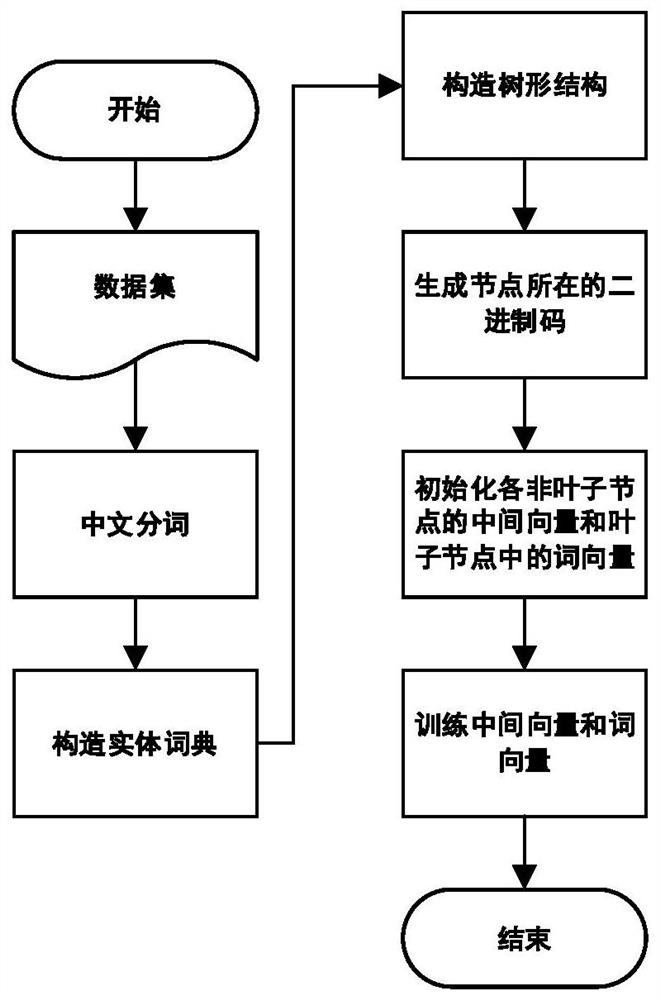
Patents
Literature
87results about How to "Improve query rate" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
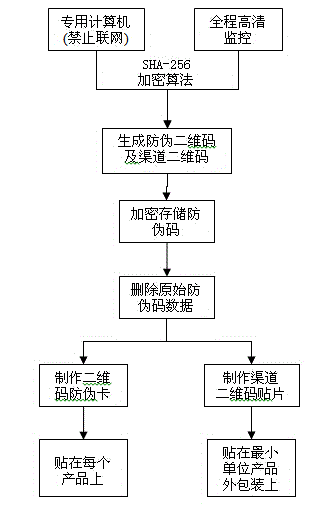
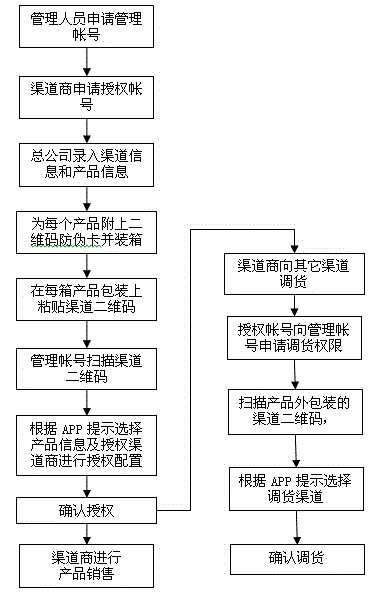
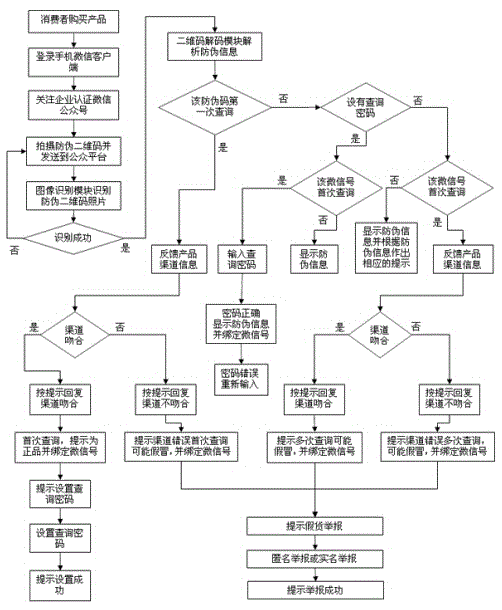
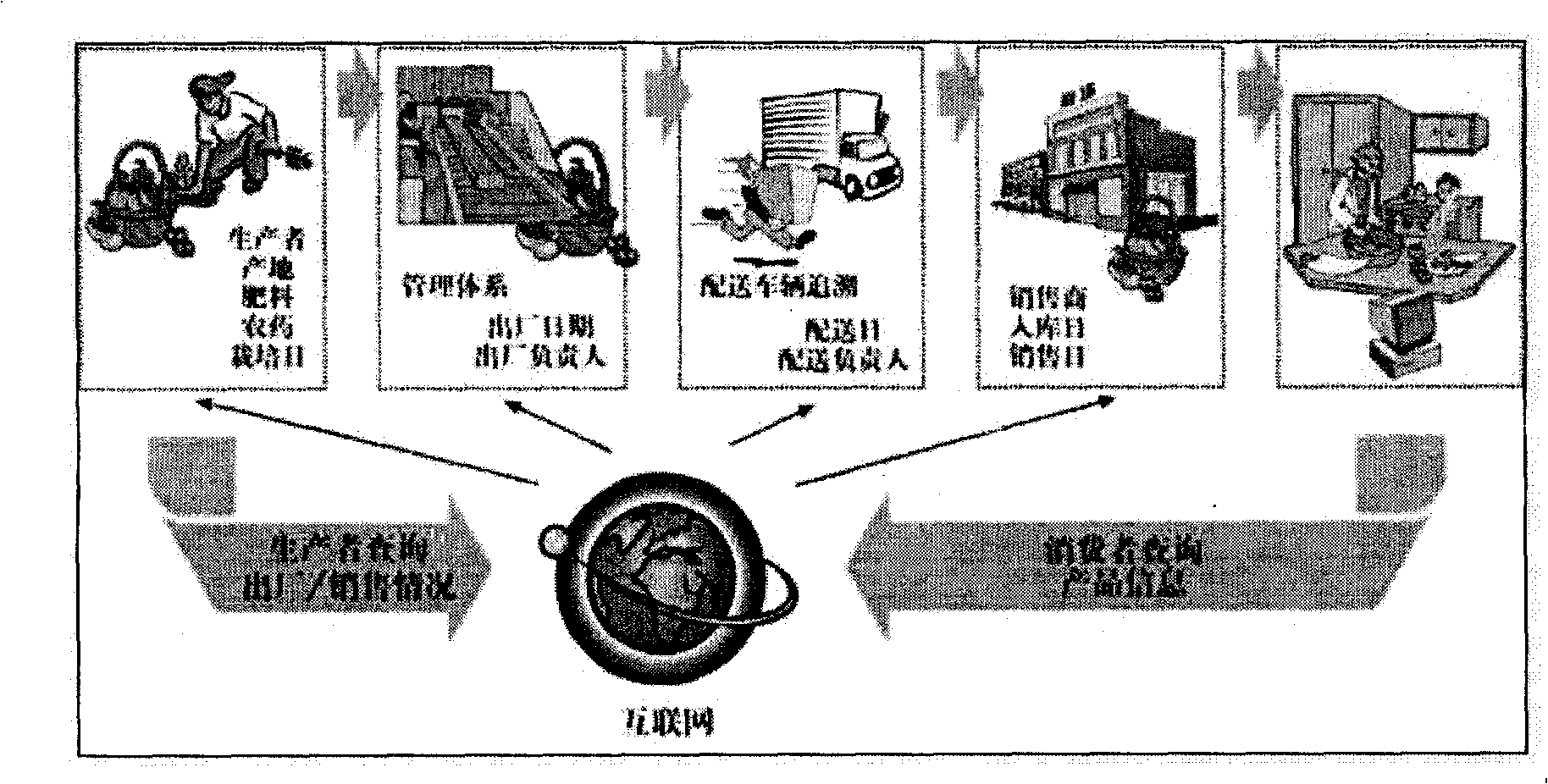
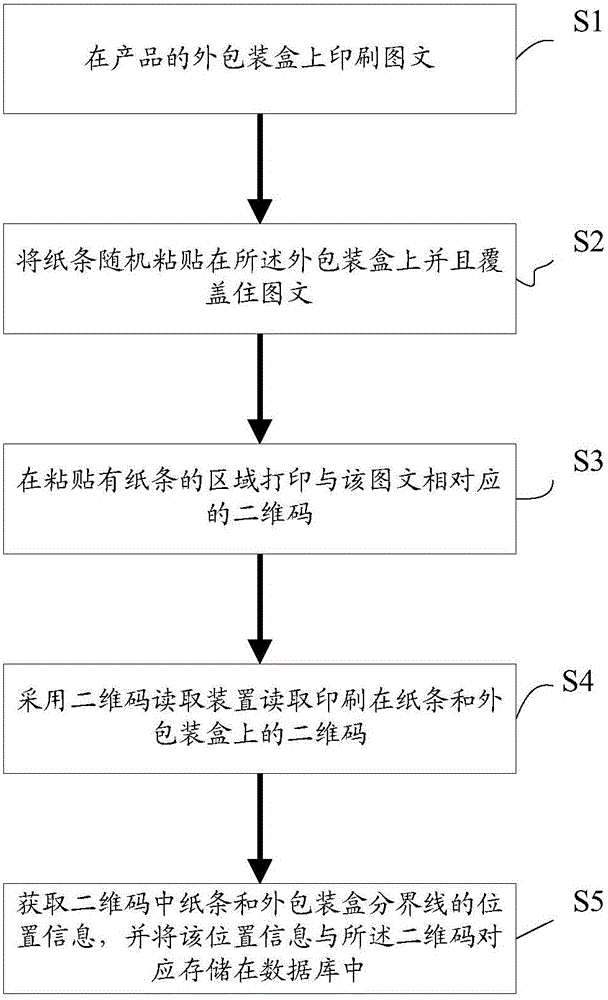
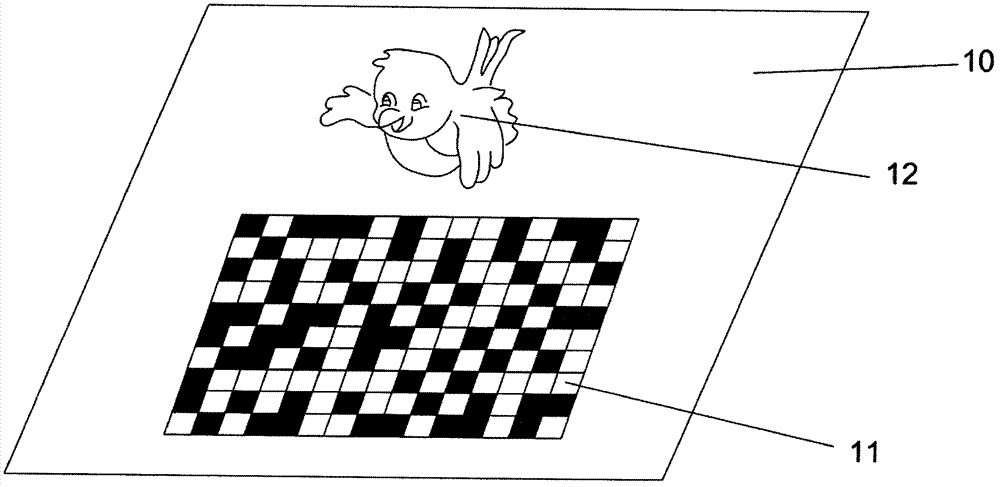
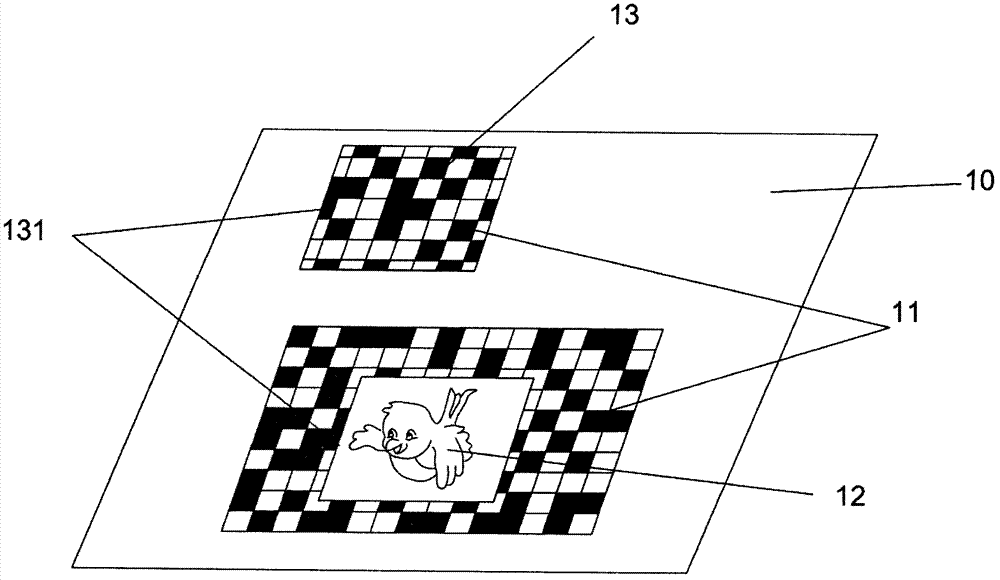
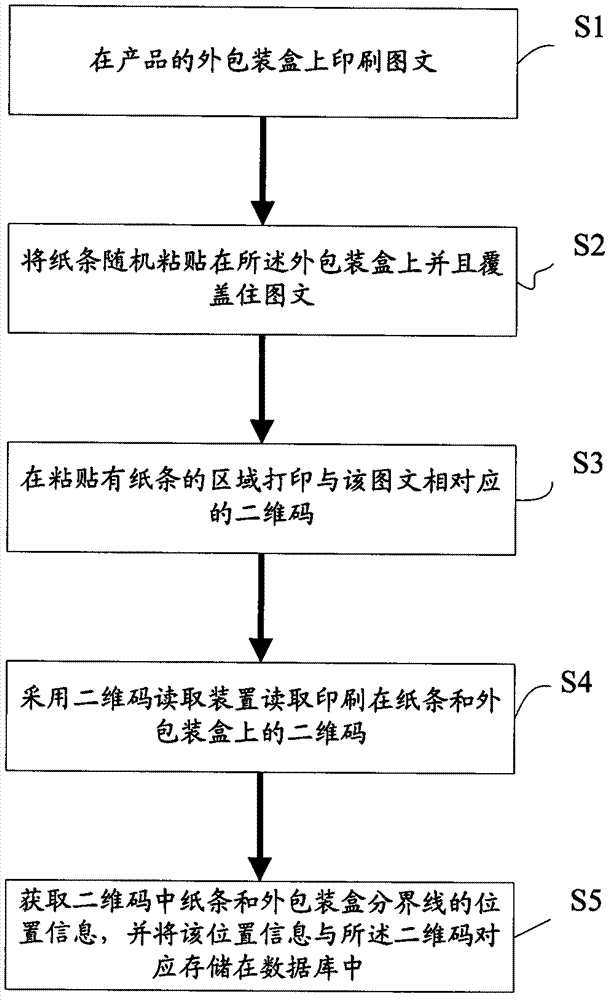
Wechat-platform-based two-dimensional code anti-fake and anti-channel conflict inquiry system and method
InactiveCN104156862AConvenient queryImprove trustCommerceRecord carriers used with machinesCoding decodingClient-side
The invention discloses a wechat-platform-based two-dimensional code anti-fake and anti-channel conflict inquiry system and a wechat-platform-based two-dimensional code anti-fake and anti-channel conflict inquiry method. The wechat-platform-based two-dimensional code anti-fake and anti-channel conflict inquiry system comprises a wechat client, a wechat platform and an anti-fake and anti-channel conflict inquiry server, wherein the anti-fake and anti-channel conflict inquiry server comprises a two-dimensional code generating module, a image recognizing module, a two-dimensional code decoding module, a database module and a channel management system; the image recognizing module is in charge of processing an anti-fake two-dimensional code picture uploaded by a customer; the two-dimensional code decoding module extracts anti-fake information of a product; the database module comprises a product and anti-fake data table and a database management system (DBMS); the wechat client exchanges the two-dimensional code with the server through the wechat platform; the server processes and decodes the two-dimensional code; the DBMS inquires the product and anti-fake data table for performing anti-fake and anti-channel conflict inquiry and verification on the product. Anti-fake inquiry of the two-dimensional code is performed through the wechat platform, so that consumer confidence is high, inquiry is convenient and rapid and a result is reliable; an anti-fake code contains channel information, so that anti-fake and anti-channel conflict operation can be achieved effectively.
