Patents
Literature
61results about How to "Reduce the possibility of counterfeiting" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
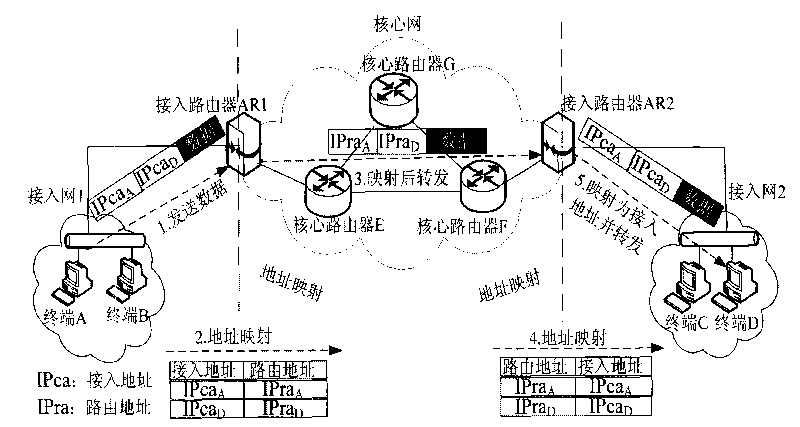
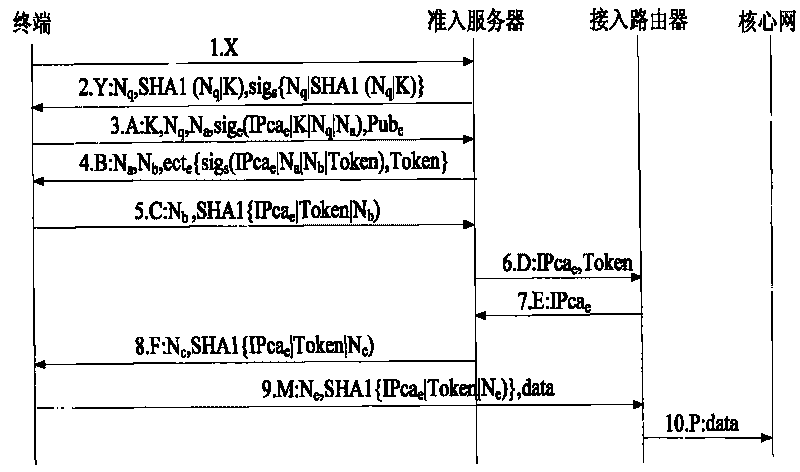
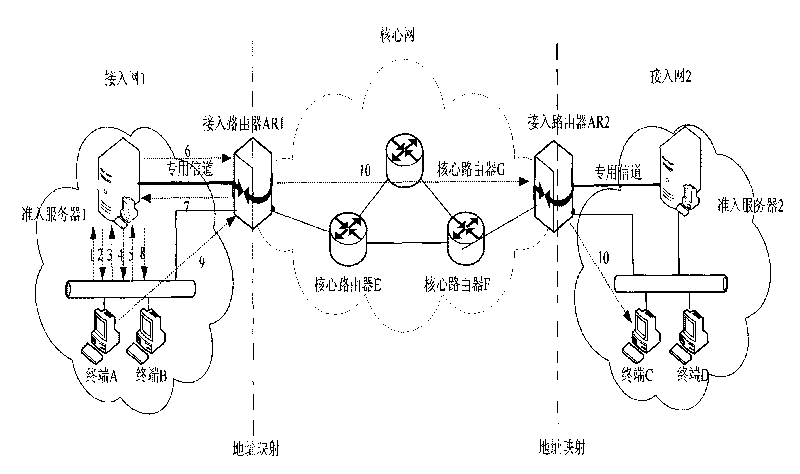
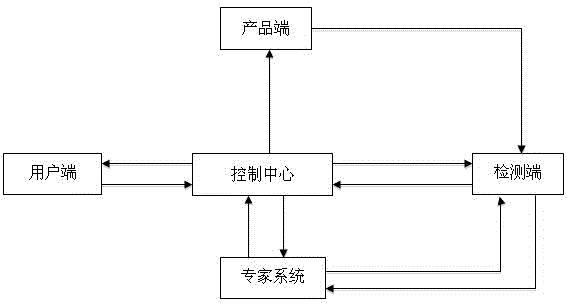
Safety access system and method for guaranteeing source address authenticity by using token mechanism
InactiveCN101729568APrevent replay attacksEfficient authenticityTransmissionAccess networkAccess method
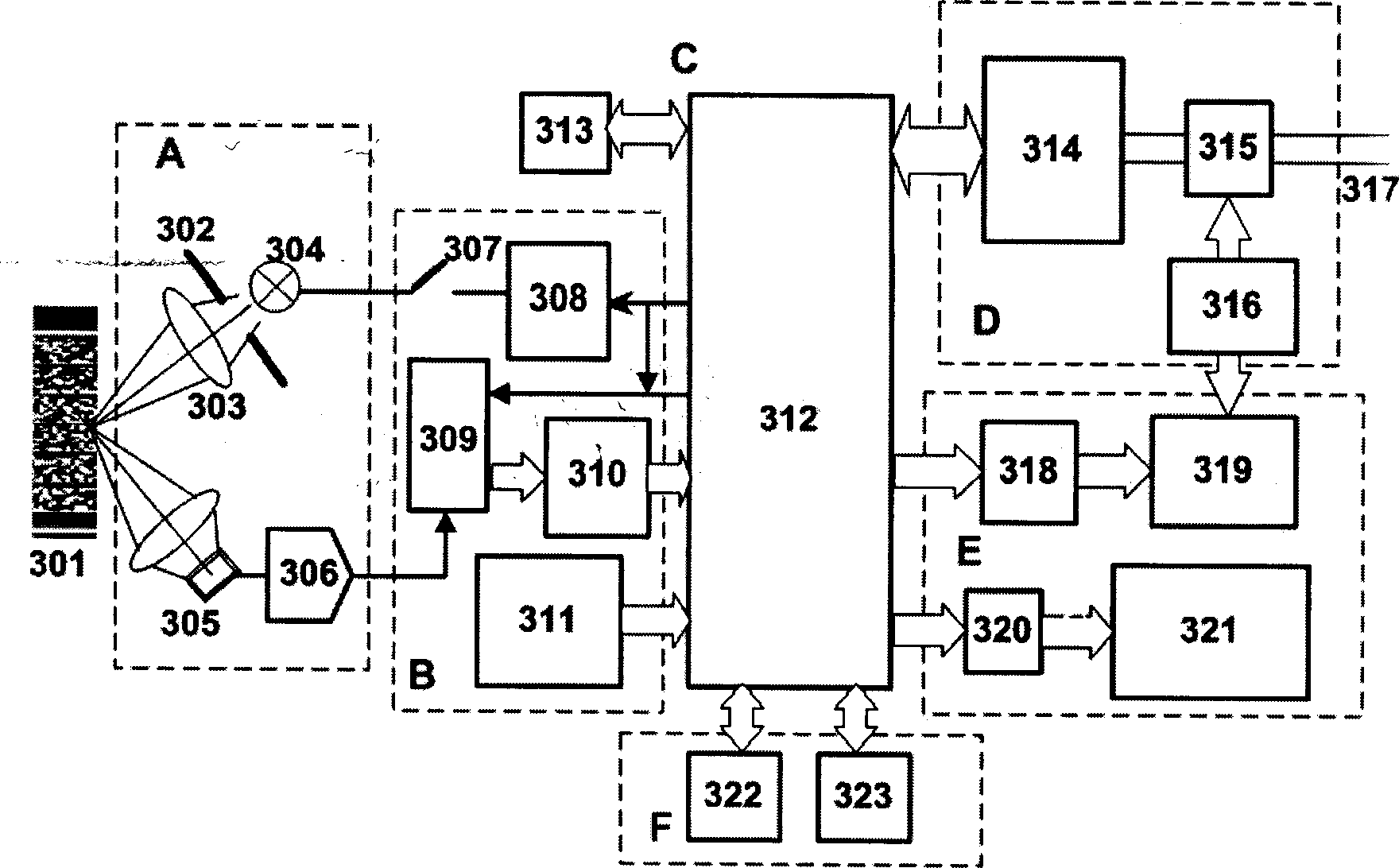
The invention provides safety access system and method for guaranteeing the source address authenticity by using a token mechanism. An admission server is arranged in an access network of an address separation mapping network, an access consultation module and a data packet verification module are arranged on an access router, an address client software module is arranged on a terminal, and the safety access method used for accessing is designed so as to achieve the aim of guaranteeing the source address authenticity in the address separation mapping network. According to the method, the terminal safely acquires a unique token which is bound to an access address so that the access address is in one-to-one correspondence with the token; the access router creates a (terminal access address, token) table which is used for verifying the binding relation between the terminal access address and the token; the admission server creates a (a terminal access address, a terminal public key) table, the admission server sends a challenge demand when the terminal requests to be accessed, and which both resist the DoS attack to the admission server to a very great extent.
Owner:BEIJING JIAOTONG UNIV
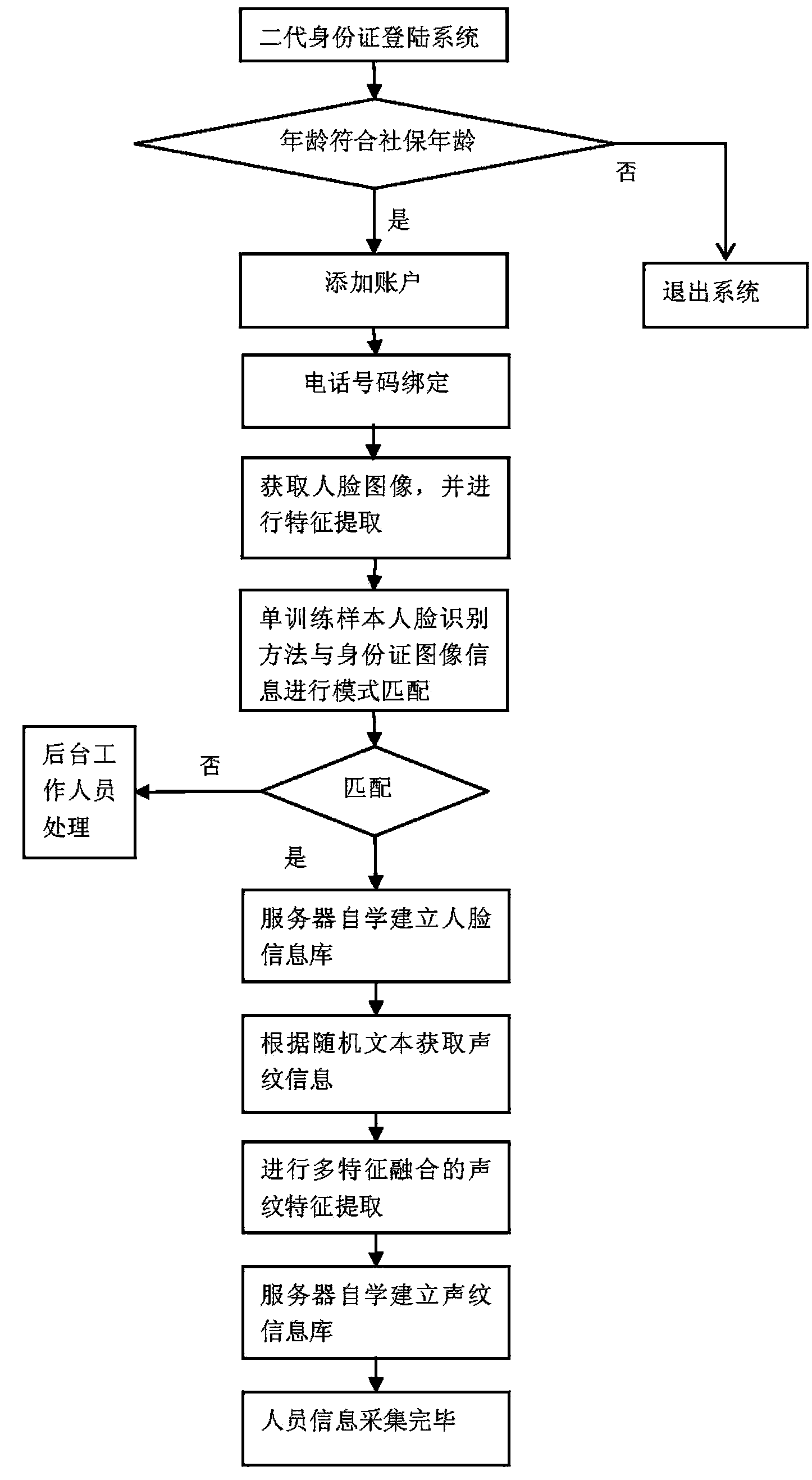
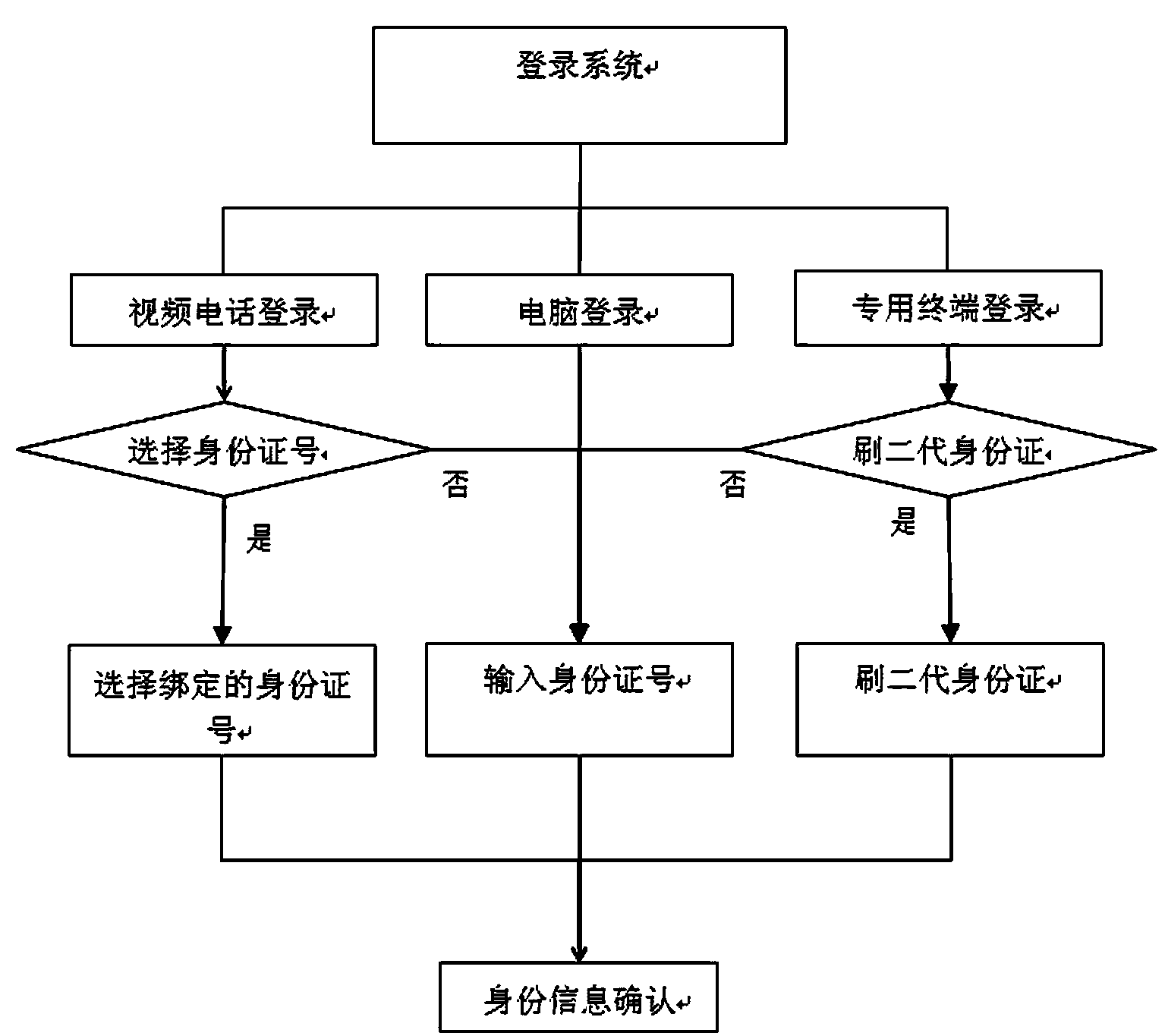
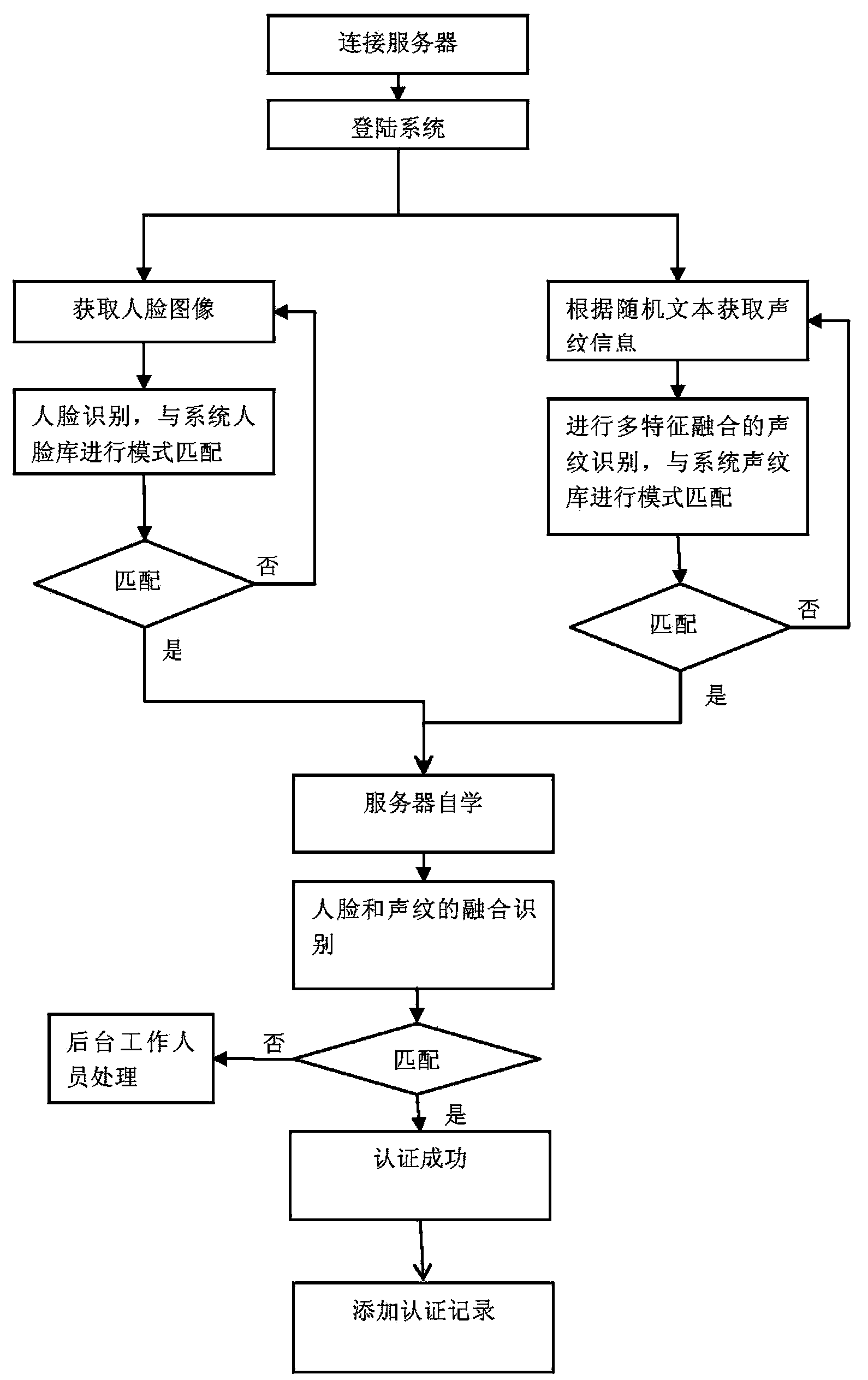
Survival authentication method on basis of identification cards and composite biological feature recognition
InactiveCN103634118AImprove remote identityImprove efficiencyUser identity/authority verificationCharacter and pattern recognitionFeature recognitionAuthentication
The invention discloses a survival authentication method on the basis of identification cards and composite biological feature recognition. The survival authentication method has the advantages that personnel is recognized by the aid of server clusters, computation resources can be integrated, accordingly, artificial auditing can be omitted, and the remote personnel identification and survival authentication efficiency can be improved; human faces and voiceprints are recognized, composite recognition of the human faces and composite recognition of the voiceprints are combined with each other, the survival of the personnel can be effectively recognized, and accordingly the counterfeiting probability can be reduced.
