Patents
Literature
30results about How to "Solve the problem of tampering" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
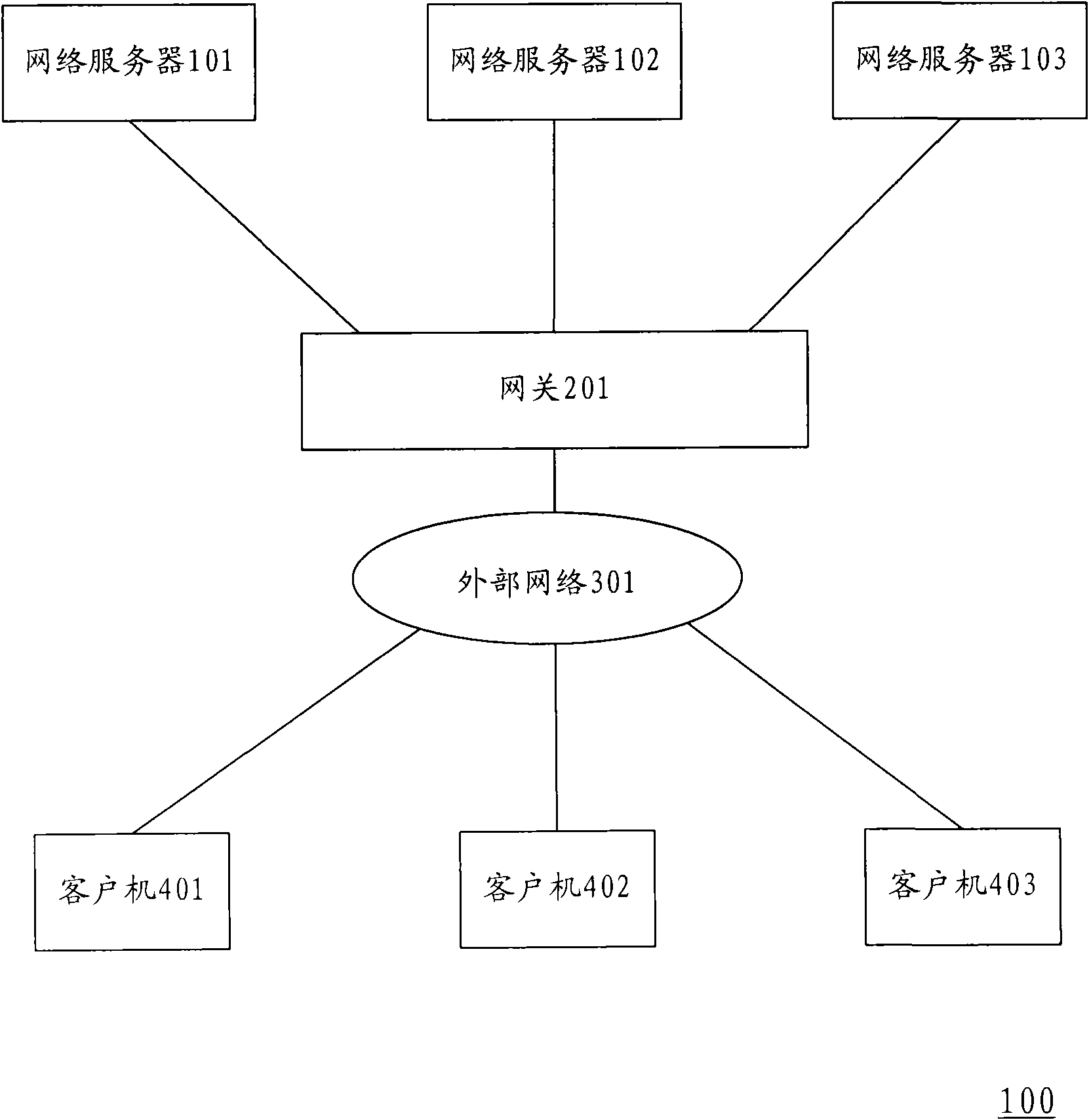
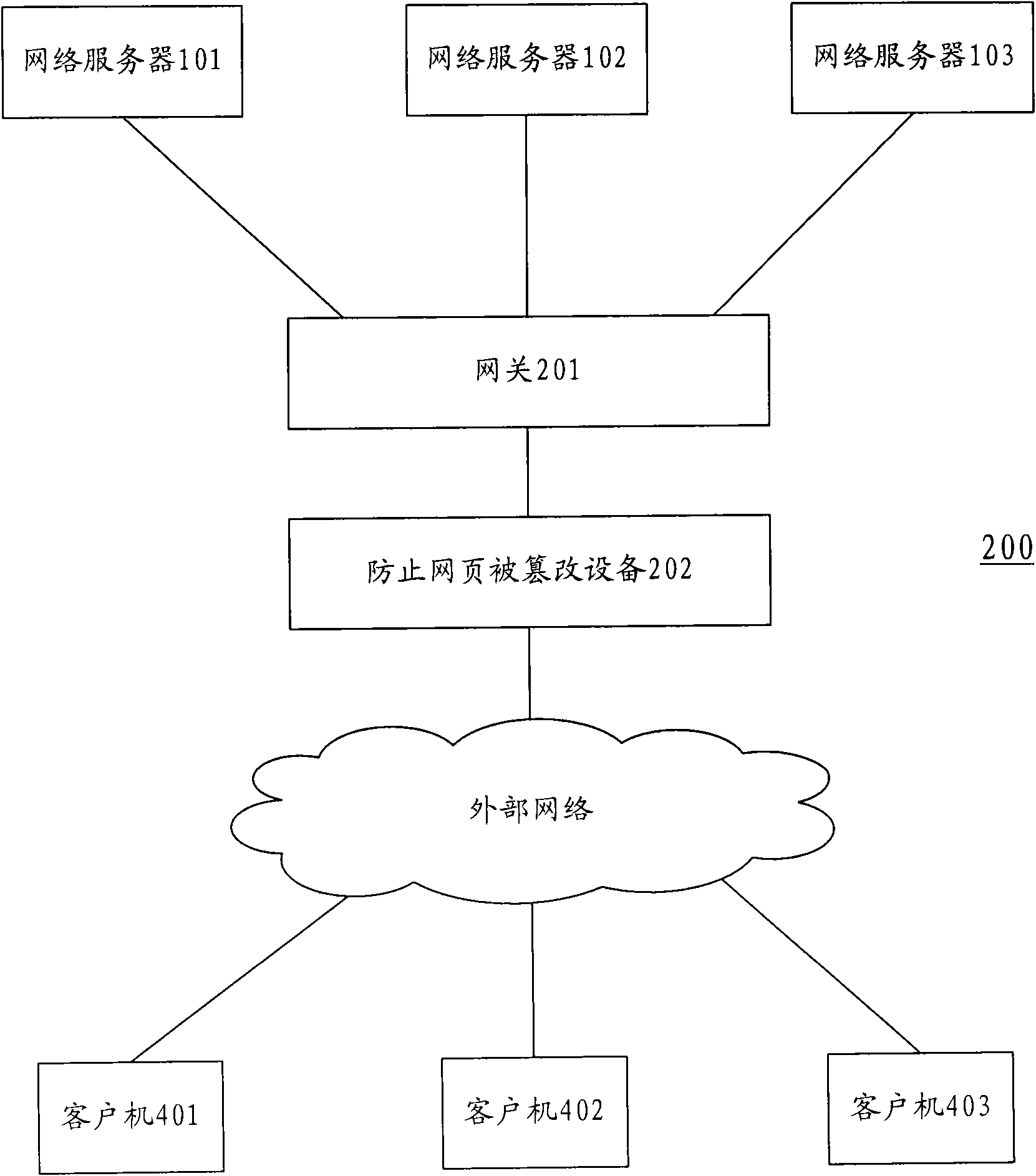
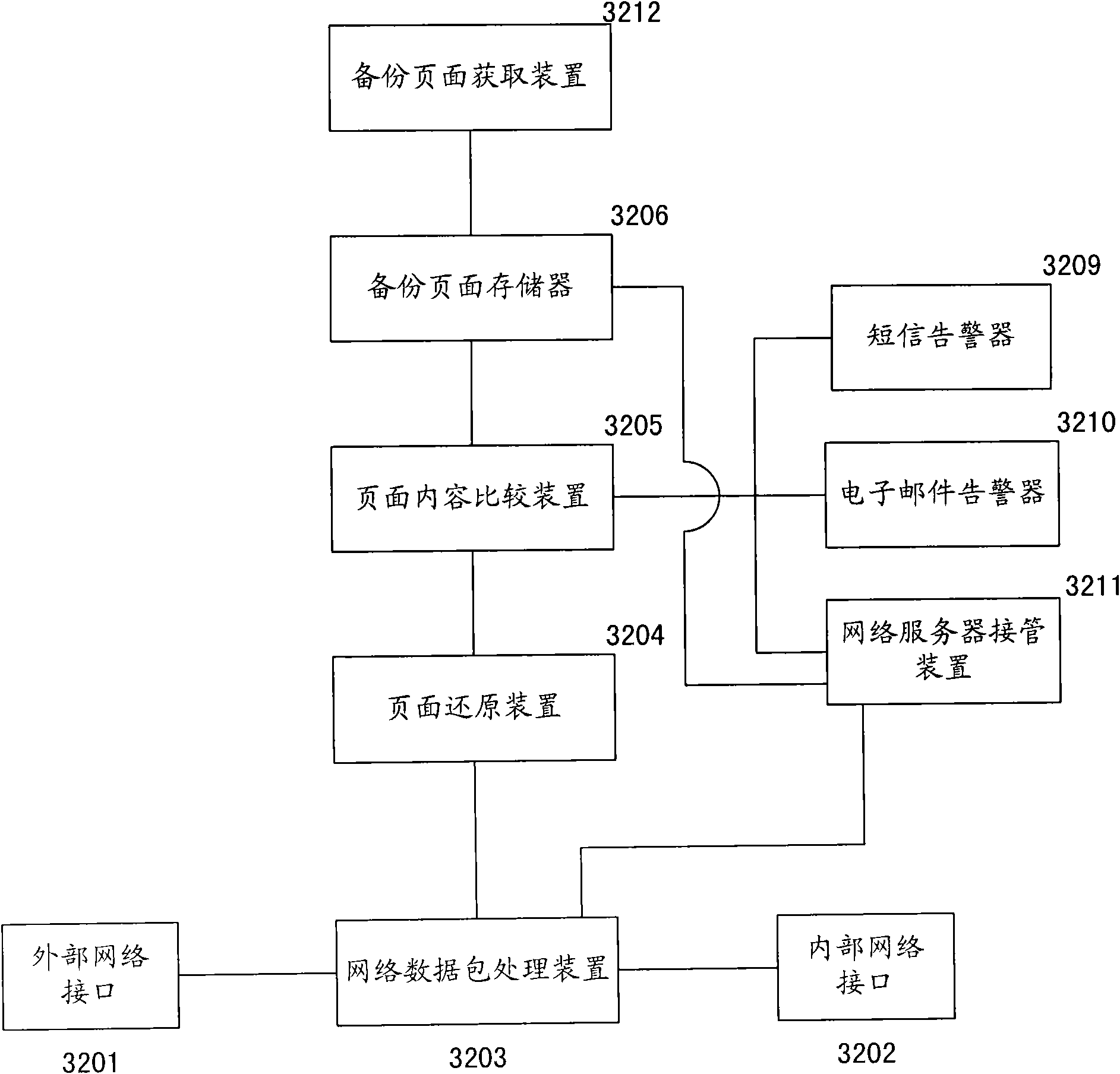
Device, method and system for preventing web page from being distorted
InactiveCN101626368APrevent secondary tamperingPrevent tamperingDigital data protectionData switching networksNetwork packetNetwork data
The invention discloses a device for preventing a web page from being distorted, wherein in the device for preventing the web page from being distorted, a network data pack processing device intercepts a network data pack returned from a network server, a page restoring device receives the network data pack intercepted by the network data pack processing device and restores the network data pack into the web page content, a page content comparing unit compares the web page content restored by the page restoring device with a pre-backup web page content corresponding to the restored web page content to determine whether the restored web page content is distorted and notifies a network server takeover device about the information on the distortion of the web page when the restored web page content is determined to be distorted, and when receiving the information on the distortion of the web page, the network server takeover device returns the pre-backup web page content corresponding to the restored web page content to external network users. The invention also provides a method used in the device for preventing the web page from being distorted, and a system using the device for preventing the web page from being distorted.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD
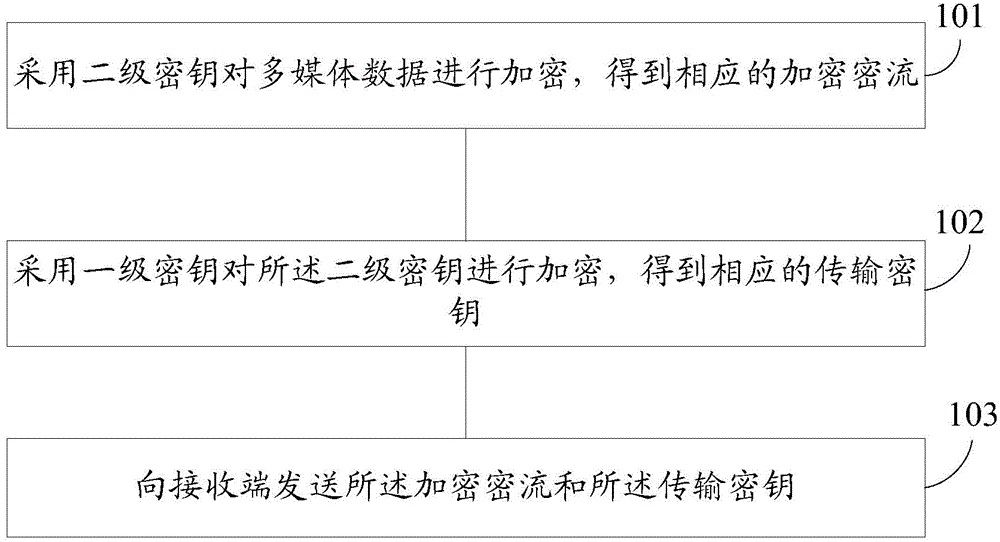
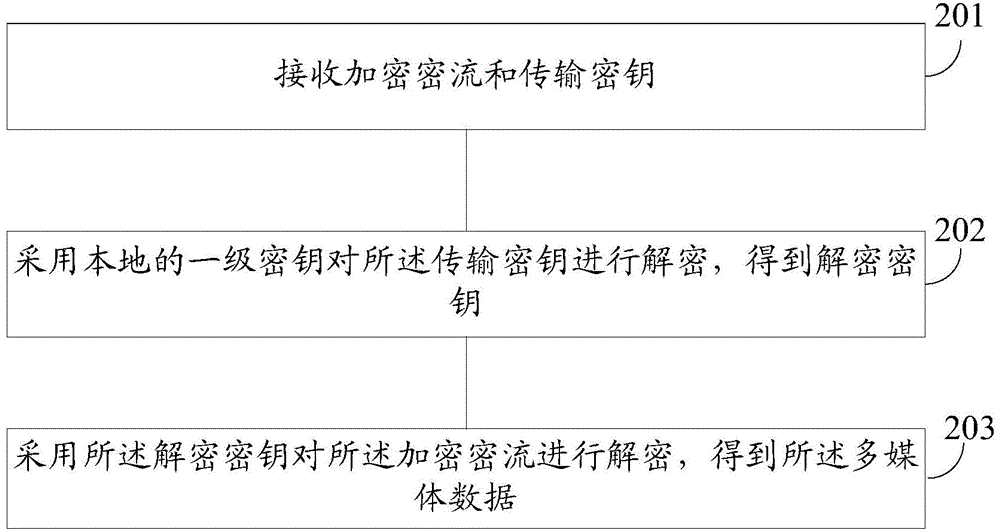
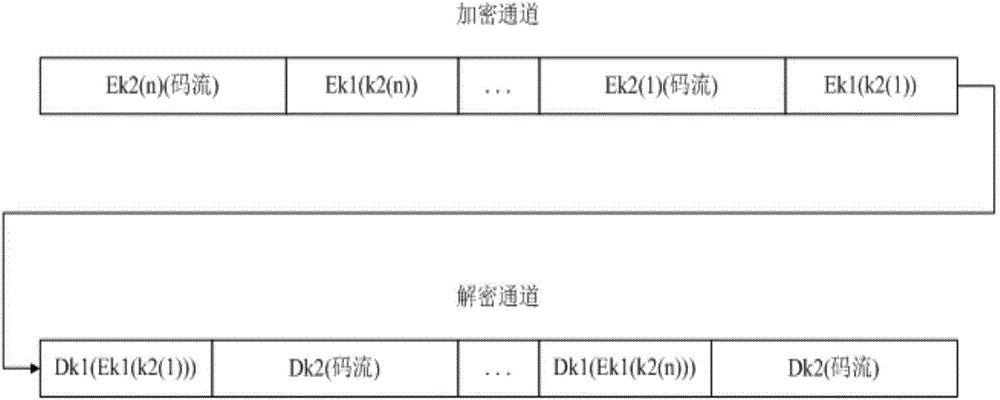
Multimedia data encryption and decryption method and device
InactiveCN106161383AEnsure safetyImprove securityEncryption apparatus with shift registers/memoriesComputer hardwareMultimedia data transmission
The invention provides a multimedia data encryption and decryption method and device. The encryption method specifically includes adopting a second level key for encrypting multimedia data and obtaining corresponding encryption key flow; adopting a first level key for encrypting a second level key and obtaining a corresponding transmission key. Since the encryption key flow and the transmission key are transmitted in the network and the first level key as a decryption key is not transmitted in the network, safety of the multimedia data in the network is ensured and a problem that the multimedia data is stolen or tampered is solved. Besides, the invention adopts the second level key for encrypting the multimedia data and adopts the first level key for encrypting the second level key, difficulty of decoding the encryption key flow is increased, thus the multimedia data transmission safety is further improved.
Owner:VISIONVERA INFORMATION TECH CO LTD
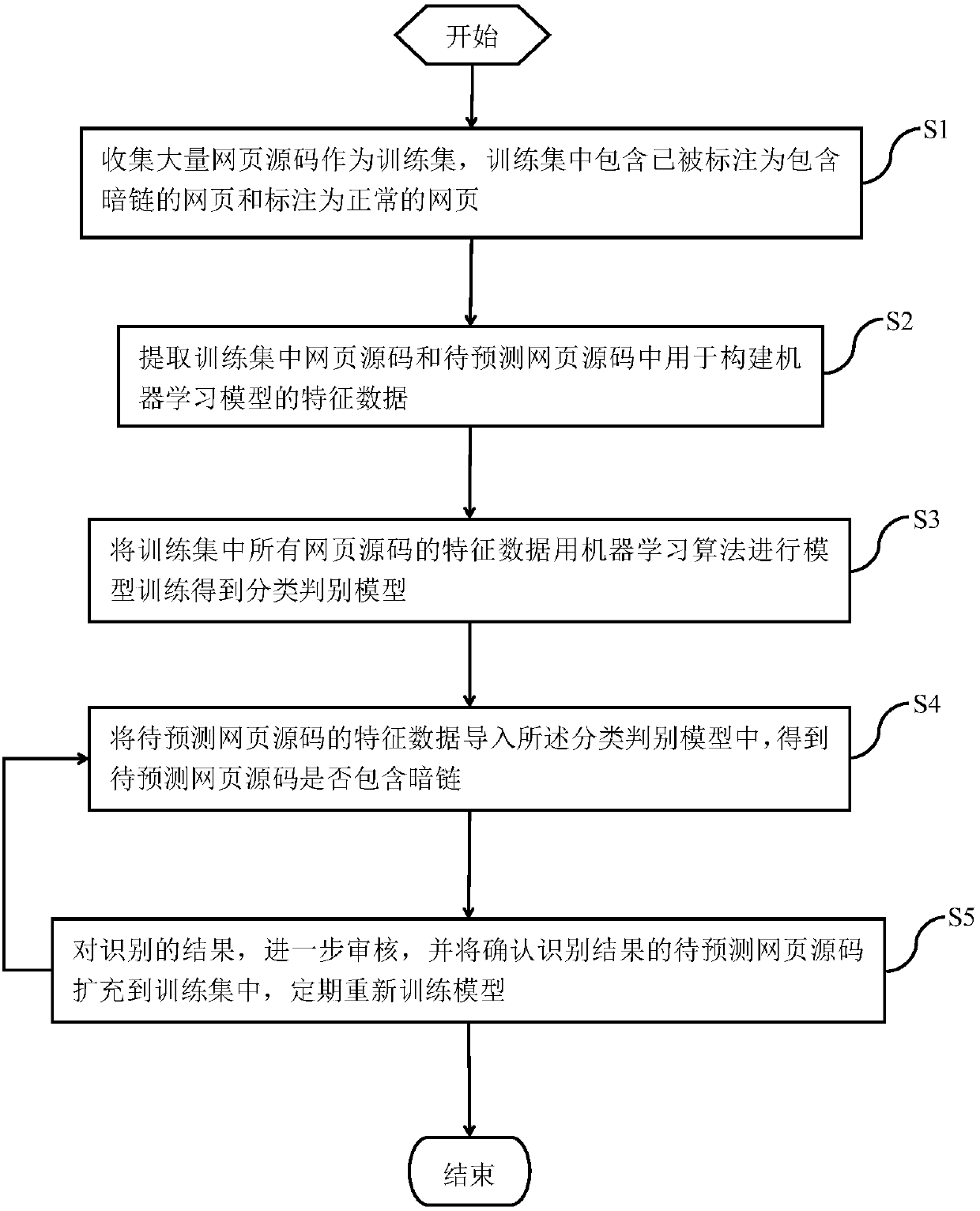
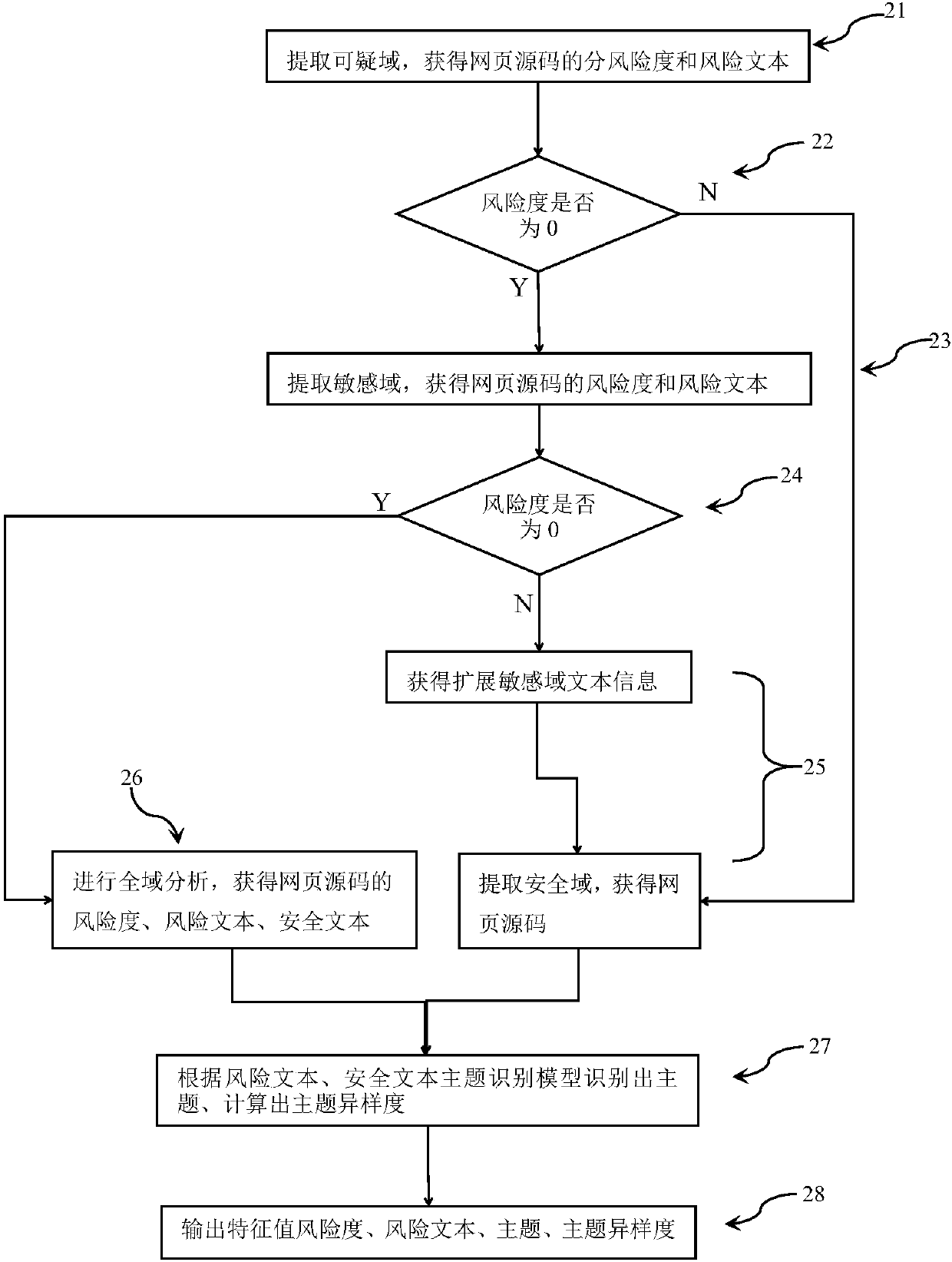
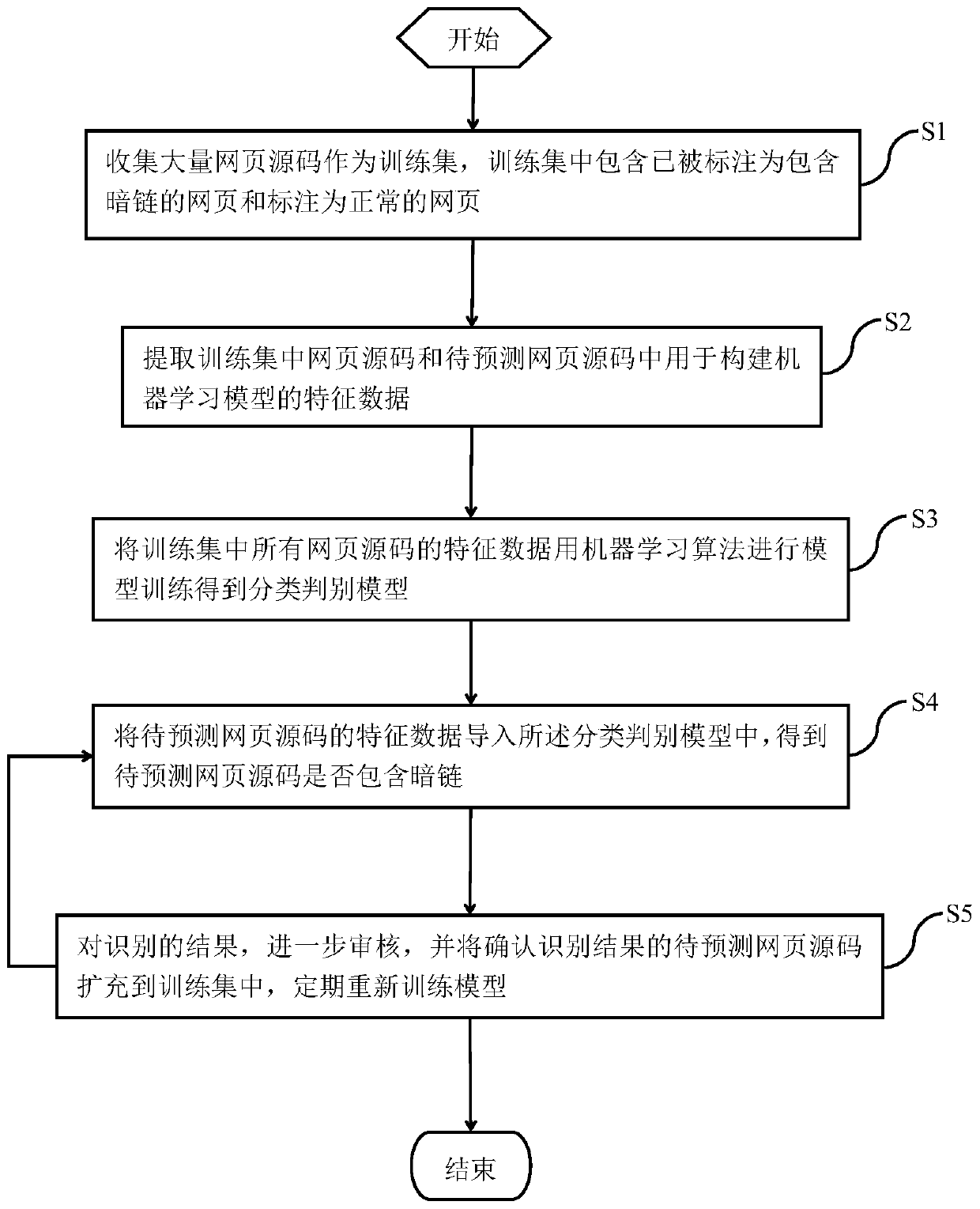
Method for establishing machine learning model to check webpage hidden links through domain identification and theme identification
ActiveCN107566391AImprove the problem of poor recognition effectSolve the problem of tamperingComputing modelsTransmissionFeature extractionDomain analysis
The invention provides a method for establishing a machine learning model to check webpage hidden links through domain identification and theme identification. The method comprises the steps of collecting a great number of webpage source codes which are marked as the webpage source codes comprising hidden links and the webpage source codes marked as the normal webpage source codes, and forming a training set based on the webpage source codes; extracting a risk text, risk degree, theme difference degree, a theme, a risk text vector, a risk text abnormal probability and the risk text length in each web page source code through suspicious domain identification, sensitive domain identification, secure domain identification, all-domain analysis and theme identification; carrying out model training on characteristic data of all web page source codes in the training set through utilization of a machine learning algorithm, thereby obtaining a classification distinguishing model; and importingthe characteristic data of to-be-predicted web page source codes into the classification distinguishing model, thereby obtaining a result of whether the to-be-predicted web page source codes comprisethe hidden links or not. According to the method, the highly mixed hidden link code identification effect is good, the feature extraction is relatively complete and the problem that a traditional method cannot accurately distinguish the hidden links and page tampering can be solved well.
