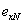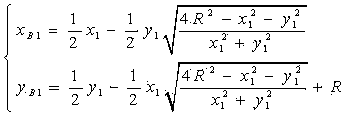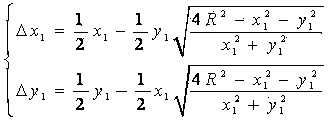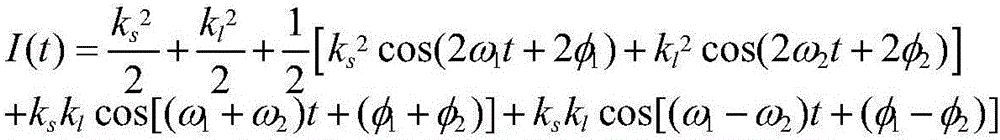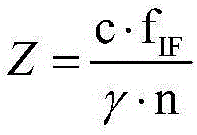Patents
Literature
222results about How to "Guaranteed authenticity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Method for analyzing Internet advertisement popularizing effect
The invention provides a method for analyzing Internet advertisement popularizing effect, which is characterized by including the following steps: step I, a Javascript is added to the website to collect codes, a user logs in a client to visit pages, and a server obtains user visit information; step II, the user type is determined according to the user visit information; step III, the user attribute of each user is categorized and analyzed; and step IV, the statistics of an analysis result is performed by the server, and the statistics result is displayed in percentage and total visit. The user visit information includes user track coordinate, total visit page time, visitor source city, source keywords, visit time, web browser, source website and visit page address. The user type includes a valid visit user and an invalid visit user. The method takes the fact that whether mouse track exists as the main standard for judging whether the flowrate is valid, and is not suitable for batch faking, thereby ensuring the authenticity and validity of the judgment.
Owner:刘志军
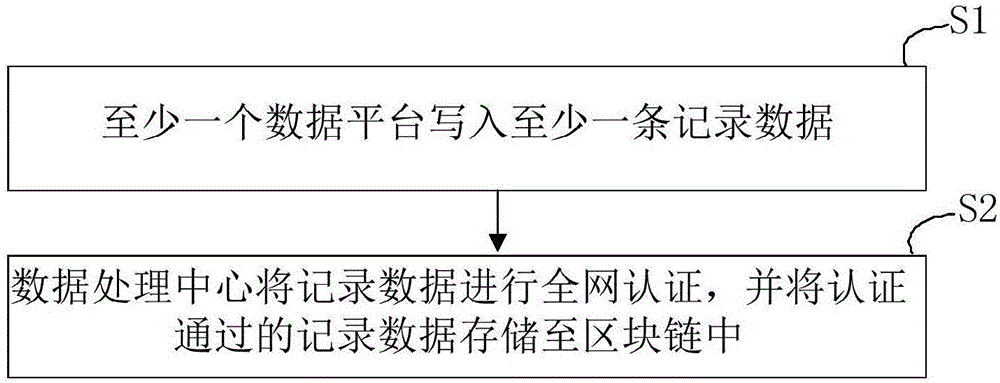
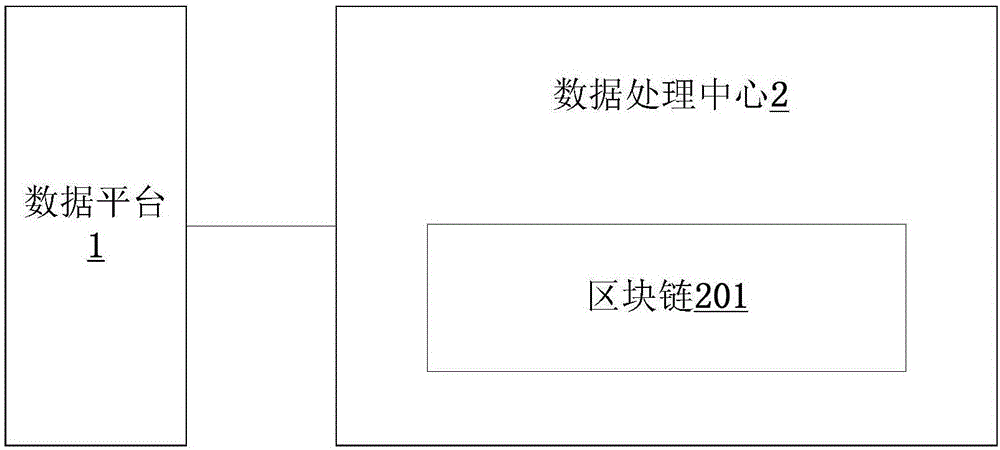
Data processing method and system based on block chain technology
InactiveCN106484836AGuaranteed authenticityDigital data protectionSpecial data processing applicationsData processing systemData platform
The invention provides a data processing method and system based on a block chain technology. The method comprises the following steps of writing at least one record data by at least one data platform; and performing whole network authentication on the record data by a data processing center, and storing the record data which pass the authentication to a block chain. The data processing method and the data processing system based on the block chain technology provided by the invention can be used for performing data recording on a plurality of mechanisms / data platforms, and storing data recorded by the plurality of mechanisms / data platforms to the block chain to count for subsequent query, and the block chain is adopted to store the data recorded by the plurality of mechanisms / data platforms, so that the authenticity and reliability of the record data can be ensured.