Owner:神思依图(北京)科技有限公司
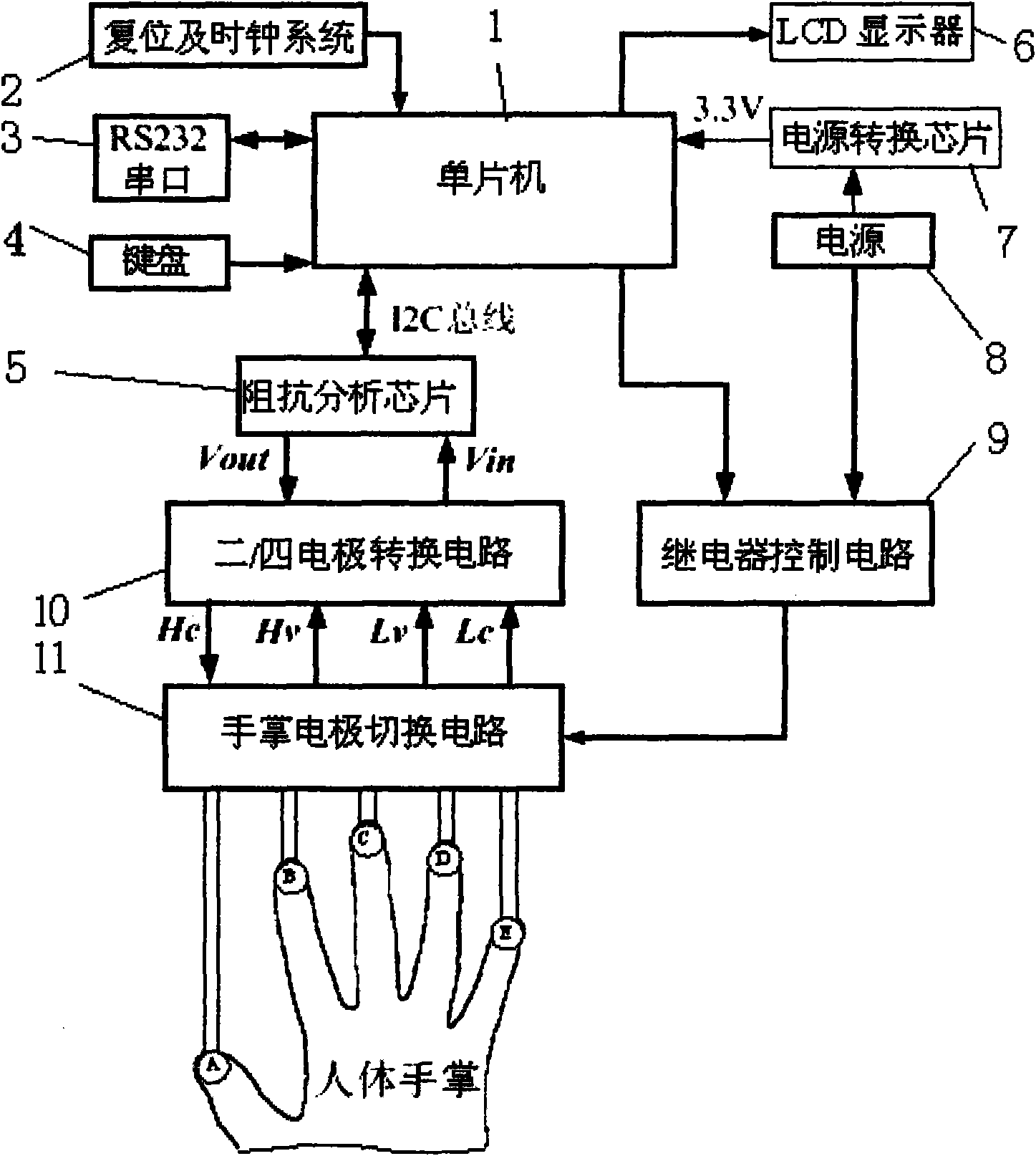
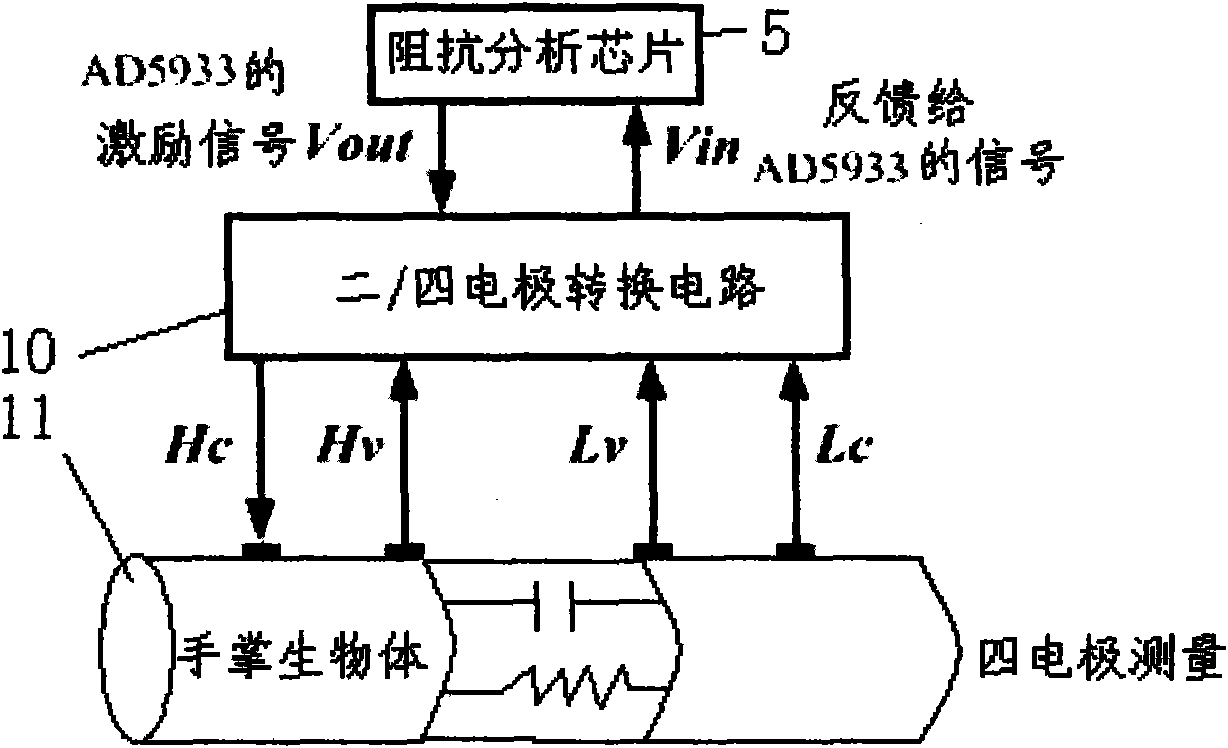
Palm bioelectrical impedance spectrum measuring device for biological characteristic recognition
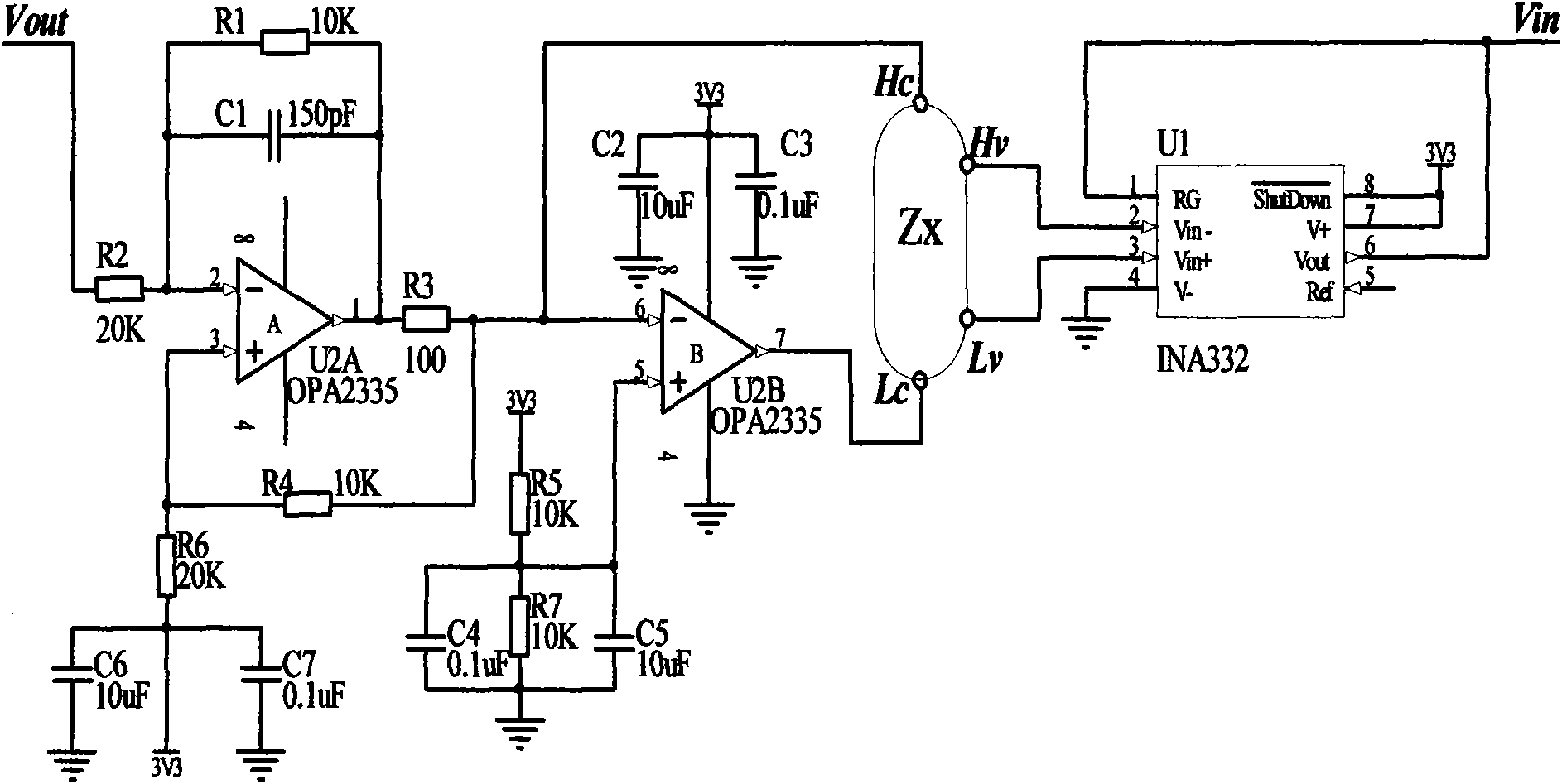
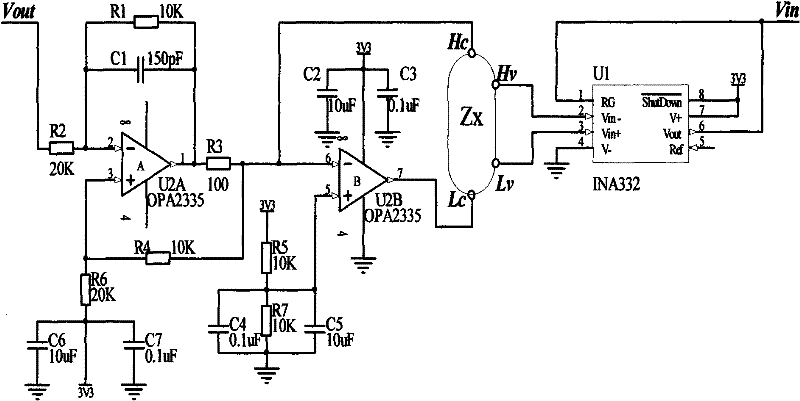
InactiveCN101889866ALow costNo light conditionsPerson identificationSensorsMicrocontrollerElectricity
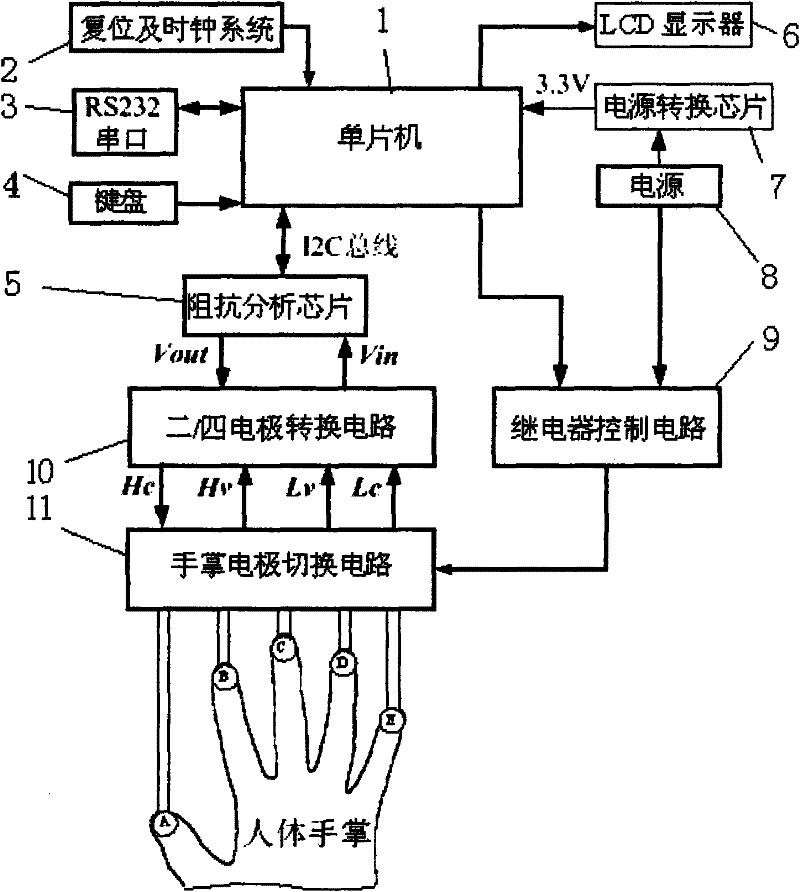
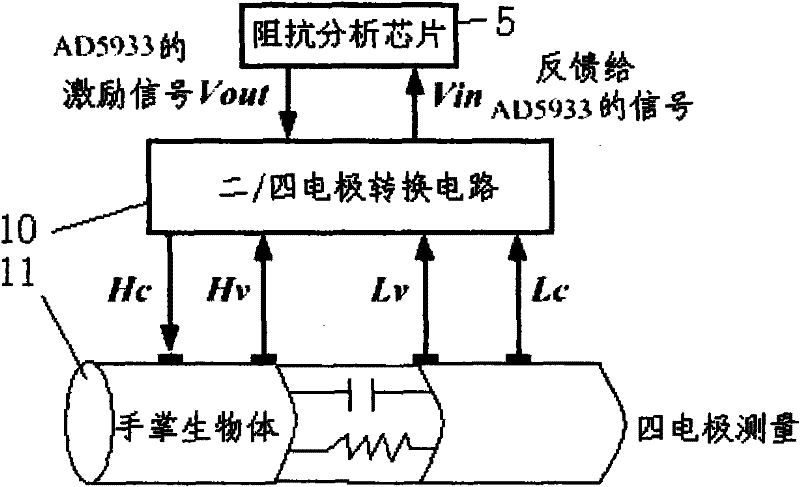
The invention discloses a palm bioelectrical impedance spectrum measuring device for biological characteristic recognition. The device comprises a singlechip which is respectively connected with a reset and clock system, an RS232 serial port, a keyboard, an impedance analyzing chip, an LCD display, a power conversion chip and a relay control circuit; a 5V power supply is arranged between the power conversion chip and the relay control circuit; the impedance analyzing chip is connected with a two / four-electrode conversion circuit; the two / four-electrode conversion circuit and the relay control circuit are respectively connected with a palm electrode switching circuit; and in the circuit of the palm electrode switching circuit, the output ends of four relays J1-J4 are respectively connected with HC and HV, and the output ends of another four relays are respectively connected with LV and LC. The palm biological impedance spectrum measuring device realizes four-electrode measurement of ten loops by opening and closing the eight relays, acquires sample data and is applicable to the biological characteristic recognition.
Owner:XIAN UNIV OF TECH
Hand-write input discriminator, method and medium for storing hand-wirte input discriminating program
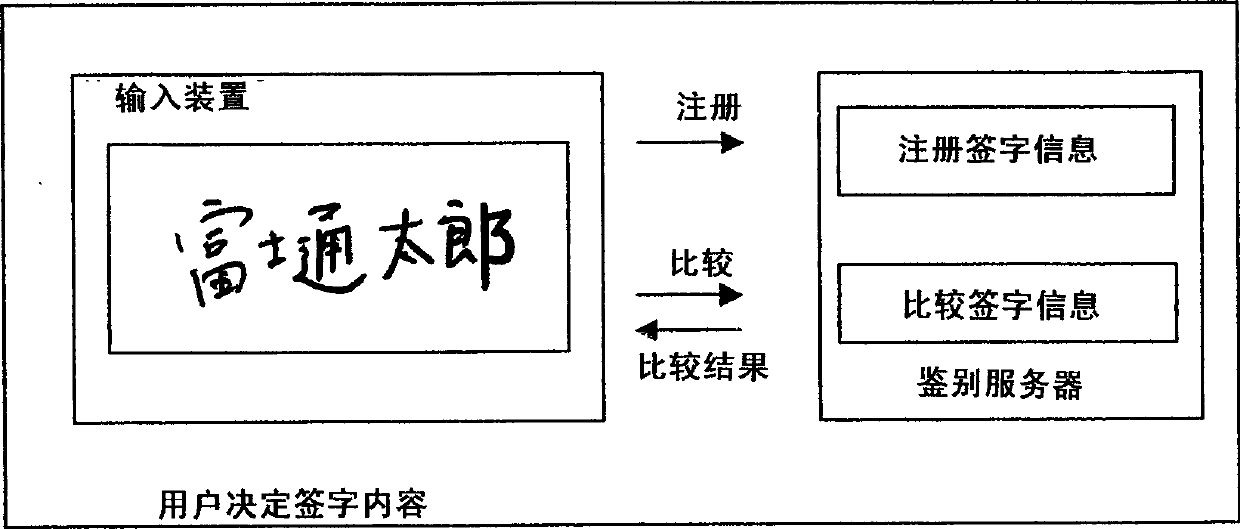
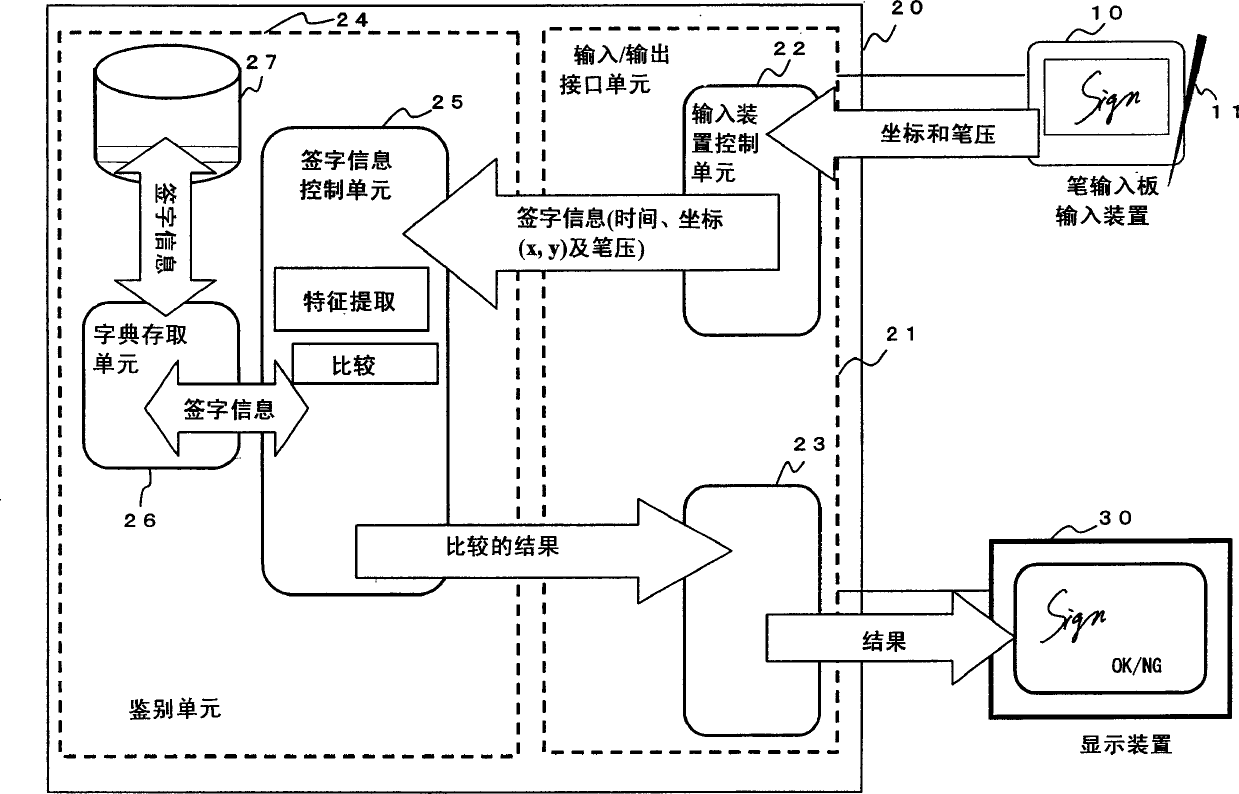
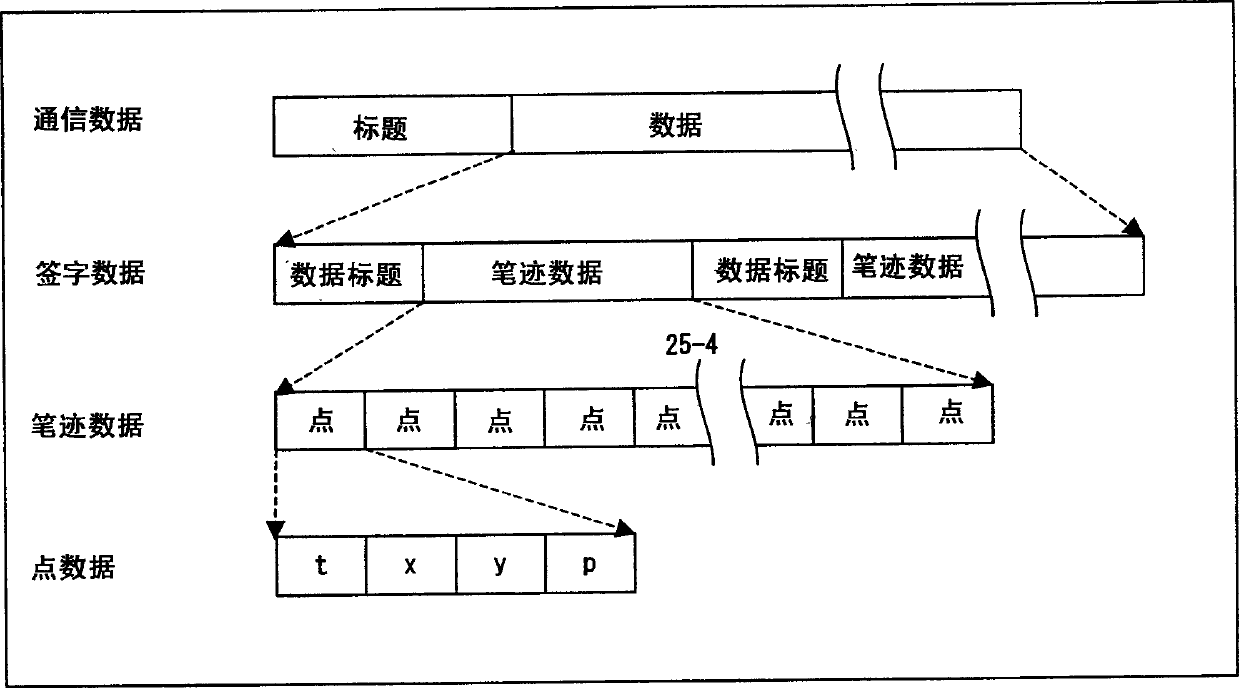
InactiveCN1445654AReduce the possibility of counterfeitingSmall sizeInput/output for user-computer interactionImage analysisHandwritingDiscriminator
The application discloses a handwriting input identification device, a method and a medium storing a handwriting input identification program. When registering a user's signature, an authentication server presents a password to the user. When the user handwrites the password with the input device, the password and handwritten signature information are registered in a dictionary. During authentication, the authentication server requires the user to write the password by hand. When the user writes the password by hand in response to the request, the signature information control unit compares the signature information newly handwritten by the user with the signature information registered in the dictionary, and outputs a result of the comparison.
Owner:FUJITSU LTD
Anti-counterfeiting off-site commodity transaction method and system
InactiveCN103489121AReduce the possibility of counterfeitingProduction real-time monitoringBuying/selling/leasing transactionsPersonalizationTransport system
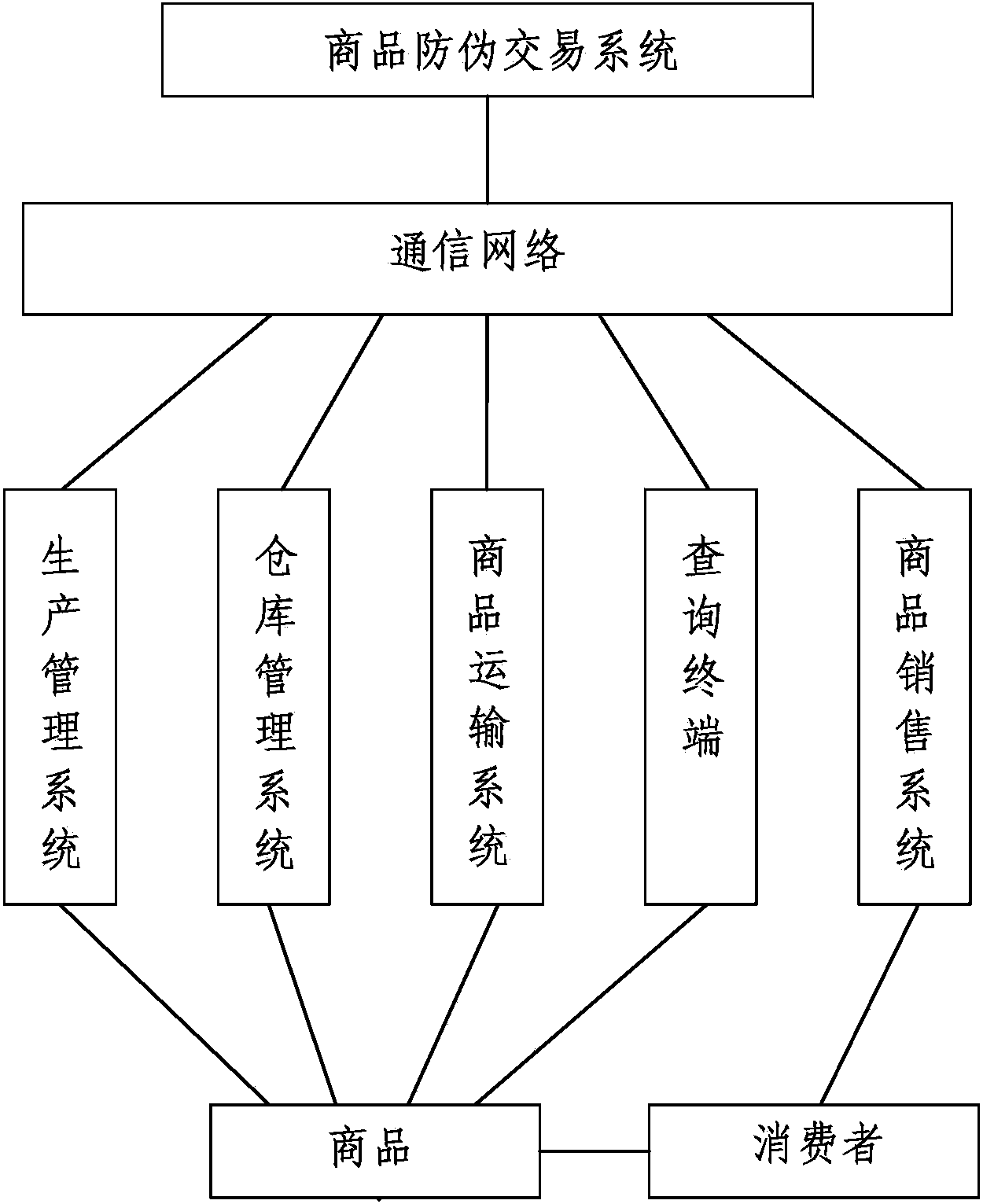
The invention discloses an anti-counterfeiting off-site commodity transaction method and system. According to the anti-counterfeiting off-site commodity transaction method and system, an anti-counterfeiting commodity transaction network formed by an anti-counterfeiting commodity transaction system, a production management system, a commodity sales system, a storehouse management system and a commodity transporting system is established, a string of user-defined anti-counterfeiting information set by a consumer runs through the whole commodity circulation process, only the final consumer can identify the authenticity of a commodity by verifying the anti-counterfeiting information, and the probability of counterfeiting of the commodity is reduced; a barcode, personalized information and a logistics barcode are bound with an order, real-time monitoring of production, storage and circulation of the commodity is achieved, planning management and dispatching are achieved, working efficiency is improved, and meanwhile tracking of the commodity is achieved. According to the anti-counterfeiting off-site commodity transaction method and system, counterfeiting and adulteration of the commodity in the tail stage of circulation are eliminated for the final consumer. The anti-counterfeiting off-site commodity transaction method and system are suitable for but not limited to off-site shopping such as online shopping and teleshopping.