Owner:上海斗象信息科技有限公司
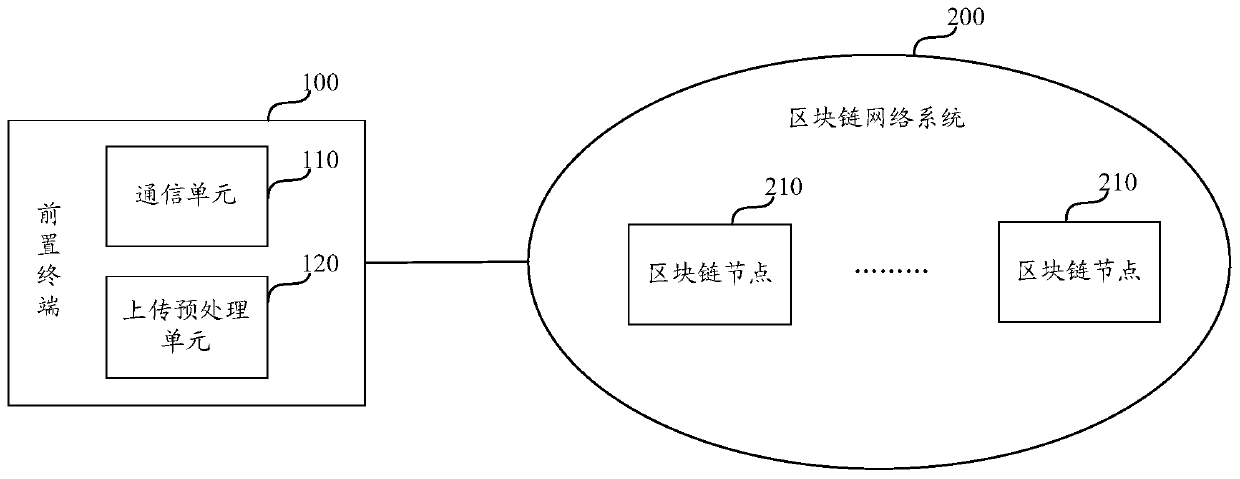
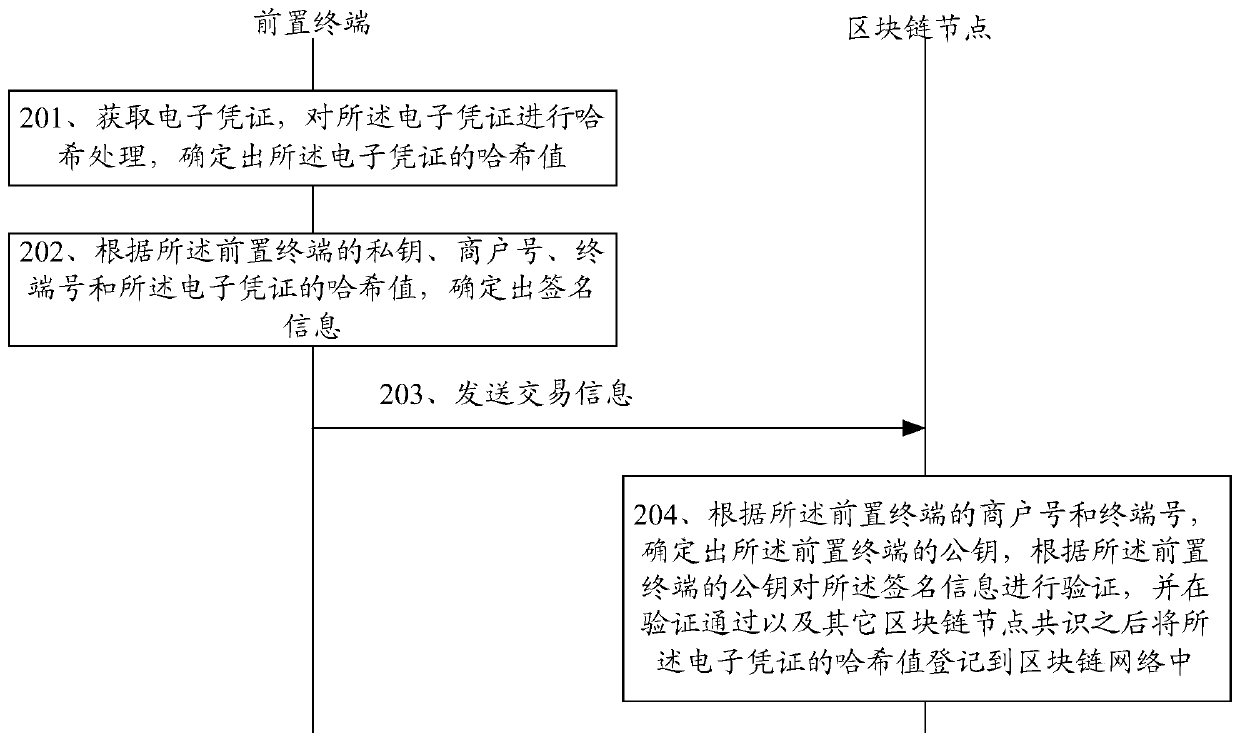
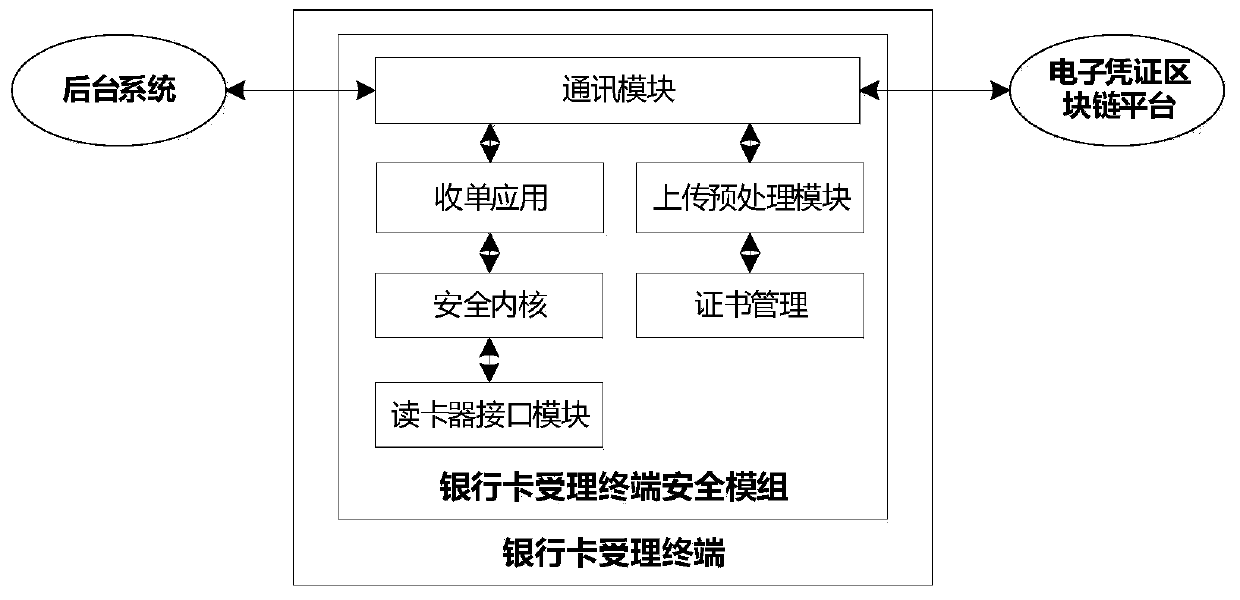
An electronic certificate uploading method and device
ActiveCN109741056ASolve the problem of counterfeitingSolve the problem of tamperingFinancePayment protocolsComputer terminalChain network
The invention discloses a method and a device for uploading an electronic certificate. The method comprises the steps that a front-end terminal obtains an electronic certificate, carrying out Hash processing on the electronic certificate; determining a hash value of the electronic certificate; and according to the private key of the front-end terminal, the merchant number, the terminal number andthe hash value of the electronic certificate, determining signature information, and uploading the merchant number and the terminal number of the front-end terminal, the hash value of the electronic certificate and the signature information to the blockchain node, so that the blockchain node verifies the signature information and then registers the signature information in the blockchain network.The front-end terminal directly uploads the electronic certificate to the block chain network after processing the electronic certificate, so that the problem that in the prior art, when the front-endterminal uploads the electronic certificate to the block chain through the background terminal, the electronic certificate is tampered is solved.
Owner:CHINA UNIONPAY
Covert communication method, device and system based on blockchain and encryption technology
PendingCN112600665AAddress easily identifiable issuesFix the leakEncryption apparatus with shift registers/memoriesCovert communicationEngineering
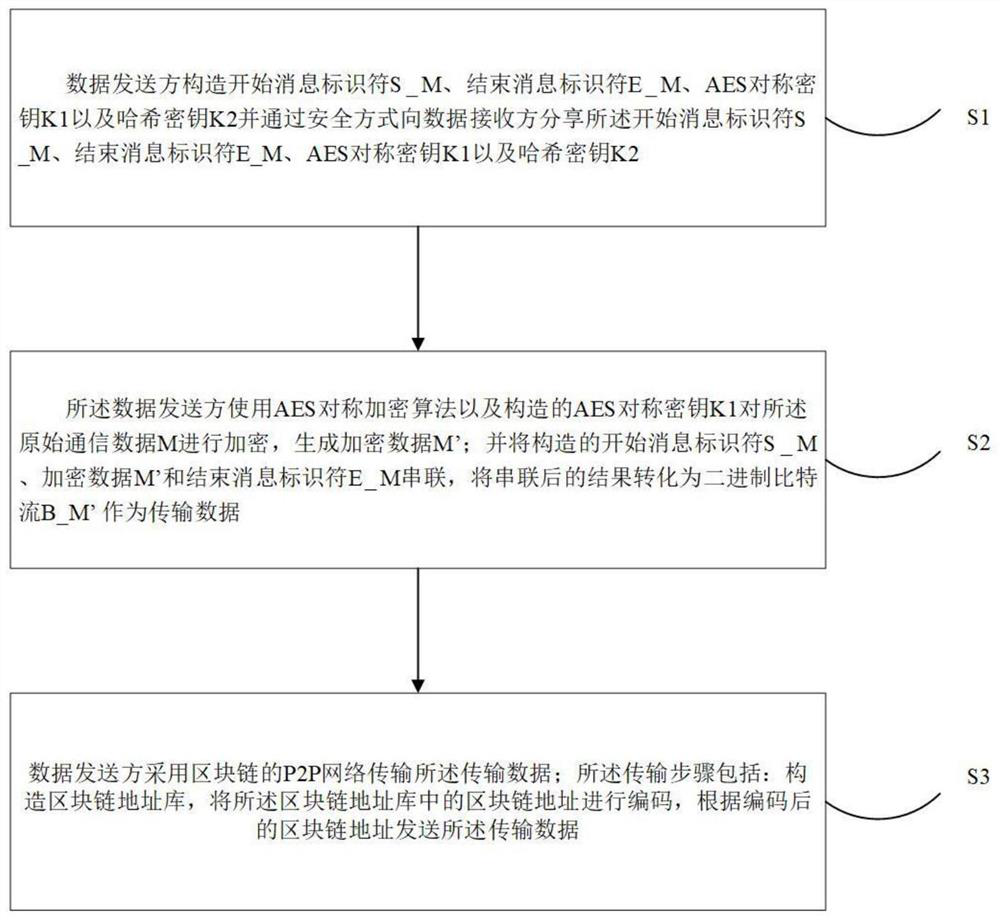
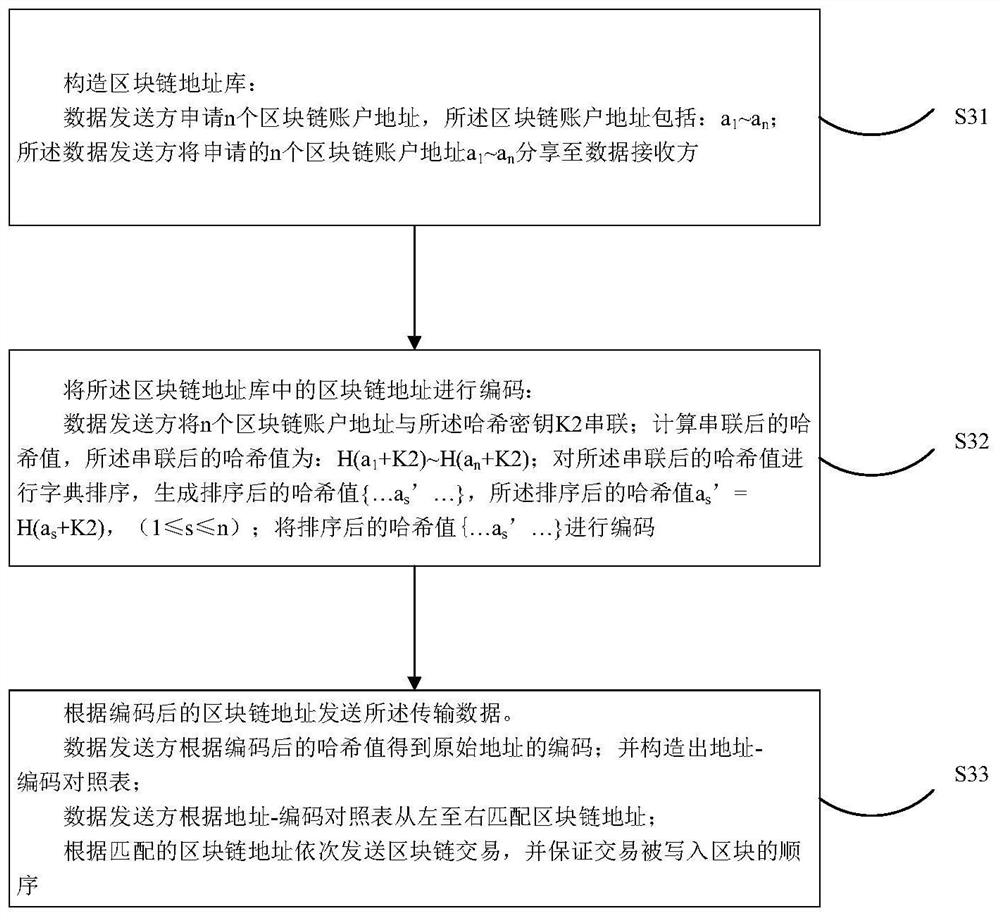
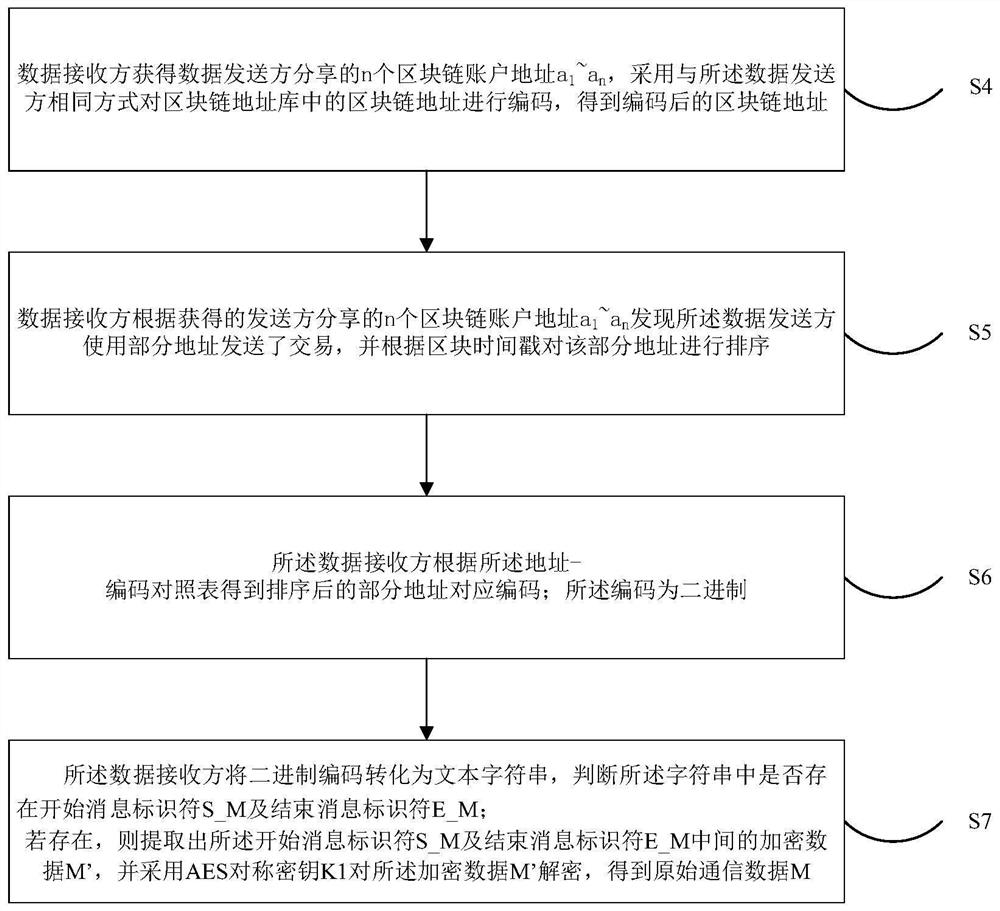
The invention discloses a covert communication method, device and system based on a blockchain and an encryption technology, and the method comprises the steps that a data sender carries out the preprocessing of original communication data M through employing the symmetric encryption technology, obtains encrypted data M', and converts the encrypted data M' into a binary bit stream B_M'as transmission data; the data sender transmits the transmission data by adopting a P2P network of a block chain; the transmission step comprises: constructing a block chain address library, encoding a block chain address in the block chain address library, and sending the transmission data according to the encoded block chain address; and the data receiver receives and extracts the transmission data, converts the transmission data into encrypted data M', and decrypts the encrypted data M' to obtain original communication data M. According to the technical scheme, the problems that communication behaviorsand communication contents are easy to identify, information leakage is caused due to the fact that communication data is transmitted in a plaintext form, the communication data is easy to hijack andtamper, and a communication tool is centralized are solved.
Owner:南京通付盾区块链科技有限公司 +1
Permission management method and device
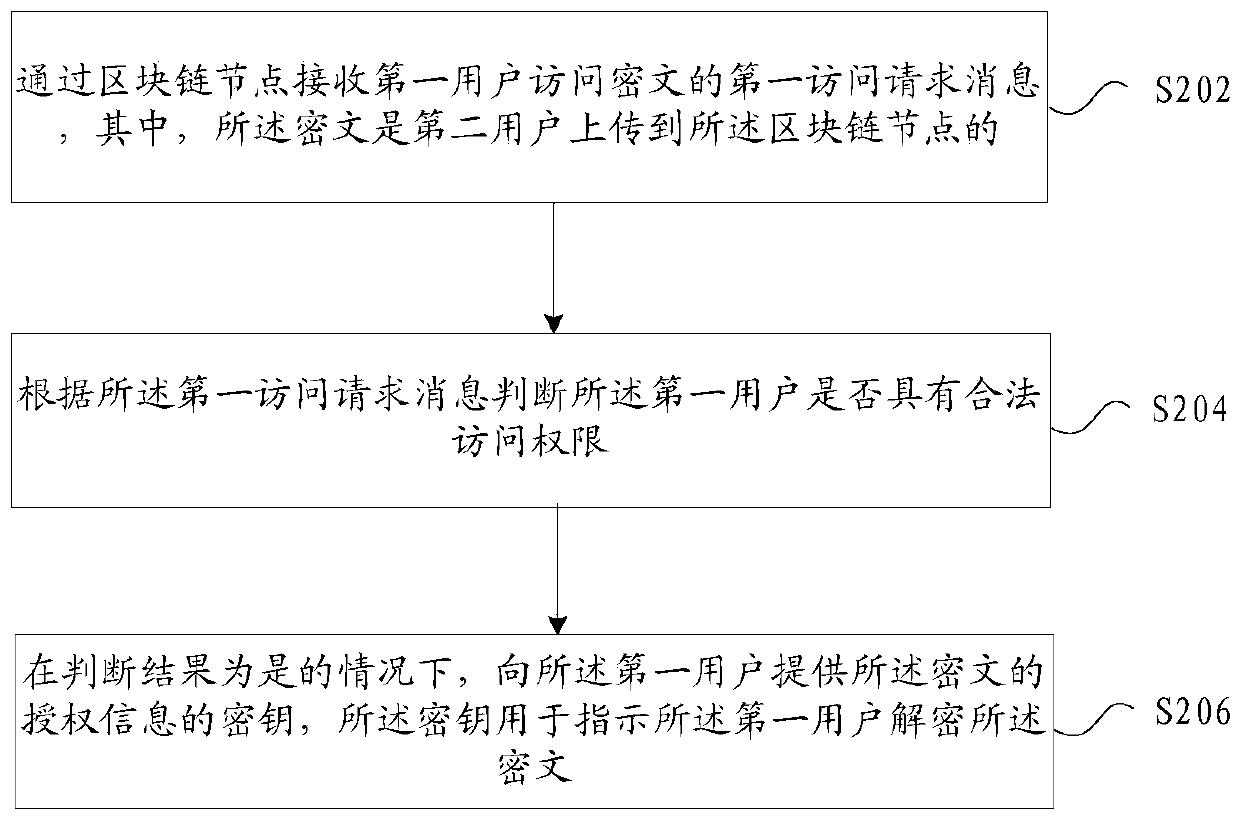
InactiveCN109889508ASolve any attackSolve the problem of tamperingTransmissionCiphertextRights management
The invention provides a permission management method and device, and the method comprises the steps: receiving a first access request message of a first user for accessing a ciphertext through a blockchain node, the ciphertext being uploaded to the blockchain node by a second user; judging whether the first user has legal access authority or not according to the first access request message; if the judgment result is yes, executing the step 2; and providing a secret key of the authorization information of the ciphertext to the first user, wherein the secret key is used for indicating the first user to decrypt the ciphertext, so that the problem that in the prior art, the authority of managing and accessing the special file through the central server is attacked or tampered by any person can be solved, the access authority is managed through the block chain, and the risk of being attacked or tampered is reduced.
