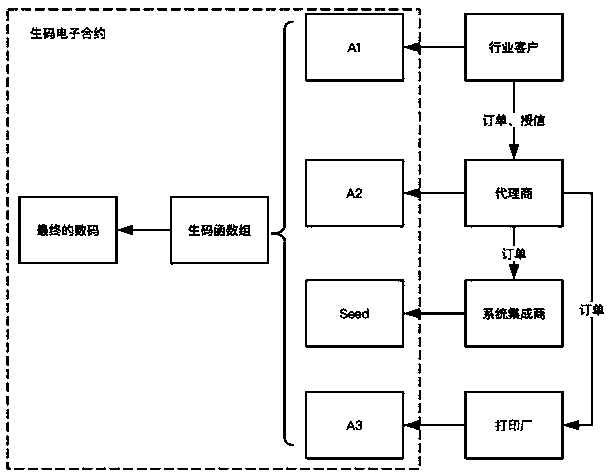
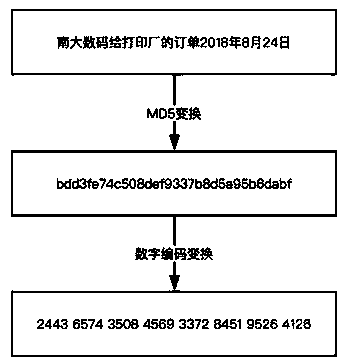
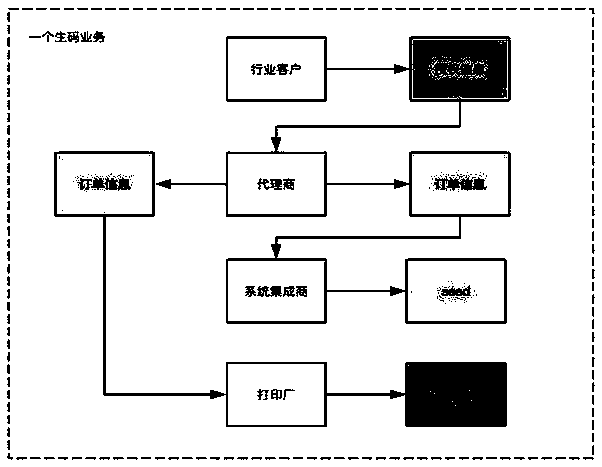
Patents
Literature
44results about How to "Solve the problem of counterfeiting" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
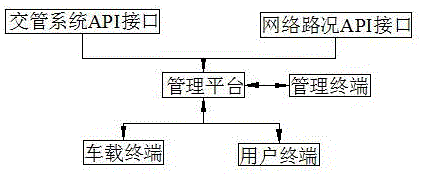
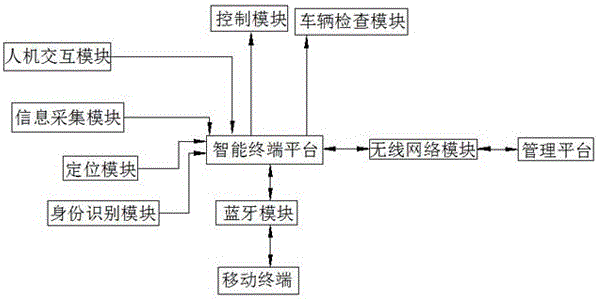
Unattended electric car rental system and rental method
ActiveCN104992364AEasy to useProtect the rights and interests of usersBuying/selling/leasing transactionsData transmissionAutomatic deduction
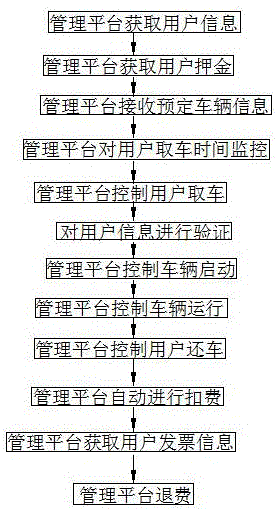
Provided are an unattended electric car rental system and a rental method. The system comprises a vehicle-mounted terminal, a user terminal and a management platform; and the vehicle-mounted terminal and the user terminal both perform data transmission with the management platform, and a wireless connection is formed between the vehicle-mounted terminal and the user terminal. The method comprises steps of: the management platform obtaining user information, obtaining user deposit, receiving information of a reserved vehicle, monitoring a time when a user picks up the vehicle, controlling the user to pick up the vehicle, verifying the user information, controlling starting up and running of the vehicle, controlling the user to return the vehicle, the management platform performing automatic deductions, and introducing a whole process of implementation of vehicle renting. The system provided by the invention is novel in design, and is convenient for the user to use; a rental process does not need the participation of staff members, thereby implementing unmanned renting. The method provided by the invention provides more convenience for the user in a renting process, and real-time feedback of information enables the user to timely obtain related information, thereby ensuring rights and interests of rental enterprises and users.
Owner:联世海富威海智慧科技有限公司
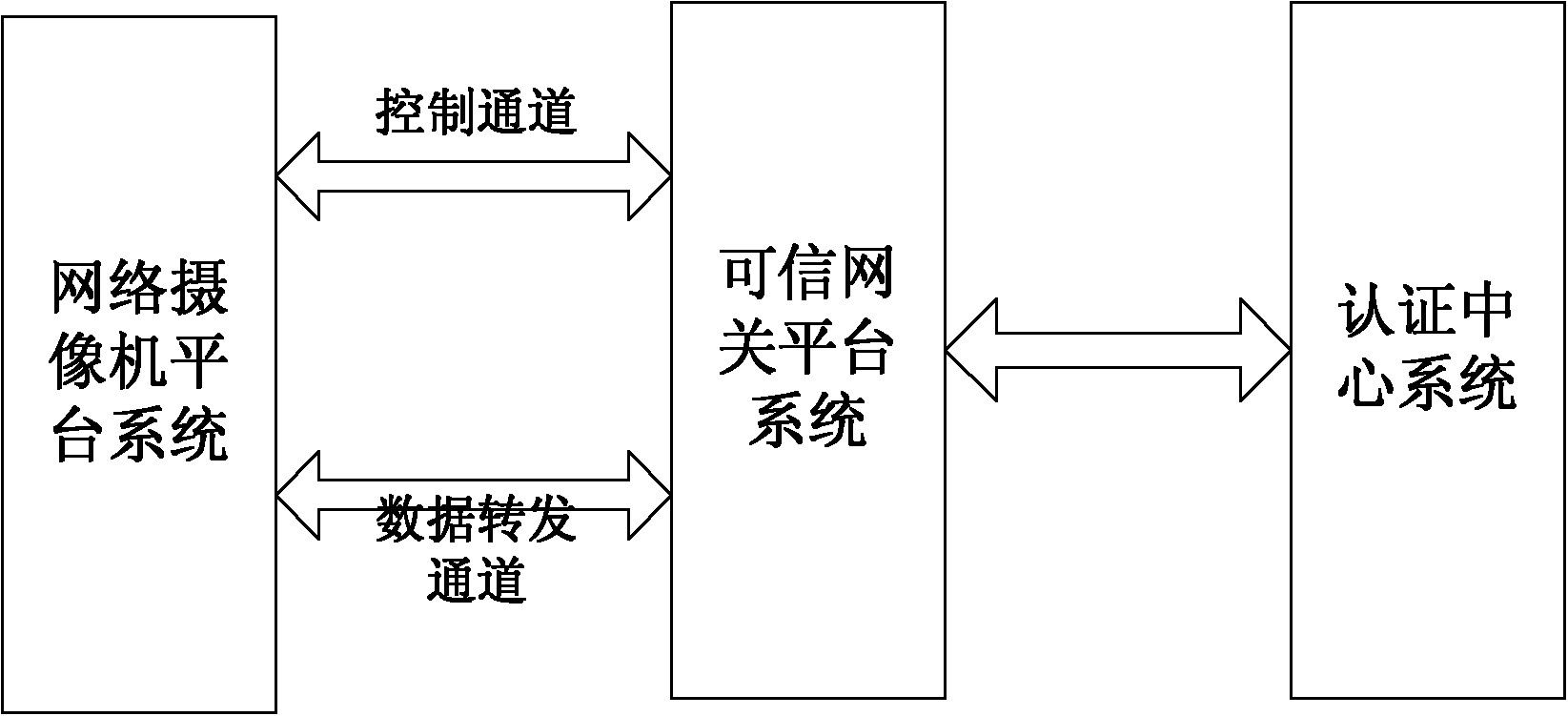
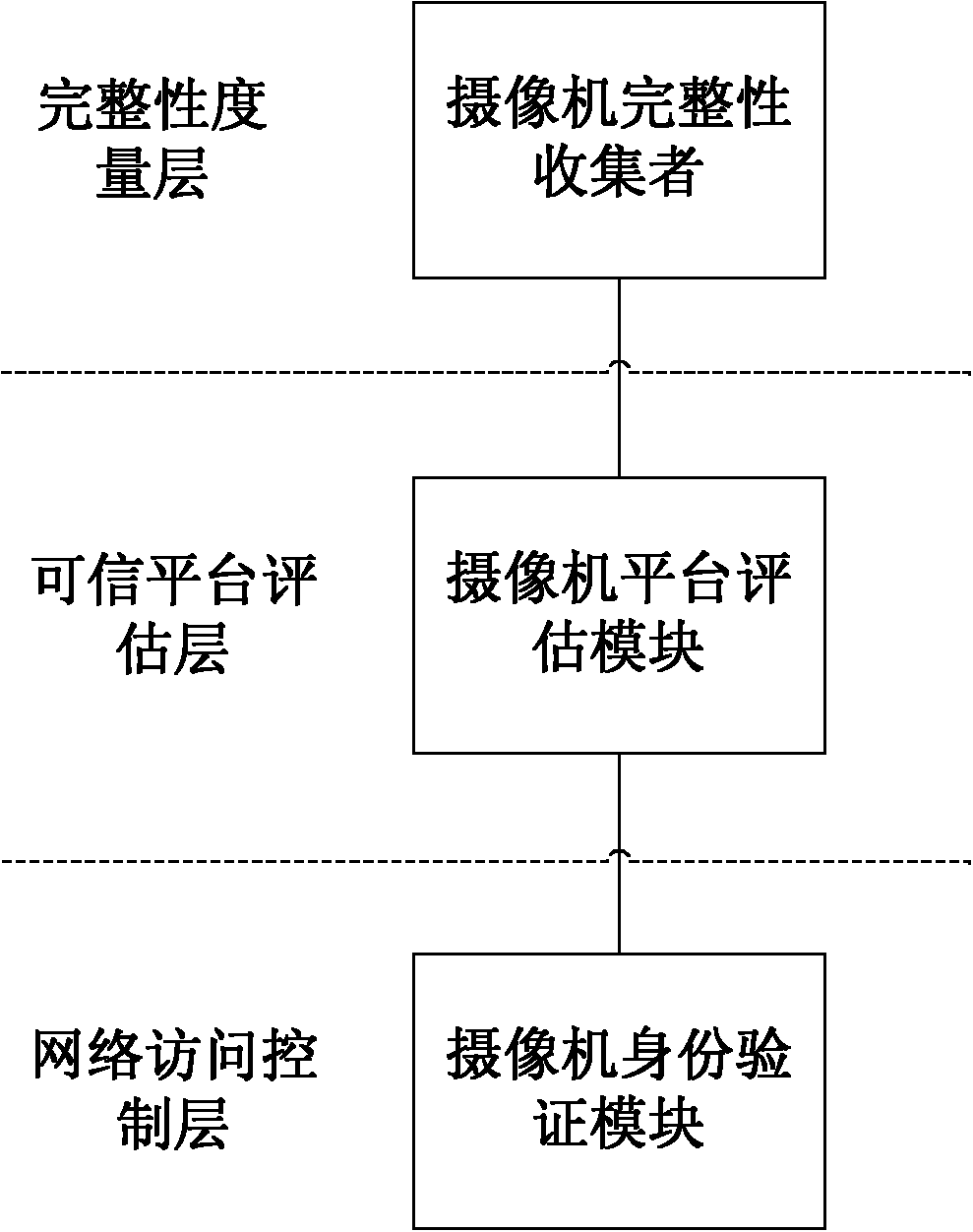
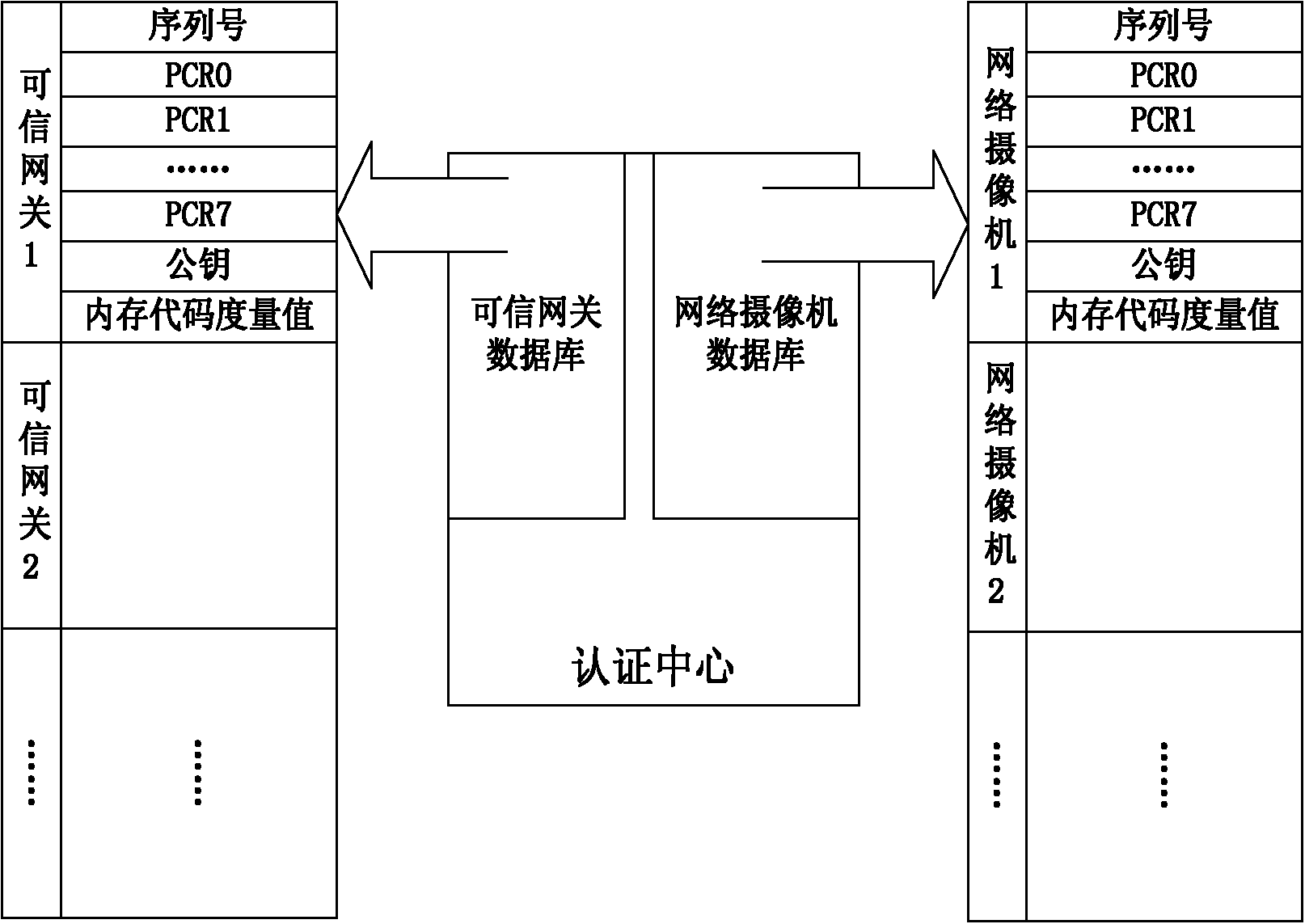
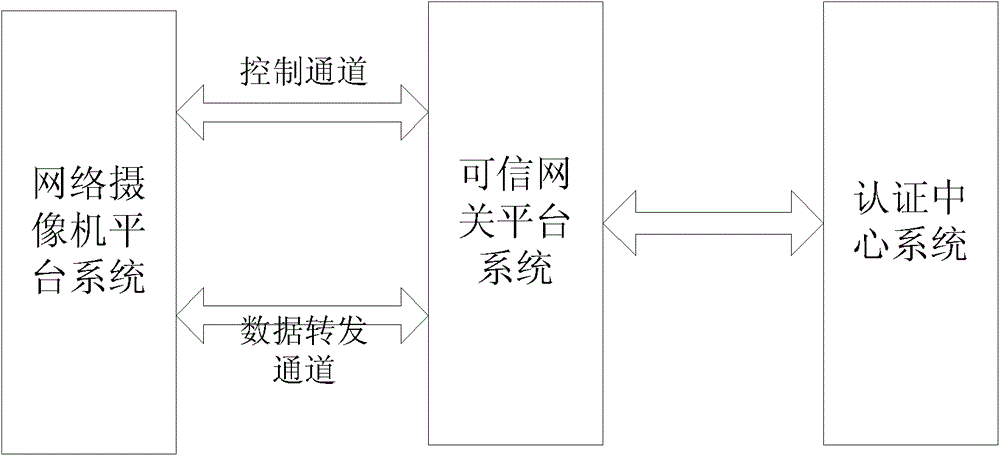
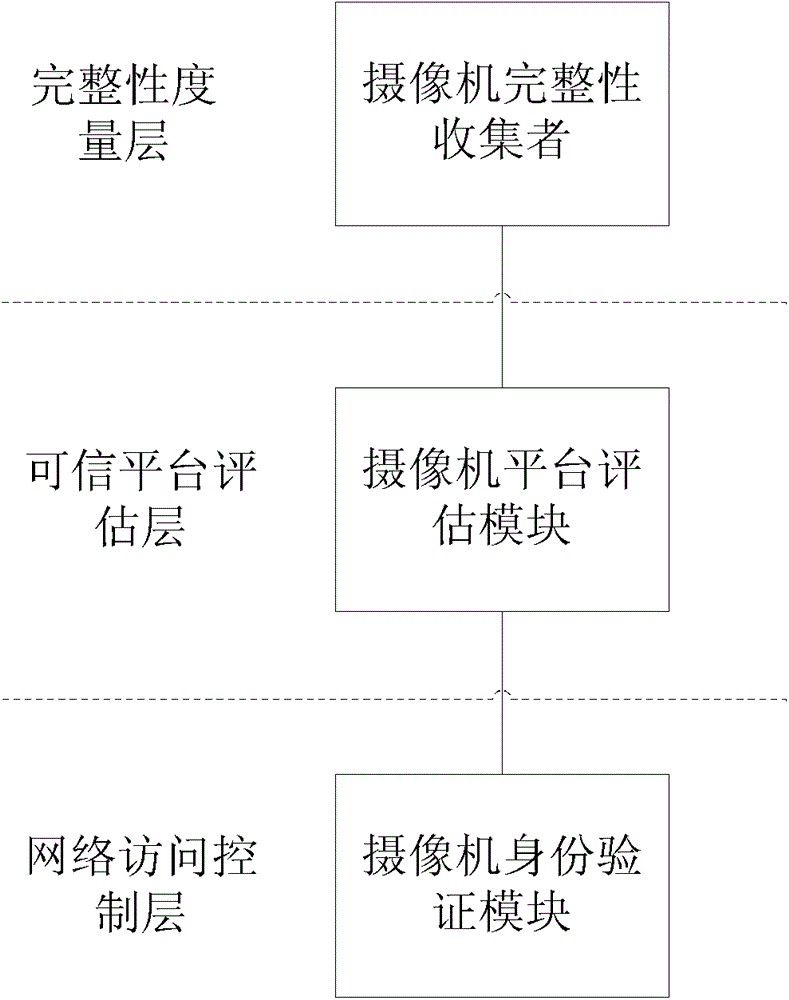
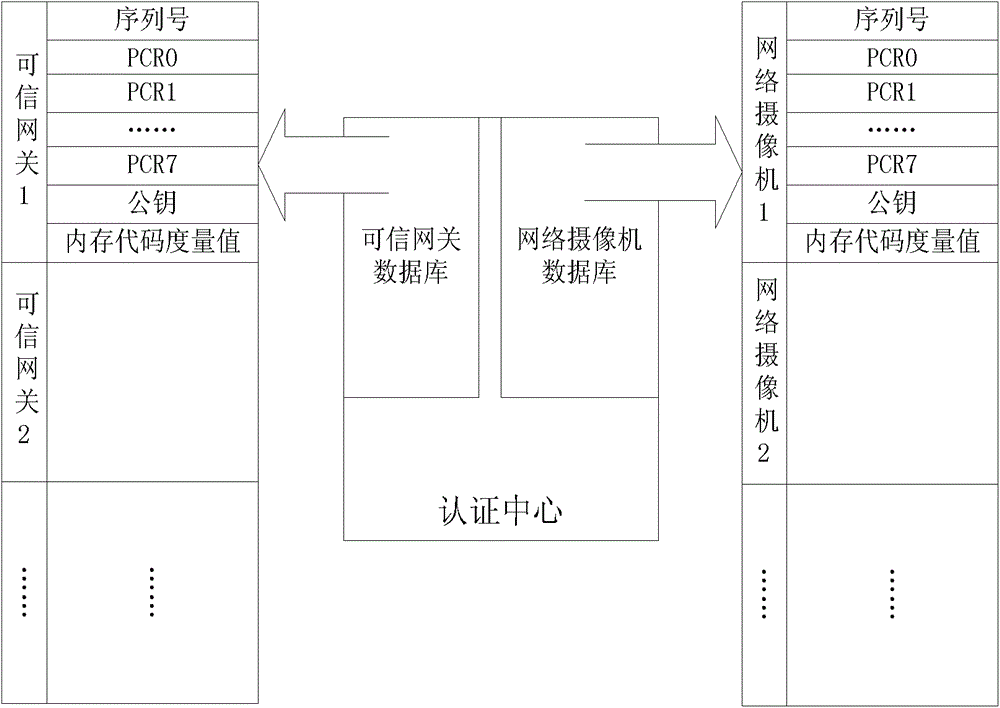
Network camera identity authentication method based on TPCM
ActiveCN103888257AImplement identity authenticationReduced authenticationUser identity/authority verificationClosed circuit television systemsProcessor registerMemory code
The invention provides a network camera identity authentication method based on a TPCM. The method is characterized in that a network camera and a reliable gateway adopt a self-signing mode to generate a digital certificate which comprises a value of a platform configuration register and a measurement result of a memory code segment in operation. An authentication center verifies validity of the digital certificate and confirms identity of the verified party. Advantages are that a measurement value in the starting process of equipment is stored in the platform configuration register so that hardware of the network camera and the reliable gateway is ensured to be unchanged. Reliability of equipment identity is ensured from the aspect of software via measurement of the memory code segment. Besides, a signature secret key is generated by a TPCM chip and bound with the hardware platform state of the equipment so that the digital certificate is difficult to forge.