Owner:SICHUAN TOOGU INFORMATION TECH
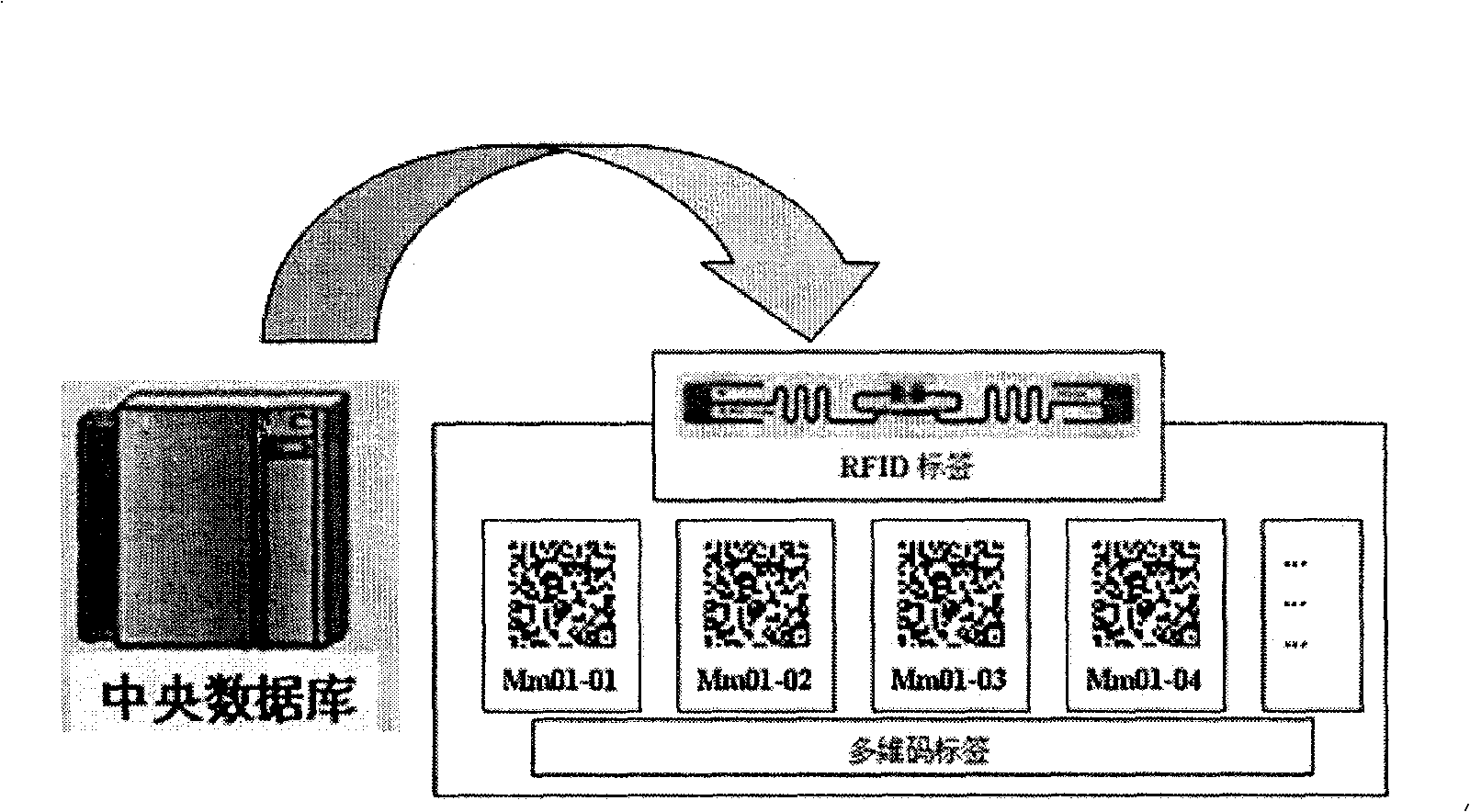
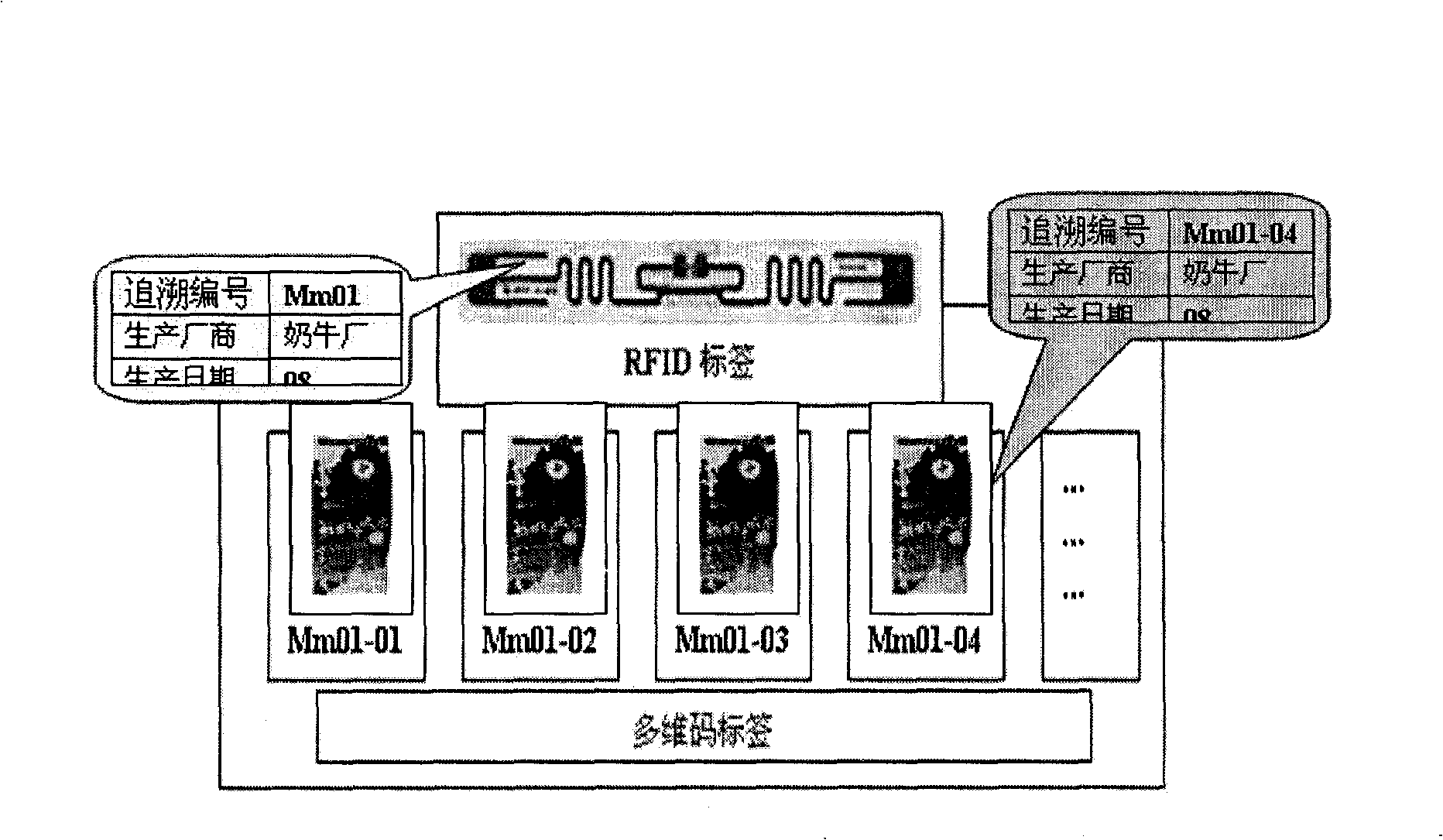
Article anti-counterfeiting system combining radio frequency identification and two-dimension code
InactiveCN101515352AIncrease active participationCompress living spaceCo-operative working arrangementsCommerceLogistics managementConfidentiality
The invention discloses an article anti-counterfeiting system combining radio frequency identification and two-dimension code, which consists of a center database, a radio-frequency identification label, and a two-dimension code icon, wherein the center database consists of a production management module, a logistics and storage module, a sales module, and a consumption query module; the radio-frequency identification label is stuck to an outer packing of a product, and information in a chip of the radio-frequency identification label is related to product information of the two-dimension code icon; the two-dimension code icon is stuck to a single product or an inner packing in the outer packing; and a user compares the information stored in the radio-frequency identification label with the center database to realize identification and tracing of the outer packing, and compares the product information of the two-dimension code icon with the center database through a verification terminal to realize verification of the single product or the inner packing. The article anti-counterfeiting system has the advantages of physical uniqueness, non-contact information identification, high confidentiality, strong tracing property, good fouling resistance, low price, simple implementation and the like.
Owner:段建国
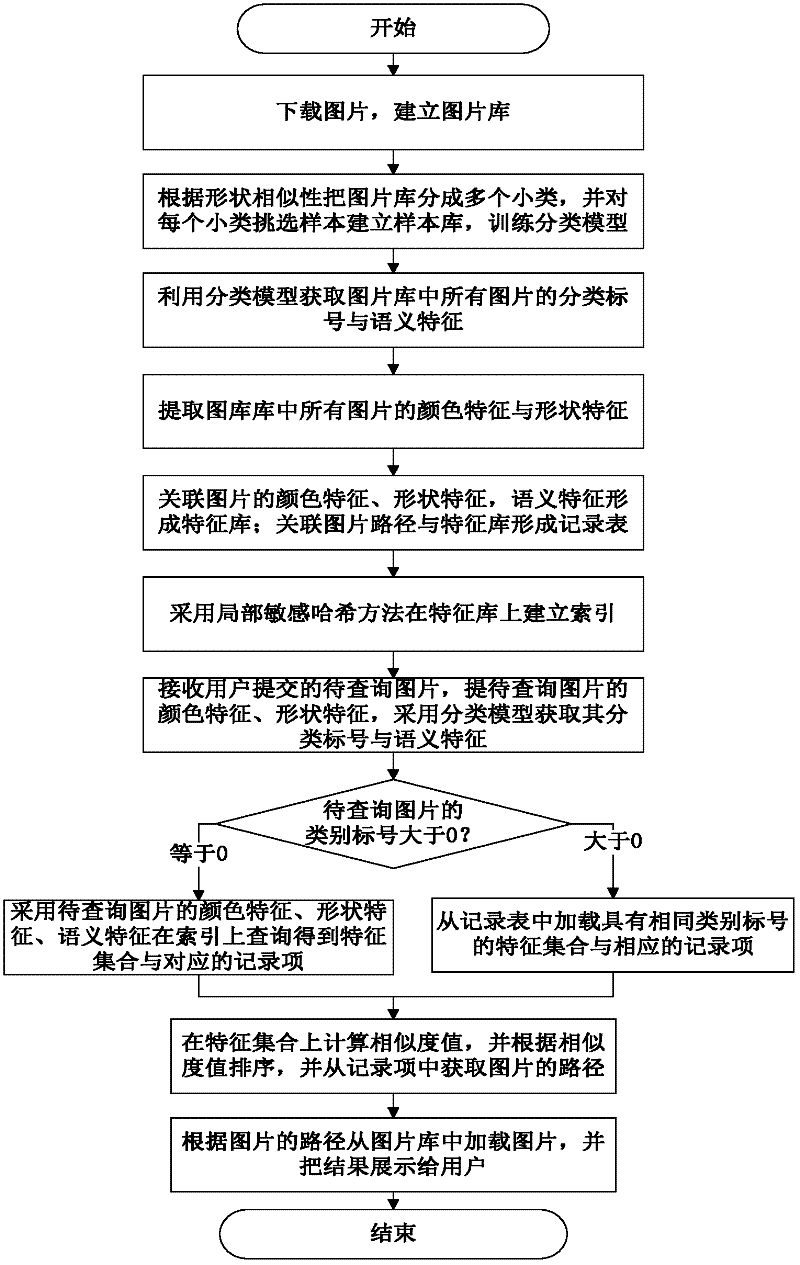
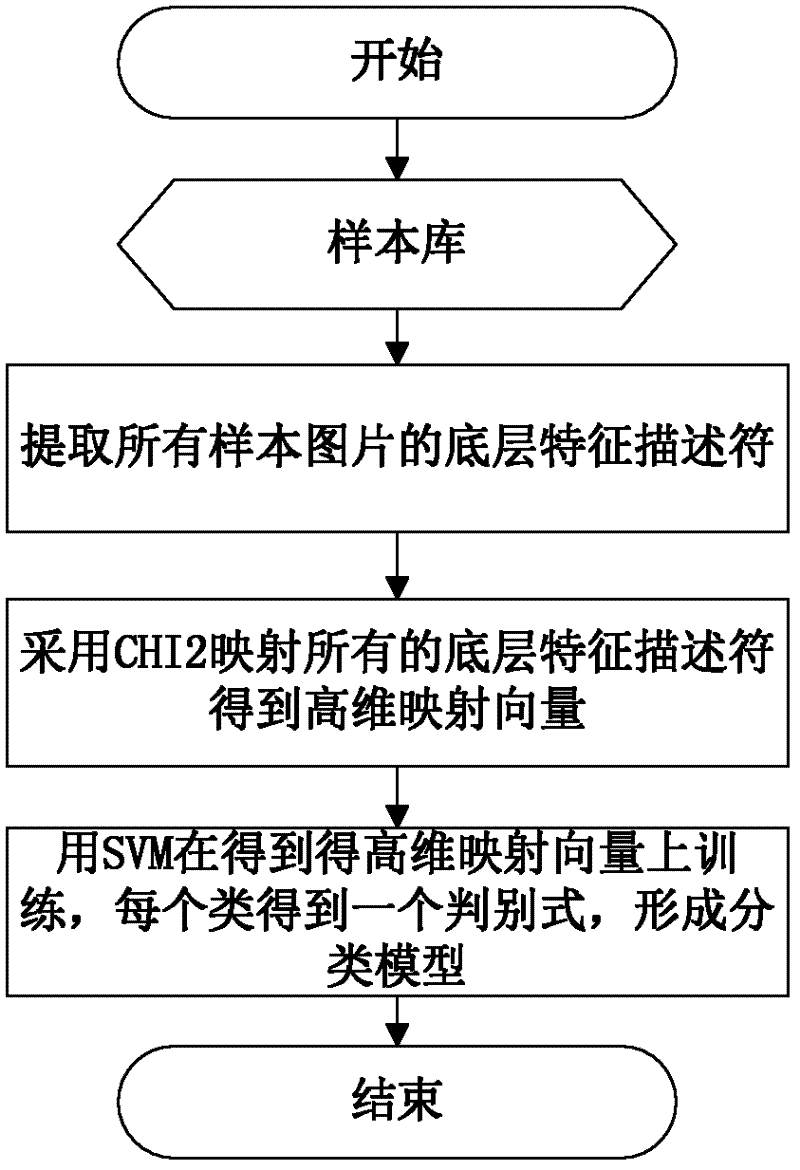
Image retrieval method integrating classification with hash partitioning and image retrieval system utilizing same
InactiveCN102521366AImprove query accuracyQuick responseSpecial data processing applicationsSupport vector machineDiscriminant
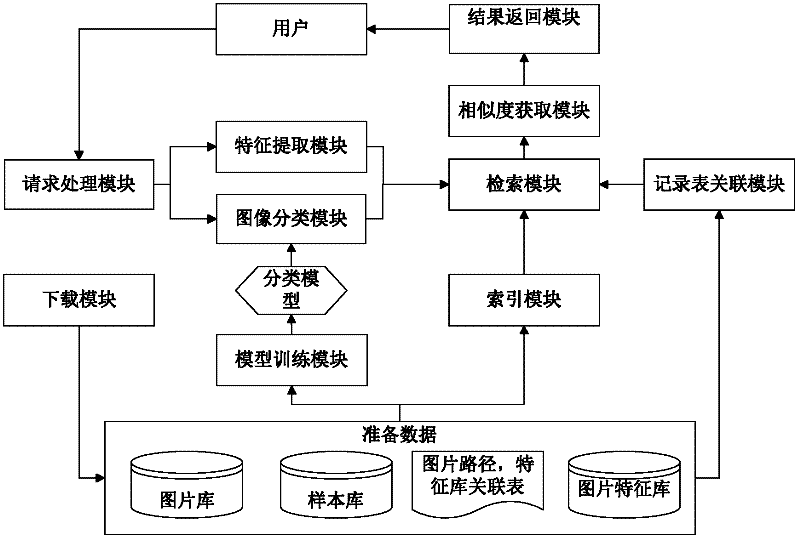
The invention discloses an image retrieval system integrating classification with hash partitioning, which comprises a downloading module, a classification module training module, an image classification module, a characteristic extraction module, a recording table building module, a partitioning module, a request processing module, a retrieval module, a similarity acquiring module and a result returning module. The downloading module is used for downloading images so as to build an image library, the classification model training module classifies the images in the image library according tothe shapes and selects representative sample images from the image library to form a sample library firstly, then extracts characteristic descriptors of the classification bottom layer of all images in the sample library and performs trainings on the characteristic descriptors of the classification bottom layer by a support vector machine so as to obtain discriminant of each classification. Classification models are formed according to the discriminants of all the classifications. Precision ratio of the image retrieval system is increased, the problem of low recall ratio during classificationmistakes is overcome, and the retrieval speed of the image retrieval system is increased integrally.
Owner:HUAZHONG UNIV OF SCI & TECH
Data query method, data query system and computer readable and writable recording medium
InactiveUS20110093486A1Reduce in quantityIncreasing data query rateDigital data information retrievalDigital data processing detailsExtensible markupData query
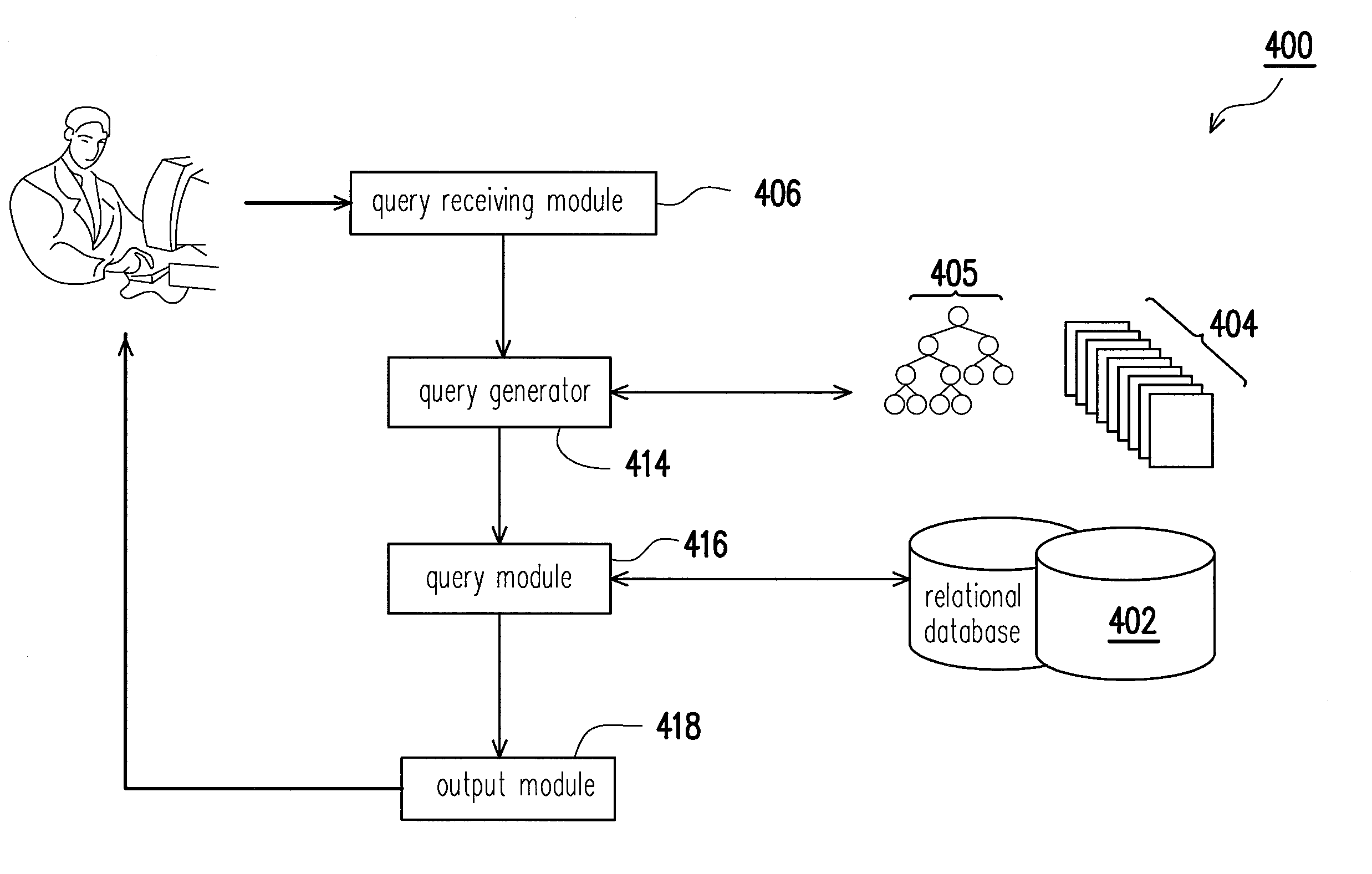
A relational database query system for a relational database is provided, wherein the relational database comprises several relational tables including at least one constant table storing several unique data. The relational database query system comprises a query receiving module for receiving an extensible-markup-language query (XML query); at least a constant mapping tree respectively corresponds to one of the at least constant tables, wherein the at least constant mapping tree comprises several tree nodes respectively with node numbers respectively corresponding to the unique data in the at least constant table; a query generator for converting the XML query to be a structured query language (SQL) query according to the at least constant mapping tree; a query module for querying the relational database with the SQL query.