Owner:SHENZHEN AUDAQUE DATA TECH
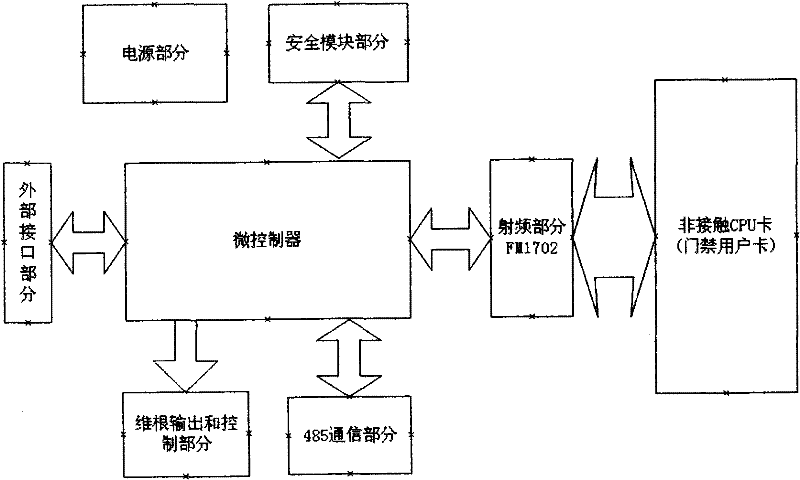
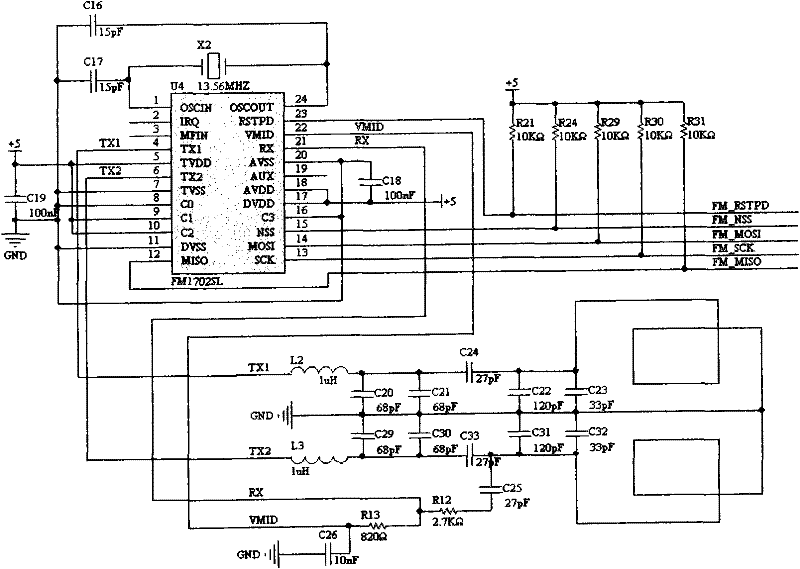
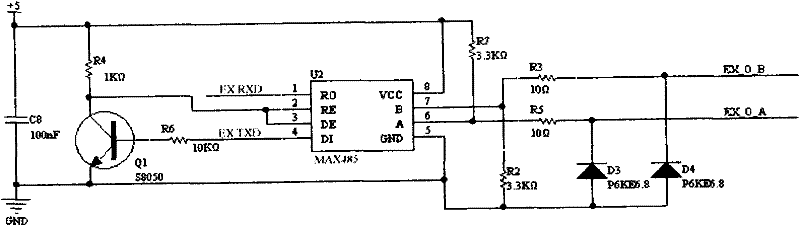
Non-contact CPU (Central Processing Unit) card entrance guard reader
InactiveCN102129730AMake the most of security featuresImprove security levelSensing record carriersIndividual entry/exit registersMicrocontrollerComputer module
The invention discloses a non-contact CPU (Central Processing Unit) card entrance guard reader comprising a radio frequency part, a 485 communication part, a security module part, a Wigan output and external control part, a power supply part, an external connection part, a microcontroller part and other parts. The non-contact CPU card entrance guard reader is internally provided with a PSAM (Pilot Symbol Assisted Modulation) card and applies security certification read-write mechanisms of the PSAM card and a CPU card. The CPU card entrance guard reader builds an integral and strict key management system by adopting the security certification of the PSAM card and the CPU card, sufficiently uses the security characteristics of the CPU card and comprises key systems of the CPU card and the PSAM card; after a key is input into the PSAM card, the key cannot be externally read, the PSAM card is inserted into card reading equipment, two-way validation is carried out through the PSAM card and the CPU card, a verified message is calculated through the participation of random data, and a same card is different every time when swiped on one equipment, therefore a counterfeit card is thoroughly prevented.
