Direct anonymous attestation method applied to credible mobile terminal platform
A mobile terminal and platform technology, applied in wireless communications, electrical components, security devices, etc., can solve problems such as large computational load, long key length, system security and performance bottlenecks, and achieve reduced computational overhead and high security and reliability. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
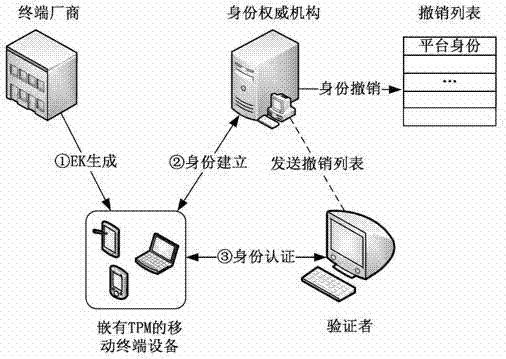
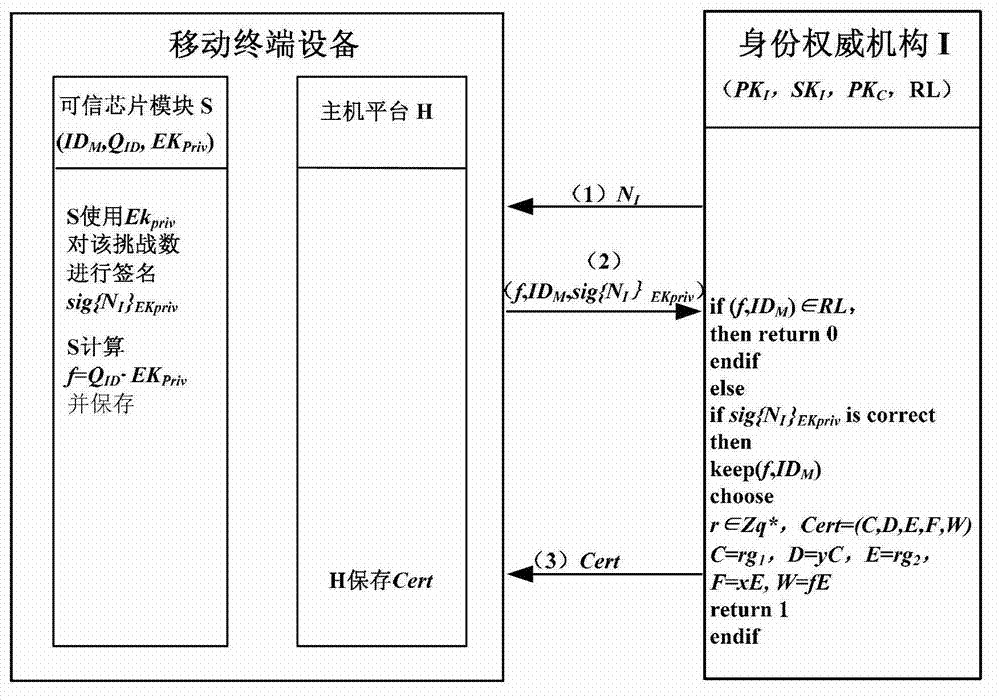
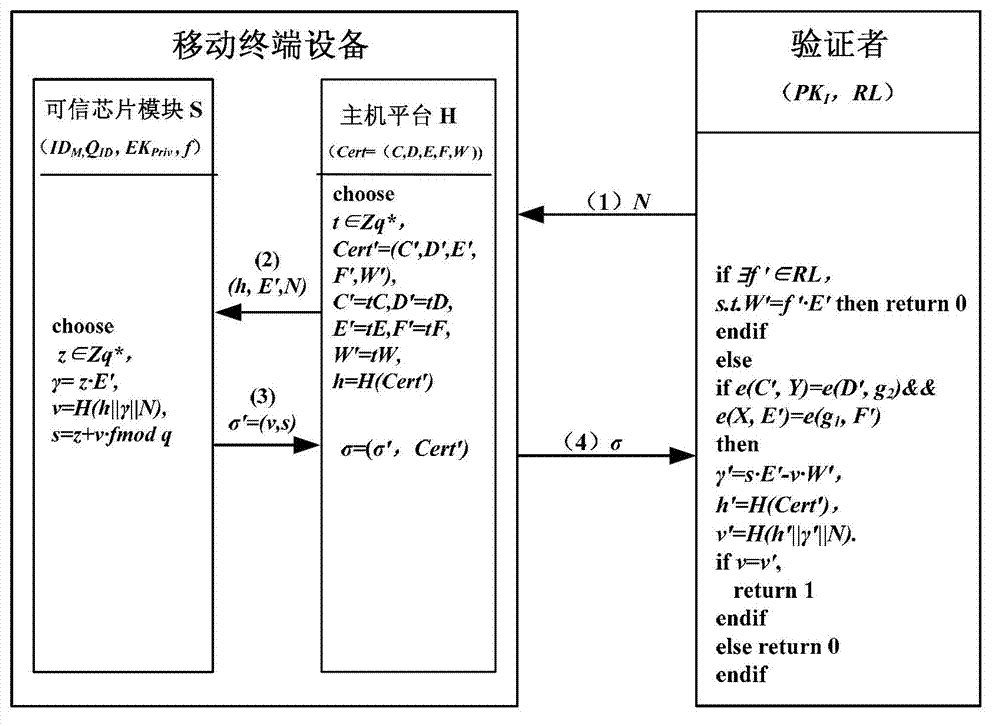
[0036] The present invention mainly includes four entities: 1) Terminal manufacturer (Company, C); 2) Identity authority (Identity authority, I); 3) Trusted terminal equipment (S, H); 4) Verifier (Verifier, V ). Described technical method will be described in detail below in conjunction with accompanying drawing, figure 1 is a system architecture diagram; figure 2 Build a process map for identity; image 3 Diagram for the authentication process.
[0037] The main symbols and algorithm explanations are shown in Table 2.
[0038] Table 2 Main symbols
[0039]
[0040] Our approach can be divided into three phases: system initialization, identity establishment process, and identity verification process. Mathematical calculation in the method can call the function in the PBC storehouse to complete calculation, and wherein hash function can select the hash function in the OpenSSL storehouse, as MD5, SHA-1 etc., the detailed execution process of the present invention is as ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com