Method and system for detecting application program behavior legality
An application and detection method technology, applied in the direction of platform integrity maintenance, instruments, electronic digital data processing, etc., can solve the unknown security loopholes in applications, cannot identify and prevent illegal behavior of legitimate applications, and cannot distinguish applications, etc. problem, to achieve good defense effect, high recognition rate, low false alarm rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
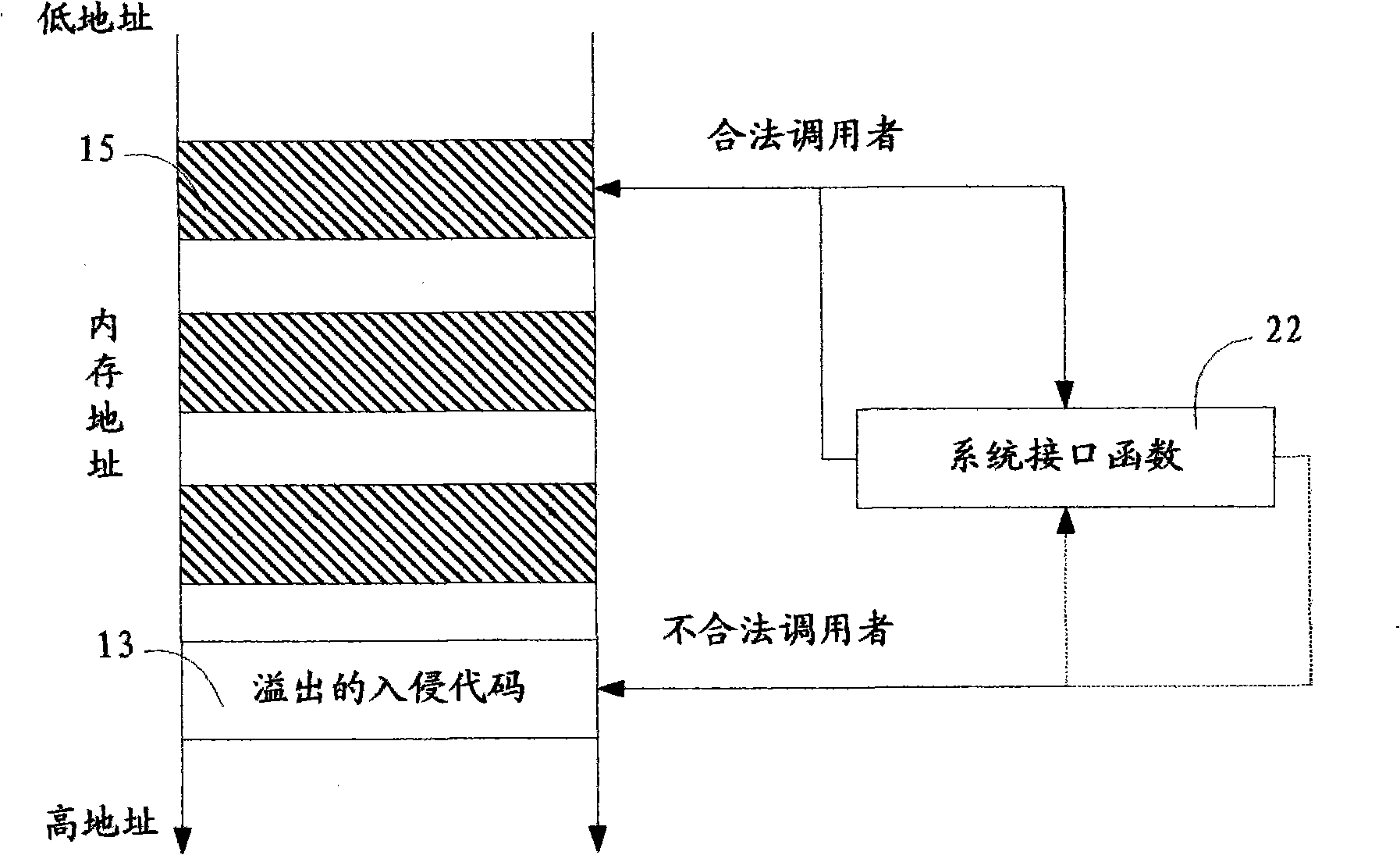
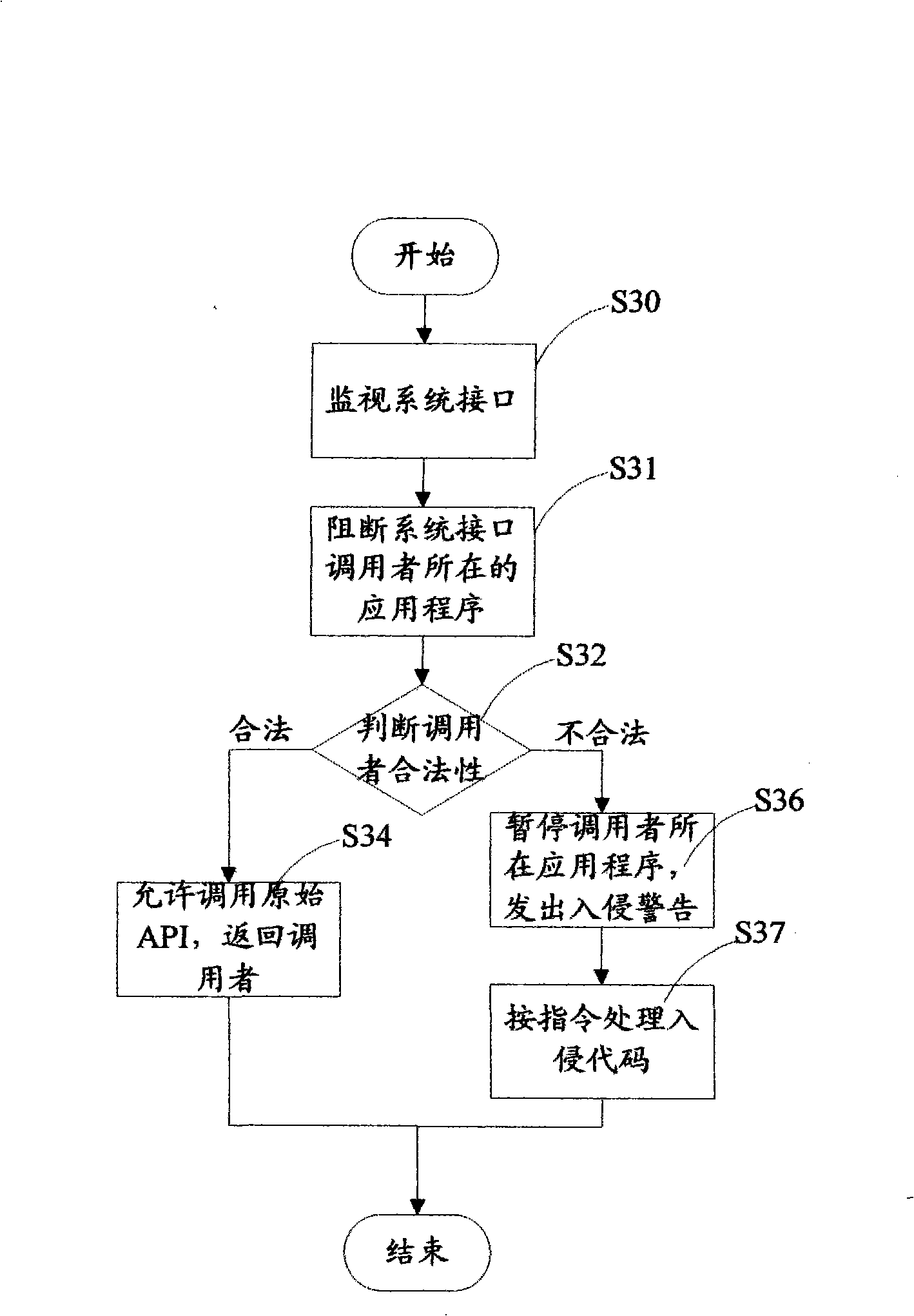
[0024] In modern operating systems, various behaviors of applications must be implemented by calling system interfaces. Therefore, as long as the caller of the system interface is traced, the actual controller of the application behavior can be found. That is to say, by monitoring some system interfaces that may be used by malicious intruders and verifying the legitimacy of the callers of these system interface functions, it is possible to identify whether the actual controllers of these behaviors are legal, thereby detecting intruders Illegal actions performed through compromised applications.
