Personal information protection method for handset
A technology for information protection and mobile phones, which is applied in the field of improvement of personal information protection methods, can solve problems such as easy loss or theft, and achieve the effect of protecting personal privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
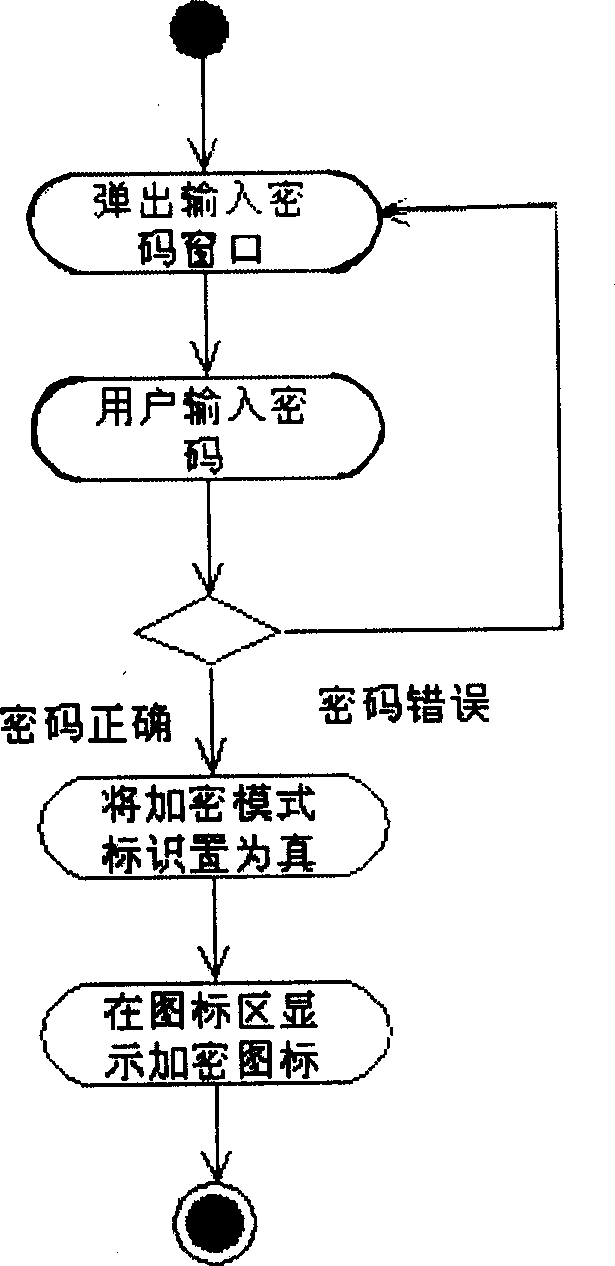
[0027] Example 1. A method for protecting personal information of a mobile phone, see Figure 1 ~ Figure 2 . It includes the following steps:
[0028] (1) The steps of storing the encrypted mode in the random access memory saved after power failure, setting or modifying the password of the mobile phone and storing it in the read-only memory;
[0029] (2) Add an "encryption mode" submenu under the EEPROM management menu of the mobile phone, the default is "cancel" status, and the step of "entering the mobile phone password" will be displayed on the screen after confirmation;
[0030] (3) After entering the set password, set the encryption mode flag to true, and then display the steps of "encryption mode has been set" and the encryption icon;
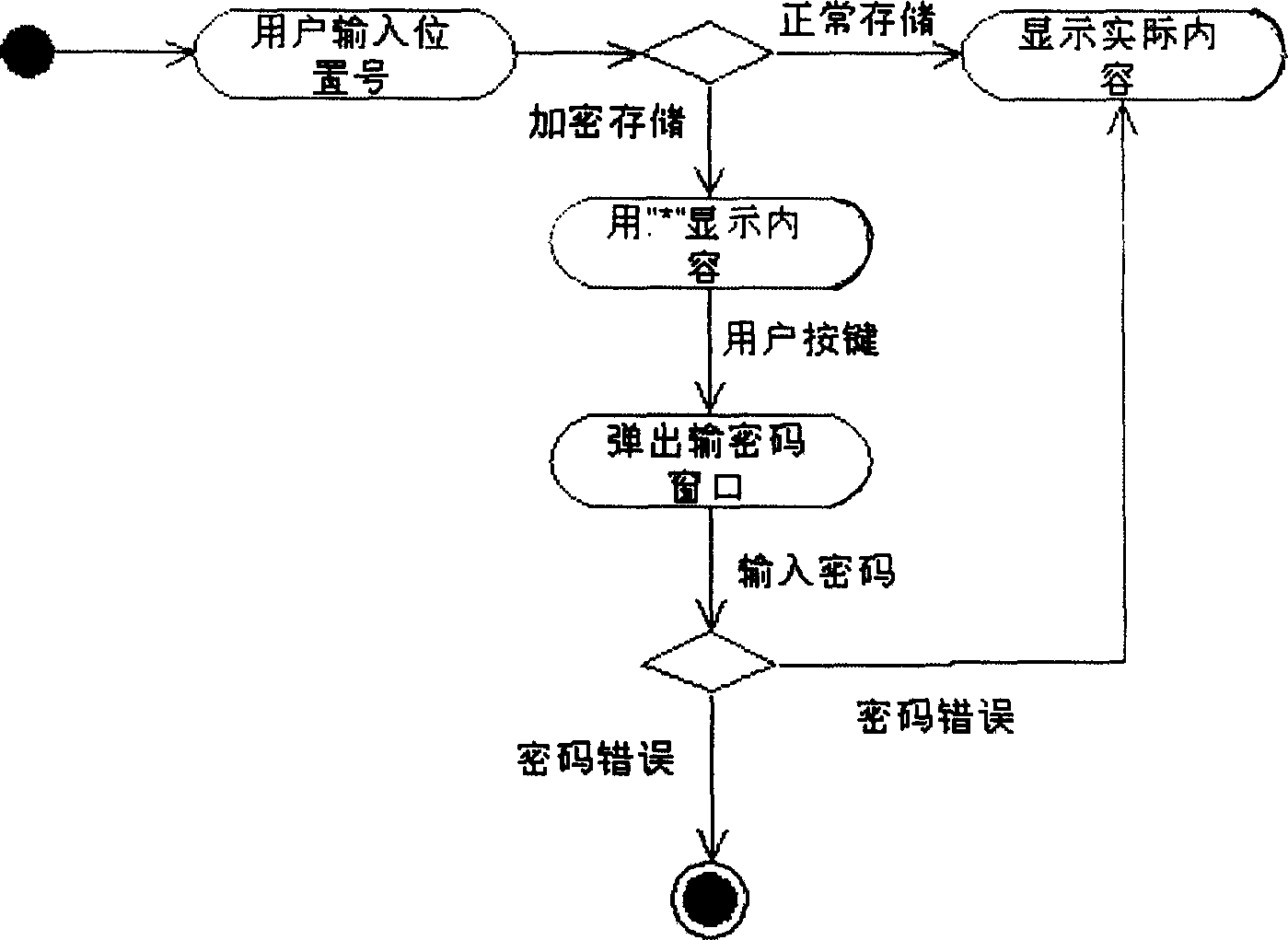