Owner:SHANGHAI ZTRON ELECTRONICS
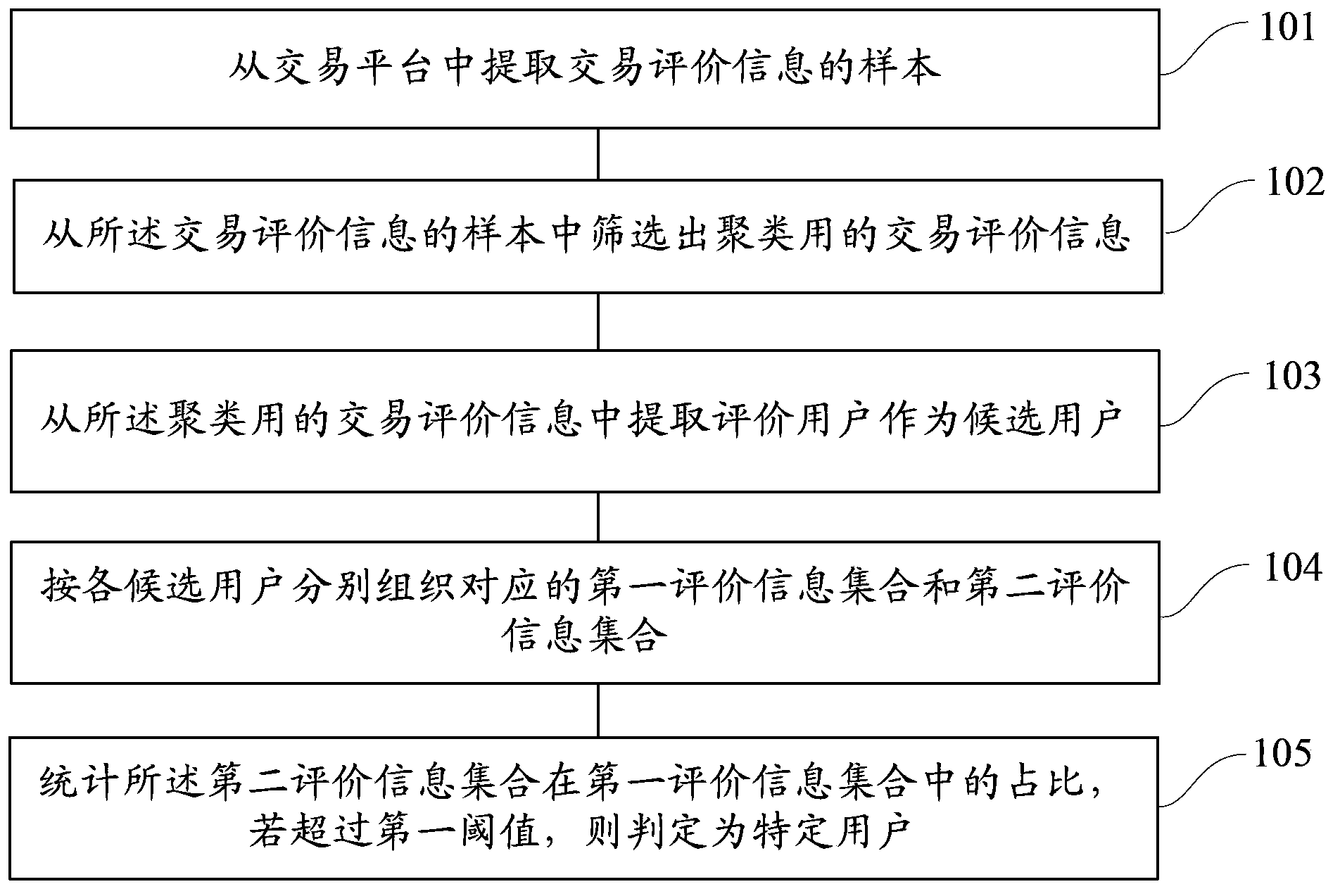
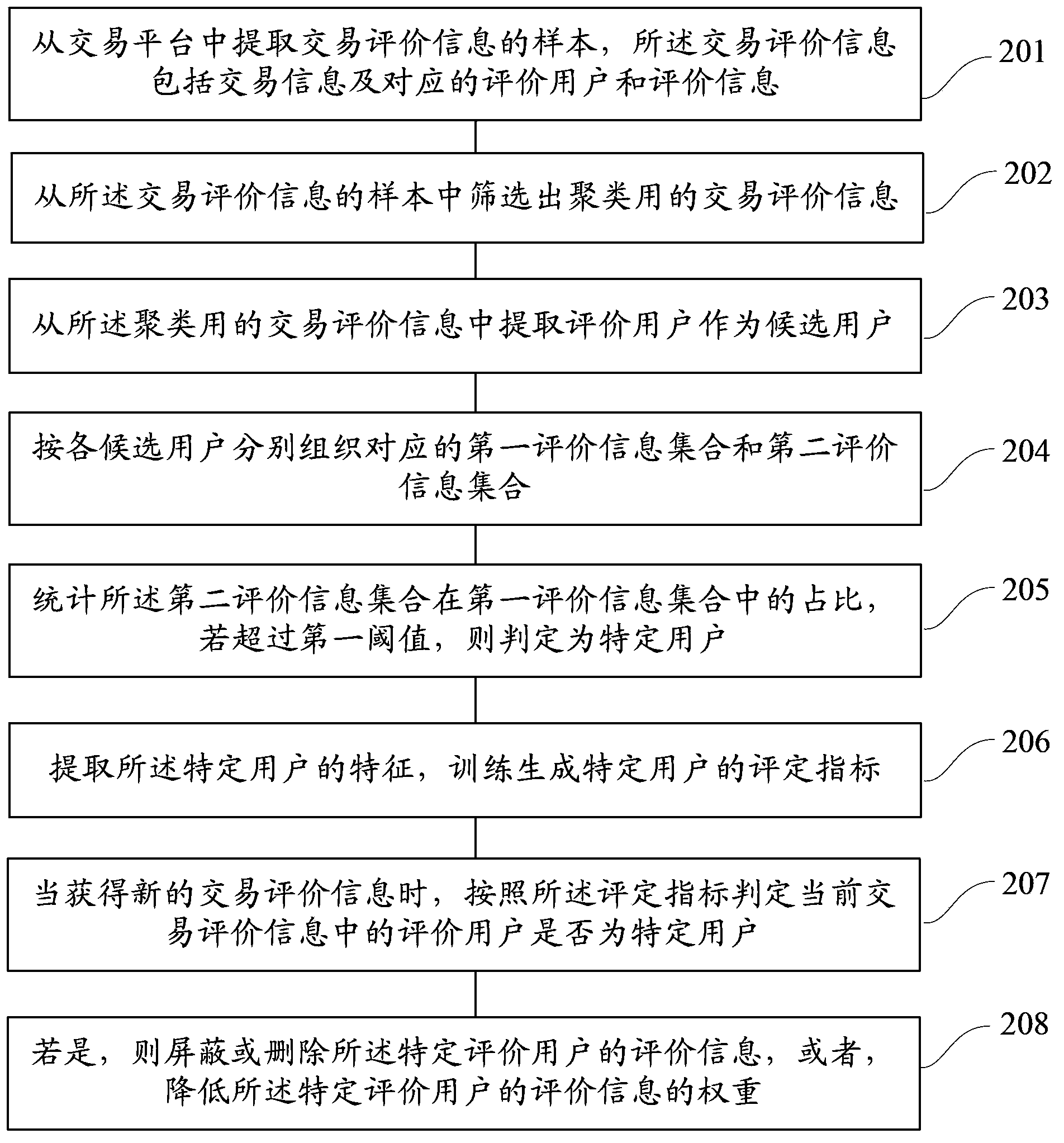
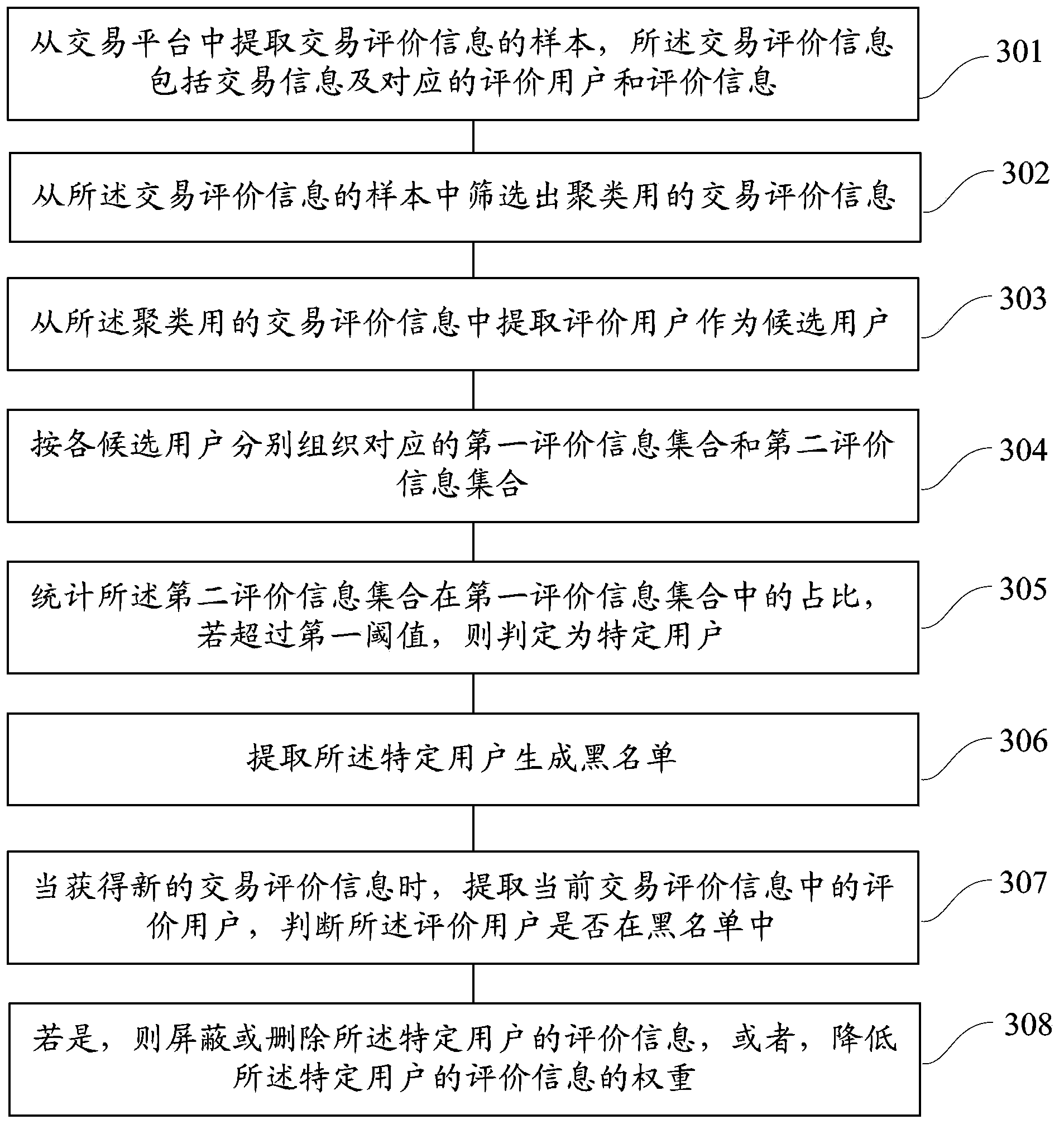
Method and device for recognizing specific user
ActiveCN103577988AEasy to identifyGuaranteed authenticityCommerceSpecial data processing applicationsData miningData science
The invention provides a method and device for recognizing a specific user. The method comprises the step of extracting samples of transaction assessing information from a transaction platform, the step of screening out transaction assessing information for clustering from the samples of the transaction assessing information, the step of extracting assessing users as candidate users from the transaction assessing information for clustering, the step of respectively organizing a first assessing information set and a second assessing information set according to the candidate users, and the step of counting the proportion, accounting for the first assessing information set, of the second assessing information set, wherein if the proportion is larger than a first threshold, the candidate user is the specific user. By means of the method, the true effectiveness of the credibility of a seller can be improved, the searching accuracy is improved, the burden borne by a server is relieved, and the occupation of the network resources is reduced.
