Trusted network communication method and device based on safety chip hardware algorithm module
A hardware algorithm and security chip technology, applied in the field of digital information transmission, can solve the problems of low credibility and security, achieve the effect of improving security and credibility, and reducing the possibility of data theft
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
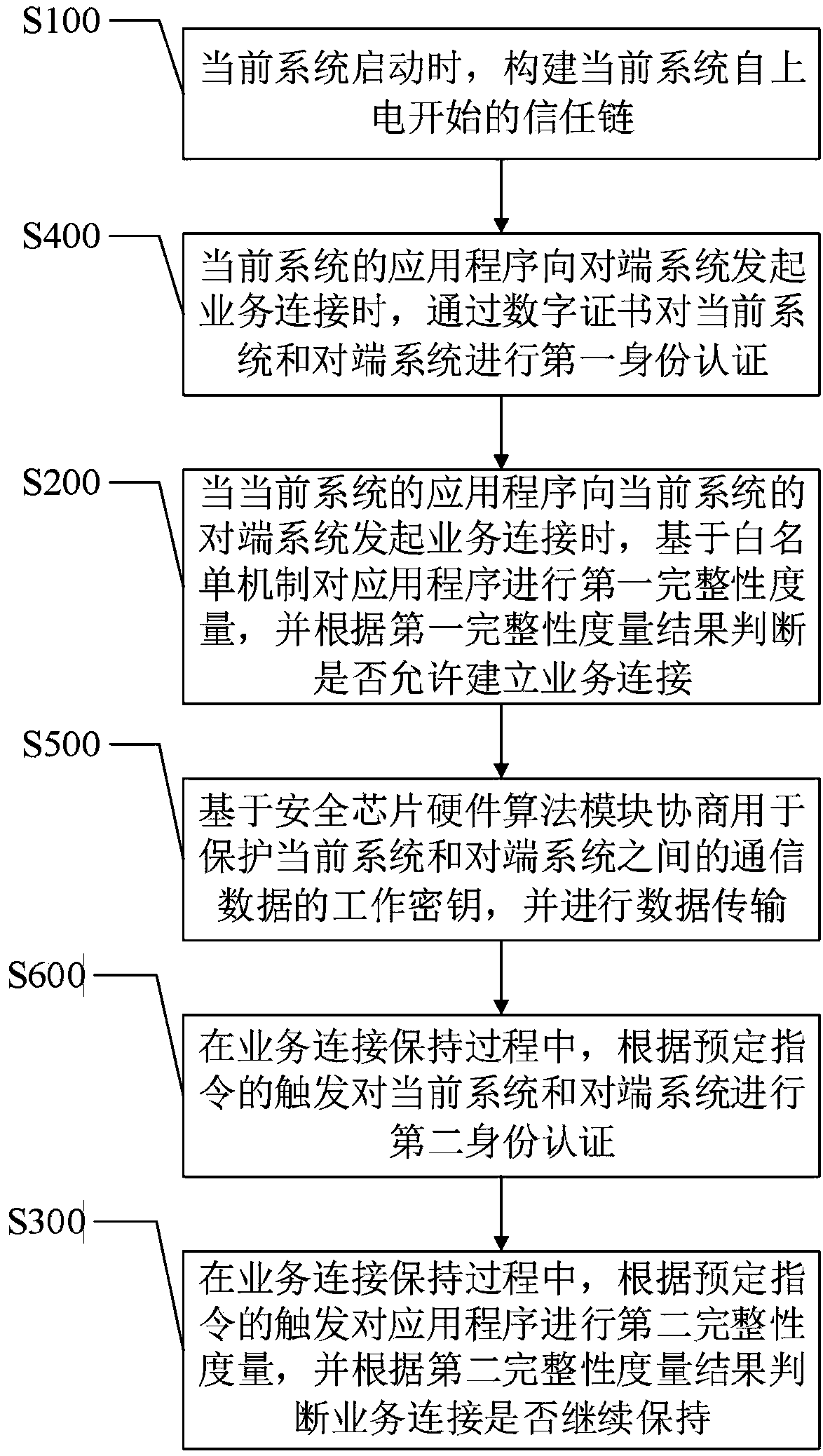
[0029] This embodiment provides a trusted network communication method based on the security chip hardware algorithm module, such as figure 1 described, including the following steps:
[0030] Step S100, when the current system starts up, build a trust chain of the current system since it is powered on. In this embodiment, the current system may be a terminal system or a master station system. In a specific embodiment, the terminal system is an embedded terminal system, and the master station system is a power master station system.