Owner:北京融链科技有限公司
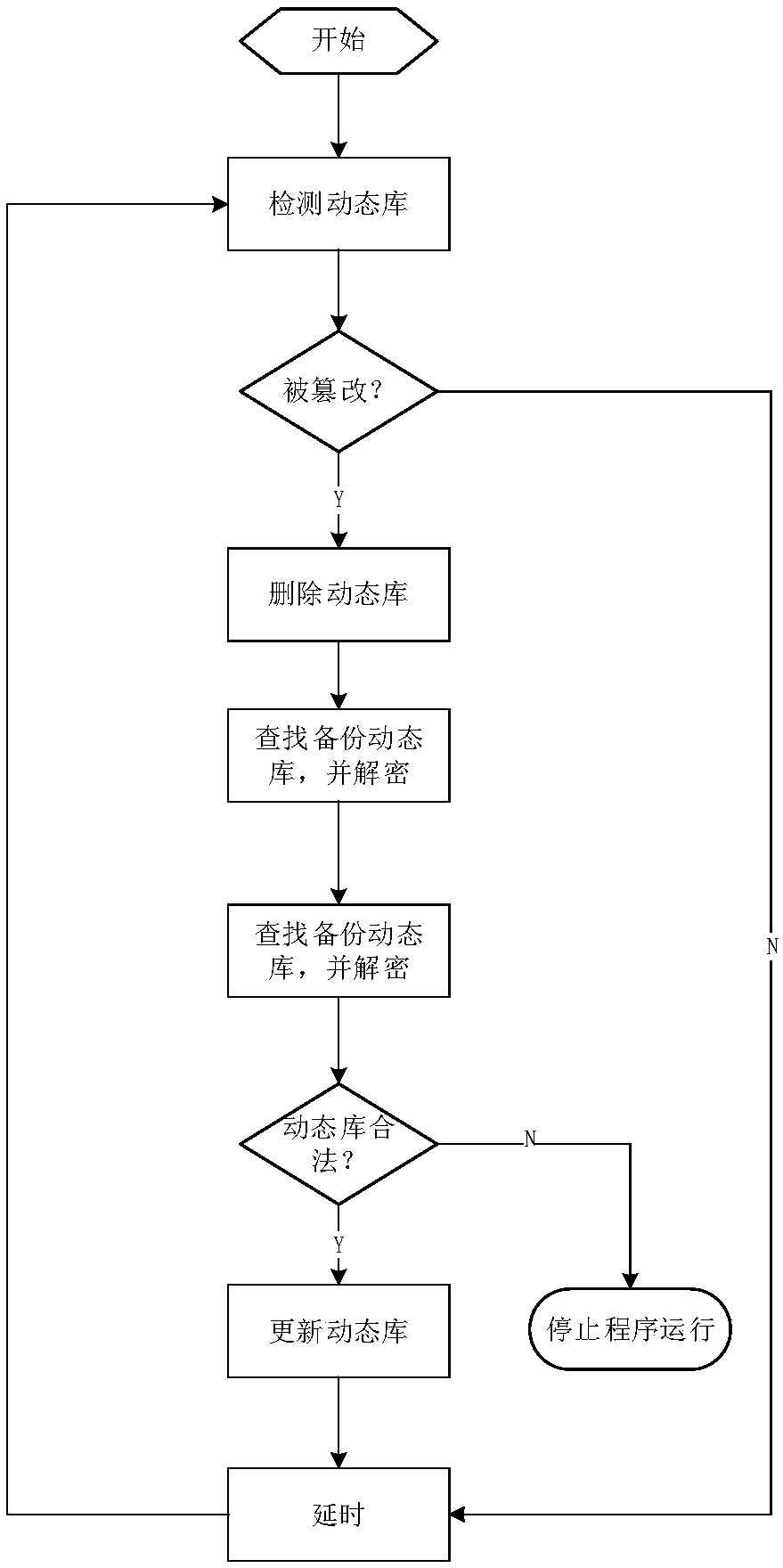
Tamper-proofing method and device for dynamic library
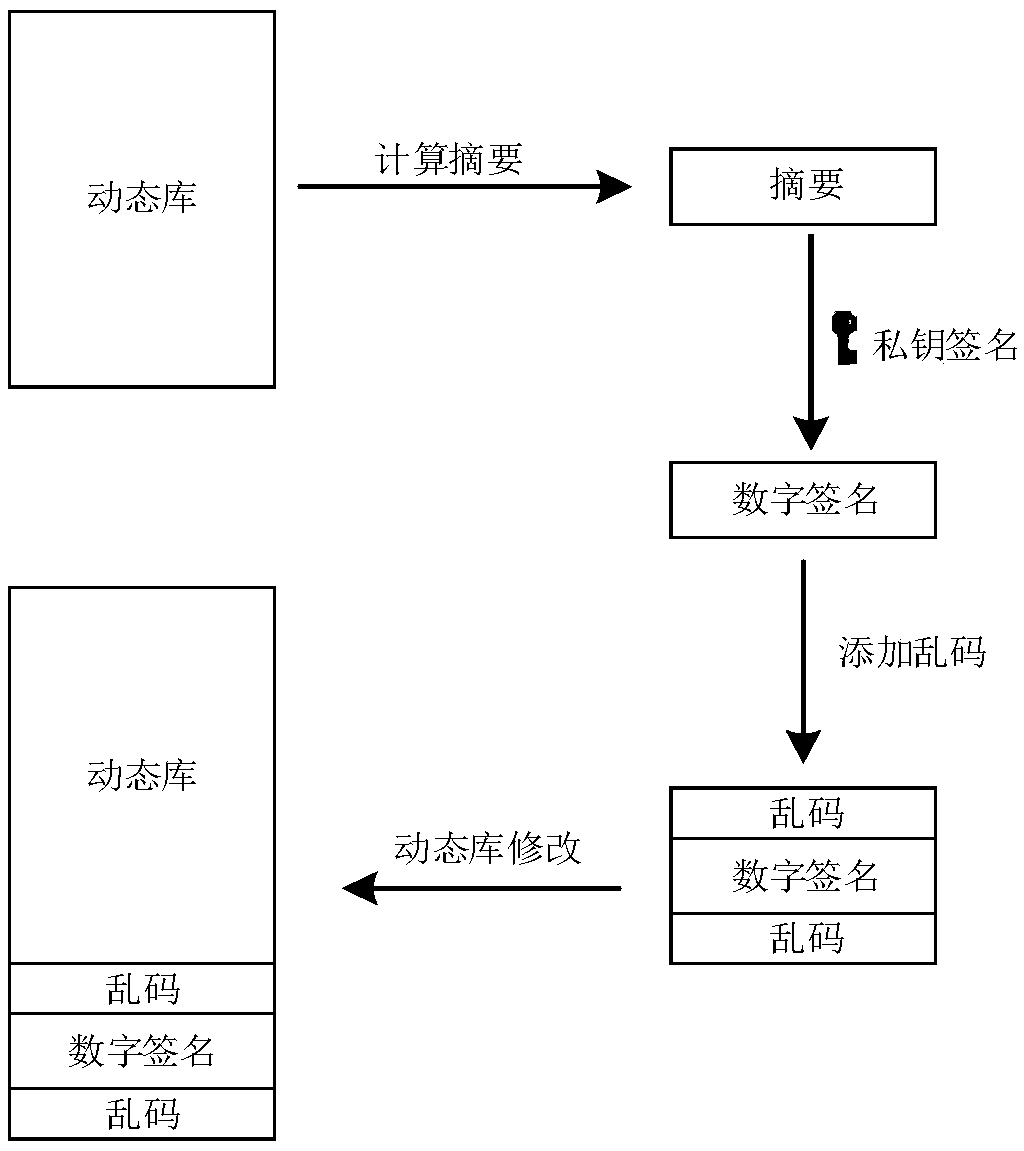
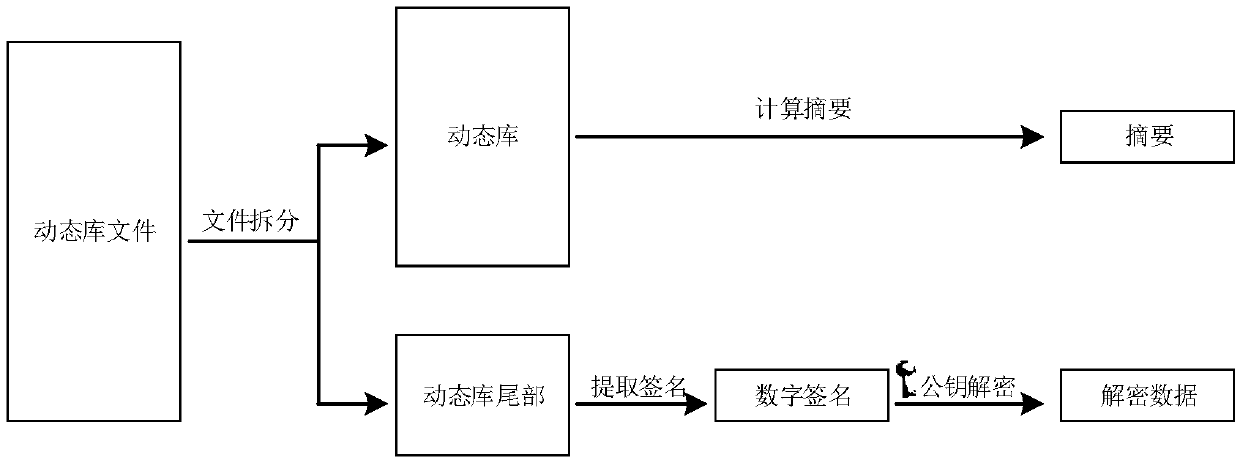
InactiveCN109635522AIntegrity guaranteedSolve the problem of tamperingDigital data protectionProgram/content distribution protectionTamper resistanceLibrary science
The invention provides a tamper-proofing method and a tamper-proofing device for a dynamic library. A digital signature of a publisher is added when the dynamic library is distributed, when the dynamic library is updated, the digital certificate of the publisher is detected, and if the updated dynamic library is the correct dynamic library published by the publisher, the dynamic library is encrypted and backed up, so that the integrity of updated file data is ensured; In the program running process, whether the dynamic library is tampered or not is checked regularly, if the dynamic library istampered, the tampered dynamic library is replaced with the backup dynamic library, and the dynamic library is prevented from being tampered in the program running process.
Owner:XUJI GRP +3
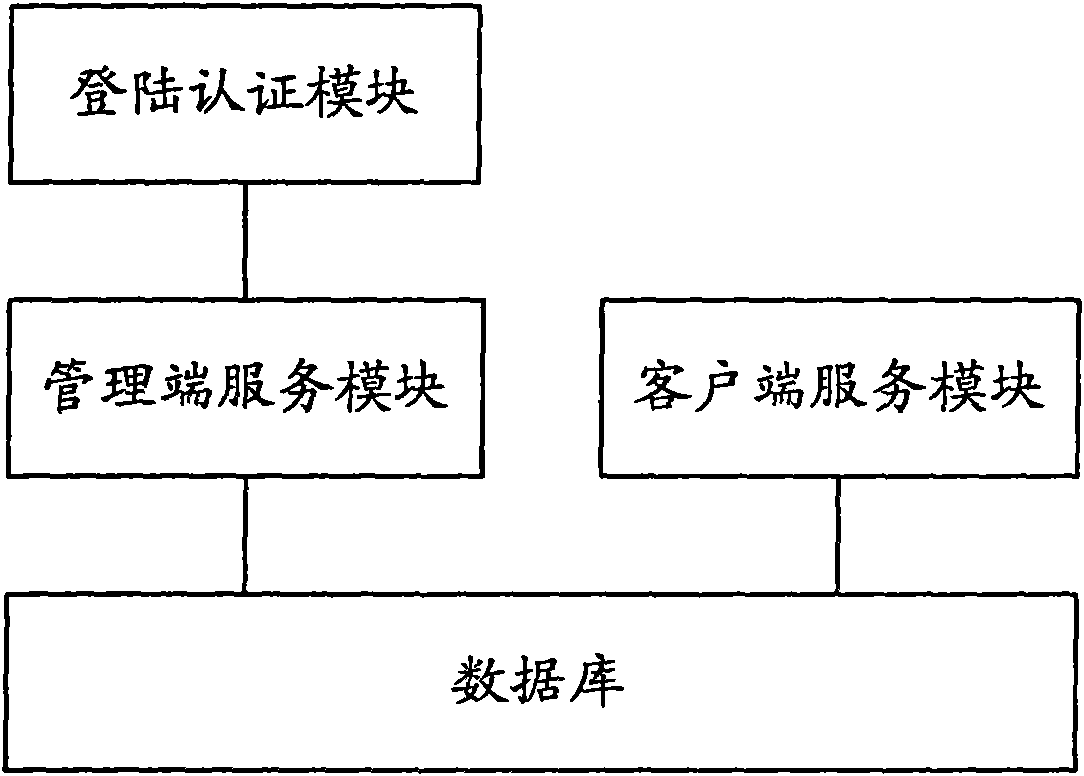
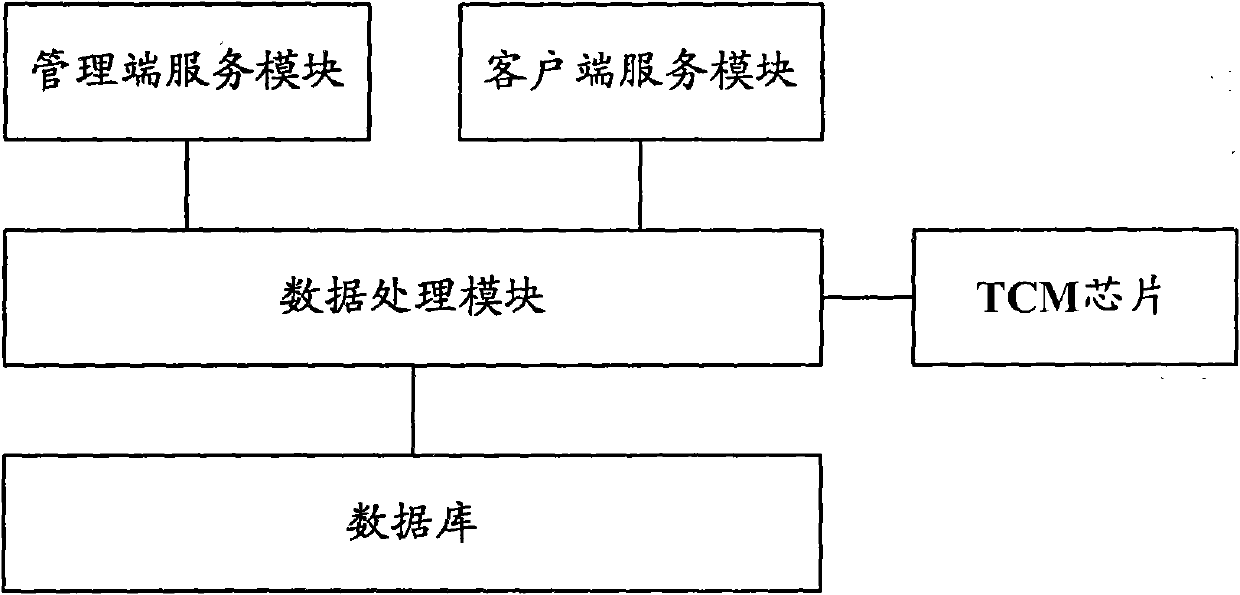
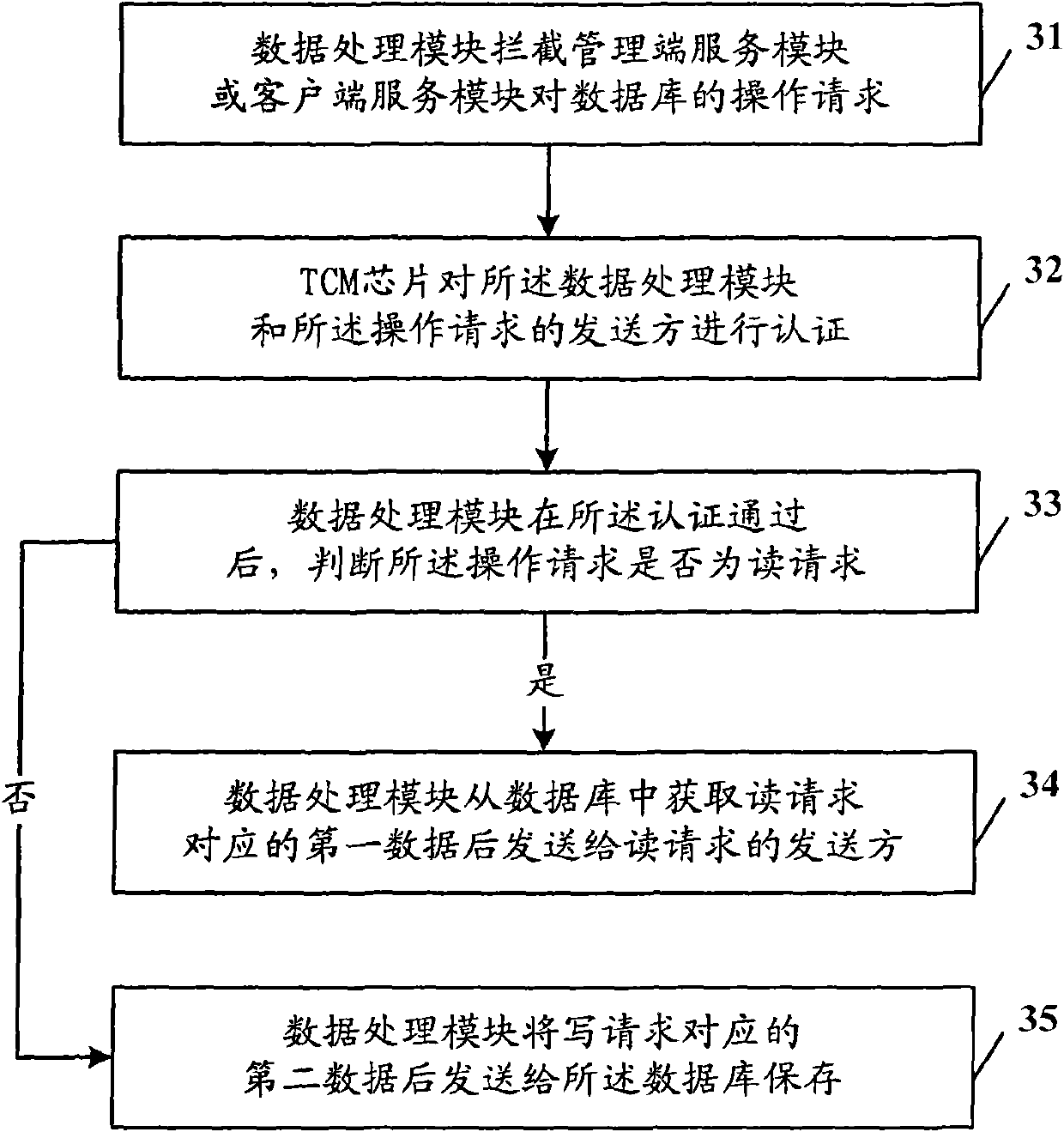
WEB server and data protection method thereof
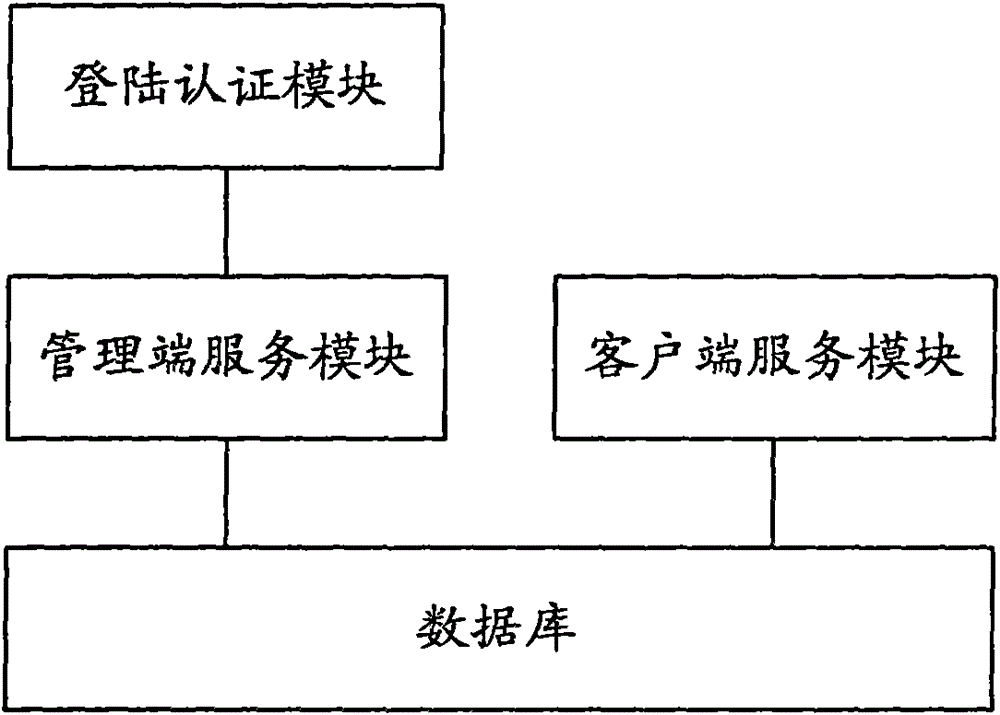
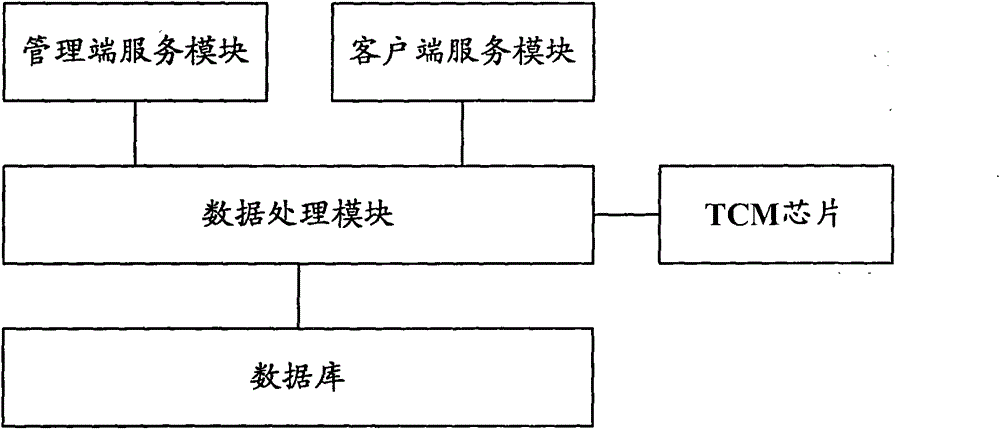
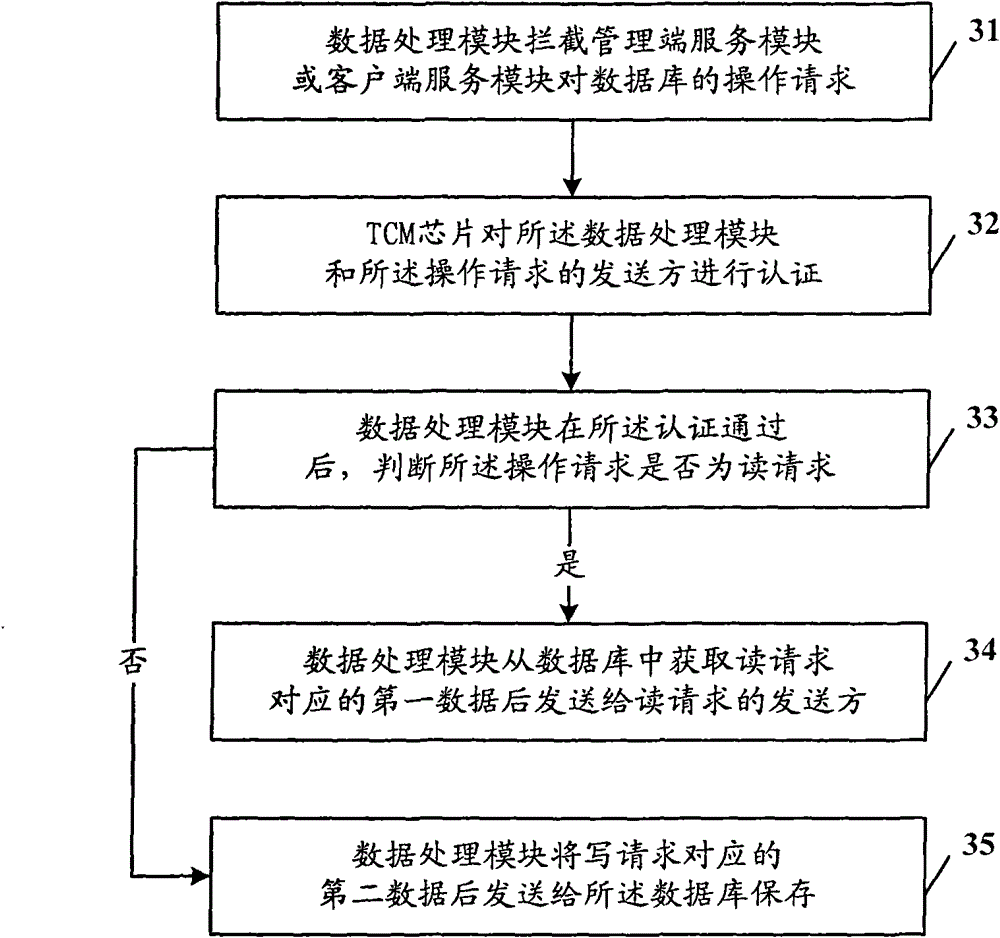
ActiveCN102025492ASolve tampered withImprove securityUser identity/authority verificationAuthentication systemWeb server
The invention provides a WEB server and a data protection method. The WEB server comprises a database used for saving data, a data processing module used for intercepting an operation request for the database, and a terminal-to-computer multiplexer (TCM) chip used for authenticating a sending party of the operation request to obtain an authentication result, wherein the data processing module is also used for performing access operation on the database according to the operation request after the authentication result indicates that the sending party passes the authentication, and returning an access result to the sending party of the operation request. The invention greatly improves the security of the database of the WEB server.