Owner:JINAN SHANHE ENVIRONMENT SCI & TECH CO LTD
A method for establishing an overseas purchasing platform based on a block chain technology
InactiveCN109325830AReduce the possibility of counterfeitingShopping with confidenceFinanceBuying/selling/leasing transactionsThird partyLogistics management
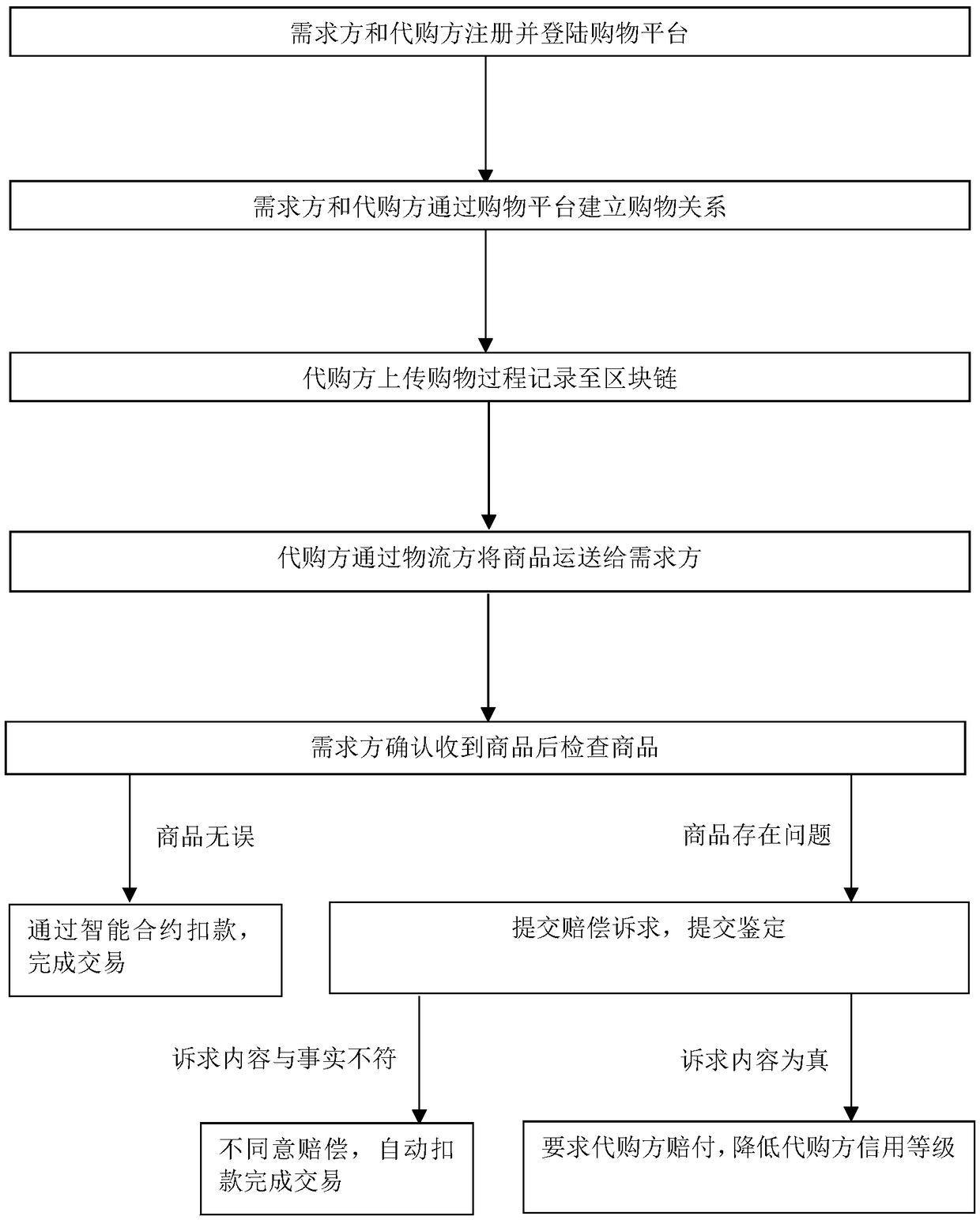
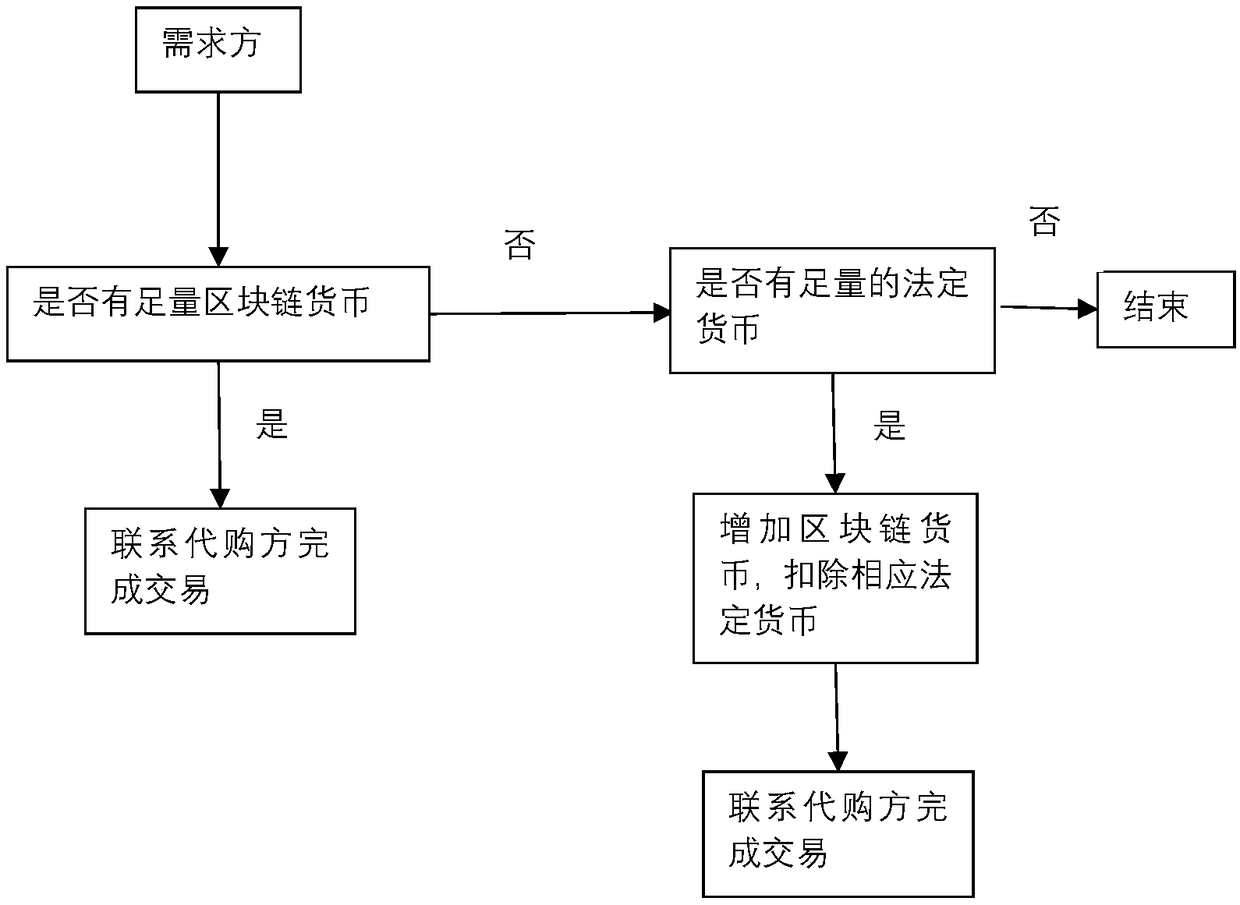
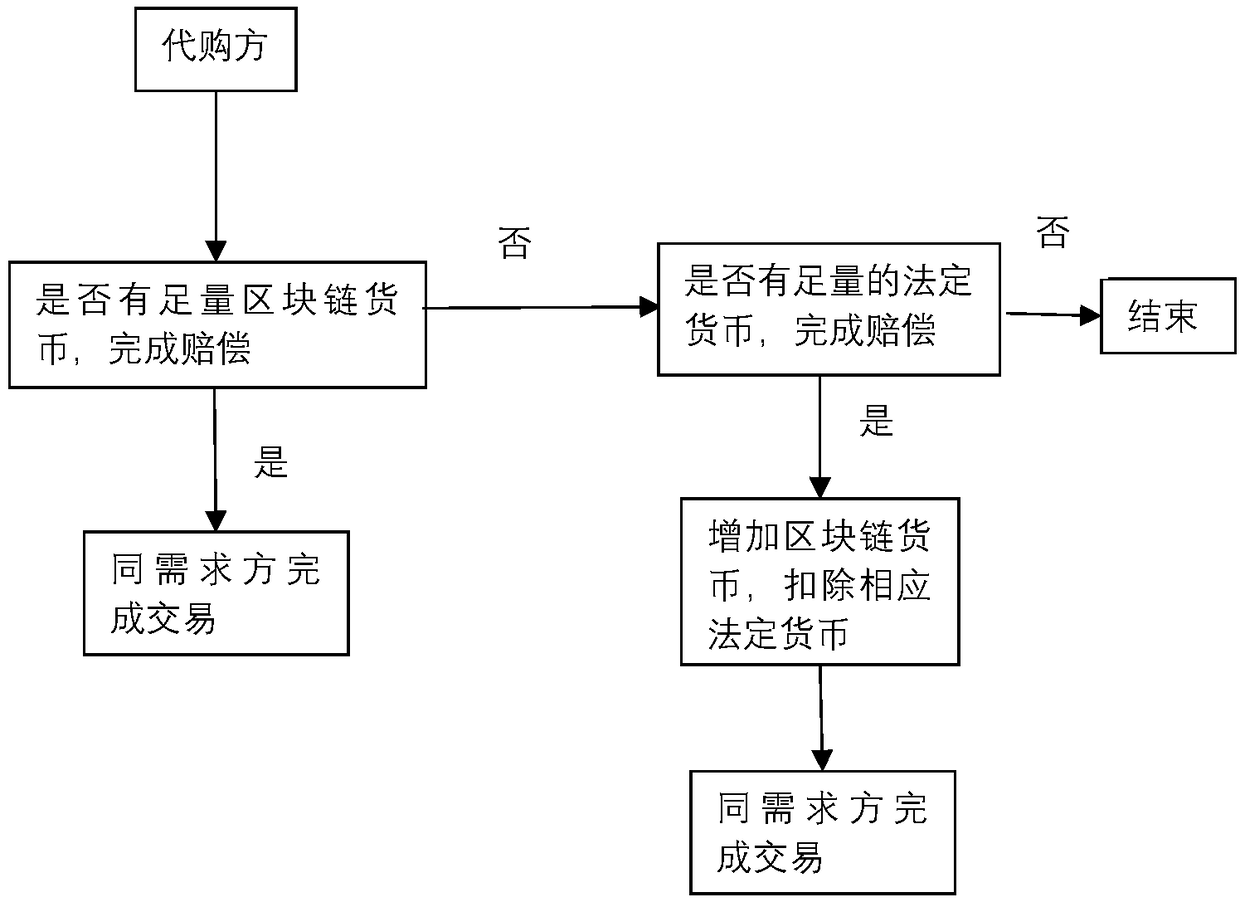
The invention relates to a method for establishing an overseas purchasing platform based on block chain technology, belonging to the field of electronic commerce. The method comprises the following steps of S1 enalbing a demander and a purchasing agent to register and log in the platform, binding a bank account, establishing a block chain currency account, associating a bank account and a block chain account; S2 establishing the shopping relationship between the demander and the agent through the platform; 3 recording and uploading the purchase process to the platform when the purchaser purchases the commodity on behalf of the purchaser; S4 enabling the logistics party to upload the logistics information to the platform; S5 inspecting after receipt of goods by the demander; S6 if the goodsare fake or inferior goods, submitting a compensation request, requiring the purchaser shall to pay compensation and lowering the credit rating of the purchaser shall if the goods are confirmed as fake or inferior goods after the inspection by a third party; S7 completing the transaction after the demander confirms that the goods are qualified; S8 enabling the platform server to record the transaction information in a platform block chain network. The method of the invention introduces an intelligent contract and a credit evaluation mechanism based on the block chain technology to protect therights of shoppers.
Owner:CHONGQING INST OF GREEN & INTELLIGENT TECH CHINESE ACADEMY OF SCI
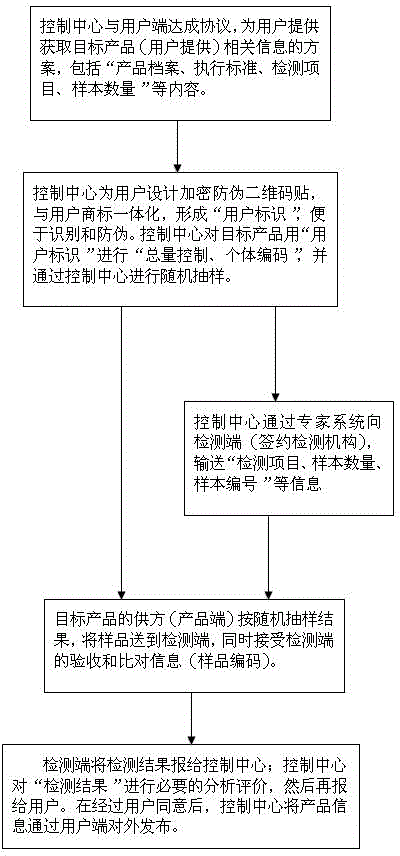
Method and system for realizing product management and control with application of statistics principle and two-dimensional code technology
InactiveCN104881792AReduce the possibility of counterfeitingCo-operative working arrangementsCommerceE-commerceSample number
The invention discloses a method and system for realizing product management and control with application of a statistics principle and a two-dimensional code technology. The method is characterized in that total quantity control of target products is carried out and each product among all products is coded uniquely to generate an encrypted two-dimensional code; random sampling is carried out and a detection mechanism compares codes of samples; after confirmation of no error existence, product detection is carried out; after detection, detection item, sample number, detection result information is recorded into the two-dimensional code; and then a user obtains detection information of the target products by using a two-dimensional code identification terminal. The system is composed of a two-dimensional code tag, a two-dimensional code identification terminal, and a control center platform. With the management and control method and system, counterfeiting products can be eliminated for E-commerce and WeChat-based companies; the commercial environment is purified; and one kind of scientific and rigorous, and convenient and practical method and technical means can be provided. The effective help and guidance are provided for consumers to get real information of the products and purchase products.
Owner:辛丘岩
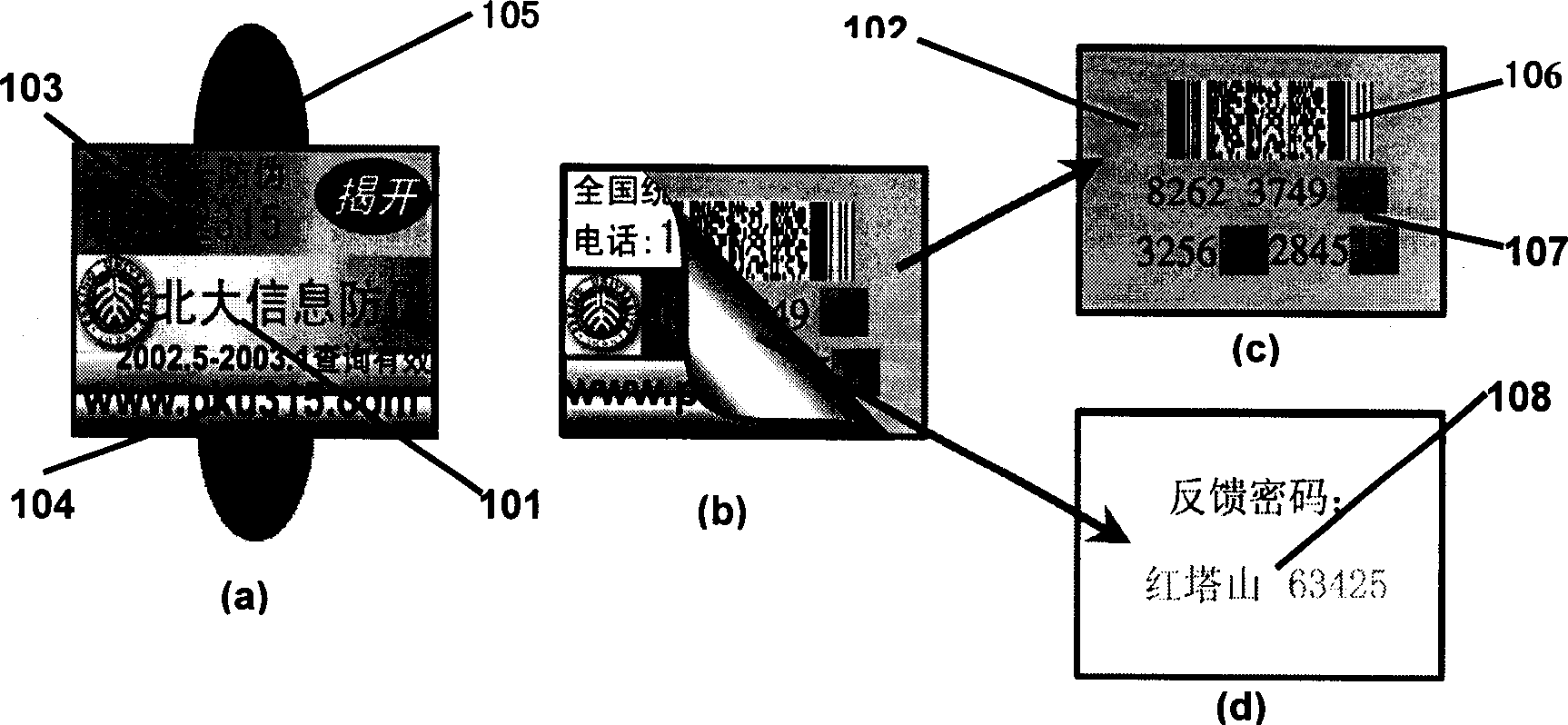
Information anti-fake label and corresponding intelligent information anti-fake service system
InactiveCN1388702AAchieve separationSolve the fatal loophole of counterfeitingStampsTelephonic communicationDatabase serverComputer terminal
The present invention is multiple-feedback information anti-fake label and corresponding intelligent informatino anti-fake service system. The information anti-fake label consists of observed label with double feedback cipher and information checking label comprising bar code and sectional feedback code. The intelligent information anti-fake service system consists of information anti-fake platform and connected checking terminal, the information anti-fake platform includes FSK access server, AAA server, information anti-fake central processing machine and data base server; and the private intelligent checking terminal includes PSTN, scanning input and FSK code information. The present invention has very high commodity anti-fake checking rate.
Owner:谷安佳 +3
Network payment-based card-free metro ticket selling and checking methods, terminal and server
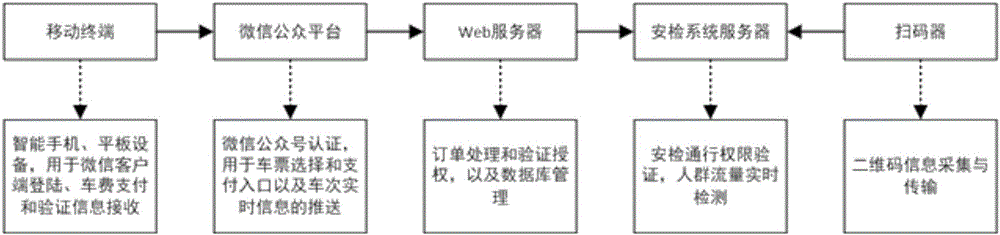
ActiveCN106779937AEliminate the risk of lossHigh speedCredit schemesDebit schemesPaymentComputer terminal
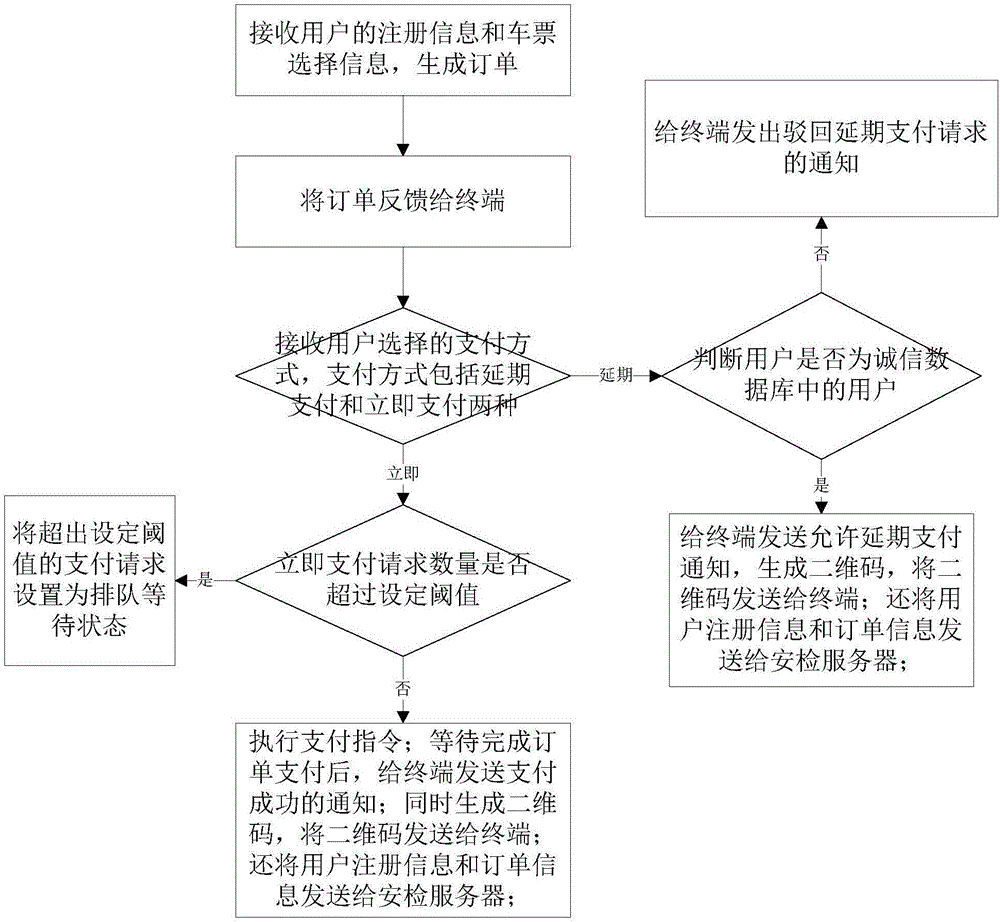
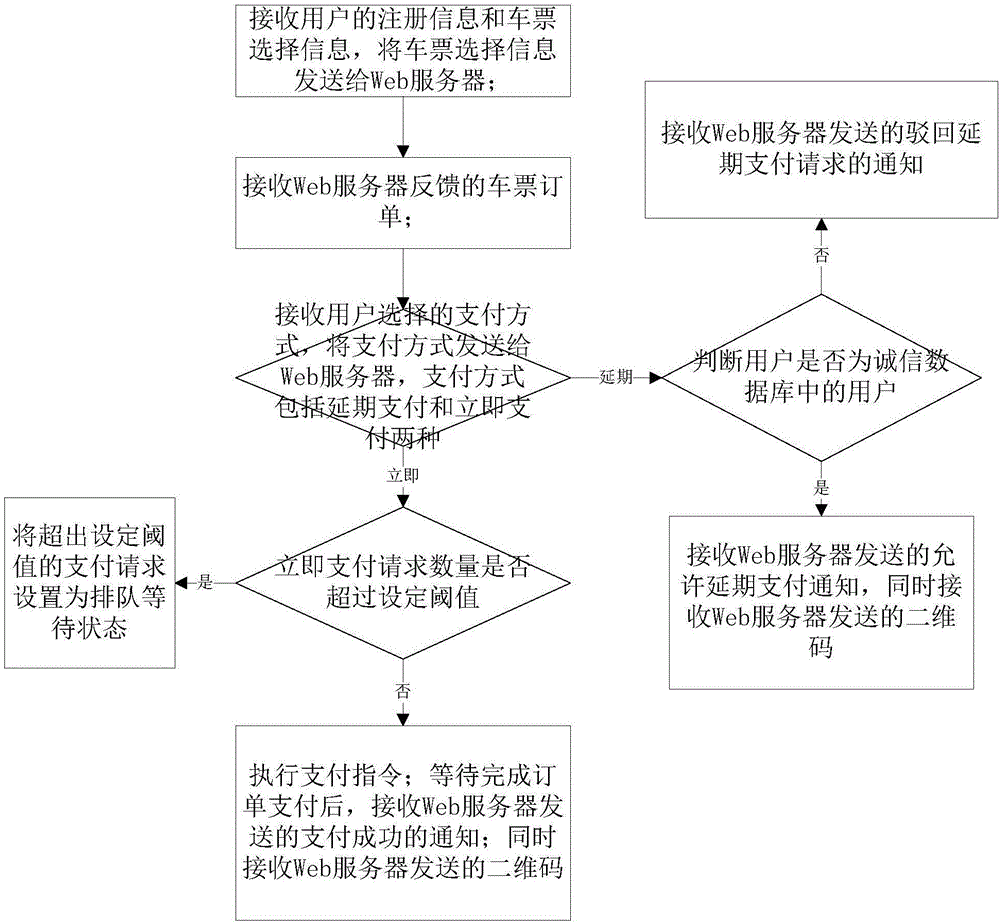
The invention discloses a network payment-based card-free metro ticket selling method, a network payment-based card-free metro ticket checking method, a terminal and a server. The ticket selling method comprises the steps of receiving registration information and ticket selection information of a user, and generating an order; feeding back the order to the terminal; receiving a payment mode selected by the user, wherein the payment mode includes deferred payment and immediate payment; if the payment mode is the immediate payment, judging whether an immediate payment request quantity exceeds a set threshold or not, and if the immediate payment request quantity exceeds the set threshold, setting payment requests with the quantity exceeding the set threshold to be in a queue waiting state, otherwise, executing a payment instruction; after the order is paid, sending a notification of payment success to the terminal; generating a two-dimensional code, and sending the two-dimensional code to the terminal; sending the registration information of the user and order information to a safety inspection server; if the payment mode is the deferred payment, judging whether the user is a user in a honesty database or not, and if yes, sending the two-dimensional code to the terminal; and if not, sending a notification of rejecting a deferred payment request to the terminal. The ticket selling and checking methods have the advantages of card-free ticket selling and checking.