Owner:INSTITUTE FOR INFORMATION INDUSTRY
Large data inquiring method based on distribution relation-object mapping processing
ActiveCN103678609AGuaranteed Data IntegrityGuaranteed query efficiencyRelational databasesSpecial data processing applicationsData processingData mining
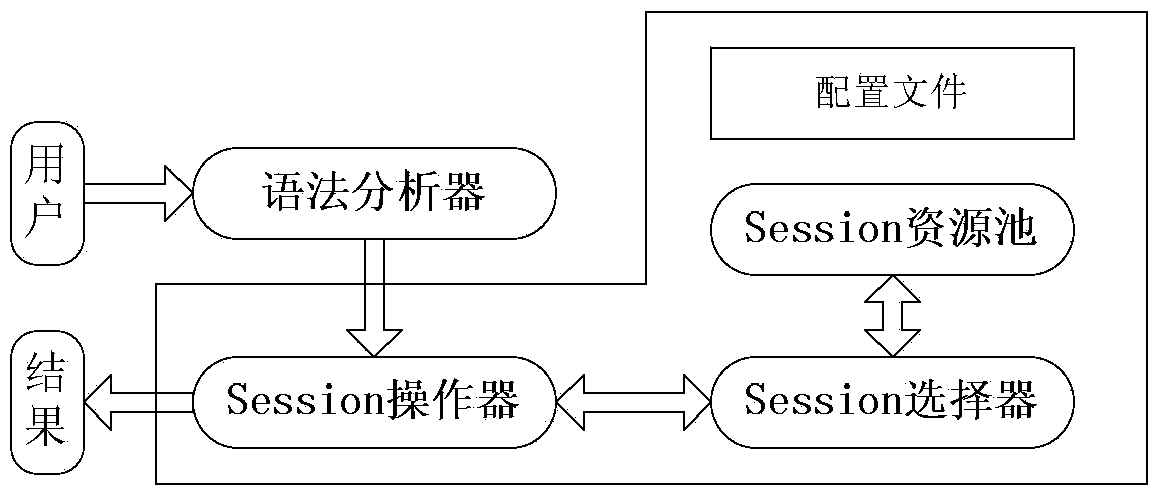
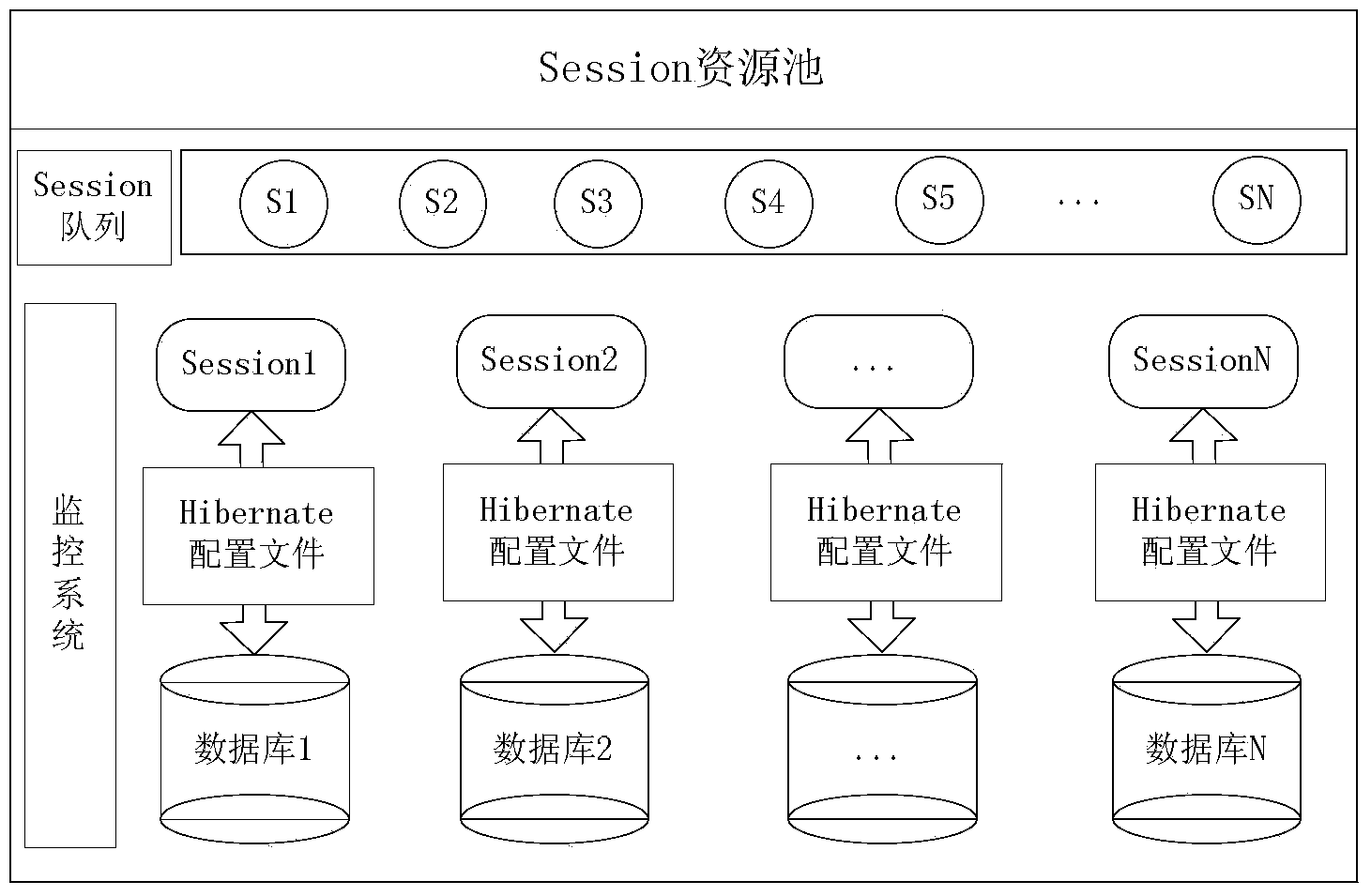
The invention discloses a large data inquiring method based on distribution relation-object mapping processing. The method includes the following steps that firstly, m data processing nodes are selected, a Hibernate Session object is constructed for each data processing node, a distributed Hibernate framework is obtained and a Session resource queue is generated; secondly, a configuration file is set, a storage strategy and a routing strategy corresponding to a list of each type are set, an S list with a data volume is backed up at each data processing node, and an L list with a large data volume is stored to the m data processing nodes in a blocking mode; thirdly, an input inquiring request is analyzed and a corresponding processor is selected according to the type of the inquiring request; fourthly, the selected processor selects the corresponding node from the resource queue to process the inquiring request according to the inquiring request, the corresponding routing strategy, and a processing result is protocoled. The large data inquiring method based on distribution relation-object mapping processing can obviously improve the rate of inquiring large data lists.
Owner:COMP NETWORK INFORMATION CENT CHINESE ACADEMY OF SCI
Large-scale character string high-speed searching method based on TCAM
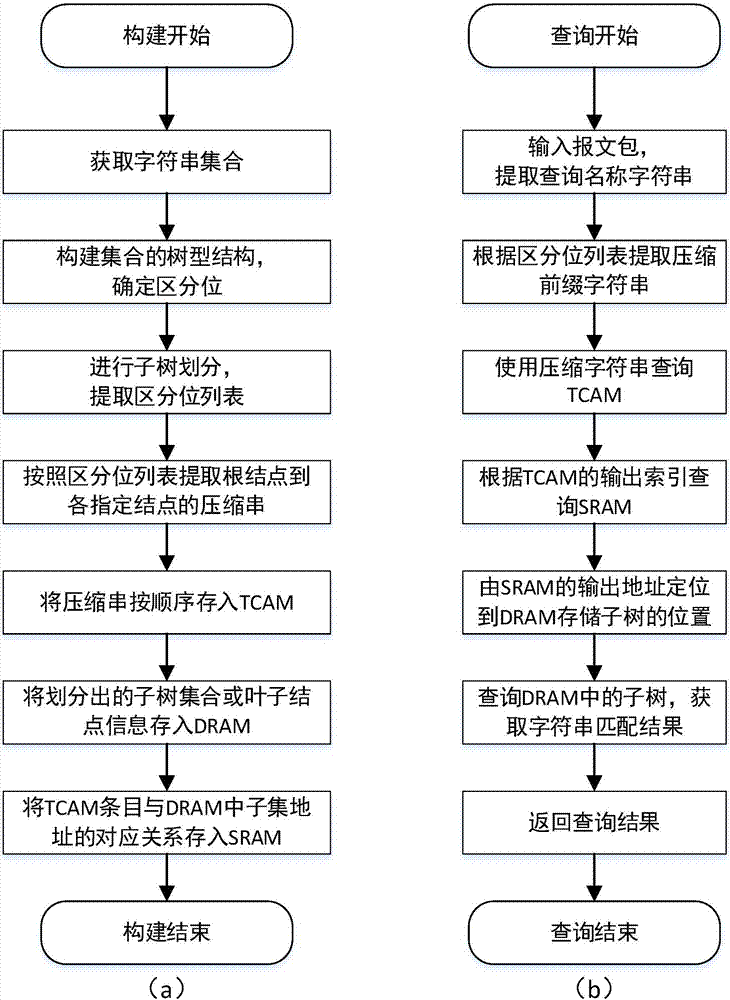
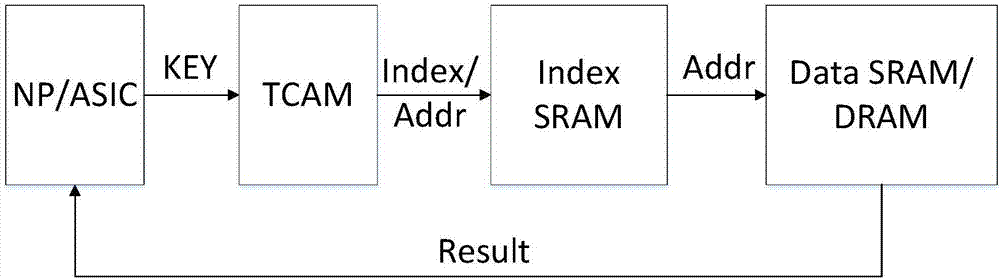
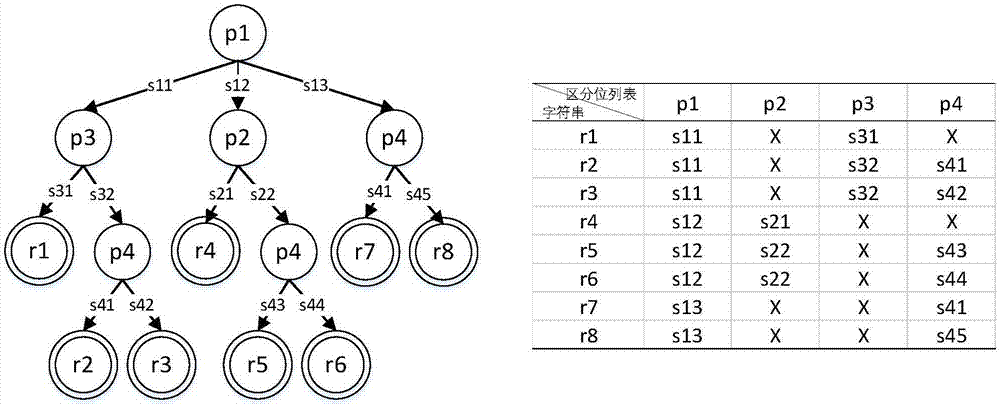
ActiveCN107967219AQuick searchFast query speedMemory adressing/allocation/relocationQuery stringTheoretical computer science
The invention discloses a large-scale character string high-speed searching method based on a TCAM, and belongs to the field of network infrastructures. The method comprises the steps of constructionand query, during construction, a large-scale character string set is utilized to construct a tree structure, then a distinction position of two or multiple character strings is utilized to extract distinction position lists, the values corresponding to distinction positions on all assigned node paths in the tree structure according to the sequence of the distinction position lists, compression stings are constructed to serve as TCAM storage items, the divided subtree or leaf information is stored in a DRAM, and the SRAM is utilized to store the corresponding relation of the TCAM items and a DRAM address; during query, the distinction position lists are utilized to extract query character strings to generate query keywords of the TCAM, high-speed lookup features of the TCAM are utilized tolocate a subset or matching information stored in the DRAM, and high-speed matching of a large scale of character strings is achieved. By means of the large-scale character string high-speed searching method based on the TCAM, the matching speed of name prefixes is increased, and a large scale of varchar can be well disposed.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Information storage and query method based on vertical search engine and device thereof
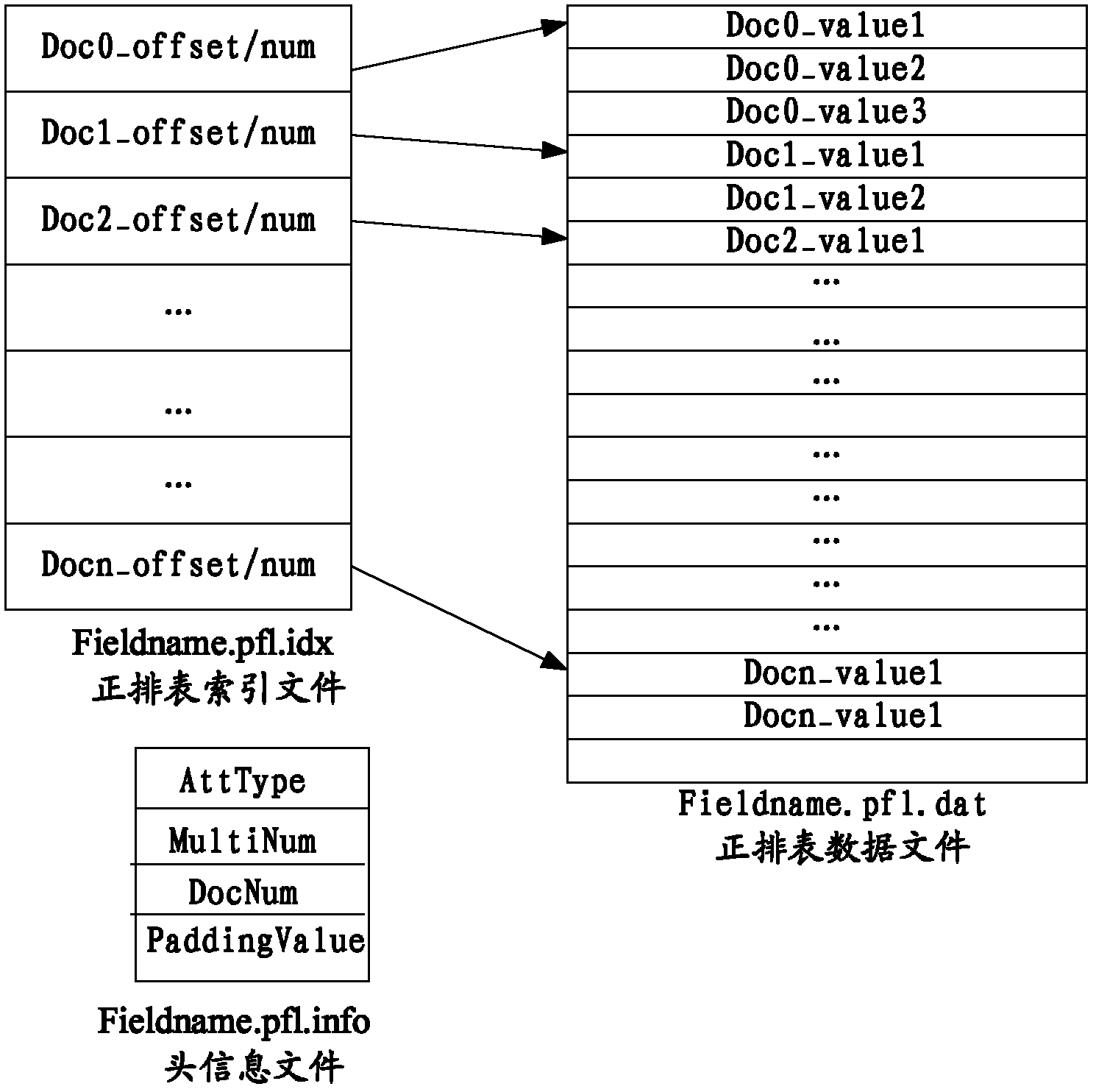
ActiveCN103164408AImprove query rateSpecial data processing applicationsInternal memoryRelevant information
The invention discloses an information storage and query method based on a vertical search engine and a device of the information storage and query method based on the vertical search engine. The method comprises the steps of confirming attribute correlation values of each document to be stored according to attribute values included in a specified attribute field, judging whether numerical values identical with the attribute correlation values are stored in a message dictionary or not, writing offset and the number of the attribute values of an initial position stored in the message dictionary in a positive row table index file if the numerical values identical with the attribute correlation values are stored in the message dictionary, confirming offset and the number of the attribute values of the initial position of the attribute values in the positive row table index file if the numerical values identical with the attribute correlation values are not stored in the message dictionary, storing the confirmed attribute correlation values, the confirmed offset and the confirmed number of the attribute values in the message dictionary, writing the confirmed offset and the confirmed number of the attribute values in the positive row table index file, and starting to write the attribute values included in the specified attribute field of the document to be stored. Therefore, occupation of internal memory resources is reduced, and the rate that a user uses the vertical search engine to inquire relevant information is improved.