Owner:LENOVO (BEIJING) CO LTD
Encrypted document processing method and system
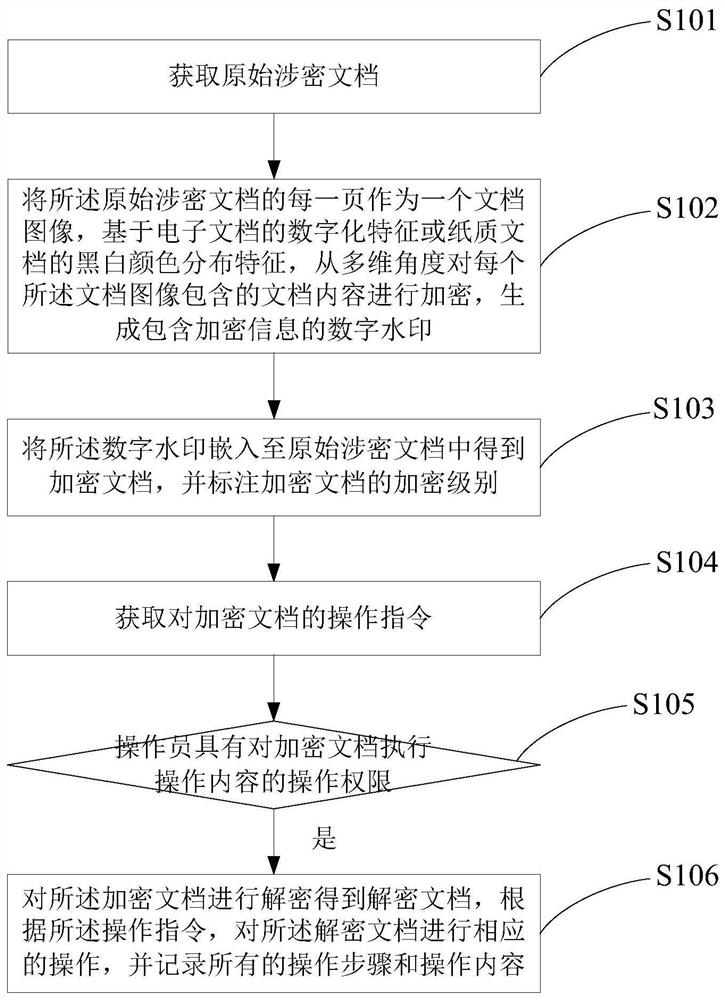
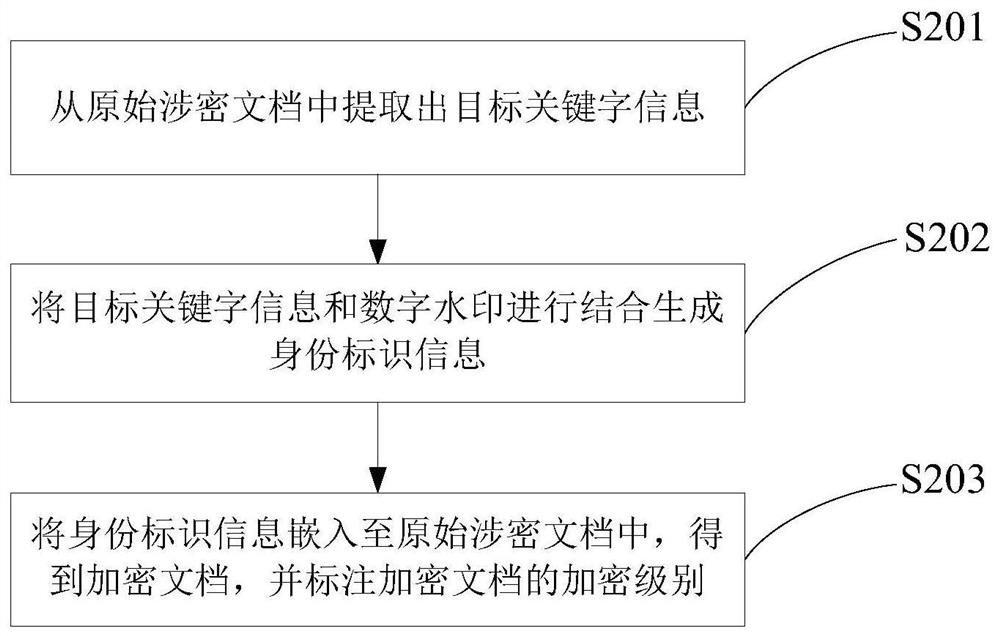
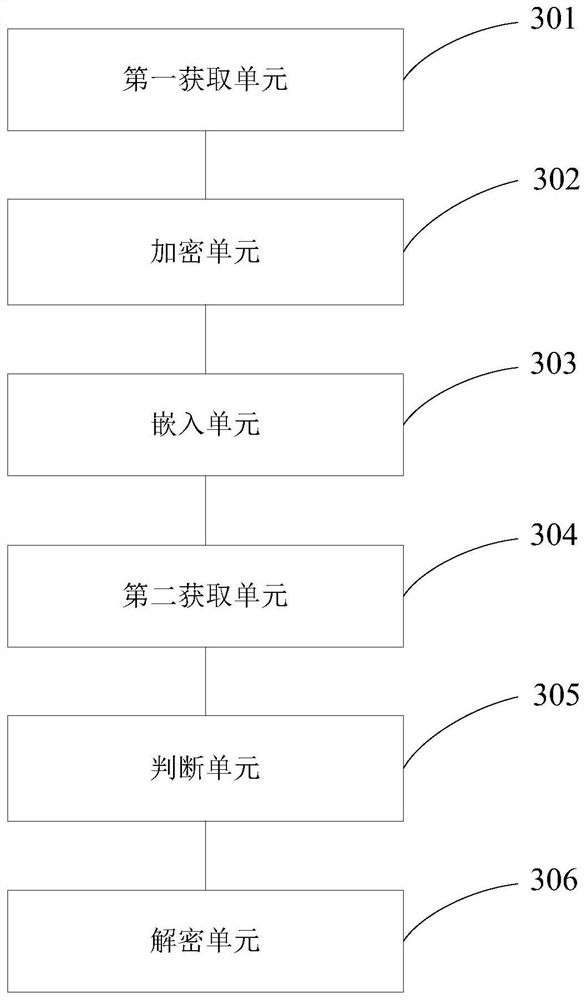
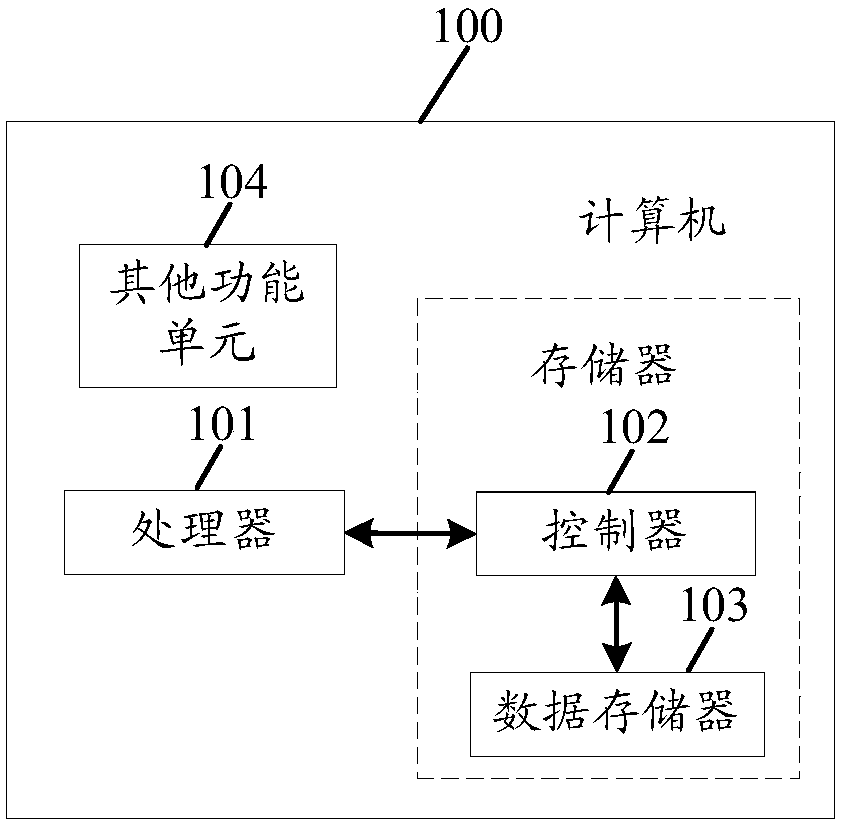
PendingCN112258376AImplement automatic encryptionSolve leakedDigital data protectionImage data processing detailsElectronic documentEngineering
The invention discloses an encrypted document processing method and system, and the method comprises the steps: taking each page of an original secret-related document as a document image, carrying out the encryption of the document content contained in each document image from a multi-dimensional angle based on the digitalization features of an electronic document or the black and white color distribution features of a paper document, generating a digital watermark containing encryption information, embedding the digital watermark into an original secret-related document to obtain an encrypted document, determining the encryption level of the encrypted document according to the use frequency of the original secret-related document, and when an operation instruction for the encrypted document is received, determining whether the operator has the operation authority of executing the operation content contained in the operation instruction on the encrypted document or not according to the identity contained in the operation instruction, and operating the encrypted document by the operator only after the verification is passed. Therefore, the problem that the secret-related document is divulged and tampered is effectively solved.
Owner:AGRICULTURAL BANK OF CHINA
Data reading method and memory
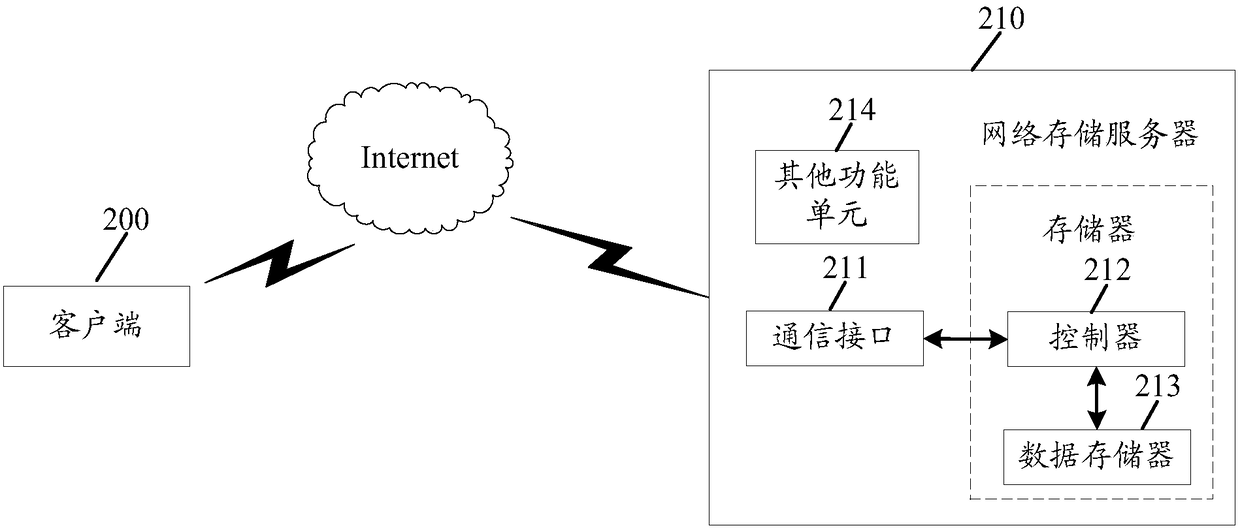
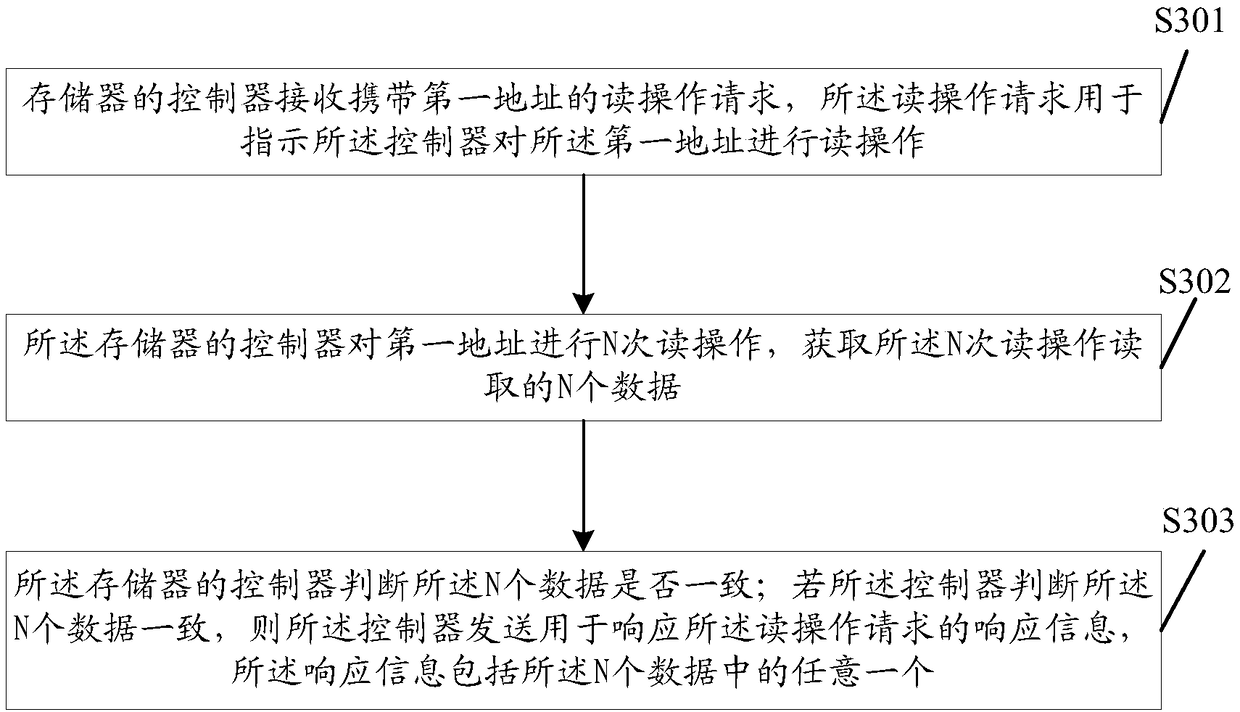
InactiveCN108073805AFix the leakSolve tampered withError detection/correctionDigital data protectionComputer scienceReal-time computing
Owner:HUAWEI TECH CO LTD
Safety verification and repair method and device for HDFS storage platform
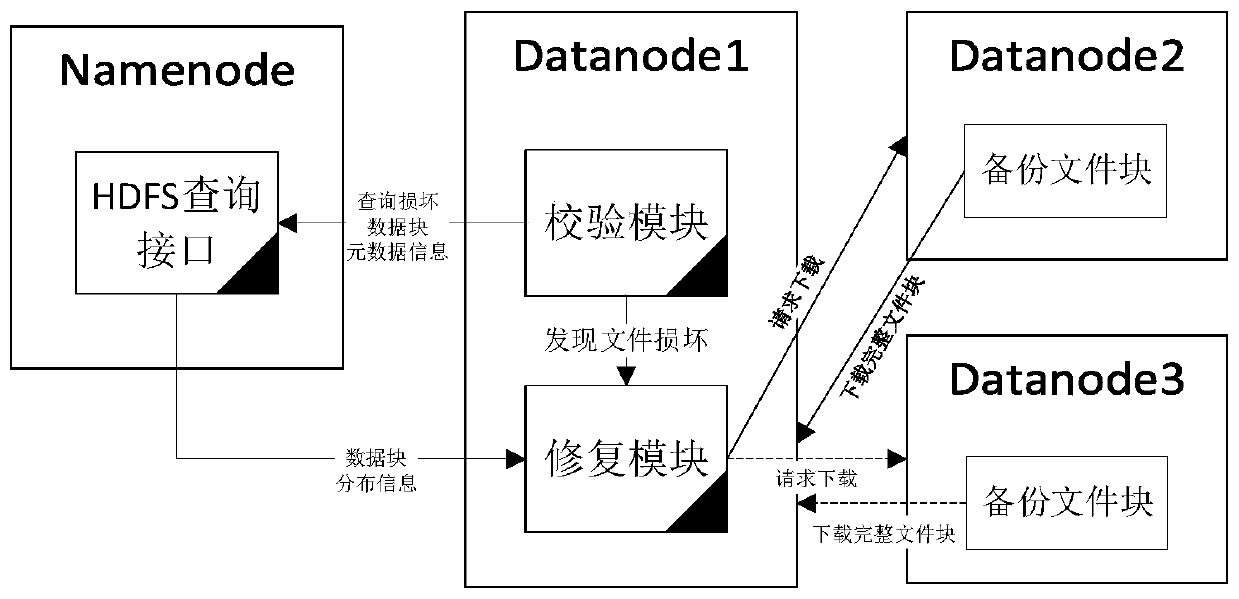
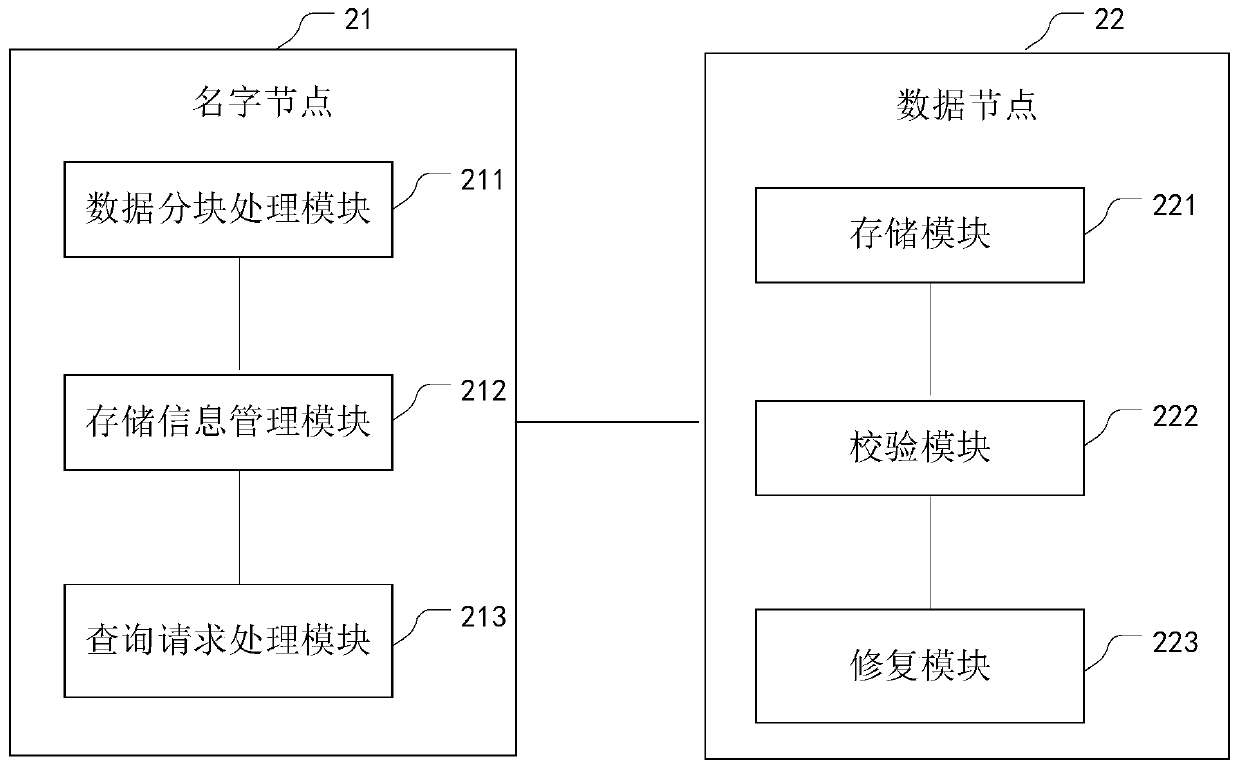
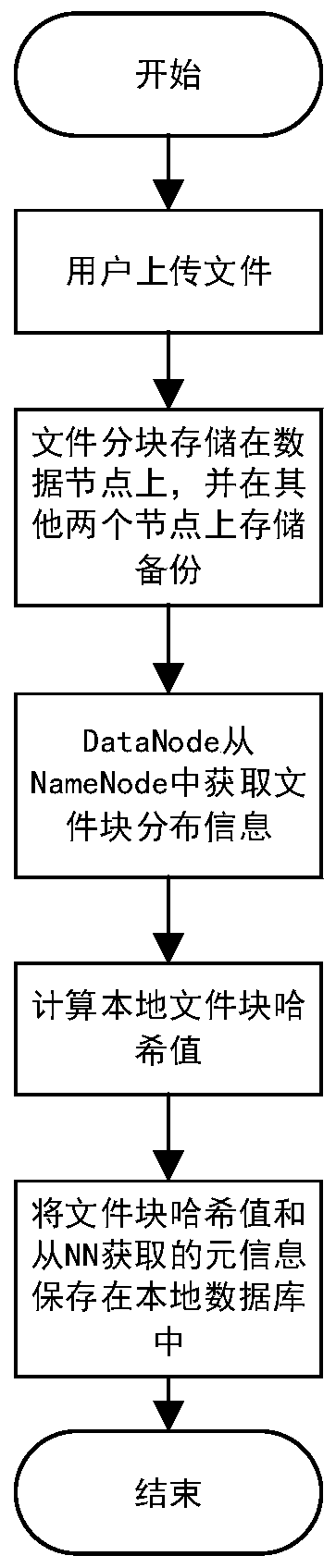
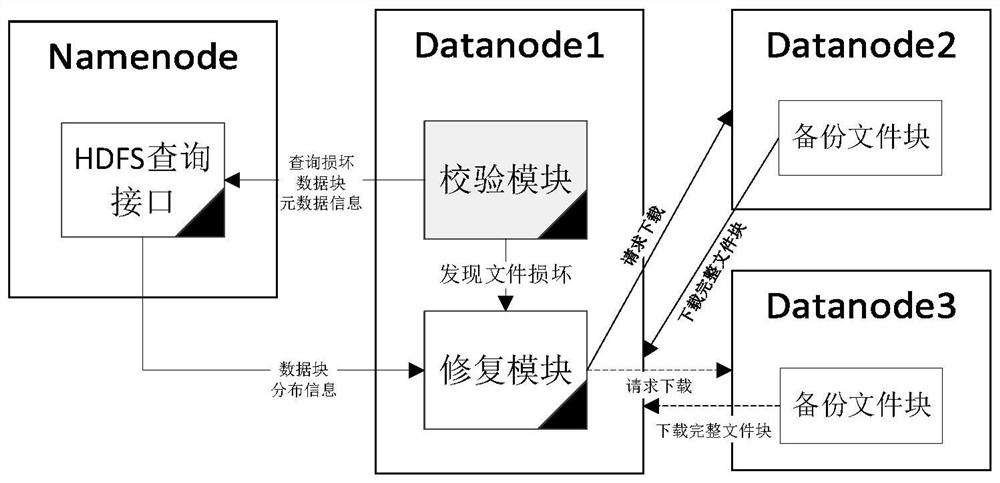
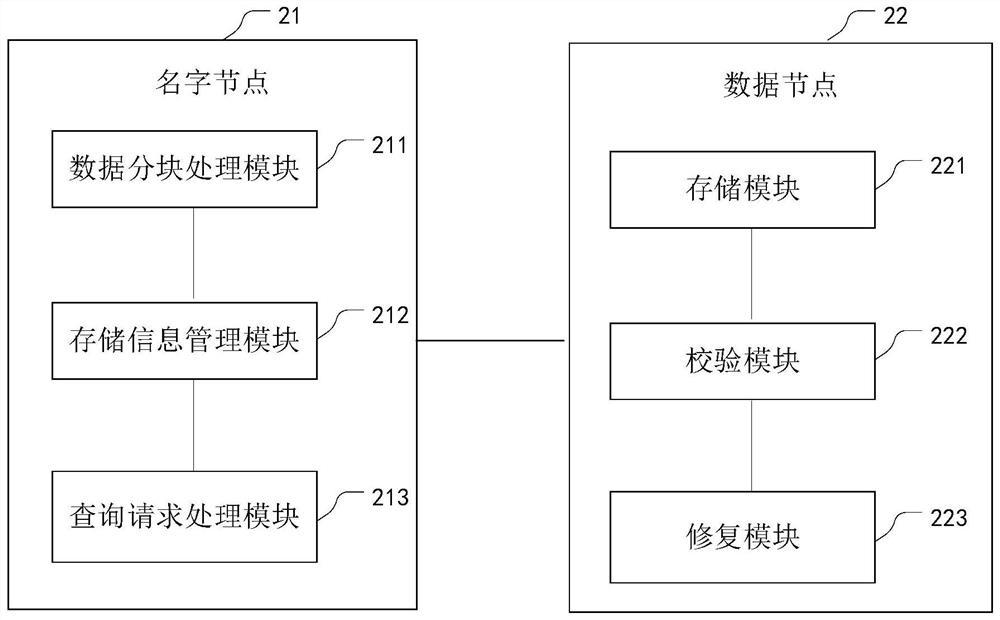
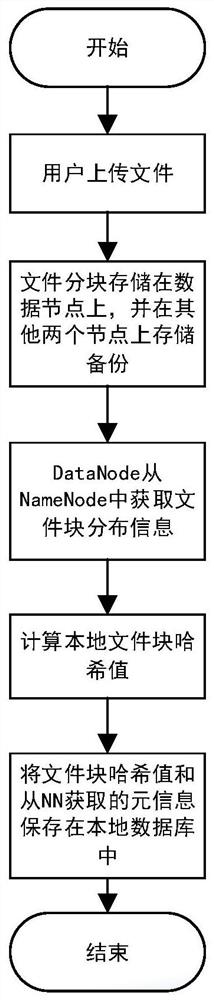
ActiveCN110163009ASolve the problem of tamperingGuaranteed reliabilityDigital data protectionFile system administrationSecurity checkOperating system
The invention provides a security check and repair method and device for an HDFS storage platform. The device is arranged on an HDFS storage platform and comprises a name node and a data node, whereinthe name node is used for managing storage data node information of a file block, receiving a query request, sent by the data node, of a damaged file block, and returning backup storage data node information of the damaged file block to the data node; and the data nodes are used for storing the file blocks, periodically checking the stored file blocks, detecting whether the file blocks are damaged or not, downloading the data blocks from other data nodes according to backup storage data node information of the damaged file blocks returned by the name nodes, and completing the repair operationof the damaged file blocks. The file block check value is calculated by using the irreversible MD5 algorithm, the problem of file tampering possibly occurring in an original system is solved, the check reliability is ensured, the check interval is adjusted according to needs, and the check efficiency is improved.