Owner:BEIJING UNIV OF TECH
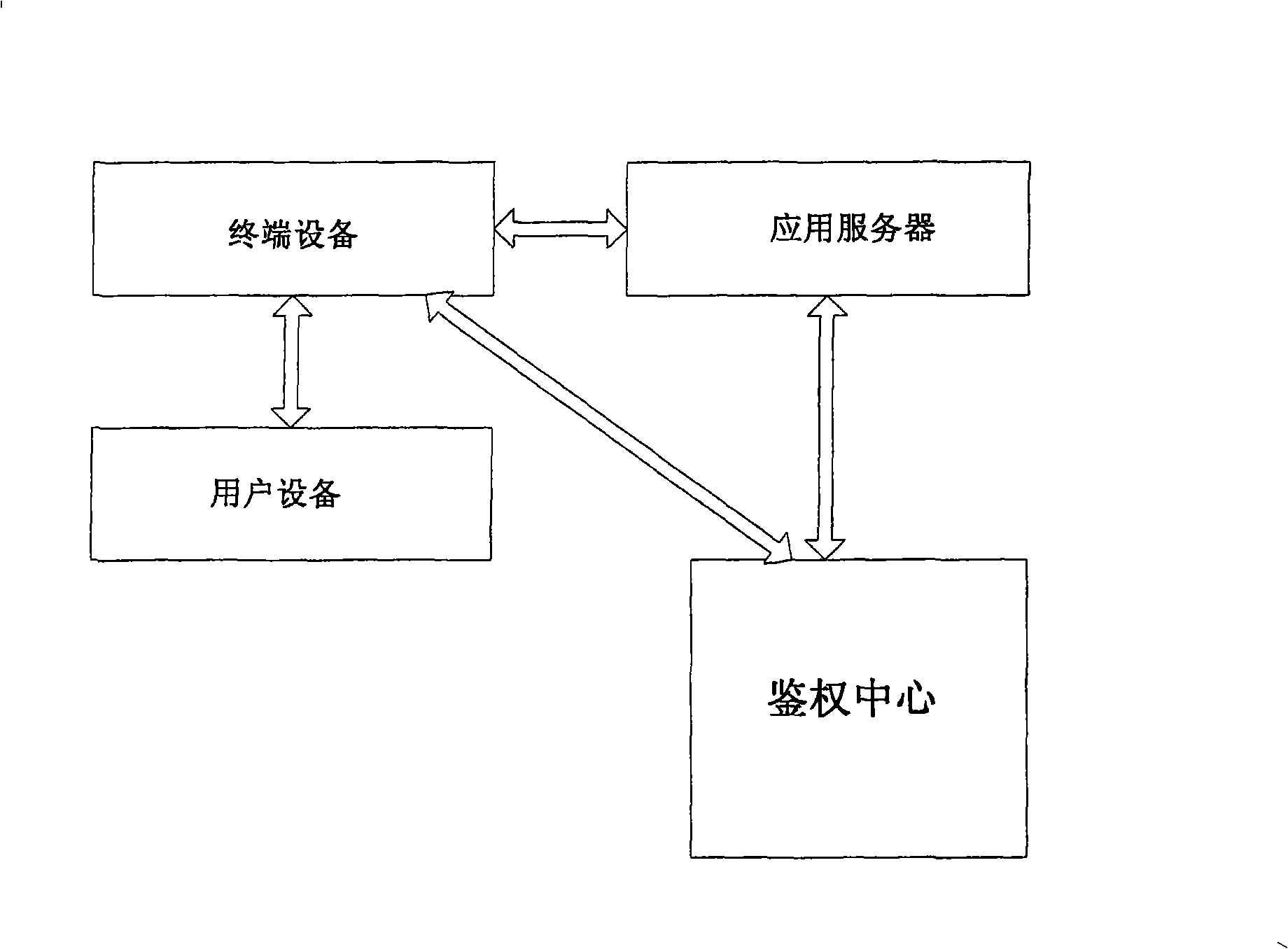
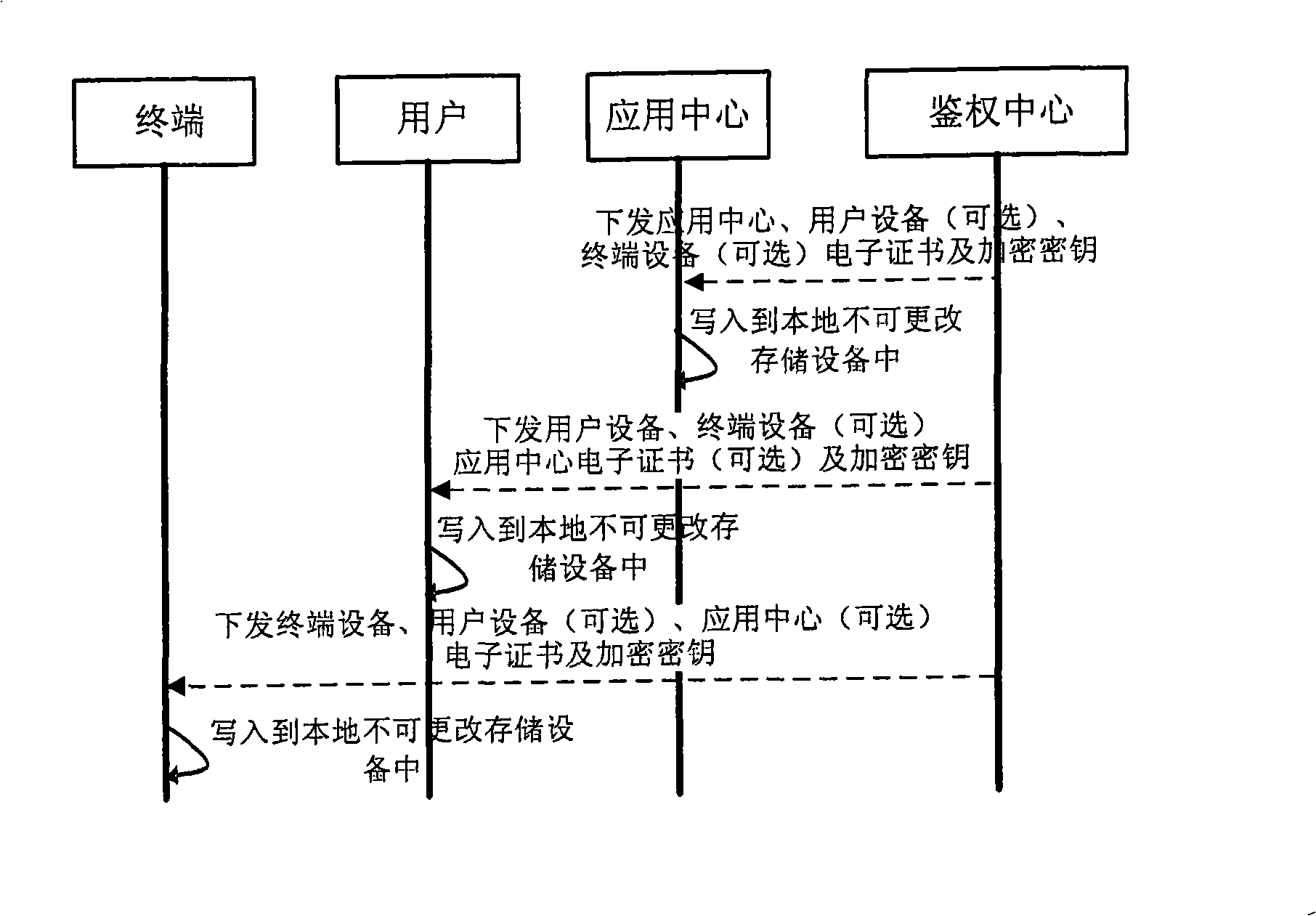
Multipart identification authentication method and system base on equipment
ActiveCN101409621ASolve the problem of counterfeitingUser identity/authority verificationAuthentication serverInternet privacy
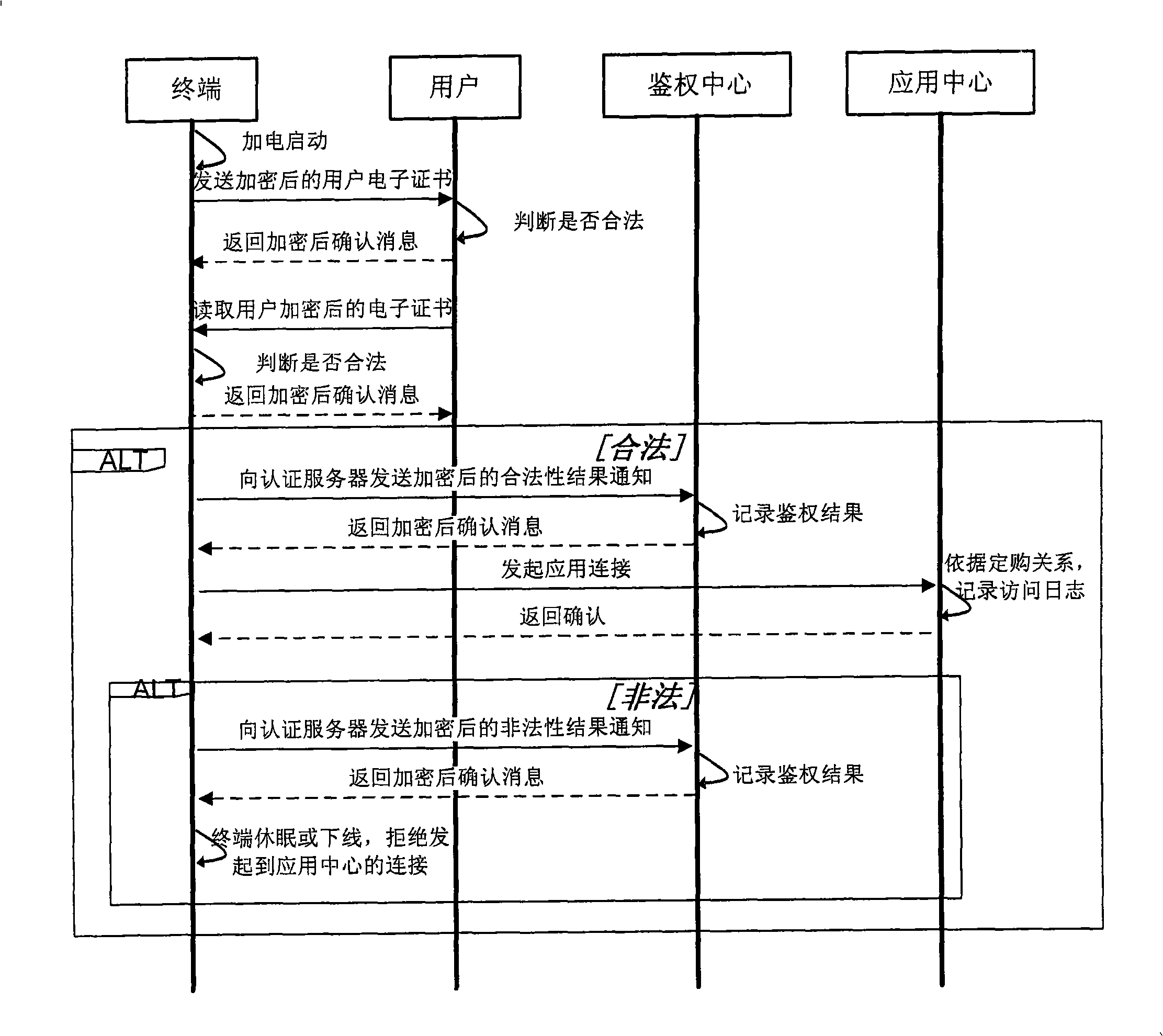
The invention provides a method for authenticating multi-party identification and a system thereof. The system comprises an authentication server and at least two authentication devices, wherein, the authentication server transmits identification authenticating data containing digital certificates of all authentication devices participating authentication to two authentication devices at least; the authentication devices store the received identification authentication data. The authentication device comprises an authentication initiating party device and an authentication treating party device, wherein, the authentication initiating party device transmits information of an authentication request containing a digital certificate of the authentication initiating party device to the authentication treating party device; and the authentication treating party device carries out consistency comparison between the digital certificate of the authentication initiating party device stored in the device self and the received digital certificate in the information of the authentication request, if yes, identification legal message is transmitted to the authentication server; if not, identification illegal message is transmitted to the authentication server. The method solves the problem of identification authentication among a server, a terminal and a user.
Owner:CHINA MOBILE GRP BEIJING
Anti-counterfeiting off-site commodity transaction method and system
InactiveCN103489121AReduce the possibility of counterfeitingProduction real-time monitoringBuying/selling/leasing transactionsPersonalizationTransport system
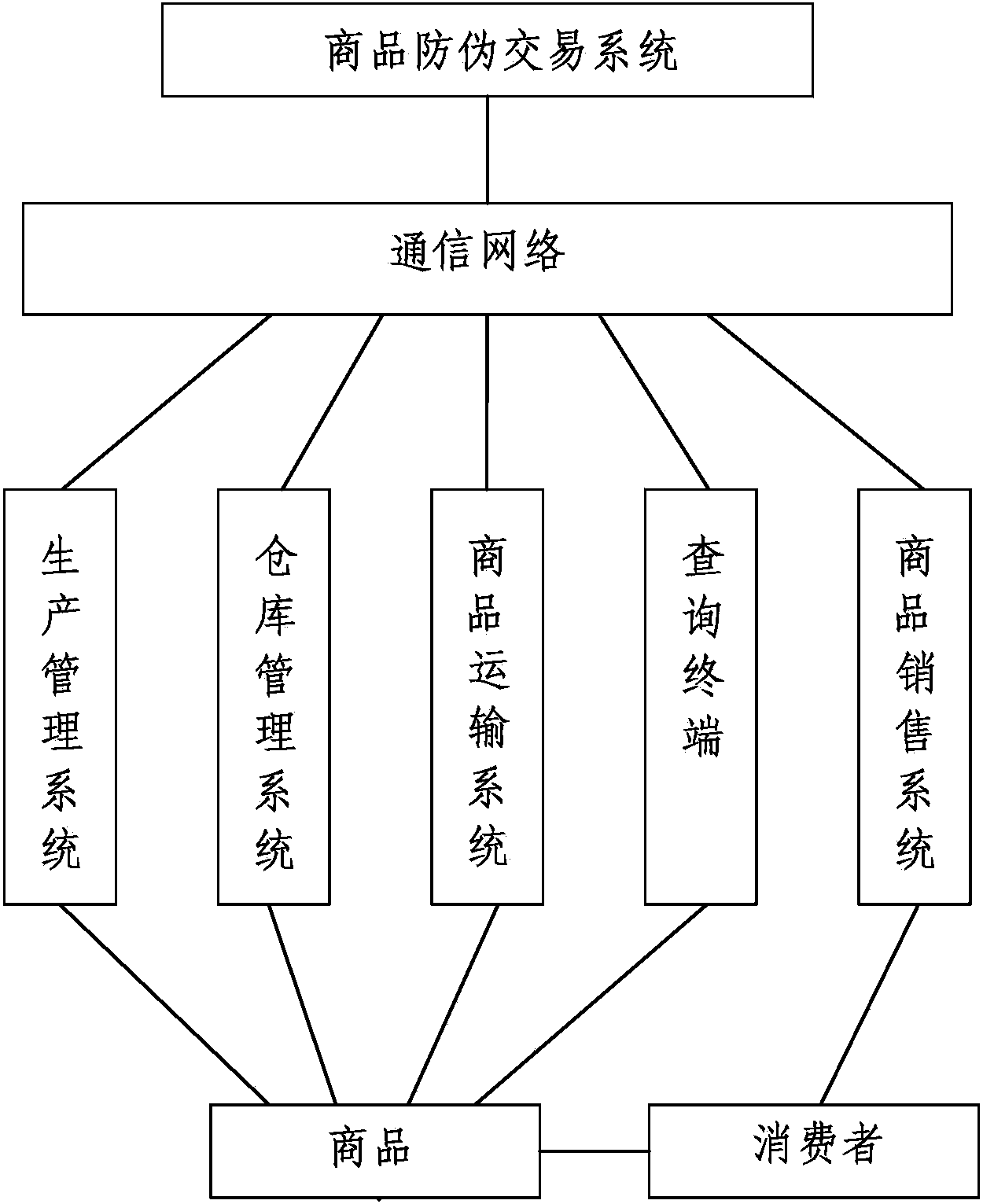
The invention discloses an anti-counterfeiting off-site commodity transaction method and system. According to the anti-counterfeiting off-site commodity transaction method and system, an anti-counterfeiting commodity transaction network formed by an anti-counterfeiting commodity transaction system, a production management system, a commodity sales system, a storehouse management system and a commodity transporting system is established, a string of user-defined anti-counterfeiting information set by a consumer runs through the whole commodity circulation process, only the final consumer can identify the authenticity of a commodity by verifying the anti-counterfeiting information, and the probability of counterfeiting of the commodity is reduced; a barcode, personalized information and a logistics barcode are bound with an order, real-time monitoring of production, storage and circulation of the commodity is achieved, planning management and dispatching are achieved, working efficiency is improved, and meanwhile tracking of the commodity is achieved. According to the anti-counterfeiting off-site commodity transaction method and system, counterfeiting and adulteration of the commodity in the tail stage of circulation are eliminated for the final consumer. The anti-counterfeiting off-site commodity transaction method and system are suitable for but not limited to off-site shopping such as online shopping and teleshopping.
Owner:JINAN SHANHE ENVIRONMENT SCI & TECH CO LTD
An electronic certificate uploading method and device
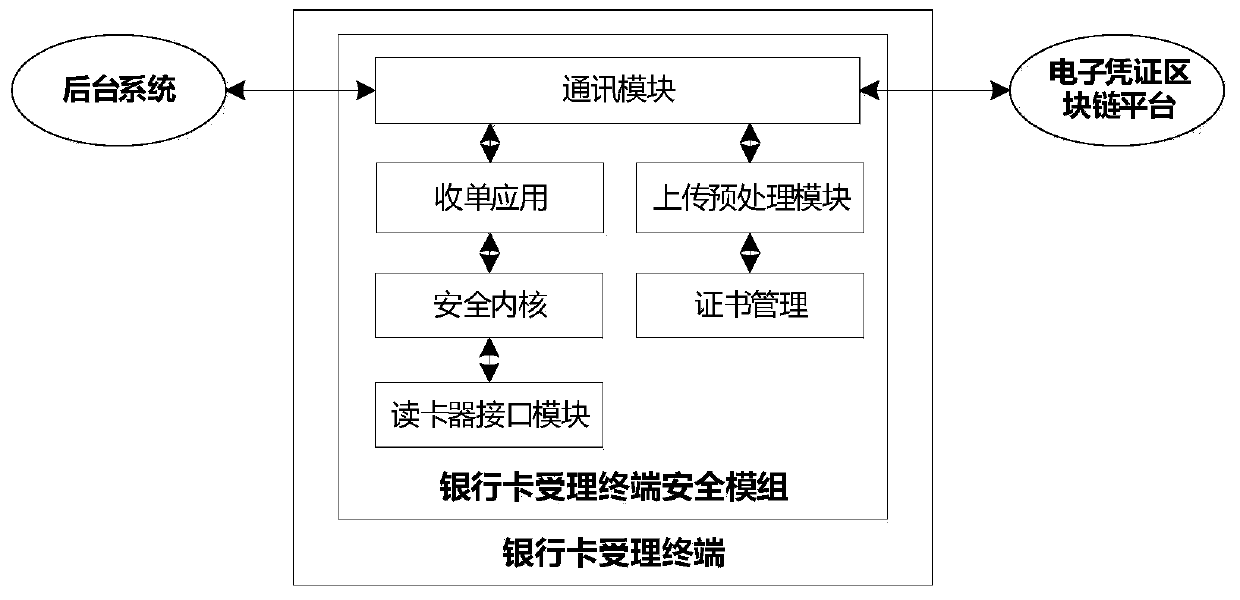
ActiveCN109741056ASolve the problem of counterfeitingSolve the problem of tamperingFinancePayment protocolsComputer terminalChain network
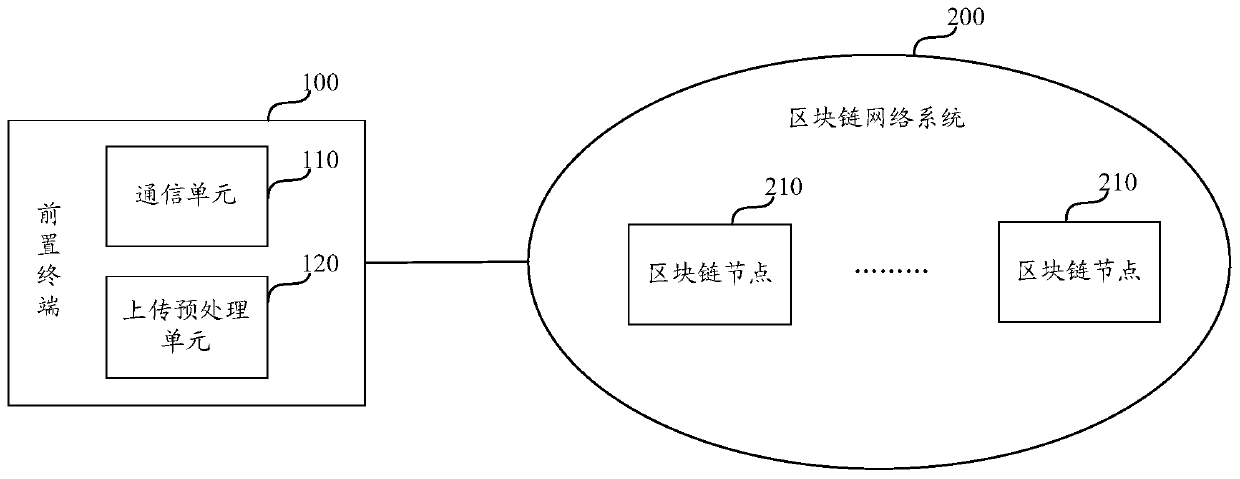
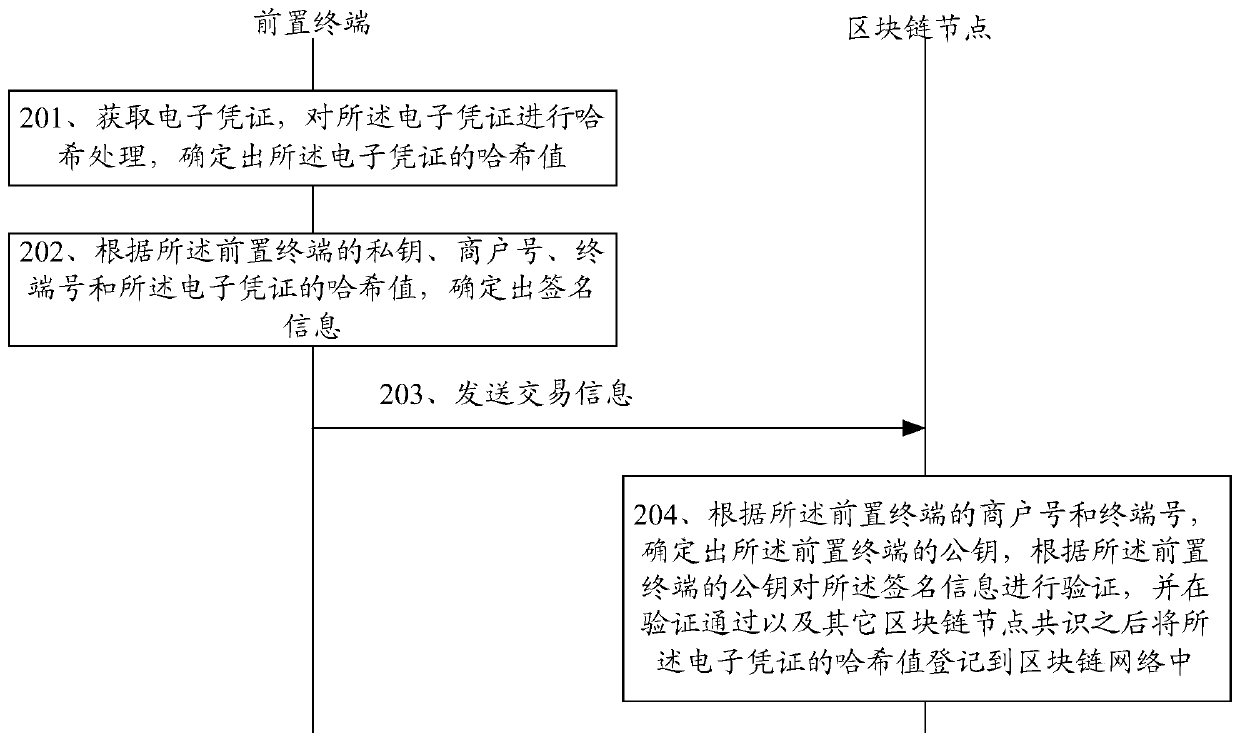
The invention discloses a method and a device for uploading an electronic certificate. The method comprises the steps that a front-end terminal obtains an electronic certificate, carrying out Hash processing on the electronic certificate; determining a hash value of the electronic certificate; and according to the private key of the front-end terminal, the merchant number, the terminal number andthe hash value of the electronic certificate, determining signature information, and uploading the merchant number and the terminal number of the front-end terminal, the hash value of the electronic certificate and the signature information to the blockchain node, so that the blockchain node verifies the signature information and then registers the signature information in the blockchain network.The front-end terminal directly uploads the electronic certificate to the block chain network after processing the electronic certificate, so that the problem that in the prior art, when the front-endterminal uploads the electronic certificate to the block chain through the background terminal, the electronic certificate is tampered is solved.
