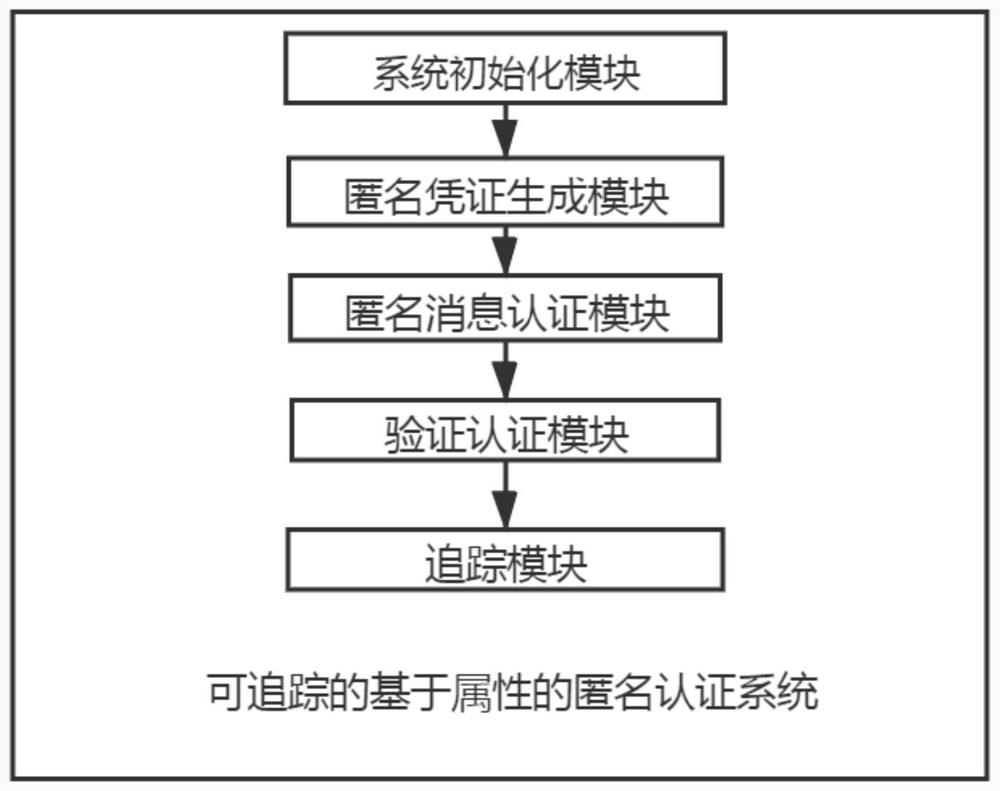
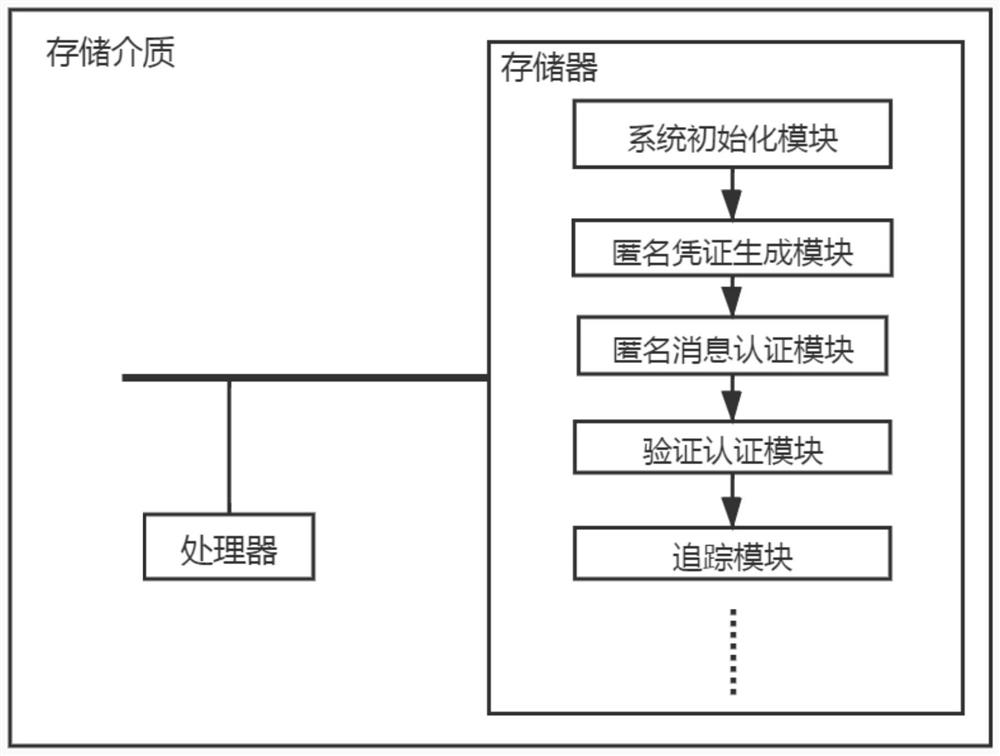
Traceable attribute-based anonymous authentication method and system and storage medium
An anonymous authentication and traceable technology, applied in transmission systems, digital transmission systems, user identity/authority verification, etc., can solve problems such as registration information interception and privacy leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
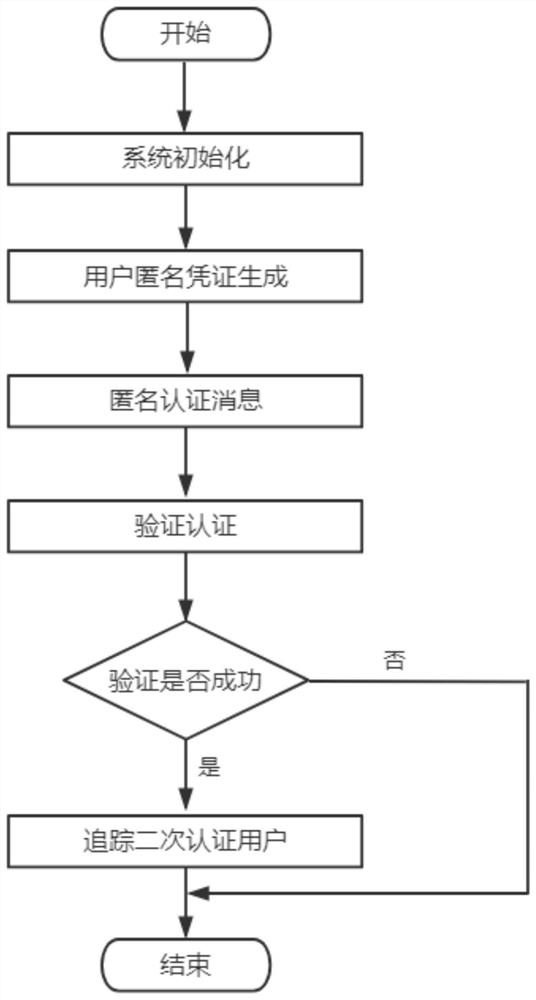
[0063] Such as figure 1 As shown, in the present invention, a traceable attribute-based anonymous authentication method comprises the following steps:
[0064] S1, system initialization, generate the master public key and the master private key by setting the algorithm, in this embodiment, specifically:
[0065] S11, system initialization, specifically:
[0066] Let Cre = (Cre.Setup, Cre.Gen, Cre.Verify) be an anonymous credential scheme with attributes;
[0067] Cre.Setup is the setup algorithm of the Cre scheme, specifically Cre.Setup(λ)→(pk,msk), input the security parameter λ, output the public parameter pk and the master private key msk, which are used to initialize the anonymous credential scheme;
[0068] Cre.Gen is the certificate generation algorithm of the Cre scheme, which is used to generate the user's anonymous credentials. Specifically, the common input of the user and the certificate authority is the public parameter pk and the commitment C i =Commit(L i ,r ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com