Owner:BEIJING JIAOTONG UNIV +1
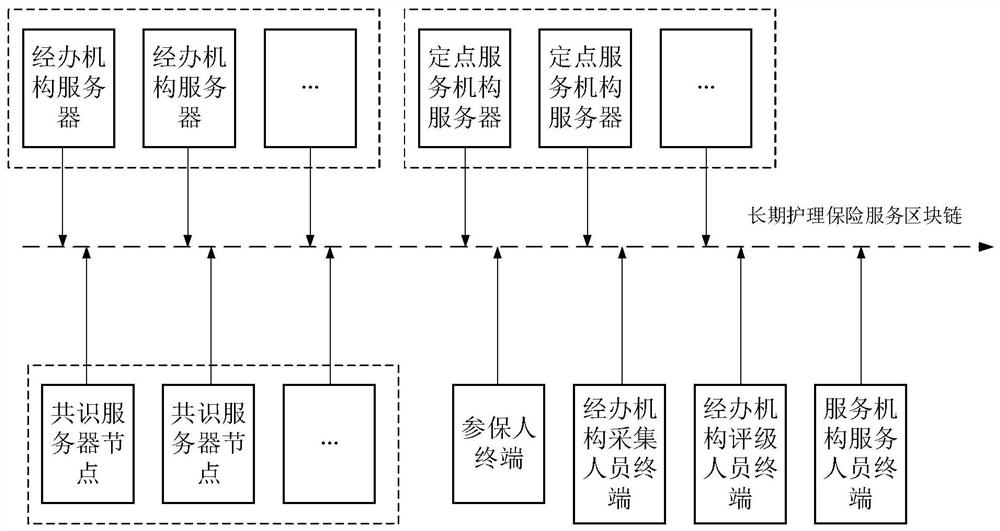
Long-term nursing insurance realization method based on block chain, storage medium and device
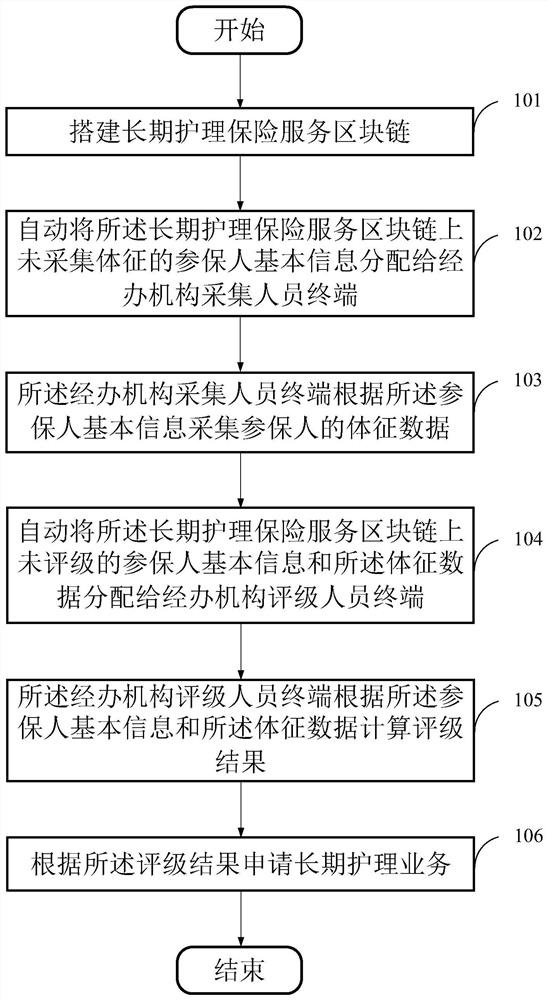
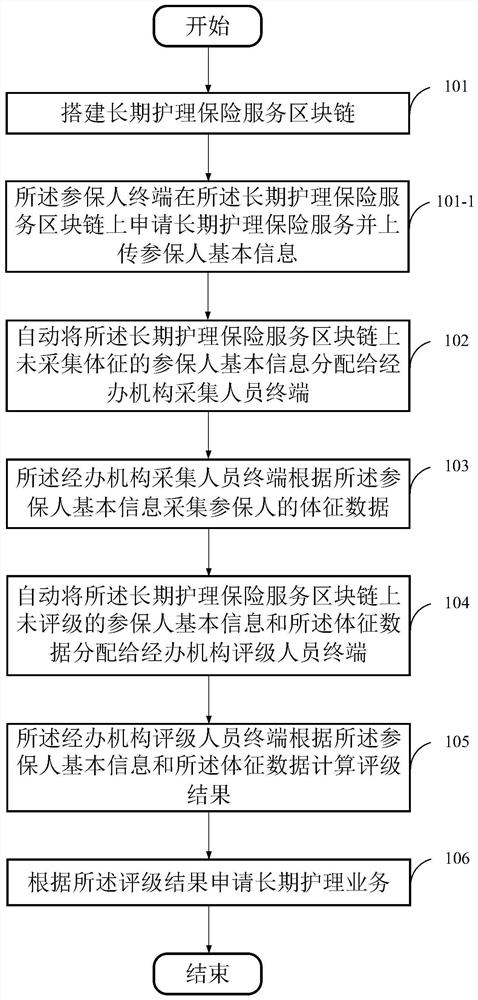
ActiveCN109785172AGuaranteed to be trueGuaranteed traceabilityFinancePayment protocolsComputer scienceBlockchain
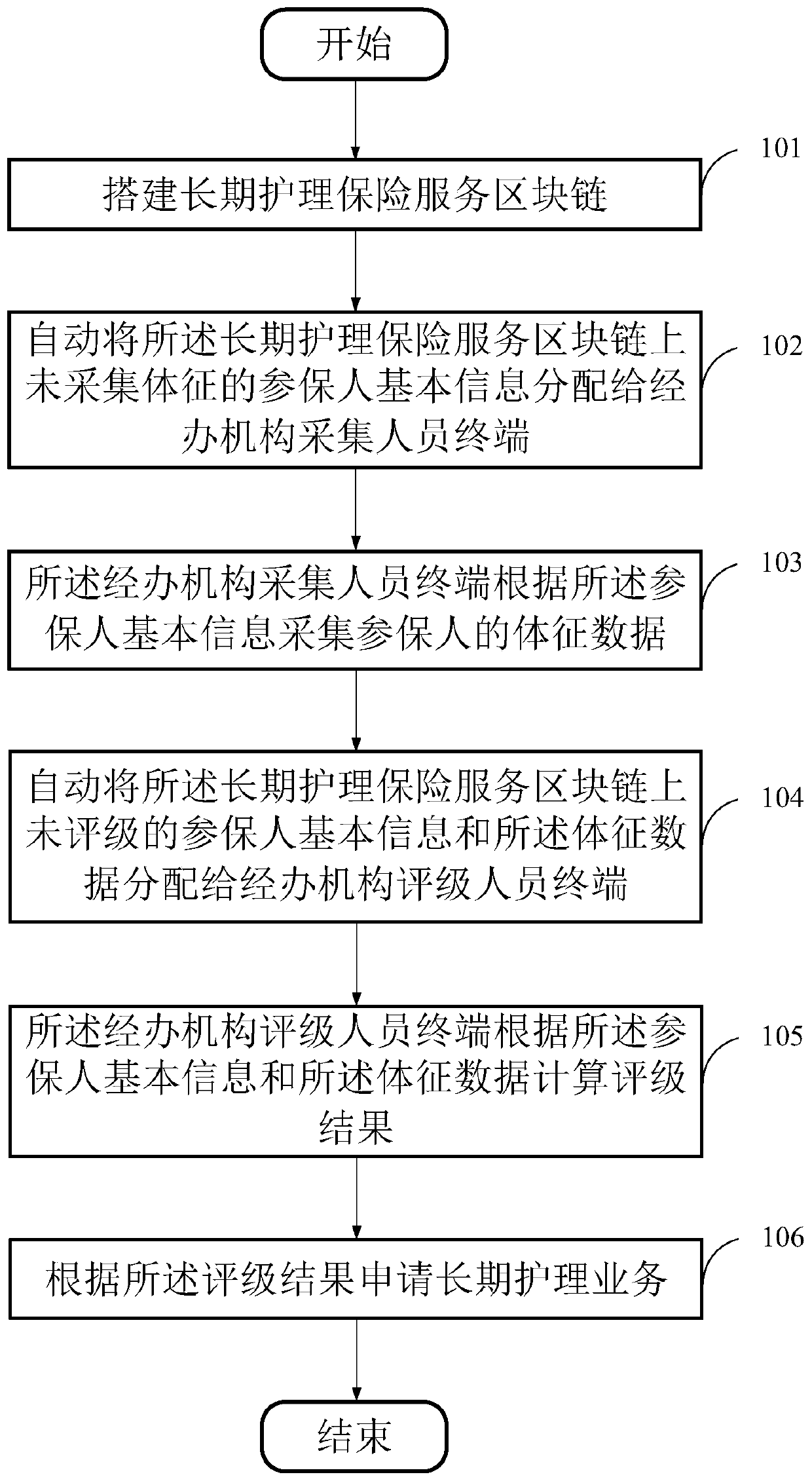
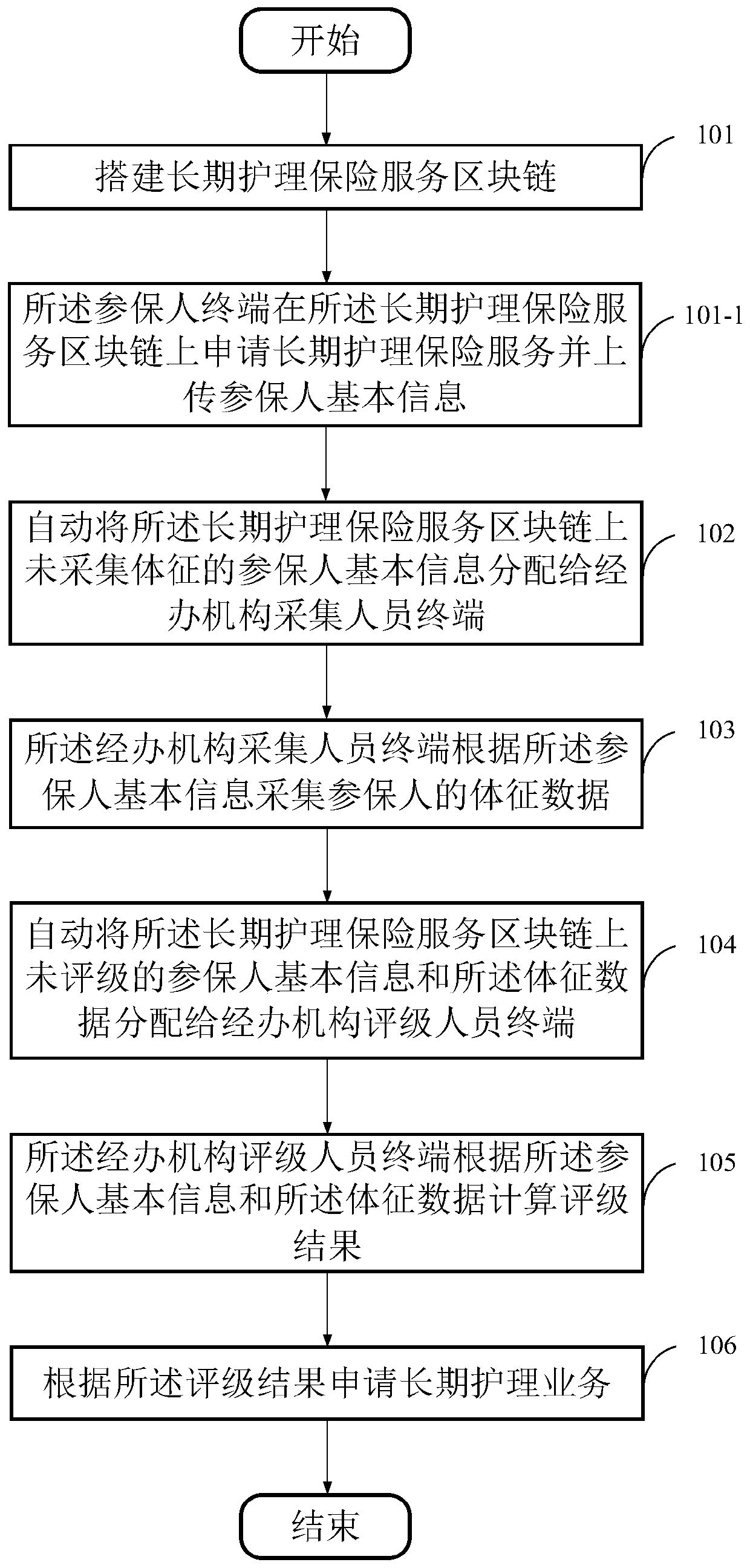
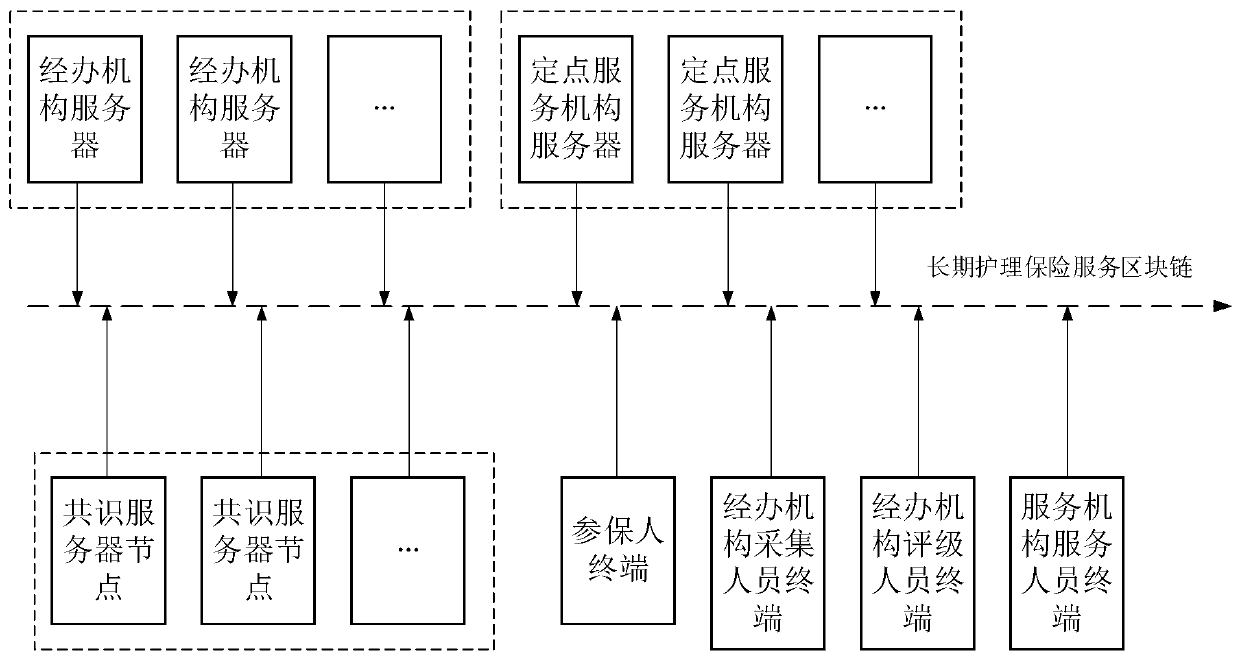
The invention provides a long-term nursing insurance realization method based on a block chain, a storage medium and device. The method comprises the following steps: establishing a long-term nursinginsurance service block chain; automatically distributing the basic information of the insurers who do not collect the physical signs on the long-term nursing insurance service block chain to a manager collection personnel terminal; The administrative organization acquisition personnel terminal acquires physical sign data of the insured person according to the basic information of the insured person; Unrated insurer basic information and the sign data on the long-term nursing insurance service block chain are automatically distributed to a manager rating personnel terminal; the administrativeorganization rating personnel terminal calculates a rating result according to the basic information of the insured person and the sign data; and applying for a long-term nursing service according tothe rating result. The safety and traceability of the long-term nursing insurance service are ensured, the sharing is clear, the objectivity and accuracy of the rating result are ensured, and the userexperience is improved.
Owner:易保互联医疗信息科技(北京)有限公司
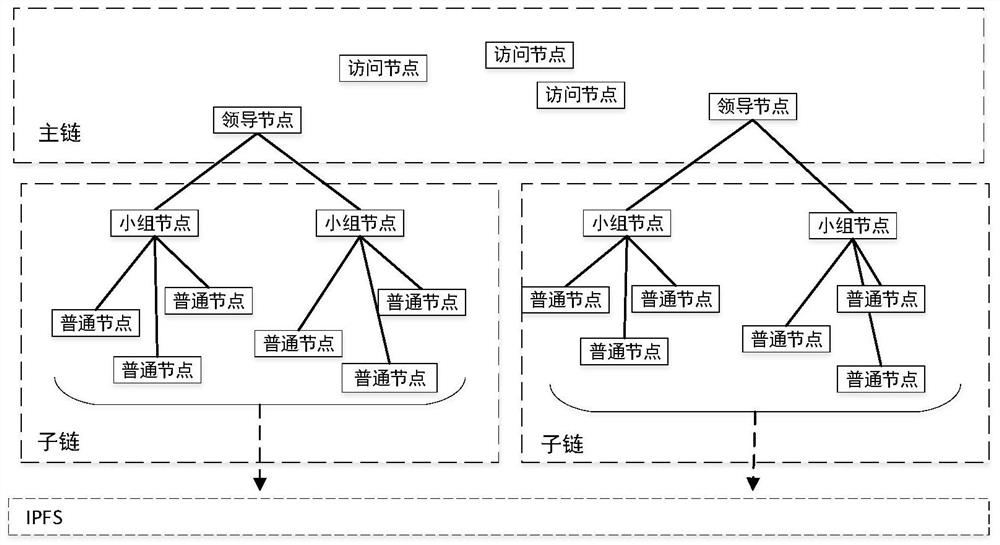
Archive secure storage and sharing system based on hybrid block chain and implementation method
ActiveCN112540957AAddress the right to knowSolve protection problemsDatabase distribution/replicationDigital data protectionThird partyPrivacy protection
The invention discloses an archive secure storage and sharing system based on a hybrid block chain and an implementation method, belongs to the field of archive sharing, and aims to solve the technical problem of how to realize archive privacy protection, prevent archives from forging and tampering, enable authorized access of the archives, and improve the archive sharing speed. According to the technical scheme, the system comprises a storage layer which is used for storing shared files and protecting the files against tampering, and adopts an IPFS; a sharing layer which is used for recordinggenerated transaction information, providing evidences for tracing of the file sharing process, automatically executing identity authentication and guaranteeing safe sharing of files under the condition that no third party participates, and comprises a multi-layer block chain model and an intelligent contract on a block chain; and a user layer which is used for managing, updating, checking and sharing files, and is composed of participants. The method specifically comprises the following steps: initializing; identity registration and authentication; encrypting and storing the archives; and archive sharing.
Owner:QILU UNIV OF TECH
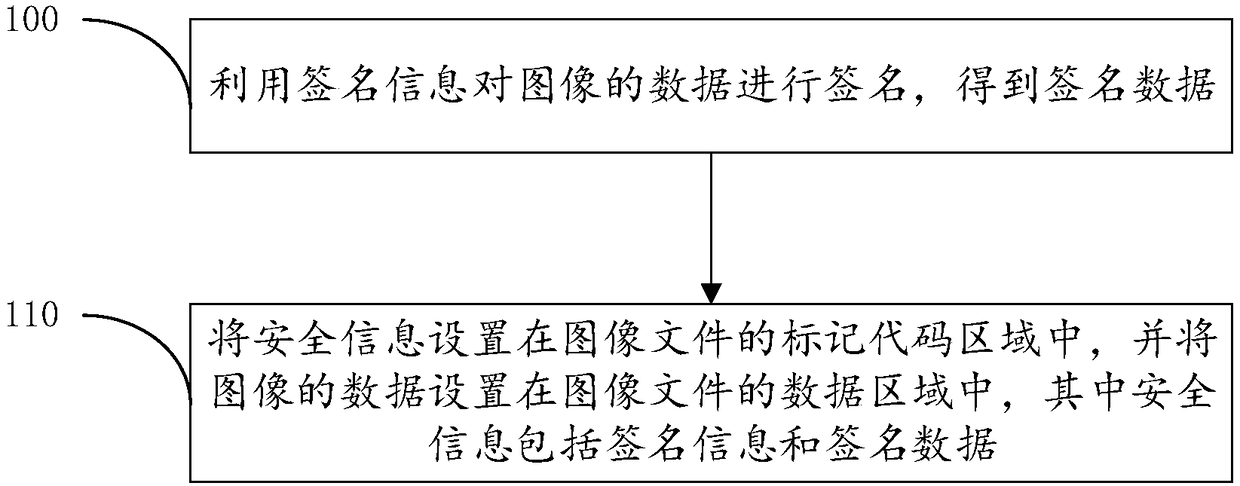
Signature method and device and signature verification method and device of image
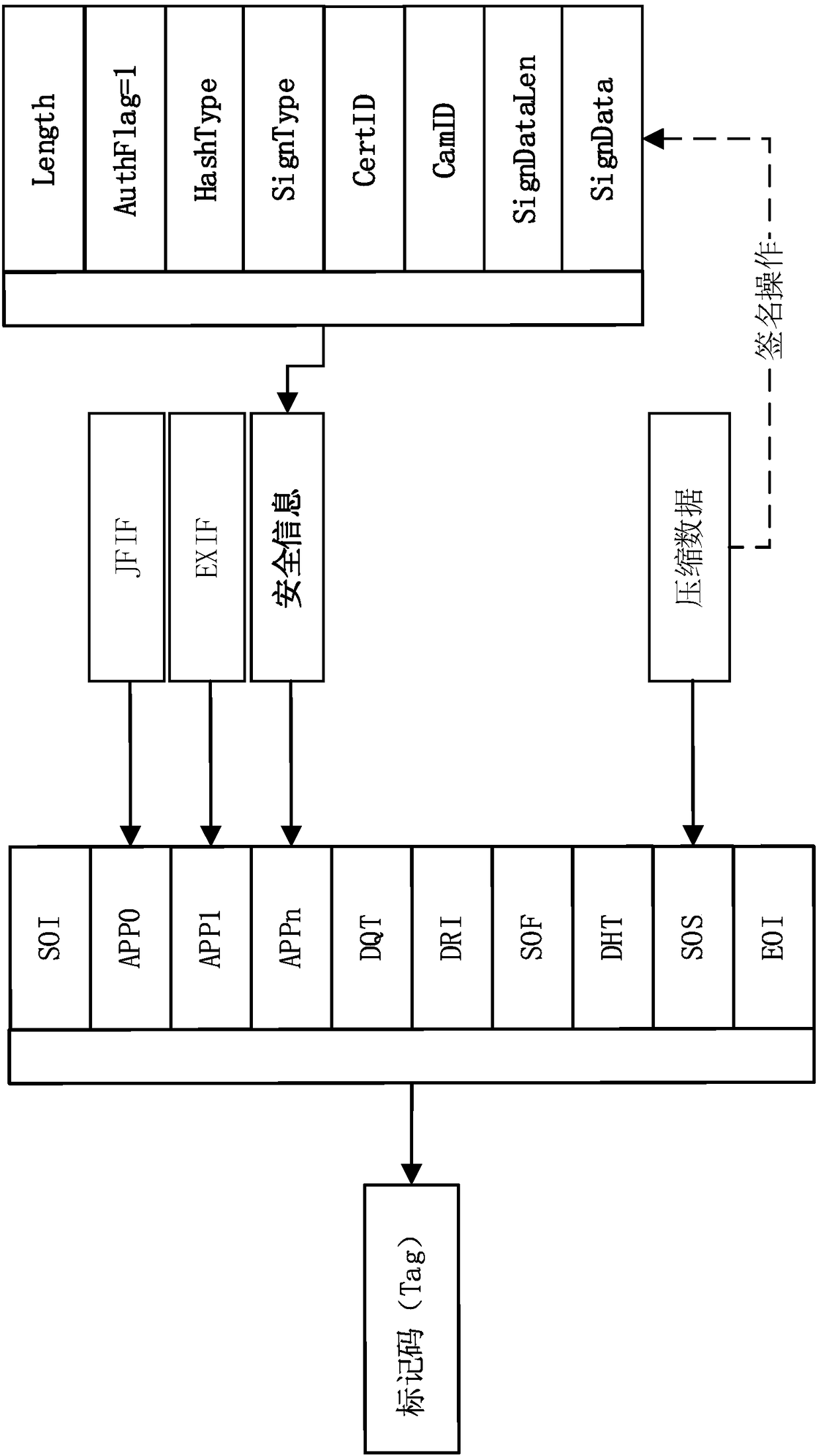
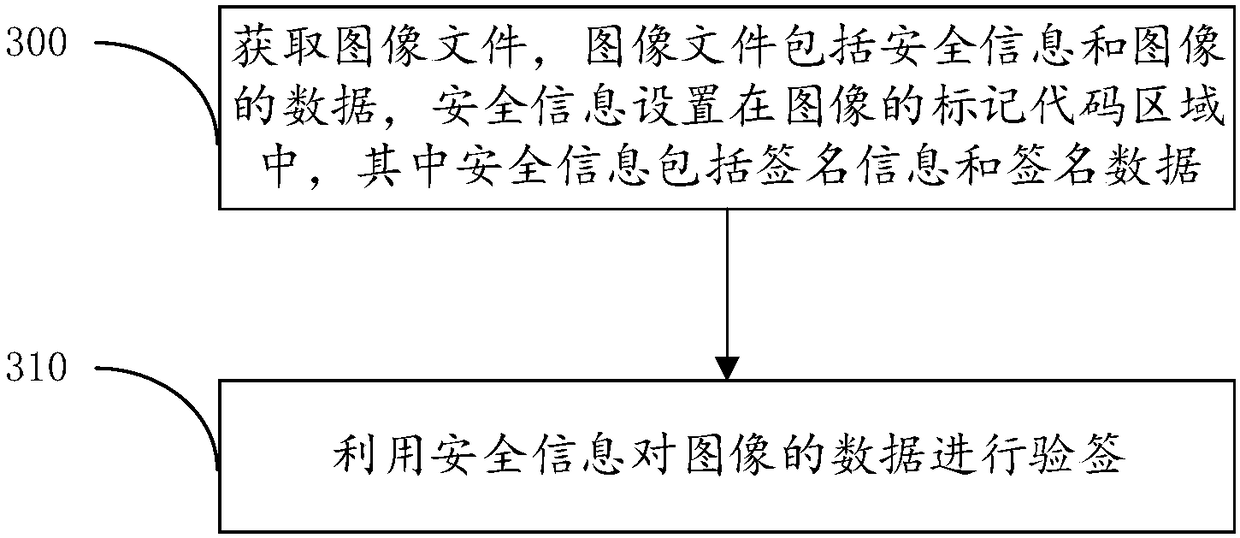
InactiveCN108596050ADoes not affect browsingSolve the problem of tamperingSignature reading/verifyingSecurity informationImage content
The invention provides a signature method and device and a signature verification method and device of an image. The image is signed, a signature and / or security information required for signature verification is set at an image data header, thus browsing of image contents is not impacted, whether the image is already tampered with can also be verified, and the tampering problem of the image contents is effectively solved. The signature method of the image includes: using signature information to sign data of the image to obtain signature data; and setting the security information in a mark code area of an image file, and setting the data of the image in a data area of the image file, wherein the security information includes the signature information and the signature data.
