Blockchain-based anonymous identity authentication method and device
An anonymous authentication and identity authentication technology, applied in the Internet field, can solve the problems of personal identity theft and leakage, and achieve the effect of avoiding leakage and realizing anonymous verification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
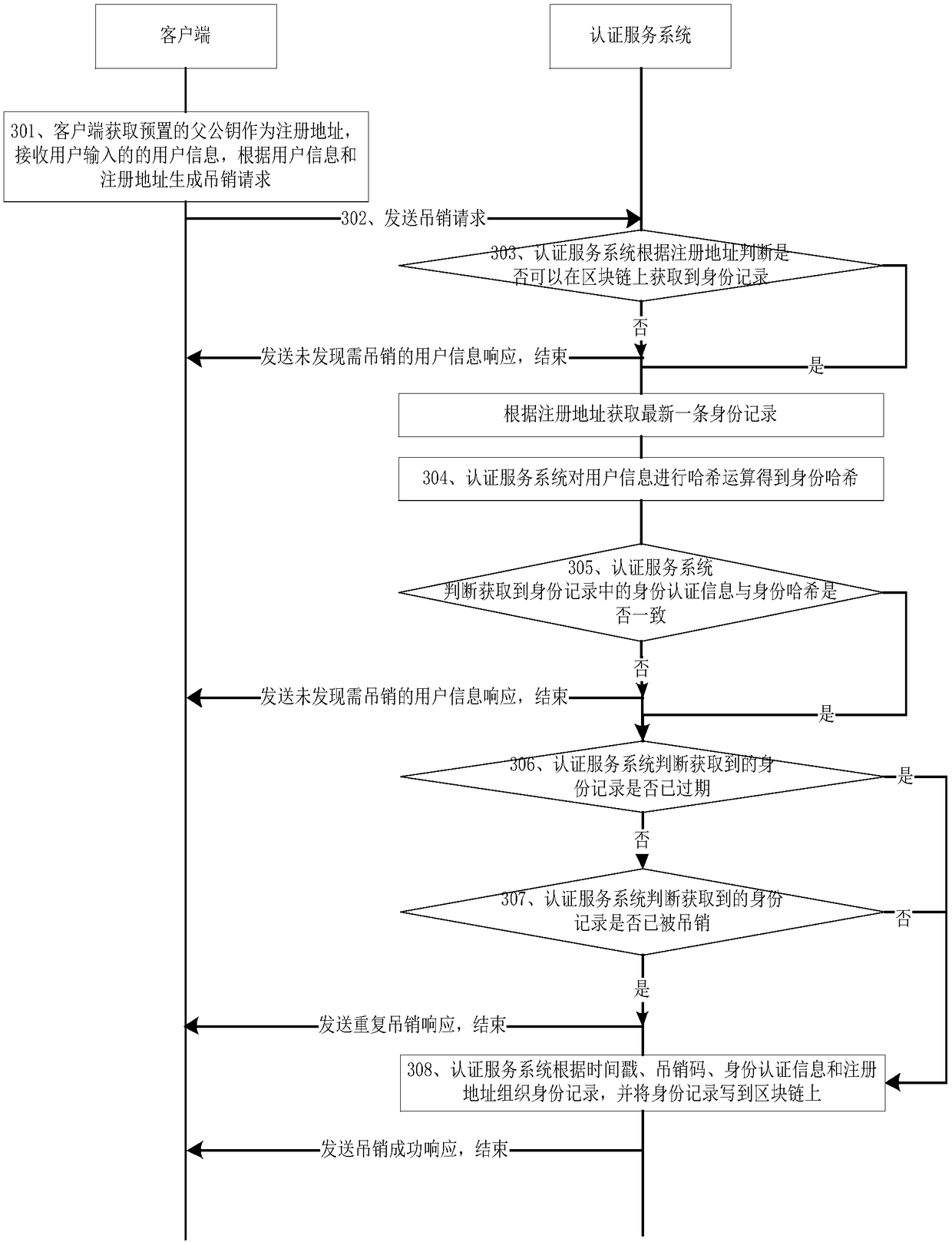
[0036] This embodiment provides a blockchain-based anonymous identity authentication method, specifically including: a user identity registration method, a user identity authentication method, and a user identity revocation method;
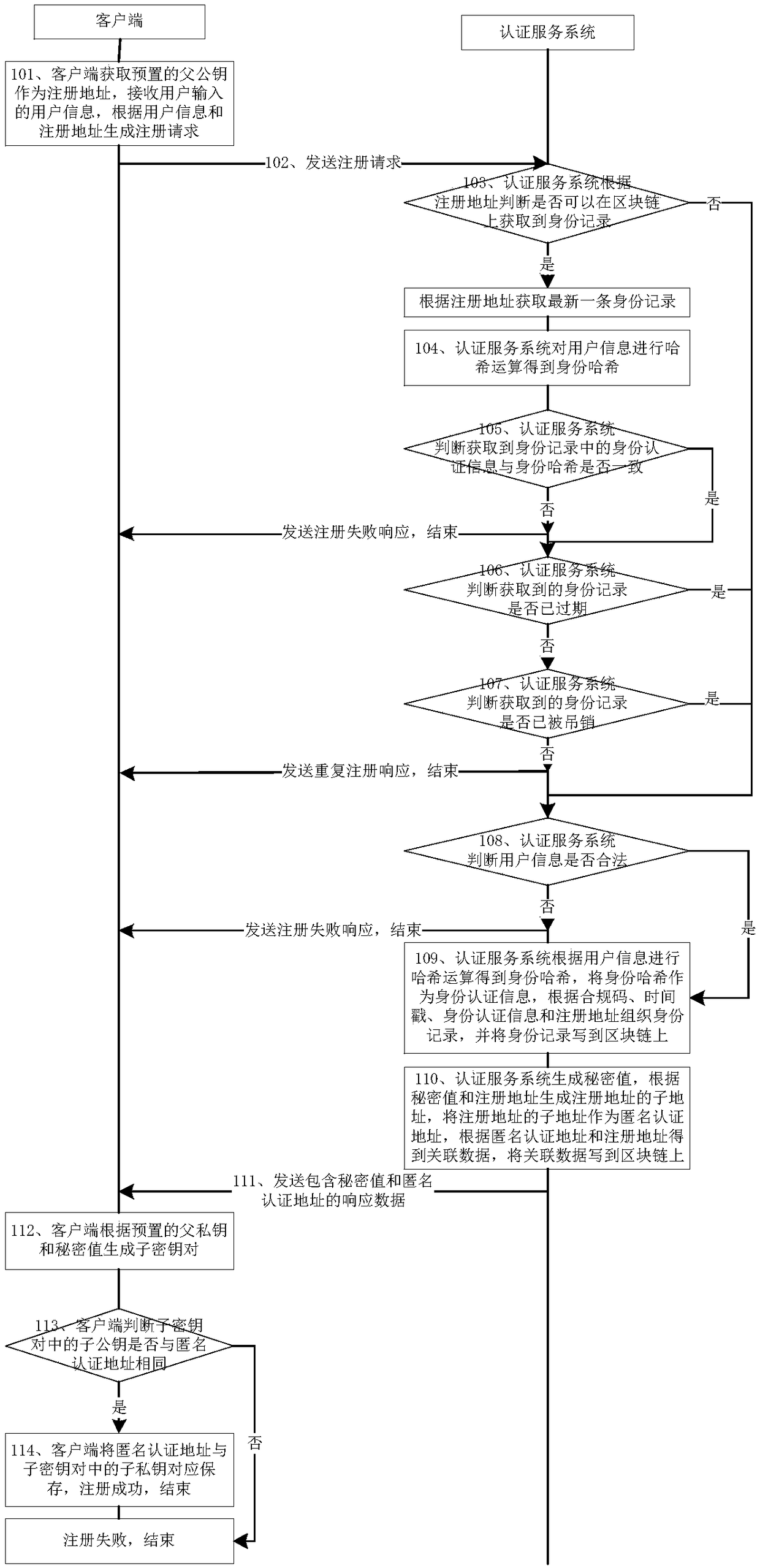
[0037] User identity registration method, such as figure 1 shown, including:
[0038] Step 101, the client obtains the preset parent public key as the registration address, receives the user information input by the user, and generates a registration request according to the user information and the registration address;
[0039] Specifically, the parent key pair is preset in the client, and it should be noted that each parent key pair uniquely corresponds to one user; obtain the parent public key in the parent key pair as the registration address;
[0040] User information includes: user information such as user name, user's date of birth, and user's residential address / business address;
[0041] Step 102, the client sends a registration reques...
