Multimedia data encryption and decryption method and device
A technology for multimedia data and multimedia data packets, applied in the network field, can solve problems such as stealing and encryption key tampering, and achieve the effects of ensuring security, improving security, and increasing difficulty.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] In order to make the above objects, features and advantages of the present invention more comprehensible, the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
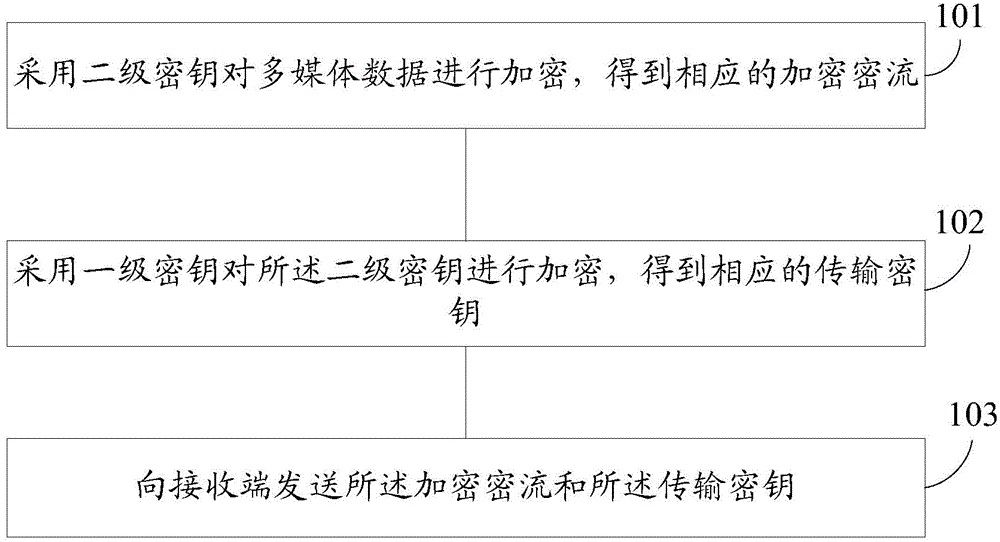
[0046] In the Internet environment, multimedia data may be intercepted by hackers during network transmission, resulting in theft or tampering of the multimedia data. For example, in a video conference, audio and video streams may be intercepted by hackers in the network and thus Restoring meeting content, especially for confidential meetings, will seriously affect the security of its meeting content transmission.
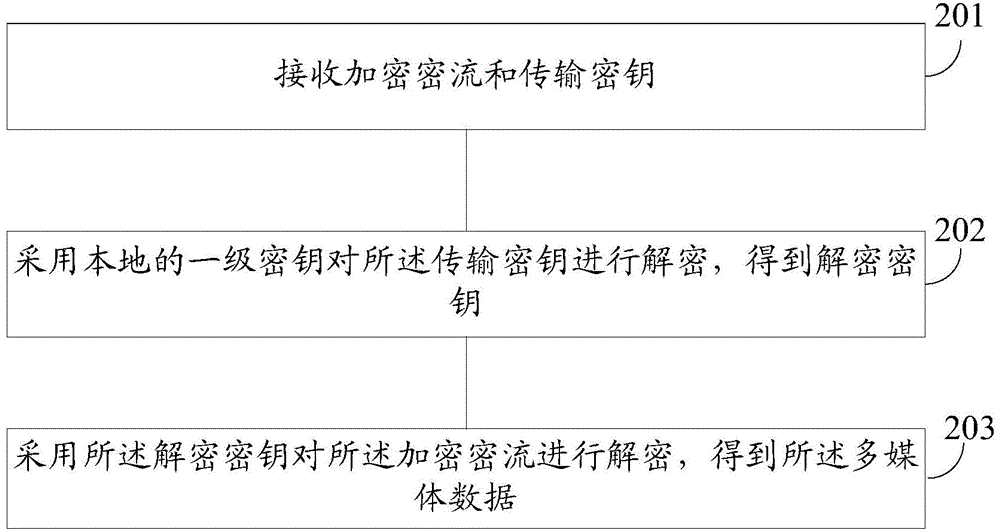
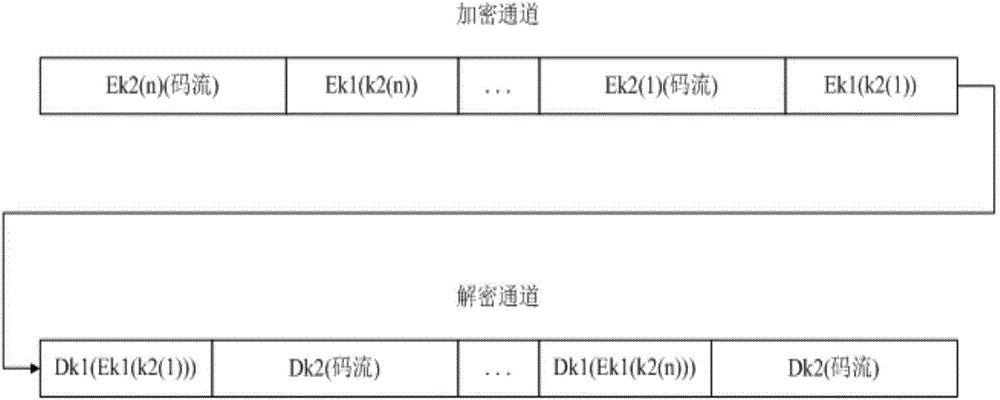
[0047] The invention provides a method for encrypting multimedia data, which uses a secondary key to encrypt multimedia data to obtain a corresponding encrypted stream; the secondary key is encrypted by an external primary key input through the RS232 serial port, Obtain the corresponding transmission key; since the enc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com