Owner:ALIBABA GRP HLDG LTD
Method for optimizing domain name system and optimized domain name system
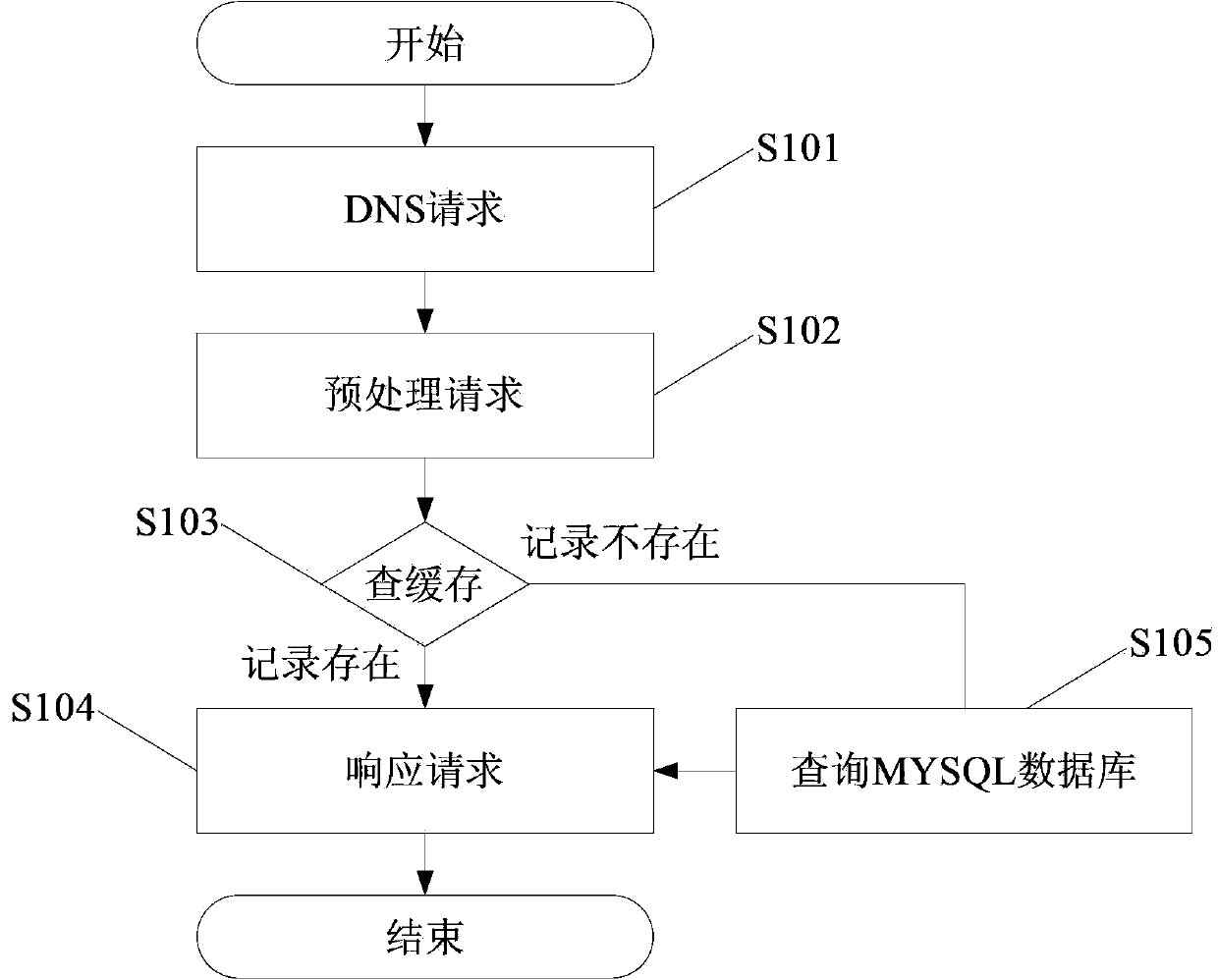
InactiveCN103973820AImprove query efficiencyImprove query rateTransmissionSpecial data processing applicationsDomain nameName server
The invention discloses a method for optimizing a domain name system and the optimized domain name system. The method includes the steps that a domain name server receives a domain name inquiring request of a client terminal; the domain name server carries out finding in a local cache module to respond to the domain name inquiring request, wherein domain name information is cached in the local cache module; the finding result is fed back through the domain name server to the client terminal. The local cache module is additionally arranged in the domain name server, the cache result of a database is cached, when same inquiring is carried out next time, locally-cached data can be directly returned without database inquiring, and therefore the inquiring efficiency can be greatly improved.
Owner:SHENZHEN QVOD TECH
Digital antifalse method, and l antifalse marker
InactiveCN1959733AHigh technical difficultyIncrease the cost of counterfeitingStampsCommerceInternet networkWorld Wide Web
A digital false -proofing method includes coding false-proof object, printing exclusive one or multiple coding on each object and generating a set of character information corresponding to printed coding, storing said coding and said character information together into databank of computer identification system connected to Internet network for enabling consumer to call said coding and its correlated character information to verify true or false of product.
Owner:俞熹
Anti-counterfeit method based on two-dimensional code
InactiveCN105117918AAvoid the problem of brute force method crackingIncrease the cost of counterfeitingUser identity/authority verificationDigital data protectionGraphicsComputer science
Owner:李华容
Method and tag based on two-dimension code anti-counterfeiting and tag manufacturing method
ActiveCN103093355AAvoid the problem of brute force method crackingIncrease the cost of counterfeitingUser identity/authority verificationDigital data protectionComputer scienceData library
Owner:李华容
Texture anti-counterfeit structure combining barcode inquiry with short message inquiry, texture anti-counterfeit logistics system, and texture anti-counterfeit logistics method
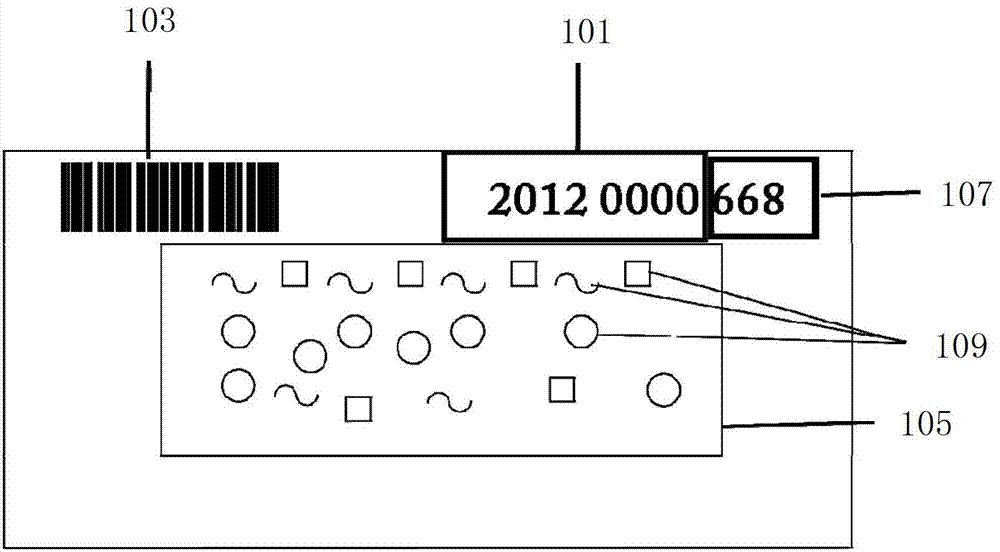
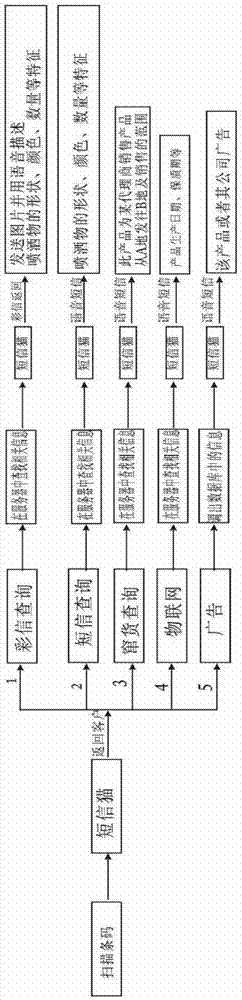
InactiveCN102880902ASimple queryImprove query rateMessaging/mailboxes/announcementsCommerceGraphicsBarcode
The invention discloses a texture anti-counterfeit structure combining barcode inquiry with short message inquiry, a texture anti-counterfeit logistics system and a texture anti-counterfeit logistics method. The texture anti-counterfeit structure comprises a texture anti-counterfeit characteristic area and a barcode, wherein the texture anti-counterfeit characteristic area comprises more than two kinds of markers; the barcode comprises a sequential number and characteristic code information of the anti-counterfeit structure; and the characteristic code corresponds to the structural characteristic of each kind of marker. The texture anti-counterfeit logistics system comprises the texture anti-counterfeit structures, a short message modem, and a server in which texture anti-counterfeit characteristic information of each of the texture anti-counterfeit structures is memorized, wherein the sequential number of the texture anti-counterfeit structure or sequential number information obtained by scanning the barcode is sent to the short message modem by a customer by means of a short message; the short message modem inquires on the server, and then feeds an inquiry result in need back to the customer. According to the texture anti-counterfeit structure combining barcode inquiry with short message inquiry, the texture anti-counterfeit logistics system and the texture anti-counterfeit logistics method disclosed by the invention, texture anti-counterfeit and barcode inquiry are combined, texture anti-counterfeiting is implemented by the barcode inquiry and the short message inquiry; as a result, not only is the advantage that picture anti-counterfeiting is random and is hard to be counterfeited kept, but also the advantage of quick barcode inquiry is achieved.
Owner:李峰
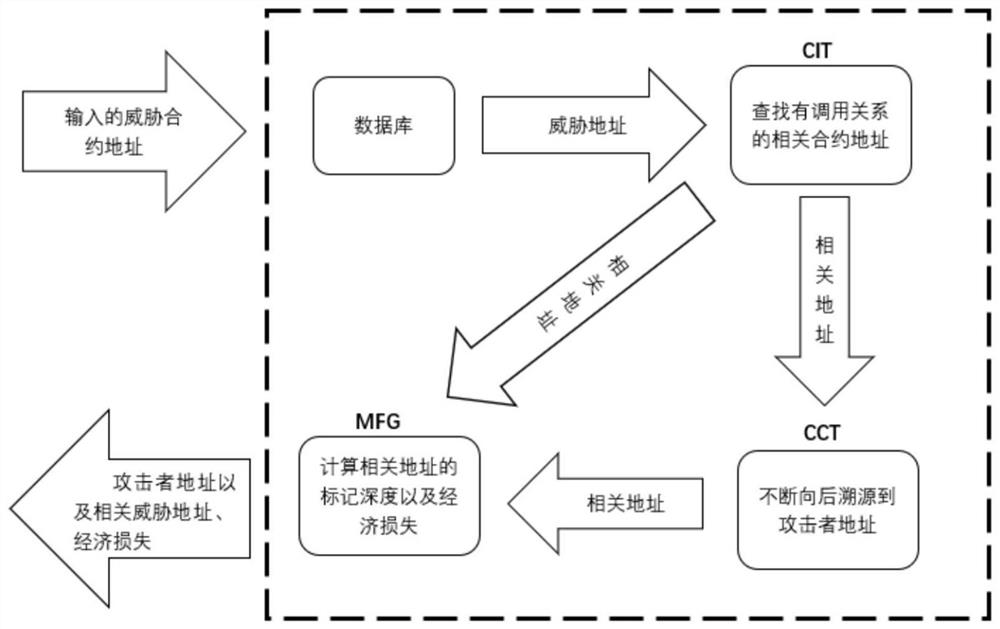
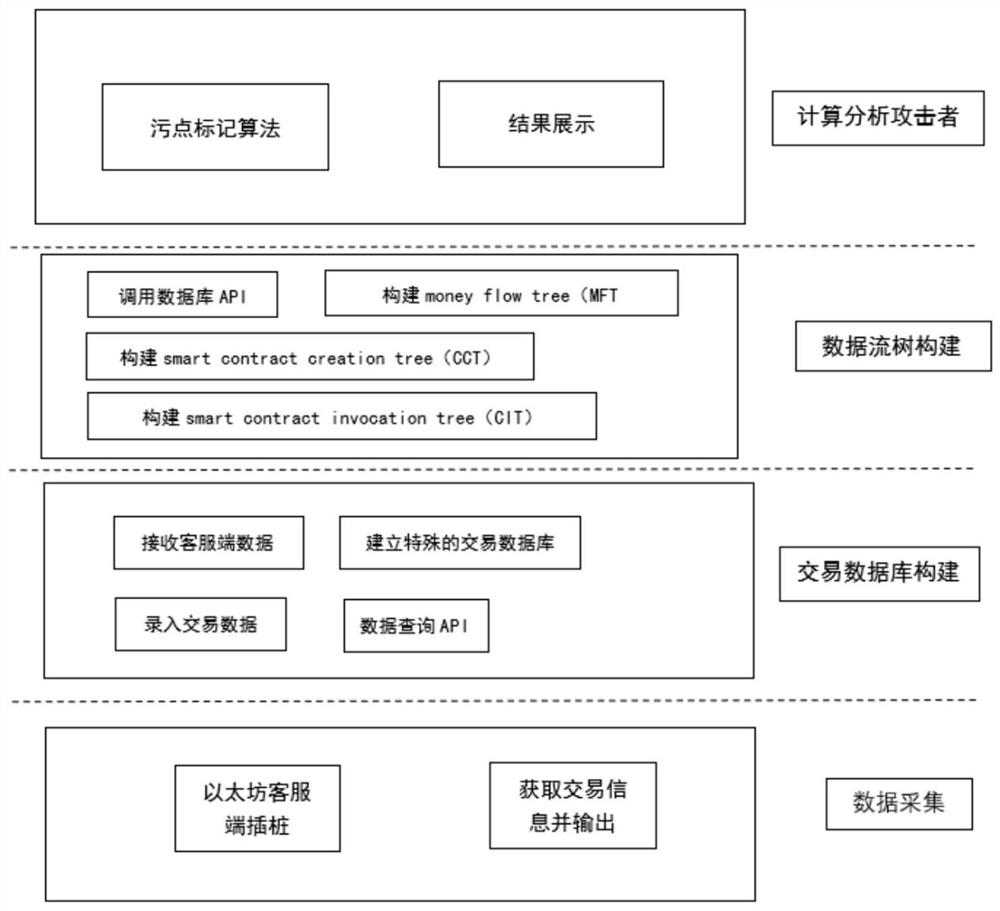
Blockchain attack tracing system and method
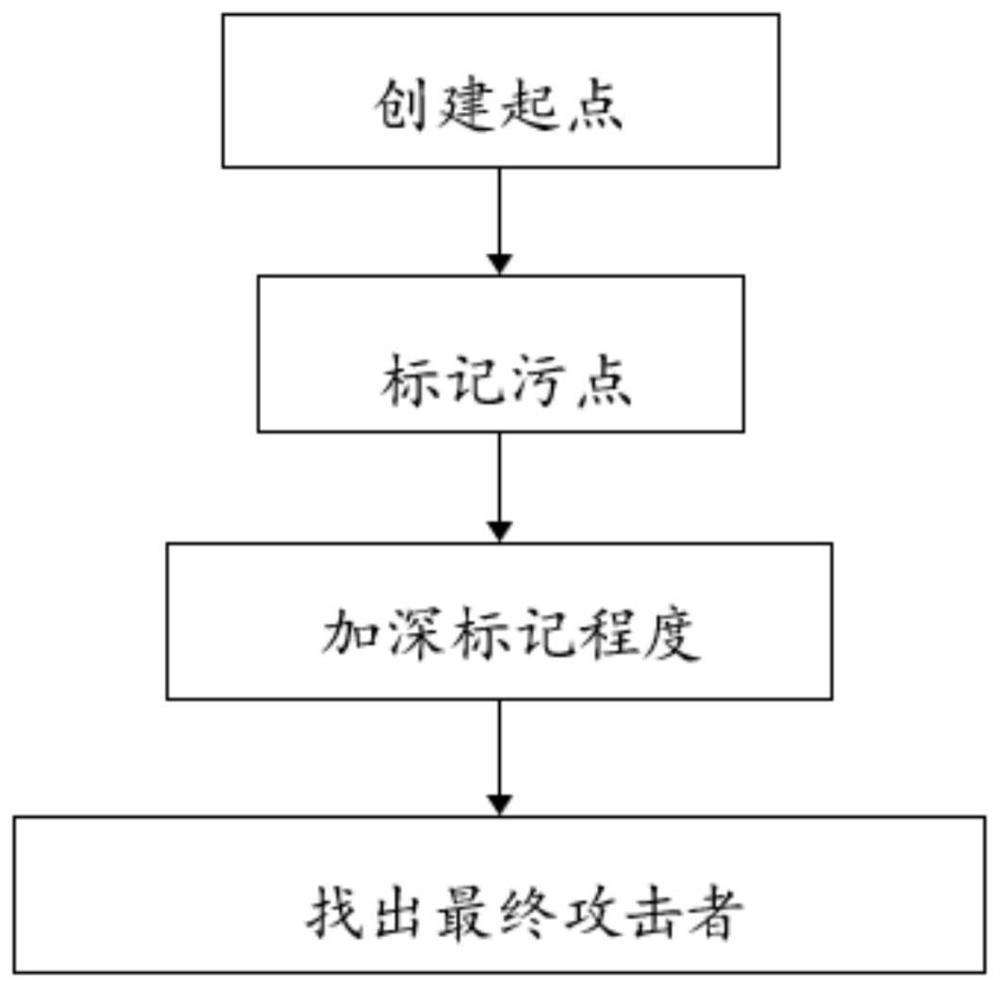
ActiveCN111787017AIncrease credibilityImprove operational efficiencySecuring communicationData streamAttack
The invention relates to the technical field of information security, provides a blockchain attack tracing system and method, and aims to solve the technical problem that an attacker cannot be tracedback when an attack threat is detected in a blockchain. According to the main scheme, the system comprises: a data acquisition module for capturing corresponding data in a full synchronization processto obtain transactions and transaction information thereof; a transaction database construction module which is used for establishing an external transaction information table, an internal transaction information table and a contract creation information table according to the obtained transaction and transaction information thereof and providing an API for data query, wherein the data mainly comprises two transaction parties, a transaction block height, a transaction amount and consumed gas; a data flow tree construction module which is used for acquiring transaction data through the API ofthe database to construct a data relationship tree; and an attacker tracing module which is used for carrying out stain marking on the basis of the established data flow tree and finally positioning an attacker according to the depth of stain marking.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
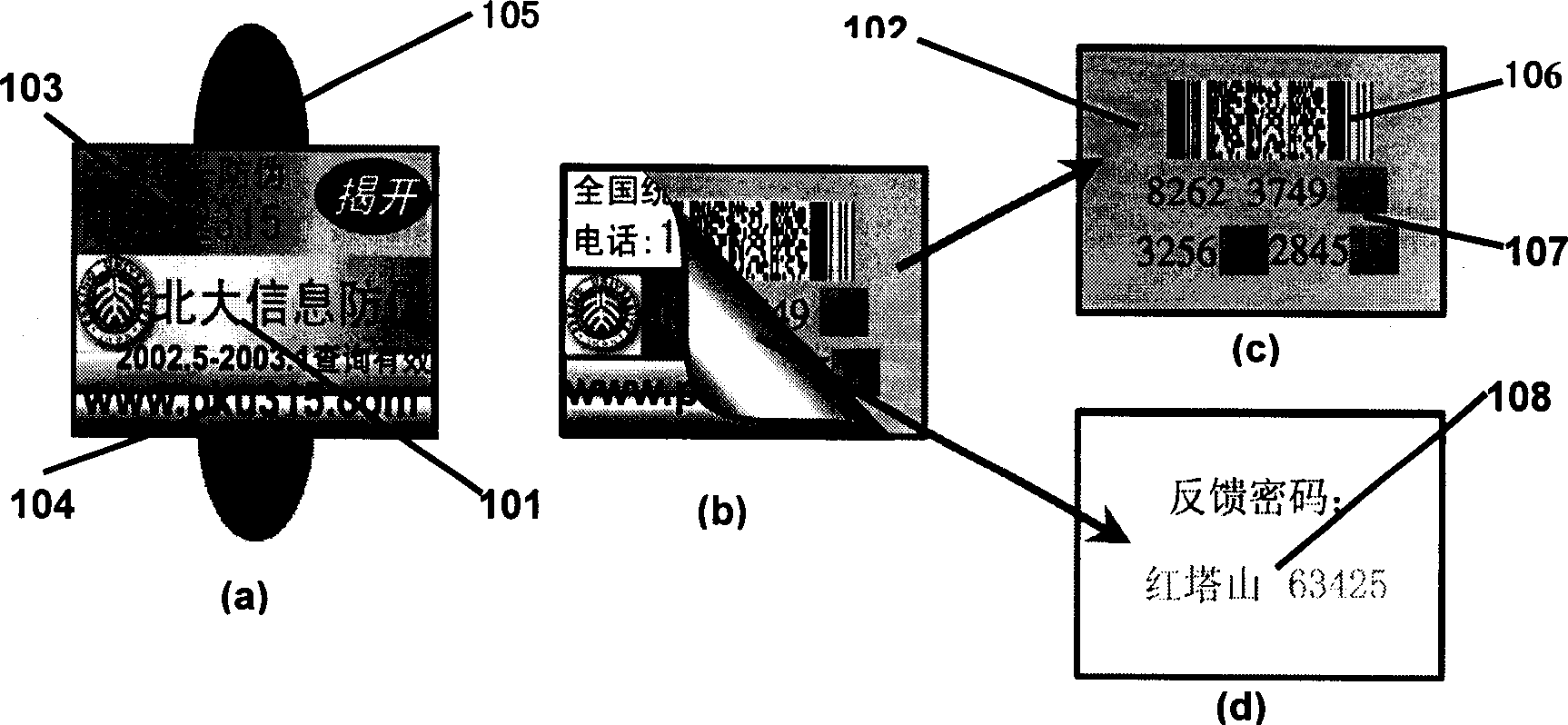
Information anti-fake label and corresponding intelligent information anti-fake service system
InactiveCN1388702AAchieve separationSolve the fatal loophole of counterfeitingStampsTelephonic communicationDatabase serverComputer terminal
The present invention is multiple-feedback information anti-fake label and corresponding intelligent informatino anti-fake service system. The information anti-fake label consists of observed label with double feedback cipher and information checking label comprising bar code and sectional feedback code. The intelligent information anti-fake service system consists of information anti-fake platform and connected checking terminal, the information anti-fake platform includes FSK access server, AAA server, information anti-fake central processing machine and data base server; and the private intelligent checking terminal includes PSTN, scanning input and FSK code information. The present invention has very high commodity anti-fake checking rate.
