Sensitive data trading system and method based on block chain
A sensitive data and transaction system technology, applied in the field of blockchain technology and e-commerce, can solve problems such as tampering, participants' inability to prove their innocence, and digital information leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
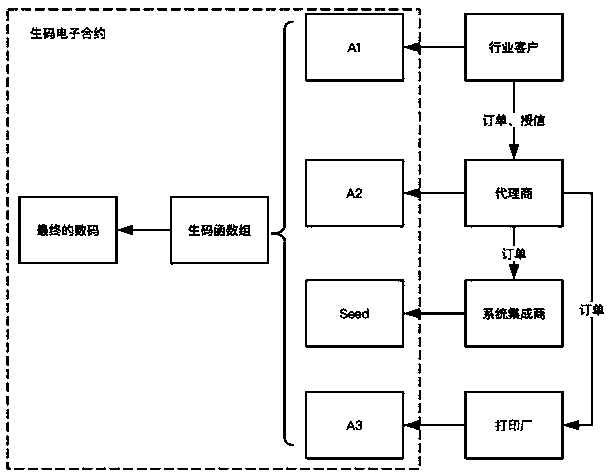
[0079] Embodiment 1: A blockchain-based sensitive data transaction system, including a blockchain bottom layer module, an electronic contract layer module, and a SaaS layer module;
[0080] The blockchain layer module provides underlying blockchain technical support, including a virtual machine that supports electronic contract operation, a consensus algorithm, a transaction verification mechanism, and an accounting mechanism;
[0081] The electronic contract layer module provides distributed application services, endorses using blockchain technology, and runs codes for sensitive data transactions of the system and codes for digital generation algorithms at the electronic contract layer;
[0082] The SaaS layer module provides cloud platform services, allowing each participant to conveniently participate in business collaboration through the web platform and the client.
[0083] Preferably, each of the bottom layer modules of the blockchain, the electronic contract layer modul...
Embodiment 2
[0101] Embodiment 2: The present invention also proposes a method for a blockchain-based sensitive data transaction system, comprising the following steps:
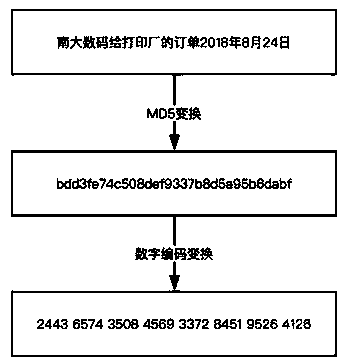
[0102] In the first step, the first participant obtains a random number A_1 through the hash algorithm according to the order information, stores it in the electronic contract, and is invisible to the outside world;
[0103] In the second step, the second participant obtains a random number A_2 through the Hash algorithm according to the order information, and stores it in the electronic contract for subsequent code generation, which is invisible to the outside world;
[0104] The third step is the step of uploading the seed code by the third party. If the third party has a seed code, it can choose to upload the seed code to the blockchain electronic contract. The seed code is generated by the third party itself; If the third participant does not have a seed code, the seed code will actually be automatically generated by ...
Embodiment 3
[0106] Embodiment 3: The present invention also proposes a method for applying a blockchain-based sensitive data transaction system, comprising the following steps:
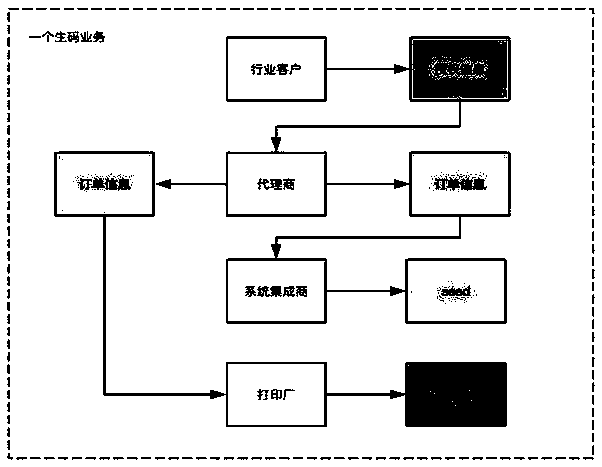
[0107] Steps for an industry customer to place an anti-counterfeit label order to an agent or directly to a system integrator and a printing factory. The industry customer logs in to the industry user sub-module, places an order for an anti-counterfeit label to the agent, and calls the electronic contract interface through the SaaS layer when placing the order. The order information is stored in the blockchain electronic contract on the blockchain platform, and the system automatically obtains a random number A_1 through the hash algorithm according to the order information, which is stored in the electronic contract and is invisible to the outside world;
[0108] The agent receives the anti-counterfeit label order from the industry customer and outsources it to the system integrator and printing factory; the agen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com