Network safety protection method and system
A network security and protection system technology, applied in the field of network security protection, can solve the problem of time-consuming and laborious search, isolation, and repair, and achieve the effect of defending against network attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
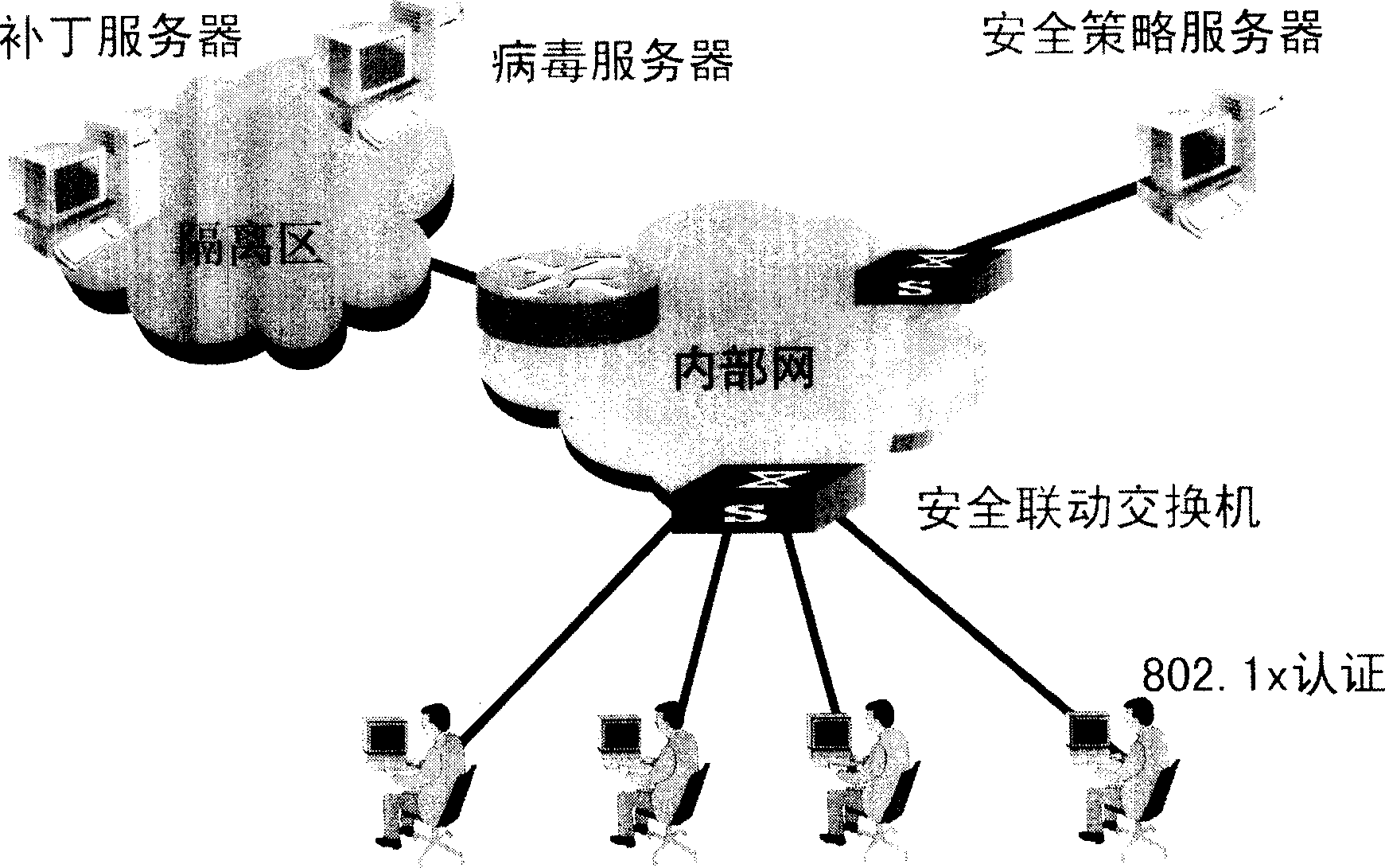
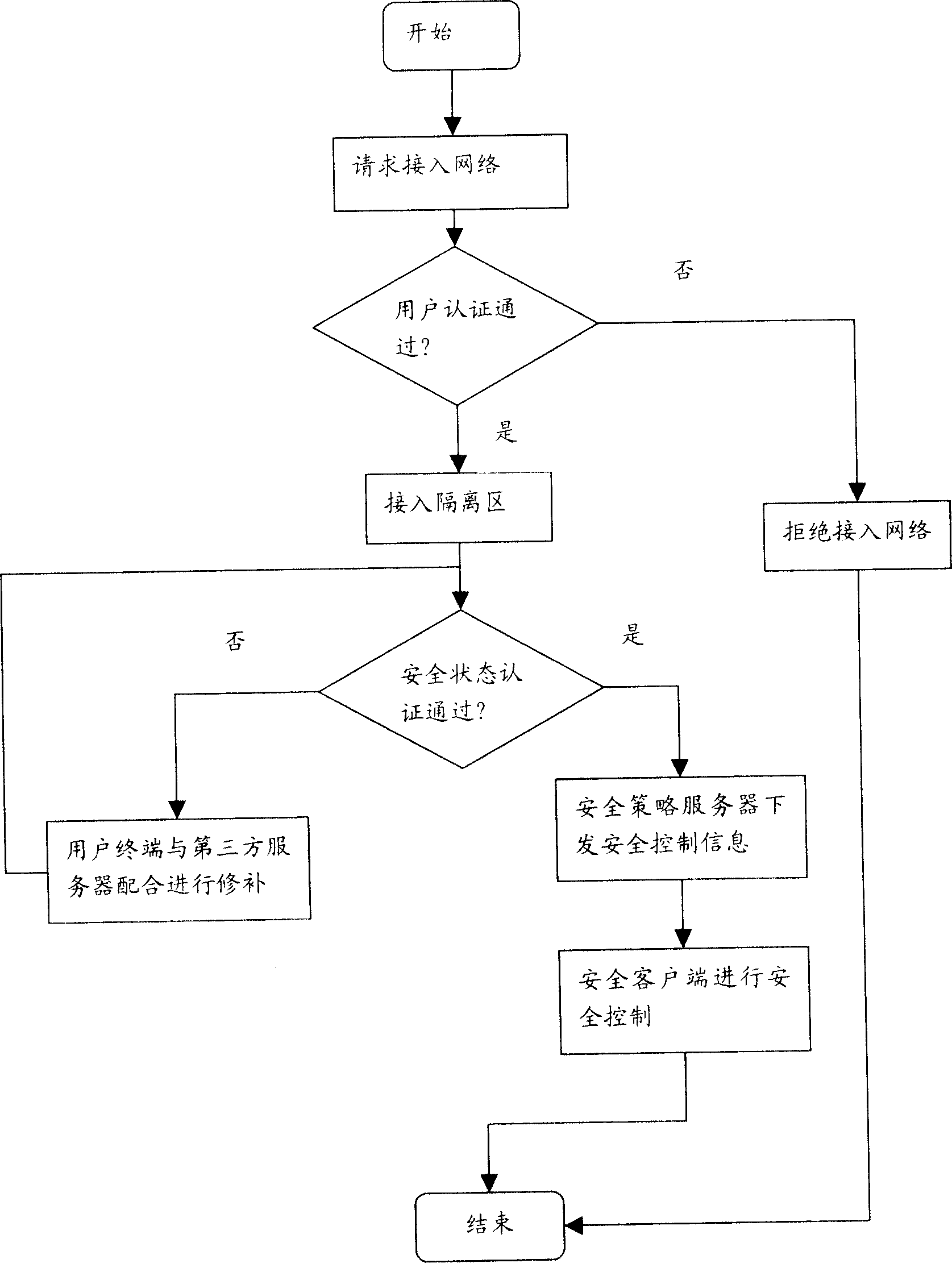
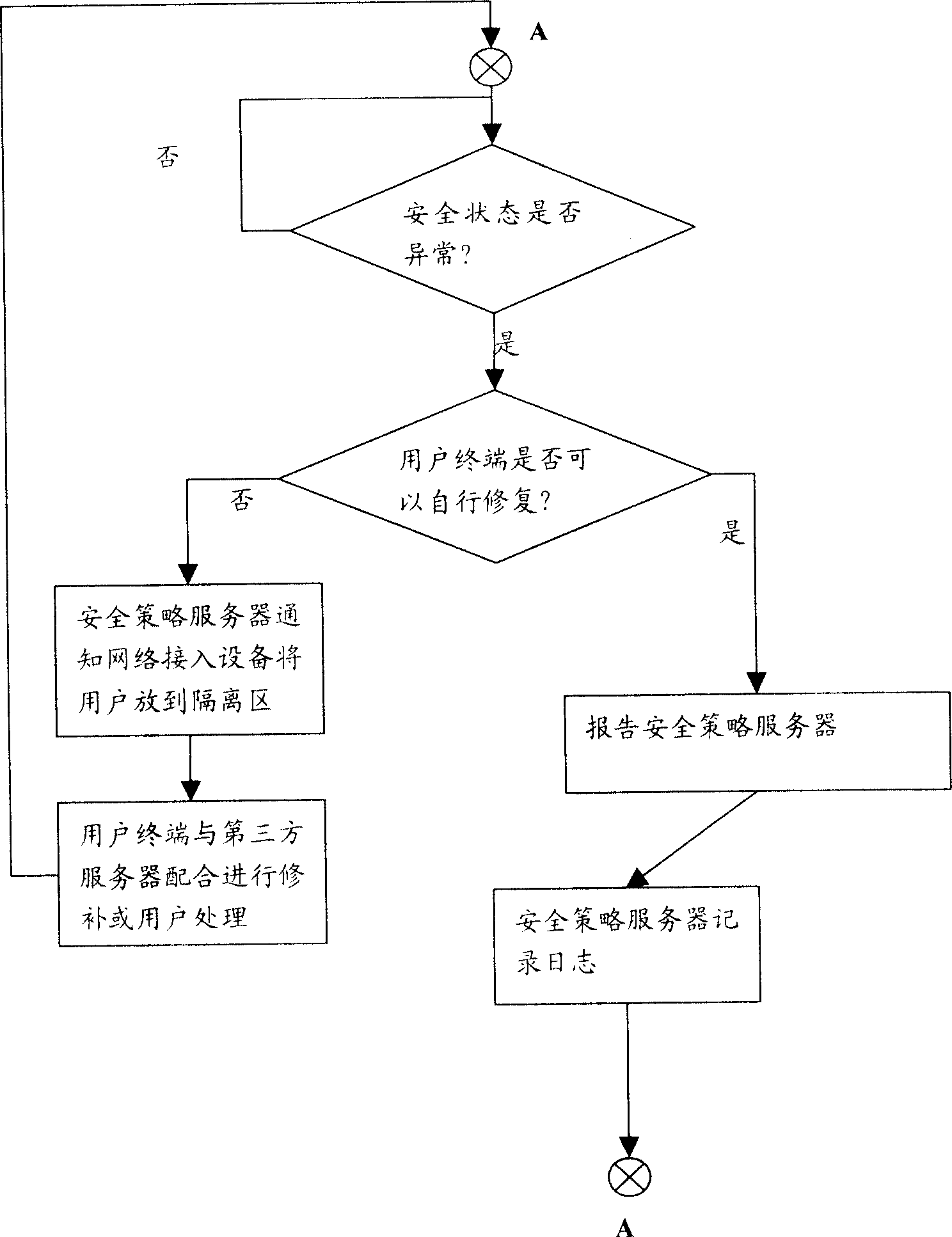
[0037] The essence of the present invention is to provide security authentication for user terminals accessing the network. If the security status of the user terminal does not meet the security policy requirements of the network being accessed, the user terminal is temporarily isolated in an isolated network area with third-party network services. , and use the third-party network service to repair the corresponding security status for the user terminal, so that it meets the security policy requirements of the connected network, thereby ensuring that the entire network is always in an overall unified security protection policy state. In addition, it can also control the user terminal to be monitored all the time during the online process. Once there is a situation that does not comply with the security policy, security measures will be taken in time to control the entire network from damage, such as the above-mentioned isolation of the user terminal that does not comply with th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com