Owner:谷安佳 +3
HDFS distributed file sharing method based on local area network
ActiveCN106254466AEnsure safetyAchieve horizontal expansionTransmissionSpecial data processing applicationsTraffic capacityFile area network
The invention discloses an HDFS distributed file sharing method based on a local area network. The method comprises the following steps that 1) an HDFS is deployed on the local area network, and one server is used as a host node, which is an applied monitoring server; other N servers are used as slave nodes, which are applied storage servers; and 2) on a server terminal, the host node divides a file into a plurality of blocks with a fixed size and the blocks are stored in different slave node storage servers, and each data block has 2-3 backups. In the invention, a community file sharing function of the HDFS in the local area network can be realized, a file uploading rate can be greatly increased and a flow rate is reduced.
Owner:HOHAI UNIV CHANGZHOU
Untransferable and unrescind commodity bonus card and method thereof
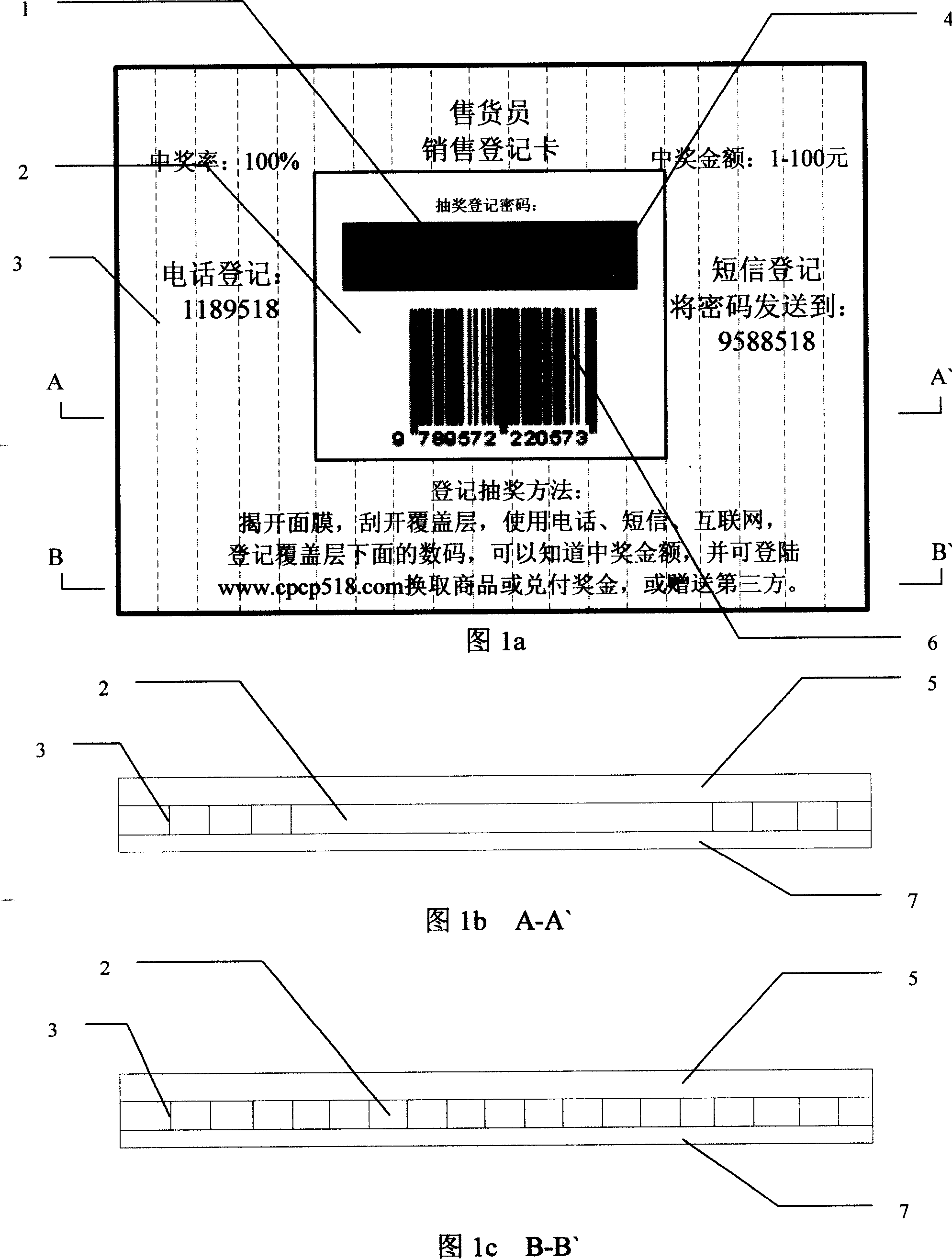
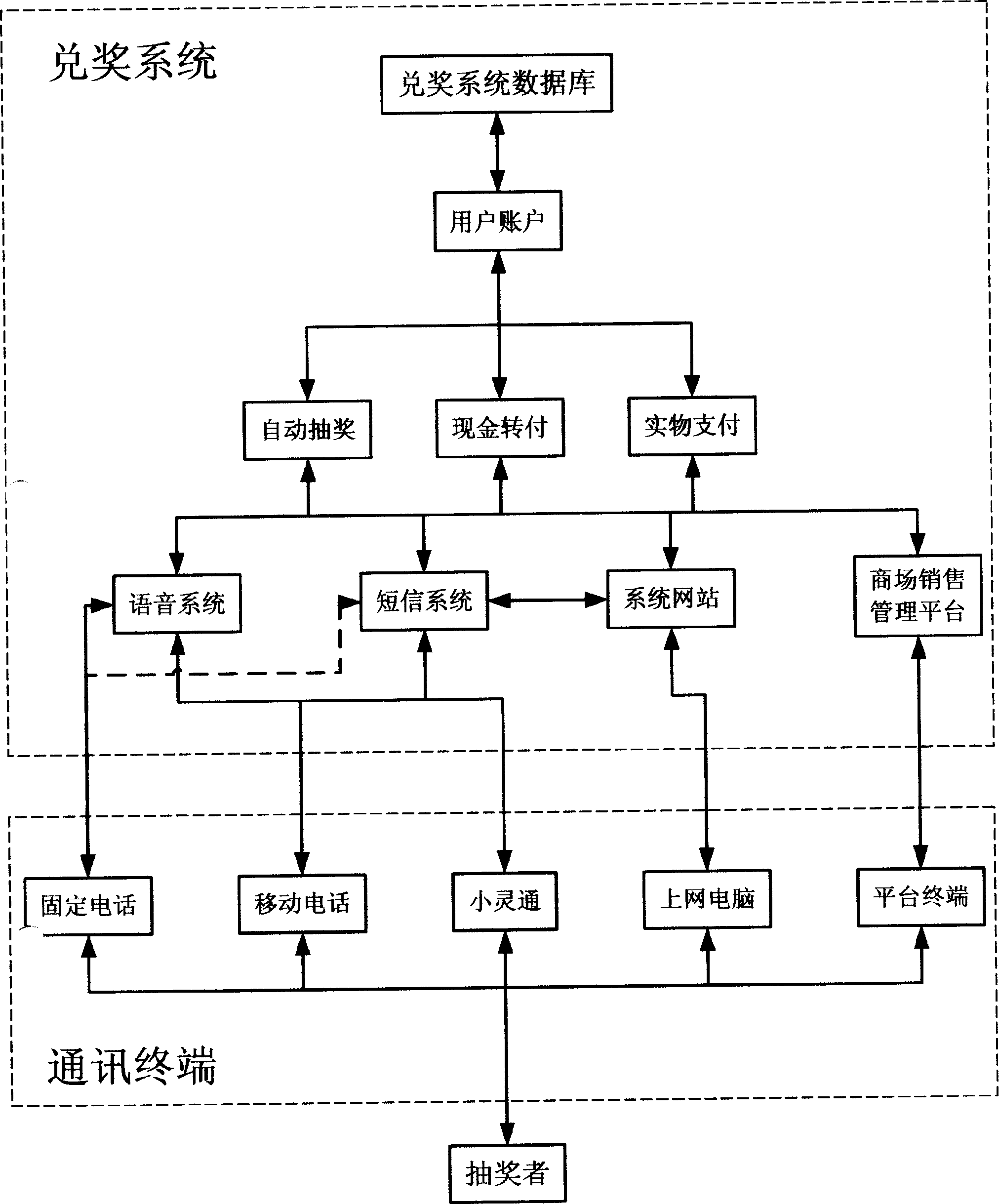
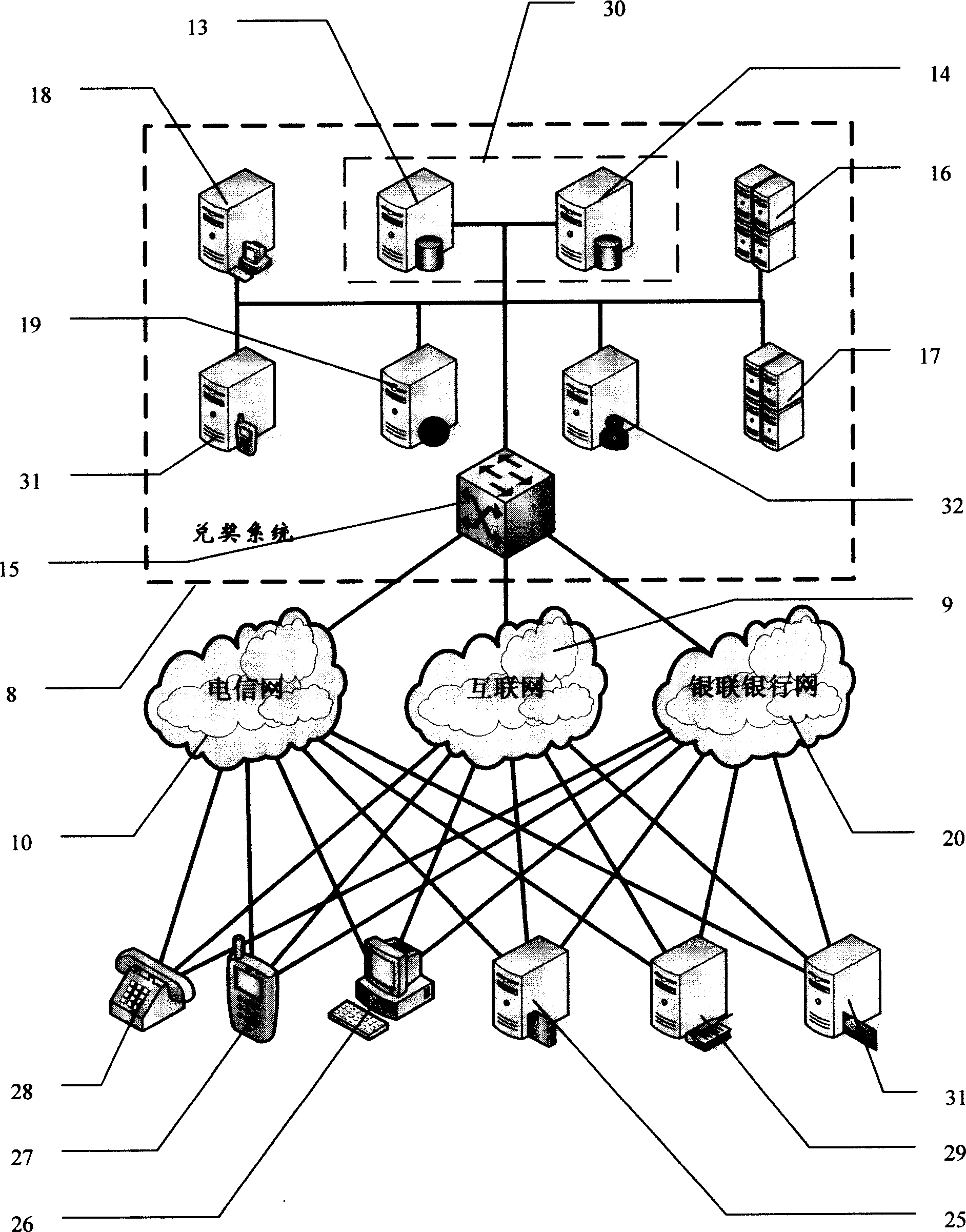
A method includes attaching an award draw card on commodity as a present, obtaining award draw number on the card by the buyer, obtaining money award immediately by inputting award draw number through dialing to award draw phone or sensing short message or logging in network, transferring money award to phone account or credit card account of his own or the third party, or logging on cash network to exchange commodity you want for yourself or for sending it to the third party as gift.