Owner:SHANDONG UNIV
Monitoring method and device, and electronic equipment
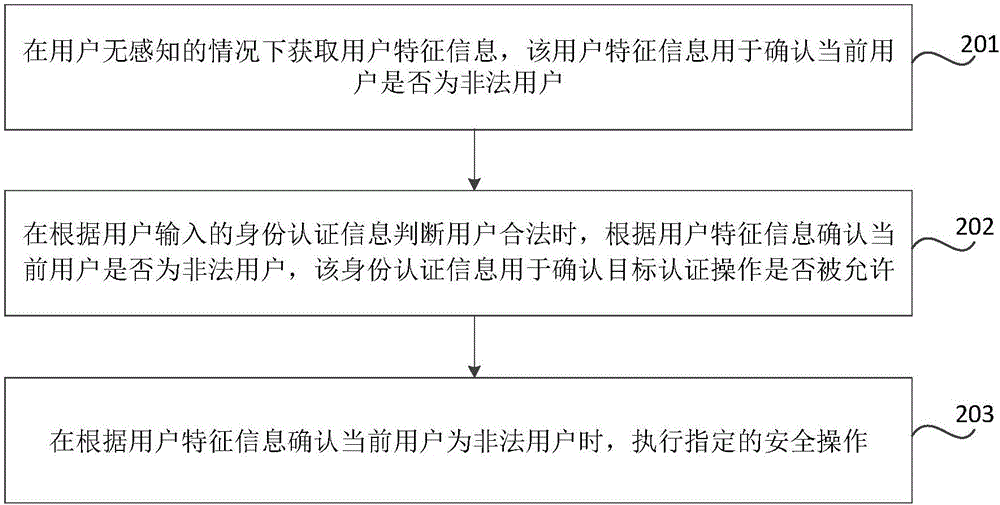
InactiveCN106716429AImprove accuracyReduce parodyDigital data authenticationSecuring communicationUser inputInternet privacy
The invention relates to a monitoring method and device, and electronic equipment. The monitoring method comprises obtaining the user feature information under the non-sensing condition of the user; determining whether the current user is a legal user according to the user feature information when the user is determined to be legal according to the identity authentication information input by the user, wherein the identity authentication information is used for determining whether target authentication operation is permitted or not; and executing specified safe operation when the current user is determined to be an illegal user according to the user feature information. Thus, even if an illegal user cracks or forges identity authentication information of a legal user, and logs in the electronic equipment successfully, the electronic equipment can carry out secondary verification to the identity of the user by acquiring the user feature information of the current user. When the secondary verification result shows that the user is an illegal user, the specified safe operation is executed, and therefore the service safety of the electronic equipment is improved, and problems that user information is leaked, user property is damaged and the like are avoided.
Owner:CLOUDMINDS (SHENZHEN) ROBOTICS SYST CO LTD
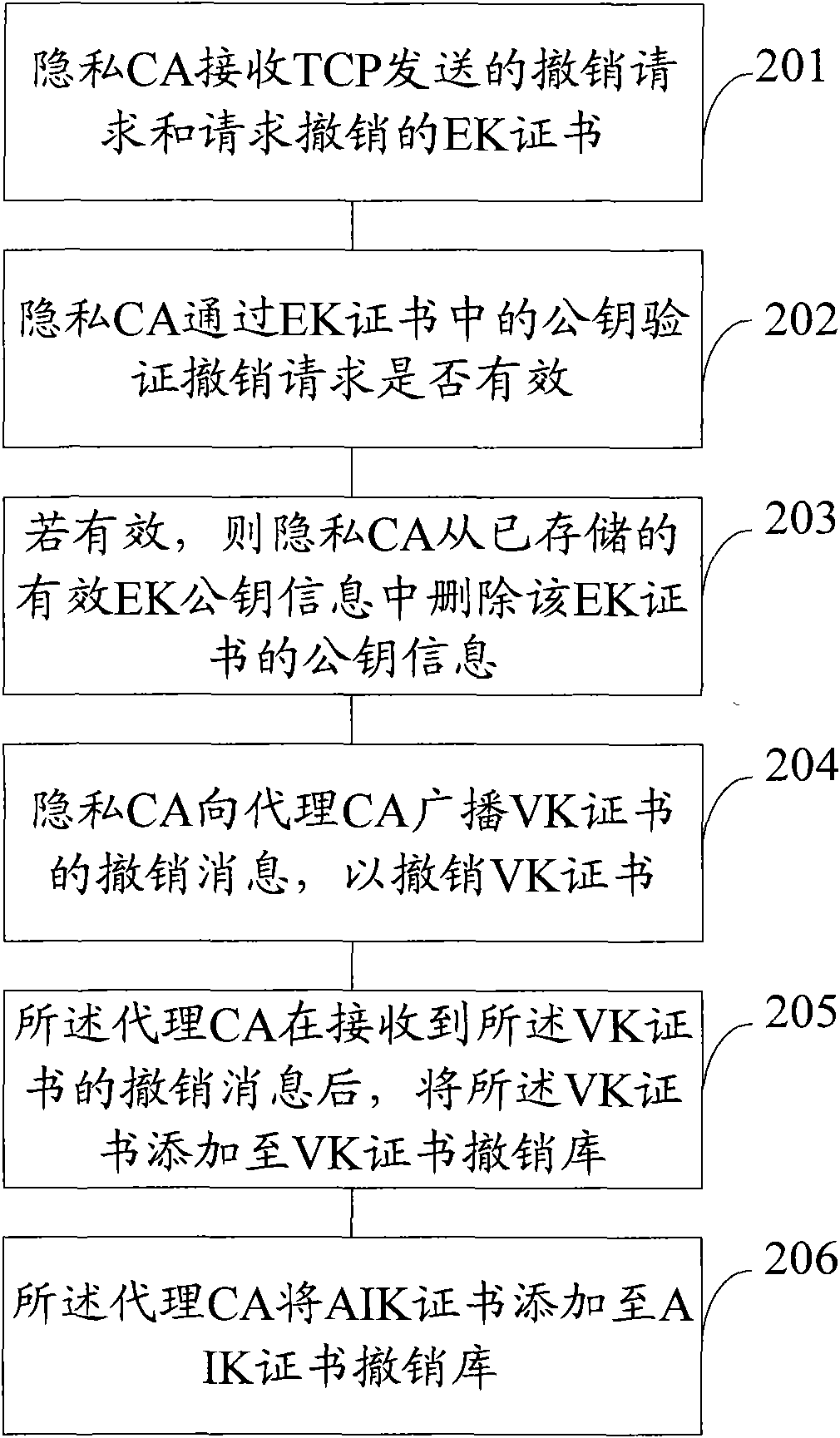
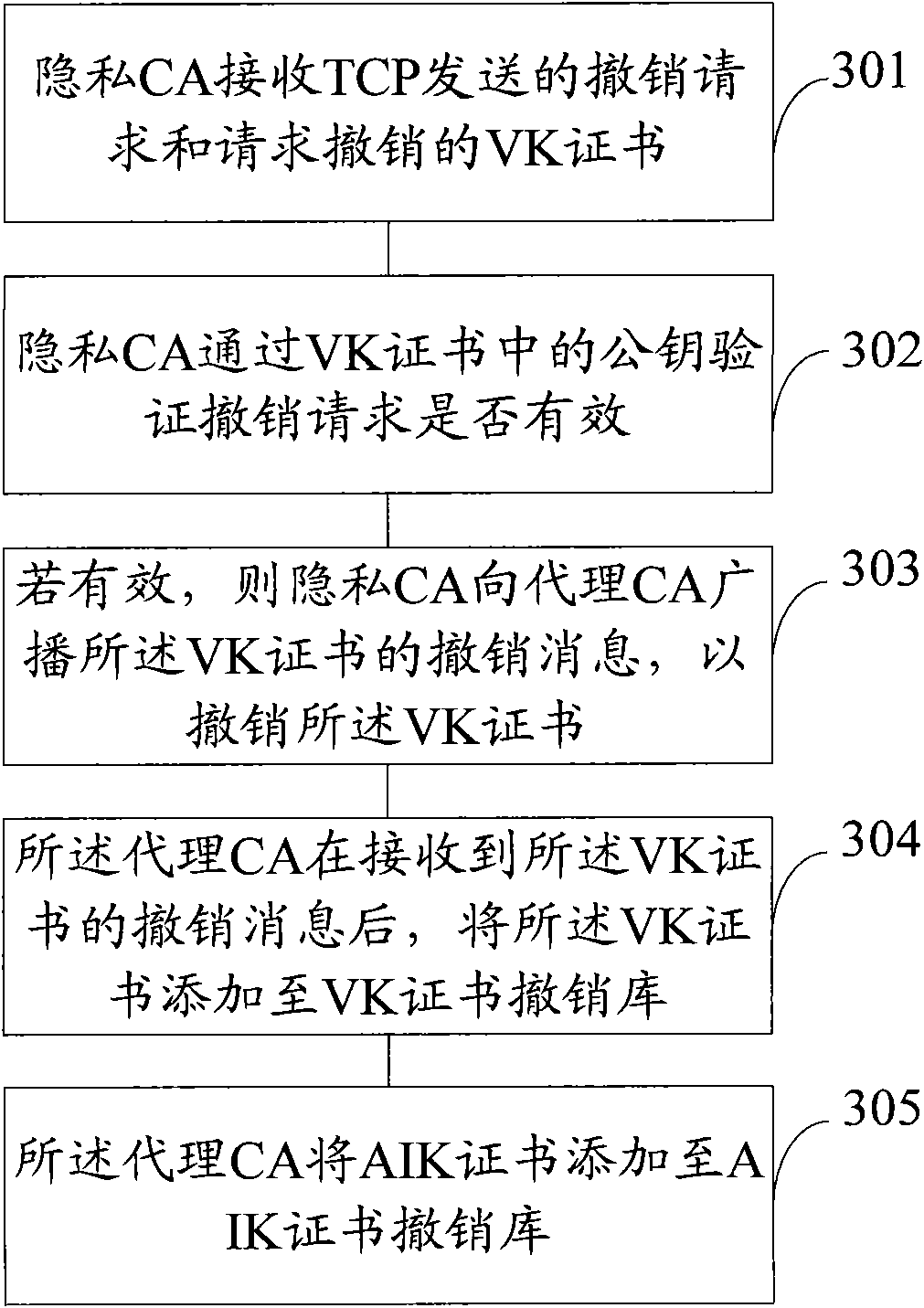
Method, device and method for repealing public key certificate in trusted computing
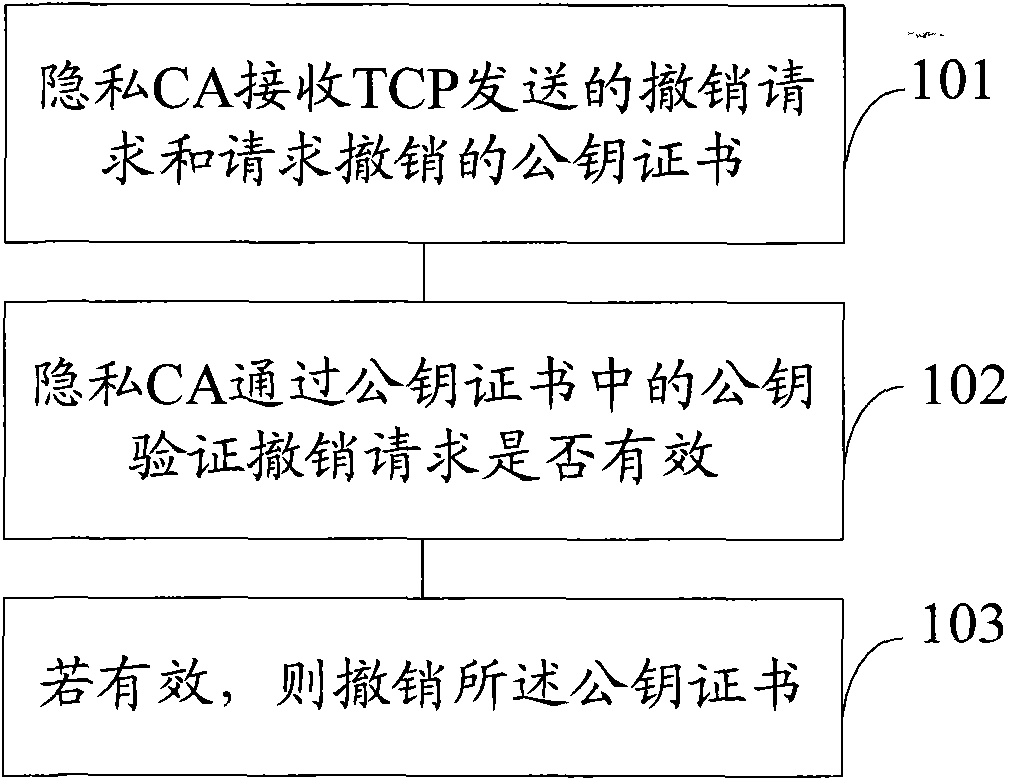
InactiveCN101853337AImprove securityReduce the possibility of counterfeitingDigital data authenticationTrusted ComputingPublic key certificate
The invention discloses a method, a device and a system for repealing a public key certificate in trusted computing. The method comprises the following steps: a privacy certificate authority receives a repealing request and the public key certificate requested to be repealed sent by a trusted computation platform, wherein the repealing request uses a privacy key to sign in advance, the privacy key corresponds to the public key in the public key certificate which is a signing certificate or an effective certificate; and the privacy certificate authority verifies whether the repealing request is effective or not through the public key in the public key certificate, and if so, the public key certificate is repealed. The embodiment of the invention leads the ineffective certificate caused by privacy key information leakage and the like not to be reused for transaction, thereby improving safety of transactions between TCPs.
Owner:THE PLA INFORMATION ENG UNIV
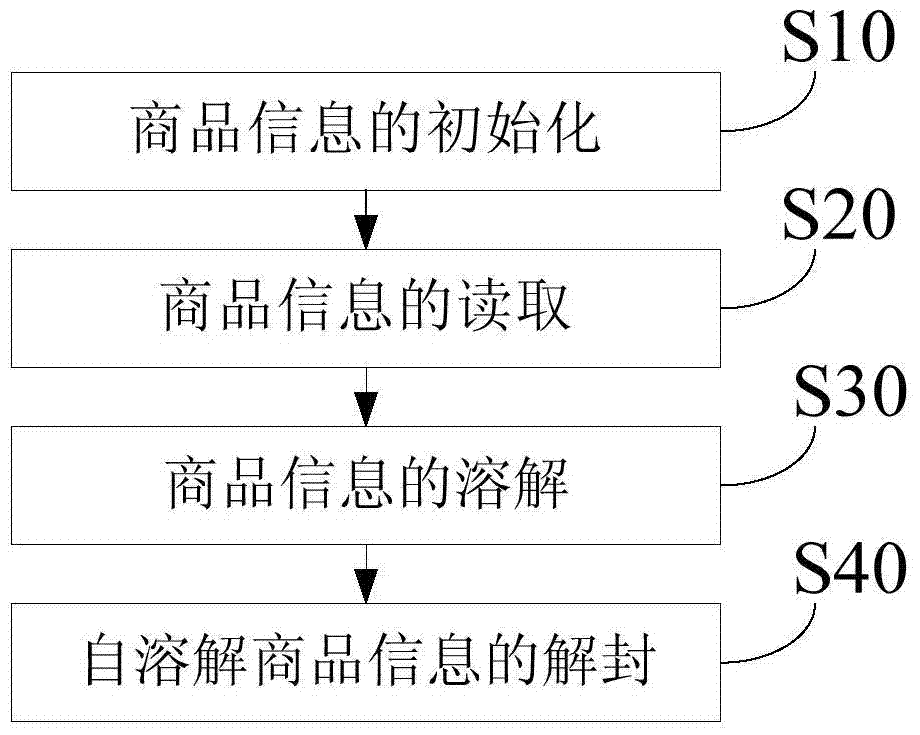
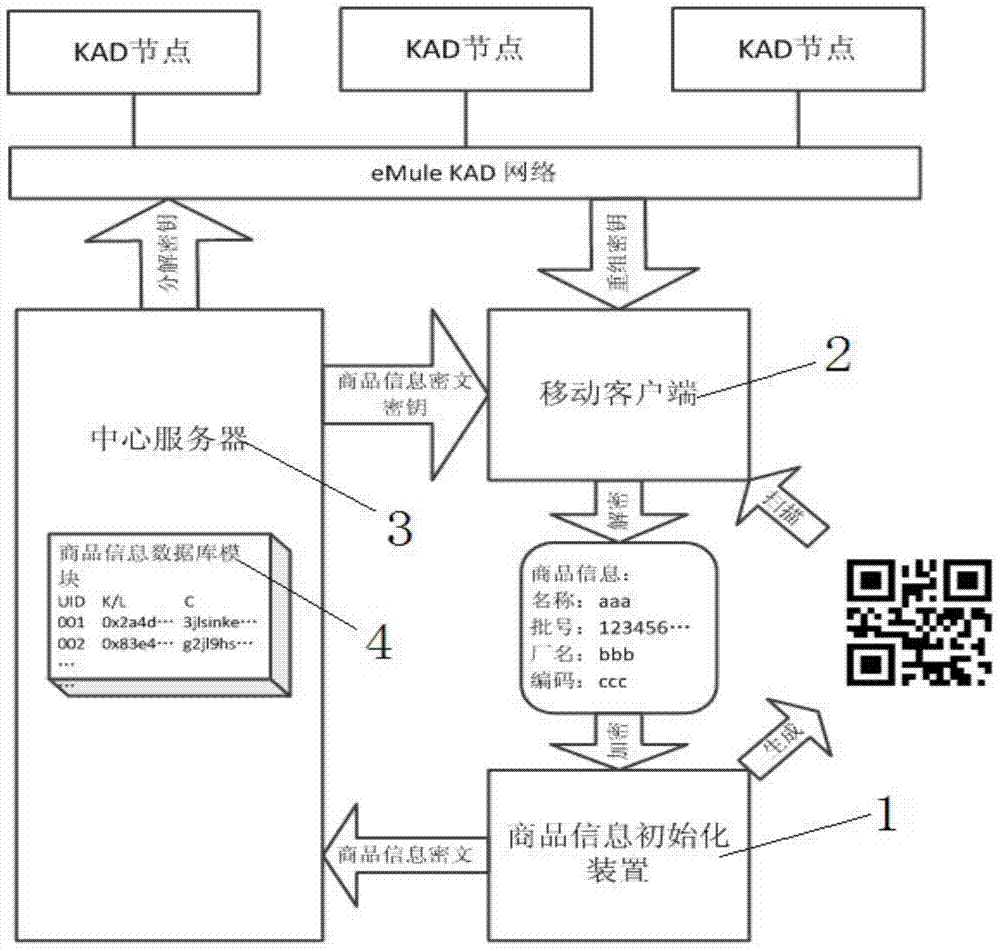
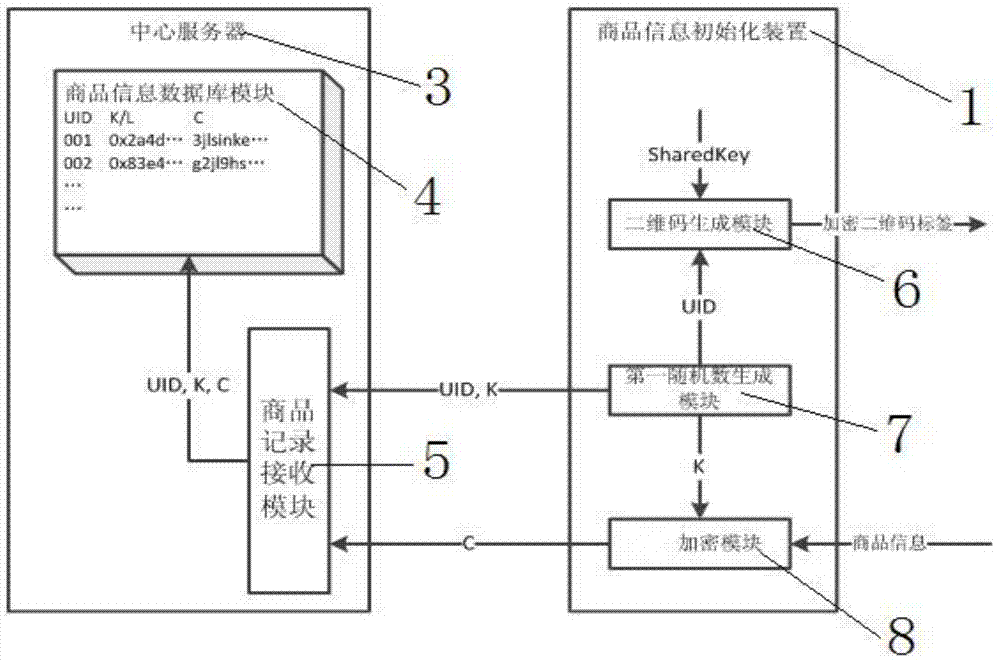
Commodity information management system and method based on two-dimensional code and self-dissolving system
InactiveCN104851007AReduce guessworkReduce the possibility of counterfeitingStampsCommerceLibrary sciencePackaging and labeling
The invention provides a commodity information management system and method based on a two-dimensional code and a self-dissolving system, and relates to the technical field of commodity information management methods. The method comprises the steps: the initializing of commodity information; the reading of commodity information; the dissolving of commodity information; and the unblocking of the self-dissolving commodity information. According to the invention, a commodity certificate which can be inquired is provided, and a dealer and a consumer can obtain the detailed commodity information through the commodity certificate, so as to discern the false from the genuine. Moreover, the commodity certificate cannot be faked or used repeatedly, thereby preventing a counterfeit and shoddy product from using a true package.
