Double-layer defense method facing power system false data injection attack
A power system and false data technology, applied in transmission systems, data processing applications, electrical components, etc., can solve the problems of power system miscuts and misoperations, damage to power grid information integrity, attacks, etc., to achieve the effect of protecting resources and optimizing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] The technical solutions of the present invention will be described in detail below in conjunction with the accompanying drawings.
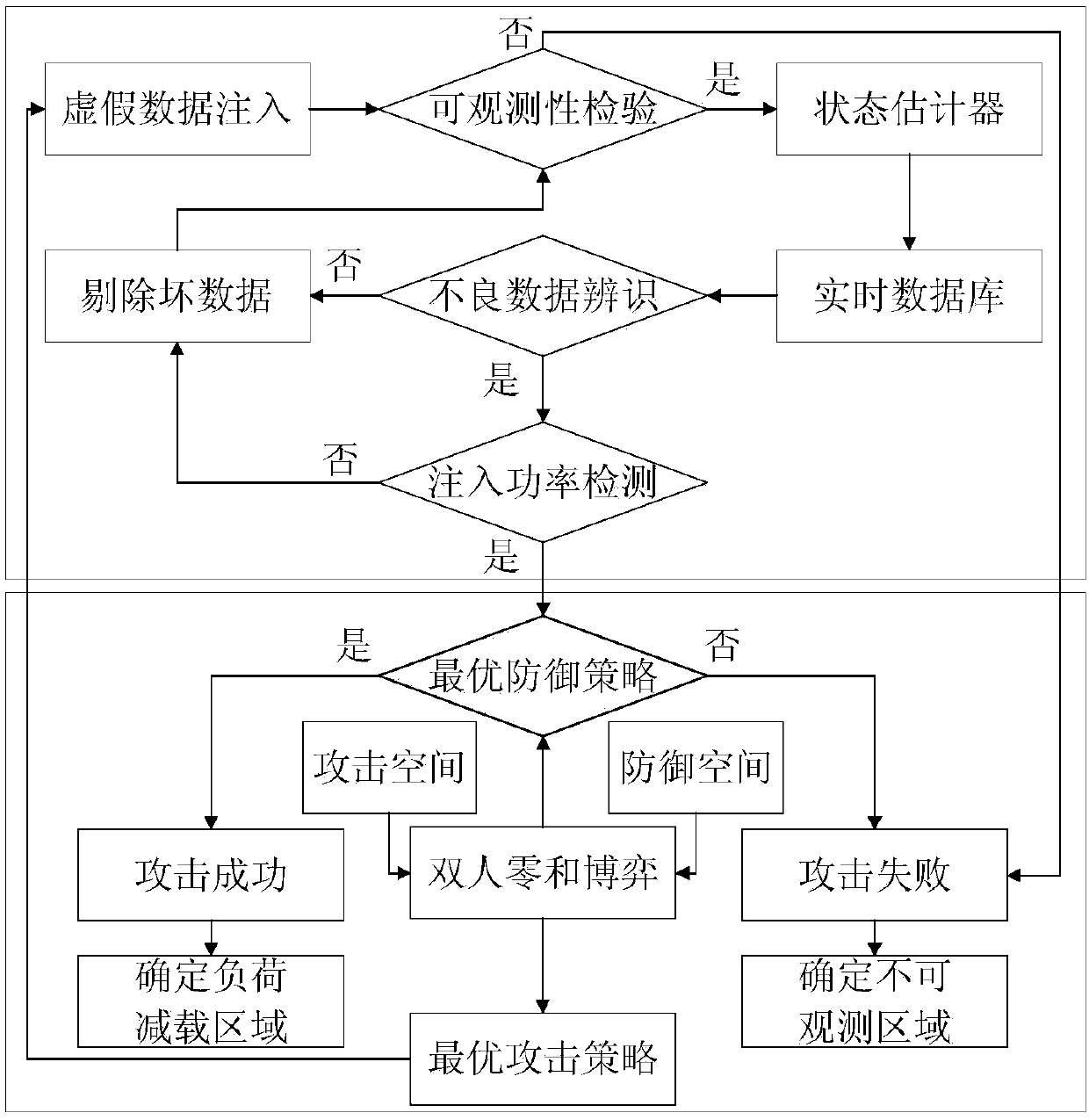
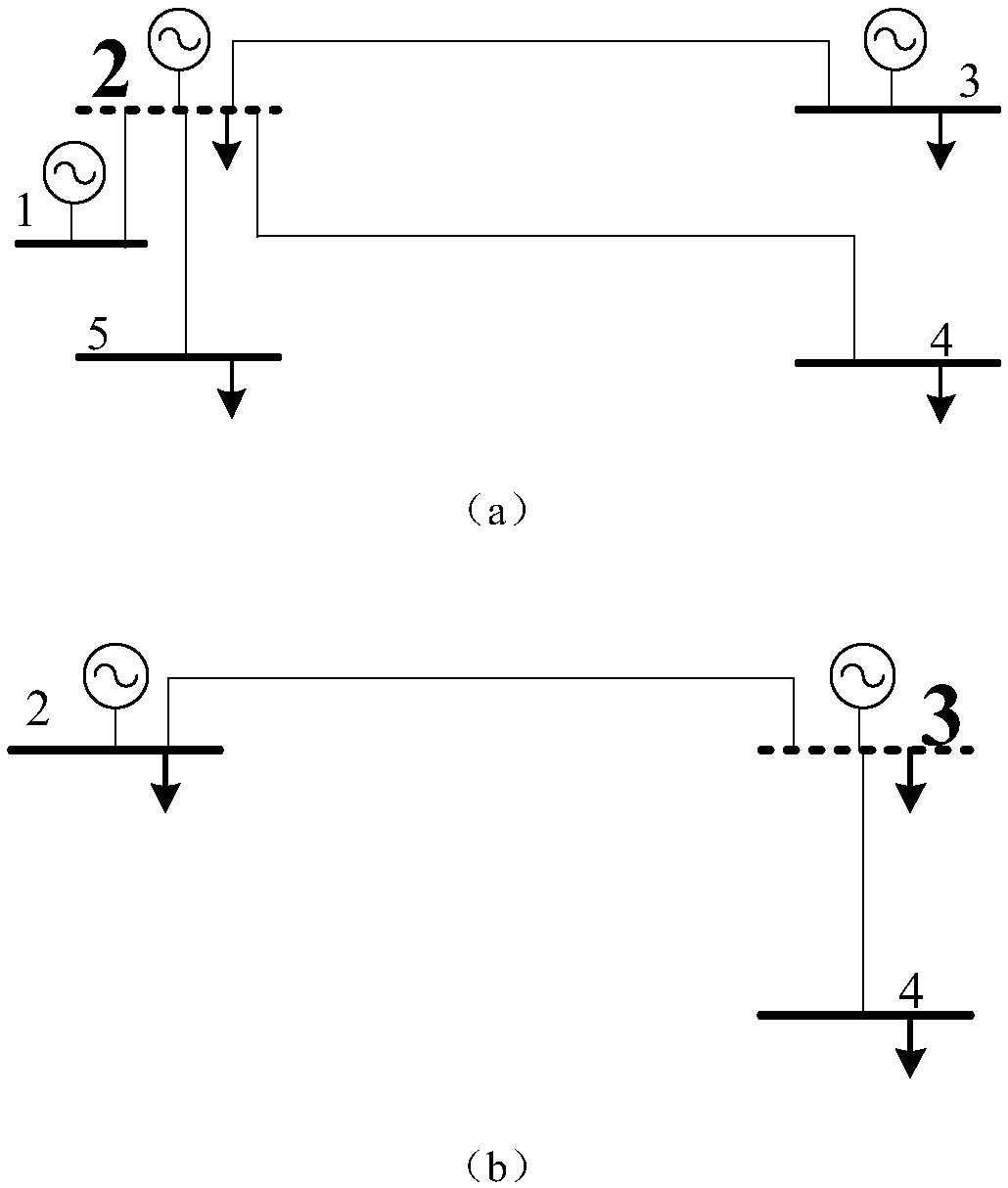
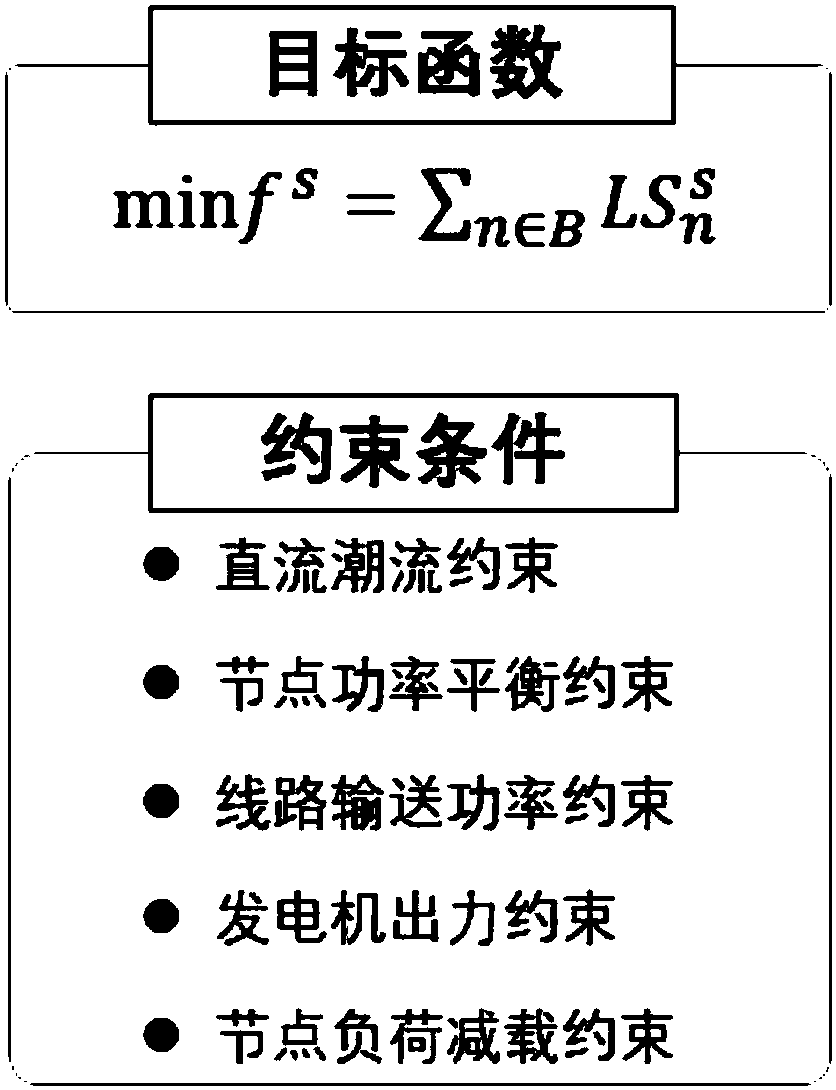
[0048] The present invention provides a double-layer defense method for false data injection attacks in electric power systems. Based on the actual attack and defense principles and game theory, the false data injection attacks are detected and defended, and the consequences of attacks on the system are minimized. In the present invention, the characteristics of false data injection attack: the data tampering object is the state value of the power element (including node voltage amplitude, phase angle, generator output active power, reactive power and line active power, reactive power flow power), in the attack For a certain power component, it is necessary to carry out a coordinated attack on the line connected to the component and all components in the node to ensure that the state information in this range is consistent and conforms to th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com