Owner:CHINA UNIONPAY
Anti-counterfeiting authentication and recording tracing system and method for paper-medium-based artworks
PendingCN106447361ARealize anti-counterfeiting filingPromote healthy developmentCharacter and pattern recognitionCommerceDatabaseImage acquisition
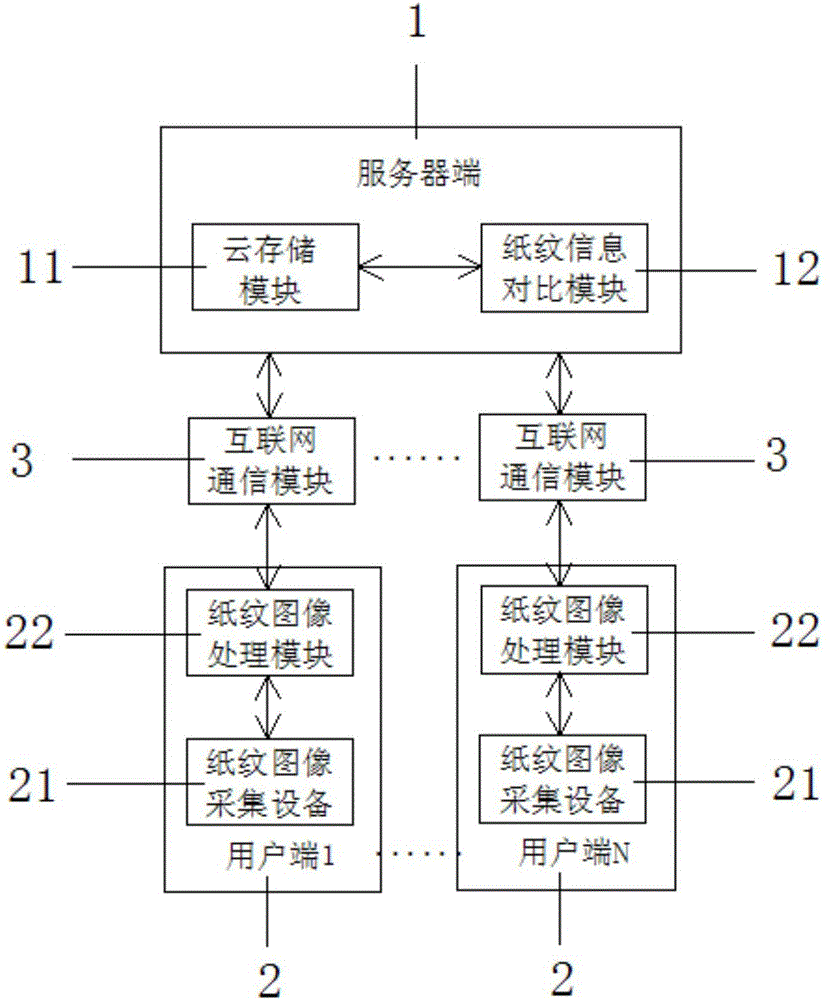
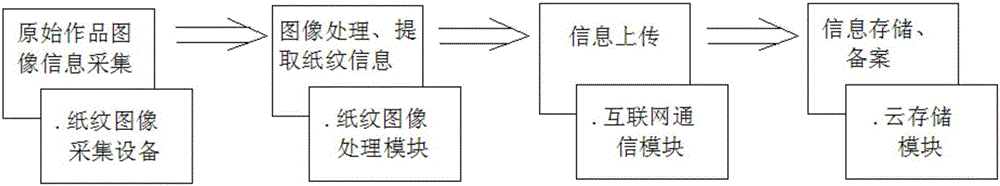
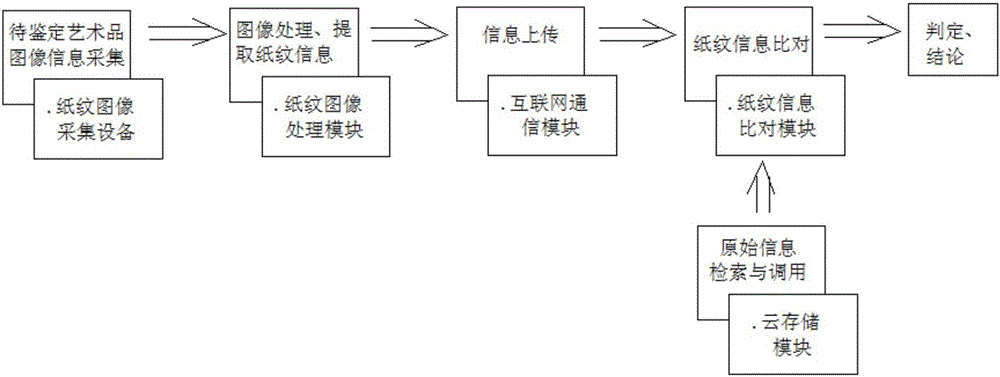
The invention, which relates to the field of authentication of authentic artworks, provides an anti-counterfeiting authentication and recording tracing system and method for paper-medium-based artworks. The method comprises: a paper print image acquisition device is used for carrying out processing on a paper-medium-based artwork like calligraphy work or a painting to obtain paper print information, and the information is uploaded to a server and is stored for the record; and when authenticity of a to-be-detected artwork needs to be authenticated, paper print information of the to-be-detected artwork paper is collected and is compared with original recorded paper print information stored in the server, and the authenticity of the artwork is determined based on the matching degree of paper print comparison. According to the system and method provided by the invention, on the basis of uniqueness, stability, and non-duplicated performance of the paper print, scientific and objective comparison is realized, thereby avoiding subjectivity of manual experience-based authentication; a problem of counterfeiting of separation of the authenticated object and the artwork according to other authentication methods can be solved; because of recording of the original artworks, records are made in a system database for all transactions, thereby realizing tracing of artworks transaction flow directions; and the system and method are convenient to implement and have the broad market application prospects.
Owner:王友炎
Sensitive data trading system and method based on block chain
ActiveCN109325764APrevent leakageSolve the problem of counterfeitingFinanceDigital data protectionElectronic contractsClient-side
The invention relates to a sensitive data trading system based on a block chain, which comprises a block chain bottom layer module, an electronic contract layer module and a SaaS layer module. The block chain layer module provides technical support for bottom block chain, includes a virtual machine supporting electronic contract running, a consensus algorithm, a transaction verification mechanismand an accounting mechanism; The electronic contract layer module provides distributed application services, endorses by using block chain technology, and runs the code of system sensitive data transaction and the code of digital generation algorithm in electronic contract layer. The SaaS layer module provides cloud platform services, so that the participants through the web platform, client, areconvenient to participate in business cooperation. The invention provides the data trading system based on the block chain, which is used for multiple parties to participate in the joint production ofsensitive data, the final sensitive data is obtained by the final data generator, and other roles do not know the final data in the data production process, so that the leakage of the sensitive datain the circulation process is prevented.
Owner:江苏南大数码科技有限公司
Method and device for identifying users
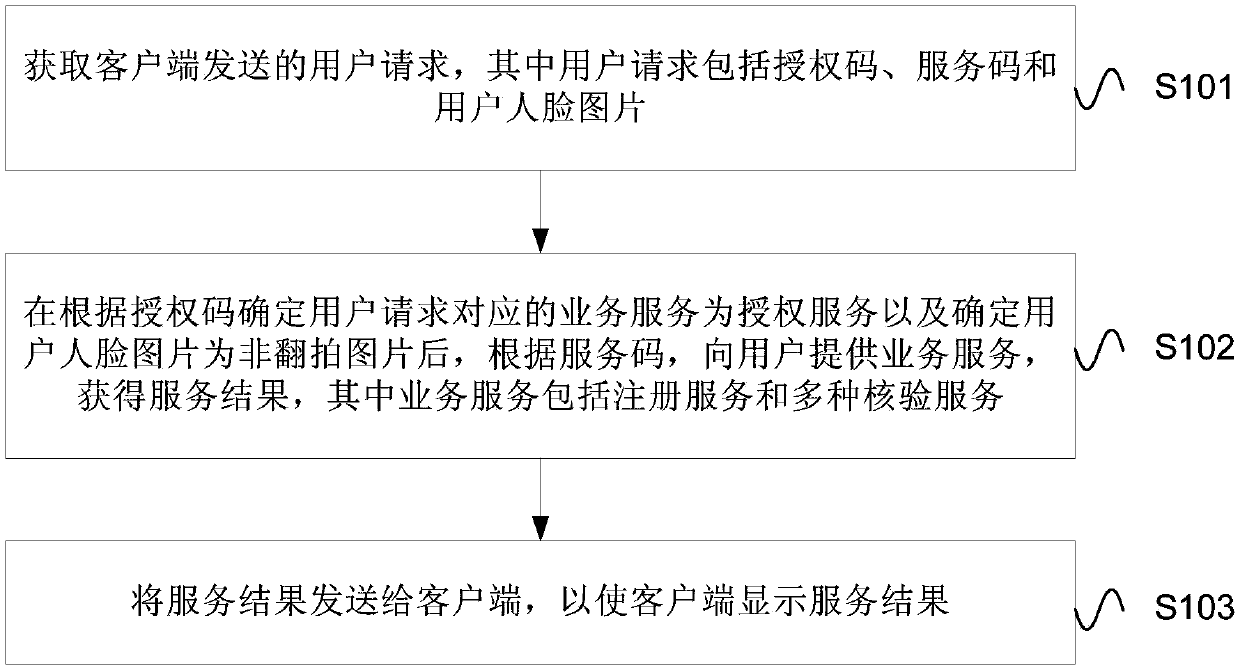
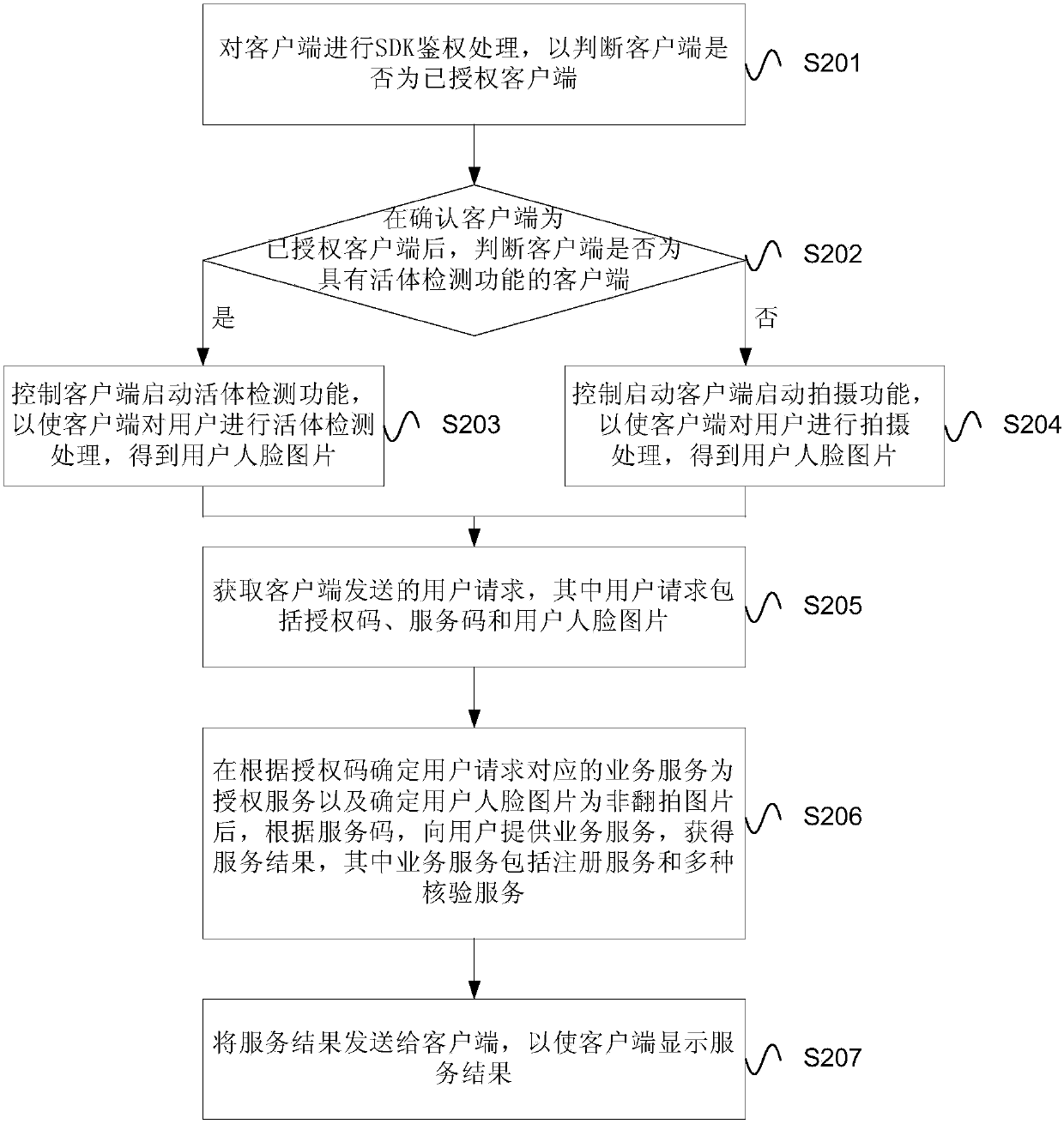
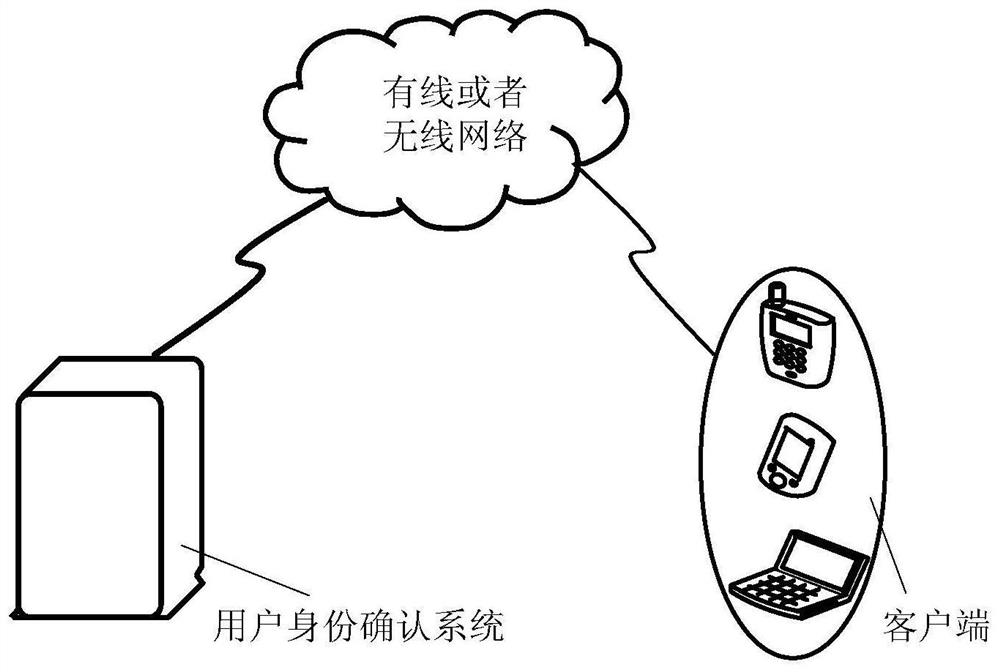
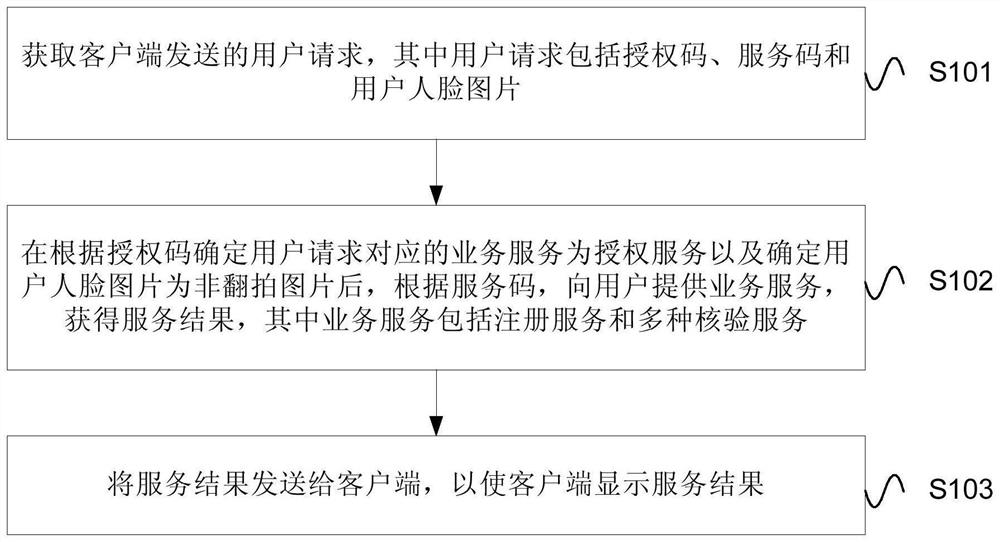
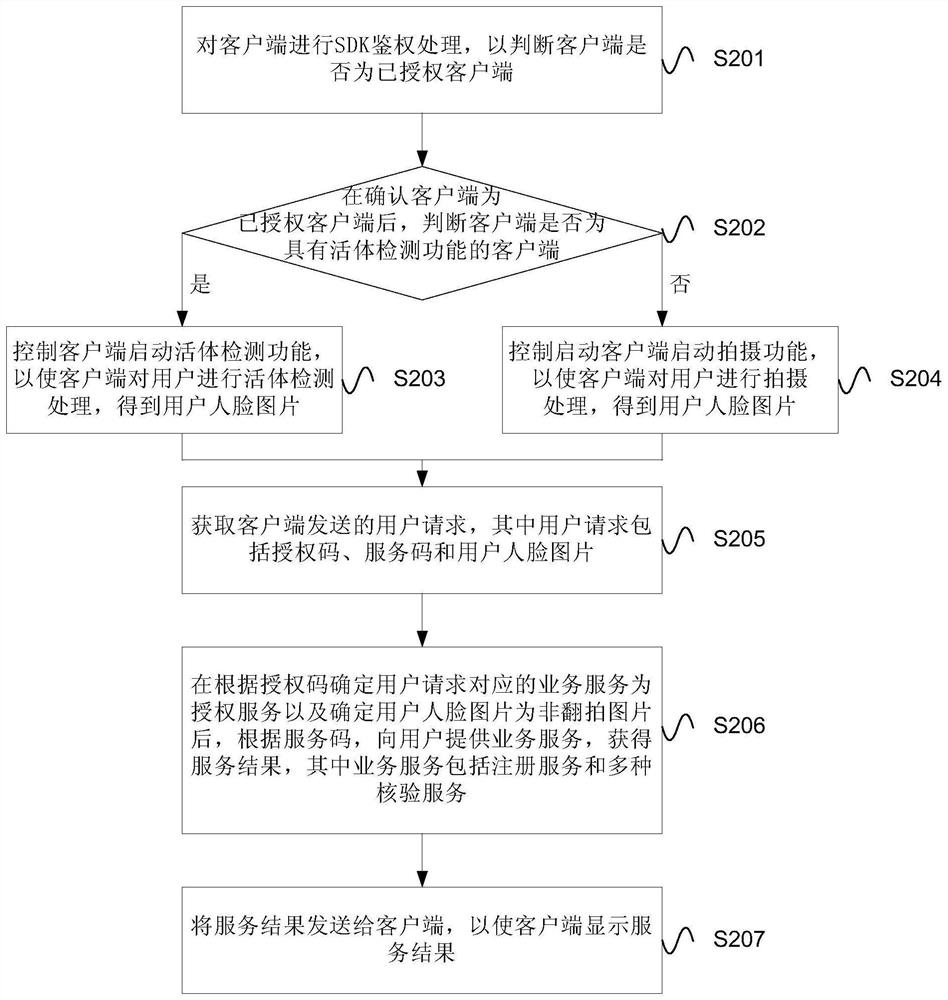
ActiveCN107609364AImprove experiencePrevent counterfeitingCharacter and pattern recognitionDigital data authenticationClient-sideAuthorization
An embodiment of the invention provides a method and a device for identifying users. The method includes acquiring a user request which includes an authorization code, a service code and a user face image sent from a client side, determining a business service corresponding to the user request according to the authorization code as authentication service while determining the user face image as anuncopy image, further, providing the business service, which includes registration service and various verification services, to the user according to the service code so as to obtain service result,and finally sending the service result to the client side while displaying the same on the client side. According to the embodiment, the problem of identification counterfeiting is solved and sourceauthenticity of identification of the user is guaranteed.