Owner:GUANGDONG VIMICRO
Concrete quality tracing method based on block chain
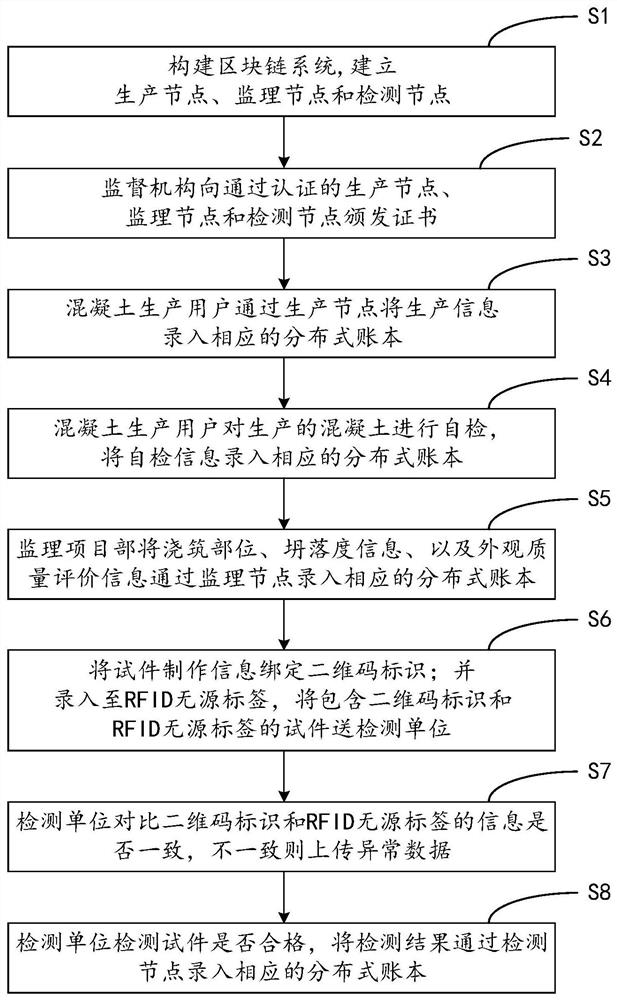
PendingCN113379426ASolve the problem of ciphertext hijackingSolve the problem of tamperingDatabase distribution/replicationCo-operative working arrangementsRelevant informationCiphertext
The invention relates to the field of concrete quality traceability, and particularly discloses a concrete quality traceability method based on a block chain, and the method comprises the steps: a block chain system is constructed, a project is brought into the block chain system through a supervision mechanism, and a certificate is issued to an authenticated node; the concrete production user and the supervision project department input related information into a distributed account book through corresponding nodes; test piece manufacturing information is input into the RFID passive tag; and the detection unit checks the information in the RFID passive tag through the block chain system, and inputs the detection result into the distributed account book. According to the invention, the block chain technology is adopted to solve the ciphertext robbery problem caused by a single network channel and the data tampering problem caused by server centralization and data management centralization, and the block chain technology is combined with the RFID anti-counterfeiting technology, so that the data sharing is realized, the user can be effectively prevented from tampering the data, and the security of the supervision system is greatly improved.
Owner:CHONGQING UNIV
File transmission method and device, server, equipment and medium
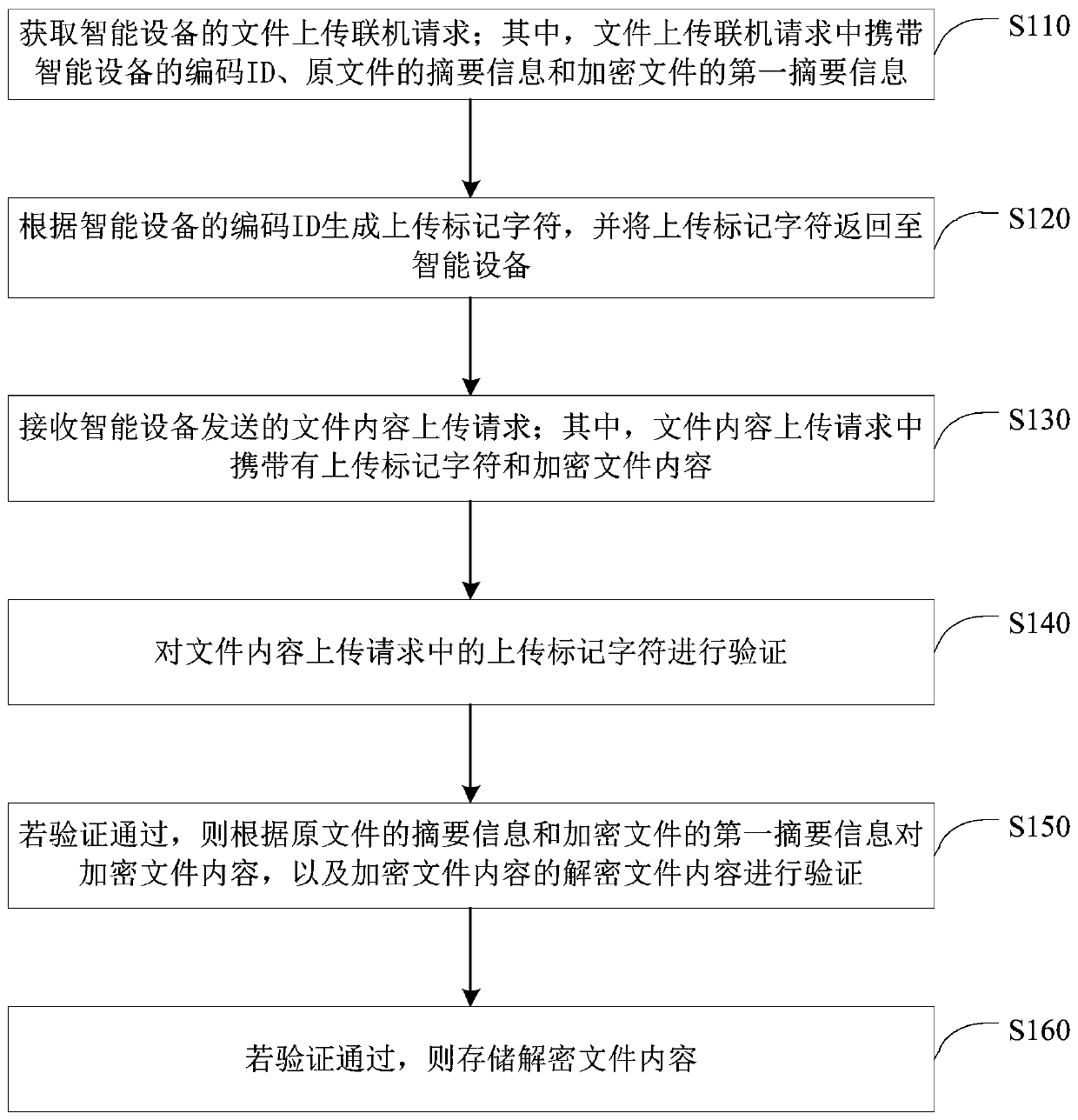
ActiveCN111324914AImprove reliabilityImprove integrityDatabase distribution/replicationDigital data protectionFile transmissionEngineering
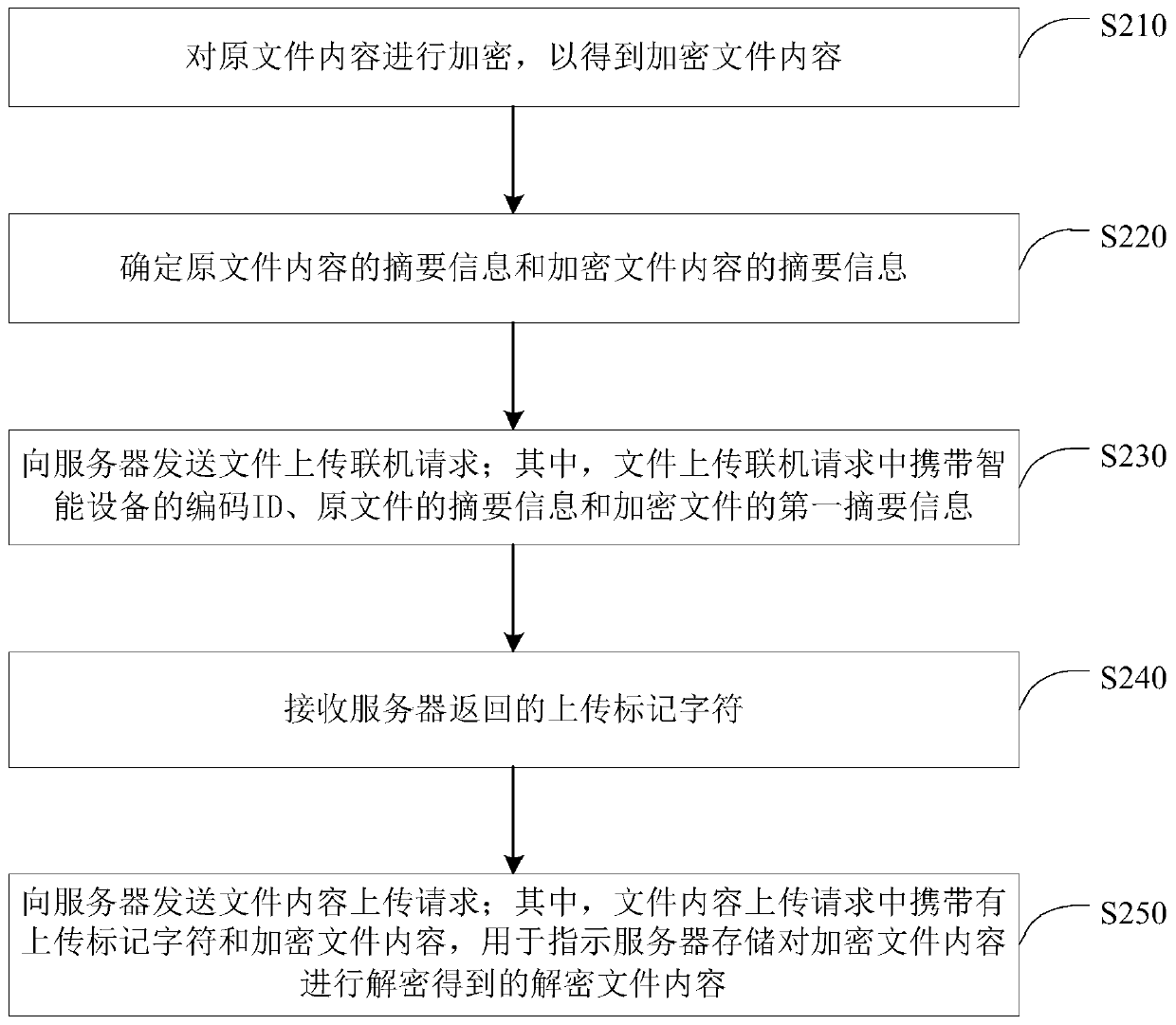
The embodiment of the invention discloses a file transmission method and device, a server, equipment and a medium. The method comprises the following steps: acquiring a file uploading online request of the intelligent equipment; wherein the file uploading online request carries a code ID of the intelligent device, abstract information of an original file and first abstract information of an encrypted file; generating an uploading mark character according to the code ID of the intelligent device, and returning the uploading mark character to the intelligent device; receiving a file content uploading request sent by the intelligent device; wherein the file content uploading request carries an uploading mark character and encrypted file content; verifying the uploaded mark character; verifying the encrypted file content and the decrypted file content of the encrypted file content; storing decrypted file content. According to the embodiment of the invention, the content of the encrypted file and the content of the decrypted file can be verified, the problem that the content of the file is tampered in the transmission process is solved, and the reliability and integrity of file contenttransmission are effectively improved.
Owner:CHINA CONSTRUCTION BANK
Information acquisition and early warning system of ultrasonic medical equipment
PendingCN112370076ARealize the technical effect of remote real-time monitoringSolve the problem of tamperingParticular environment based servicesInfrasonic diagnosticsEarly warning systemMedical equipment
The invention relates to the technical field of information acquisition and early warning, and discloses an information acquisition and early warning system for ultrasonic medical equipment. The information acquisition and early warning system comprises a sensing device for acquiring various parameters of the ultrasonic medical equipment during working, intelligent monitoring equipment SME for monitoring various operating parameters of the ultrasonic medical equipment during working, a local server LSICEW on which a working parameter real-time monitoring system operates and an intelligent mobile phone SPi. A working parameter real-time monitoring system comprises a parameter monitoring module used for sending an instruction to the intelligent monitoring equipment SME, a parameter display module used for displaying operation parameter data, a parameter analysis module used for analyzing and judging whether all operation parameters are abnormal or not when the ultrasonic medical equipment works, an abnormal early warning module used for sending early warning information to the abnormal working condition of the ultrasonic medical equipment, and a central control module. According to the invention, the problems of how to monitor the ultrasonic medical equipment in real time and how to send out real-time early warning information for abnormal conditions of the ultrasonic medical equipment during working are solved.
Owner:马炎
Blockchain Trusted Storage Execution Hardware Environment Based on Fusion Memory
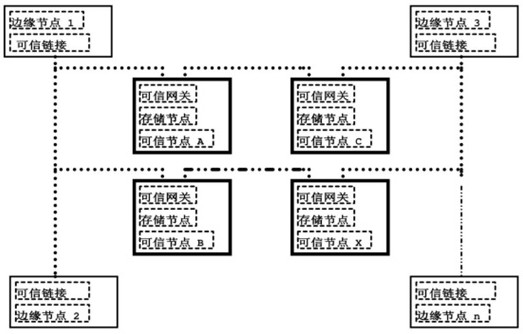
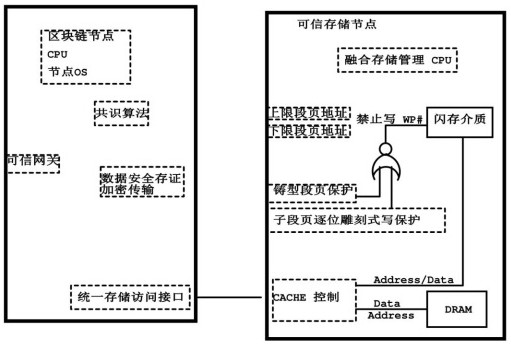
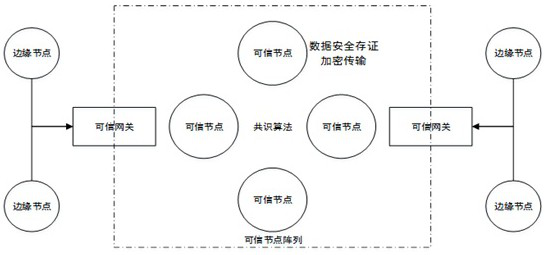
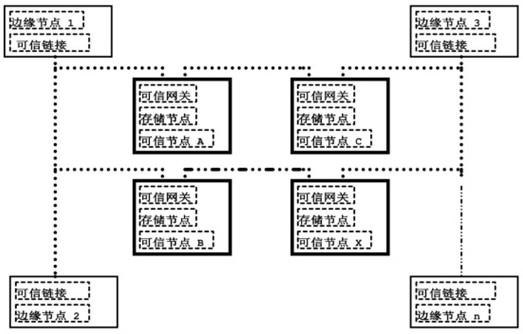
ActiveCN112118246BEfficient read and write speedSolve the problem of tamperingSecuring communicationData integrityProtection mechanism
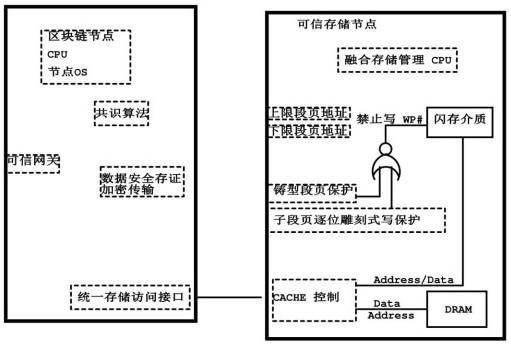
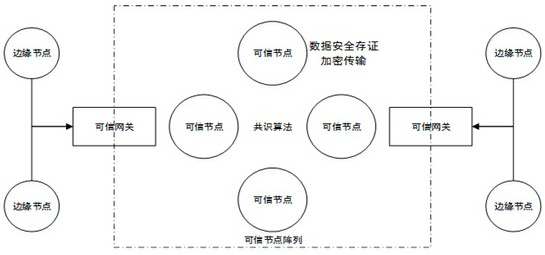
The invention discloses a block chain trustworthy storage execution hardware environment based on fusion memory, including data collection, data transmission and data storage, including the hardware environment equipped with block chain nodes, and the block chain nodes include storage mechanism nodes and the data point to the node; the WP# prohibiting writing signal of the hardware control flash memory is used to ensure that the data in the protected area can only be written once after the system is initialized and can no longer be modified; The address-set flash memory space is "cast" type write-protected, that is, once it is finalized, it can be written once. This kind of block chain trusted storage execution hardware environment based on fusion memory, the hardware has high-efficiency read and write speed, and can store a large amount of data; it has its own CPU processor, can write encryption algorithms, independent packaging, and can be used as a block Chain security nodes are used; from the hardware level, the data is written once and read out multiple times to ensure the integrity of the data on the chain and cannot be deleted.
Owner:北京微密科技发展有限公司
Blockchain trusted storage execution hardware environment based on fused memory
ActiveCN112118246AEfficient read and write speedSolve the problem of tamperingSecuring communicationWrite protectionData integrity
The invention discloses a blockchain trusted storage execution hardware environment based on a fused memory, which comprises data acquisition, data transmission and data storage comprises a hardware environment carrying blockchain nodes, and is characterized in that the blockchain nodes comprise storage mechanism nodes and data pointing nodes; WP# write forbidding signals of a flash memory are controlled through hardware, and it is guaranteed that data in a protection area is written only once after a system is initialized and cannot be modified any more; and a cast segment page storage protection mechanism performs cast-type write protection on a flash memory space set by the upper and lower limit addresses, namely once the flash memory space is shaped, the flash memory space is written once. According to the blockchain trusted storage execution hardware environment based on the fused memory, hardware has an efficient read-write speed, and can store large-volume data; a built-in CPU processor is provided, an encryption algorithm can be written into the CPU processor, is independently packaged and can be used as a blockchain security node; from a hardware level, the data is writtenin once and read for multiple times, so that the integrity of the uploaded data is guaranteed and cannot be deleted.
Owner:深圳市微密科技有限公司
An anti-counterfeit verification method based on digital signature technology
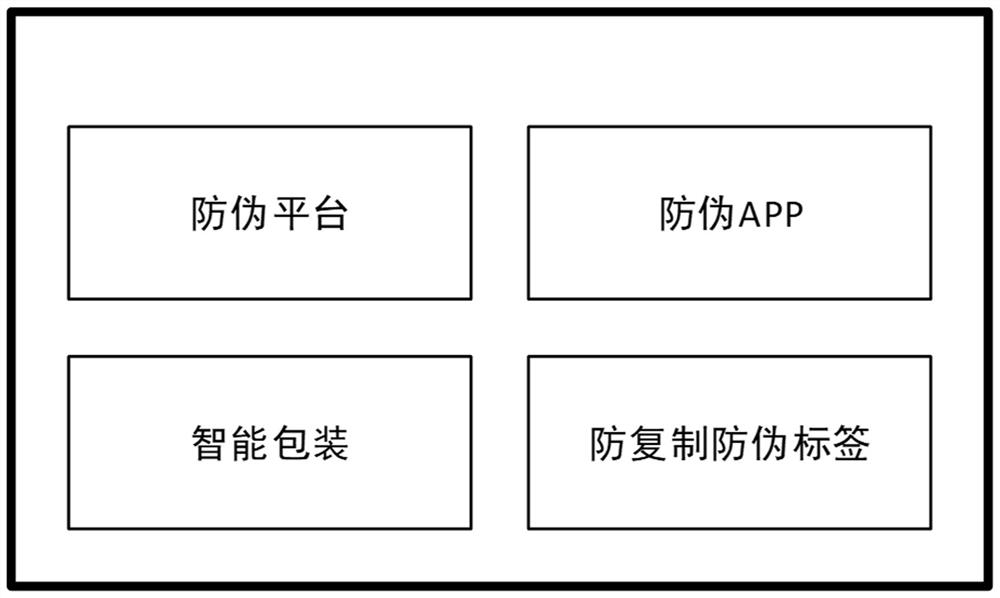
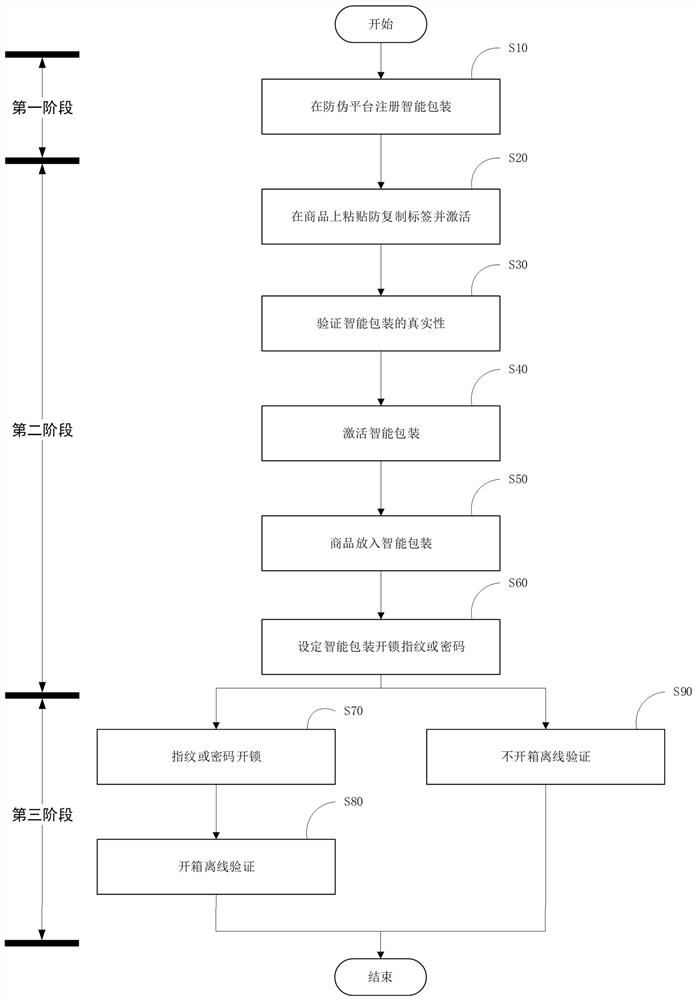
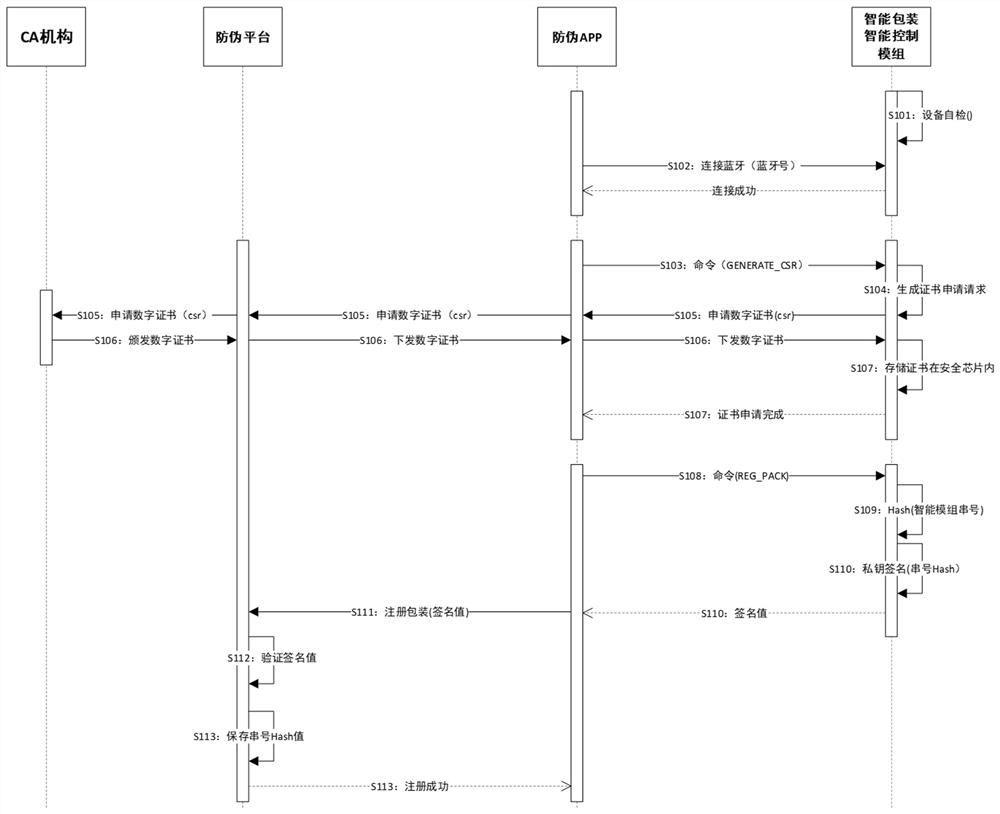
ActiveCN111932285BAvoid the risk of counterfeitingPrevent counterfeitingDigital data protectionInternal/peripheral component protectionDigital signatureSecurity information
The invention discloses an anti-counterfeit verification method based on digital signature technology, comprising: A. registering smart packaging on an anti-counterfeiting platform through an anti-counterfeiting APP and applying for a digital certificate of the smart packaging; Anti-counterfeiting anti-counterfeiting label; C. Obtain the anti-counterfeiting information of the smart packaging through the anti-counterfeiting APP and send it to the anti-counterfeiting platform for verification. If the smart packaging passes the verification, go to the next step; D. Activate the smart packaging and establish the relationship between the smart packaging and the product E. The smart packaging verifies the put-in commodity, and determines whether it is an associated commodity, and if so, controls the lock module to be locked; F. sets the unlocking data of the smart packaging, and the method of the present invention establishes the item and The corresponding relationship of packaging enables smart packaging to correctly perceive the packaged items, achieve the multi-party verification anti-counterfeiting packaging effect between the system, items, and packaging, and also realize unopened package verification and offline verification.