[0031] (4) Start the phone book storage function, when selecting the location storage mode to input, the mobile phone first reads the value of the encryption mode identification in the random access memory, confirms that this value is ...
Embodiment 2
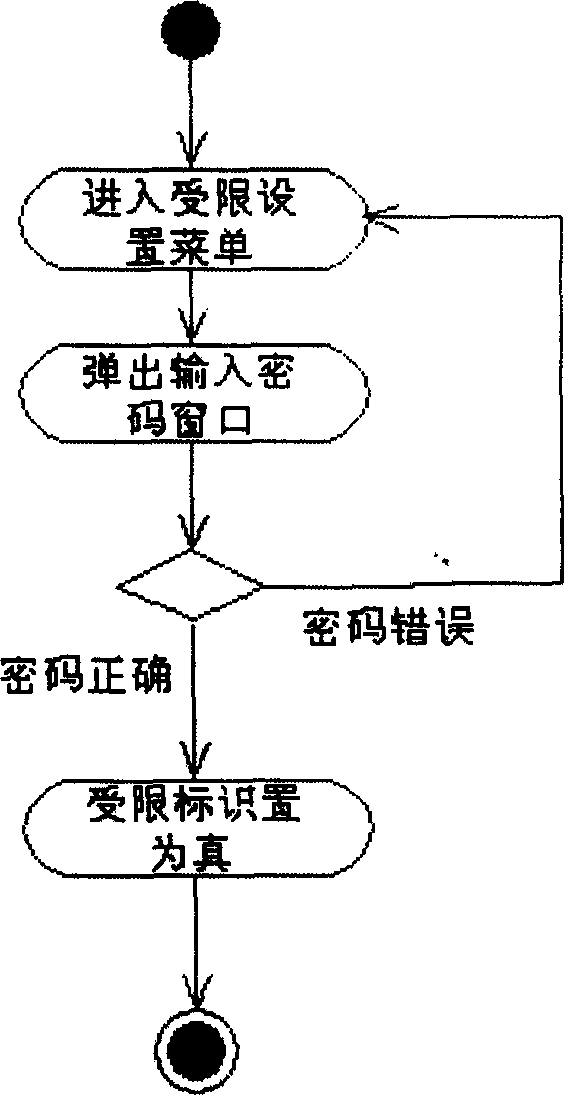
[0042] Example 2. A method for protecting personal information of a mobile phone, see image 3 . On the basis of embodiment 1, it sets the limited function of the phonebook. Include the following steps:
[0043] (1) the step of storing the phonebook restricted identifier in the random access memory saved after power-off;
[0044] (2) Add a "Phone Book Restricted" submenu under the EEPROM management menu of the mobile phone, the default is "Cancel" status, and the step of asking "Enter mobile phone password" will be displayed on the screen after confirmation;
[0045] (3) After inputting the password, the CPU of the mobile phone compares this password with the mobile phone password stored in the read-only memory, if identical then the phone book limited sign stored in the random access memory saved after power failure is set to true, and Steps to display "Phone book restricted functions have been set" and return to the standby state;
[0046] (4) If you want to use the phone ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com