Owner:许康康 +1
On-line monitoring outdoor acquisition device for relay protection of power system
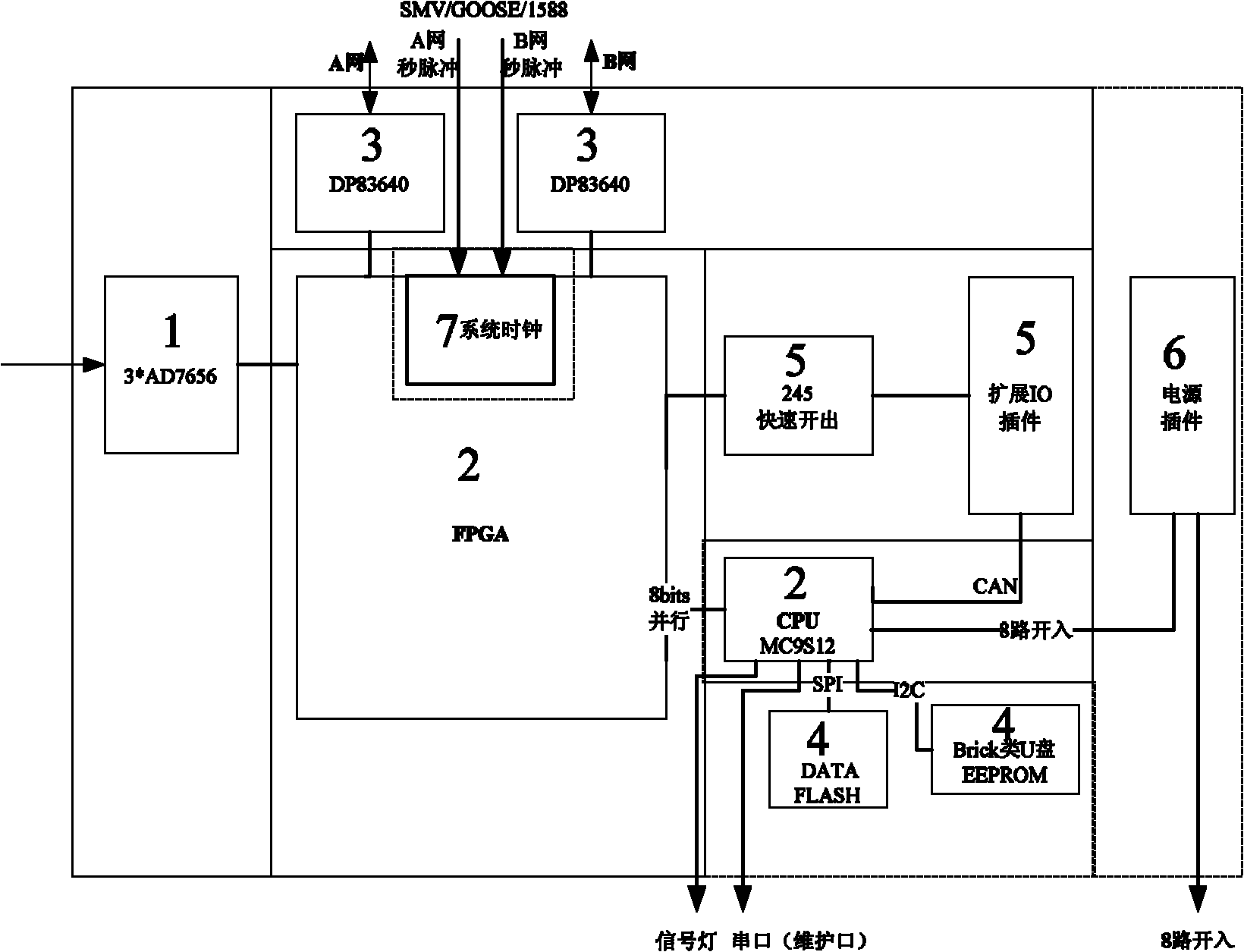
ActiveCN101917066ARealize localized collectionGuaranteed collectionCircuit arrangementsSynchronisation signal speed/phase controlInformation processingFiber
The invention discloses an on-line monitoring outdoor acquisition device for relay protection of a power system in the technical field of power systems. The acquisition device comprises an acquisition conversion module, an information processing module, a communication module, a storage module, a quick interface module, a power supply module and a system clock. The acquisition device realizes local acquisition of information, and provides judgment basis for protective acquisition loop monitoring by modeling according to IEC61850, converting the information into digital signals, transmitting the digital signals through fibers and forming a closed loop circuit between the acquisition device and the primary protective acquisition device.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER +2
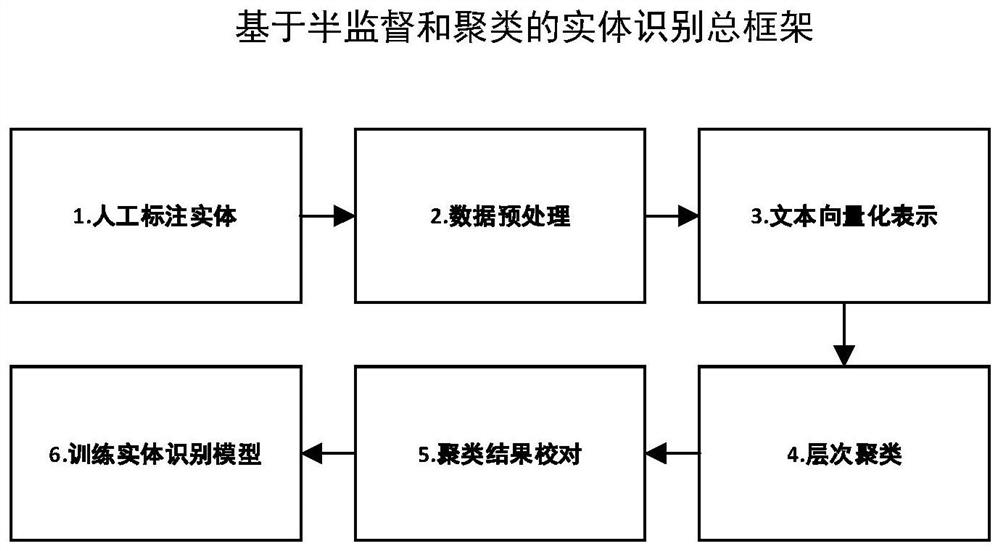
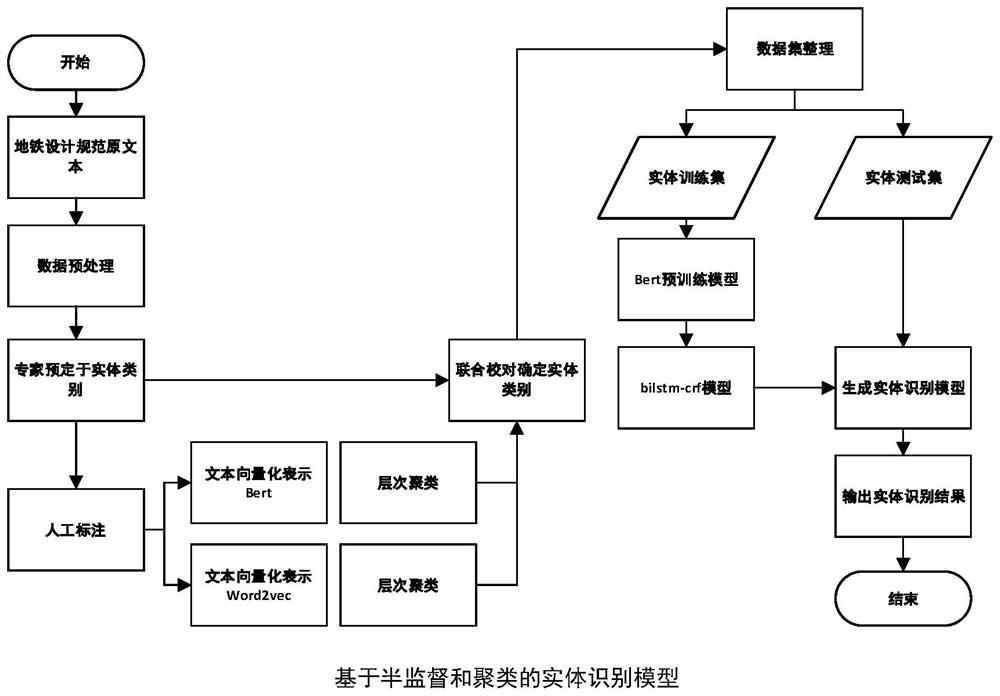
Entity recognition method based on semi-supervised learning and clustering
PendingCN113191148AReduce processing timeImprove query rateNatural language data processingNeural architecturesEntity typeData set
The invention relates to an entity recognition method based on semi-supervised learning and clustering. The method comprises the steps of: pre-defining entity categories through the ontology library to label the rail transit standard unstructured data; performing vectorization representation on label data by using word2vec, and then performing a hierarchical clustering algorithm on entity word vectors with labels; performing conjoint analysis on entity categories and clustering results, proofreading entity category definitions, and finally determining the entity types of the ontology library in the field of rail transit; and finally, rearranging a data set, and inputting generated word vectors into a BiLSTM-CRF deep learning model to train a named entity recognition model, wherein a Softmax function is used to carry out tag classification on recognized entity features, and an entity tag classification result is evaluated. According to the method, the entity extraction speed and accuracy in the rail transit specifications can be improved, so that the time for processing the rail transit specifications by automatic question and answer system and semantic network labeling is shortened, the query rate of employees in the building field on the rail transit specifications is improved, and the user experience degree is improved.
Owner:XIAN UNIV OF TECH
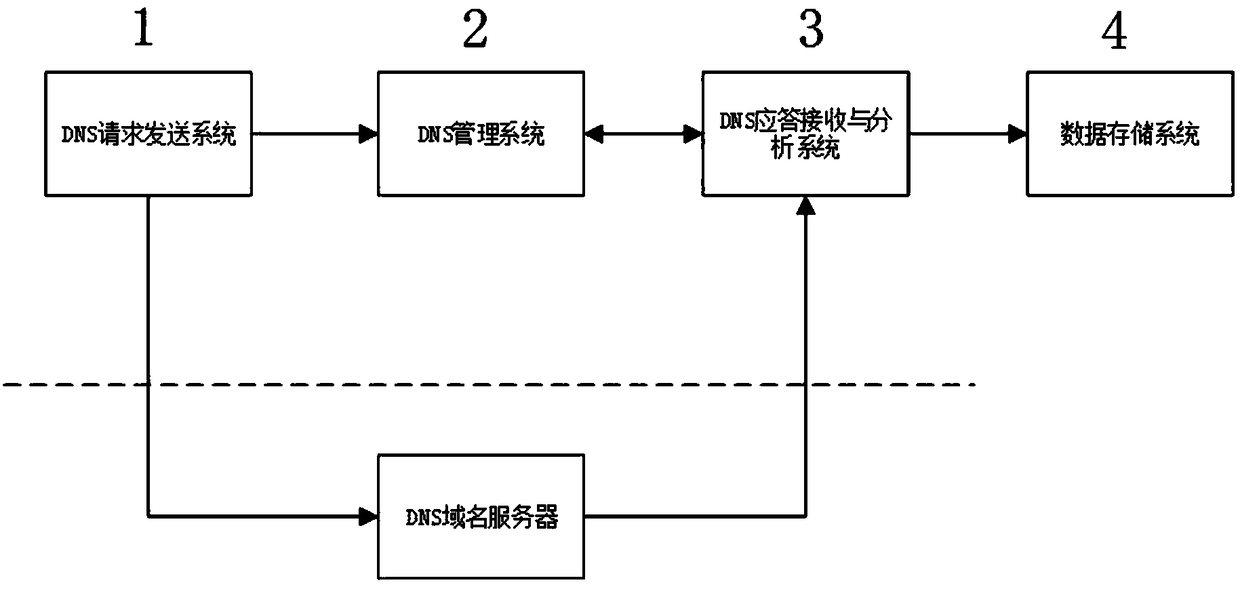
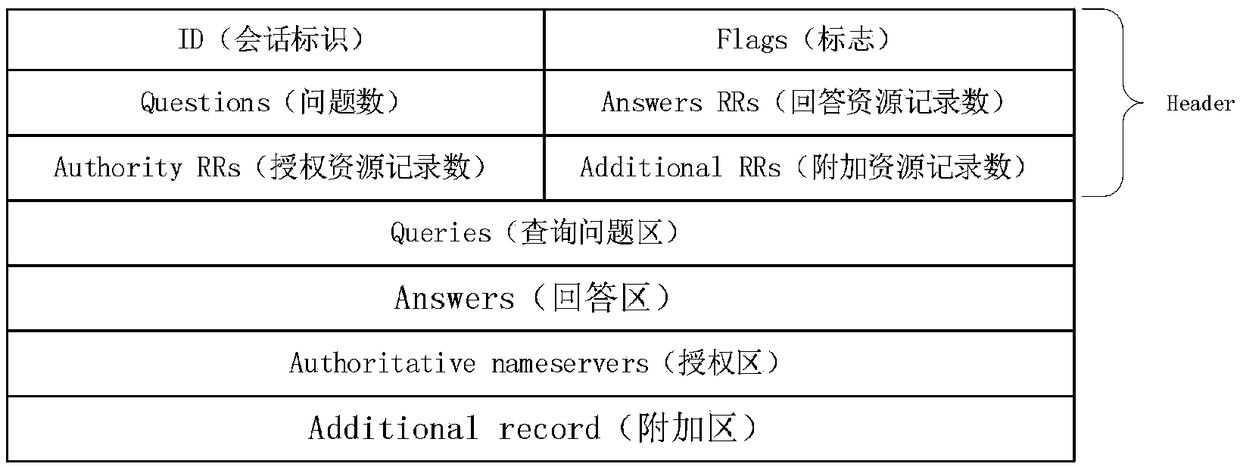
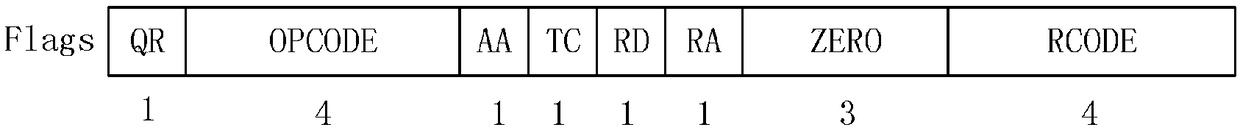
DNS domain name obtaining system and method
InactiveCN109347996AGet high speed and efficientEffective judgmentTransmissionDomain nameNetwork packet
The invention discloses a DNS domain name obtaining system and method. The system comprises a DNS request packet sending subsystem, a DNS management subsystem and a DNS response packet receiving and analysis subsystem. The DNS request packet sending subsystem, the DNS management subsystem and the DNS response packet receiving and analysis subsystem carry out multithread parallel working. The DNS request packet sending subsystem is used for sending and resending DNS request data packets. The DNS response packet receiving and analysis subsystem is used for receiving DNS response packets and judging whether the DNS response packets are the response packets corresponding to the DNS request packets or not. The DNS management subsystem is used for managing a state value of domain name resolutionservice, carrying out timing after the DNS request data packets are sent, determining the DNS request data packets needing to be resent according to the DNS response packets received by the DNS response packet receiving and analysis subsystem, and triggering the DNS request packet sending subsystem to resend the DNS request data packets needing to be resent, when the timing is carried out to settime. The DNS domain name obtaining system and method provided by the invention are characterized by efficiency and accuracy.
Owner:中共中央办公厅电子科技学院
Anti-counterfeiting method for establishing network database platform
InactiveCN101882151AIncrease awarenessReduced awarenessCommerceSpecial data processing applicationsThird partyCognition
The invention discloses an anti-counterfeiting method for establishing a network database platform, which comprises the following steps: a. randomly generating a unique identification digital code for each commodity, and making a digital code anti-counterfeiting label to be labeled on the commodity; b. establishing the network database platform for customers to inquire the identification digital code of the commodity; and c. visiting the network database platform through an inquiry terminal and obtaining inquiry results by customers. The invention is characterized in that the network database platform established in the second step is the unique public network database platform in China, each enterprise can joint in the platform after passing the application certification, and digital code anti-counterfeiting labels of commodities of enterprises in the platform are in unified management by the platform. Compared with the prior art, the invention has the advantages that 1. a third party of the network platform is added between enterprises and customers, so the anti-counterfeiting network platform with the strongest influence force and the strongest authority can be formed in the nation-wide range under the operation of operators of the network platform, and the approval of the enterprises and the customers can be obtained, so folk professional anti-counterfeiting organizations with the industrial professional property can appear to remove difficulties and alleviate sufferings for the enterprises and the customers, and the counterfeiting and the adulterated goods can gradually disappear; 2. after the standardized management of the digital code anti-counterfeiting labels of commodities, on one hand, the creditworthiness of the commodity of the enterprises can be improved, and the cognition degree of the customers can be enhanced; on the other hand, the anti-counterfeiting operation cost of the enterprises can be reduced.
Owner:阳仁华
Novel on-chain data high-speed retrieval model
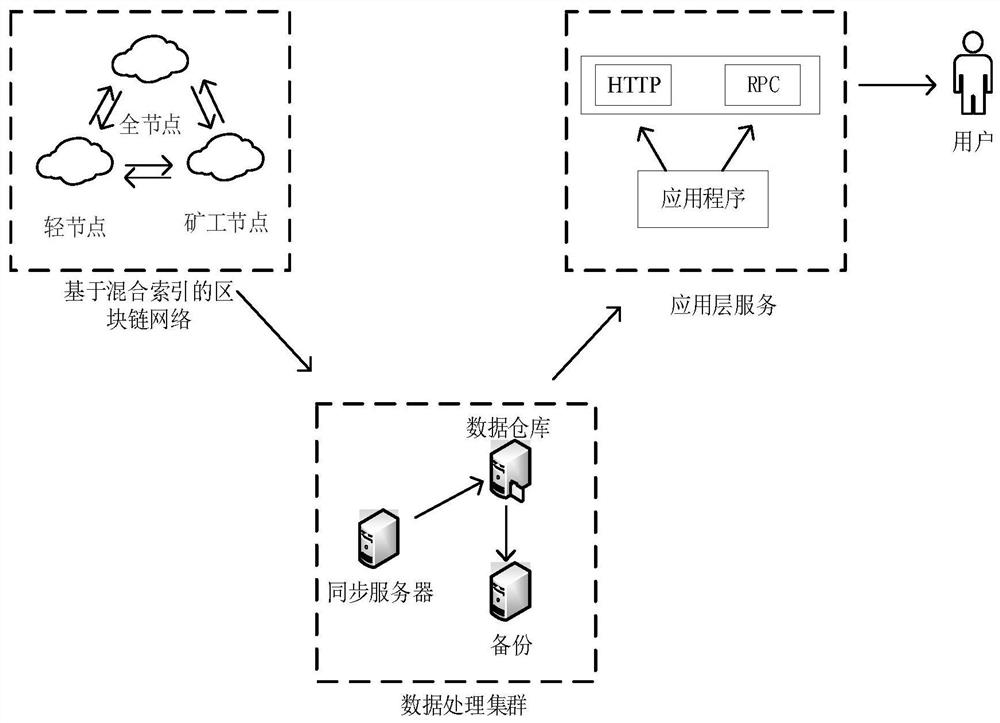
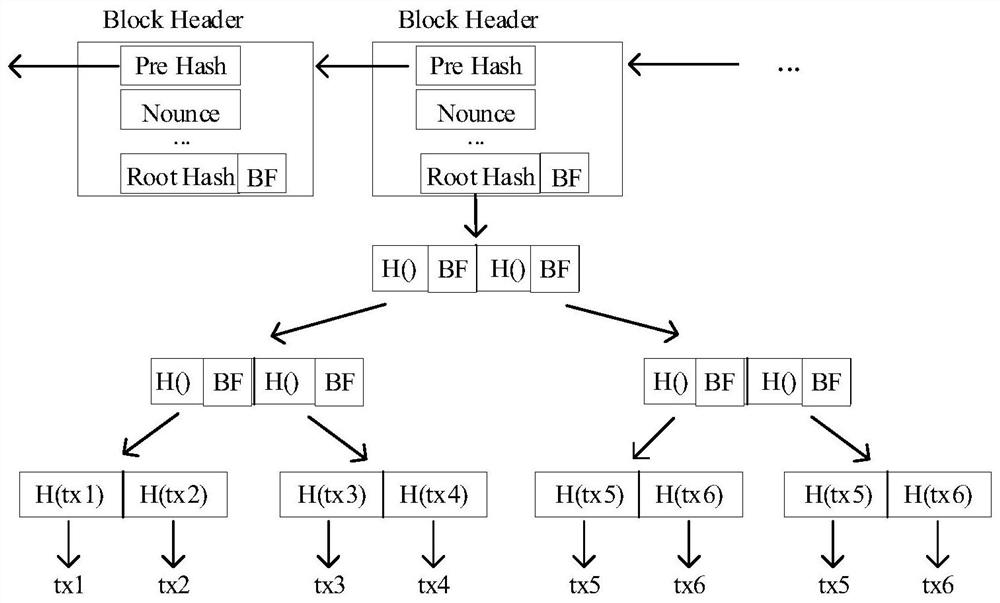
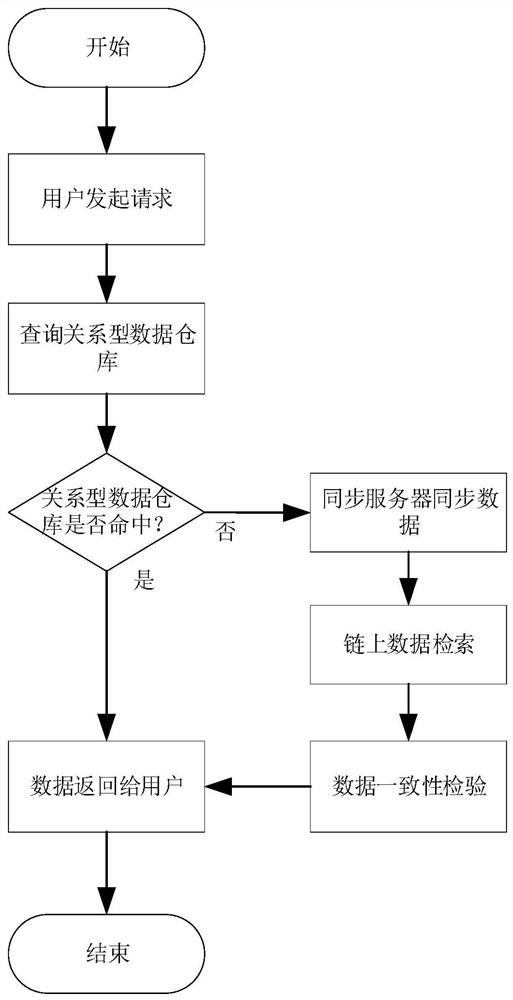
PendingCN113961598AImprove retrieval rateVersatileDatabase updatingDatabase distribution/replicationChain networkData processing
The invention provides a novel on-chain data high-speed retrieval model based on a built-in index and external connection data warehouse method. The model is composed of a block chain network in an improved index storage form, a data processing cluster and an application layer service. According to the novel block chain network, the organization form of transaction data of a traditional block chain system is improved, and a data structure suitable for high-speed retrieval is designed to organize the transaction data; the data processing cluster is responsible for synchronizing on-chain data to the under-chain relational data warehouse according to an efficient synchronization strategy under the condition of ensuring data consistency; and the application layer service encapsulates rich query functions supported by the relational database, and finally provides services to the outside in forms of HTTP, RPC and the like. By means of the model, the block chain system can be effectively expanded in the aspects of query efficiency, query functions and the like, and the query rate of data on the block chain is increased.