Owner:SHENZHEN RUIMENG PACKAGING CO LTD
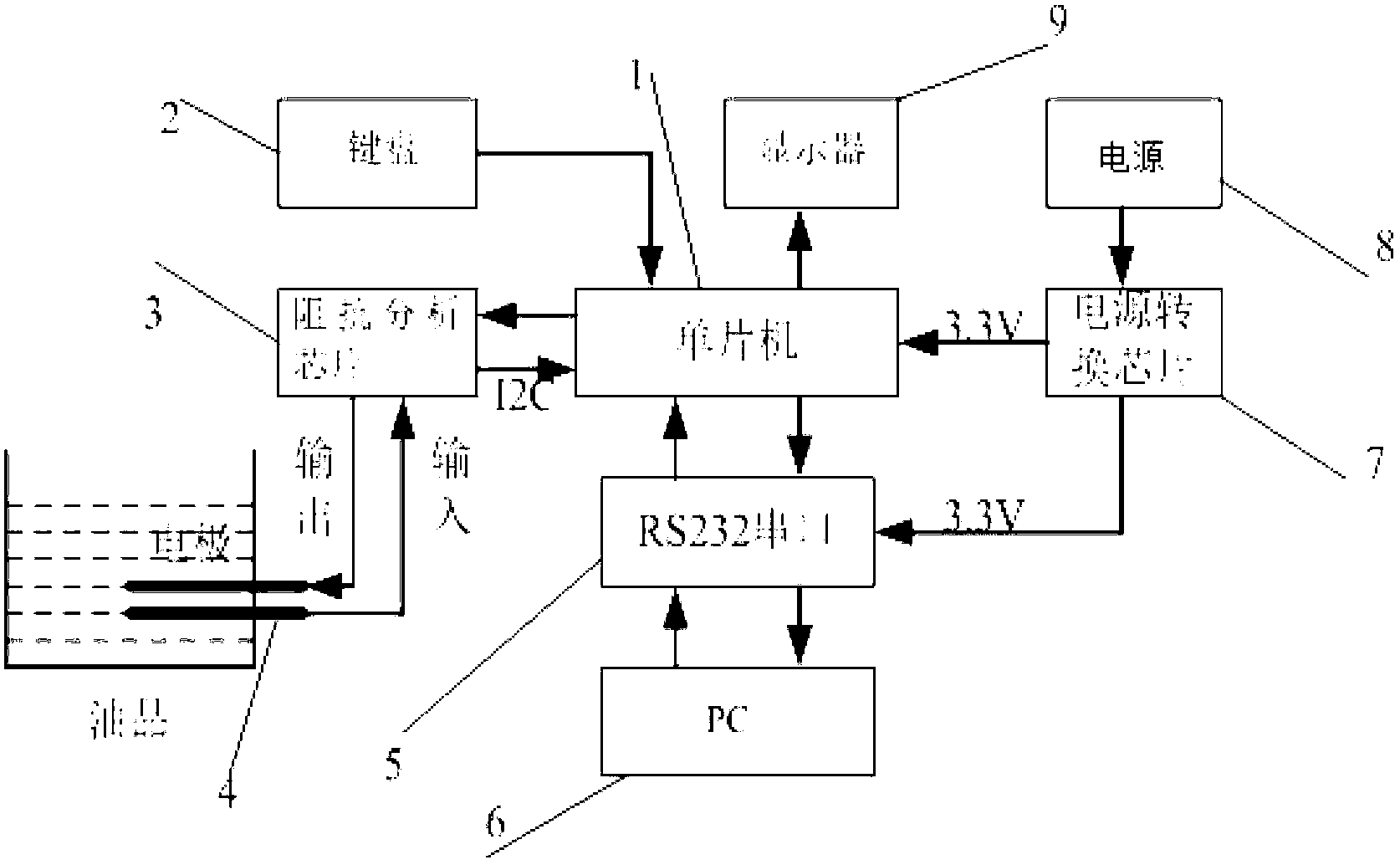
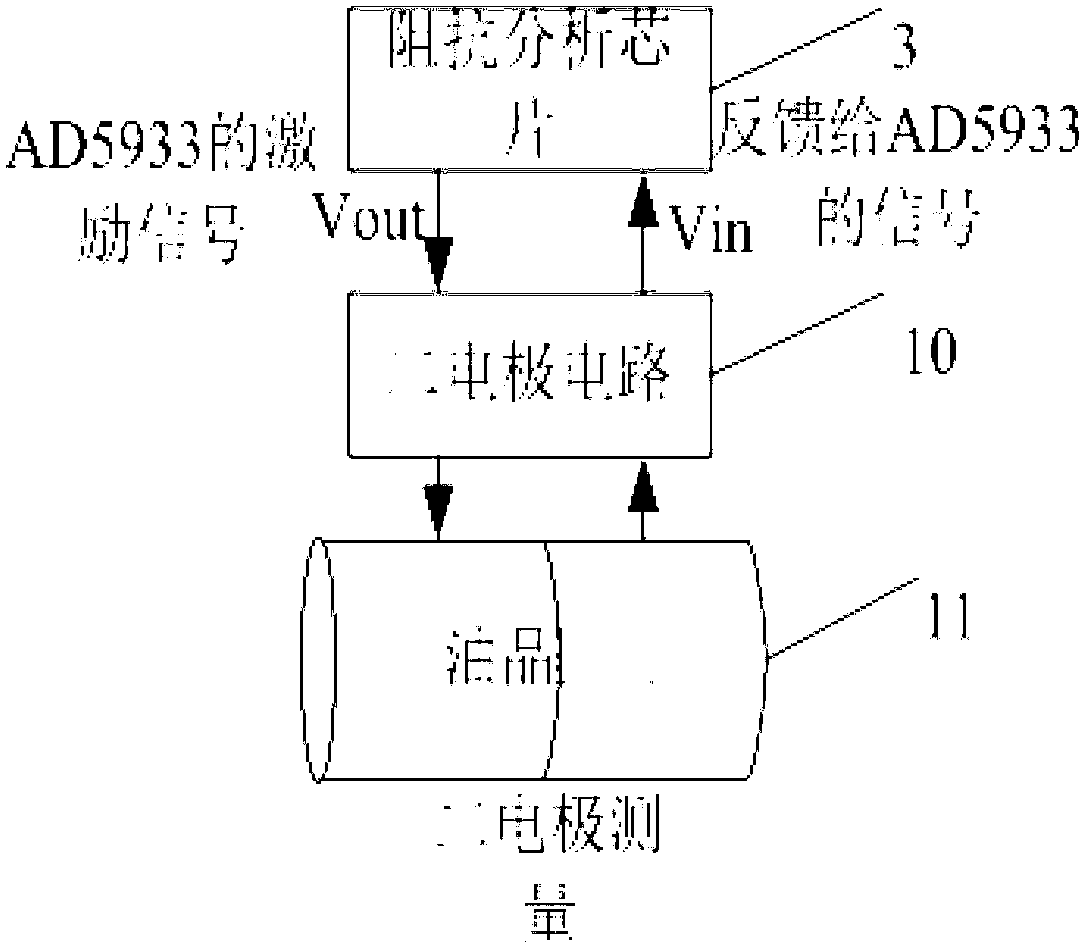
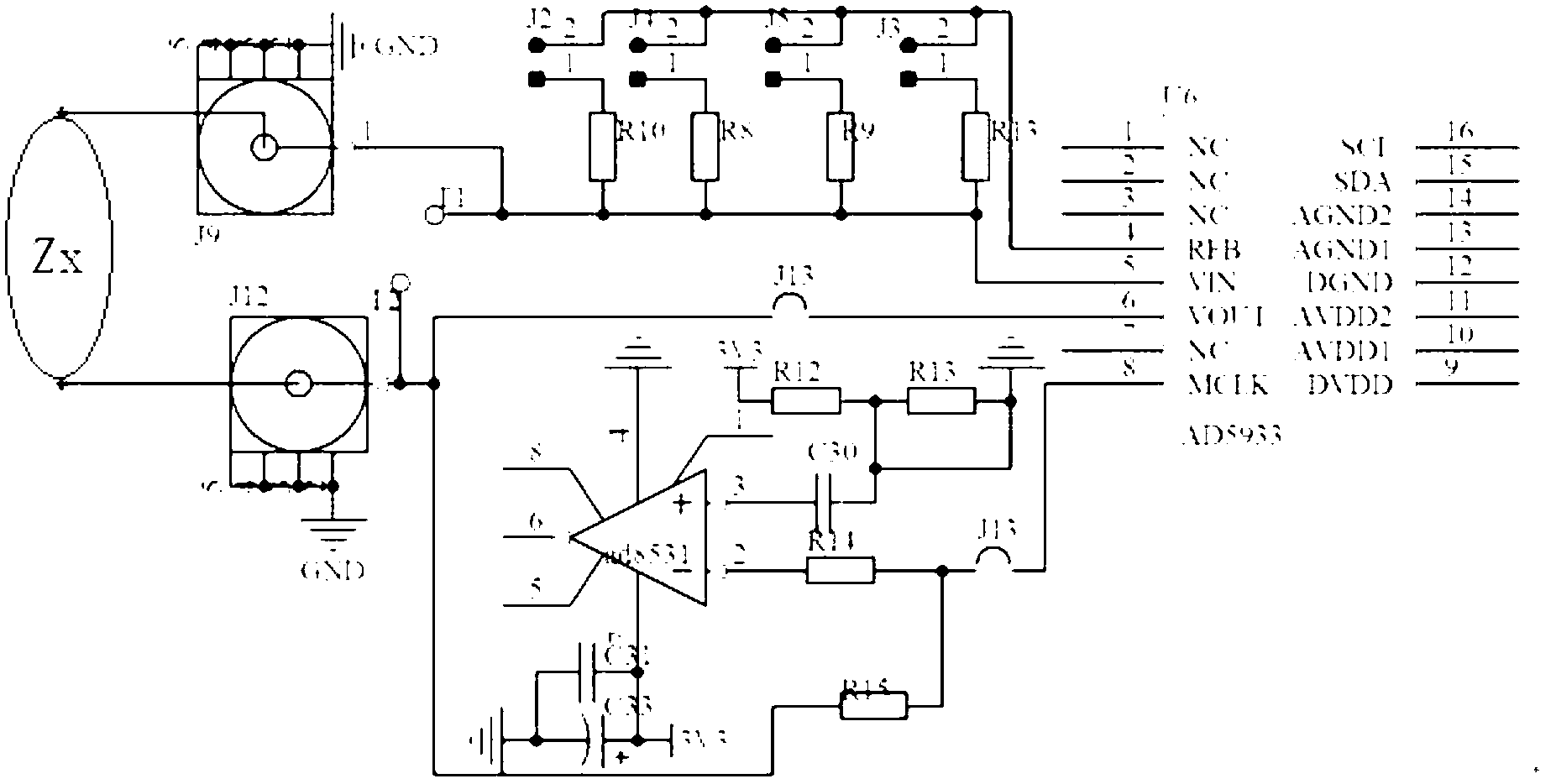
Fast detection device for waste cooking oil and detection method of device
InactiveCN103175870ASimple structureReduce volumeMaterial resistanceMicrocontrollerProcessor register
The invention relates to a fast detection device for waste cooking oil. The fast detection device comprises a singlechip, wherein the singlechip is connected with a keyboard, an impedance analysis chip, a serial port RS232 (recommend standard 232), a power supply conversion chip and a display respectively to form a main control unit; the impedance analysis chip is connected with two electrodes; the two electrodes are connected with oil products through circuits of the two electrodes; and the serial port RS232 is connected with an upper computer. A detection method of the fast detection device for the waste cooking oil comprises the steps of: putting the to-be-detected oil products into a utensil fixed with the two electrodes; supplying power to the singlechip and the serial port RS232 by the power supply conversion chip, inputting measuring parameters by utilizing the keyboard, writing the parameters into a register of the impedance analysis chip by the singlechip, generating amplitude-constant alternating-current drive signals by the impedance analysis chip to drive the to-be-detected oil products through one electrode, and sending feedback signals back to the impedance analysis chip through the other electrode, thus obtaining measuring data of the oil products; and sending the measuring data of the singchip to the upper computer through the serial port RS232 to be corrected, and sending a final corrected result to the display to be displayed.
Owner:XIAN UNIV OF TECH
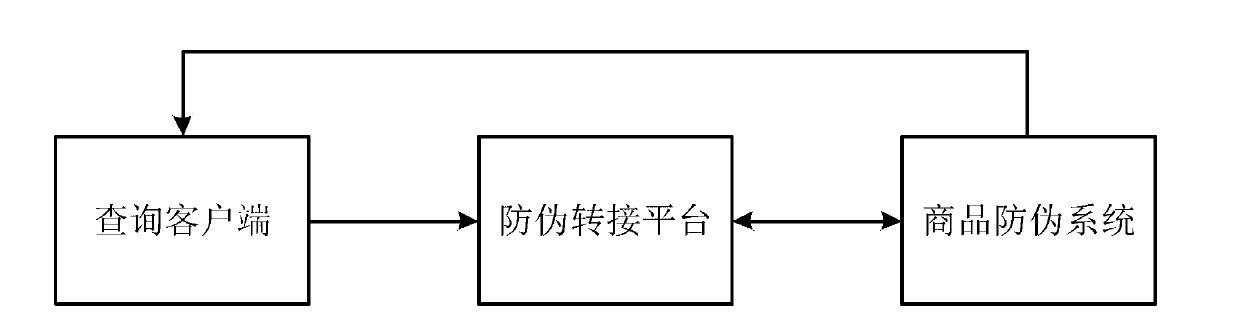
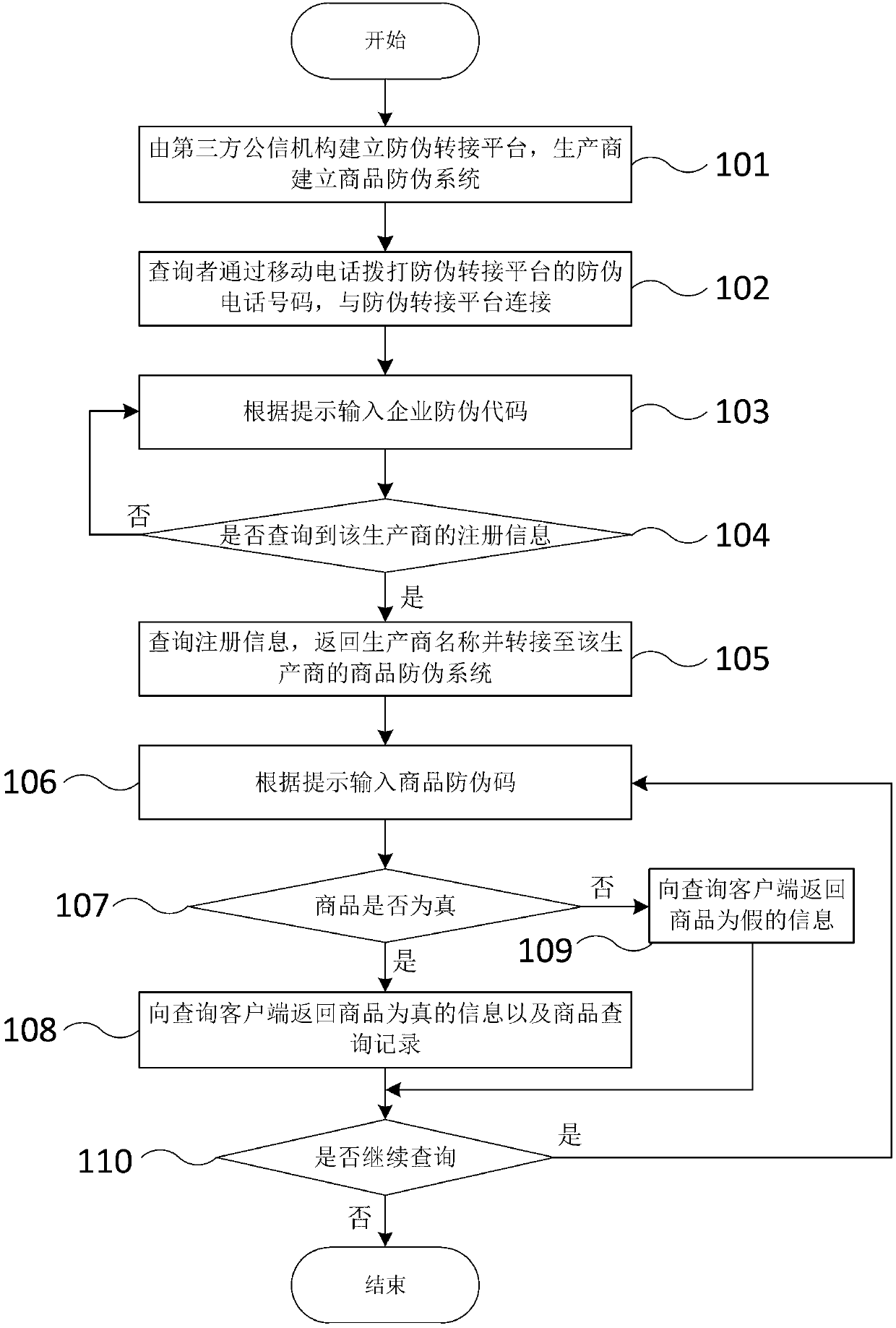
Merchandise anti-counterfeiting identification method
InactiveCN103136677AReduce blindness and counterfeiting costsReduce complexityUser identity/authority verificationLogisticsDatabase
The invention relates to the field of anti-counterfeiting, in particular to a merchandise anti-counterfeiting identification method. The merchandise anti-counterfeiting identification method includes the steps: constructing an anti-counterfeiting through-connection platform and storing enterprise register information and enterprise anti-counterfeiting codes in the anti-counterfeiting through-connection platform, wherein the enterprise register information comprises register names and register phone numbers; constructing query client-ends for connecting with the anti-counterfeiting through-connection platform; printing anti-counterfeiting phone numbers, the enterprise anti-counterfeiting codes and merchandise anti-counterfeiting codes on merchandises by manufacturers; and constructing a merchandise anti-counterfeiting system by the manufacturers, and the merchandise anti-counterfeiting system is used for storing the merchandise anti-counterfeiting codes and merchandise query records. Merchandise anti-counterfeiting query can be carried out on any link in the merchandise sales process, complexity of the merchandise anti-counterfeiting query is lowered, enterprise names are informed to inquirers strictly according to the enterprise register information registered on the anti-counterfeiting through-connection platform, and probability of producing counterfeit and shoddy products by the manufacturers is eliminated.
Owner:XIANG YANG HAO ZHENG IND
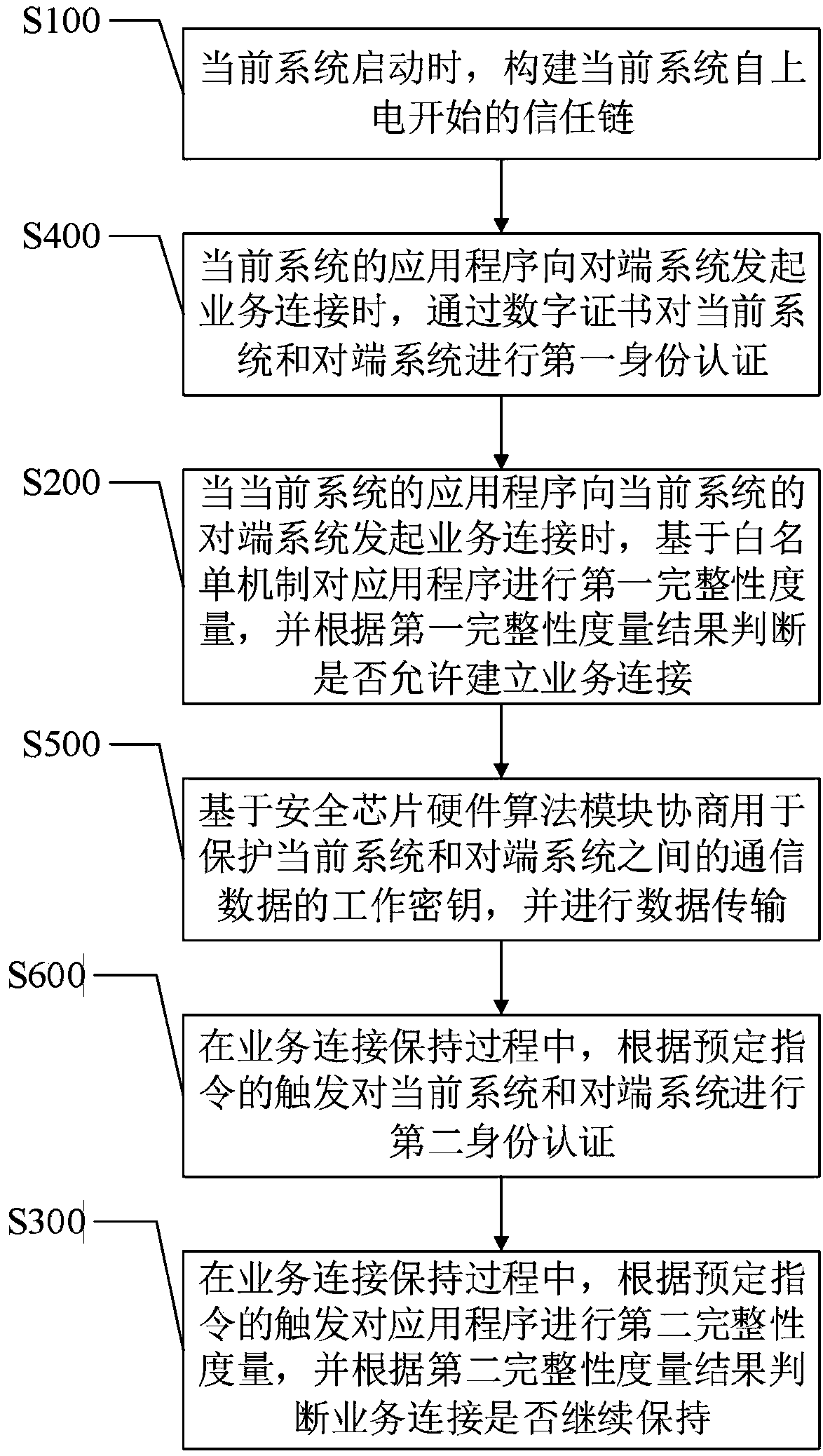
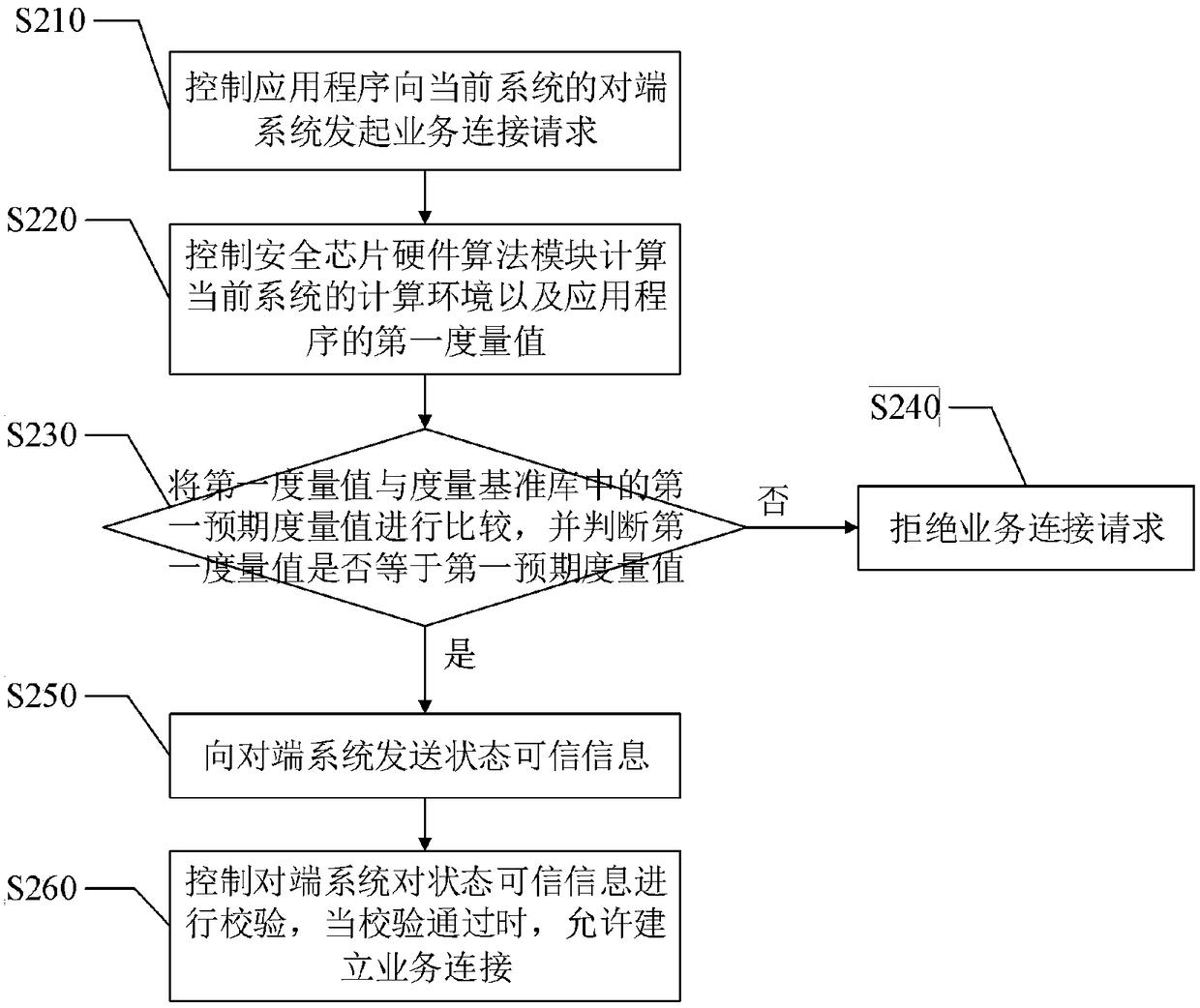
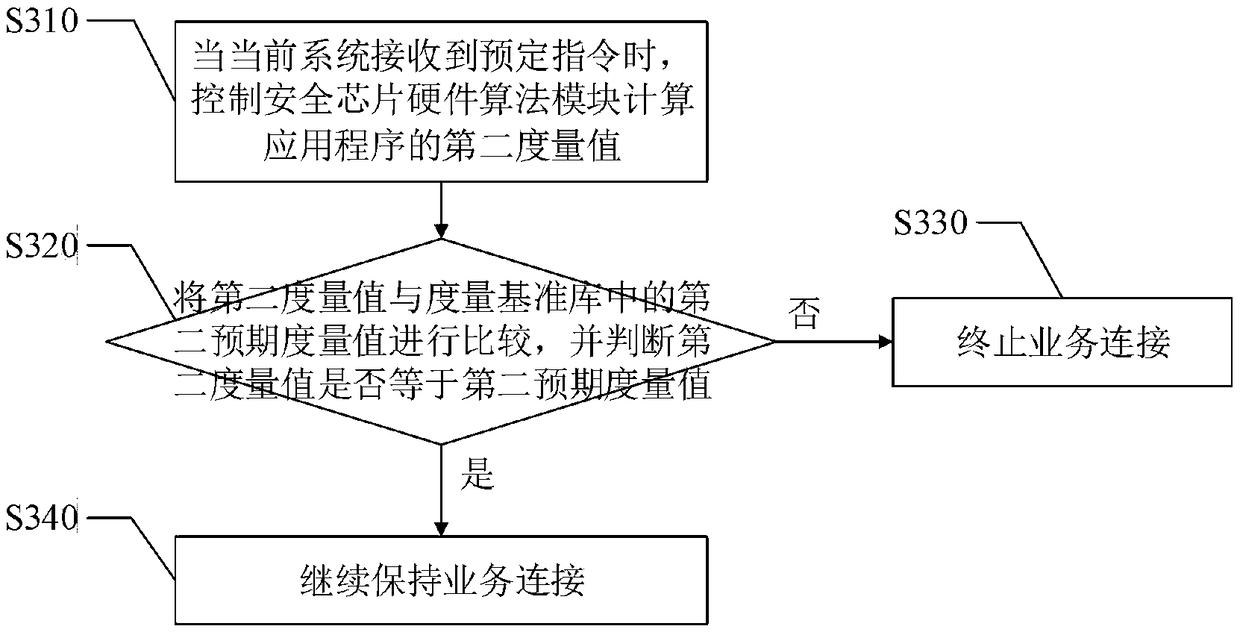
Trusted network communication method and device based on safety chip hardware algorithm module
InactiveCN108632243AImprove securityIncrease credibilityKey distribution for secure communicationUser identity/authority verificationElectricityPrimary station
The invention discloses a trusted network communication method and device based on a safety chip hardware algorithm module. The method comprises the following steps of when a system is started, constructing the trust chain of a current system from the beginning of power on; when the application program of the current system initiates service connection to the opposite end system of the current system, carrying out first integrity measurement on the application program based on a whitelist mechanism, and according to a first integrity measurement result, determining whether the service connection is allowed to establish; and during a service connection maintenance process, carrying out a second integrity measurement on the application program based on the triggering of a predetermined instruction, and according to a second integrity measurement result, determining whether the service connection is continuously maintained. When the application program initiates the service connection tothe opposite end system, the first integrity measurement is performed, and during the service connection maintenance process, the second integrity measurement is performed so as to reduce a possibility that transmission data between a terminal system and a main station system is stolen, and improve the safety and the credibility of the method.
