Hand-write input discriminator, method and medium for storing hand-wirte input discriminating program
A handwriting input and identification process technology, applied in the input/output process of data processing, input/output of user/computer interaction, memory system, etc., can solve the problem that handwritten strings will be seen or forged by others
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] Preferred embodiments of the present invention will be described below with reference to the accompanying drawings.
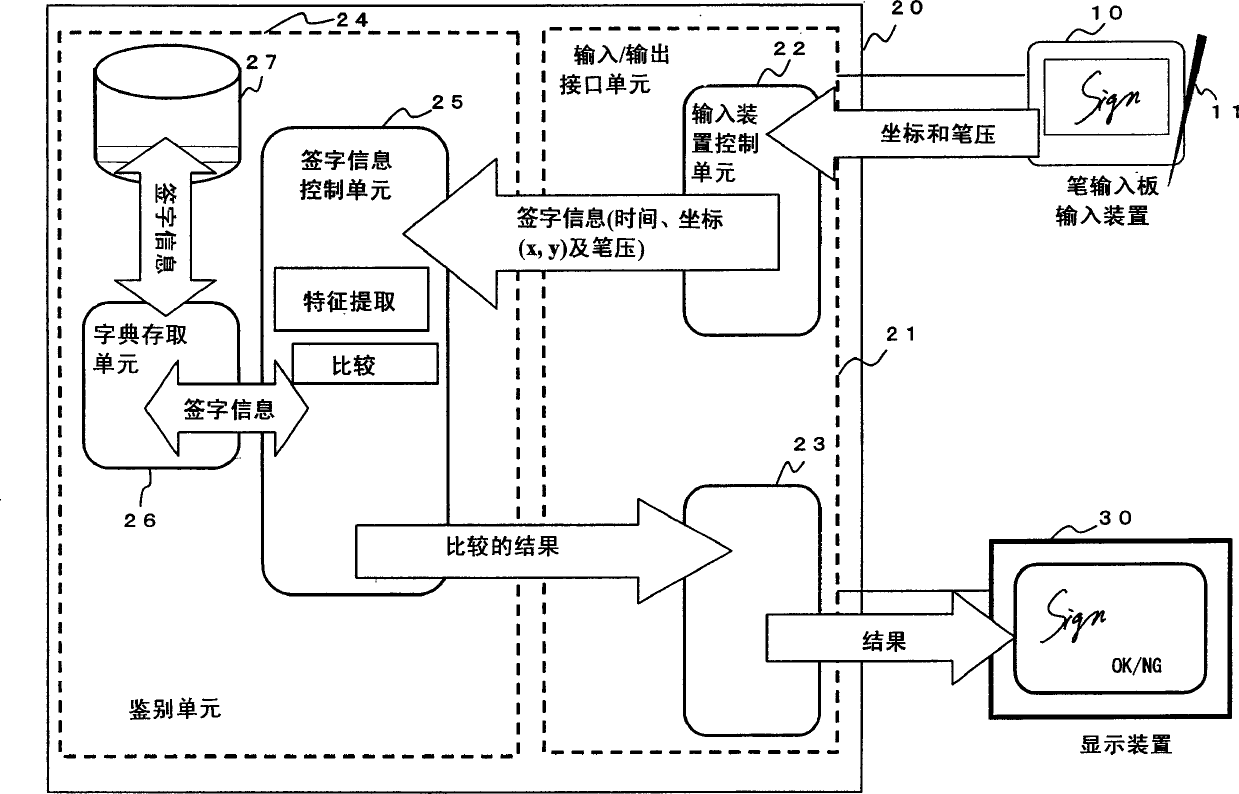
[0039] Fig. 2 shows the hardware structure of the handwriting input identification system in the embodiment of the present invention. The handwriting input authentication system of this embodiment includes an input device 10 , an authentication server 20 and a display 30 .