Owner:TAIKANG LIFE INSURANCE CO LTD
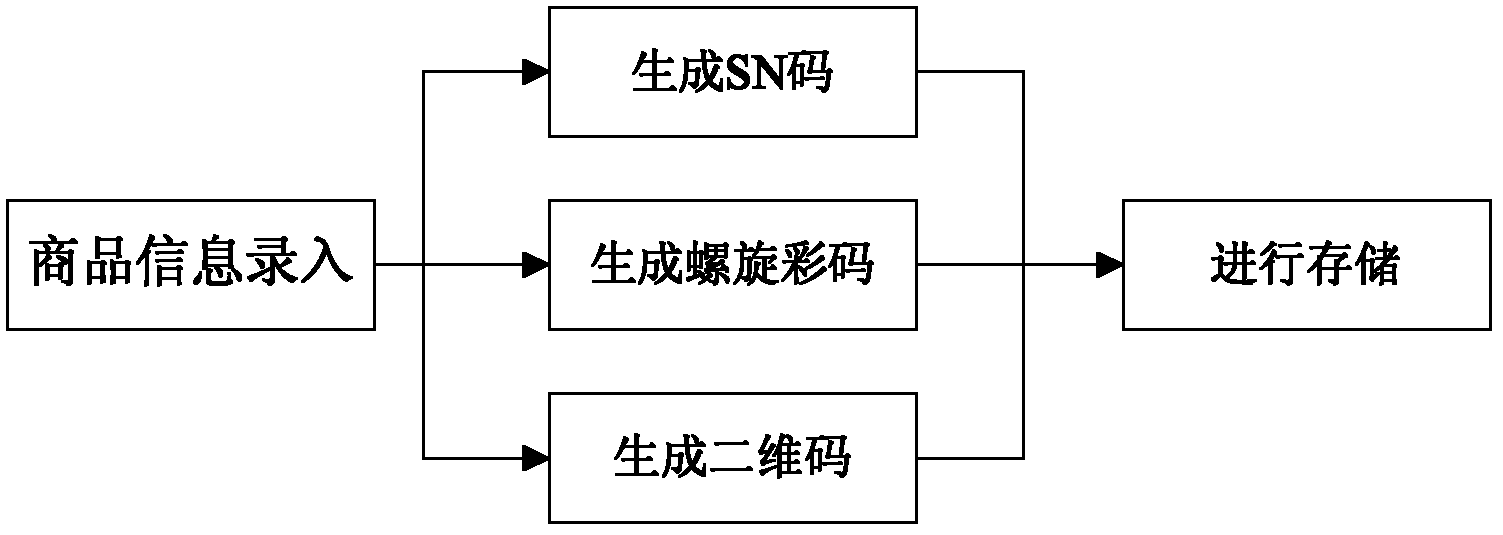
DNA (Deoxyribose Nucleic Acid) spiral color code anti-counterfeiting method and system
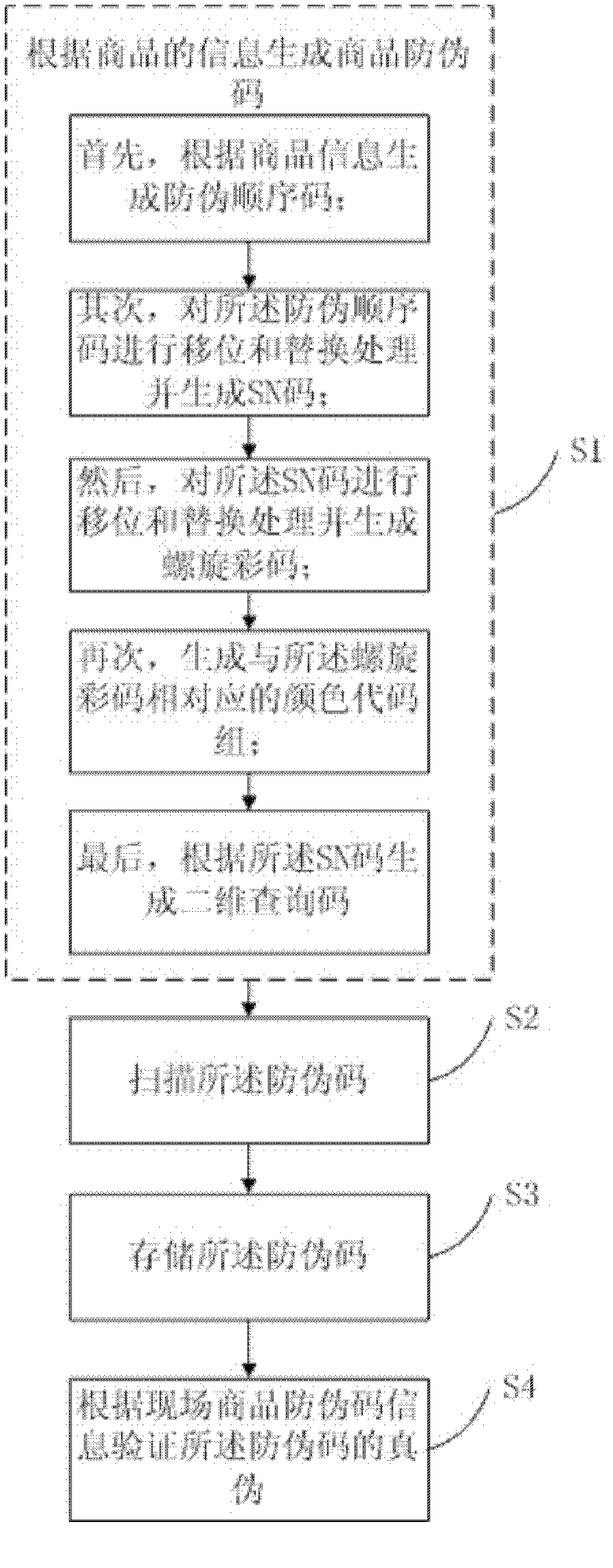
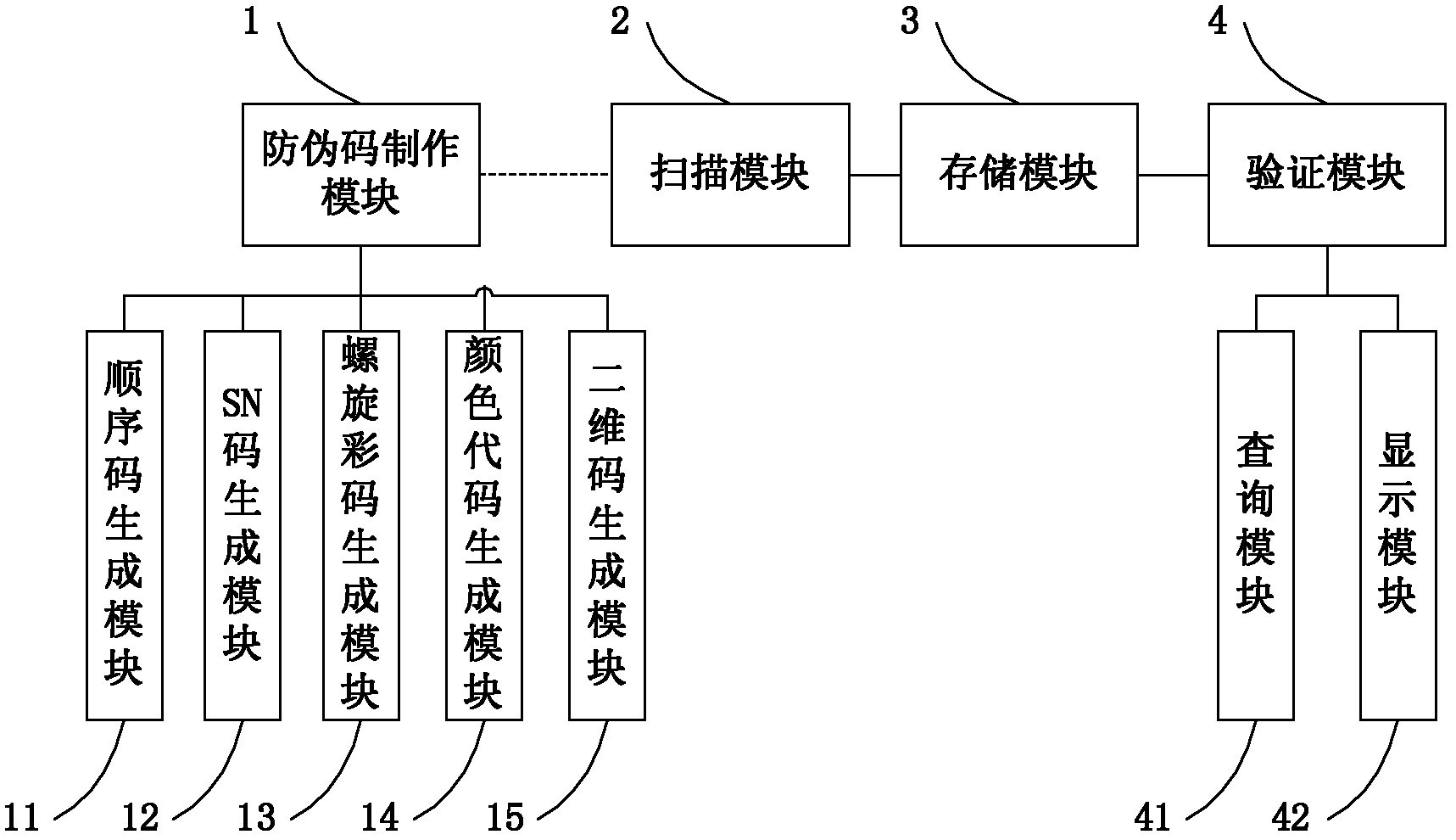
InactiveCN102622694ASolve the problem of counterfeitingCommerceRecord carriers used with machines3-deoxyriboseA-DNA
The invention discloses a DNA (Deoxyribose Nucleic Acid) spiral color code anti-counterfeiting method, belonging to the technical field of information coding. The method comprises the following steps of: 1, generating an anti-counterfeiting code of a commodity anti-counterfeiting code according to the information of a commodity; 2, scanning the anti-counterfeiting code; 3, storing the anti-counterfeiting code; and 4, verifying the truth of the anti-counterfeiting code according to field commodity anti-counterfeiting code information. The step 1 specifically comprises the following steps of: firstly, generating an anti-counterfeiting sequence code according to commodity information; secondly, performing shifting and replacing processing on the anti-counterfeiting sequence code and generating an SN (Serial Number) code; thirdly, performing shifting and replacing processing on the SN code and generating a spiral color code; fourthly, generating a color code group which corresponds to the spiral color code; and lastly, generating a two-dimensional inquiry code according to the SN code. The invention further provides a DNA spiral color code anti-counterfeiting system for implementing the method. Due to the adoption of the method and the system, the problem that the truth of products cannot be judged by a customer by inquiry detailed information due to batch counterfeiting of products.
Owner:BOA SHEN PAPER & PLASTIC PROD
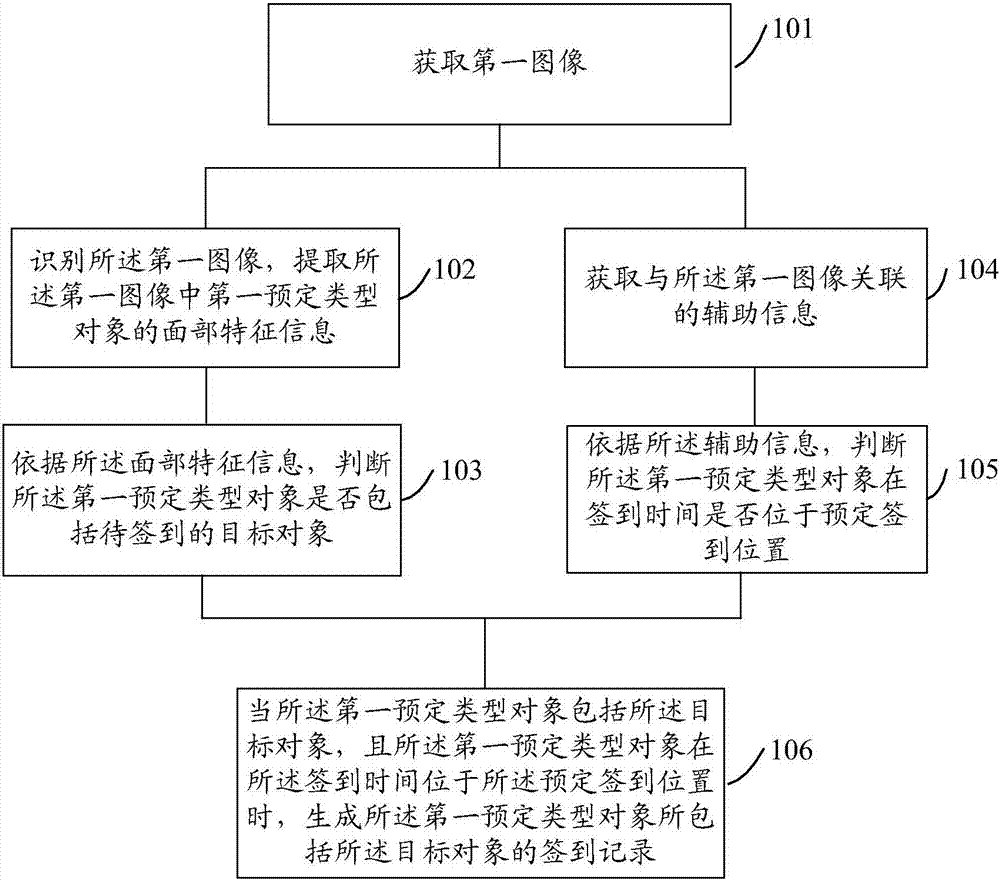
Check-in method and check-in apparatus
InactiveCN107481341AIncrease flexibilityImprove efficiencyRegistering/indicating time of eventsCharacter and pattern recognitionComputer graphics (images)Computer vision
An embodiment of the invention provides a check-in method and a check-in apparatus. The method comprises the following steps: a first image is obtained; a first image is identified in order to extract face characteristic information of objects of a first predetermined type in a first image; according to the face characteristic information, whether the objects of a first predetermined type comprises a target object to be checked in is determined; auxiliary information related to the first image is obtained; according to the auxiliary information, whether the objects of the first predetermined type are at a predetermined check in position on a check in time is determined; if the objects of the first predetermined type comprise a target object, and the objects of the first predetermined type are at the predetermined check in position on the check in time, check in records of the target object which are contained in the objects of the first predetermined type are generated.
Owner:TENCENT TECH (SHENZHEN) CO LTD
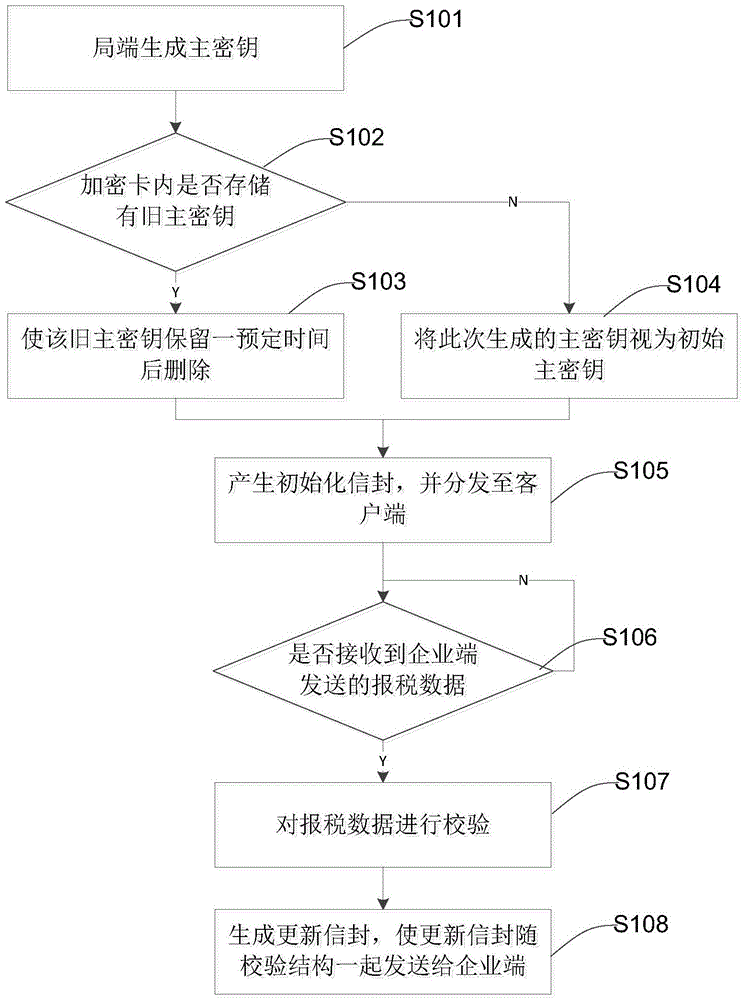
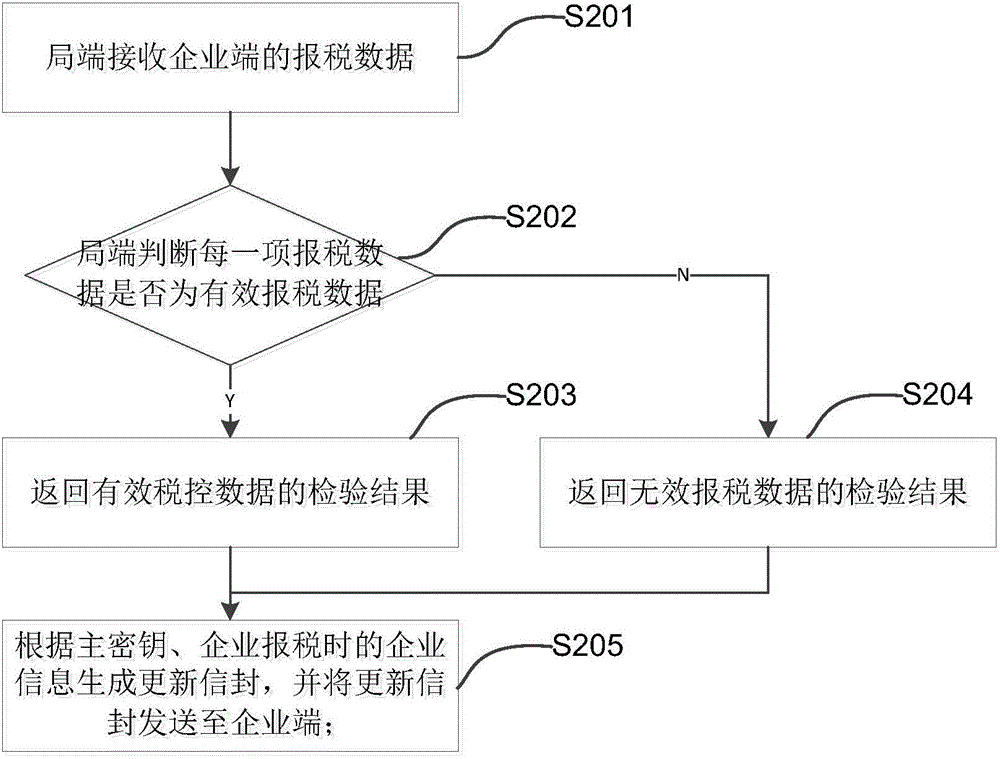
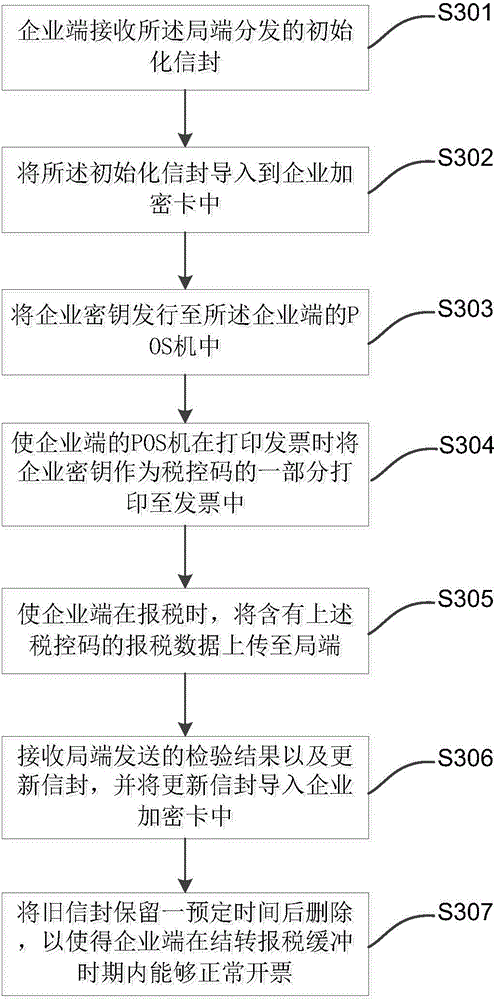
Encryption card based enterprise key distribution method and encryption card based tax declaring method
InactiveCN105809051ASimplify verification proceduresSimplify the process of negotiating keysFinanceDigital data protectionKey distributionInvoice
The present invention discloses an encryption card based enterprise key distribution method. The method comprises: generating a master key at a local side; determining whether an old master key is stored in an external encryption card; if the old key is stored, reserving the old key for a pre-determined period of time and deleting the old key; if the old key is not stored, taking the currently generated master key as an initial master key; enabling the local side to perform expansion according to the master key and stored enterprise information, so as to generate an initial envelope and distribute the initial envelope to an enterprise terminal; enabling the local side to determine whether tax declaring data sent by the enterprise terminal is received; when the tax declaring data of the enterprise terminal is received, checking the tax declaring data, and returning a check result to the enterprise terminal; and generating an update envelope according to the master key, so as to send the update envelope to the enterprise terminal along with the check result, wherein the update envelope comprises a new updated enterprise key, an update period of the new enterprise key, a maximal loss-reporting number of times within the update period, an invoice size and invoice storage region size information. The present invention further discloses a tax declaring method.
Owner:AEROSPACE INFORMATION
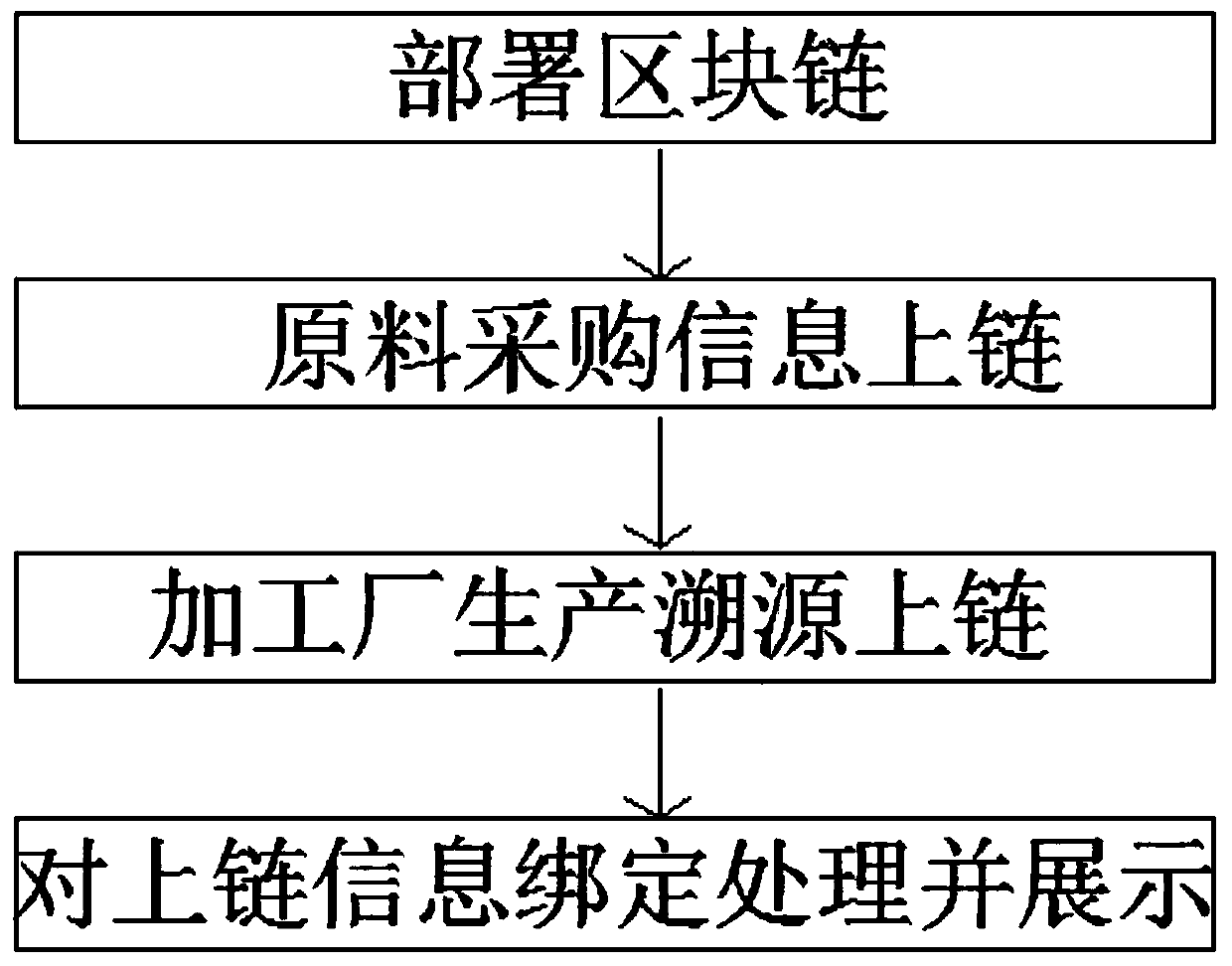
Cross-border e-commerce imported food tracing method and system based on block chain
InactiveCN110852765ASolve the problem of counterfeitingSolve productivityFinanceBuying/selling/leasing transactionsFood safetyEngineering
The invention discloses a cross-border e-commerce imported food tracing method and system based on a block chain, and belongs to the technical field of imported food safety. According to the cross-border e-commerce imported food tracing method based on the block chain, firstly, a block chain platform is deployed, endorsement logic required by imported food tracing data is defined in an intelligentcontract, chain writing is performed by utilizing data provided by a processing factory and a bonded store, a consumer scans a code to send out a data request operation, and block chain data is readand displayed. According to the cross-border e-commerce imported food tracing method based on the block chain, the data credibility can be improved, the tamper-proof difficulty is enhanced, imported food flow direction recording and displaying are safer, and the method has good application and popularization value.