Owner:SHENYANG CALCULATION TECH INST CHINESE ACAD OF SCI
Two-dimensional code verification method for food safety
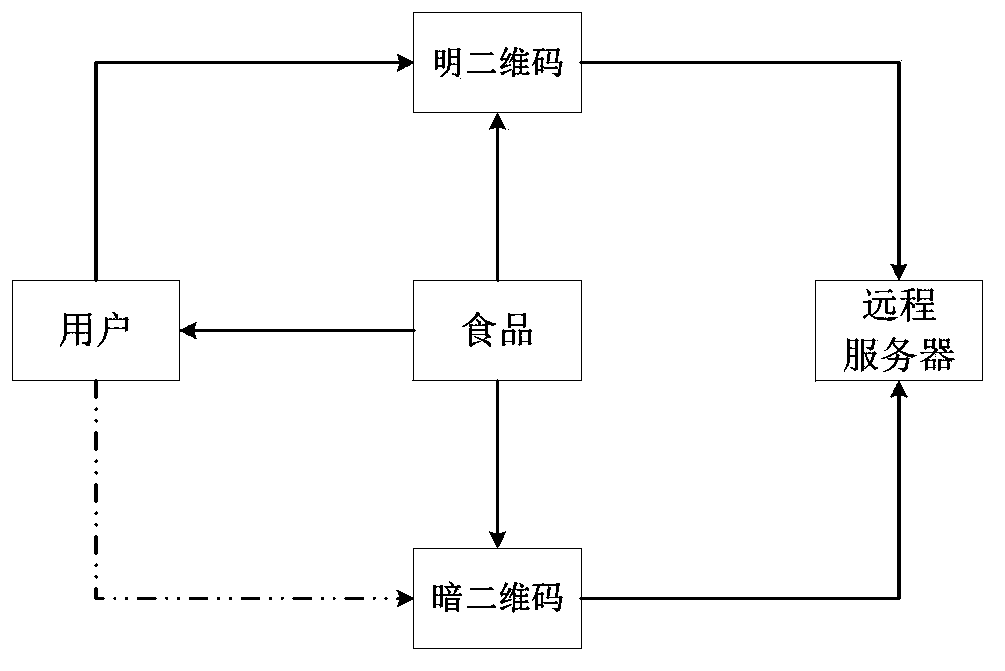
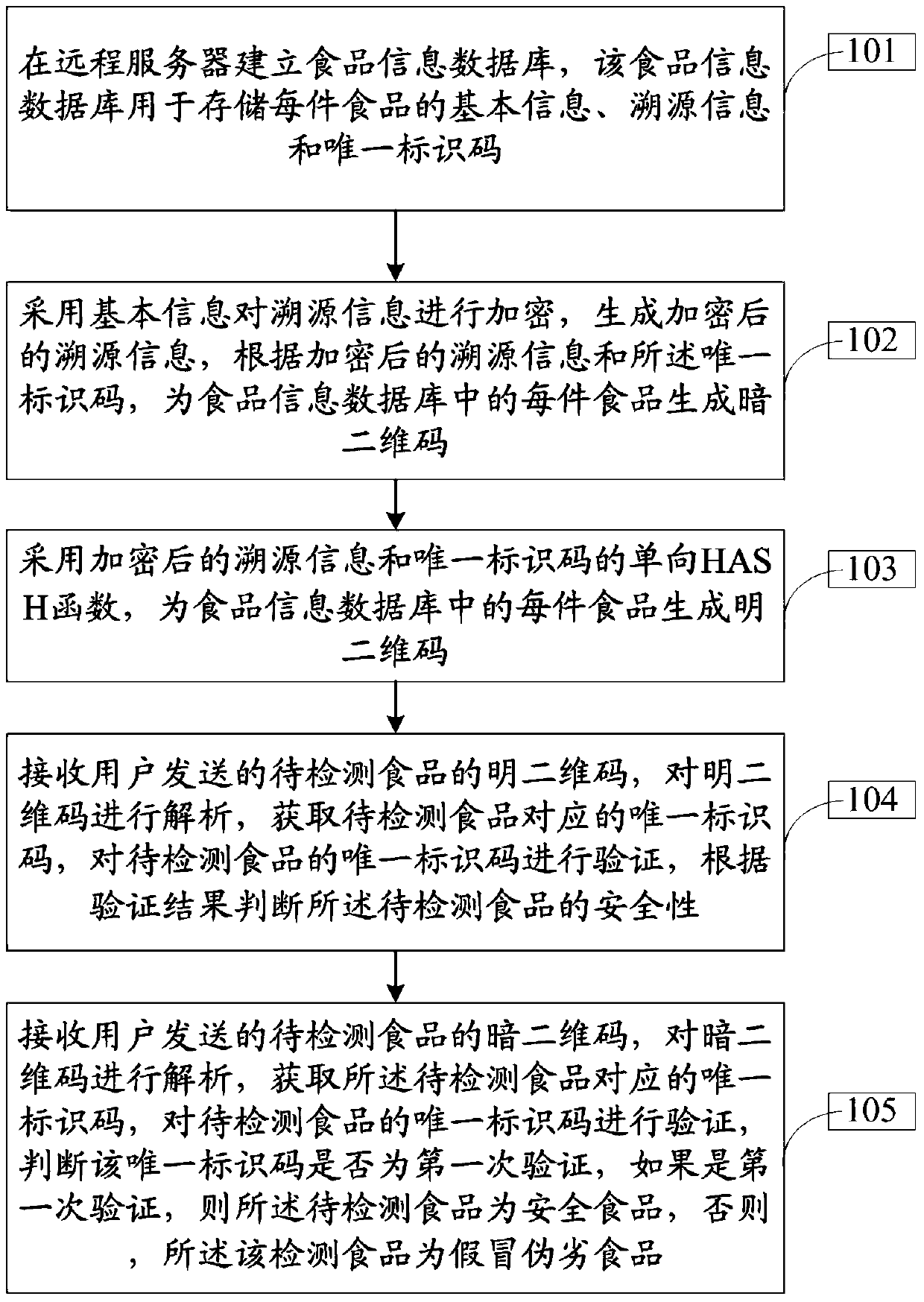
InactiveCN103426092ASolve the disadvantages of easy duplicationOvercome the disadvantage of easy duplicationCommerceState of artHash function
The invention discloses a two-dimensional code verification method for food safety and solves the problem of complex security verification operations through telephones or short messages in the prior art. According to the technical scheme, the two-dimensional code verification method comprises the steps of establishing a food information database in a remote server, wherein the food information database is used for storing basic information, tracing information and a unique identifier of each piece of food; encrypting the tracing information by the basic information to generate encrypted tracing information, and generating a dark two-dimensional code for each piece of food in the food information database according to the encrypted tracing information and each unique identifier; generating a bright two-dimensional code for each piece of food in the food information database by the encrypted tracing information and a one-way HASH function of each unique identifier; receiving the bright two-dimensional codes of to-be-detected food sent by users, analyzing the bright two-dimensional codes to obtain the unique identifiers, verifying the unique identifiers, and judging the safety of the to-be-detected food according to verification results. The two-dimensional code verification method is applicable to the security verification field.
Owner:UNIV OF SCI & TECH BEIJING
A novel counterfeit-prevention method
InactiveCN101009738AHigh degree of credibilityEliminate anti-counterfeiting loopholesAutomatic exchangesPrepayment telephone systemsUser inputDatabase
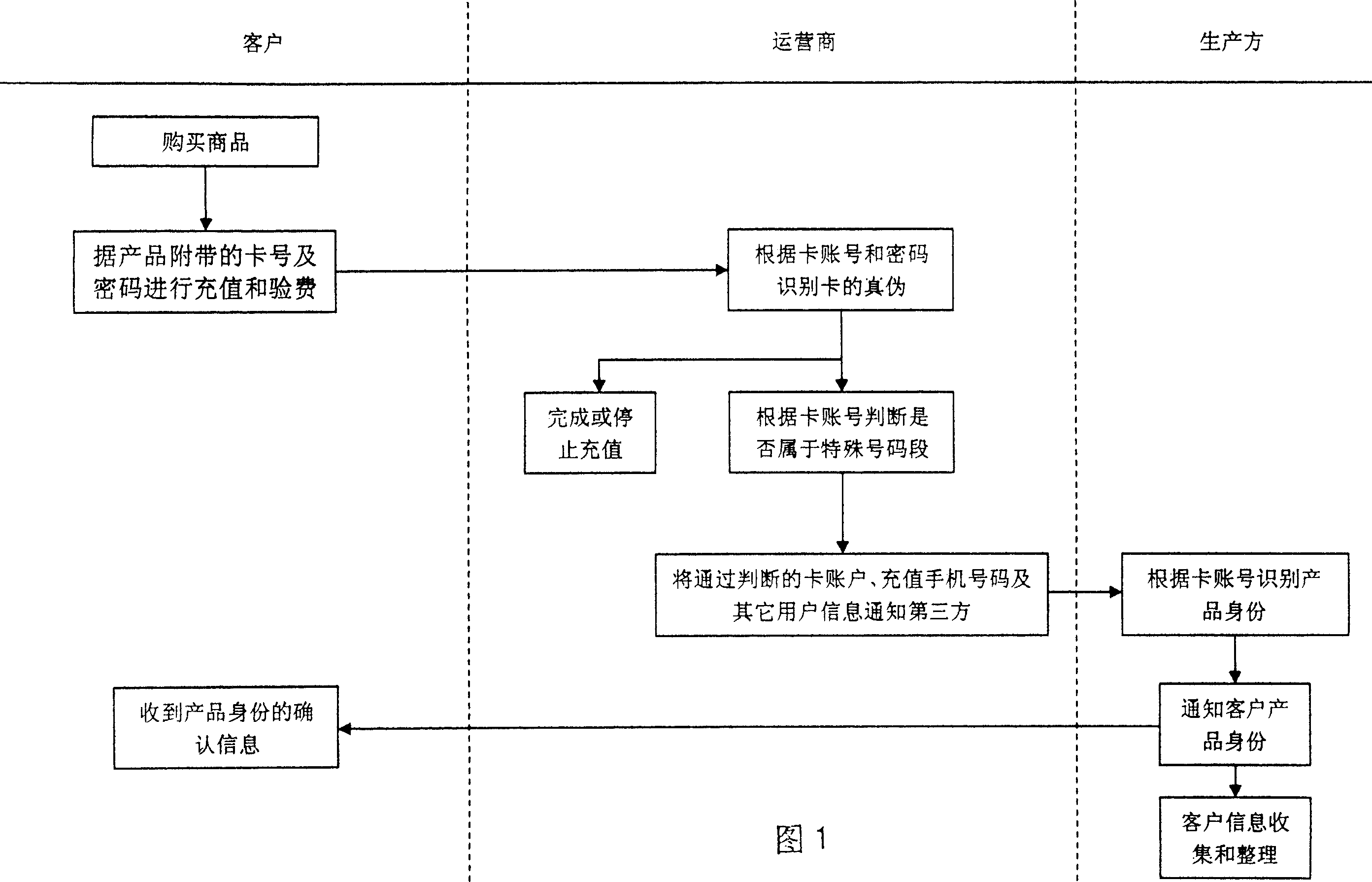
The disclosed new anti-falsification method comprises: manufacturing anti-falsification telecom charge card by telecom provider, building one-to-one code relation between card number and / or cipher and target product and company, storing the code into telecom query system while adding it on product or product description as common printing way; after buying product with anti-falsification code, customer can charges by SMS; the provider recognizes the code through said query system according to the input card number and cipher, and replies by SMS or speech. Compared with traditional technology, this invention has well reliability and query rate.
Owner:张慧荣
An Internet of things vulnerability information management system based on data virtualization
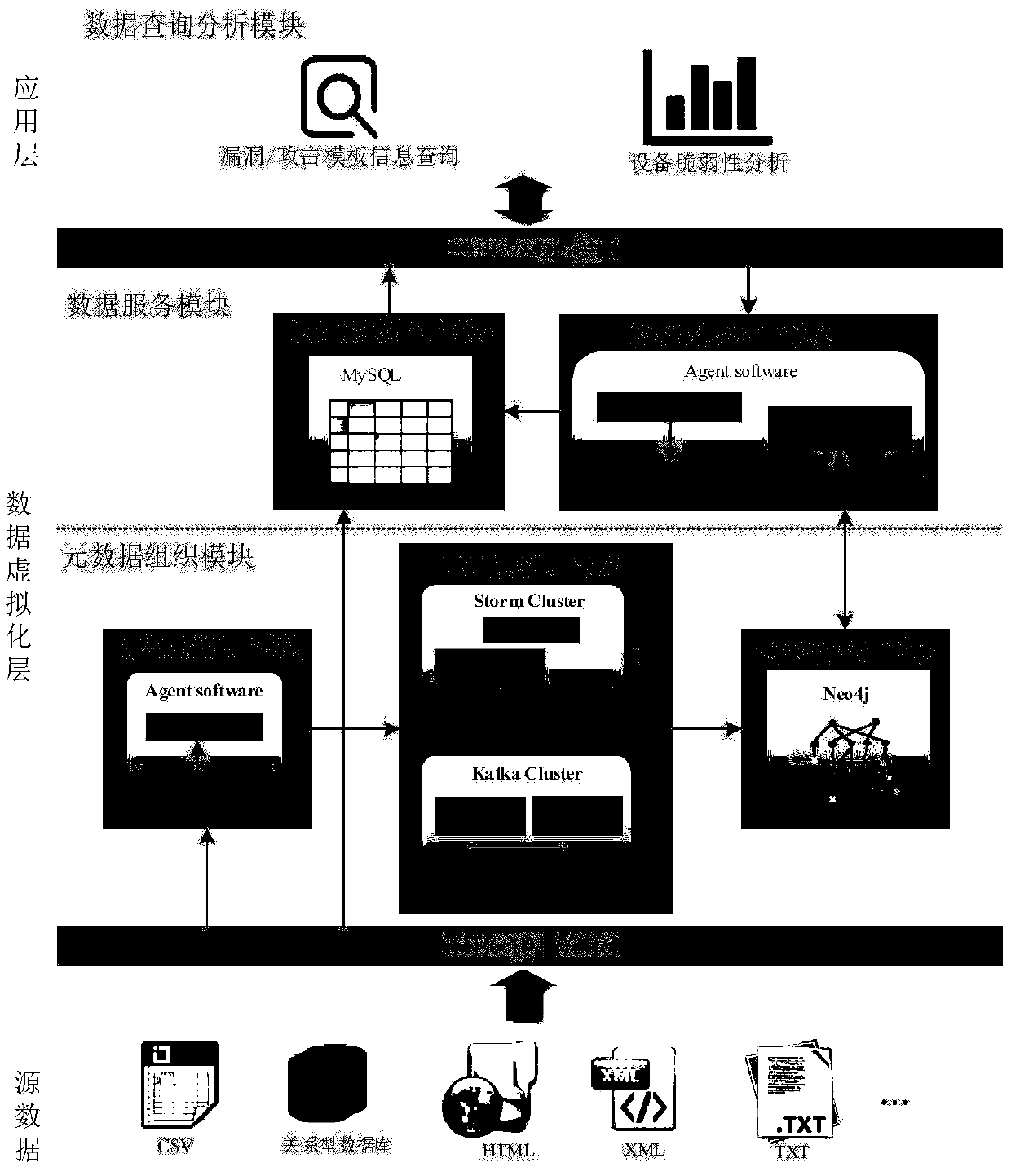
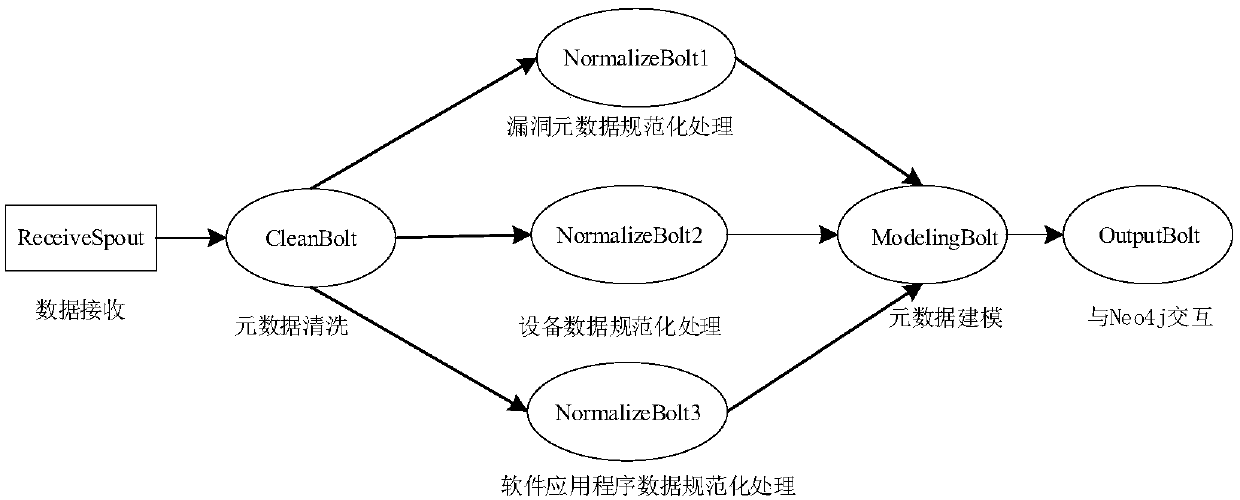
InactiveCN109542846AImprove query rateRealize managementDigital data protectionFile access structuresEffective managementVulnerability
The invention provides an Internet of things vulnerability information management system based on data virtualization, proposes a reference framework for vulnerability information management, and designs a hierarchical network structure organization model of metadata based on Neo4j, which can effectively utilize the advantages of Neo4j in multi-relationship management, establish bi-directional index structure for metadata, reduce index space, and improve the query speed of metadata. The data virtualization method has high flexibility and applicability, but there is no universally recognized solution for the implementation of its system at present. The invention systematically utilizes the relationship between the source data itself, improves the retrieval efficiency of the metadata, and improves the performance of the whole system. This system can not only realize the effective management of vulnerability information in Internet of Things, but also solve the problems of low real-time data and data security in data management system. At the same time, it also provides a new solution for other heterogeneous data management.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Method of realizing free search by bonding anti-forgery search with advertisement release in medicine sale terminal and system thereof
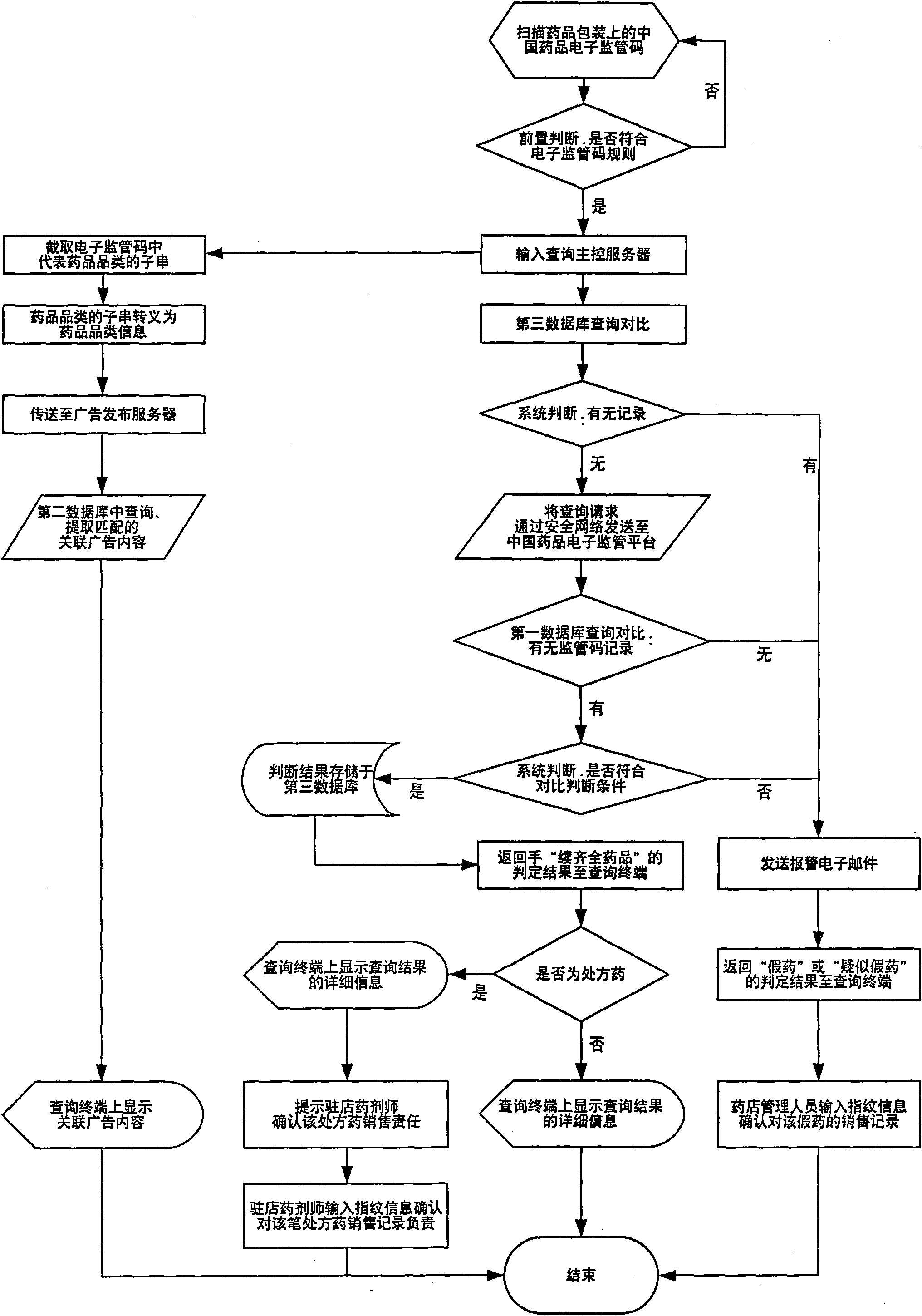
InactiveCN101661505AImprove query rateEasy to operateMarketingSpecial data processing applicationsDevice placementDrug product
The invention provides a method of realizing free search by bonding anti-forgery search with advertisement release in medicine sale terminal and a system thereof, and the system is formed by using thesearch terminal arranged in the medicine sale terminal to access the background service system. The electronic monitoring information collected by the Chinese pharmaceutical electronic monitoring platform is used as the reference of search and contrast, the judgment standards of 'fake medicine', 'suspected fake medicine' and 'medicines which meet the electronic monitoring standard of medicines' are defined; and the invention provides the contrasting and judging method which can accurately identify the fake medicines of which sale can be realized by using the regulatory codes which are sold, canceled after verification and not queried, when consumers adopt the anti-forgery search. The search equipment is arranged in the sale terminal, the search is easier and the anti-forgery search systemis bound with the function capable of triggering advertisement release so as to provide the income support for the free search of consumers, increase the anti-forgery search and the probability thatfake medicines are found, completely change the situation that the anti-forgery search rate of medicines is low and forgeries can not be resisted truly and effectively and form the method and system of electronic anti-forgery terminal block, which are strong enough to deter the people who produce and sell fake medicines.
