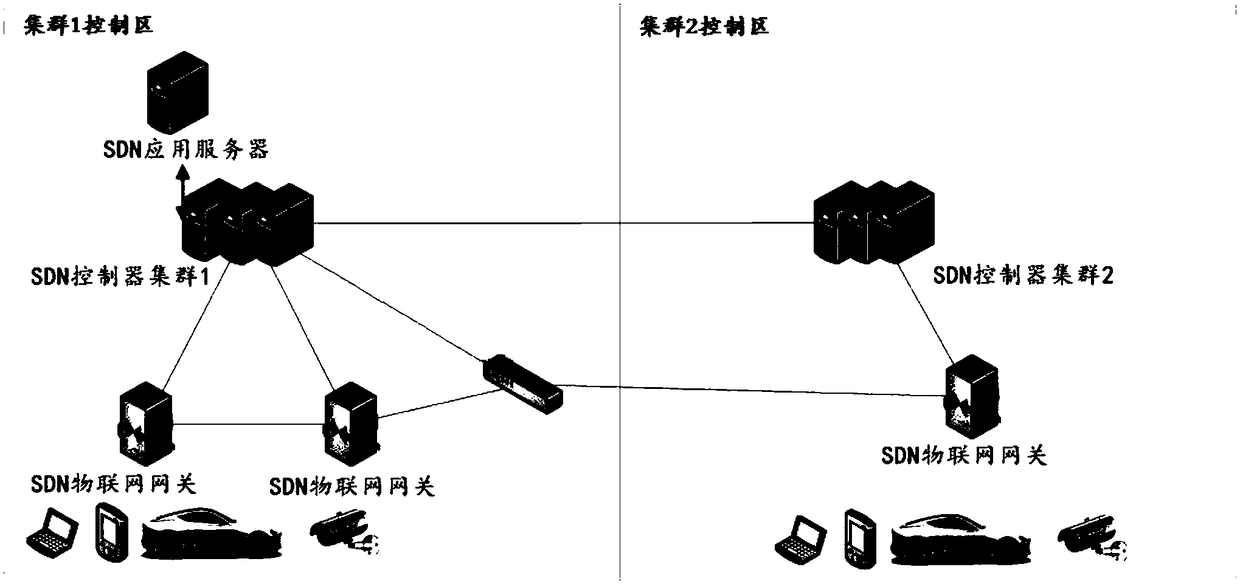
[0030] In the embodiment of the present invention, the Internet of Things where the SDN Internet of Things gateway is located is composed of SDN application servers, SDN controller clusters, SDN Internet of Things gateways, SDN switches, and IOT devices (Internet of Things devices, such as smart terminals, sensors), etc., Among them, the SDN IoT gateway is used to manage the routing between IOT devices, and the SDN controller cluster is used to manage the routing between different SDN IoT gateways...
Embodiment 2
[0045] Figure 5 The structure of the SDN-based Internet of Things DDoS attack defense device provided by Embodiment 2 of the present invention is shown. For the convenience of description, only the parts related to the embodiment of the present invention are shown, including:
[0046] The traffic collection unit 51 is used for the SDN IoT gateway to collect the network traffic sent by different IoT device nodes in the IoT, and send the network traffic to the SDN controller cluster.
[0047] In the embodiment of the present invention, the Internet of Things where the SDN Internet of Things gateway is located is composed of SDN application servers, SDN controller clusters, SDN Internet of Things gateways, SDN switches, and Internet of Things devices. Routing between networked devices, SDN controller clusters are used to manage routing between different SDN IoT gateways, between SDN IoT gateways and SDN switches, and between different SDN switches, different SDN IoT gateway mana...
Embodiment 3
[0058] Figure 6 The structure of the SDN-based Internet of Things DDoS attack defense device provided by Embodiment 3 of the present invention is shown. For the convenience of description, only the parts related to the embodiment of the present invention are shown, including:
[0059] The identity verification unit 61 is configured to perform identity verification on the Internet of Things device node by the SDN Internet of Things gateway when the Internet of Things device node is detected.
[0060] The connection establishment unit 62 is configured to establish a connection with the IoT device node when the SDN IoT gateway successfully verifies the identity of the IoT device node.
[0061] In the embodiment of the present invention, when the SDN Internet of Things gateway detects an IoT device node, the SDN Internet of Things gateway performs identity verification on the Internet of Things device (for example, through the physical fingerprint of the Internet of Things device...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com