Owner:四川省数字证书认证管理中心有限公司
Method and device for generating digital certificate
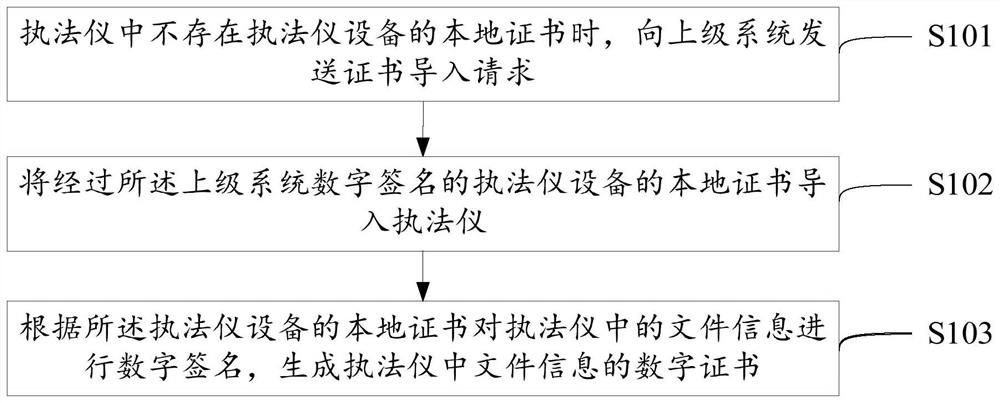
ActiveCN108322311BEnsure safetyNon-repudiationUser identity/authority verificationDigital signatureEngineering
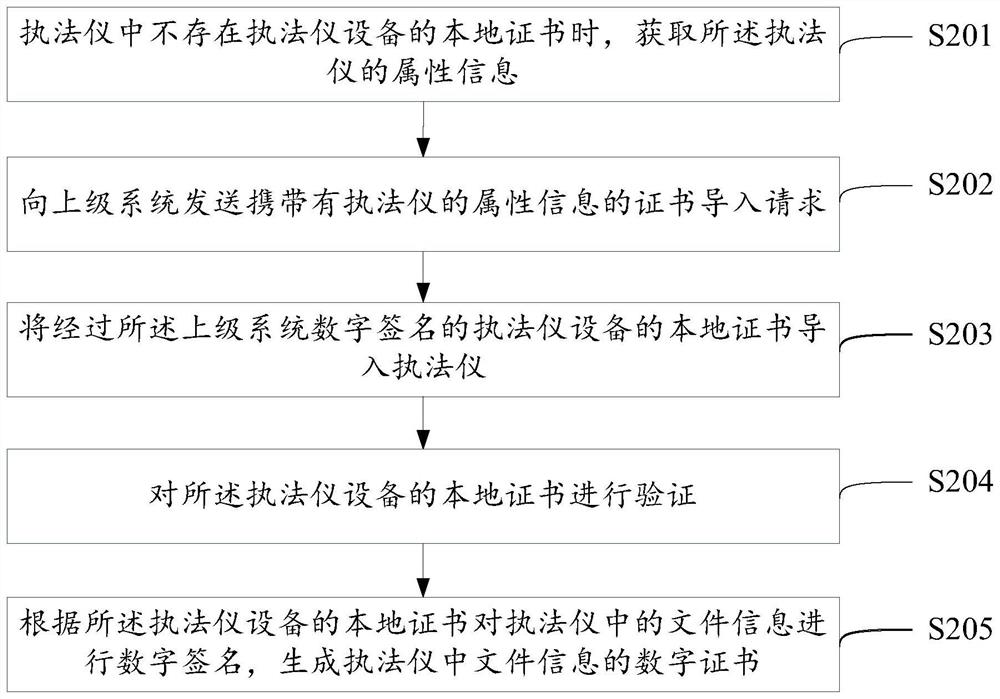
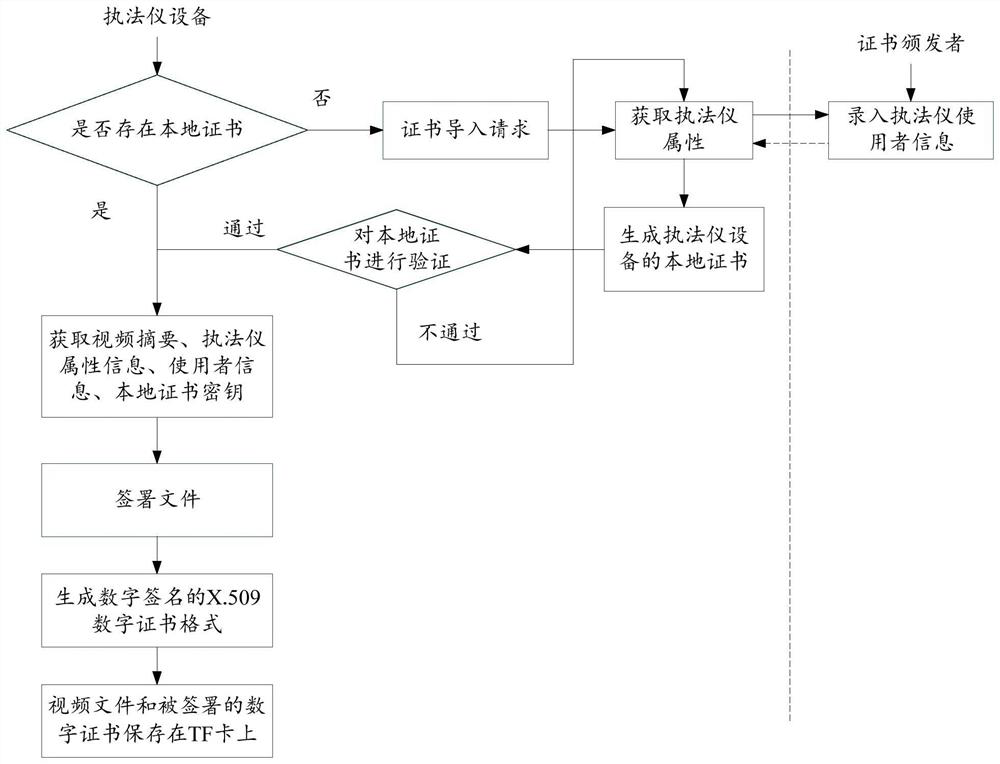
The invention discloses a digital certificate generation method and a digital certificate generation device, and relates to the technical field of Internet security, solving the problem that in related technologies, file information recorded in a law enforcement instrument is poor in security. The method comprises the steps of when the law enforcement instrument does not have a local certificationof law enforcement instrument equipment, sending a certificate import request to a superior system, wherein the certificate import request is used for requesting the superior system to perform digital signature on the law enforcement instrument equipment, and generating the local certificate of the law enforcement instrument equipment; importing the local certificate of the law enforcement instrument equipment which is subjected to digital signature by the superior system into the law enforcement instrument; and performing digital signature on the file information in the law enforcement instrument according to the local certificate of the law enforcement instrument equipment, and generating a digital certificate of the file information in the law enforcement instrument. The method and thedevice provided by the invention are applicable to generating the digital certificate.
Owner:SHENZHEN HUADEAN TECH
Method and device for security verification and repair of hdfs storage platform
ActiveCN110163009BSolve the problem of tamperingGuaranteed reliabilityDigital data protectionFile system administrationSoftware engineeringData node
Owner:BEIJING JIAOTONG UNIV +1
Workflow engine system based on public chain platform and implementation method thereof
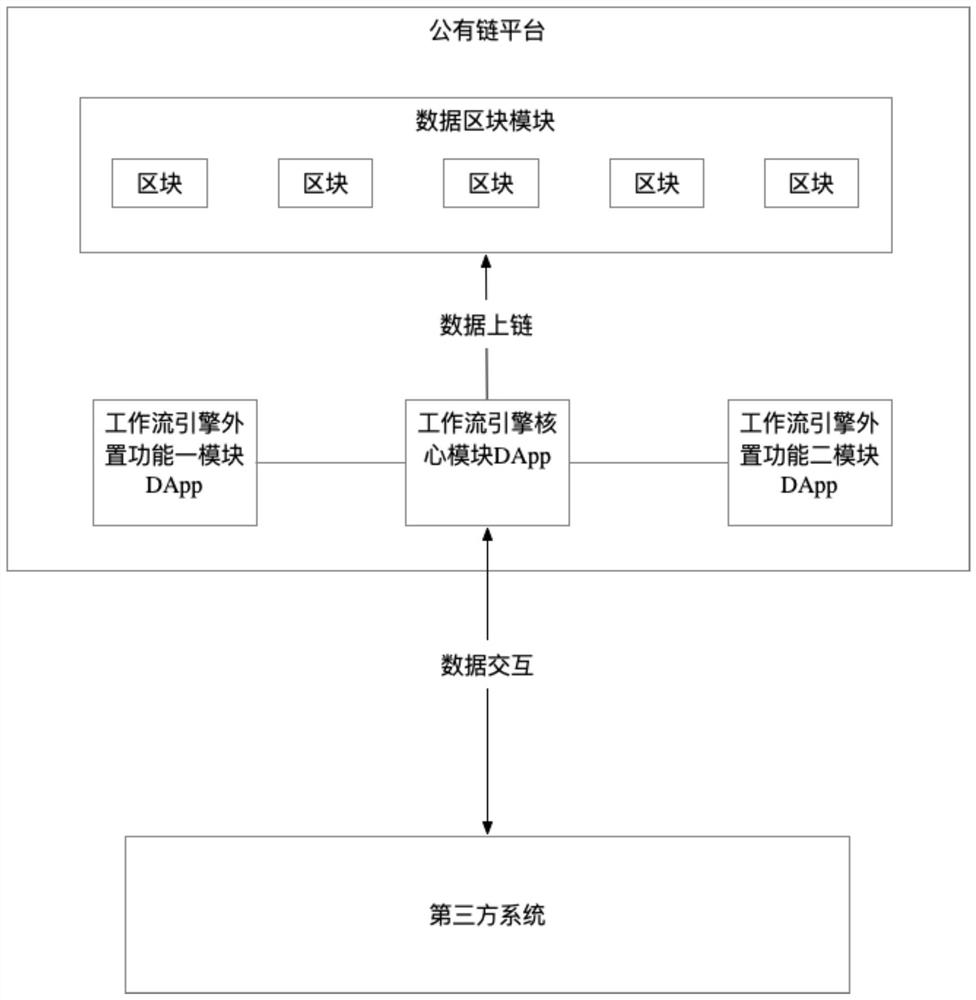
PendingCN112784304ASolve the problem of tamperingImprove authorityDatabase distribution/replicationDigital data protectionThird partyPERQ
The invention provides a workflow engine system based on a public chain platform and an implementation method thereof, and the system comprises: a workflow engine core module DApp which is used for carrying out the structured display of the data content needing to be input by a user, customizing the content of a form according to a business demand, carrying out the uplink of the customized form content, allowing a user to customize a process according to different business logic characteristics, executing process circulation, realizing data interaction with a third-party system, and performing uplink on data generated in the running process of the execution flow circulation; the workflow engine external first function module DApp; the workflow engine external second function module DApp; and the data block module that is used for storing the data and trace data chained on the workflow engine core module DApp. According to the invention, the problem of data loss caused by tampering of database data or attacking of the database by hackers can be avoided, so that the safety of the workflow engine is improved, and meanwhile, the availability of the workflow engine is greatly improved.
Owner:GUANGDONG GUANGYU SCI & TECH DEV
Blockchain-based long-term care insurance implementation method, storage medium and equipment
ActiveCN109785172BEnsure safetyEnsure objectivityFinancePayment protocolsNursing careComputer science
The invention provides a long-term nursing insurance realization method based on a block chain, a storage medium and device. The method comprises the following steps: establishing a long-term nursinginsurance service block chain; automatically distributing the basic information of the insurers who do not collect the physical signs on the long-term nursing insurance service block chain to a manager collection personnel terminal; The administrative organization acquisition personnel terminal acquires physical sign data of the insured person according to the basic information of the insured person; Unrated insurer basic information and the sign data on the long-term nursing insurance service block chain are automatically distributed to a manager rating personnel terminal; the administrativeorganization rating personnel terminal calculates a rating result according to the basic information of the insured person and the sign data; and applying for a long-term nursing service according tothe rating result. The safety and traceability of the long-term nursing insurance service are ensured, the sharing is clear, the objectivity and accuracy of the rating result are ensured, and the userexperience is improved.
Owner:易保互联医疗信息科技(北京)有限公司
WEB server and data protection method thereof
ActiveCN102025492BImprove securitySolve the problem of tamperingUser identity/authority verificationMultiplexerWeb service
The invention provides a WEB server and a data protection method. The WEB server comprises a database used for saving data, a data processing module used for intercepting an operation request for the database, and a terminal-to-computer multiplexer (TCM) chip used for authenticating a sending party of the operation request to obtain an authentication result, wherein the data processing module is also used for performing access operation on the database according to the operation request after the authentication result indicates that the sending party passes the authentication, and returning an access result to the sending party of the operation request. The invention greatly improves the security of the database of the WEB server.
Owner:LENOVO (BEIJING) LTD
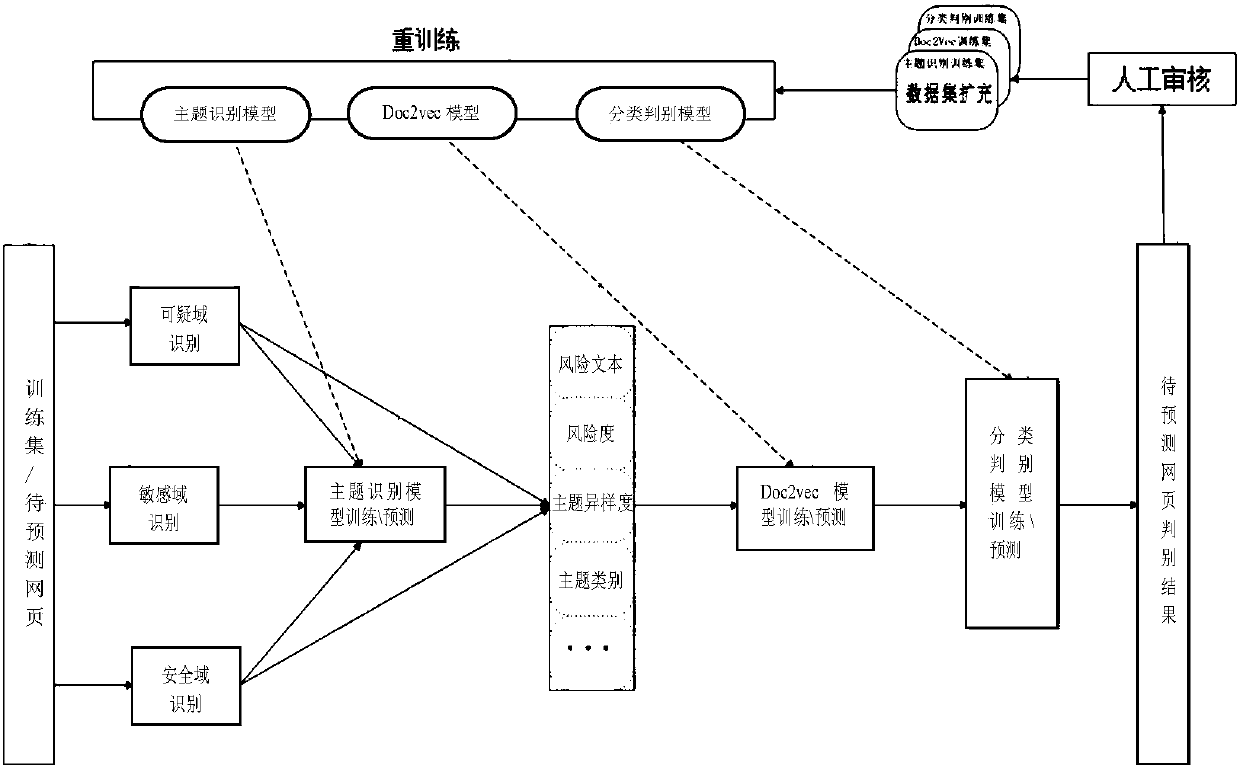
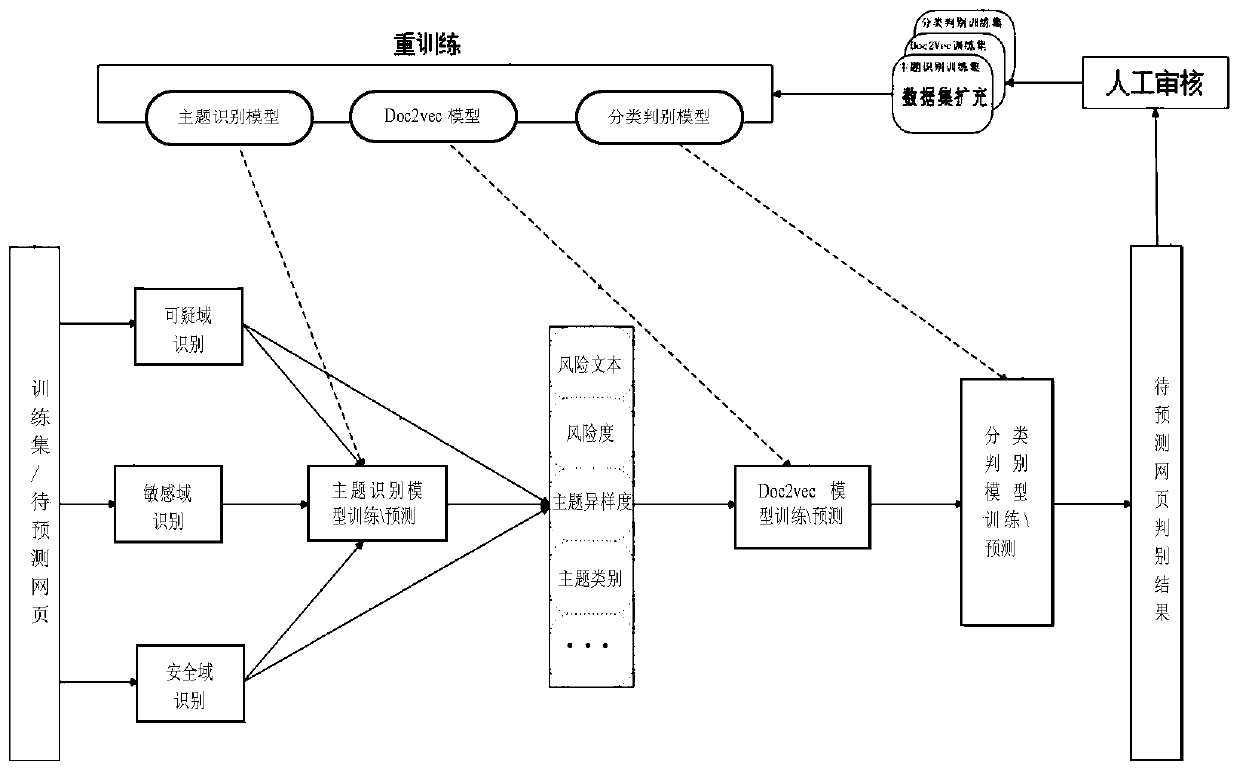
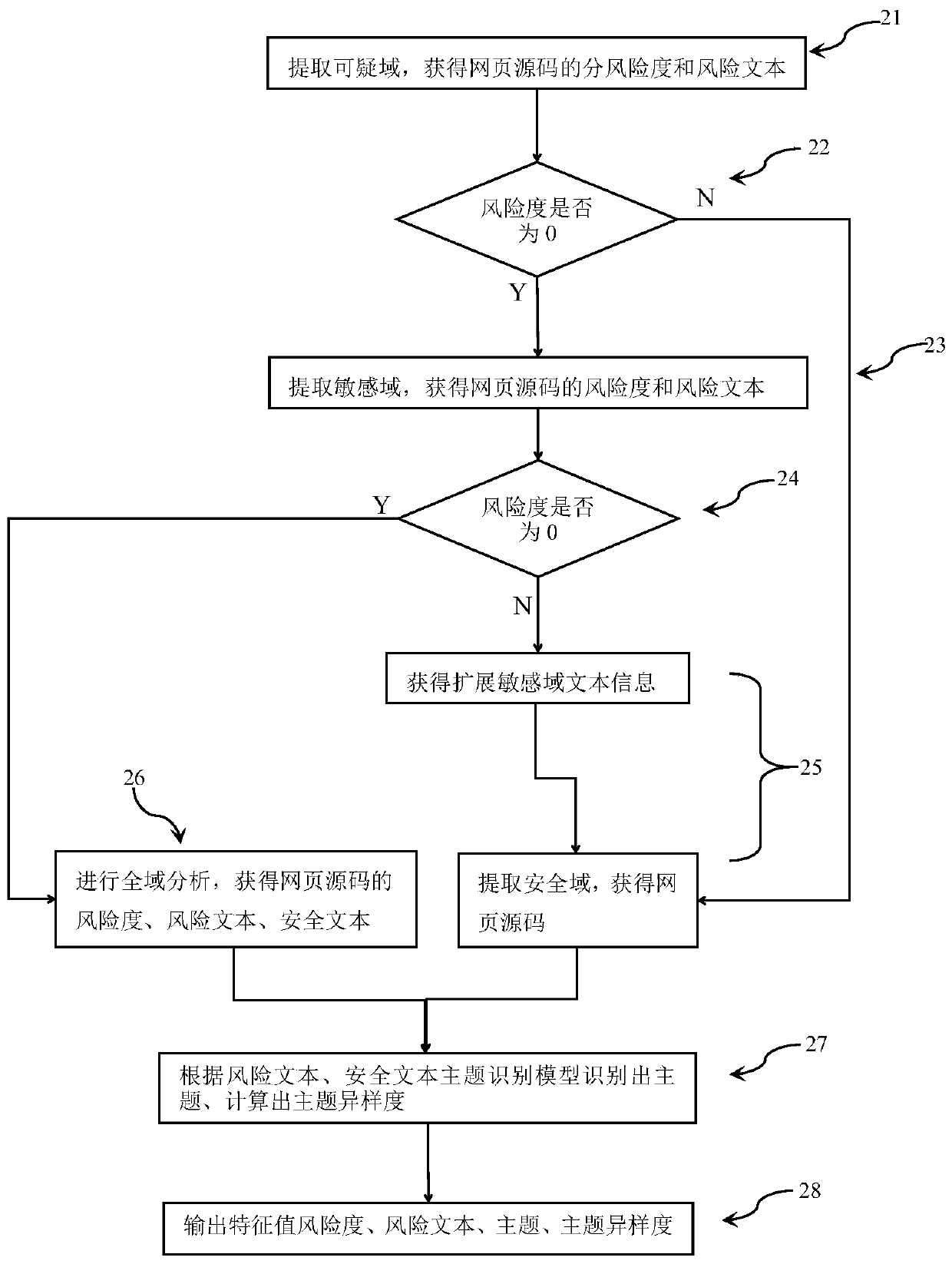
Domain recognition plus topic recognition to build a machine learning model to detect dark links in web pages
ActiveCN107566391BImprove the problem of poor recognition effectSolve the problem of tamperingComputing modelsTransmissionFeature extractionDomain analysis
The invention provides a method for establishing a machine learning model to check webpage hidden links through domain identification and theme identification. The method comprises the steps of collecting a great number of webpage source codes which are marked as the webpage source codes comprising hidden links and the webpage source codes marked as the normal webpage source codes, and forming a training set based on the webpage source codes; extracting a risk text, risk degree, theme difference degree, a theme, a risk text vector, a risk text abnormal probability and the risk text length in each web page source code through suspicious domain identification, sensitive domain identification, secure domain identification, all-domain analysis and theme identification; carrying out model training on characteristic data of all web page source codes in the training set through utilization of a machine learning algorithm, thereby obtaining a classification distinguishing model; and importingthe characteristic data of to-be-predicted web page source codes into the classification distinguishing model, thereby obtaining a result of whether the to-be-predicted web page source codes comprisethe hidden links or not. According to the method, the highly mixed hidden link code identification effect is good, the feature extraction is relatively complete and the problem that a traditional method cannot accurately distinguish the hidden links and page tampering can be solved well.
