Safety access system and method for guaranteeing source address authenticity by using token mechanism
A technology of secure access and source address, which is applied in the field of network security and can solve problems such as source address forgery
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0053] Embodiment 1: Use the hash value of identity information to construct a 128-bit access address, and use a 128-bit IPv6 address as a routing address to realize the separation of user identity and location. among them:
[0054] (1) The access address structure is:
[0055] The access address is 128 bits, the home prefix is issued by the local network access server, and the hash value of the identity information is selected by the user. Definition of each field of the access address:
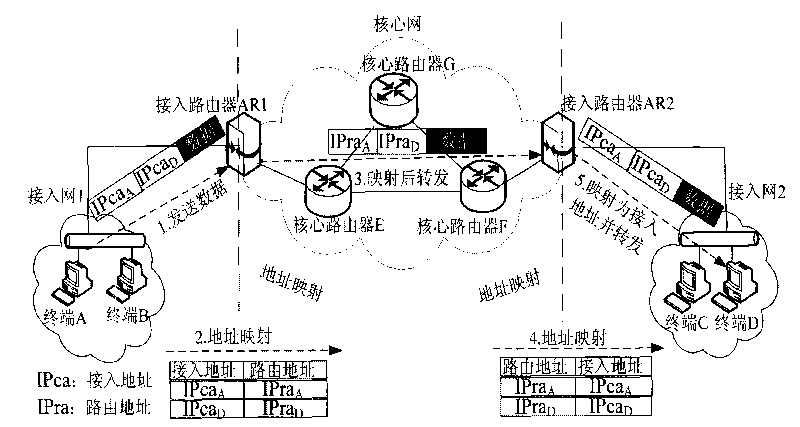
[0056] Home prefix: 24 bits, the home domain prefix of the terminal. Assign the access address home prefix of each domain according to the geographic location of the management domain to improve the access address search efficiency. The home prefix facilitates when the terminal moves to a new access network, the access router promptly informs the mapping server in the home domain of the terminal to update the mapping relationship between the terminal access address and the routing address;
[...
Embodiment 2
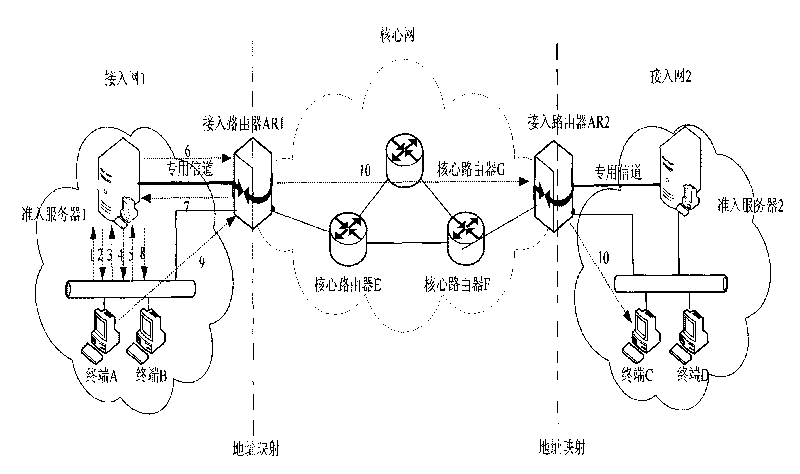
[0060] Embodiment 2: To implement the secure access system of the present invention, it is necessary to deploy an access server in the access network of the "address separation mapping" network, install the software of the access negotiation module and the data packet verification module on the access router, and Install access client software on the terminal:
[0061] (1) Access server: save for the terminal when the terminal first accesses Table; publish its own public key for terminal inquiries; assign tokens that mark the identity of the terminal; access servers can query each other; access negotiation control module and token distribution module are installed in the access server;
[0062] The admission negotiation control module installed in the admission server is responsible for receiving and processing terminal access requests. When verifying that the terminal access address requests access for the first time or not for the first time, the corresponding relationship betwee...
Embodiment 3
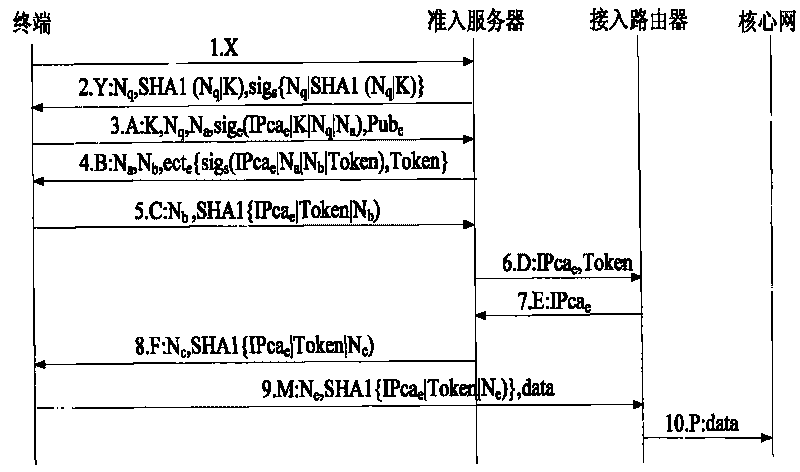
[0066] Embodiment 3: The invented secure access method is implemented by defining a specific message format, that is, the payload in the invented secure access method is defined in a specific message, and the secure access in embodiment 2 is performed through the message The interaction in the system specifically implements the secure access method.
[0067] The present invention deploys the access server in the access network, installs the software of the access negotiation module and the data packet verification module on the access router, installs the access client software on the terminal, and is designed for access security The access method guarantees the authenticity of the source address in the address separation mapping network. Such as image 3 As shown, image 3 The terminal A in the access network 1 communicates with the terminal C in the access network 2, combining figure 2 , Its secure access method is as follows:
[0068] Step 1: The terminal A in the access net...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com