Owner:山东爱城市网信息技术有限公司
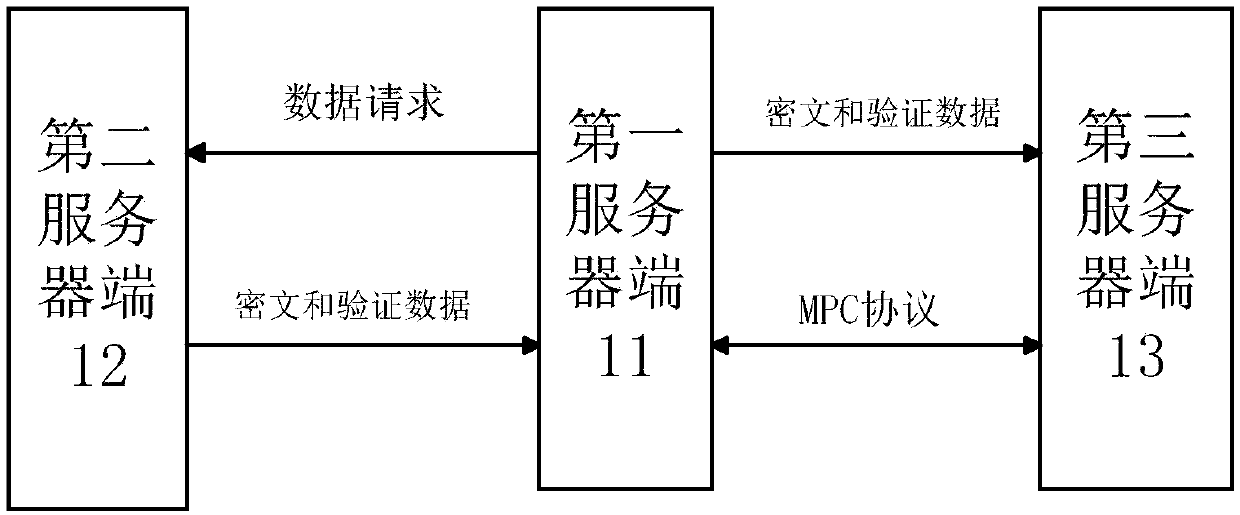
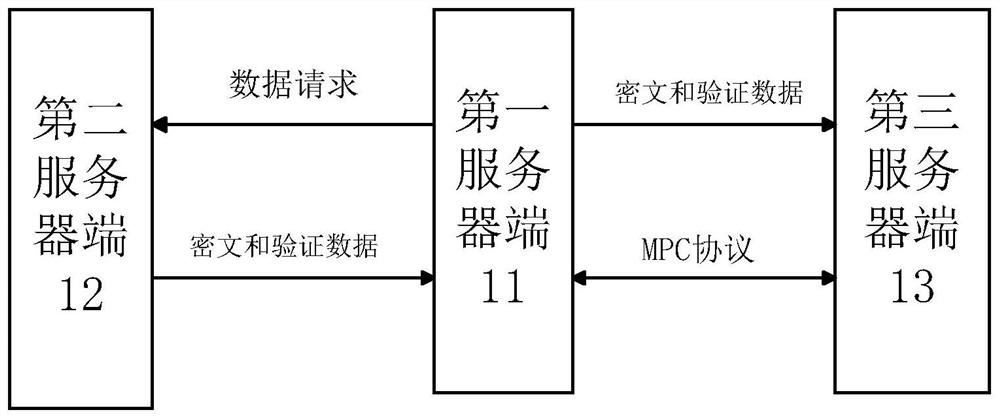
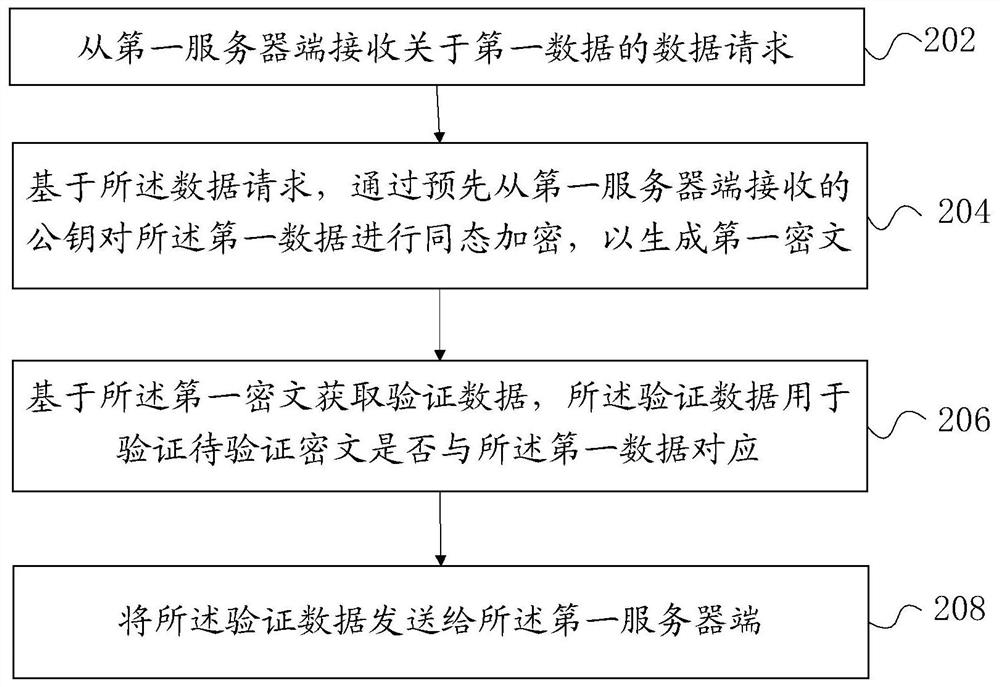
Method and device for obtaining input of secure multi-party computing protocol
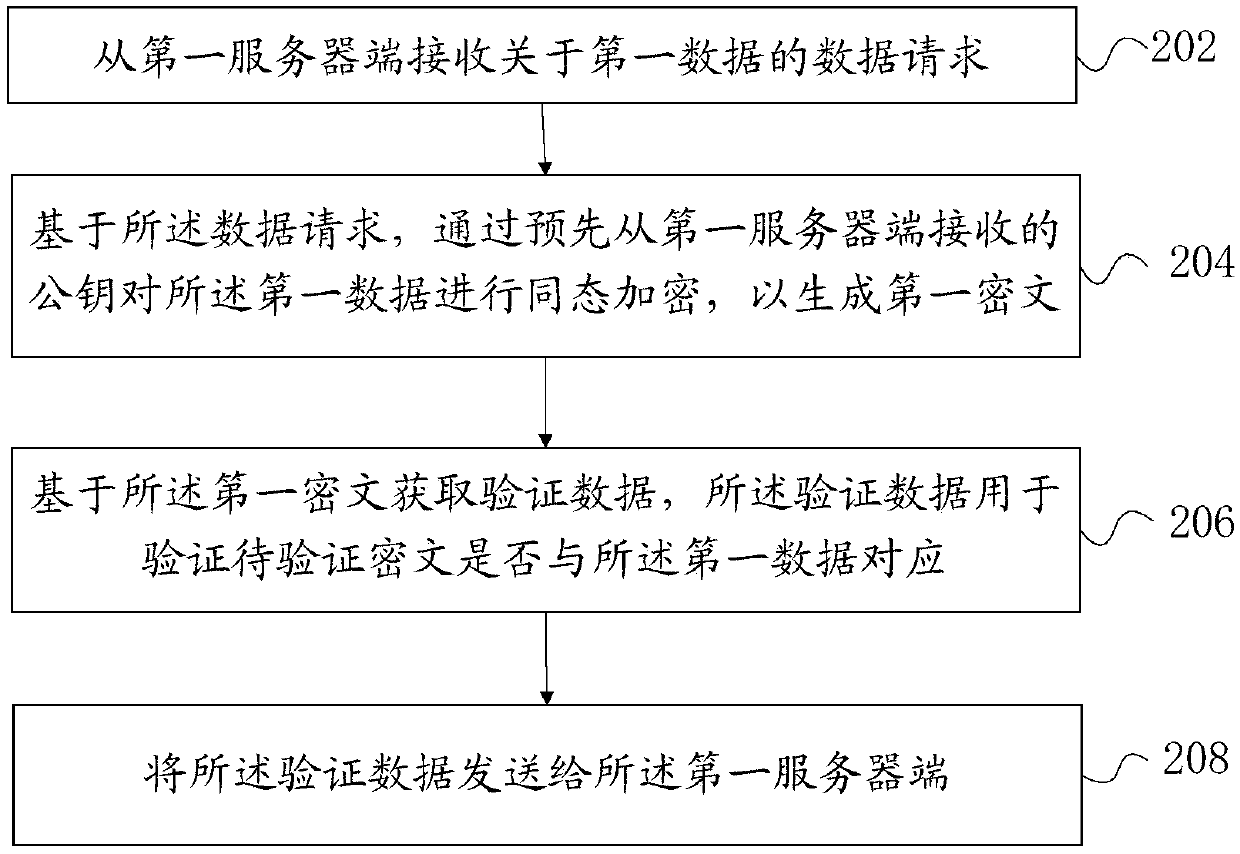
ActiveCN110661610AAddress privacy concernsSolve the problem of counterfeitingComputer security arrangementsCommunication with homomorphic encryptionProtocol for Carrying Authentication for Network AccessComputer security
The embodiment of the invention provides a method and device for obtaining input of a secure multi-party computing protocol. A participant of the secure multi-party computing protocol comprises a first server side. The first server side is a server side of a first object; the secure multi-party computing protocol performs computing based on first data of a first object, the first data is stored ina second server side, the second server side is a server side of an authority, and the method is executed at the second server side and comprises the steps that a data request about the first data isreceived from the first server side; based on the data request, homomorphic encryption is carried out on first data through a public key received from a first server in advance to generate a first ciphertext, and the public key is a homomorphic encryption public key of the first object; verification data is acquired based on the first ciphertext, wherein the verification data is used for verifying whether the to-be-verified ciphertext corresponds to the first data; and sending the verification data to the first server.
Owner:ADVANCED NEW TECH CO LTD
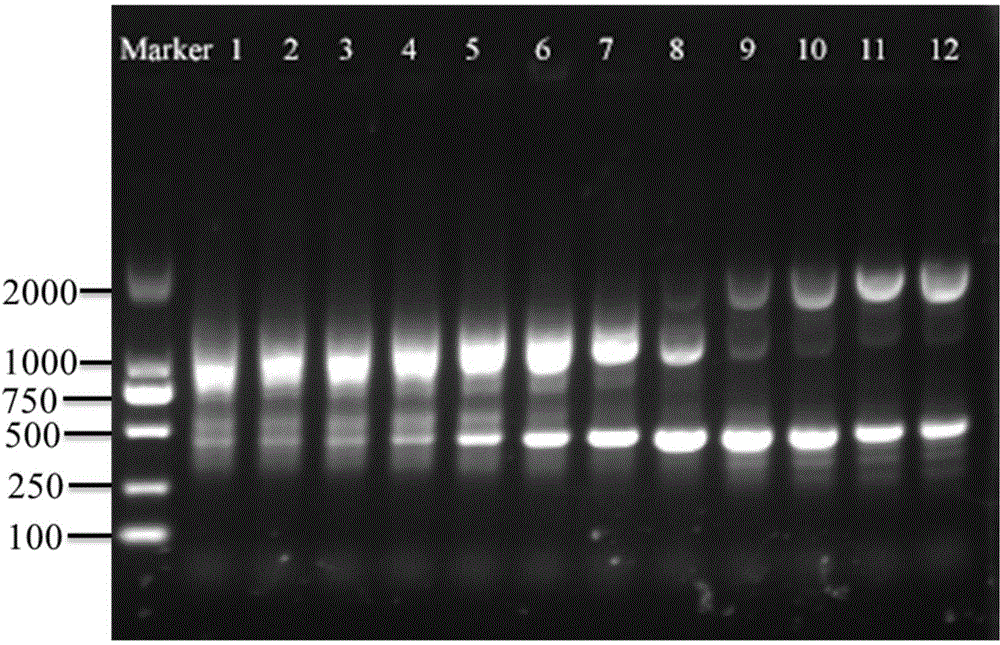
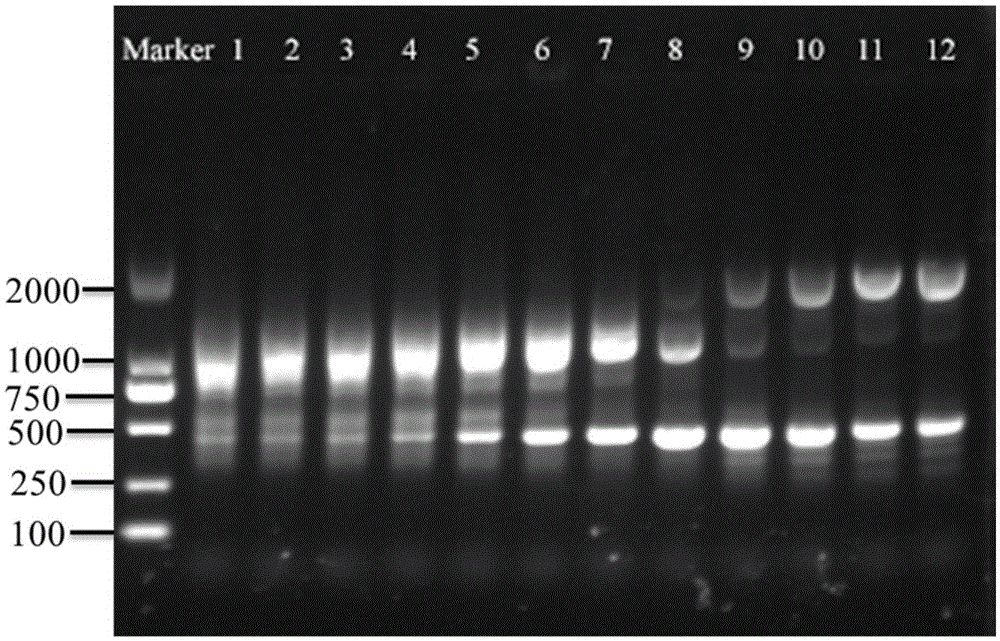
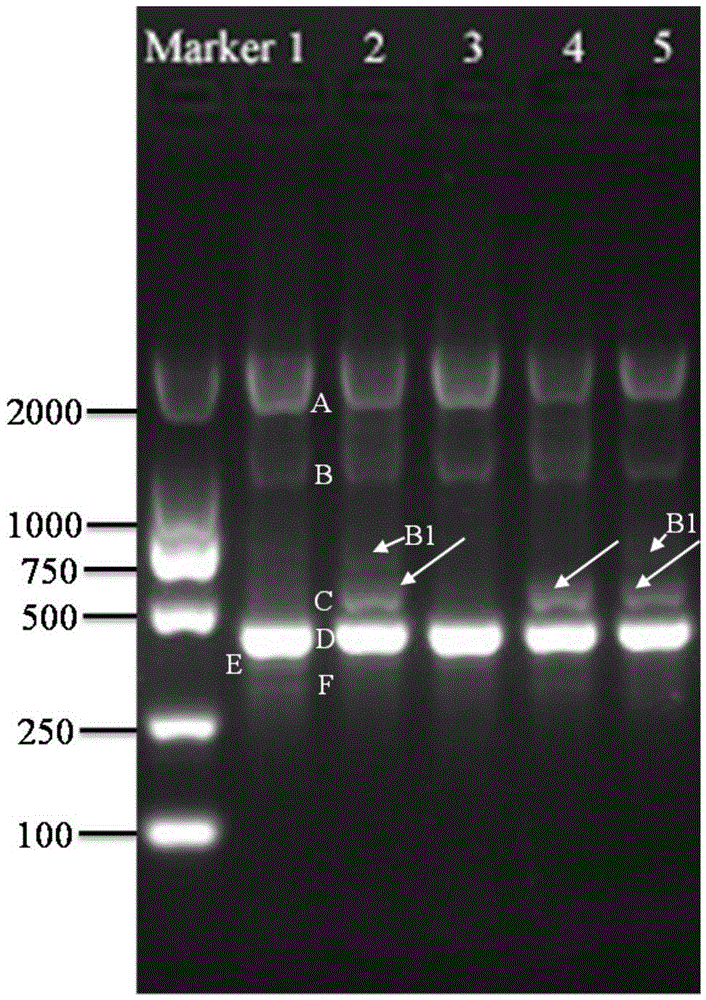
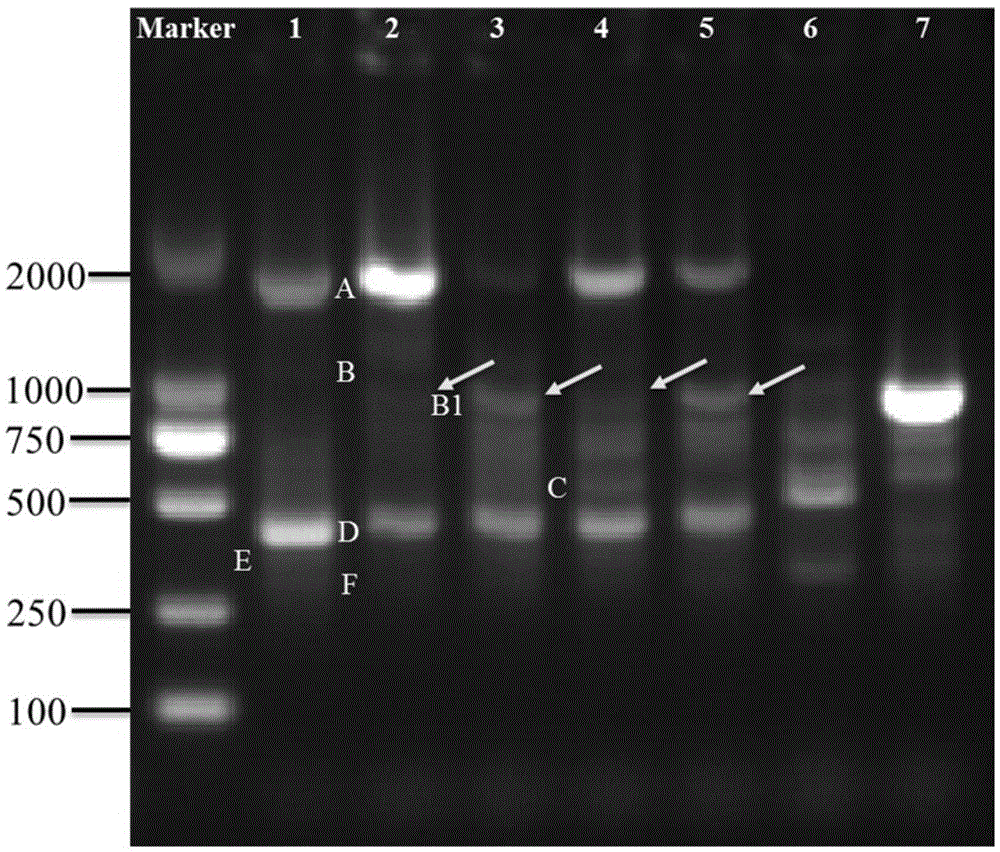
Special primer, method and kit for identifying Meishan pig or meat product thereof
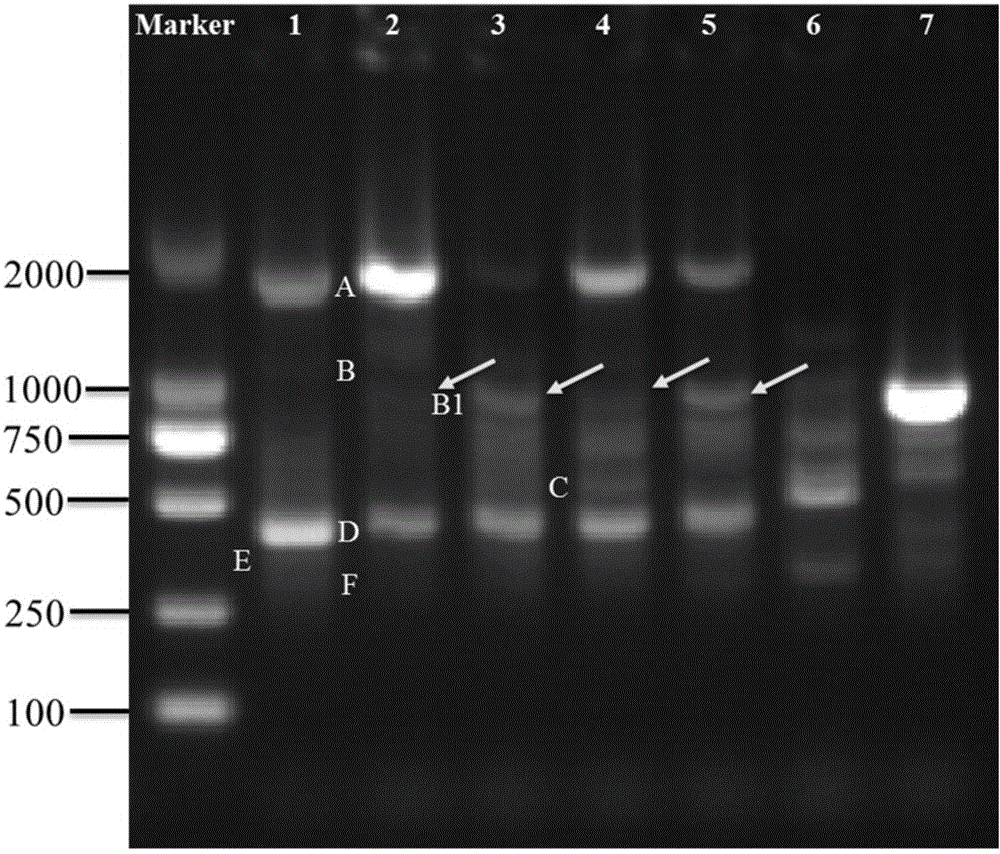
InactiveCN104593519AEasy to operateSolve the problem of counterfeitingMicrobiological testing/measurementDNA/RNA fragmentationGenomic DNAPolymerase chain reaction
The invention discloses a special primer, a method and a kit for identifying a Meishan pig or a meat product thereof. A sequence of the special primer is as shown in SEQ ID NO.1. The method comprises the following steps: (1), extracting genomic DNA (deoxyribonucleic acid) of fresh meat and / or the meat product; (2), taking genomic DNA in the step (1) as a template, and performing a PCR (polymerase chain reaction) by utilizing the primer with the nucleotide sequence as shown in SEQ ID NO.1. The method further comprises the following steps: (3), creating an electrophoretogram of amplified fragments in the PCR in the step (2); or (4), according to the electrophoretogram in the step (3), identifying the fresh meat and / or the meat product of the Meishan pig. The special primer and the method are utilized to effectively solve an identification problem of a Meishan pig variety and can distinguish the Meishan pig variety from other pig meat varieties or beef and mutton. The identification method is simple to carry out and accurate in result.