[0025] In order to illustrate the working principle of the present invention, how the intruder invades the application program is firstly described below.
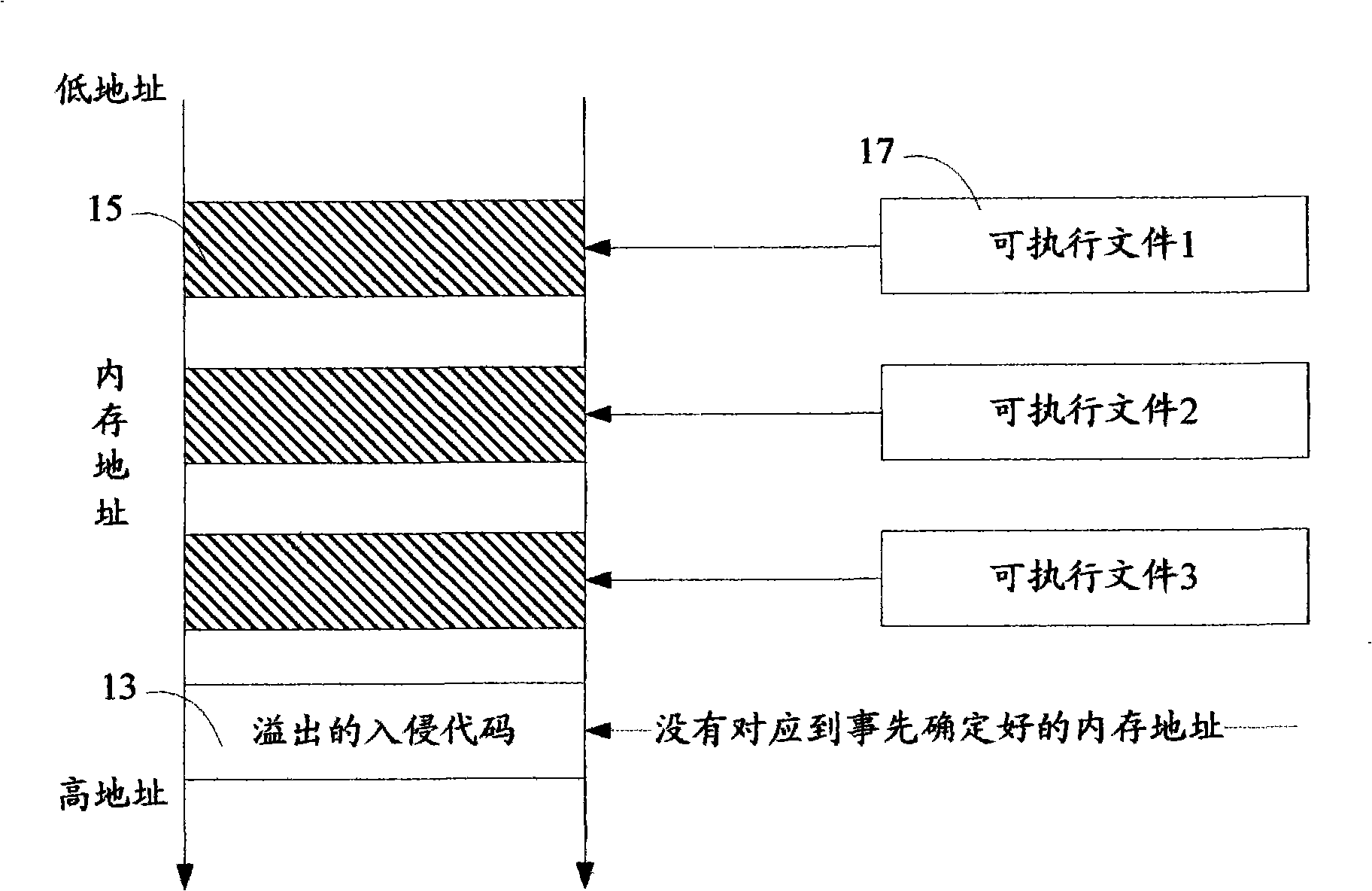
[0026] First, overflow vulnerabilities exist in many applications. The overflow vulnerability is caused by one or some input functions (user input parameters) in the program not strictly verifying the boundaries of the received ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com