Owner:GLOBAL ENERGY INTERCONNECTION RES INST CO LTD +3
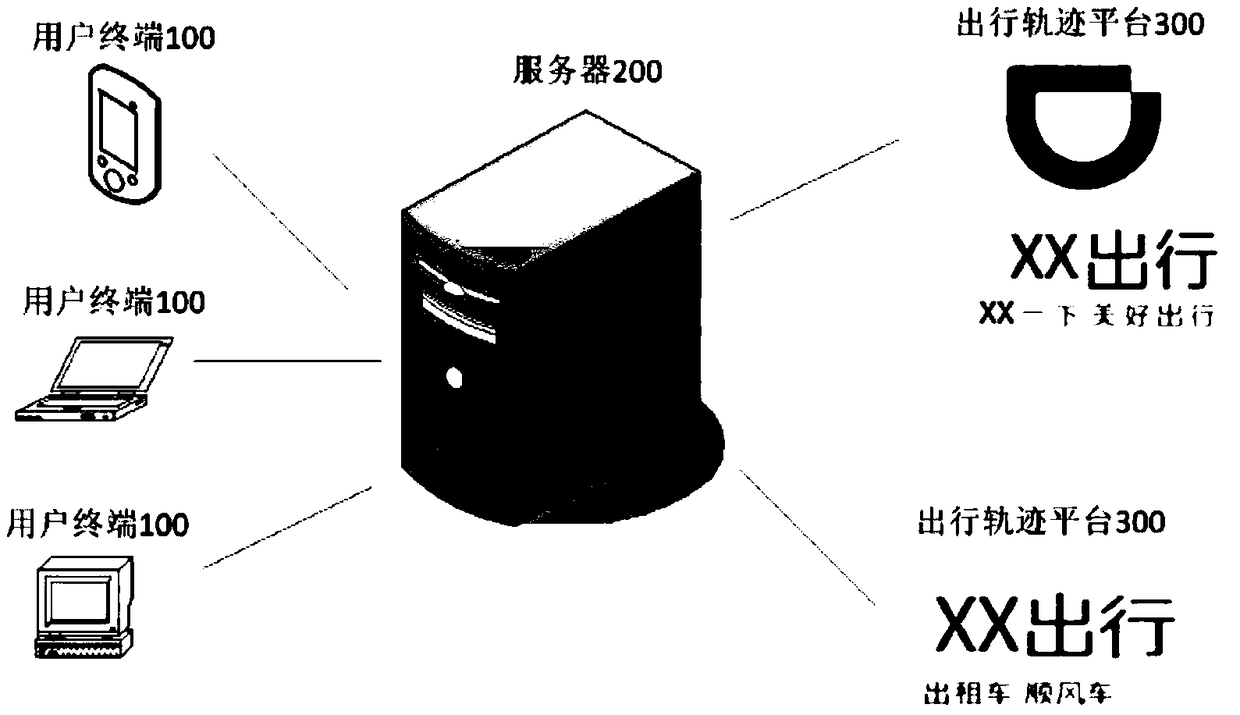
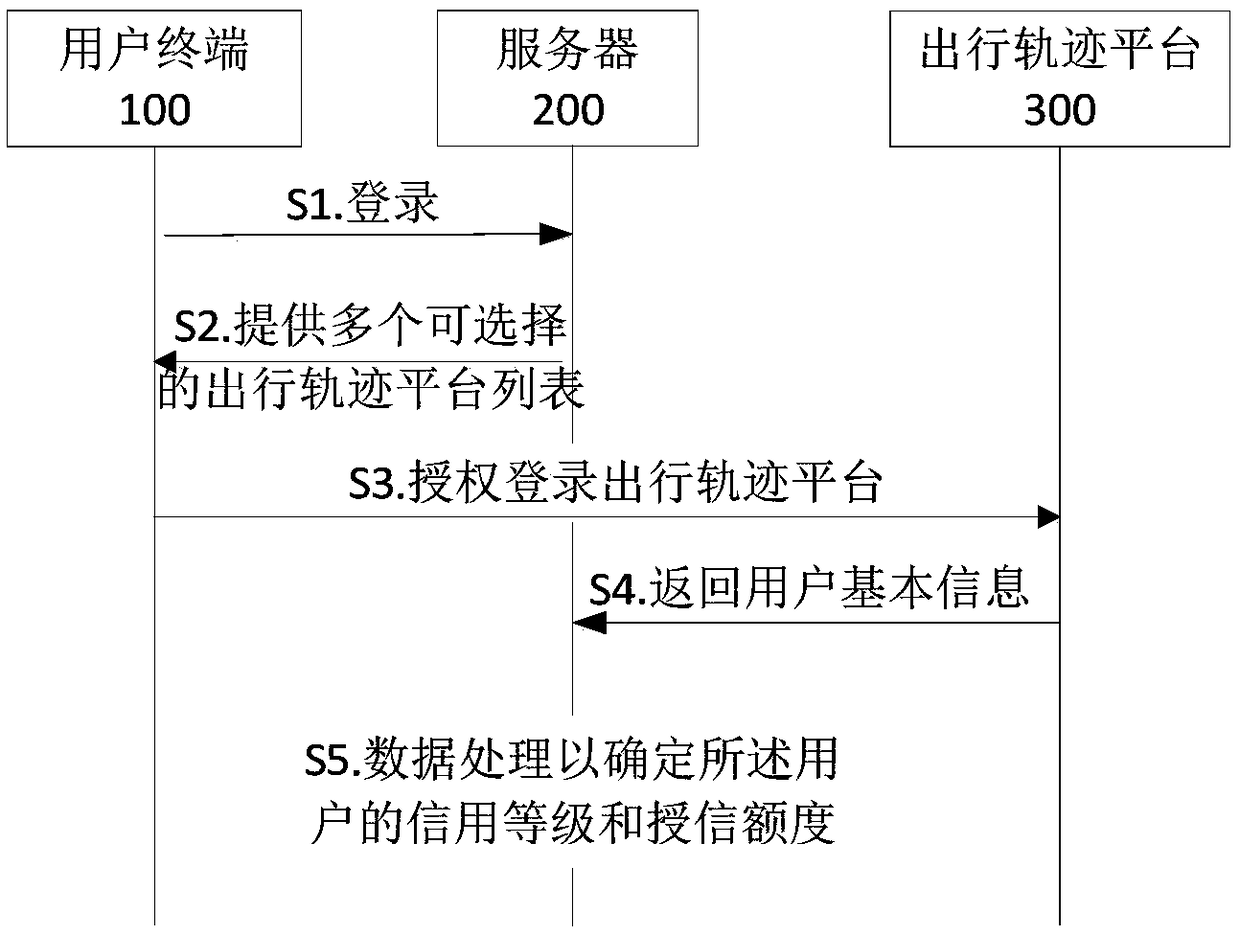
Credit granting method based on travel trajectory, user terminal and server
InactiveCN109242669AReduce the possibility of counterfeitingReduce credit riskFinanceComputer terminalData treatment
The invention discloses a credit granting method based on a user travel trajectory, a user terminal and a server. The credit granting method comprises the following steps: the user terminal logs on aserver in response to an operation of the user; the user terminal selects according to a plurality of travel trajectory platform lists provided by the server in response to an operation of the user, at least one travel trajectory platform is authorized to be logged in by the server, so that the server grasps the basic information of the user from the log-in travel trajectory platform, and performsdata processing according to the basic information to determine the credit rating and credit line of the user. The embodiment provided by the invention can solve the problem that the credit institution cannot verify the work information filled in by the user, effectively reduce the possibility of user fraud, and according to the user travel trajectory, can more accurately grasp the true information of users, can reduce credit institutions due to user credit information problems caused by credit risk, to ensure the stable operation of credit institutions.
Owner:新疆特易数科信息技术有限公司
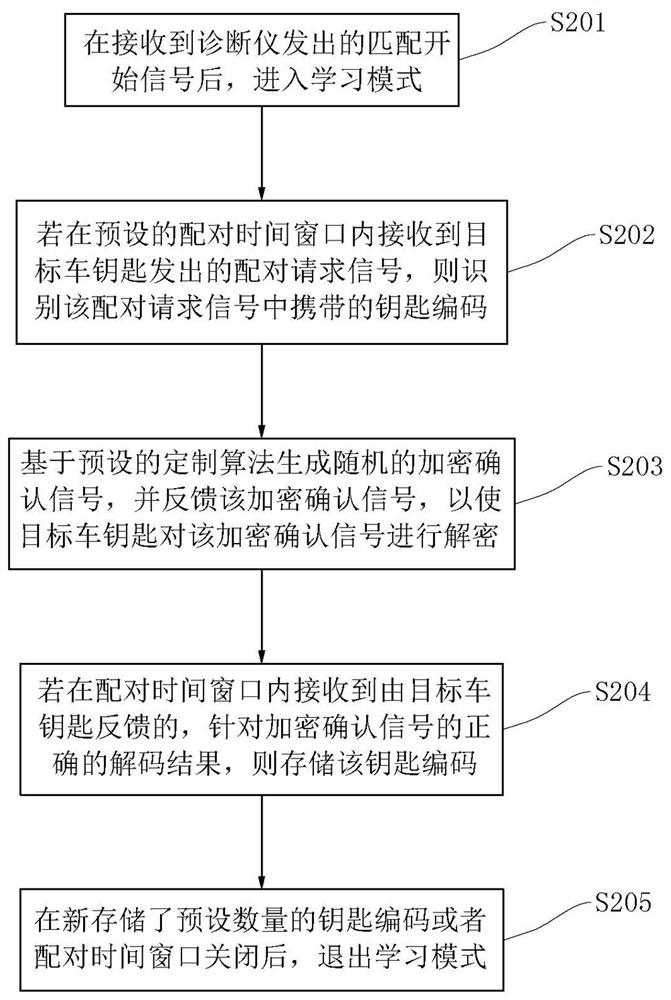
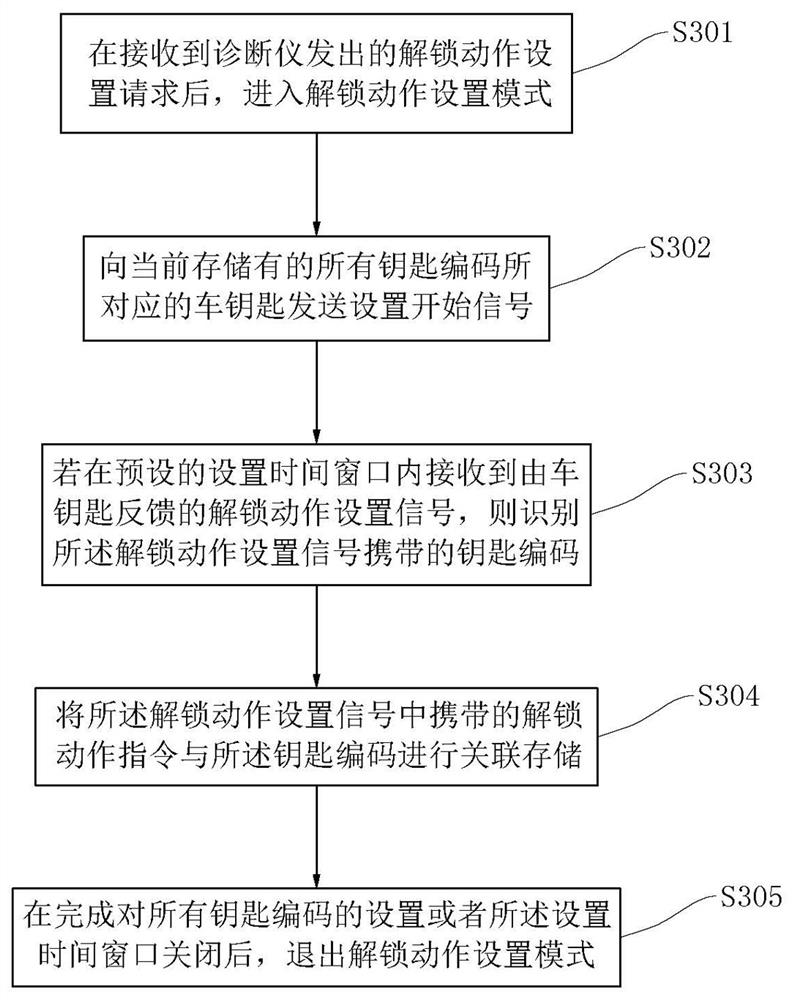
Vehicle key learning method and system, vehicle-mounted control device and storage medium
ActiveCN113269912AReduce mismatchReduce the possibility of counterfeitingIndividual entry/exit registersIn vehicleLearning methods
The invention relates to a car key learning method and system, a vehicle-mounted control device and a storage medium, and belongs to the field of automotive electronics technology. The method comprises: after a matching starting signal sent by a diagnostic instrument is received, entering a learning mode; if a pairing request signal sent by the target vehicle key is received in the preset pairing time window, identifying a key code carried in the pairing request signal; generating a random encryption confirmation signal based on a preset customization algorithm; feeding the encryption confirmation signal back so that the target vehicle key can decrypt the encryption confirmation signal; if a correct decoding result which is fed back by the target vehicle key and aims at the encryption confirmation signal is received in the pairing time window, storing the key code; and after the preset number of key codes are newly stored or the pairing time window is closed, exiting the learning mode. The method has the advantages that the reliability of the vehicle key is improved, and then the safety is improved.
Owner:JIANGSU HEYI TECH CO LTD
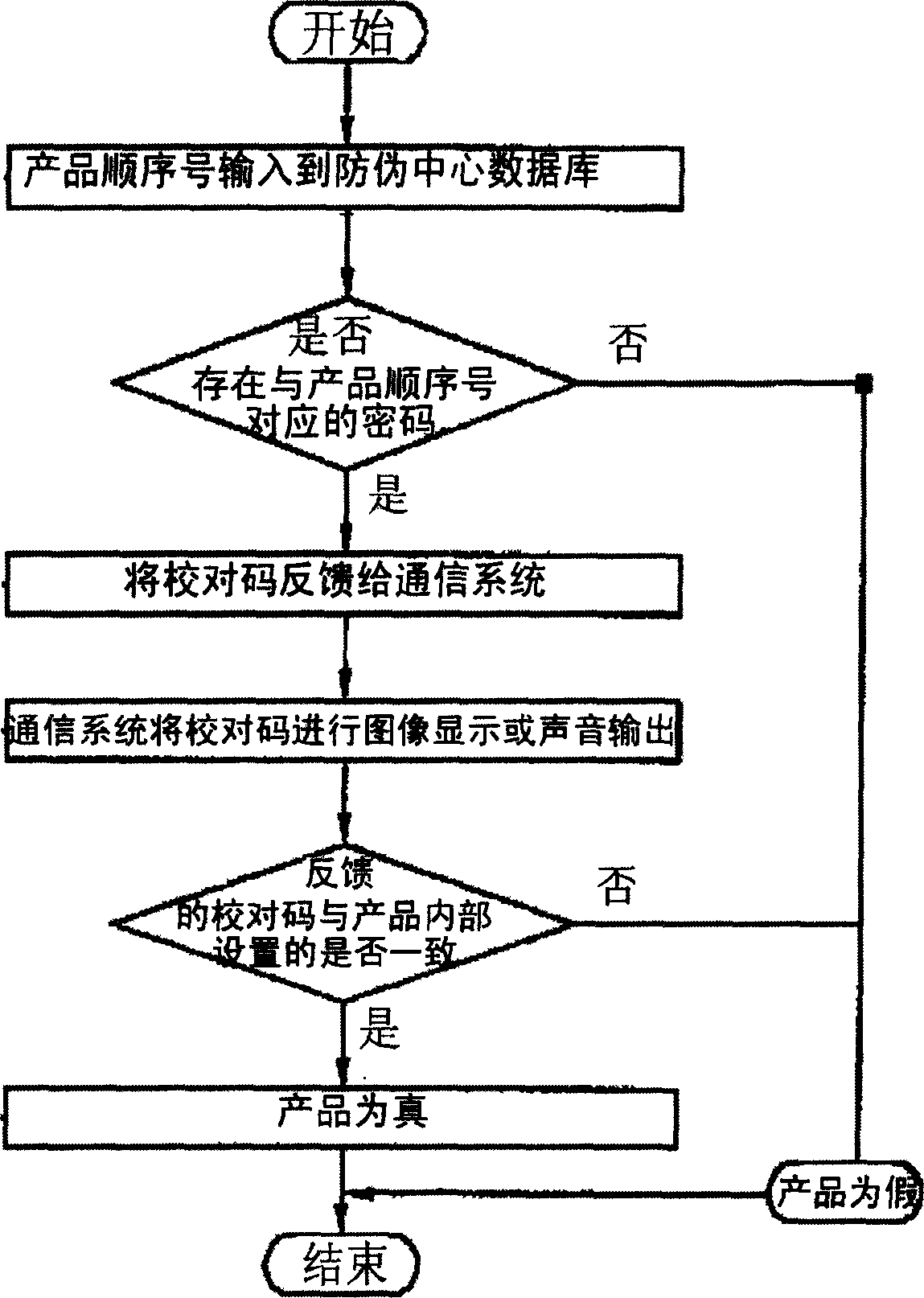
Anti-fogery double-code inquiring system and method
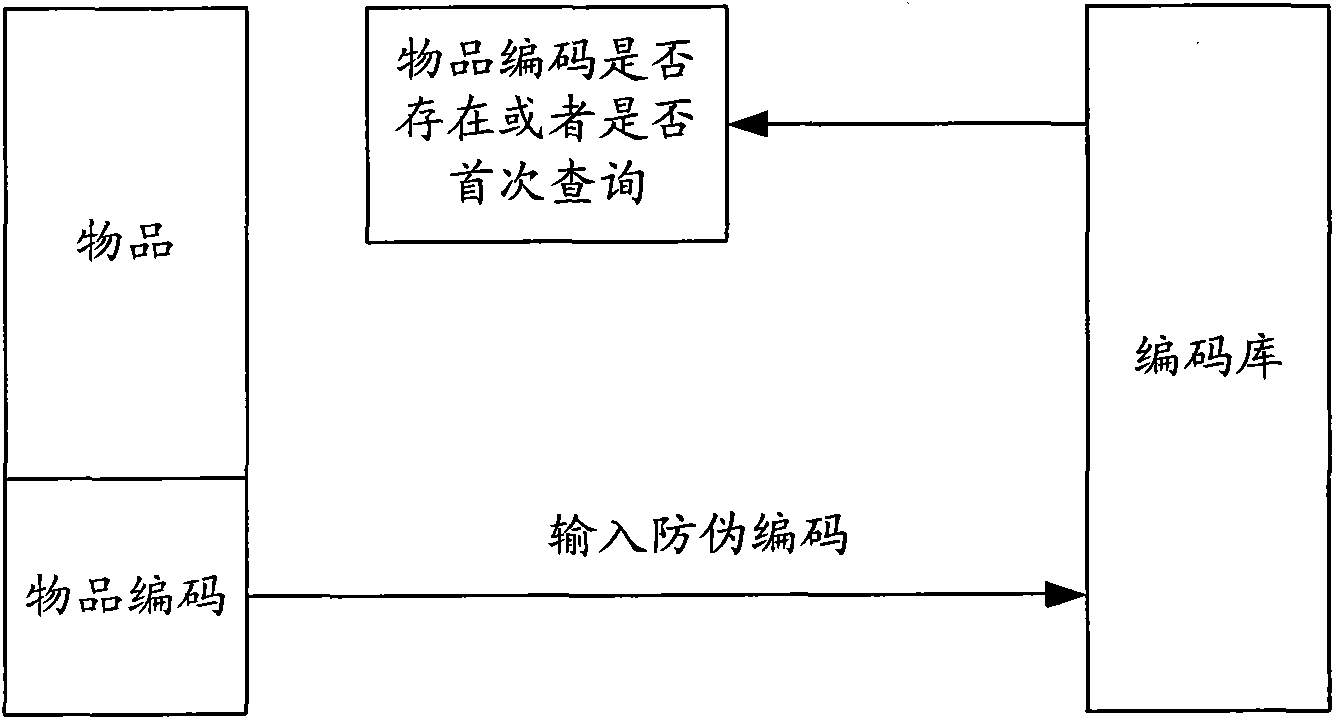
InactiveCN1614613ABreakthrough is easy to be counterfeited in batchesBreak through limitationsSpecial data processing applicationsComputer scienceComplex problems
A falseproof system of double code consultation is composed of three parts as false proof code sticker including product coding sticker sticked at external part of product with produce sequence number and random cipher as well as calibrating code sticker sticked at internal part of product; query device including computer network query device and telephone inquiry device; and databank server at enterprise falseproof centre for storing product coding and calibrating code.
Owner:官永博
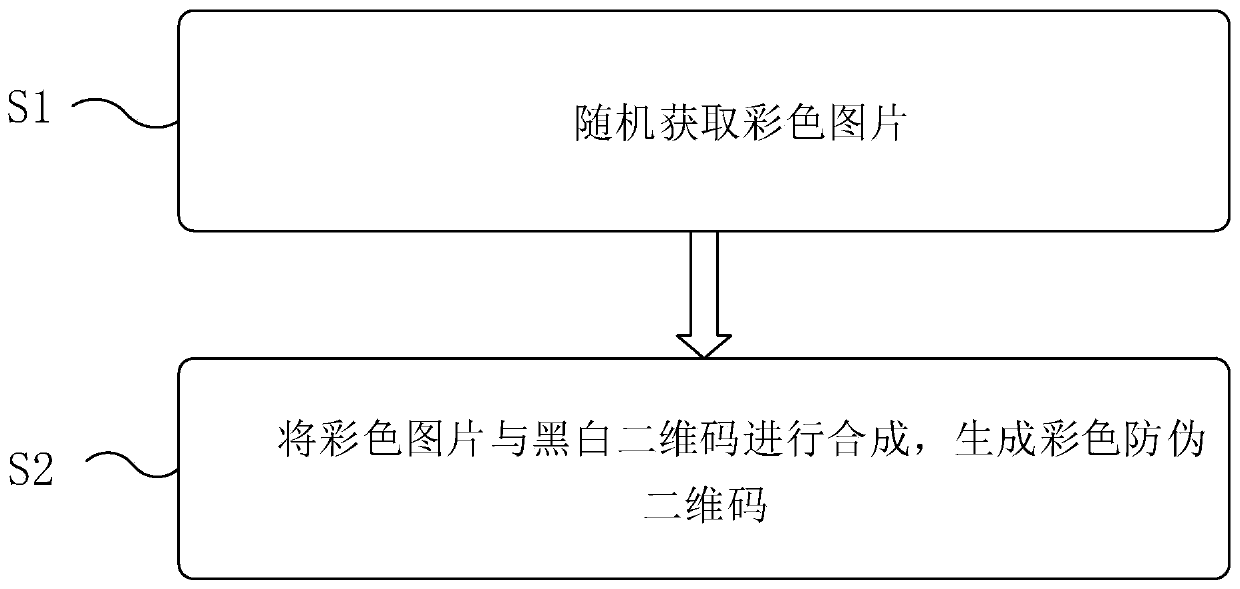
Generation method and device of color anti-counterfeiting two-dimensional code and anti-counterfeiting system
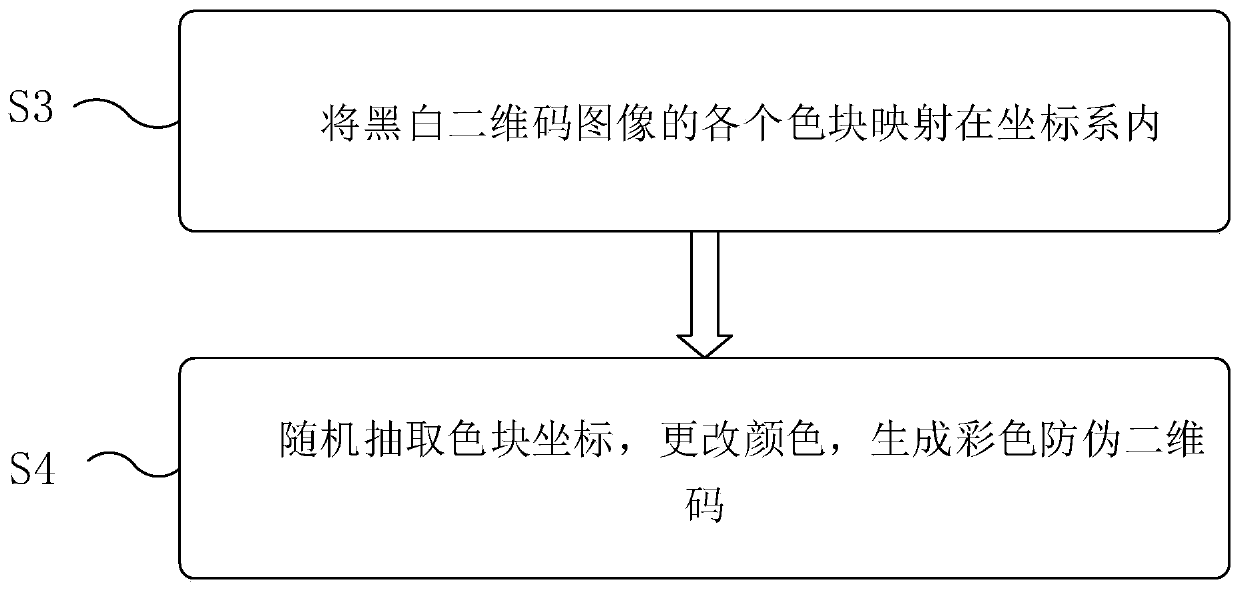
PendingCN111539503AReduce the possibility of counterfeitingProtection of rights and interestsCommerceRecord carriers used with machinesAlgorithmTheoretical computer science
The embodiment of the invention discloses an anti-counterfeiting mode, a generation method, a generation device and an anti-counterfeiting system of a color anti-counterfeiting two-dimensional code, and relates to the technical field of two-dimensional code anti-counterfeiting. The method comprises a synthesis method and a replacement method, the synthesis method comprises: randomly obtaining a color picture, and synthesizing the color picture with a black and white two-dimensional code to generate the color two-dimensional code; and the replacement method comprises: mapping each color block of the black and white two-dimensional code image into a coordinate system, randomly extracting the coordinates of the color block by utilizing an algorithm, changing the color, or changing the shape of the color block while changing the color and then generating a color anti-counterfeiting two-dimensional code. The problem that an existing two-dimensional code is low in safety can be solved, the possibility that the two-dimensional code is forged is greatly reduced, and rights and interests of consumers are guaranteed.