Owner:SHANGHAI VETERINARY RES INST CHINESE ACAD OF AGRI SCI +2
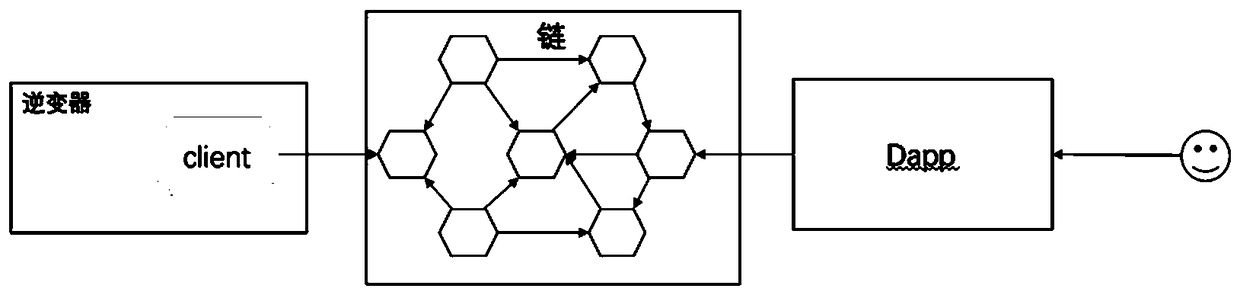
Method for monitoring new energy photovoltaic power generation data on basis of block chains
InactiveCN109327077ASolve the problem of counterfeitingReliable dataPhotovoltaic monitoringCircuit arrangementsAccess networkNew energy
The invention discloses a method for monitoring new energy photovoltaic power generation data on the basis of block chains. The method includes steps of 1, implanting block chain clients in inverters;2, mounting the inverters and allowing the inverters to access networks; 3, automatically starting the block chain clients after the inverters are powered on, detecting communication with block chainnetworks, determining whether chain accounts are available or not by means of detection and generating a chain account by means of automatic initialization if the chain accounts are not available; 4,collecting power generation data of photovoltaic power stations by the inverters, triggering data chain uploading interfaces of clients at regular time, calling intelligent contracts and carrying outdata chain uploading; 5, developing decentralization App (application) on the basis of web3.js, carrying out interactive communication with the block chain networks, calling block chain intelligent contracts and querying the real-time power generation data of the corresponding power stations by related information of equipment. The block chain clients are implemented on the basis of the web3.js or web3j, and inverters of the block chain clients are provided with wifi (wireless fidelity) or mobile communication modules.
Owner:杭州白小丁科技有限公司
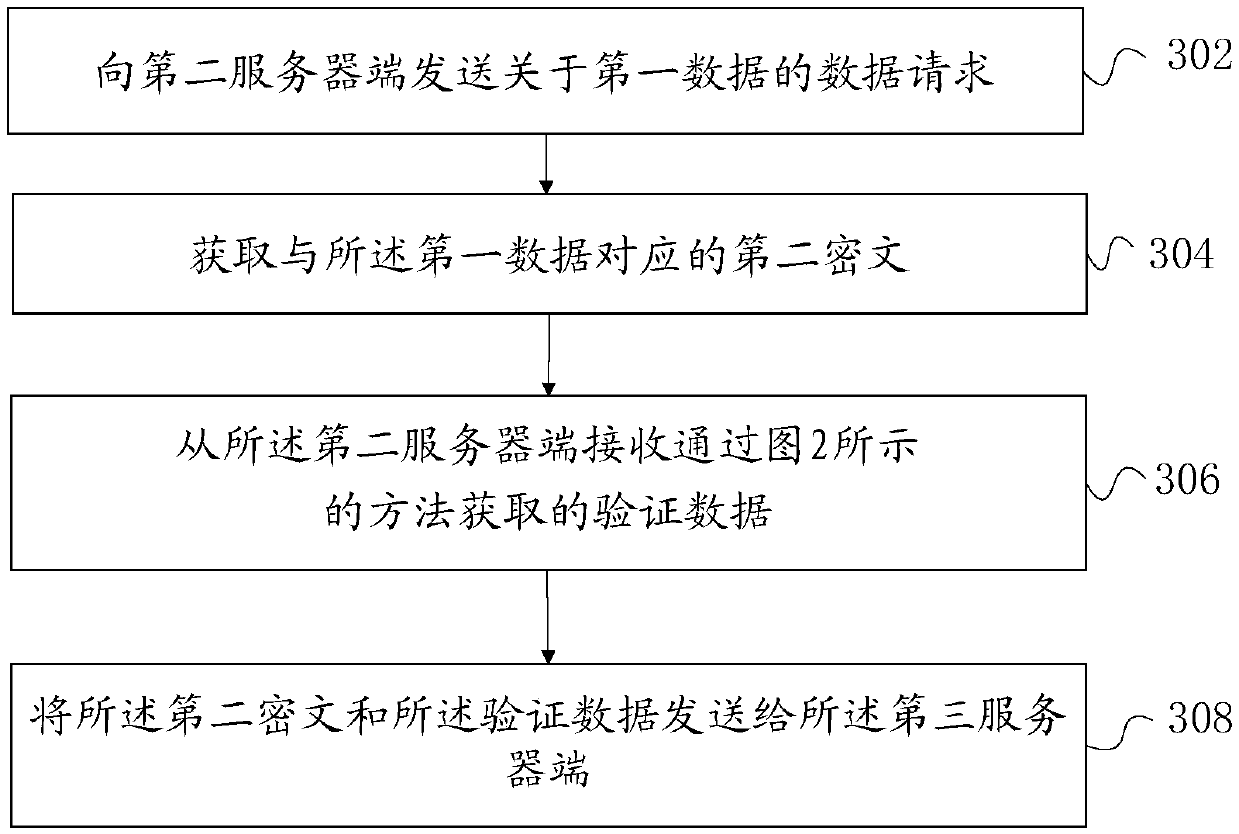
Method and device for obtaining input of secure multi-party computing protocol
ActiveCN110661610BAddress privacy concernsSolve the problem of counterfeitingComputer security arrangementsCommunication with homomorphic encryptionCiphertextProtocol for Carrying Authentication for Network Access
The embodiment of this specification provides a method and device for obtaining the input of the secure multi-party computing protocol. The participants of the secure multi-party computing protocol include the first server end, and the first server end is the server end of the first object. The secure multi-party computing protocol is based on The first data of the first object is calculated, wherein the first data is stored in the second server end, the second server end is the server end of the authority, and the method is executed on the second server end, including: from the first The server receives a data request for the first data; based on the data request, homomorphically encrypts the first data with a public key previously received from the first server to generate a first ciphertext, wherein the public key is the first ciphertext A homomorphic encryption public key of an object; obtaining verification data based on the first ciphertext, and the verification data is used to verify whether the ciphertext to be verified corresponds to the first data; and sending the verification data to the first server.
Owner:ADVANCED NEW TECH CO LTD
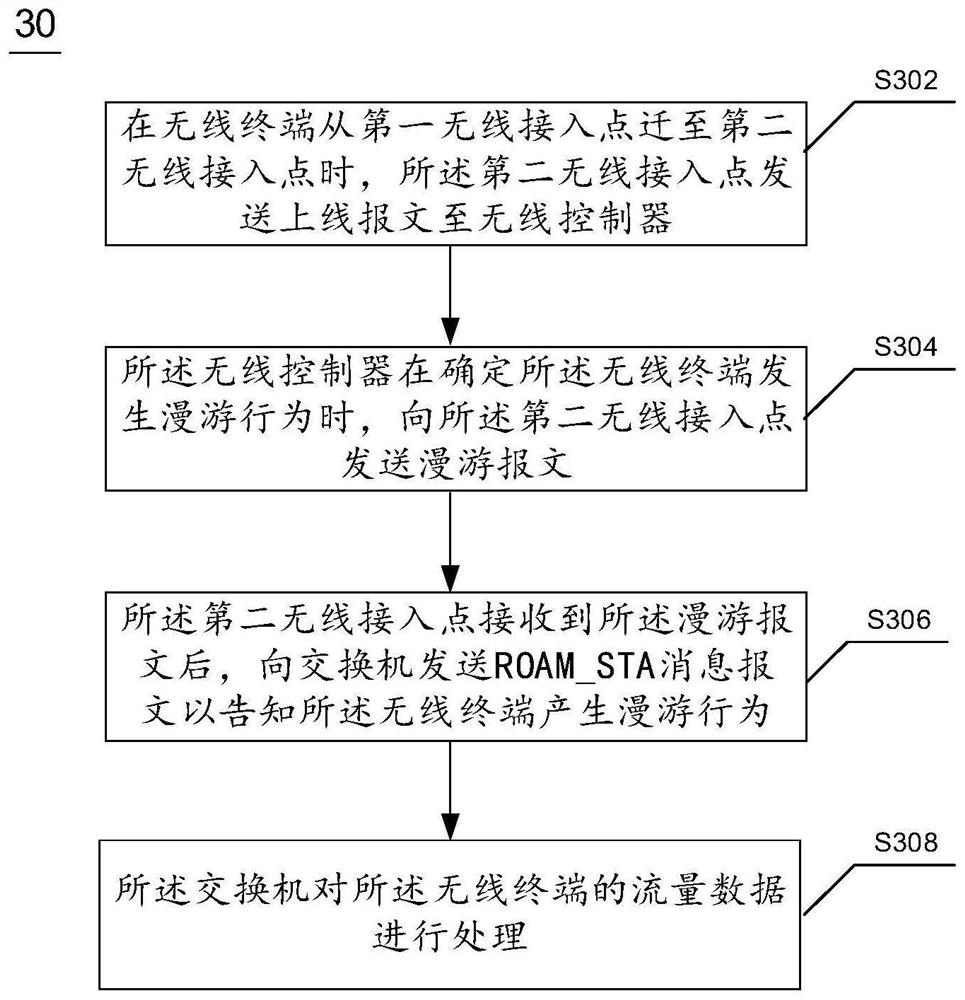
Roaming processing method and system of wireless terminal
ActiveCN114363879AReduce flow pressureSolve the problem of counterfeitingSecurity arrangementNetwork data managementComputer networkTelecommunications
The invention provides a roaming processing method and system of a wireless terminal, electronic equipment and a computer readable medium. The method comprises the following steps: when a wireless terminal is migrated from a first wireless access point to a second wireless access point, the second wireless access point sends an online message to a wireless controller; when the wireless controller determines that the wireless terminal has a roaming behavior, the wireless controller sends a roaming message to the second wireless access point; after receiving the roaming message, the second wireless access point sends an ROAMSTA information message to a switch to inform the wireless terminal of generating a roaming behavior; and the switch processes the flow data of the wireless terminal. According to the roaming processing method and system of the wireless terminal, whether the roaming behavior happens to the wireless terminal or not can be accurately notified to the switch, the problem of flow pressure of the switch in a special scene is reduced as much as possible, and the problem that the switch misreports terminal counterfeiting due to roaming of the wireless terminal is solved.
Owner:HANGZHOU DPTECH TECH
A tpcm-based network camera identity authentication method
ActiveCN103888257BReduced authenticationImplement identity authenticationUser identity/authority verificationClosed circuit television systemsProcessor registerMemory code
Owner:BEIJING UNIV OF TECH
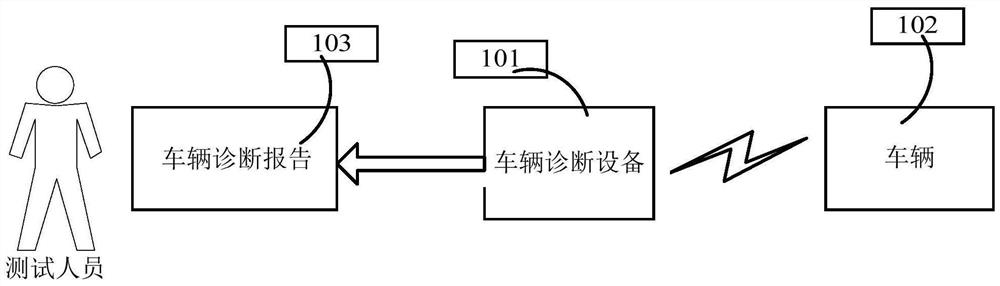
Vehicle test data recording method, vehicle diagnosis equipment and storage medium
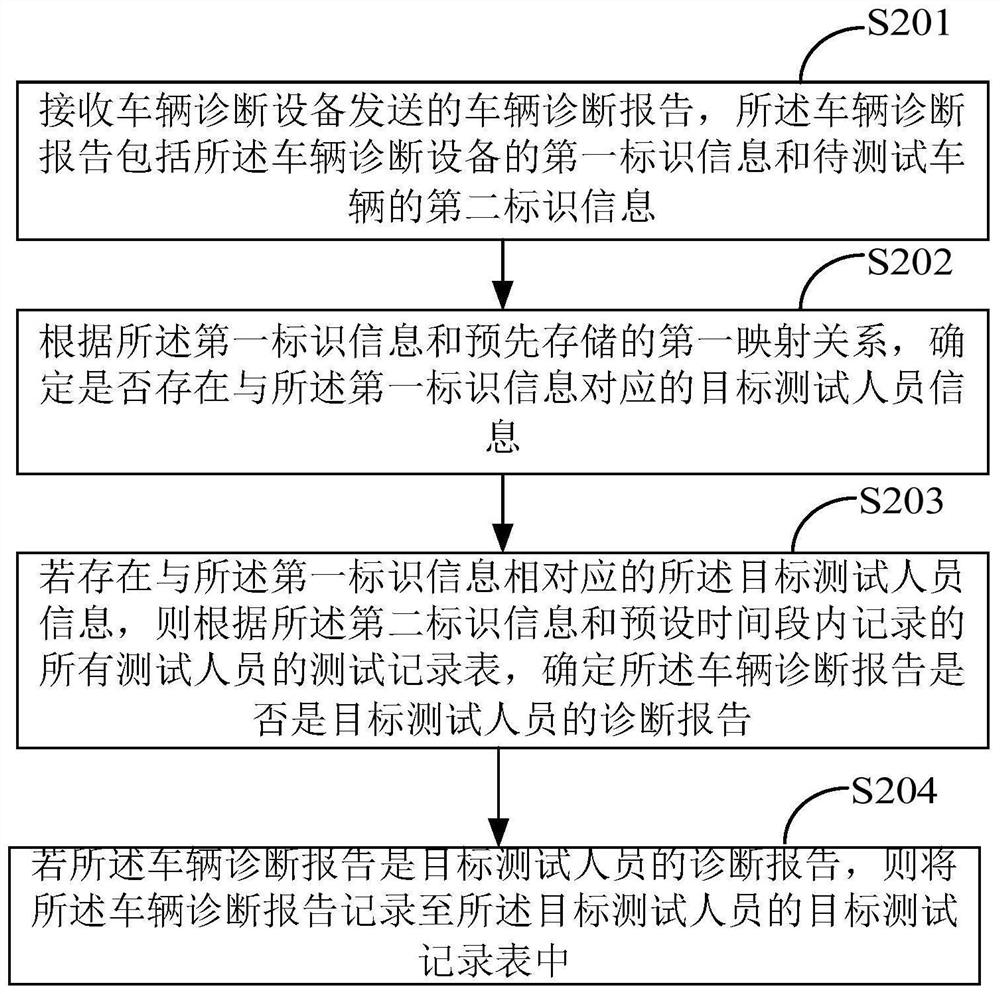
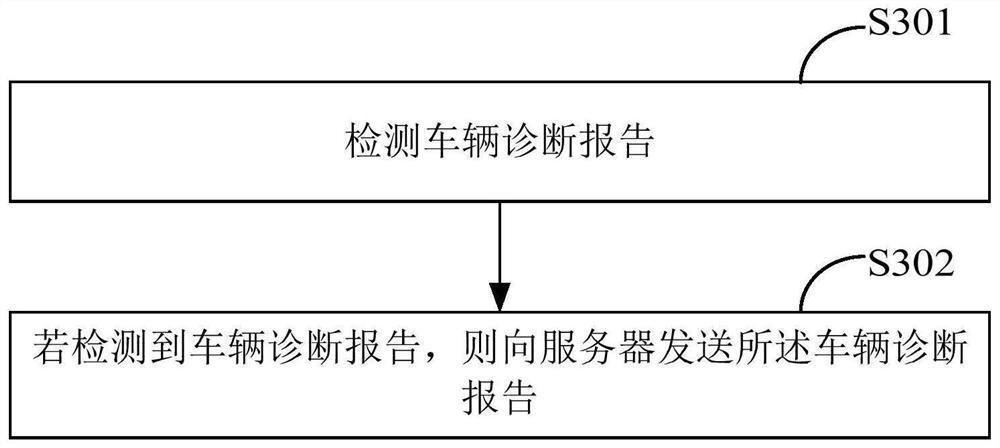
ActiveCN111813776ASolve the problem of counterfeitingVehicle testingOffice automationData recordingDiagnostic equipment
The invention provides a vehicle test data recording method, a server, vehicle diagnosis equipment and a storage medium, relates to the field of vehicles, and can effectively avoid the problem that test personnel counterfeit vehicle test data. The vehicle test data recording method comprises the following steps: receiving a vehicle diagnosis report sent by vehicle diagnosis equipment; determiningwhether target tester information corresponding to the first identification information exists or not according to the first identification information and a pre-stored first mapping relationship; ifthe target tester information corresponding to the first identification information exists, determining whether the vehicle diagnosis report is a diagnosis report of a target tester or not according to the second identification information and test record tables of all testers recorded in a preset time period; and if the vehicle diagnosis report is a diagnosis report of a target tester, recordingthe vehicle diagnosis report into a target test record table of the target tester.
Owner:LAUNCH TECH CO LTD
Anti-recycling and anti-counterfeiting packaging structure and anti-counterfeiting method thereof
PendingCN112978075ASolve the problem of counterfeitingImprove anti-counterfeiting effectLocking devicesEngineeringMechanical engineering
The invention belongs to the technical field of packaging, and relates to an anti-recycling and anti-counterfeiting packaging structure. The anti-recycling and anti-counterfeiting packaging structure comprises a packaging shell body, a packaging film and an anti-counterfeiting mark, wherein the packaging shell body is provided with a pattern I, the packaging film is coated on the packaging shell body, and the packaging film is provided with a pattern II; and the anti-counterfeiting mark is adhered to the position, corresponding to the pattern I, of the packaging film, the anti-counterfeiting mark is provided with a pattern III, the pattern I, the pattern II and the anti-counterfeiting mark are partially overlapped, and the overlapping is random overlapping. According to the invention, the packaging film is randomly coated on the packaging shell body, and the anti-counterfeiting mark is randomly adhered to the packaging film, so that a plurality of overlapped images for comparison are randomly generated, and a counterfeiter is difficult to obtain a plurality of identical overlapped images for comparison by repeating the two random processes in a completely identical manner; and therefore, a great anti-counterfeiting effect is achieved, and the problem of counterfeiting of the anti-counterfeiting package can be thoroughly solved.
Owner:BEIJING KESIYUAN TECH
Anti-counterfeiting method of anti-counterfeiting package
PendingCN114249024AImprove anti-counterfeiting effectSolve the problem of counterfeitingContainers for flexible articlesPackaging cigaretteAlgorithmIndustrial engineering
The invention belongs to the technical field of anti-counterfeiting, and relates to an anti-counterfeiting method of an anti-counterfeiting package, which comprises the following steps of: 1, acquiring an anti-counterfeiting identification pattern on the anti-counterfeiting package, and uploading the anti-counterfeiting identification pattern to a cloud database as a stored anti-counterfeiting identification pattern; and step 2, during identification, a user obtains an anti-counterfeiting identification pattern to be identified on the anti-counterfeiting package to be identified, obtains a stored anti-counterfeiting identification pattern in the cloud database, and compares the anti-counterfeiting identification pattern to be identified with the stored anti-counterfeiting identification pattern so as to judge the authenticity of the anti-counterfeiting package to be identified and a product in the anti-counterfeiting package. The anti-counterfeiting identification patterns are generated by randomly overlapping a stay wire pattern and a packaging material pattern or a packaging material overlapping pattern or an adhesive film pattern, so that counterfeiters are difficult to obtain a plurality of same anti-counterfeiting identification patterns for comparison by repeating the random process in a completely identical manner. Therefore, the anti-counterfeiting method of the anti-counterfeiting package can thoroughly solve the problem of counterfeiting of the anti-counterfeiting package.
Owner:BEIJING KESIYUAN TECH
Verification system for verifying authenticity of electronic deposit certificate
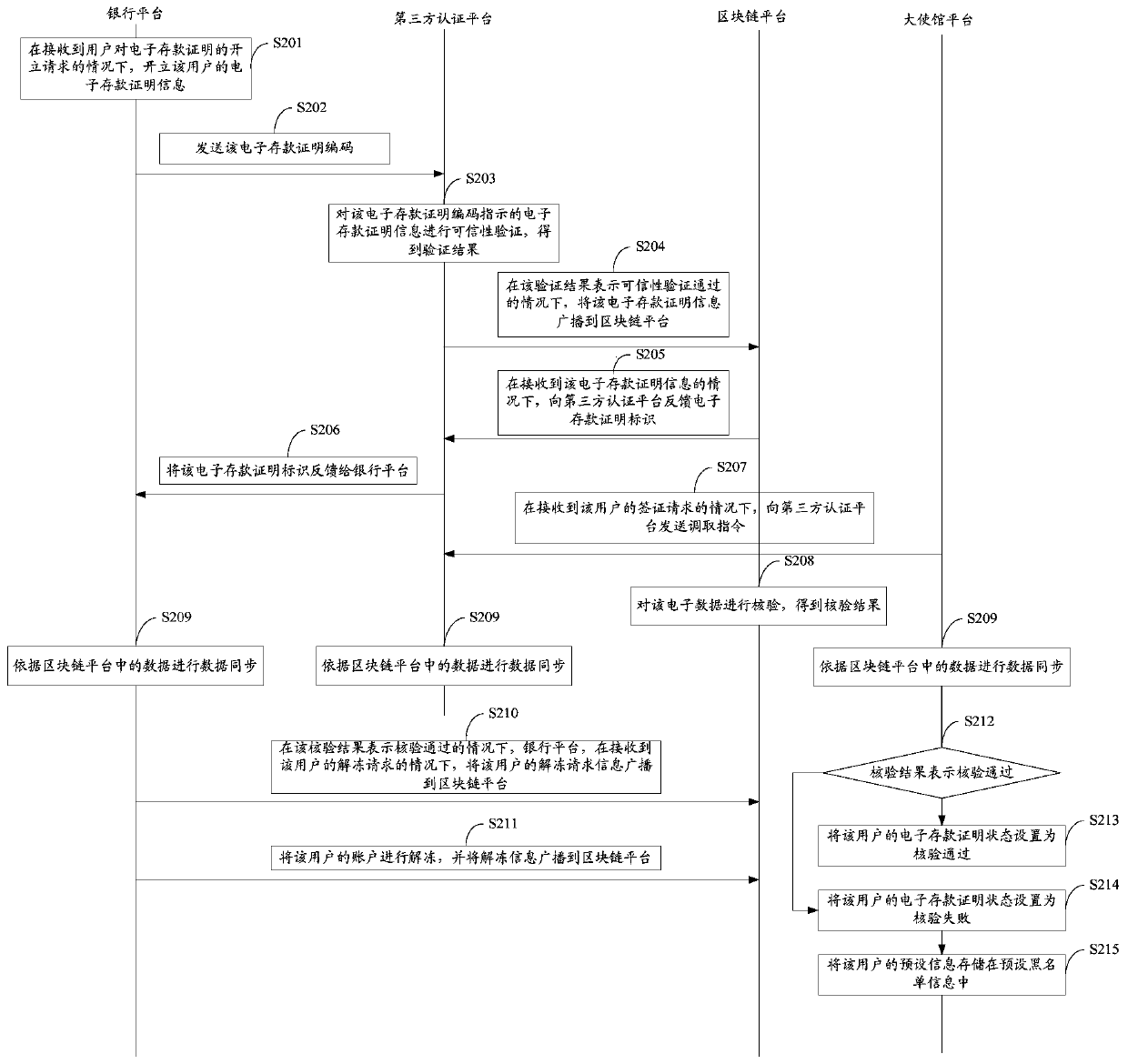
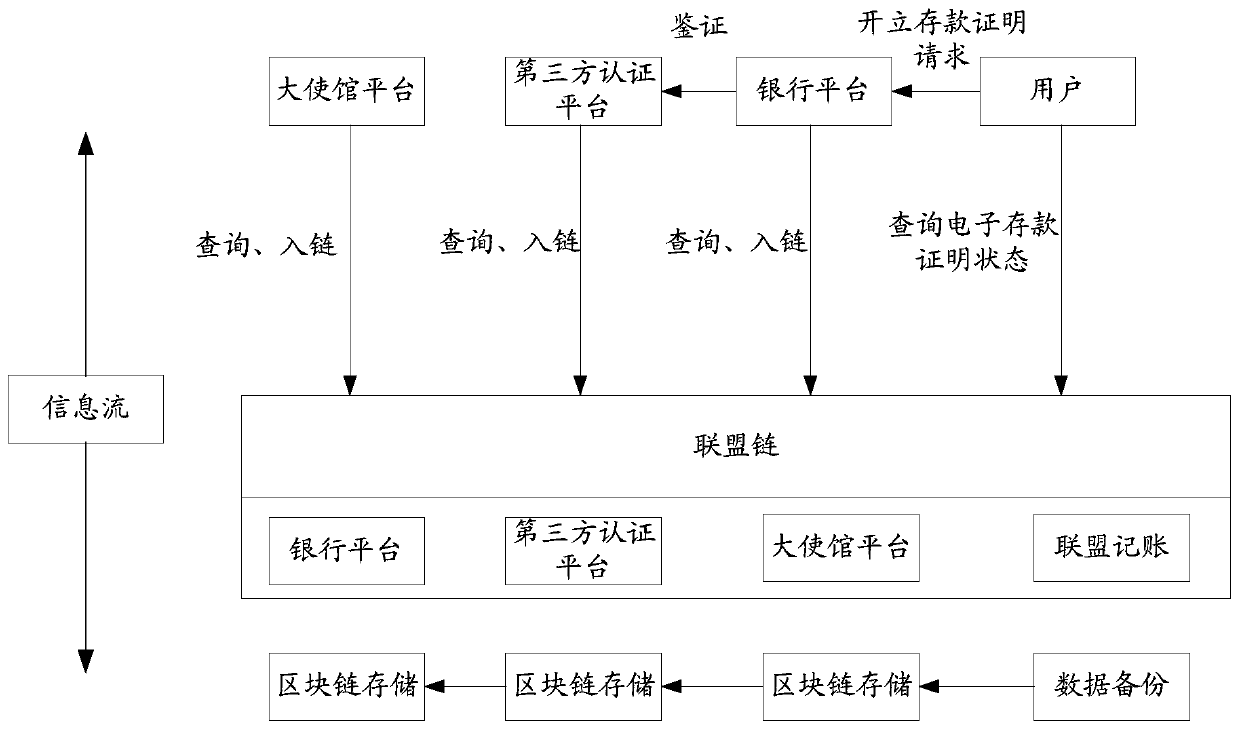
ActiveCN111582888AGuarantee authenticityEnsure openness and transparencyFinanceDatabase distribution/replicationThird partyEngineering
The invention provides a verification system for authenticity of an electronic deposit certificate, and the system comprises the steps that a bank platform opens the electronic deposit certificate information of a user under the condition that the bank platform receives an opening request of the user for the electronic deposit certificate, and transmits an electronic deposit certificate code to athird-party authentication platform; the third-party authentication platform performs credibility verification on the electronic deposit certificate information indicated by the electronic deposit certificate code to obtain a verification result; after the verification result shows that the credibility verification is passed, the electronic deposit certificate information is transmitted to the blockchain platform; the blockchain platform feeds back an electronic deposit certificate identifier to the third-party authentication platform; under the condition that the mission hall platform receives the visa request of the user, a calling instruction is sent to a third-party authentication platform; and the block chain platform verifies the electronic data. According to the application, the third-party authentication platform is a trusted authentication platform verified by the market, so that the problem of counterfeiting of deposit certificate information can be avoided.