Owner:耿泉生
Three-dimensional sawtooth anti-counterfeiting product
ActiveCN110084348AEasy to identifySave the hassleStampsRecord carriers used with machinesForming processes
Owner:HAINAN PAIPAIKAN INFORMATION TECH CO LTD
Self nucleus structure anti-fake peper method
InactiveCN1782228AImprove recognition rateImprove query rateNon-fibrous pulp additionRecord carriers used with machinesProgramming languageBarcode
The present invention relates to a kind of self-checking structure anti-fake paper method. The random anti-fake characteristic information on the safety line embedded inside paper is selected and converted into self-checking code and bar code corresponding to the number characteristic of the random anti-fake characteristic information and printed on the safety line. The self-checking code and the sequence code are stored in the computer database, and the consumer may one by one check based on the structure characteristic and its conversion code in different frames on the safety line. Or, by means of communication facility and inputting the conversion code and sequence code, the truth of the paper product may be checked via inquiring the stored code in the database. The bar code in the safety line may be also used in management.
Owner:李峰
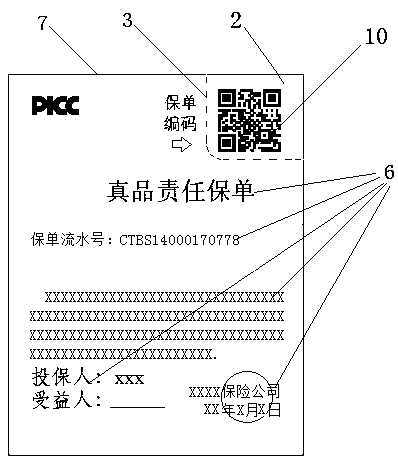
Genuine product responsibility insurance policy setting method and query and registration system
PendingCN110570218ADifficult to counterfeitIncrease credibilityFinanceCommerceTechnology researchComputer science
The invention belongs to the technical field of product responsibility insurance, and relates to a genuine product responsibility insurance policy setting method and a query and registration system. The method comprises the following steps: setting a genuine responsibility insurance policy for a product, encoding the insurance policy, making the code on an insurance marker, setting the marker on the product, and correspondingly storing insurance policy information, anti-counterfeiting information and the insurance policy code into an insurance policy query and registration system database; a consumer unconsciously identifying the authenticity of the insurance policy in the process of registering the received insurance policy in the insurance policy query and registration system by using the smart phone. According to the invention, a new function and a new application for providing anti-counterfeiting protection for other products are added to the genuine product responsibility insurance policy. The outstanding unexpected technical effect is the beneficial technical effect which is dreamy for domestic and overseas anti-counterfeiting technology and insurance technology research anddevelopment personnel.
Owner:HAINAN PAIPAIKAN INFORMATION TECH CO LTD
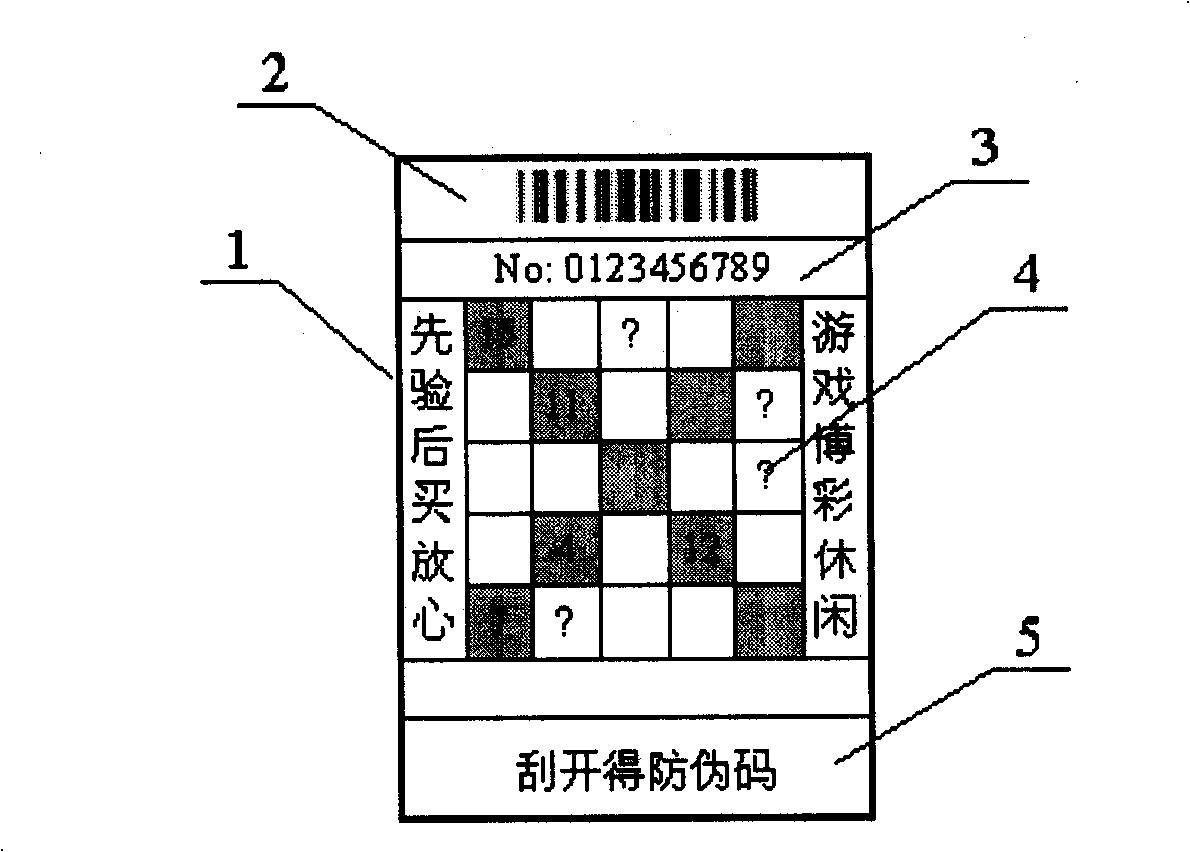
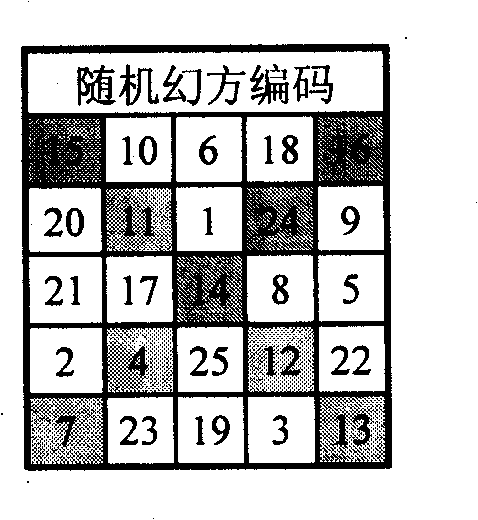
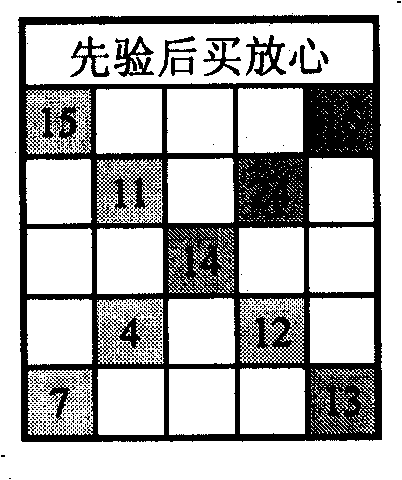
Magic square multifunctional numerical code information anti-counterfeiting label and anti-counterfeiting method
InactiveCN101256725AImprove query rateImprove monitoring effectStampsCommerceNon destructiveComputer science
The invention discloses a magic square multifunctional digital information anti-fake label integrated with anti-counterfeit, logistical monitoring, lottery promoting and game promoting. The multifunctional digital anti-fake label comprises the label with ID code, anti-fake code and defect magic square; the anti-fake code has covering layer; the defect magic square is obtained in such way: selecting part of column, row or diagonal in an optional magic square as bidirectional correction number element, and then selecting about half of the numbers as label character number information as plain code printed on the label defect magic square. The invention makes the ID code, the anti-fake code and the defect magic square integrated in a label, and makes the label lottery information to hide in database correction code. The invention has multiple anti-counterfeiting ability including anti-fake correction before non-destructive purchase and destructive anti-fake authentication after purchase, which accomplishes commodity in set associative anti-counterfeit, and improves inquiry ratio of anti-fake label greatly by promoting lottery and promoting game; meanwhile, the encryption algorithm can be public, as well as the database.
Owner:谢涛
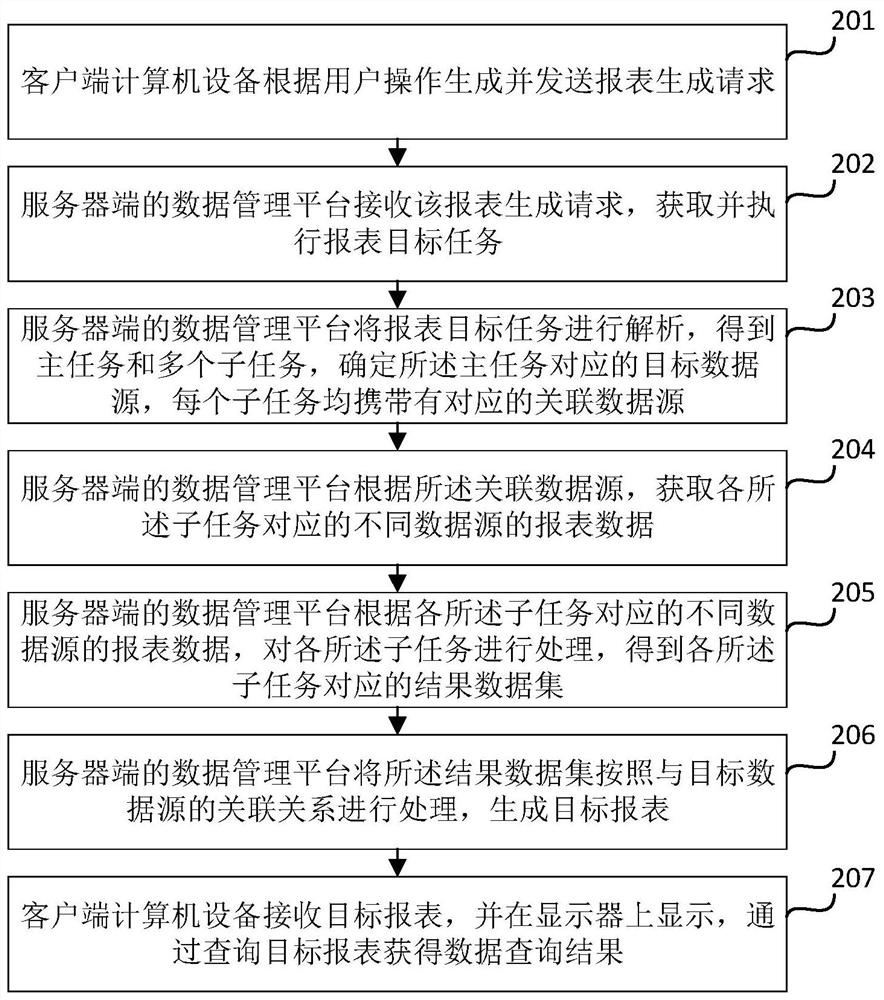
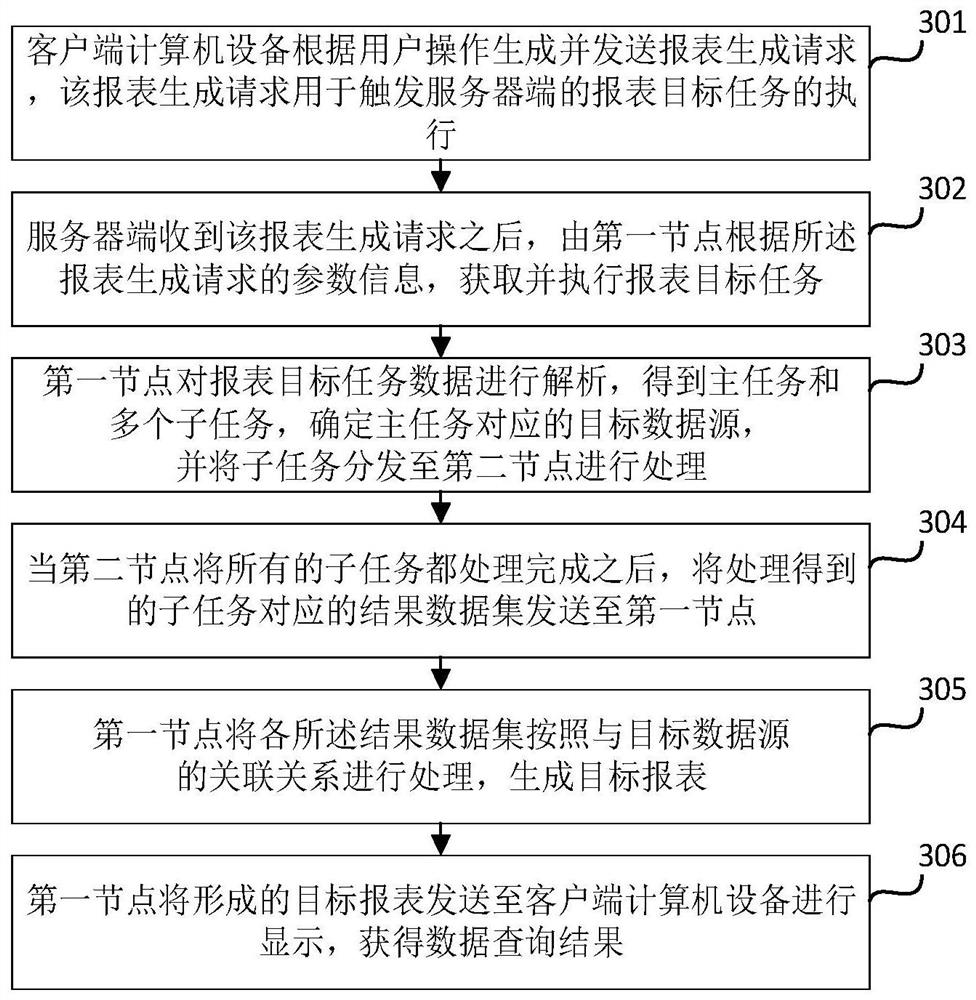
Report data query method, device and system based on multiple data sources and storage medium
ActiveCN112527848AImprove query rateEnable real-time integrationRelational databasesEnergy efficient computingData setData source
The invention relates to a report data query method, device and system based on multiple data sources and a storage medium, and belongs to the technical field of computer data processing. The method comprises the steps: according to a report generation request, obtaining a report target task, analyzing the report target task, and obtaining a main task and multiple sub-tasks, determining a target data source corresponding to the main task and an associated data source corresponding to each sub-task; according to the associated data source, obtaining report data of different data sources corresponding to each subtask, and processing each subtask to obtain a result data set corresponding to each subtask; processing each result data set according to an association relationship with a target data source to generate a target report; and obtaining a data query result according to the target report. According to the method, the problem of relatively low query speed caused by data query of different data sources can be solved; according to the method and the device, different data sources can be integrated into one report by decomposing the target task, so that quick query of the data is realized.
Owner:SUZHOU KEDA TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com