Method and system for detecting bot network
A botnet and zombie technology, applied in the transmission system, digital transmission system, data exchange network, etc., can solve problems such as difficult to achieve effective results, and achieve good overall defense effect, good defense effect, and effective defense effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
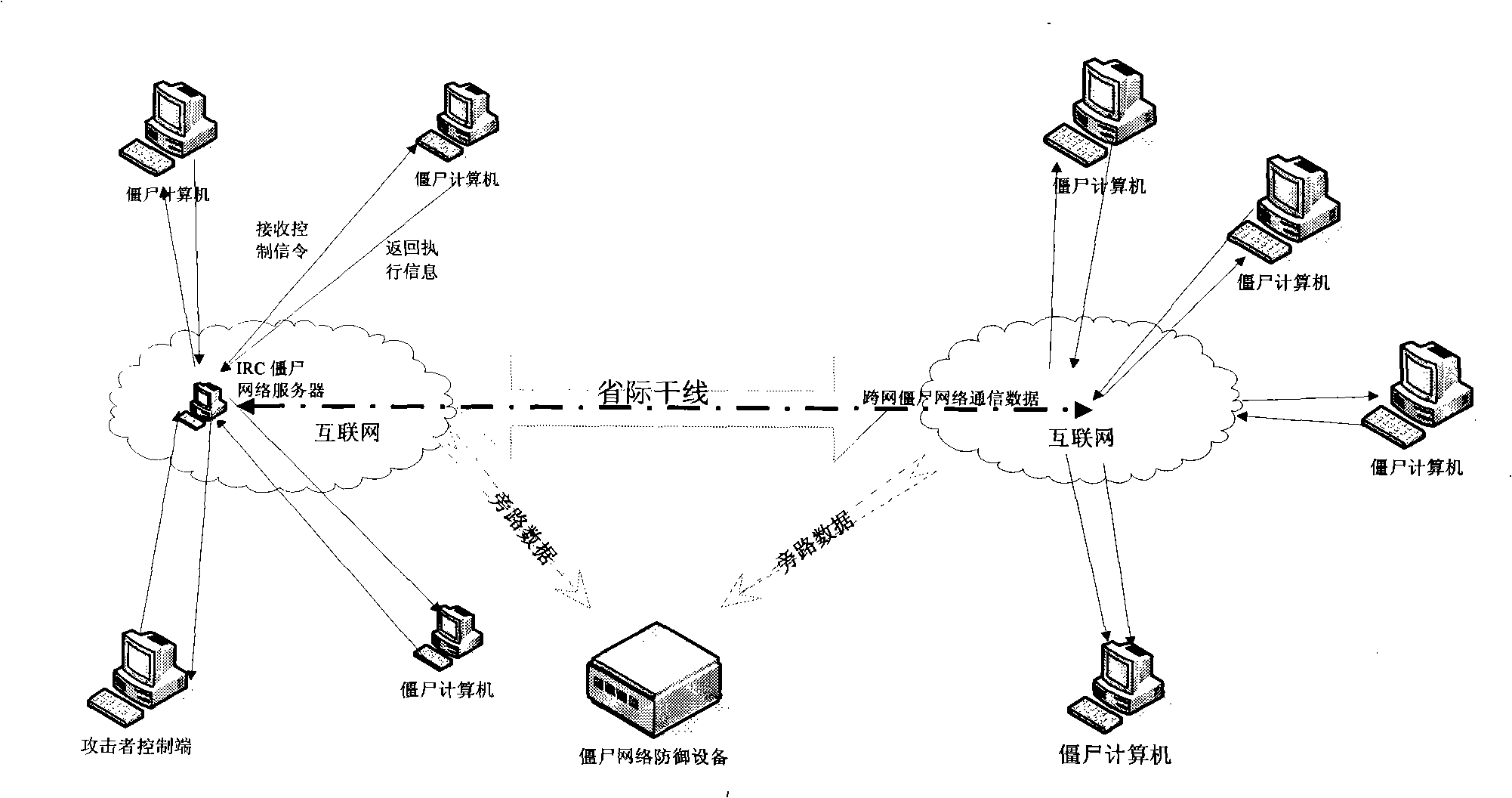
[0048] 1. Deployment location:
[0049] Deploy this device to the inter-provincial outlet of the Internet, bypass the data flowing into and out of the provincial outlet, and then connect the bypassed data to the device.