Owner:BANK OF CHINA
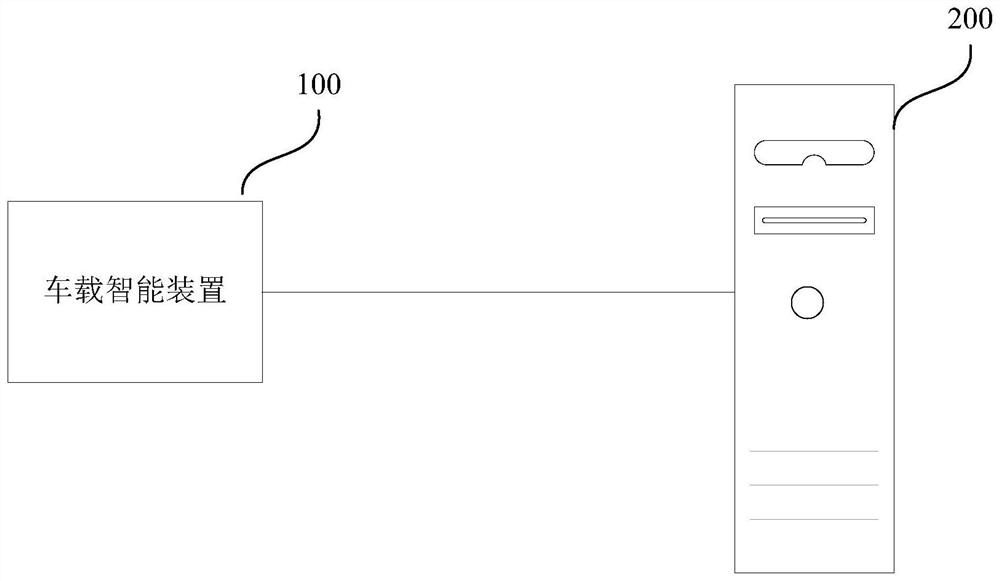
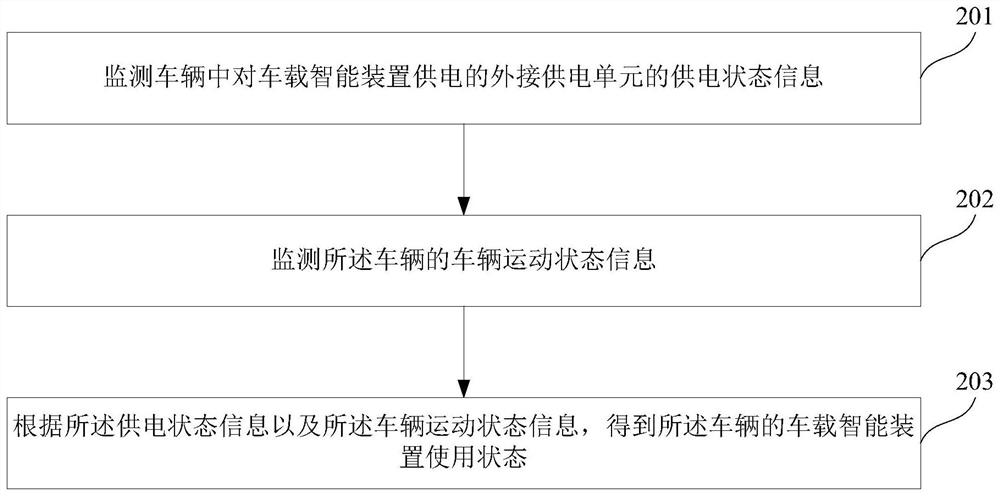
A vehicle-mounted intelligent device usage status monitoring device and method
ActiveCN112061054BSolve the problem of counterfeitingGuaranteed authenticityVehicle connectorsCoupling contact membersIn vehicleArtificial intelligence
This article relates to the field of monitoring technology, and in particular to a device and method for monitoring the usage status of a vehicle-mounted intelligent device. It is used to solve the problem of artificial cheating on the usage of vehicle-mounted intelligent devices. The device provides a power supply monitoring unit for monitoring the power supply status information of an external power supply unit in the vehicle that supplies power to the vehicle-mounted intelligent devices; a vehicle motion status monitoring unit is used for monitoring Vehicle motion status information of the vehicle; a processing unit configured to obtain the vehicle-mounted intelligent device usage status of the vehicle based on the power supply status information and the vehicle motion status information. It can solve the problem of data fraud caused by abnormal use of vehicle-mounted smart devices. After the vehicle-mounted smart devices are installed and fixed in the car, they can be powered and used normally, which can ensure the authenticity and validity of the relevant data collected, which is conducive to the normal operation of UBI auto insurance.
Owner:TAIKANG LIFE INSURANCE CO LTD
Packaging film, anti-counterfeiting package, manufacturing method of anti-counterfeiting package and anti-counterfeiting method of anti-counterfeiting package
PendingCN114249023AImprove anti-counterfeiting effectSolve the problem of counterfeitingContainers for flexible articlesFlexible coversMechanical engineeringManufacturing engineering
The invention belongs to the technical field of packaging, and relates to a packaging film, in particular to a packaging film for anti-counterfeiting packaging, the packaging film comprises a base material, the base material is provided with a plurality of anti-counterfeiting elements, the plurality of anti-counterfeiting elements are used for forming an anti-counterfeiting pattern after the packaging film completes wrapping of a packaging object, and the anti-counterfeiting pattern is used for forming an anti-counterfeiting pattern after wrapping of the packaging object is completed. According to the packaging film disclosed by the invention, the packaging film random pattern formed after the packaging of the packaging material is completed is difficult to copy, so that the technical problems that in the prior art, anti-counterfeiting packaging products are easily counterfeited by counterfeiters in batches and are counterfeited by secondary recovery, and the anti-counterfeiting effect is poor can be solved; the invention further relates to an anti-counterfeit package, a manufacturing method of the anti-counterfeit package and an anti-counterfeit method of the anti-counterfeit package, the anti-counterfeit package adopts multiple anti-counterfeit technologies, the randomness is higher, the anti-counterfeit effect is better, and the same technical problems can be solved.
Owner:BEIJING KESIYUAN TECH
User identity confirmation method and device
ActiveCN107609364BImprove experiencePrevent counterfeitingCharacter and pattern recognitionDigital data authenticationEngineeringAuthorization
An embodiment of the invention provides a method and a device for identifying users. The method includes acquiring a user request which includes an authorization code, a service code and a user face image sent from a client side, determining a business service corresponding to the user request according to the authorization code as authentication service while determining the user face image as anuncopy image, further, providing the business service, which includes registration service and various verification services, to the user according to the service code so as to obtain service result,and finally sending the service result to the client side while displaying the same on the client side. According to the embodiment, the problem of identification counterfeiting is solved and sourceauthenticity of identification of the user is guaranteed.
Owner:TAIKANG LIFE INSURANCE CO LTD
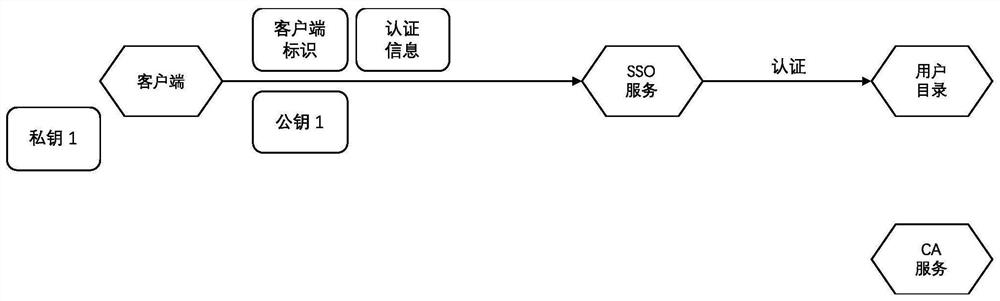
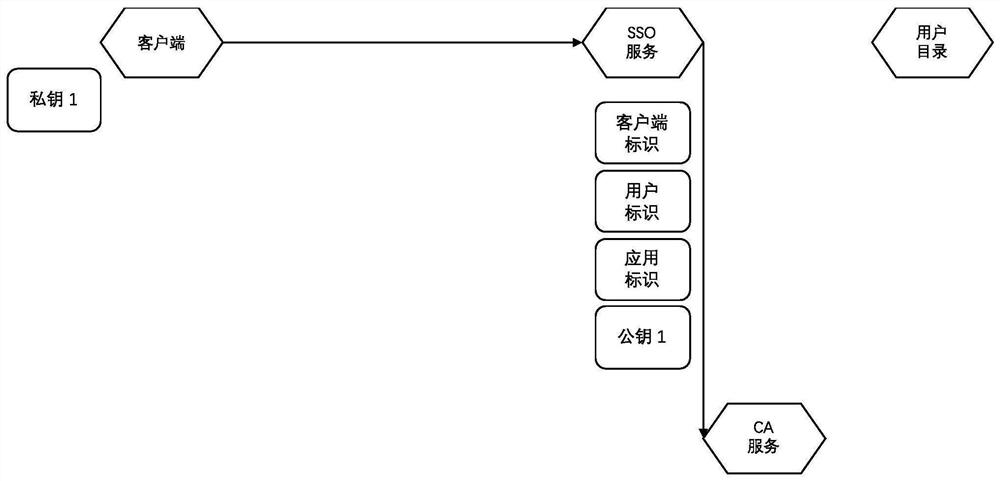
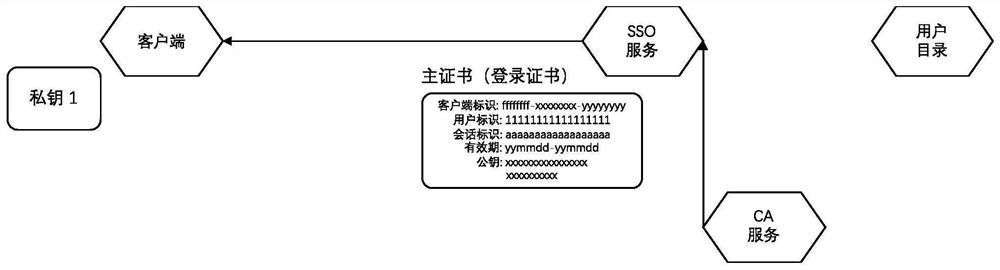
A Method of Enhancing the Security of Single Sign-on Using Digital Certificate
ActiveCN111447194BEnsure safetySolve the problem of counterfeitingUser identity/authority verificationTicketInternet privacy
The invention discloses a method for enhancing the security of single sign-on by using digital certificates, which uses public and private keys and digital certificates to replace one master ticket (login ticket) and N slave tickets (application tickets) in the process of single sign-on. Use digital certificates + asymmetric keys to complete the verification of whether the client has the right to hold certain types of information, to solve the problem that the application can verify whether the client has the right to hold these tickets when the single sign-on ticket is hijacked or obtained illegally. This problem makes the tickets in this solution non-replicable, which greatly improves the security of single sign-on login.
Owner:KOAL SOFTWARE CO LTD
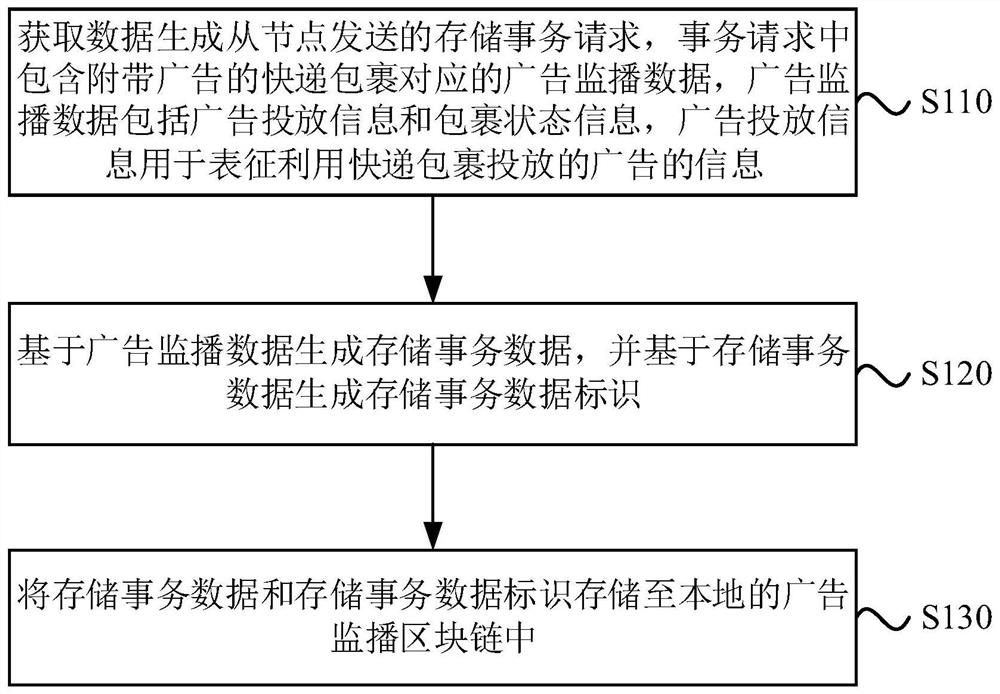
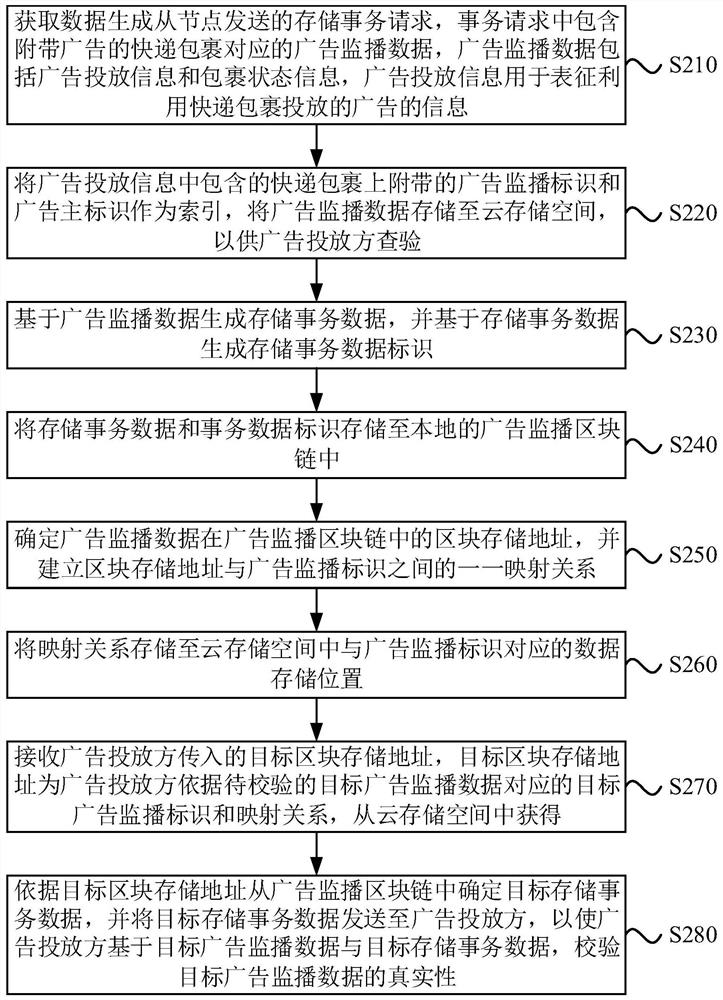
Advertisement monitoring method and device, equipment and storage medium
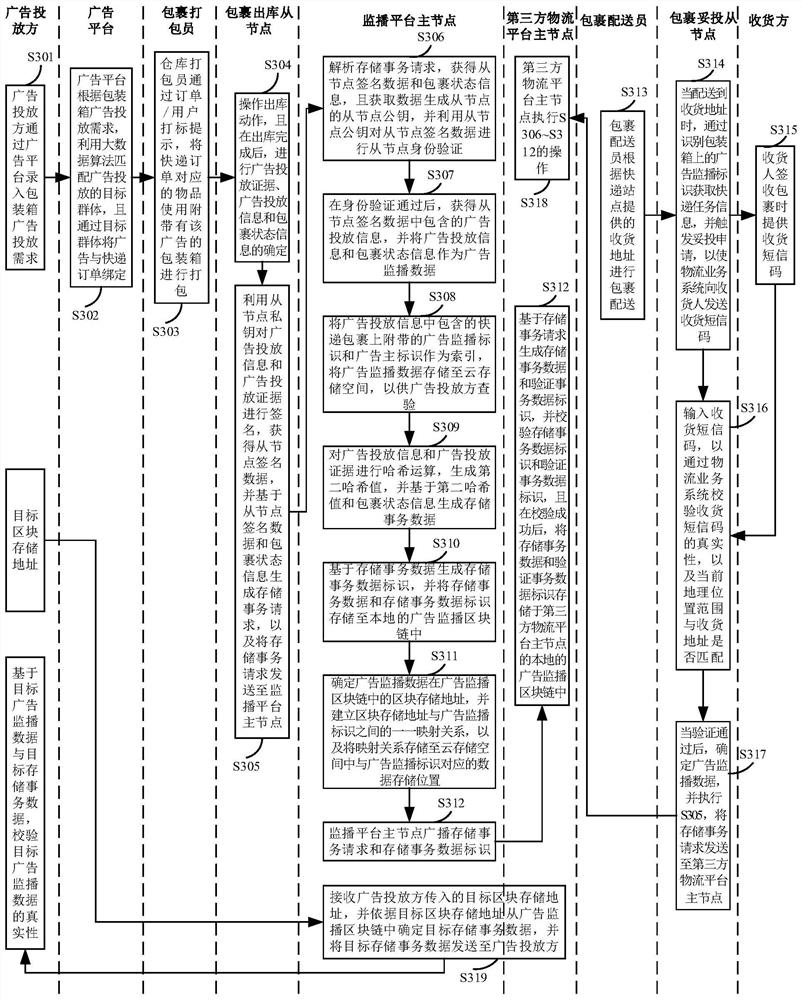
PendingCN113077278ASolve the problem of counterfeitingIncrease authenticityDigital data protectionMarketingData packTransaction data
The embodiment of the invention discloses an advertisement monitoring method and device, equipment and a storage medium. The method comprises the steps that a storage transaction request sent by a data generation slave node is collected, the transaction request comprises advertisement monitoring data corresponding to an express parcel with an advertisement, and the advertisement monitoring data comprises advertisement putting information and parcel state information; the advertisement putting information is used for representing information of an advertisement put by using the express parcel; generating storage transaction data based on the advertisement monitoring data, and generating a storage transaction data identifier based on the storage transaction data; and storing the storage transaction data and the storage transaction data identifier in a local advertisement monitoring block chain. According to the technical scheme, the advertisement monitoring data based on the express parcel is stored by utilizing the block chain, so that the authenticity of the advertisement monitoring data is enhanced by utilizing the non-tampering characteristic of the block chain technology.