Owner:ADVANCED NEW TECH CO LTD
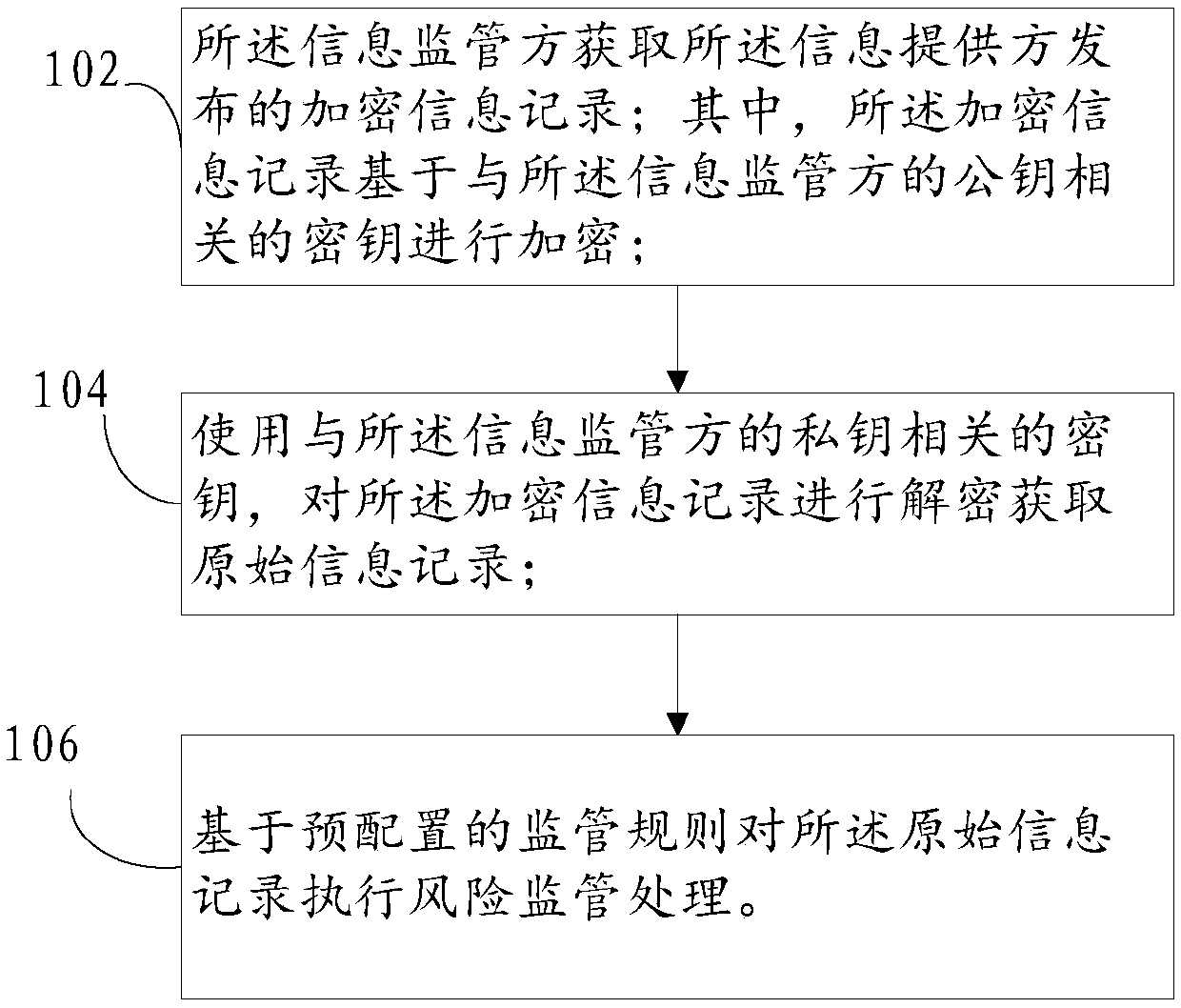
Block chain-based information supervision method and device
ActiveCN108681966AEnsure safetyGuaranteed authenticityFinanceDigital data protectionInformation provisionInformation providers
The specification provides an information supervision method and device, and is used for an information supervisor to supervise information provided by an information provider. The information supervisor and the information provider are set to be nodes of a block chain; the information supervisor obtains an encrypted information record issued by the information provider, wherein the encrypted information record is encrypted based on a key associated with a public key of the information supervisor; the encrypted information record is decrypted to obtain an original information record by using akey related to a private key of the information supervisor; and risk supervision processing is executed on the original information record based on pre-configured supervision rules.