[0050] 2. Data processing process:
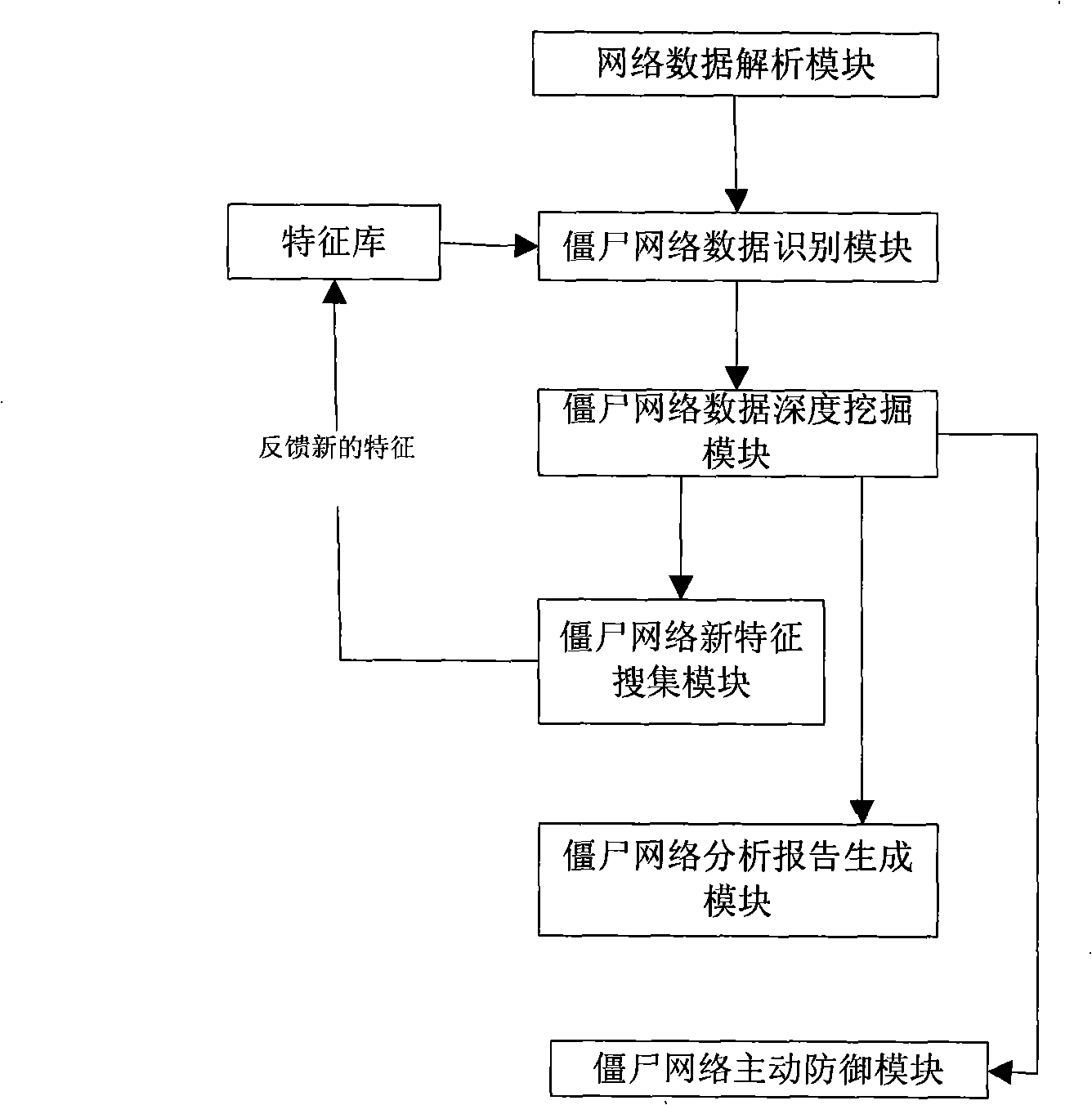
[0051] (1) The bypassed data flows into the "network data analysis module" module, which analyzes the data according to the TCP / IP network protocol framework, extracts the data of the IRC protocol in the network, and transfers it to the "botnet data identification module" ", other data will be discarded without processing.
[0052] (2) The "botnet data identification module" loads the feature codes in the botnet communication data feature database, and compares these feature codes with the IRC protocol data parsed by the "network data analysis module", so as to find the botnet data packets . The found botnet data packets, as well as the parsed source IP and destination IP, source port number and destination port number,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com