Owner:北京环网瑞通软件有限责任公司
Palm bioelectrical impedance spectrum measuring device for biological characteristic recognition
InactiveCN101889866BLow costNo light conditionsPerson identificationSensorsElectricityElectrical resistance and conductance
The invention discloses a palm bioelectrical impedance spectrum measuring device for biological characteristic recognition. The device comprises a singlechip which is respectively connected with a reset and clock system, an RS232 serial port, a keyboard, an impedance analyzing chip, an LCD display, a power conversion chip and a relay control circuit; a 5V power supply is arranged between the power conversion chip and the relay control circuit; the impedance analyzing chip is connected with a two / four-electrode conversion circuit; the two / four-electrode conversion circuit and the relay controlcircuit are respectively connected with a palm electrode switching circuit; and in the circuit of the palm electrode switching circuit, the output ends of four relays J1-J4 are respectively connectedwith HC and HV, and the output ends of another four relays are respectively connected with LV and LC. The palm biological impedance spectrum measuring device realizes four-electrode measurement of ten loops by opening and closing the eight relays, acquires sample data and is applicable to the biological characteristic recognition.
Owner:XIAN UNIV OF TECH
Ultrahigh-frequency fluorescence frangible bottle label
PendingCN105760924AGood printabilityStrong adhesionRecord carriers used with machinesRadio frequencyUltrahigh frequency
The invention relates to an ultrahigh-frequency fluorescence frangible bottle label. The bottle label comprises a decoration printing layer, a frangible membrane, polarity coating layers, an electronic label antenna and an electronic label chip. Polarity coating layers are arranged on two side surfaces of the frangible membrane in parallel and closely. The decoration printing layer is arranged on the outer surface of the polarity coating layer above the frangible membrane in parallel. The electronic label antenna is arranged on the outer surface of the polarity coating layer under the frangible membrane in parallel. The electronic label chip is arranged under the electronic label antenna. The electronic label antenna and the electronic label chip are connected together. An electronic label is arranged in the electronic label chip. The bottle label employs the frangible membrane as a base material, a high-safety intelligent chip is embedded in a printed antenna, thus the label has an intelligent card function self, radio frequency identification of the label can be carried out, and the multistage encryption and dual cipher protection chip data functions can be achieved. The bottle label achieves the common anti-fake of the physical anti-fake and the intelligent anti-fake and avoids the anti-fake oneness.
Owner:TIANJIN ZHONGTIAN LICENSE PRINTING
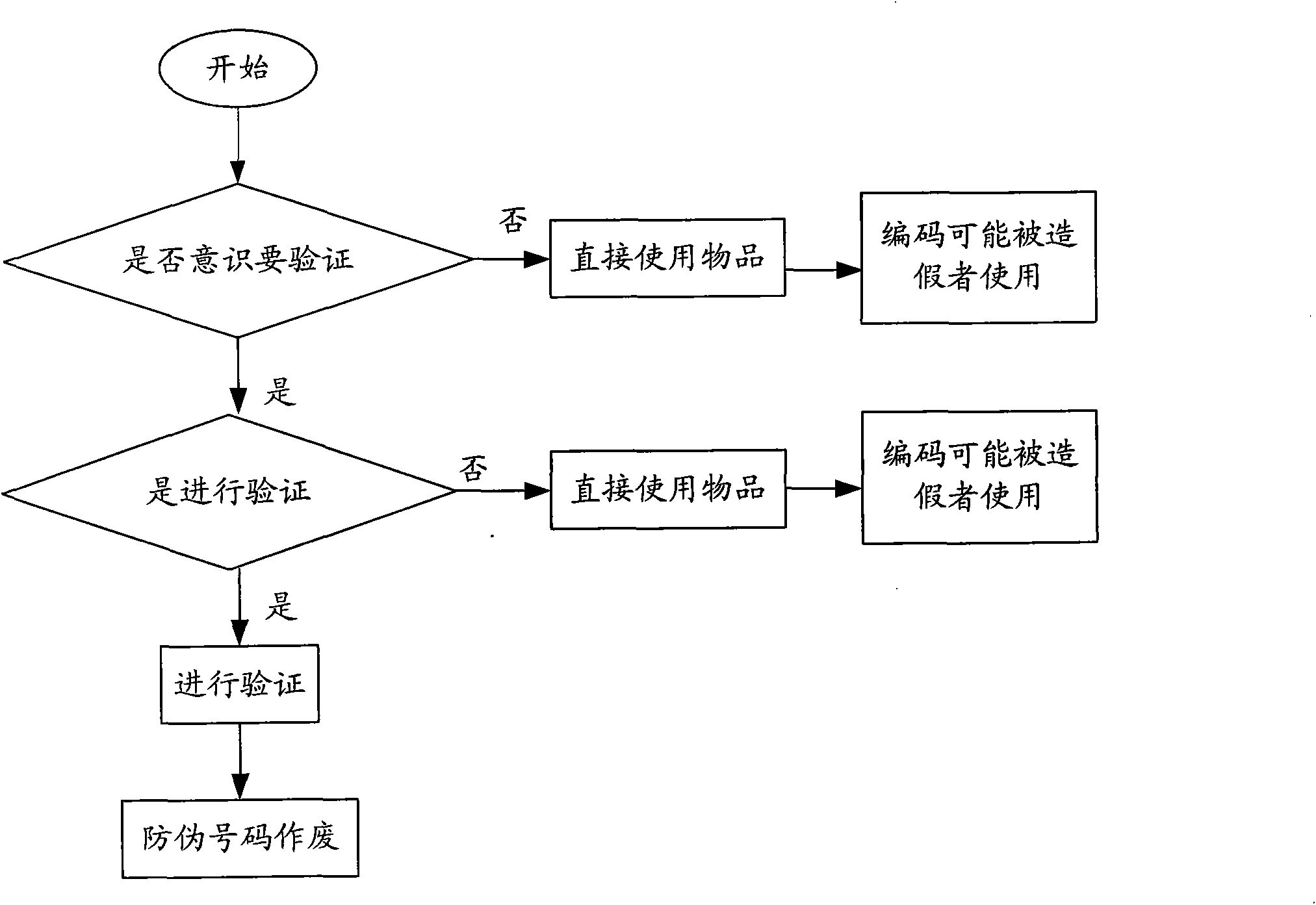
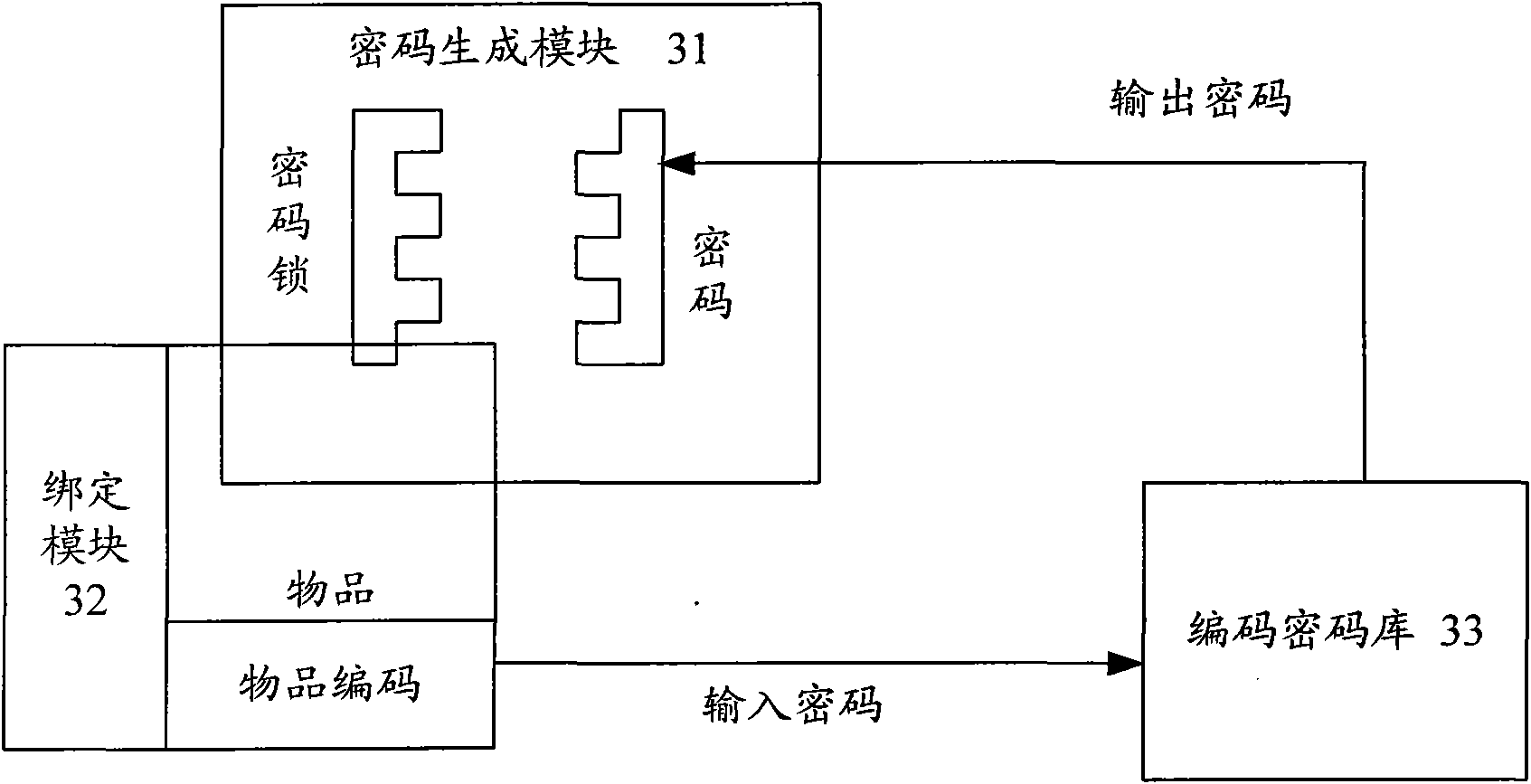
Article identification system and authorization method thereof
InactiveCN101853472ASolve the problem of low query rateCannot or cannot easily be forgedUser identity/authority verificationDigital data authenticationAuthorizationPassword
The invention discloses an article identification system, comprising a password generation module, an encoding generation and binding module and an encoding password database, wherein the password generation module is used for generating passwords, setting a password for a coded lock, sending the password to the encoding password database, and sending the coded lock to the encoding generation and binding module, wherein the password is used for unlocking the coded lock; the encoding generation and binding module is used for generating an article code, receiving the coded lock, and binding the article code with the coded lock; and the encoding password database is used for receiving, matching and storing the password and article code or when received the article code, searching correspondent password based on the article code and feed the password back to a user. The invention also discloses an article identification authorization method. The invention provides a brand-new anti-forgery technology which can be widely applied to article identification, article anti-forgery, accreditation, etc.
Owner:祝明敬
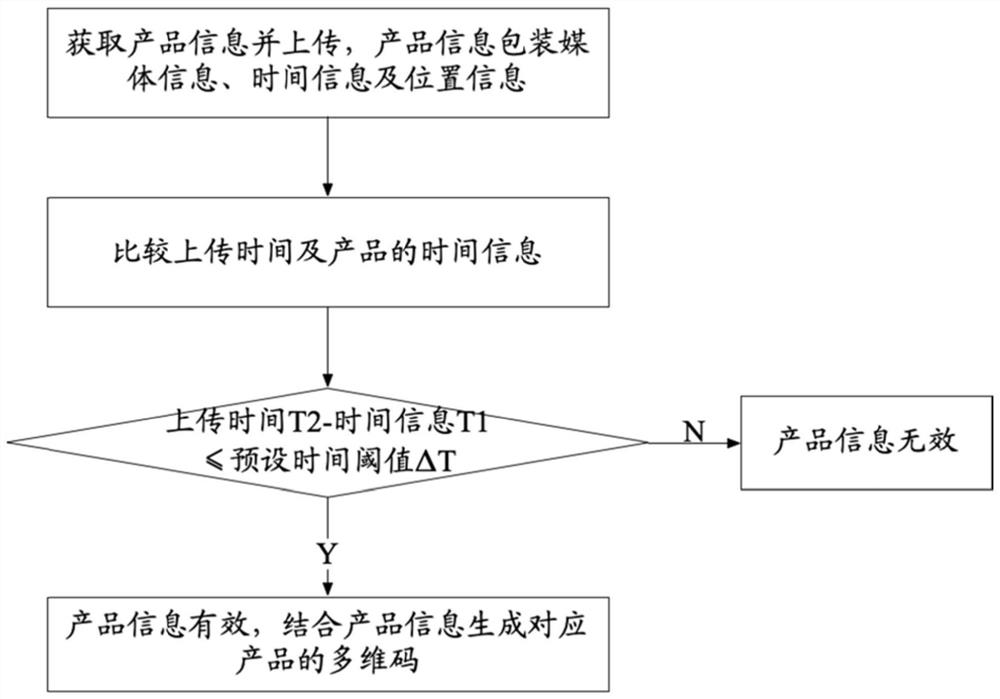
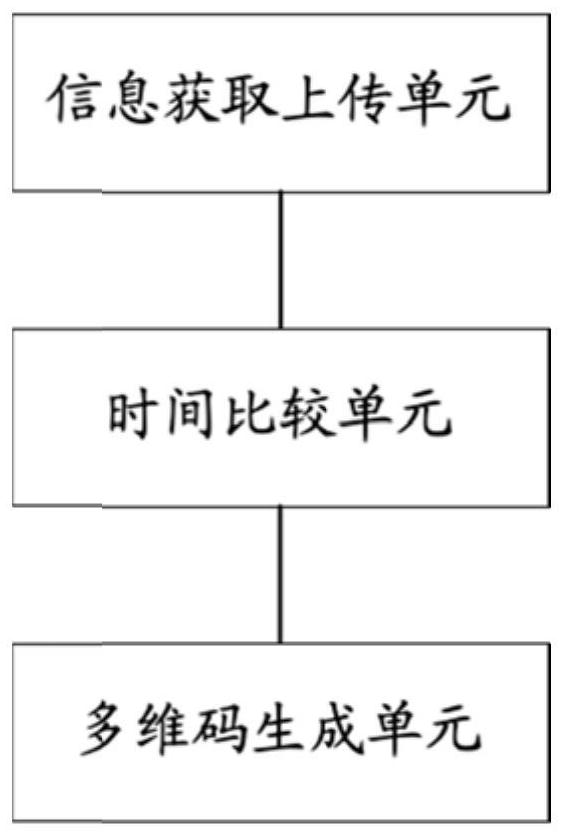
Multi-dimensional code generation method and system and multi-dimensional code verification method and system
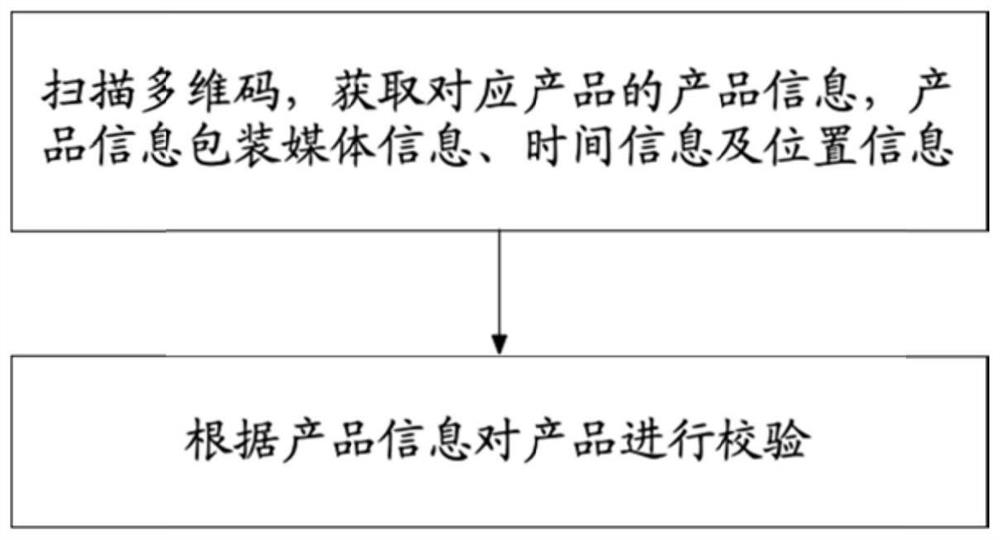
PendingCN111814940AReduce the possibility of counterfeitingPrevent secondary useMultimedia data indexingMetadata multimedia retrievalCode generationTime information
The invention discloses a multi-dimensional code generation method and system and a multi-dimensional code verification method and system. The generation method comprises the steps that product information is acquired and uploaded, and media information, time information and position information are packaged in the product information; comparing the uploading time with the time information of theproduct; if the uploading time and the time information of the product are within a preset time threshold, judging that the product information is valid, and generating a multi-dimensional code corresponding to the product in combination with the product information; and if the uploading time and the time information of the product are not within the preset time threshold, judging that the productinformation is invalid, and not generating a multi-dimensional code corresponding to the product. The packaging media information, the time information and the position information are introduced into the multi-dimensional code, uniqueness confirmation is completed from the perspective that counterfeit goods and genuine goods cannot be produced at the same time and position, and the possibility that the counterfeit goods are forged through the two-dimensional code is eradicated.
Owner:张家港市爱上旅途网络科技有限公司
Soil sampling method based on IOT (Internet of things) technology
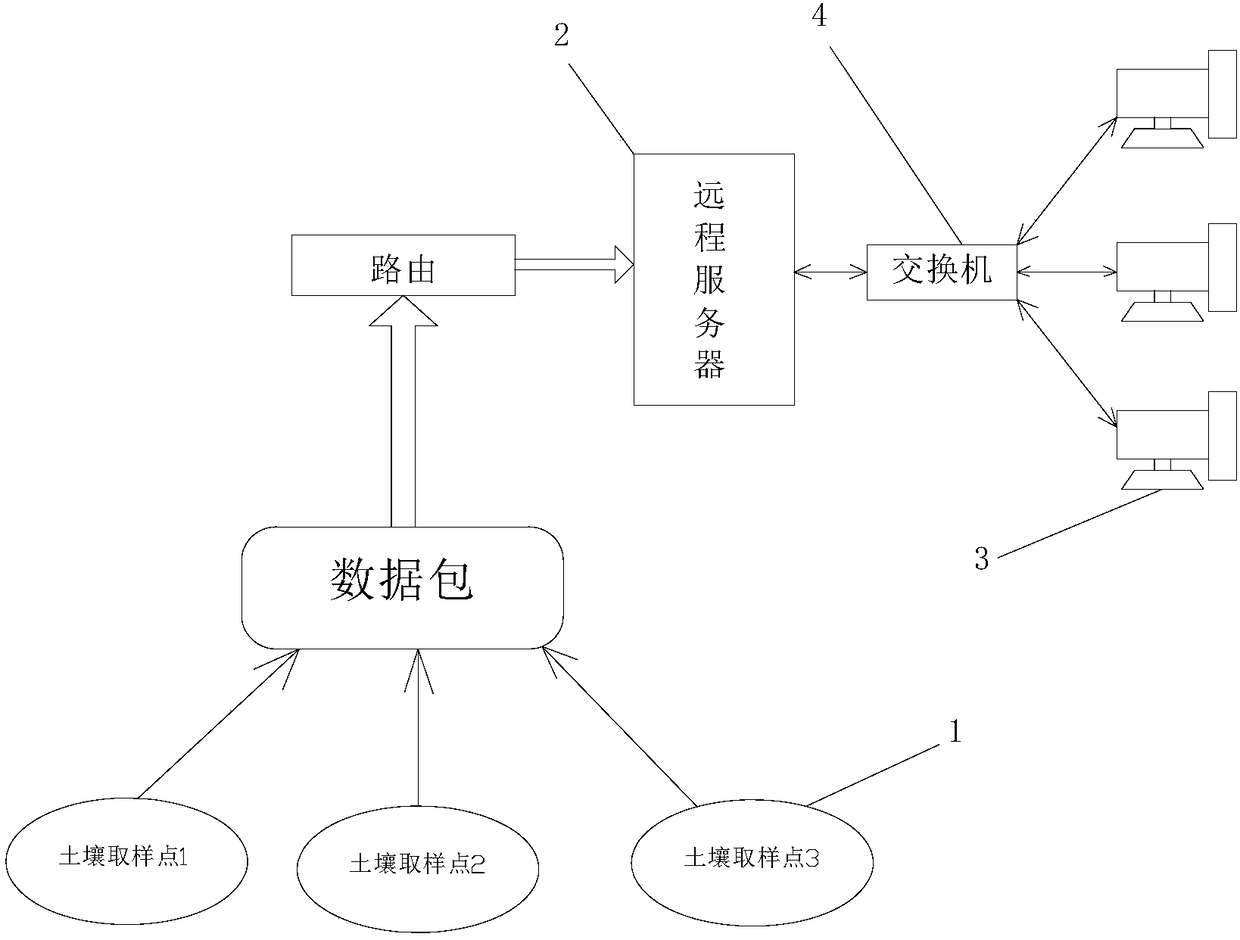
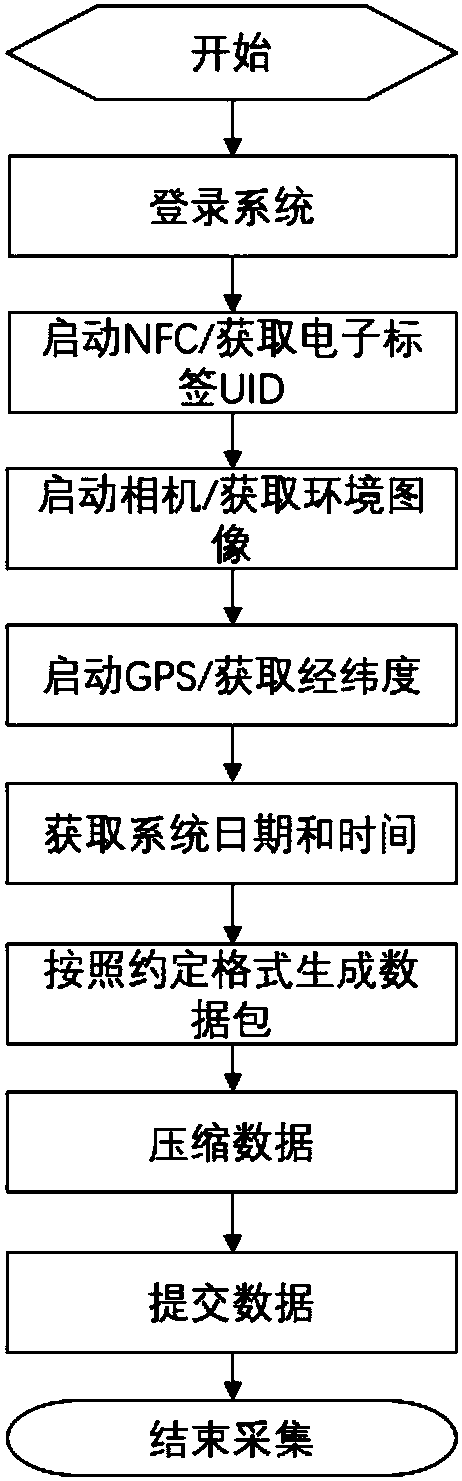
InactiveCN108225814AEasy analysis managementAvoid confusionWithdrawing sample devicesTransmissionTemporal informationGeolocation
The invention discloses a soil sampling method based on an IOT (Internet of things) technology. The method is characterized by comprising the following steps: 1) sampling personnel stick labels to sampling vessels; 2) mobile communication terminals and the sampling vessels are carried over to planned sampling spots, and soil samples are sampled and are contained in the sampling vessels; 3) the sampling personnel log on soil sampling APP installed on the mobile communication terminals, and label information is recognized through the soil sampling APP; 4) sampling personnel log-on accounts, thelabel information, geographical position information of the sampling spots and sampling time information are sent to a remote server together by using the soil sampling APP. During actual work, analysis staff can very easily carry out analysis management on collected soil samples through the remote server, and the possibility that the soil samples are confused and counterfeit is avoided fundamentally.
Owner:FOSHAN POLYTECHNIC
Blockchain-based red wine scarcity proofing method
InactiveCN108734480AGuarantee authenticityGuaranteed scarcityMultiple keys/algorithms usageCommerceSmart contractBottle
The present invention particularly relates to a blockchain-based red wine scarcity proofing method. The method comprises the following steps that: (A) different public keys and hidden private keys areprepared for each bottle of red wine; (B) the total number of bottles and the number of remaining bottles of the batch of red wine are recorded on the blockchain, and the batch of red wine is writteninto a blockchain network; (C) smart contracts are deployed on the blockchain to provide query verification and status change functions; (D)before purchase, wine information of the red wine, and thetotal number of bottles and the number of remaining bottles of the batch of red wine can be inquired by a customer according to the public key; and (E) after opening the bottle, the customer can modify the red wine status and the number of remaining bottles on the blockchain according to the private key. According to the method provided by the present invention, the authenticity and scarcity of the wine can be inquired by the customer through the public key at any time, and the status of the red wine on the blockchain can be updated through the private key, so that the possibility of forgery can be reduced; and the blockchain network ensures the data to be authentic and reliable, scarcity verification and status update can be automatically performed by using the smart contracts, human interference cannot occur, and the credibility of the data is increased.
Owner:四川海纳仁东科技有限公司
Foldable Internet of Things cycle use box and use method thereof
PendingCN109795786AEasily damagedReduce packaging material costsNon-removalbe lids/coversRigid containersWork periodEcological environment
The invention relates to the technical field of Internet of Things, in particular to a foldable Internet of Things cycle use box and a use method thereof. The foldable Internet of Things cycle use boxcomprises a box body and an upper flip cover, two sides of a front fixed plate and a rear fixed plate are separately connected through foldable side plates, each foldable side plate comprises a firstside plate and a second side plate, the near side of the first side plate is rotatably connected with the near side of the second side plate, one end of a bottom plate is rotatably connected with thefirst side plate and the rear side plate, and the other end of the bottom plate can turnover upwards from the interior of the box body. Compared with the prior art, the foldable Internet of Things cycle use box has the advantages that plastic adhesive tape and plastic fillers are put an end to use, damage of logistics industry to the ecological environment is improved, the logistics industry packing material cost is reduced, energy conservation and environment protection are achieved, the box body can be rotatably placed in the upper flip cover after folding, and transportation and storage are facilitated; and through a structural design of an Internet of Things intelligent lock, a spring of a lock body does not be participated in the starting process, a motor load and power consumption are reduced, and the integral product standby and use time are greatly prolonged.