Owner:ADVANCED NEW TECH CO LTD
Permission block chain privacy protection and supervision method based on group signatures
InactiveCN109636599AProtect identity privacyGood anonymityFinanceDigital data protectionPrivacy protectionIdentity privacy
The invention discloses a permission block chain privacy protection and supervision method based on group signatures. In a transaction process, whether the endorsement verification of the endorsementnode, the sequencing service of the sequencing node and the consensus process of the main node and the accounting node can only verify the legality of the identities of the two parties of the transaction, and cannot correspond the signature to the real identity of the user, so that the identity privacy of the user is guaranteed. After the transaction is completed, the supervision department can synchronize the block with other nodes through the supervision node, then open the signature contained in the transaction, and enable the signature to correspond to the real identity of the transactionuser, so as to supervise the block chain.
Owner:GUANGXI NORMAL UNIV
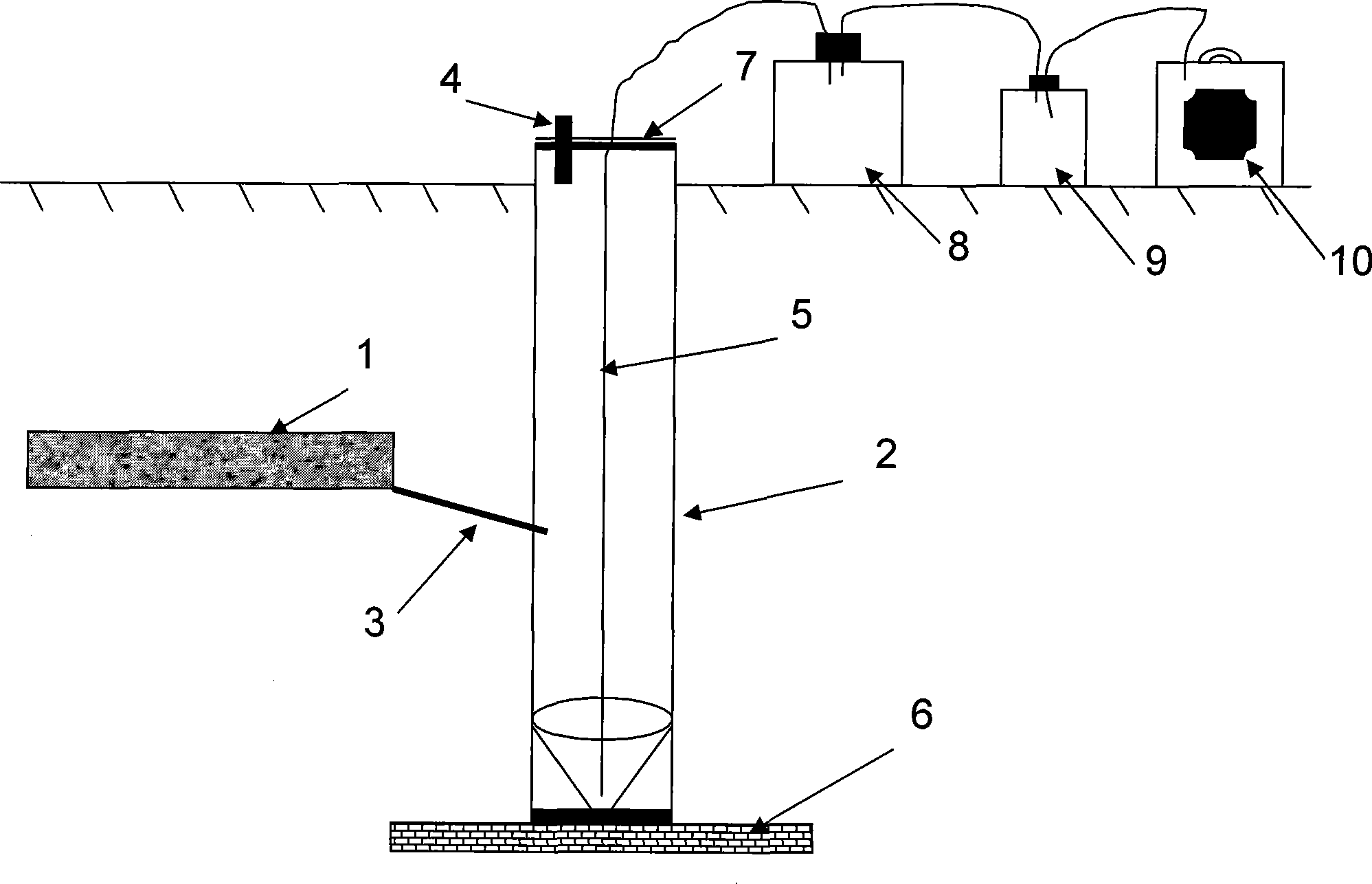
Gravity flow type farmland underground leaching liquor collecting device
InactiveCN101246094AGuaranteed leaching conditionUnrestricted installation depthWithdrawing sample devicesEarth material testingWater dischargePhosphor
The present invention discloses a self-flowing farmland underground drenching solution collecting device which belongs to the field for researching the environment science, agrology and plant nutriology. The device of the invention comprises an eluviation disk, a water-discharging pipe, a liquid-collecting pipe, a breathing pipe, a liquid drawing pipe, a sampling bottle, a buffering bottle and a vacuum pump; the eluviation disk is used for collecting the drenching solution; the liquid-collecting pipe is connected to the water outlet of the eluviation disk through the water-discharging pipe, the drenching solution in the eluviation disc can automatically flow into the liquid collecting tube; and the vacuum pump is used for extracting the drenching solution collected by the liquid-collecting pipe to the sampling bottle through the liquid drawing pipe under the buffering of the buffering bottle. Comparing with the prior art the invention has the characters of reasonable structure, convenient manufacturing, easy actualizing and the like, and the invention is especially suitable for monitoring the influence of the soil solutes of nitrogen, phosphor, agriculture chemicals and the like to the groundwater.
