Multipart identification authentication method and system base on equipment
An identity authentication and legal identity technology, applied in the field of device-based multi-party identity authentication methods and systems, can solve the problems of fixed authentication process, low identity authentication security, and high authentication consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
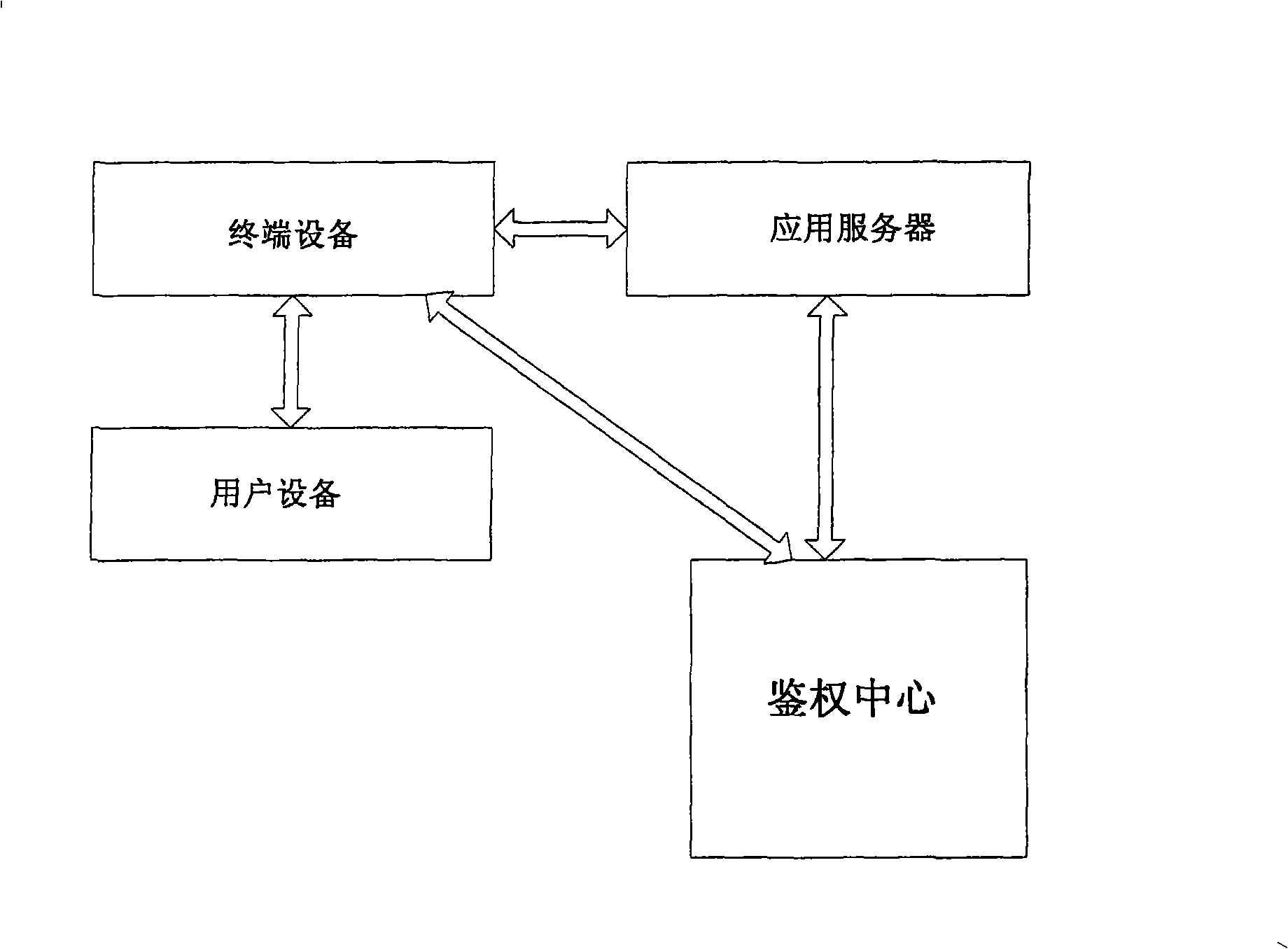
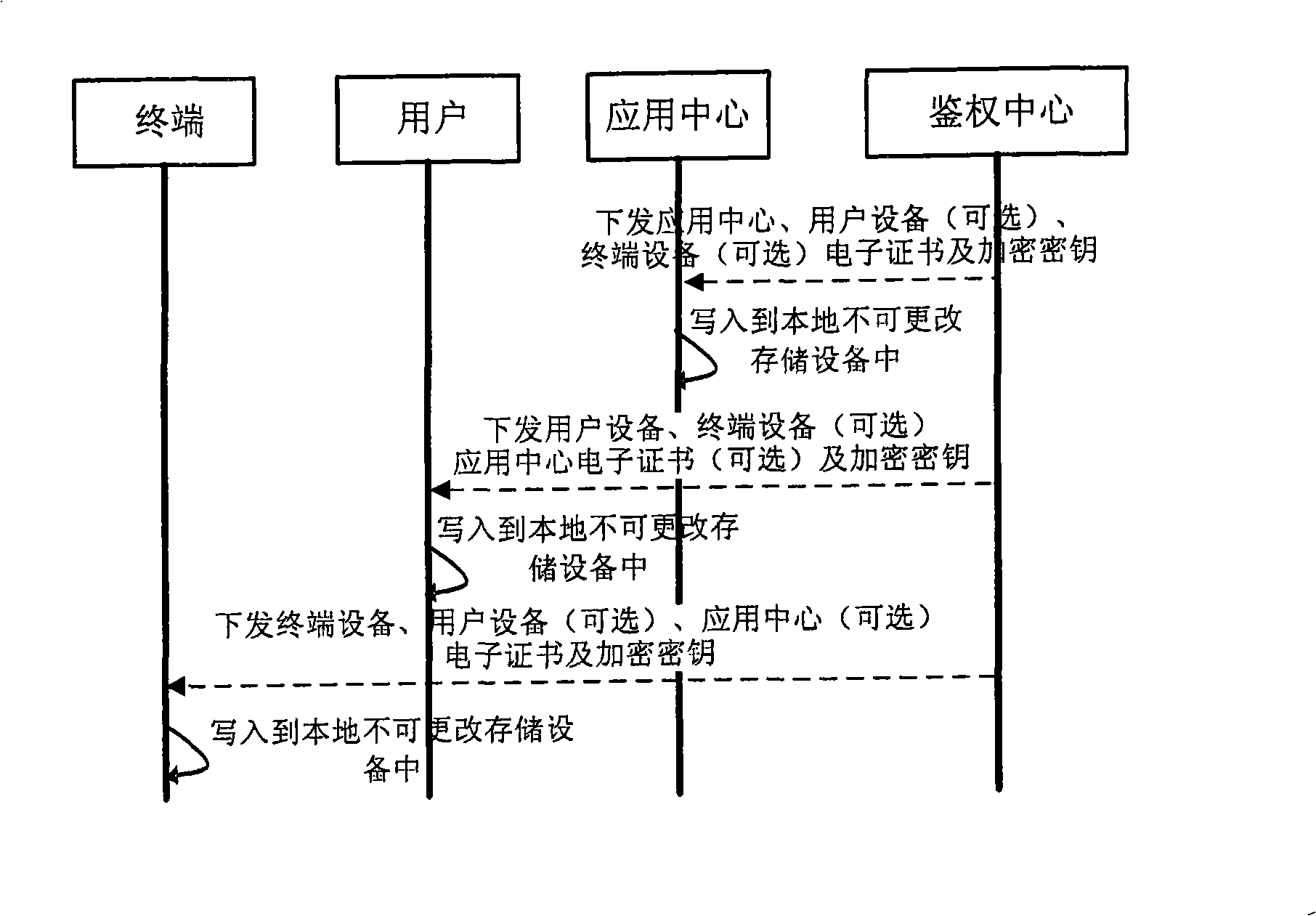
[0023] Such as figure 2 As shown, the authentication server of the authentication center issues a unique electronic certificate to the terminal device in a secure manner, and the terminal device solidifies the electronic certificate in the terminal device to ensure that it cannot be tampered with. The authentication center provides a security key to the terminal device through a secure channel, and the terminal device stores the key in a local hardware environment. The algorithm of encryption and decryption is implemented by hardware to prevent tampering and theft. According to the records of the authentication policy module of the authentication center, if the terminal device needs to authenticate the user equipment or the application server of the application center, the authentication center will pass the electronic certificate and the corresponding encryption key of the user equipment and the application center through a secure method. Send it directly to the terminal de...
Embodiment 2
[0034] Such as Figure 4 As shown, the process of user equipment authentication terminal equipment includes the following two schemes:
[0035] 1) When the user equipment performs the operation of authenticating the terminal equipment, the user equipment assumes that the terminal equipment is untrustworthy, transmits the identity information of the terminal equipment locally stored in the user equipment to the terminal equipment, and uses the terminal equipment key stored locally in the user equipment for encryption ;The terminal device receives the encrypted terminal device information transmitted by the user device, decrypts it using the terminal device key stored locally, obtains the electronic certificate of the terminal device uploaded by the user device, compares it with the identity information stored locally, and returns to the user device the The locally stored terminal device key encrypts the confirmation message, and the user equipment uses the locally stored termin...