Owner:BEIJING JINGDONG ZHENSHI INFORMATION TECH CO LTD
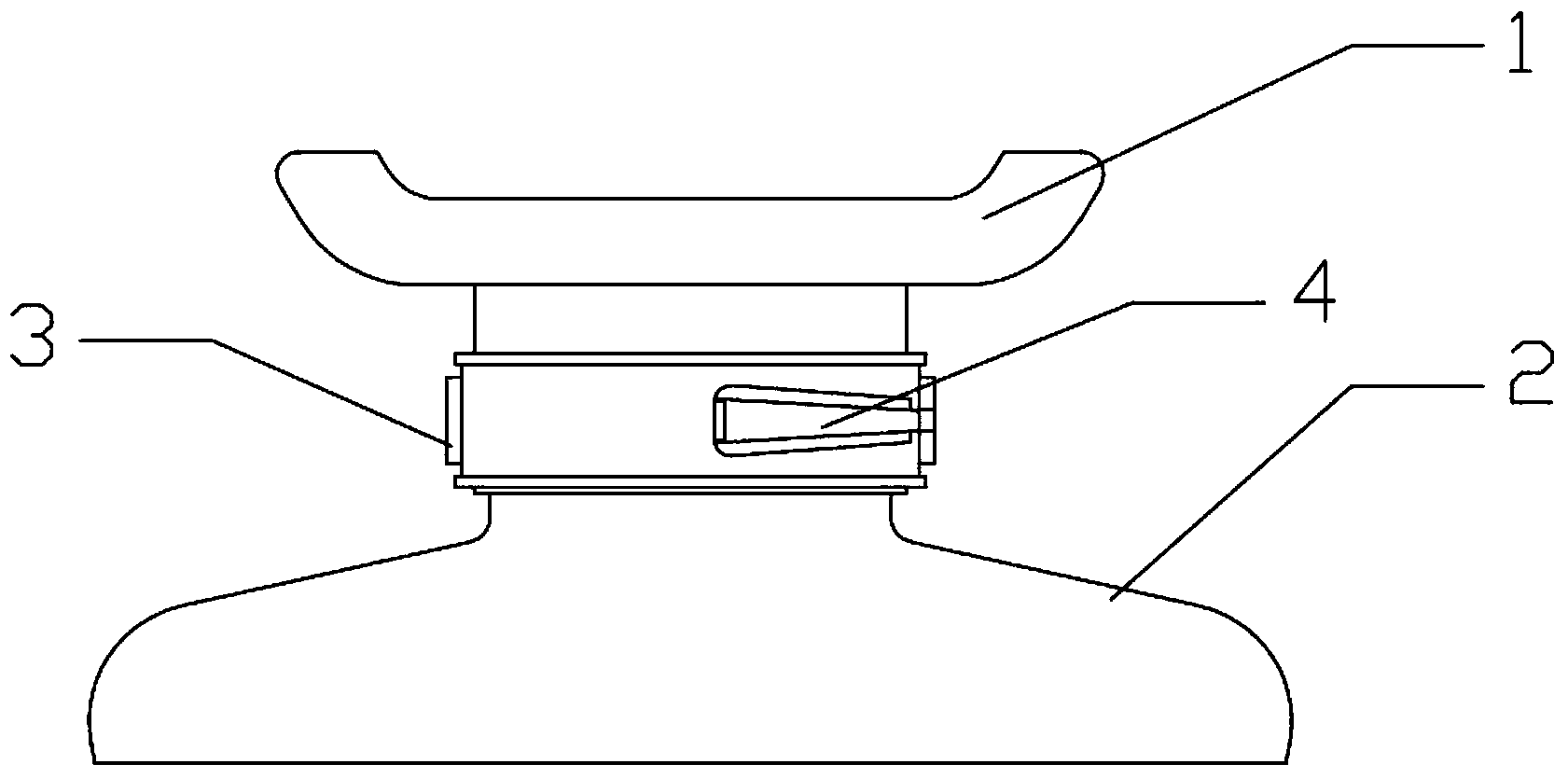
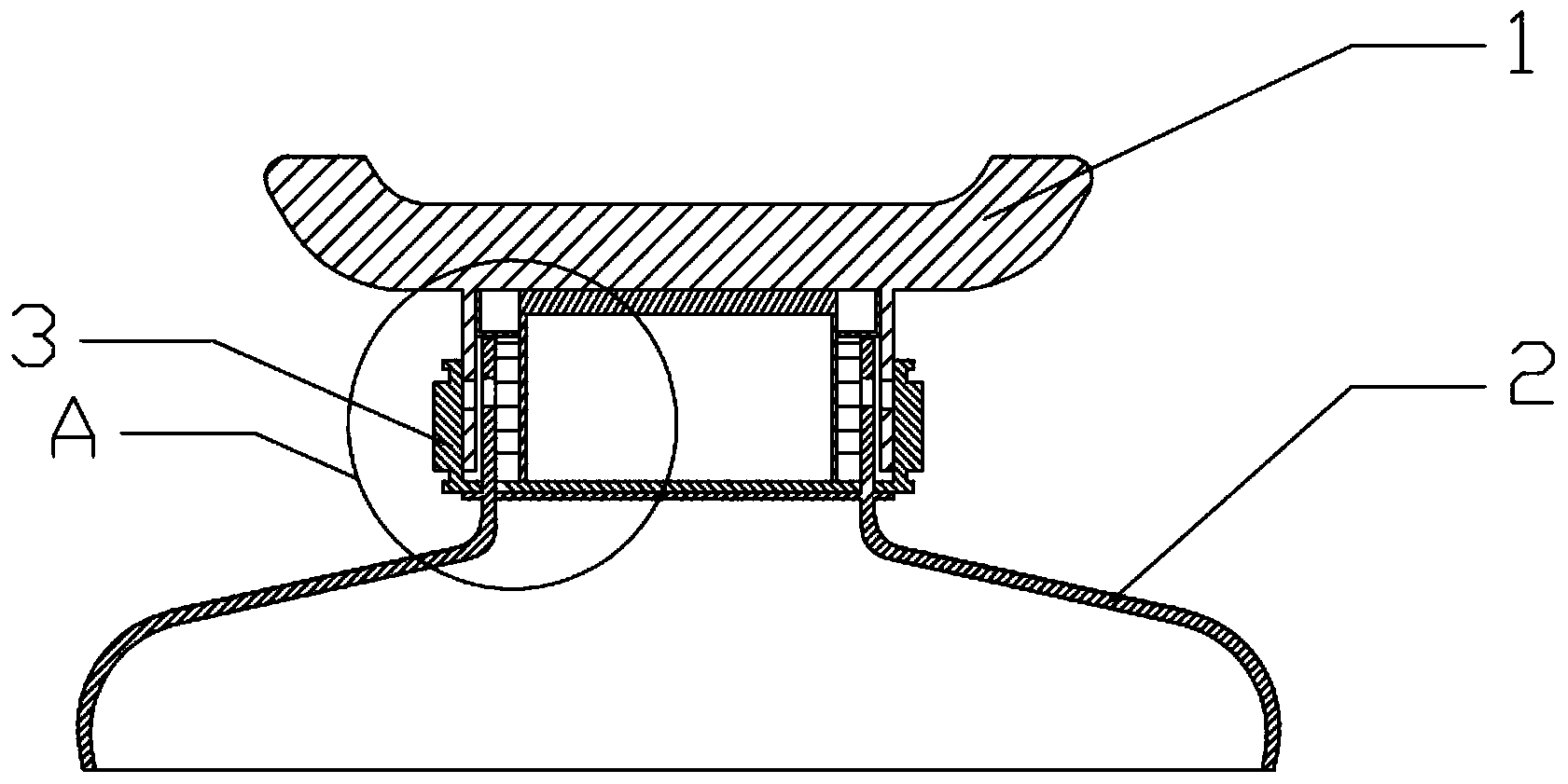
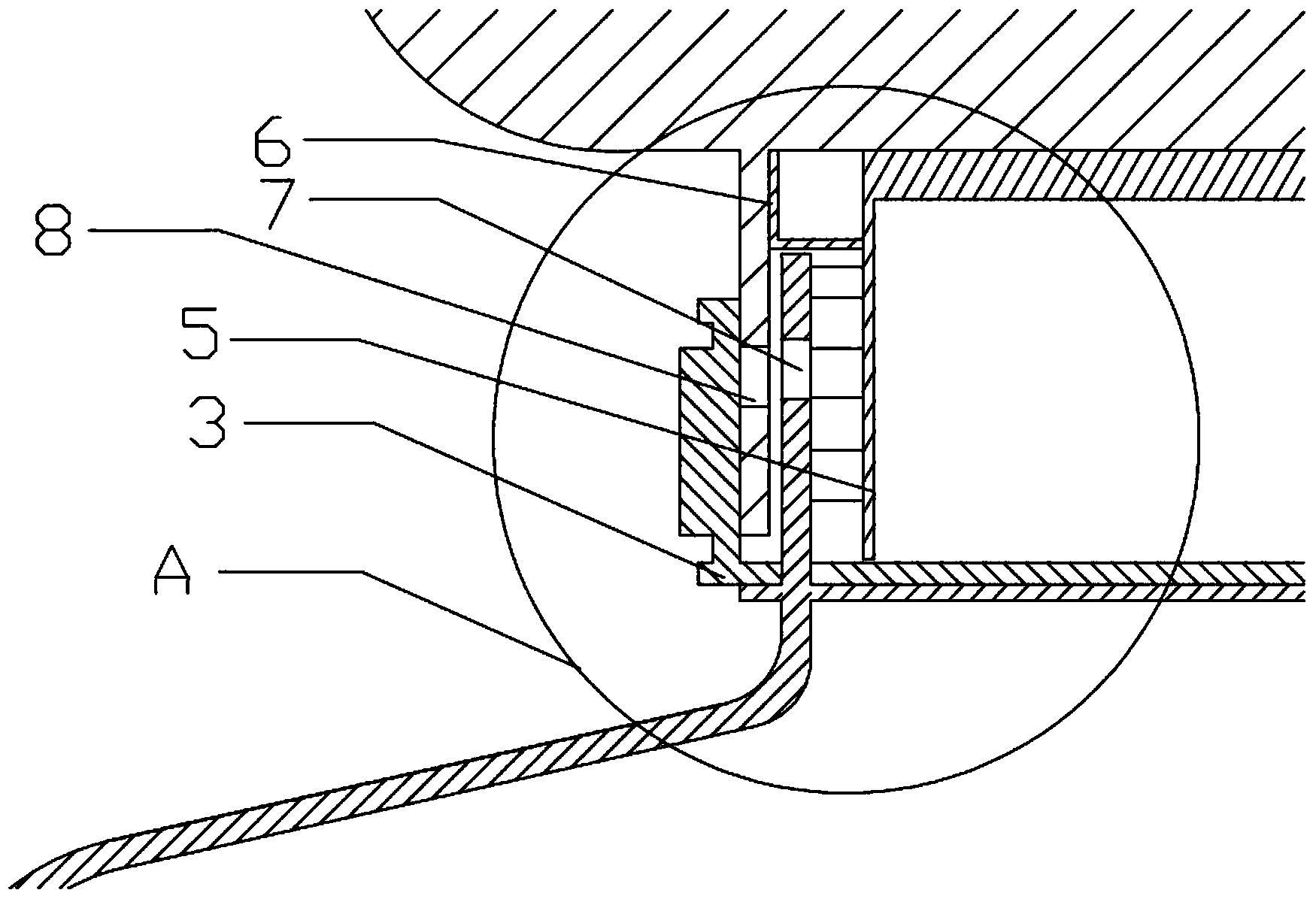
Anti-fake liquor bottle
ActiveCN103979199ADestructiveImprove damage effectClosures to prevent refillingEngineeringBottle cap
The invention provides an anti-fake liquor bottle. The anti-fake liquor bottle comprises a bottle mouth portion. A through hole penetrating through the inner wall and the outer wall of the bottle mouth portion is formed in the wall of a mouth of the bottle mouth portion. A plastic bottle plug is inserted into the bottle mouth portion. A sealing metal cap is arranged on the top of the plastic bottle plug. A tearing portion is arranged on the metal cap. The upper portion of the plastic bottle plug is covered with a ceramic bottle cap. A through hole penetrating through the inner wall and the outer wall of the ceramic bottle cap is formed in the wall of the ceramic bottle cap. The ceramic bottle cap is sleeved with a metal ring which is matched with the bottle cap in a tightly matching mode. A disposable anti-fake clamping ring is arranged on the outer wall of the metal ring. A plastic protective cover is arranged in the ceramic bottle cap. The plastic bottle plug is sleeved with a plastic plug sleeve. A horizontal protrusion is arranged on the outer wall of the plastic plunger sleeve. The horizontal protrusion and the plastic plug sleeve are concentric. A plastic inner cover is arranged in the metal cap arranged on the top of the plastic bottle plug. According to the anti-fake liquor bottle, opening needs five steps, the five-step anti-fake opening technology is adopted, and product faking is restrained to a certain extent.
Owner:赊店老酒股份有限公司
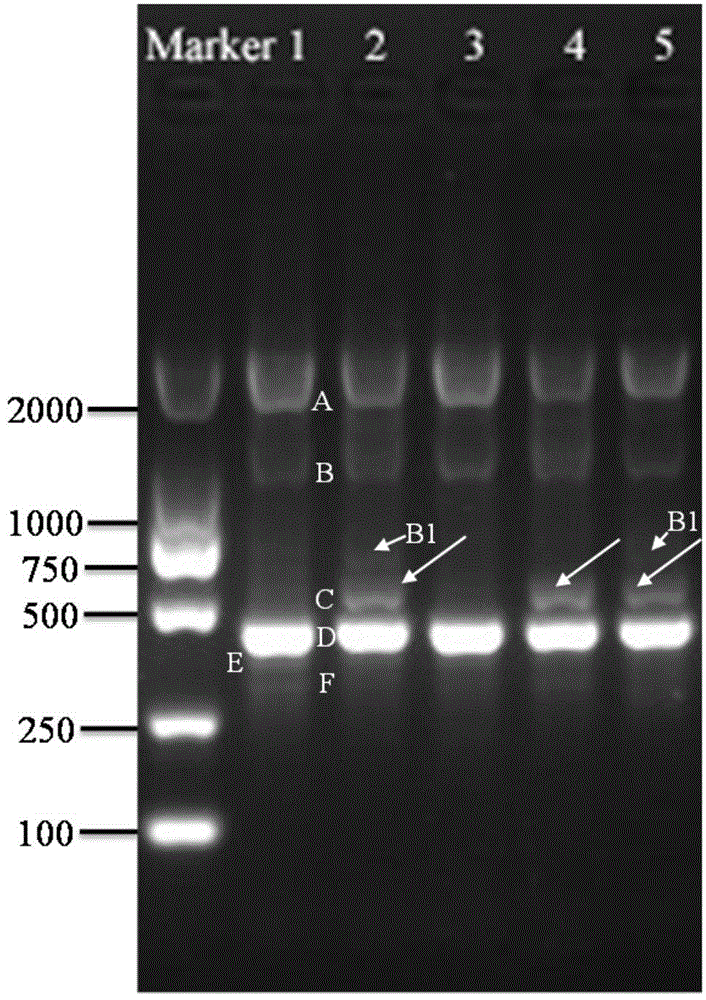
A special primer, method and kit for identifying Meishan pig or its meat products
InactiveCN104593519BSolve the problem of counterfeitingEasy to operateMicrobiological testing/measurementDNA/RNA fragmentationGenomic DNANucleotide sequencing
The invention discloses a special primer, a method and a kit for identifying a Meishan pig or a meat product thereof. A sequence of the special primer is as shown in SEQ ID NO.1. The method comprises the following steps: (1), extracting genomic DNA (deoxyribonucleic acid) of fresh meat and / or the meat product; (2), taking genomic DNA in the step (1) as a template, and performing a PCR (polymerase chain reaction) by utilizing the primer with the nucleotide sequence as shown in SEQ ID NO.1. The method further comprises the following steps: (3), creating an electrophoretogram of amplified fragments in the PCR in the step (2); or (4), according to the electrophoretogram in the step (3), identifying the fresh meat and / or the meat product of the Meishan pig. The special primer and the method are utilized to effectively solve an identification problem of a Meishan pig variety and can distinguish the Meishan pig variety from other pig meat varieties or beef and mutton. The identification method is simple to carry out and accurate in result.
Owner:SHANGHAI VETERINARY RES INST CHINESE ACAD OF AGRI SCI +2
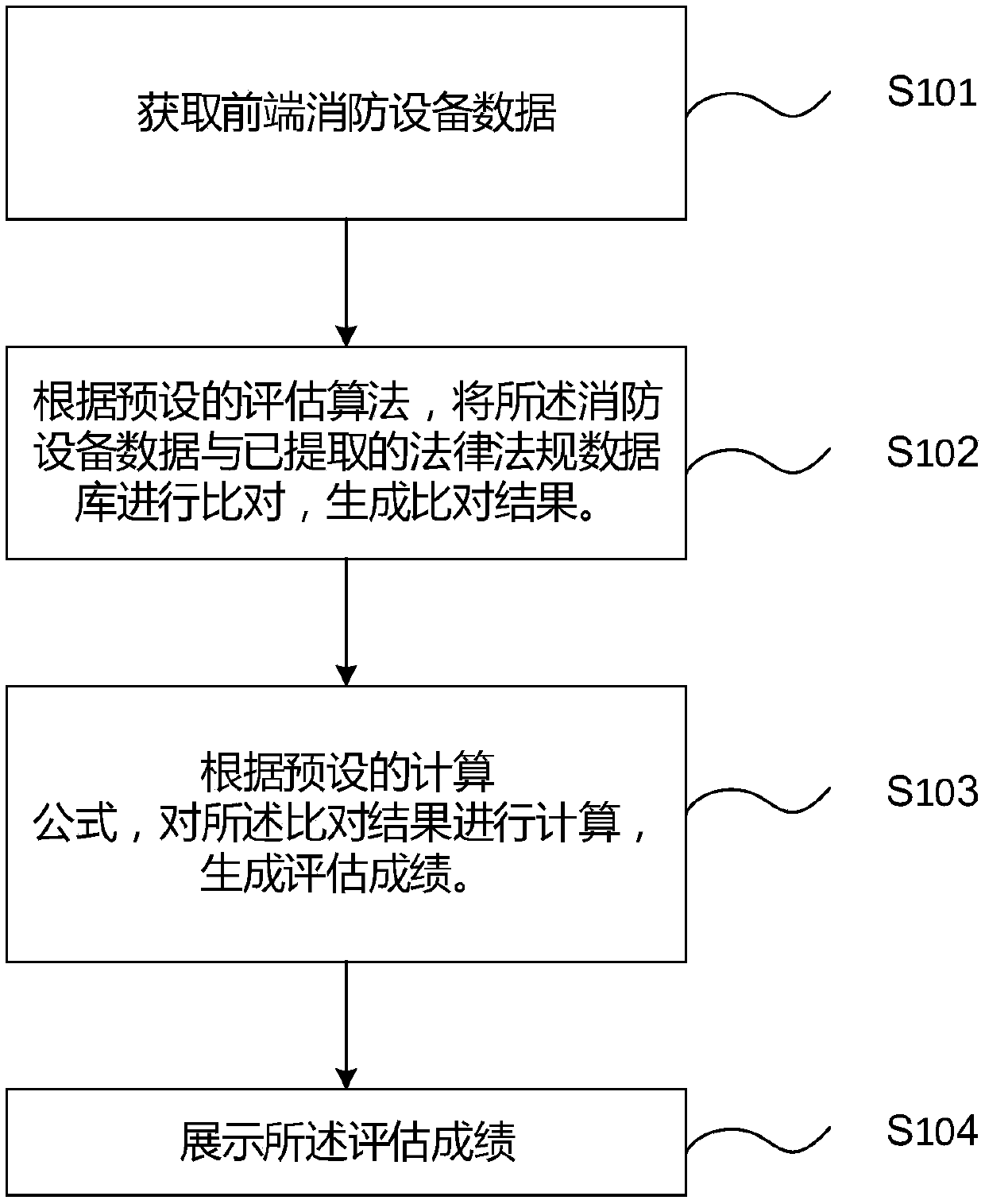
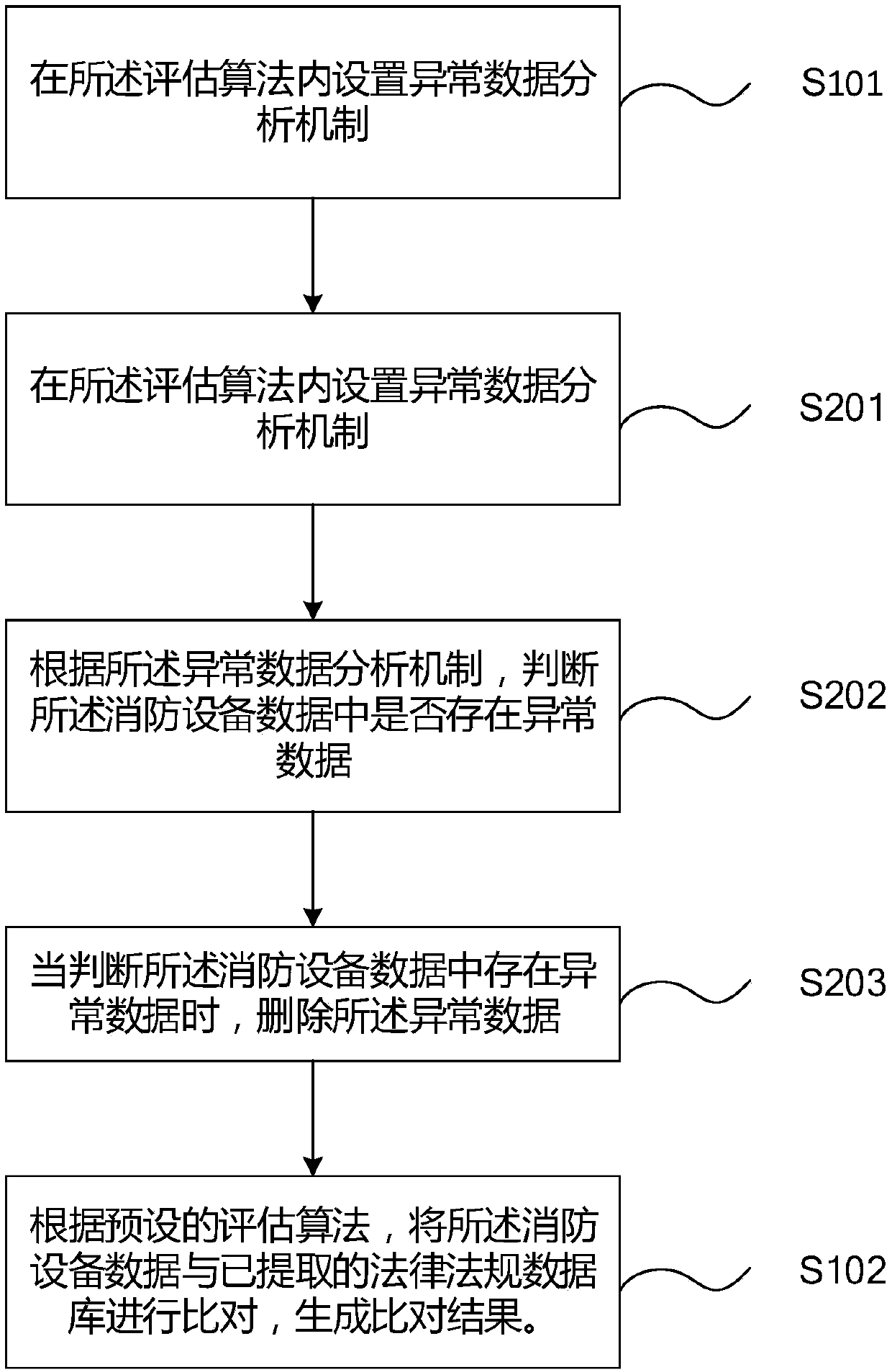
Fire safety assessment method and device based on Internet of Things, computer equipment and storage medium
PendingCN110728414ASolve the problem of counterfeitingMaster the status of fire fighting equipmentResourcesThe InternetFire safety
The invention is applicable to the field of the Internet of Things, and provides a fire safety assessment method and device based on Internet of Things, computer equipment and a storage medium, beingapplied to an Internet of Things terminal. The fire safety assessment method comprises the following steps: acquiring front-end fire-fighting equipment data; according to a preset evaluation algorithm, comparing the fire-fighting equipment data with an extracted law and regulation database to generate a comparison result; calculating the comparison result according to a preset calculation formulato generate an evaluation score; and displaying the assessment score. According to the embodiment of the invention, the unit fire safety is evaluated and analyzed through the fire safety evaluation method based on the Internet of Things without depending on human sensory judgment, so that the unit fire safety condition is reflected more truly, and the counterfeiting problem is avoided, and a firesupervision department masters the real state of the unit fire safety and formulates emergency prevention measures in time; and meanwhile, relevant fire-fighting responsible persons can master the fire-fighting equipment state, the personnel workload, the working state and the like of the unit in real time, thus facilitating fire-fighting safety management.
Owner:烟台淼盾物联技术有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com