Owner:INST OF AGRI RESOURCES & REGIONAL PLANNING CHINESE ACADEMY OF AGRI SCI +4
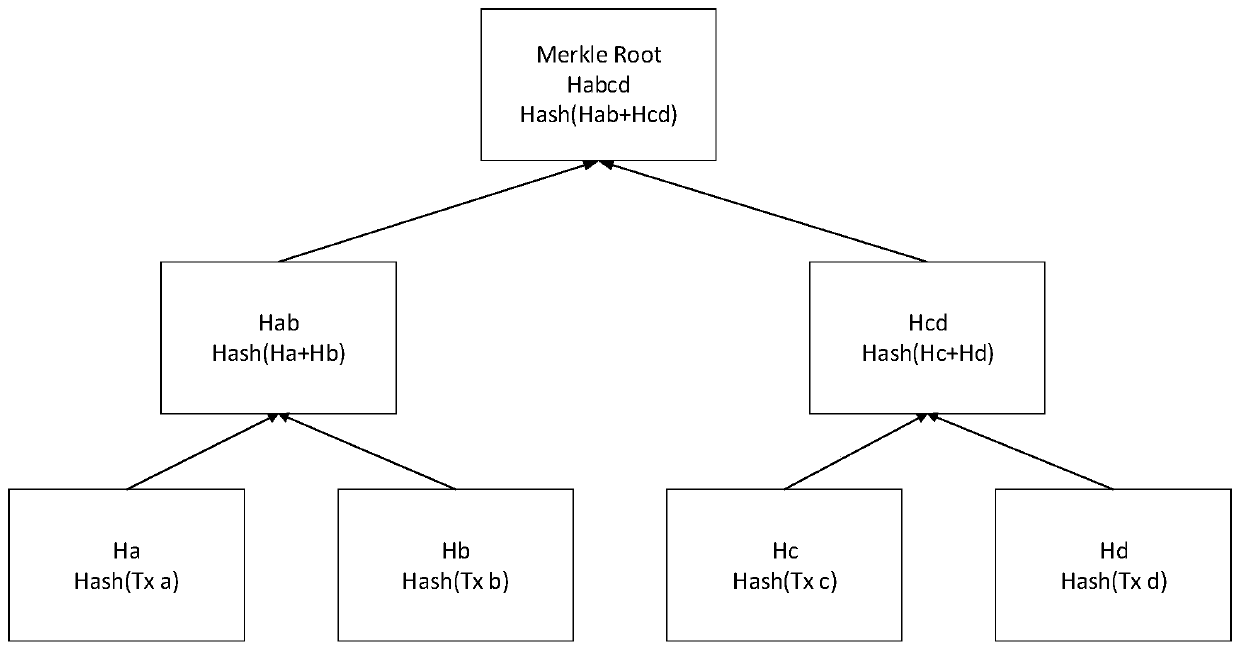
Transaction information verification method and related device
ActiveCN110060064AGuaranteed authenticityEnergy efficient computingProtocol authorisationValidation methodsData acquisition
The invention discloses a transaction information verification method and a related device. The method is applied to the lightweight node, the light node stores a root node of the state tree, whereinthe state tree is used for storing state data of each user account in the block chain network; after receiving a to-be-processed transaction, a transfer-out party account and to-be-verified information corresponding to the transaction are determined, a target state data acquisition request related to the to-be-verified information is initiated to the total node,target state data and Merkle proof for verifying whether the target state data is true or not are obtained; according to the Merkle tree principle, only the root node of the state tree needs to be stored in the light-weight nodes, and when the target state data is verified, whether the target state data is real or not can be verified through the Merkle proof and the stored real root node. Therefore, for a lightweight node serving asan accounting node, the verification of the to-be-verified information can be completed only by storing the root node of the state tree without storing the state data of all the user accounts, and the real reliability of a verification result is ensured.
