Anonymous Traitor Tracking Method Based on Compressive Sensing
A compressed sensing and rebel technology, applied in the field of information security, can solve the problems of not considering ciphertext authentication, not considering user anonymous authentication, security issues, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0128] The present invention will be described in further detail below in conjunction with the accompanying drawings.
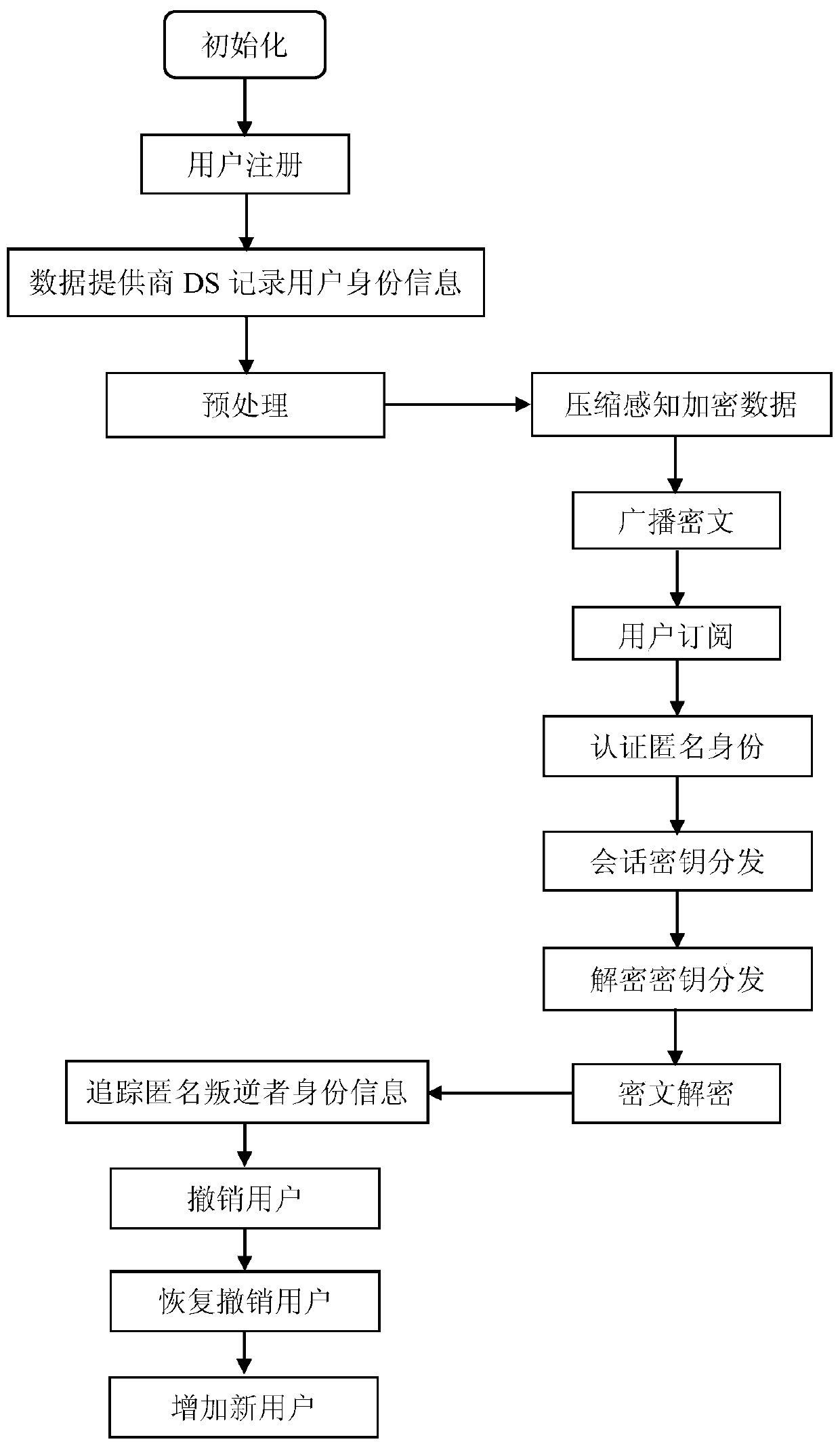
[0129] refer to figure 1 , to further describe in detail the specific steps for realizing the present invention.
[0130] Step 1, initialization.