Embodiment 3
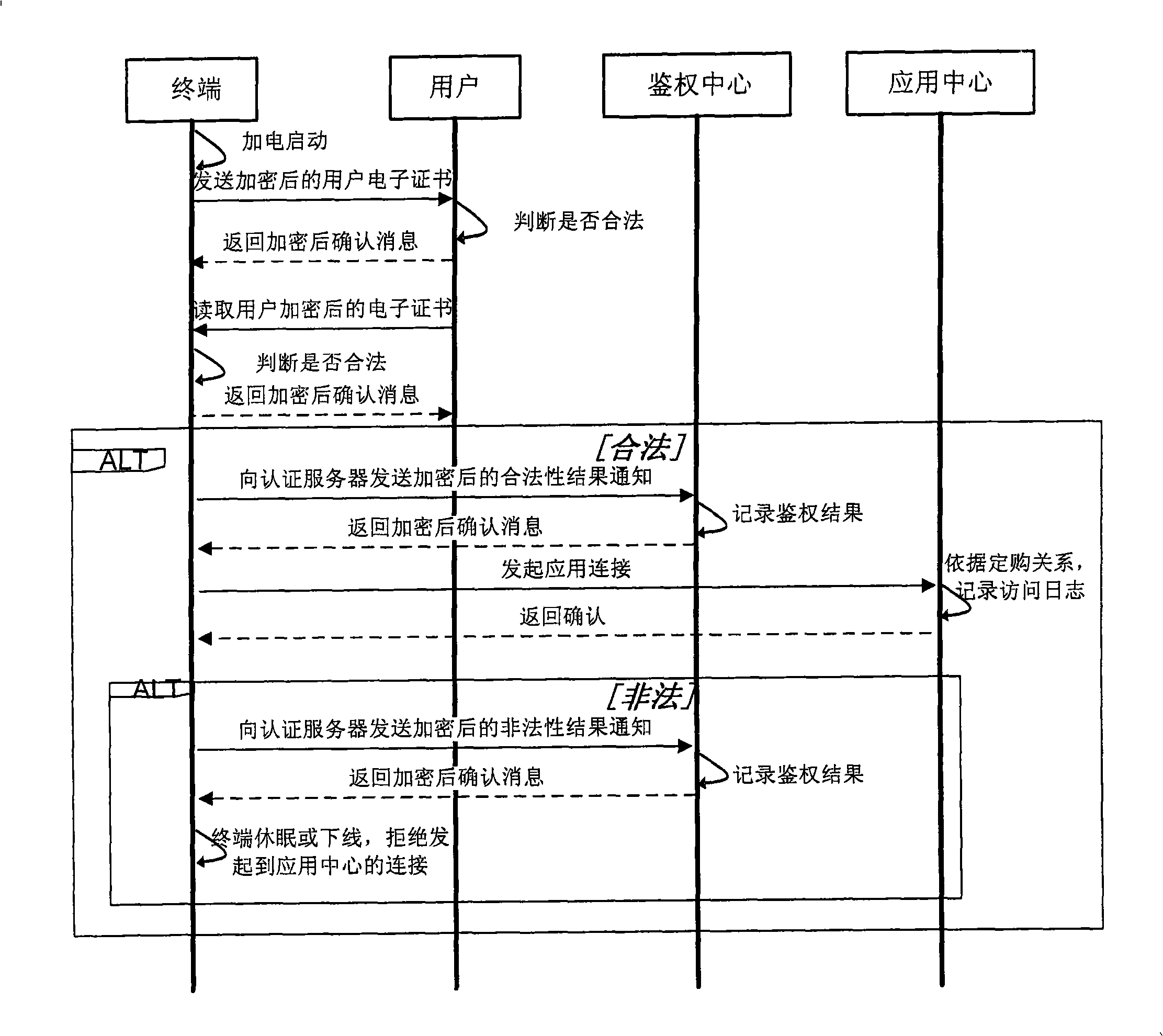
[0039] Such as Figure 5 As shown, the authentication of the terminal to the application center includes two schemes:
[0040] 1) After the terminal is powered on and started, it sends the application center identity authentication information locally stored in the terminal to the application center, and encrypts it with the application center key stored locally in the terminal; the application center receives the encrypted application center identity information transmitted by the terminal, and uses the local The stored application center key is decrypted, the application center electronic certificate uploaded by the terminal is obtained, and compared with the identity information stored locally, the terminal sends an authentication result notification to the authentication center according to the comparison result, and uses the locally stored identity information The terminal encryption key encrypts the message. The terminal judges that the identity of the application cente...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com