Embodiment 2
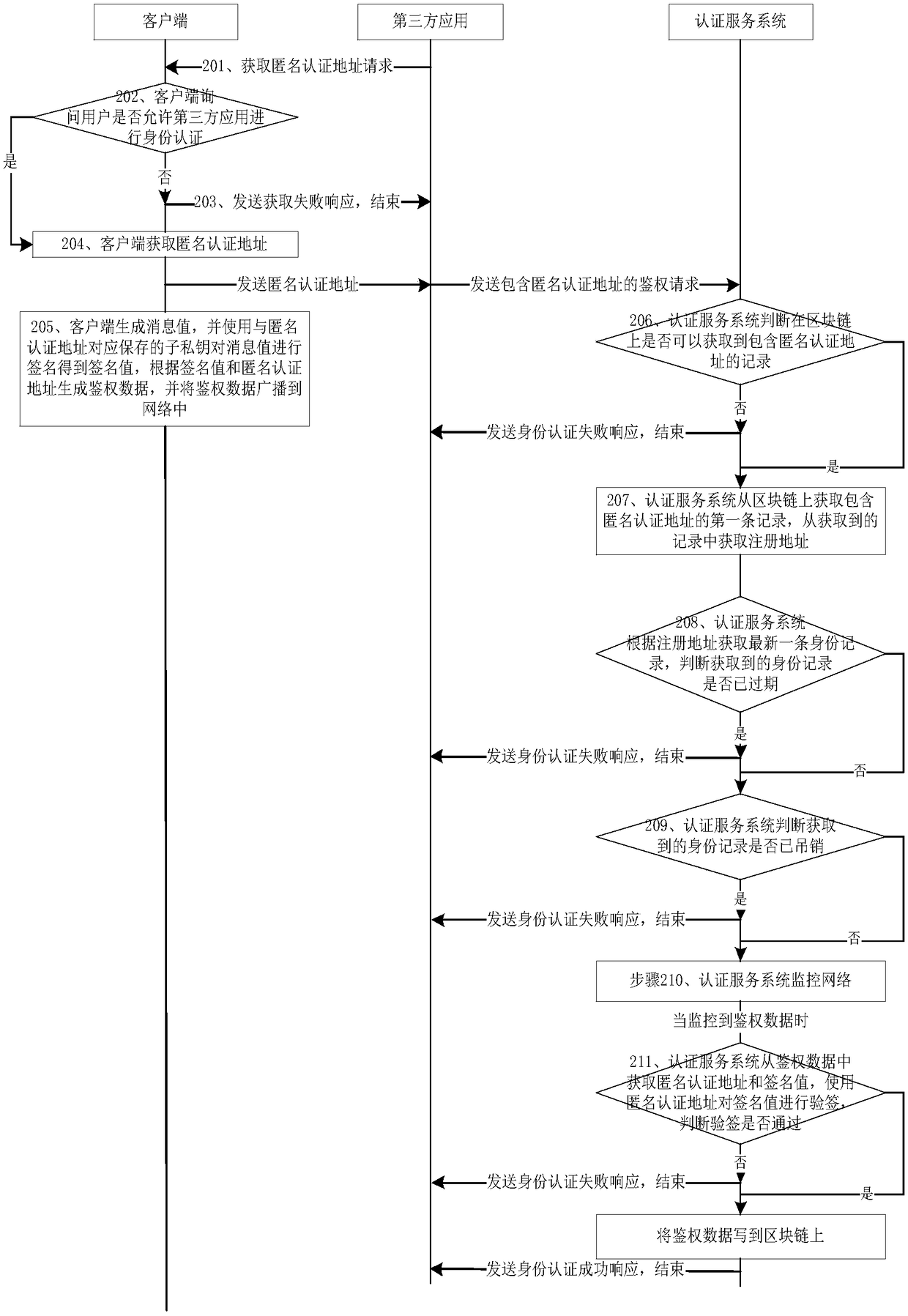
[0113] This embodiment provides a device for anonymous identity authentication based on blockchain, such as Figure 4 As shown, including: third-party application 1, client 2 and authentication service system 3;
[0114] Third-party apps1 include:
[0115] The first receiving module 11 is used to receive the login request initiated by the user through the client 2; it is also used to receive the anonymous authentication address sent by the client 2; it is also used to receive the identity authentication success response sent by the authentication service system 3; it is also used for Receiving an authentication failure response sent by the authentication service system 3;
[0116] The first sending module 12 is used to send to the client 2 a request for obtaining an anonymous authentication address after the first receiving module 11 receives the login request; it is also used to send the anonymous authentication address sent by the client 2 when the first receiving module 11...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com