[0131] The data provider DS randomly selects two large prime numbers p, q, satisfying q|(p-1), q>N, where | represents the modulo operation, N represents the total number of users to be registered at the data provider DS, p Indicates public parameters.
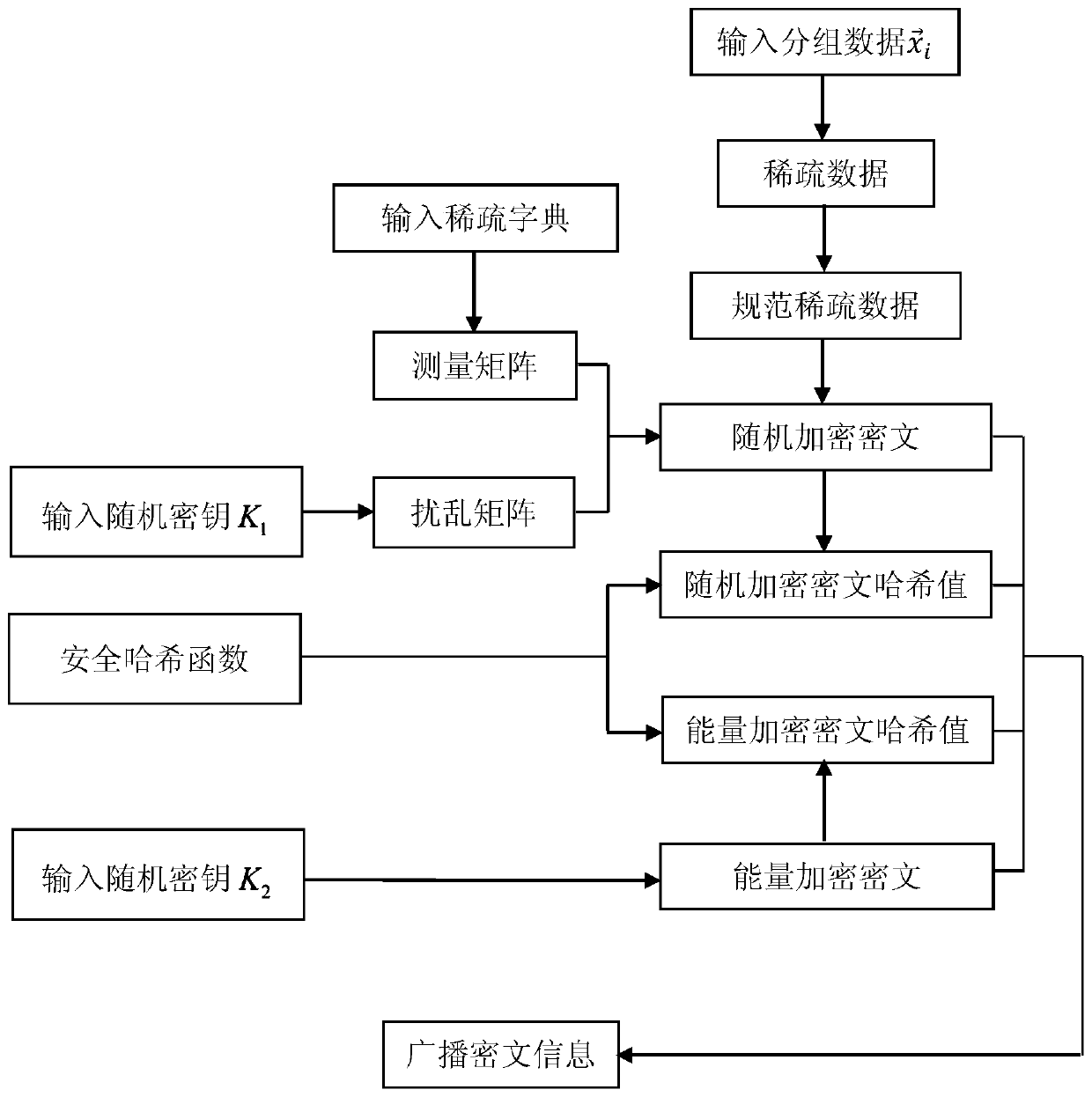
[0132] The data provider DS selects a safe hash function and a pseudo-random normal distribution matrix generator, and broadcasts the selected safe hash function and pseudo-random normal distribution matrix generator to user groups.
[0133] Using the pending registration share calculation formula, the data provider DS calculates each pending registration share value.
[0134] The formula for calculating the share to be registered is as follows:
[0135] f(i)...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com