Owner:SHANGHAI QINQI TECH CO LTD
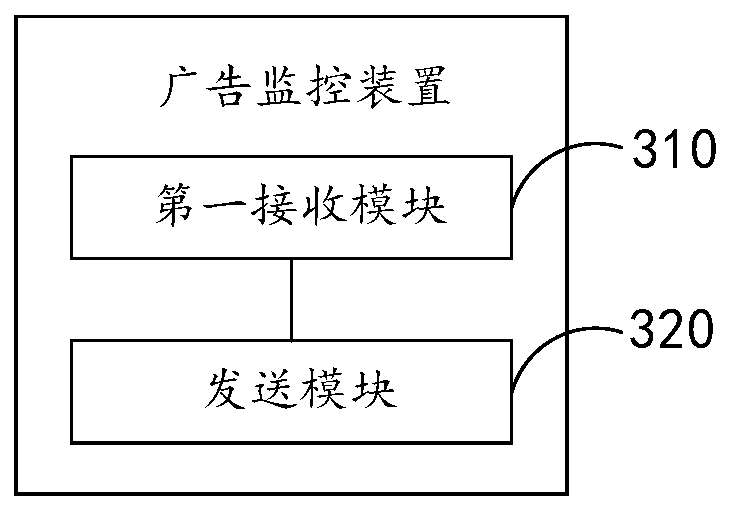
Advertisement monitoring method and device, electronic equipment and storage medium
PendingCN111062748AReduce the possibility of counterfeitingAccurate supervisionMarketingIndustrial engineeringServer
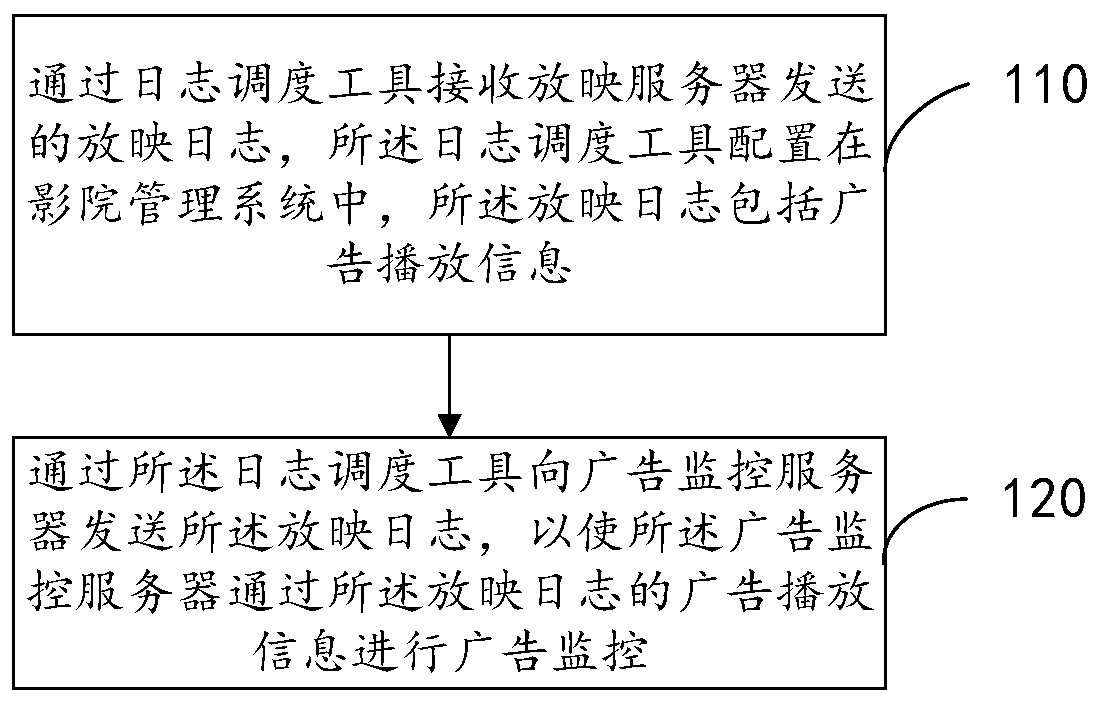
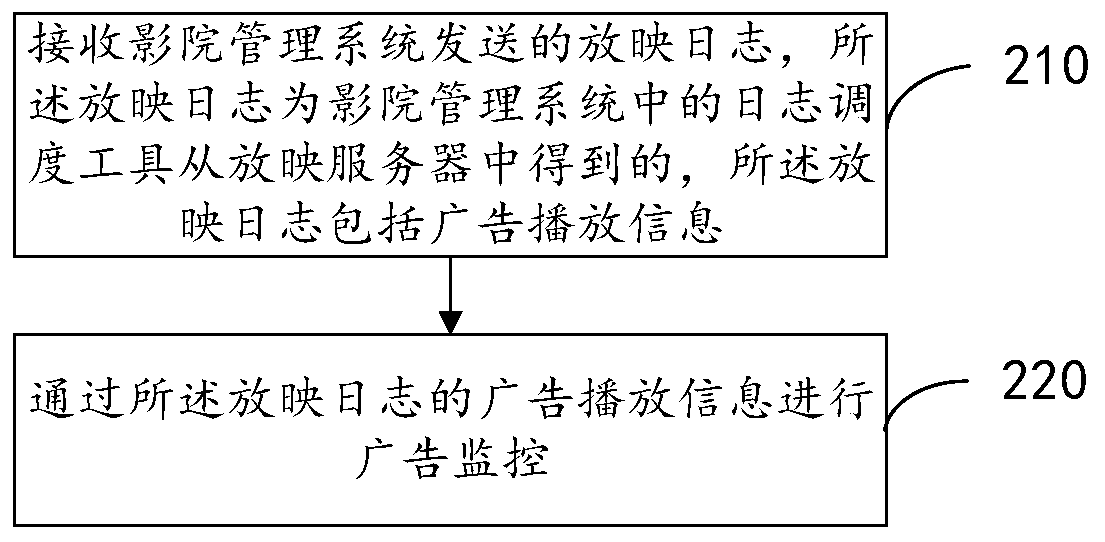
The invention provides an advertisement monitoring method and device, electronic equipment and a storage medium, and the method comprises the steps: receiving a projection log transmitted by a projection server through a log scheduling tool, wherein the log scheduling tool is configured in a cinema management system, and the projection log comprises advertisement playing information; and sending the projection log to an advertisement monitoring server through the log scheduling tool, so as to enable the advertisement monitoring server to perform advertisement monitoring through advertisement playing information of the projection log. According to the embodiment of the invention, the projection log sent by the projection server is directly received through the log scheduling tool, and thenthe projection log is sent to the advertisement monitoring server, so that the advertisement monitoring server can perform advertisement monitoring according to the advertisement playing information in the projection log. Therefore, the possibility that the projection log is forged can be reduced, and the advertisement before movie mapping can be accurately supervised.
Owner:MIAOZHEN INFORMATION TECH CO LTD
Internet of things intelligent clamp and use method thereof
PendingCN109703898AReduce the possibility of counterfeitingClosely connectedStampsCo-operative working arrangementsLogistics managementSpring force
The invention relates to the technical field of internet of things, in particular to an internet of things intelligent clamp and a use method thereof. The intelligent clamp comprises a motion part anda limiting part matched with the motion part; the motion part comprises a motion part body with an inner cavity and a driving mechanism, a first connecting plate and a second connecting plate which are connected through a spring are arranged in the inner cavity in the motion direction of the motion part, the outer end of the first connecting plate is provided with a plunger, the second connectingplate is connected with the driving mechanism, the plunger can be matched with the limiting part to achieve locking of the intelligent clamp under the effect of spring force, and under driving of thedriving mechanism, locking of the intelligent clamp can be relieved. Compared with the prior art, the clamp has the advantages of anti-fake, wherein illegal exchange and making contact with objects in a logistics package can be prevented; clearing up of legal liability of all parties in the full logistics flow; environment friendliness; unique consignee assigning; privacy protection; and full-process recording of logistics environment physical parameters (temperature / humidity / acceleration / air pressure and the like)
Owner:SHANGHAI QINQI TECH CO LTD
Anti-counterfeiting technology for manual tear sheet
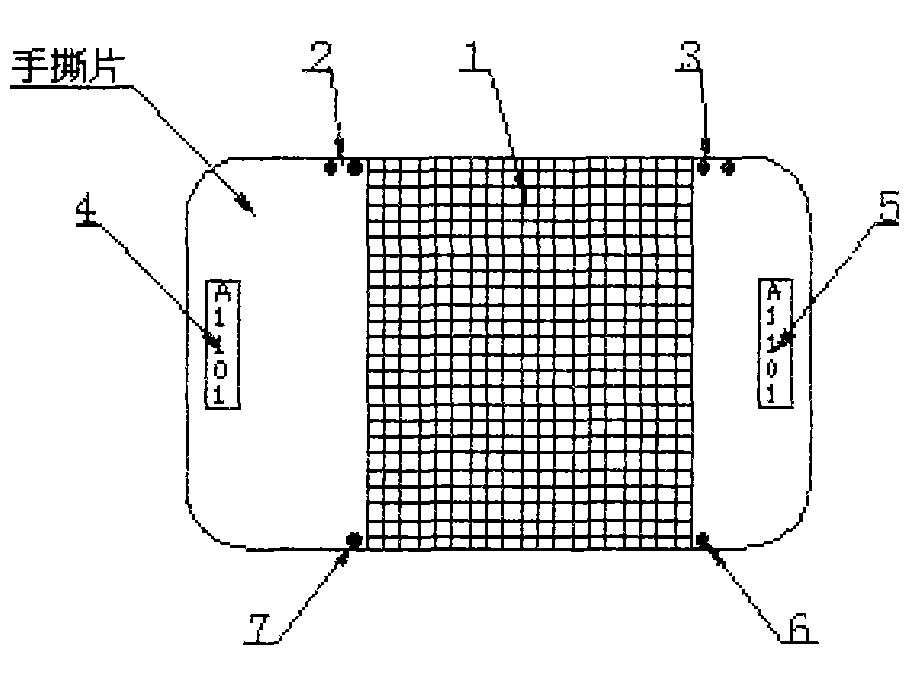
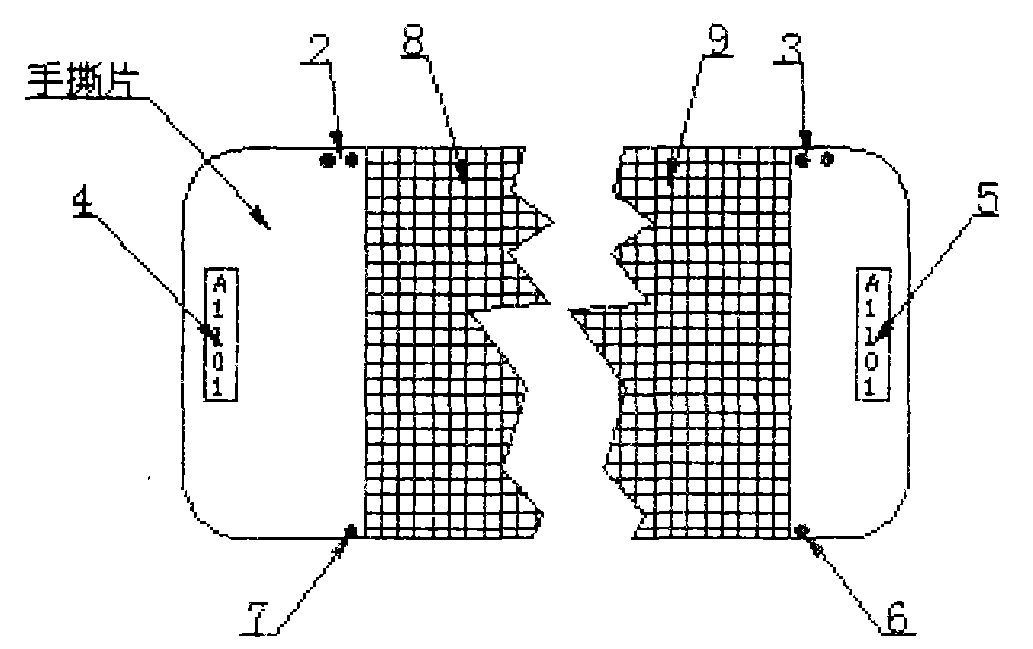
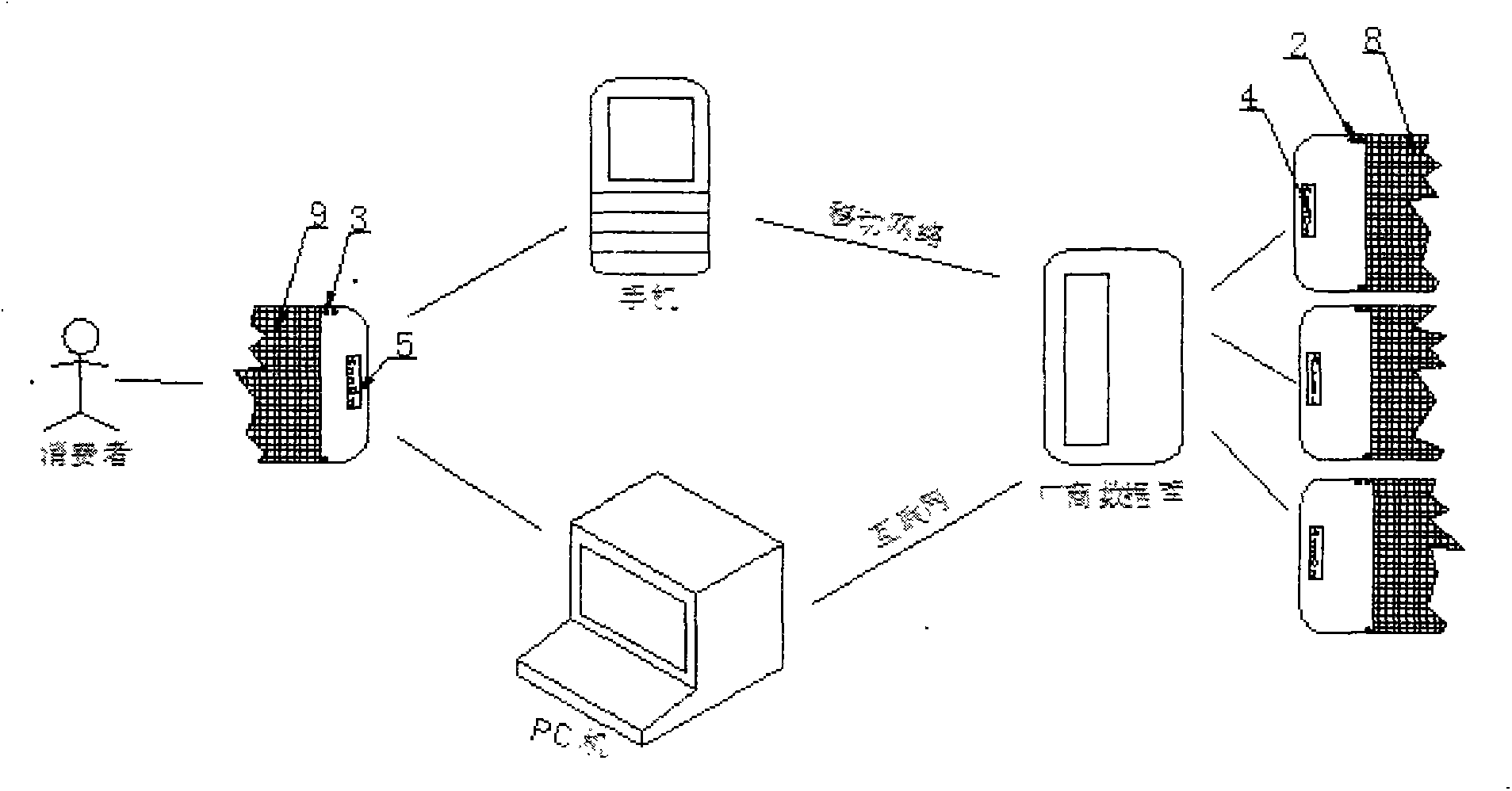
InactiveCN103456239AIngenious ideaReduce the possibility of counterfeitingStampsIdentification meansMechanical engineeringMesh grid
The invention relates to an anti-counterfeiting technology, in particular to an anti-counterfeiting technology for a manual tear sheet. The anti-counterfeiting technology is implemented by the aid of the manual tear sheet. The middle area of the manual tear sheet is a tear area, grid lines are printed in the tear area, double points of a preservation strip are arranged on the left upper side of the tear area, double points of a checking strip are arranged on the right upper side of the tear zone, a single point of the preservation strip arranged on the left lower side of the tear area, and a single point of the checking strip is arranged on the right lower side of the tear area; a preservation flow code and a checking flow code are respectively printed on the left side and the right side of the manual tear sheet; after the tear area of the manual tear sheet is torn, the preservation strip is arranged on the left side of the manual tear sheet, and the checking strip which is adhered onto a commodity is arranged on the right side of the manual tear sheet. The anti-counterfeiting technology has the advantages that when the tear area is torn, two irregular tear cracks which cannot be copied can be obtained according to a principle that identical cracks cannot be formed on two different pieces of paper, and opening cracks of the checking strip and the preservation strip are compared with each other in a follow-up procedure, so that an anti-counterfeiting effect can be realized for the manual tear sheet, the possibility that the manual tear sheet is counterfeited by criminals is eliminated, operation is simple and convenient, and the anti-counterfeiting technology is convenient to implement and is perfect.
Owner:张宁
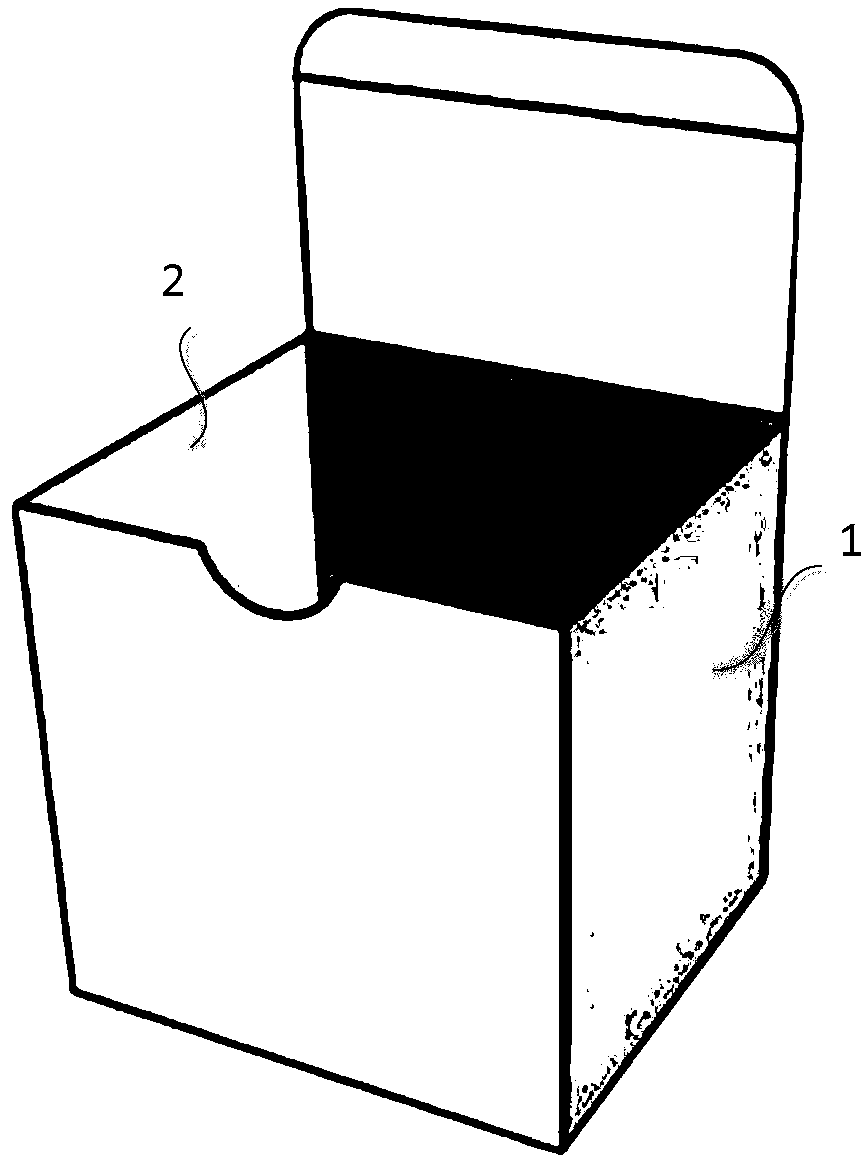
Article anti-counterfeiting method based on multiple identifiers, and system thereof
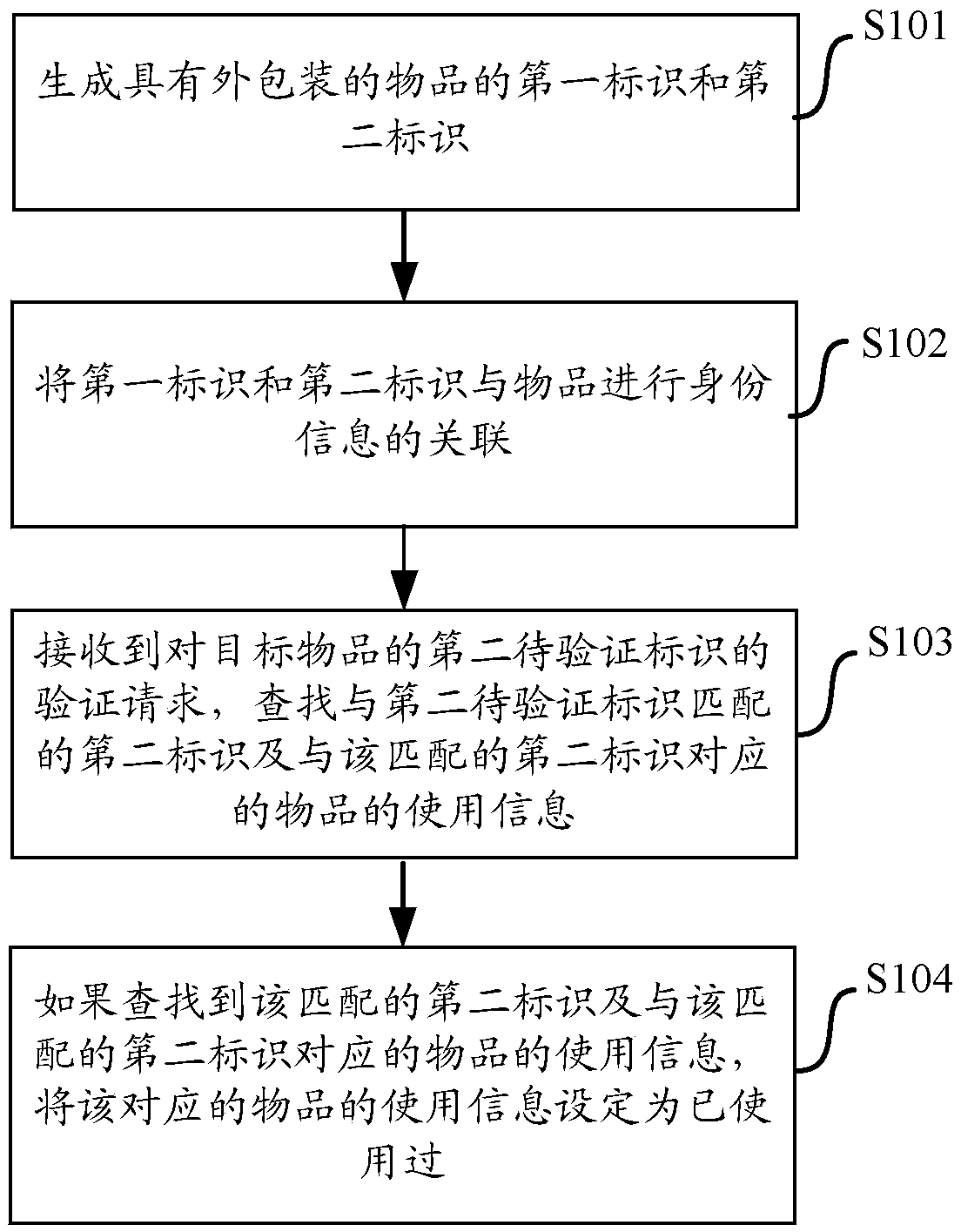
PendingCN110503437AImprove real reliabilityImprove convenienceCo-operative working arrangementsCommerceUser identifierComputer science
The invention provides an article anti-counterfeiting method based on multiple identifiers, an article anti-counterfeiting server, a client and an article anti-counterfeiting package. The article anti-counterfeiting method comprises the steps: generating a first identifier and a second identifier of an article with a package, wherein the first identifier and the second identifier are used for carrying out the identity verification and use condition verification of the article, and the first identifier can be obtained before the article is used, and the second identifier is in a hidden state before the article is used and is acquired after the article is used; associating the first identifier and the second identifier with identity information of an article; receiving a verification requestfor a second to-be-verified identifier of the target article, and searching for a second identifier matched with the second to-be-verified identifier and the use information of the corresponding article; and if the corresponding article is found, setting the use information of the corresponding article to be used. According to the scheme of the invention, the reliability of product anti-counterfeiting verification by a user can be effectively improved.
Owner:喜地霁石文化传媒(北京)有限公司 +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com