Owner:上海斗象信息科技有限公司
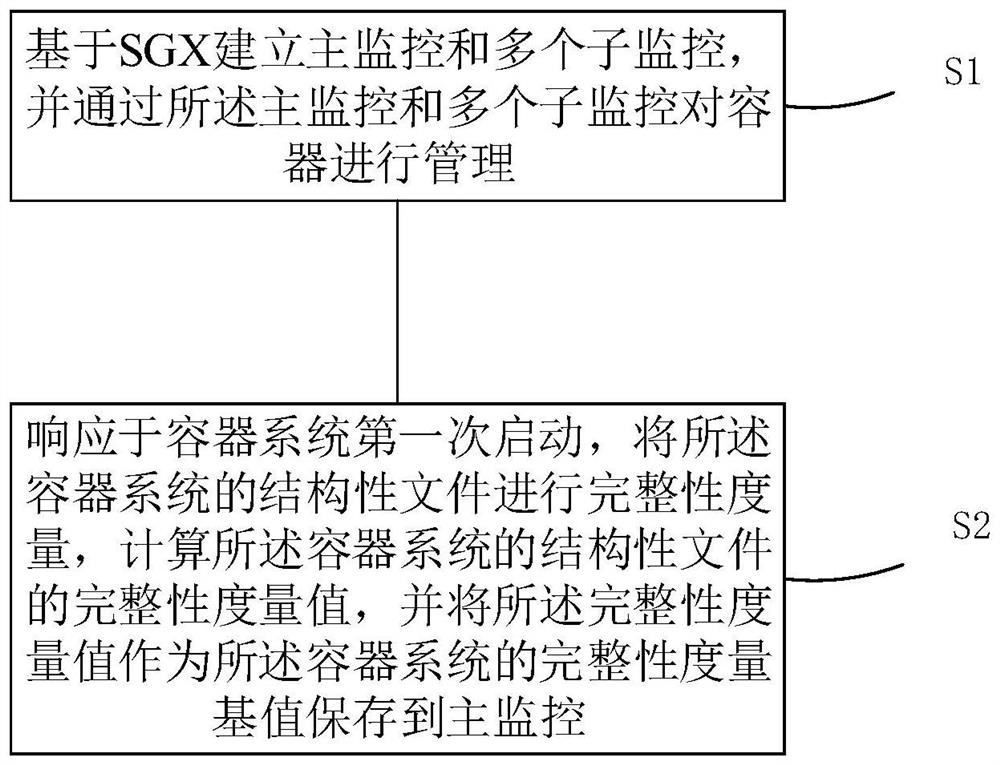
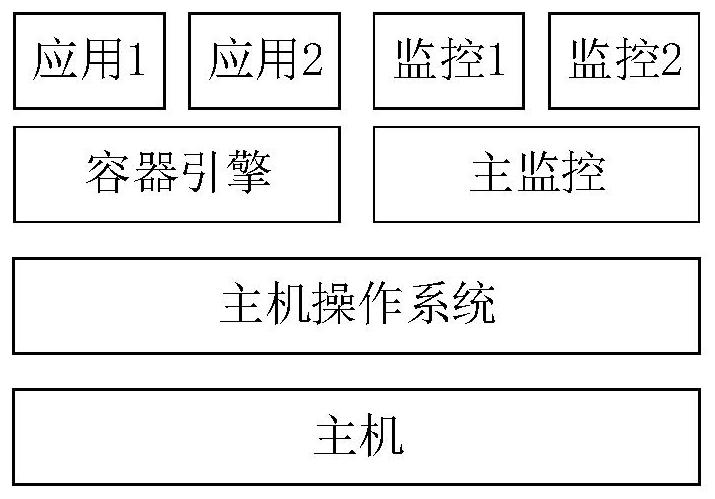
Container security execution method and device and storage medium
PendingCN114662092ASolve the isolation problem between containersSolve the mutual access problemPlatform integrity maintainanceWhitelistCode segment
The invention provides a container security execution method and device and a storage medium, and the method comprises the steps: building a main monitor and a plurality of sub-monitors based on an SGX, and carrying out the management of a container through the main monitor and the plurality of sub-monitors; the method comprises the following steps: in response to the first starting of a container system, carrying out integrity measurement on a structural file of the container system, calculating an integrity measurement value of the structural file of the container system, and storing the integrity measurement value as an integrity measurement base value of the container system to a main monitor. The problem that containers in the same Network Namespace can access each other is solved, the problem of isolation between the containers is solved, and malicious attack behaviors of untrusted containers are prevented by setting a container network white list and limiting the access capability of other containers to the running containers. The problems that the integrity and legality of a code segment and a stack function return address are verified when a container runs, the code segment is tampered when the container runs, and the stack function return address overflows are solved.
Owner:SUZHOU LANGCHAO INTELLIGENT TECH CO LTD
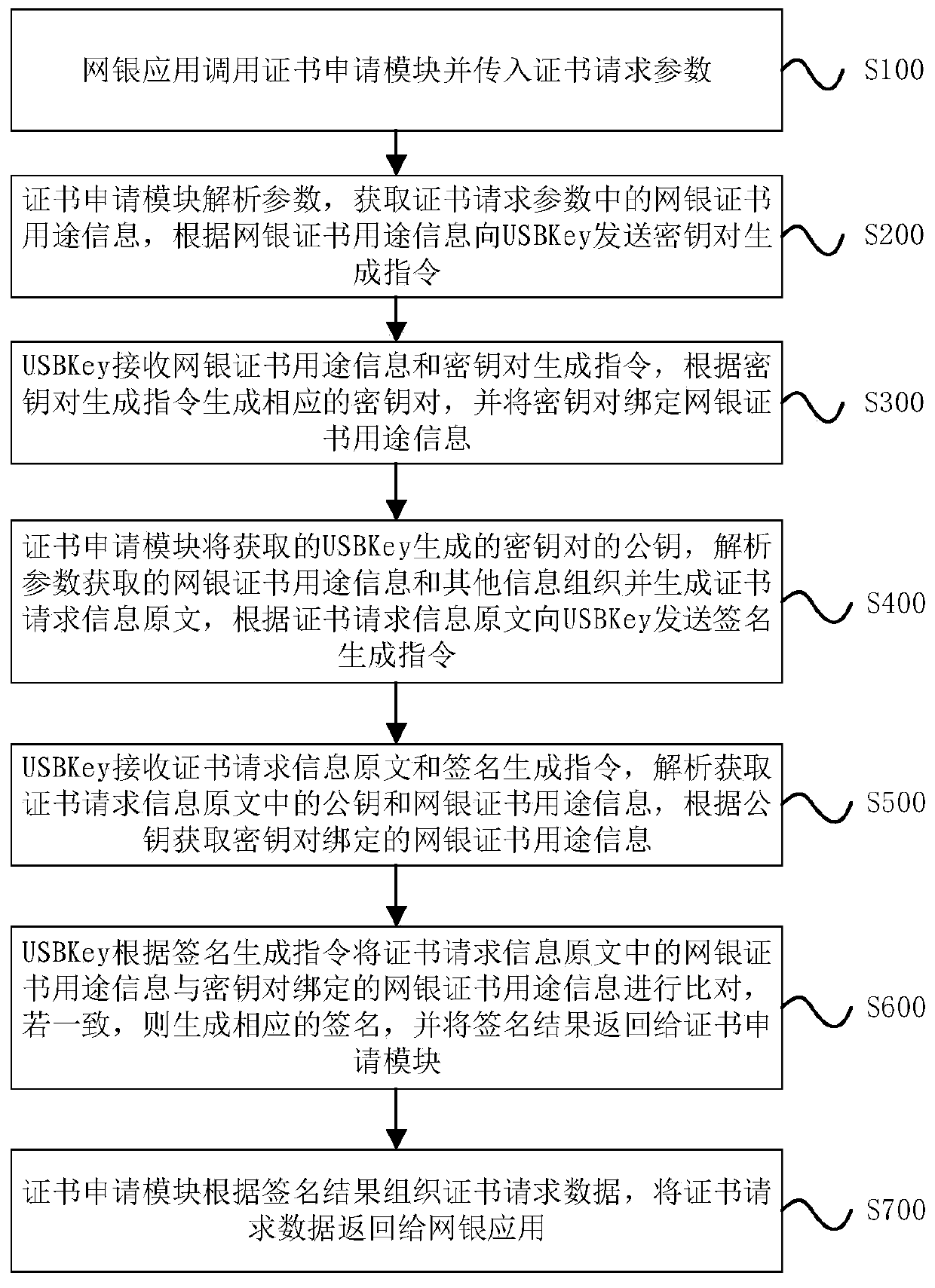
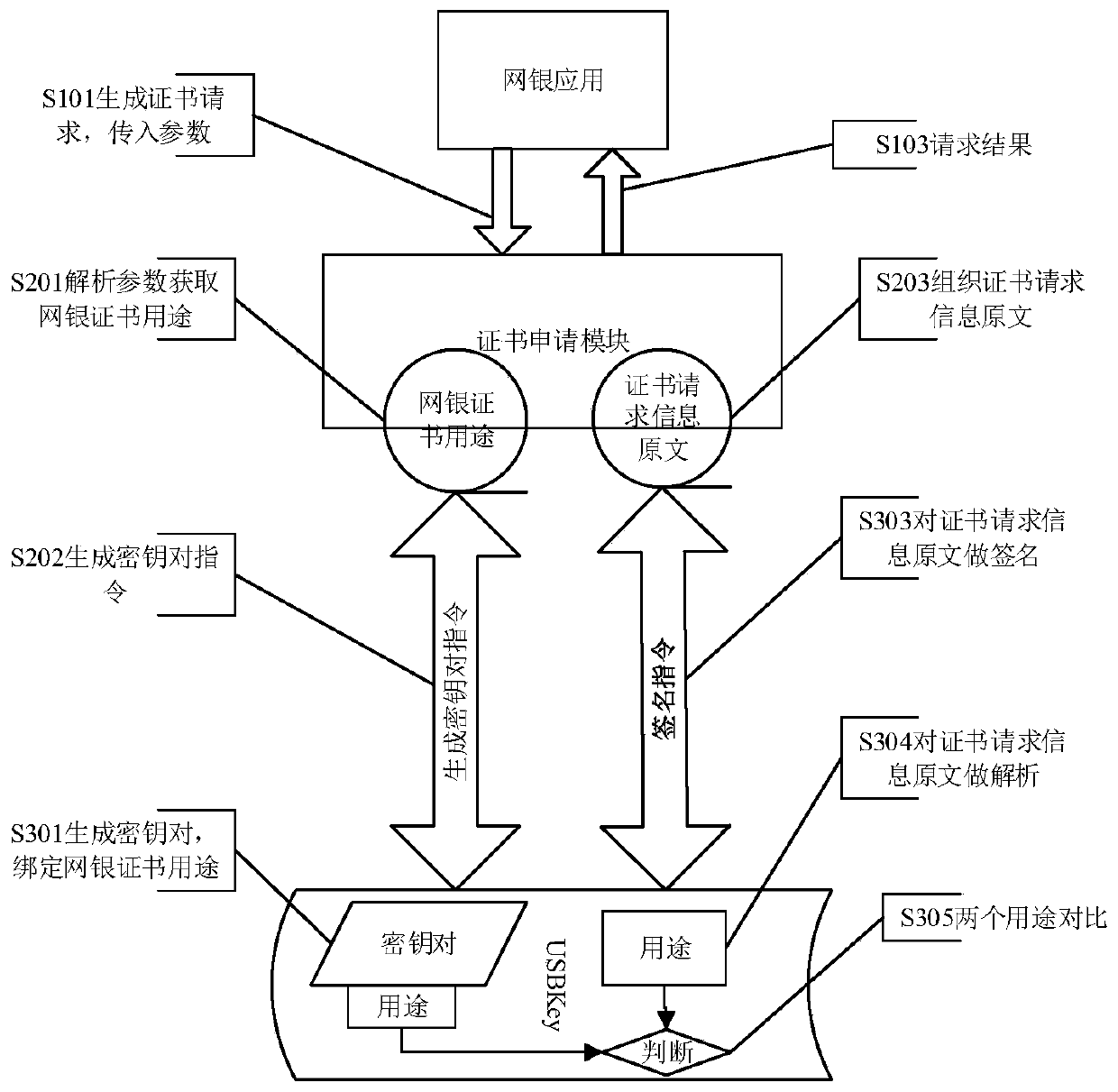
Bank USBKey certificate application tamper-proof protection method and system
PendingCN111049654ASolve the problem of tamperingImprove securityUser identity/authority verificationDigital data protectionInternet privacyEngineering
The invention discloses a bank USBKey certificate application tamper-proof protection method and system. The method comprises the steps that S100, an online banking application calls a certificate application module and transmits certificate request parameters; S200, the certificate application module acquires online banking certificate purpose information in the certificate request parameters andsends a key pair generation instruction to the USBKey; s300, the USBKey generates a corresponding key pair according to the key pair generation instruction, and binds the key pair with online bankingcertificate purpose information; s400, the certificate application module sends a signature generation instruction to the USBKey; s500, the USBKey analyzes and acquires a public key and E-bank certificate purpose information in the certificate request information original text, and acquires the E-bank certificate purpose information bound with the key pair according to the public key; s600, the USBKey compares the E-bank certificate purpose information in the certificate request information original text with the E-bank certificate purpose information bound with the key pair; and S700, the certificate application module organizes certificate request data and returns the certificate request data to the online banking application. According to the invention, the problem that the online banking certificate is tampered in the certificate issuing process can be solved.
Owner:WATCHDATA SYST
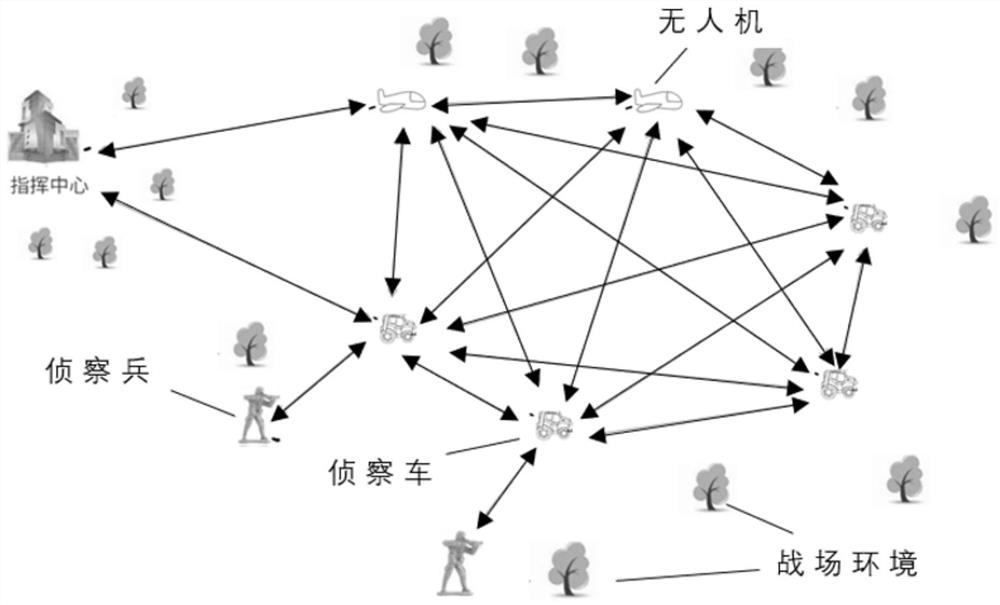
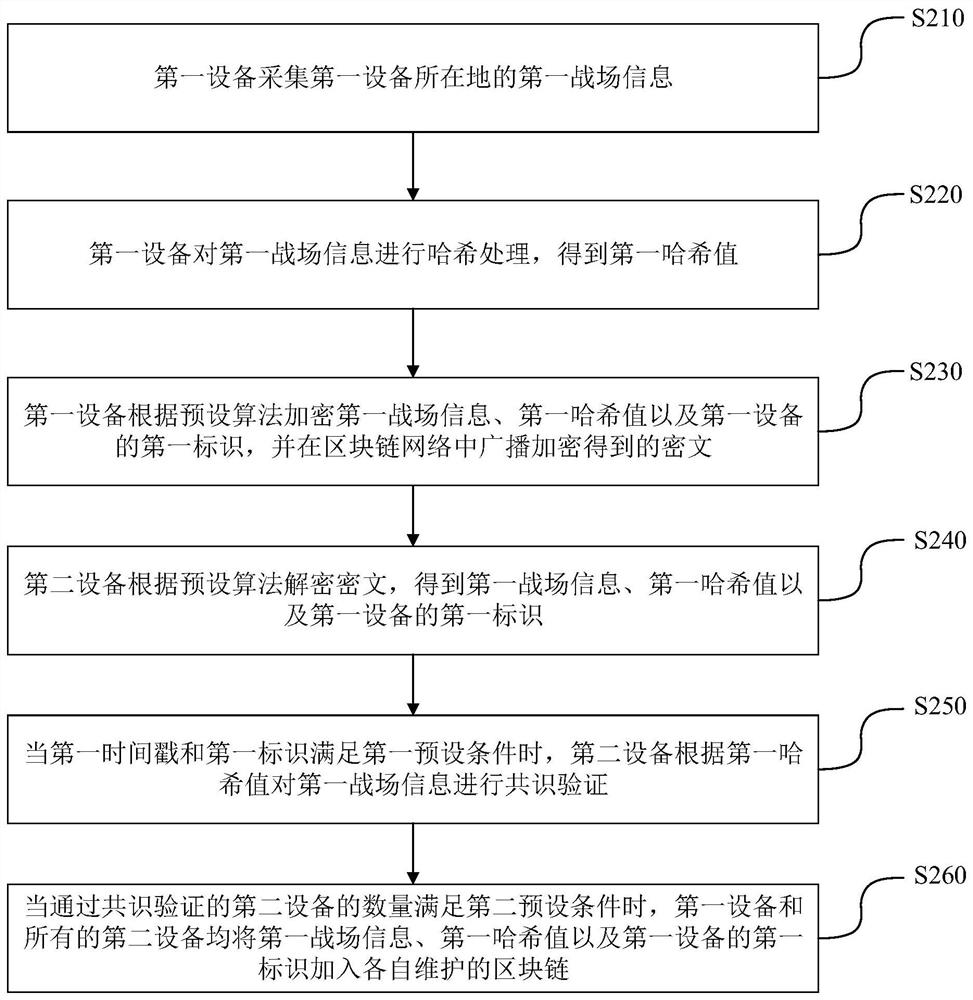
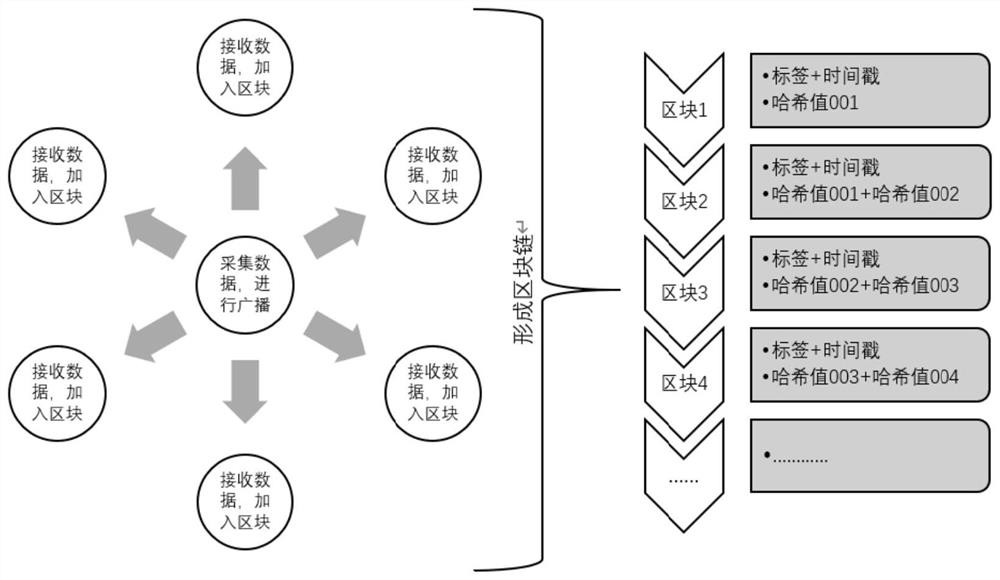
Battlefield situation awareness method and system and terminal equipment
ActiveCN112989392AStrong anti-strike abilitySolve the problem of tamperingDigital data protectionCiphertextTerminal equipment
The invention is suitable for the technical field of electronic information, and provides a battlefield situation awareness method and system and terminal device. The method comprises the steps that first equipment collects first battlefield information of the place where the first equipment is located; the first device performs hash processing on the first battlefield information to obtain a first hash value; the first device encrypts the first battlefield information, the first hash value and a first identifier of the first device according to a preset algorithm, and broadcasts a ciphertext obtained by encryption in the block chain network; the second device decrypts the ciphertext according to the preset algorithm; and when the number of the second devices passing the consensus verification meets a second preset condition, the first device and all the second devices add the first battlefield information, the first hash value and the first identifier of the first device into respective maintained block chains. According to the invention, the data security of the battlefield situation awareness system can be improved.
Owner:HEBEI UNIVERSITY OF SCIENCE AND TECHNOLOGY
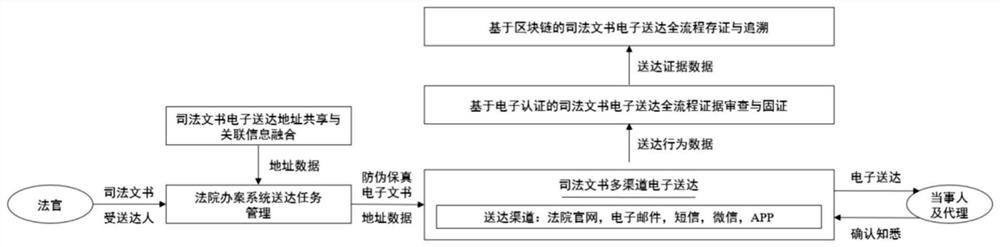
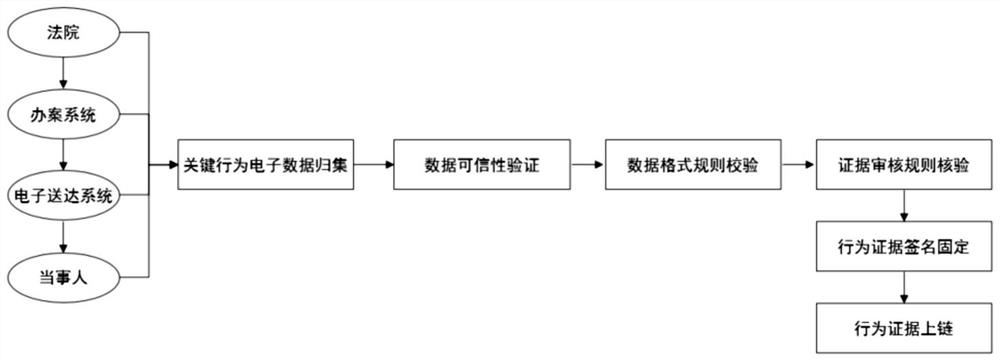
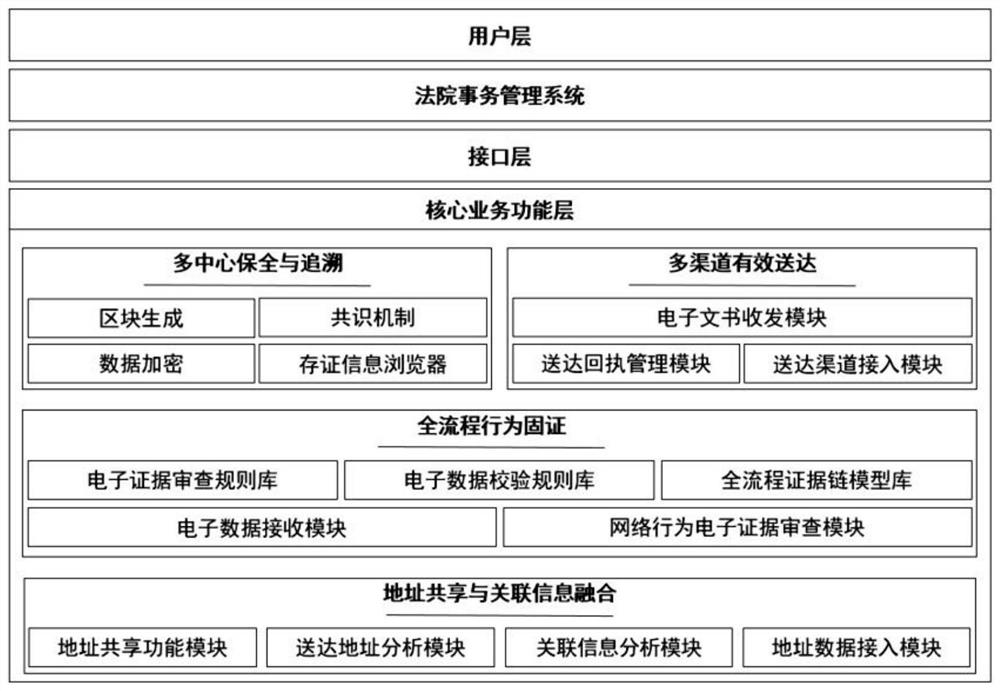
Block chain-based judicial electronic delivery management method and system
ActiveCN113438090ASolve the problem of difficult deliveryShare high securityData processing applicationsUser identity/authority verificationInformation sharingEngineering
The invention provides a block chain-based judicial electronic delivery management method and system. The method comprises the following steps: 1, uploading a judicial document in an electronic format to a court system; 2, encrypting and storing the judicial document at a server side by using the identity label of the addressee; 3, the court system searching the matched address data according to the identity label of the addressee, and achieving the address information sharing; 4, sending the encrypted electronic judicial document to the party through the shared address information; 5, the party receiving the electronic judicial document and then returns a delivery receipt; 6, collecting electronic data in the electronic delivery process, constructing electronic evidence of the whole process behavior, and completing authenticity examination and evidence fixation; and 7, subjecting the fixed electronic evidence to uplink evidence storage for sharing and tracing of each court node. According to the invention, by adopting the information association fusion technology of the multi-source address base, the addressee is positioned to the greatest extent, and the problem of difficulty in delivery is solved.
Owner:SHANGHAI WANXIANG BLOCK CHAIN CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com