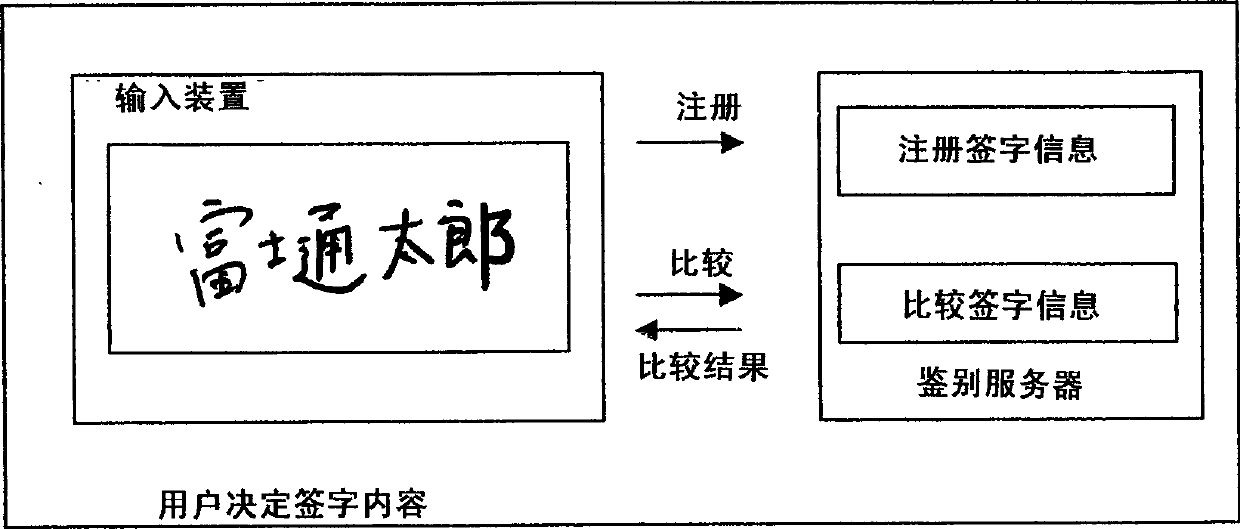
[0040] The hardware structure of the handwritten input authentication system of this embodiment is basically the same as that of a general handwritten signature authentication system. However, in the system of this embodiment, the information used for authentication is not necessarily limited to "user's name", and other character strings, a graphic or a symbol can also be used.
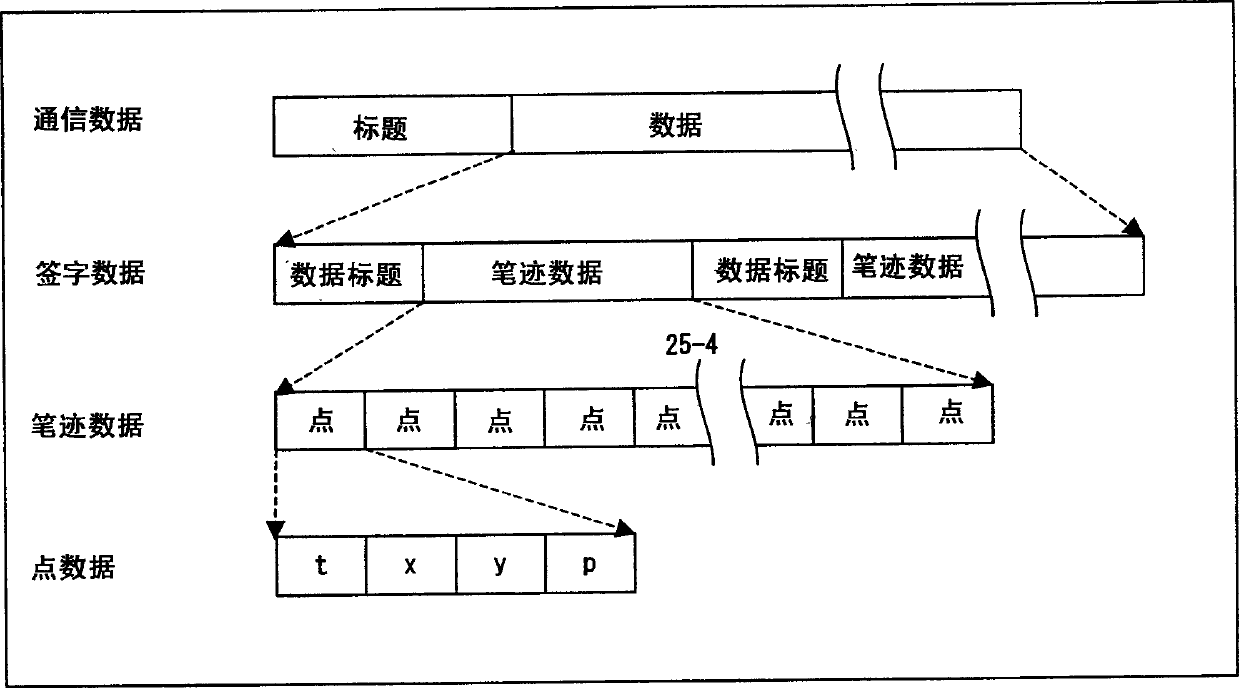
[0041] The input device 10 can be realized, for example, by a pen tablet system. Here, the input device 10 receives input by the user with the pen 11 . In particular, the input device 10 is provided with ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com