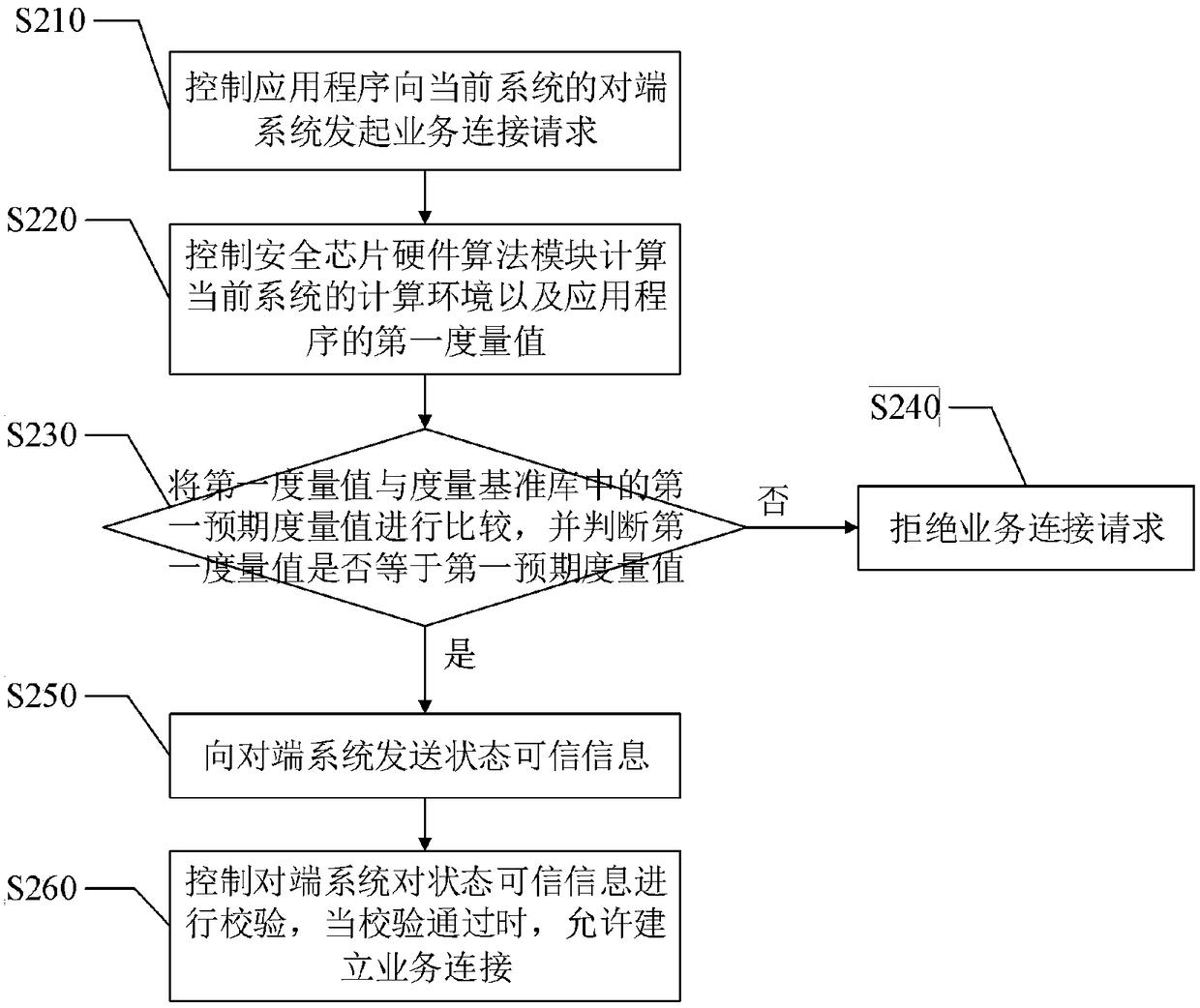
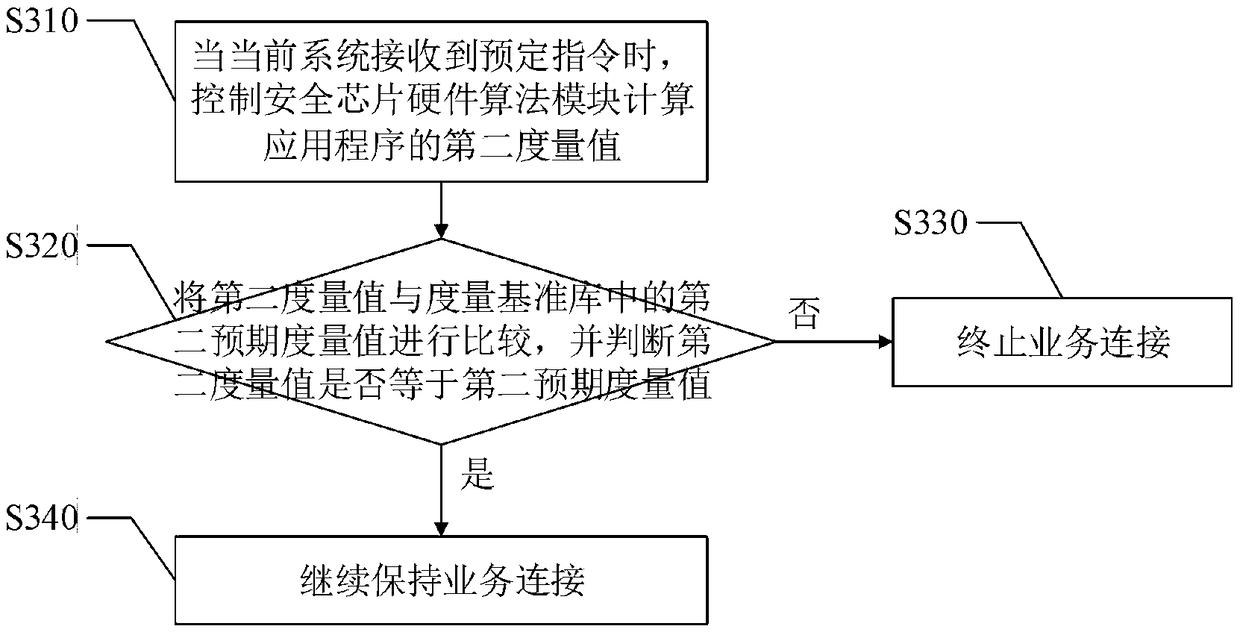
[0031] Step S200, when the application program of the current system initiates a service connection to the peer system of the current system, perform a first integrity measurement on the application program based on the whitelist mechanism, and judge whether to allow establishment of a service connection according to the result of the first integrity measurement. In this embodiment, step S200 is used to perform the first state authentication whe...
Embodiment 2
[0056] This embodiment provides a trusted network communication device based on a security chip hardware algorithm module, including: a trust chain building module, a static measurement module and a dynamic measurement module.
[0057] The trust chain building module is used to build the trust chain of the current system since power-on when the current system starts. In this embodiment, the current system may be a terminal system or a master station system. In a specific embodiment, the terminal system is an embedded terminal system, and the master station system is a power master station system.
[0058] The static measurement module is used to perform the first integrity measurement on the application program based on the white list mechanism when the application program of the current system initiates a business connection to the peer system of the current system, and judge whether to allow the establishment of business according to the first integrity measurement result co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com