Owner:SHENZHEN THUNDER NETWORK TECH +1
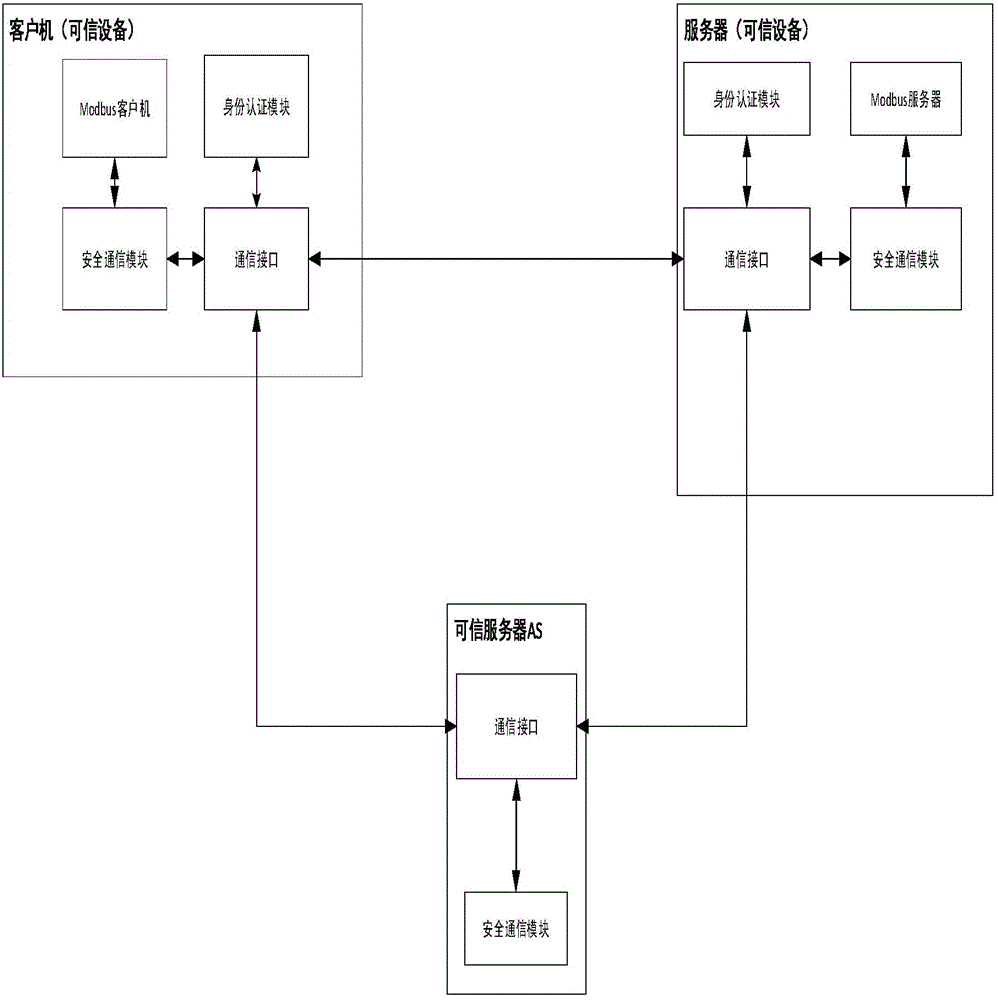
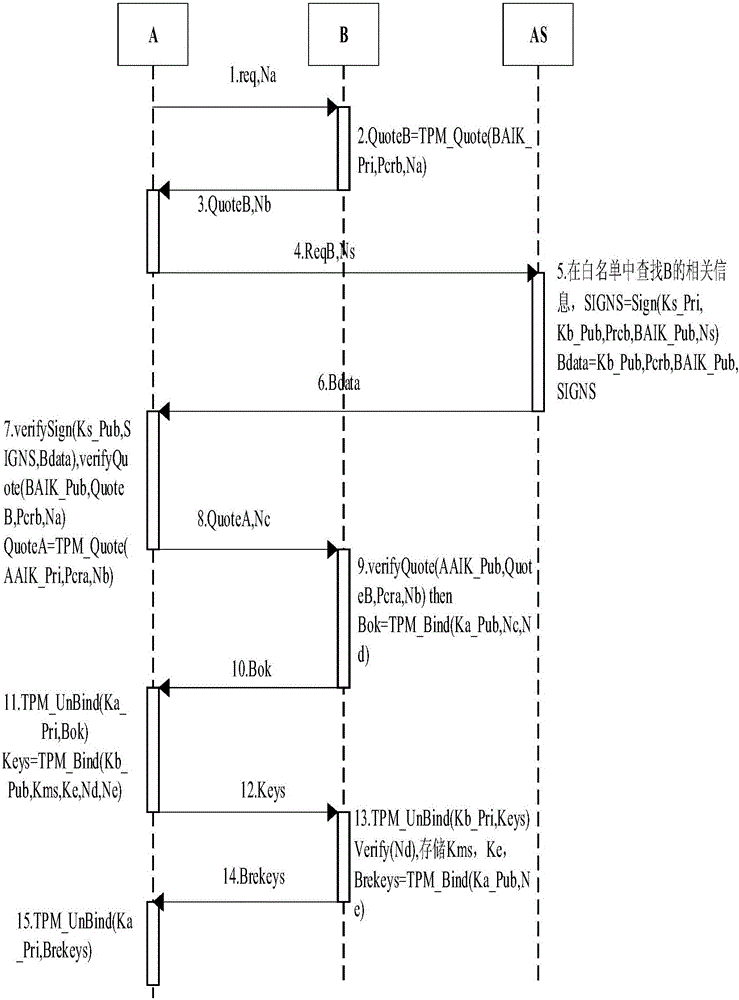
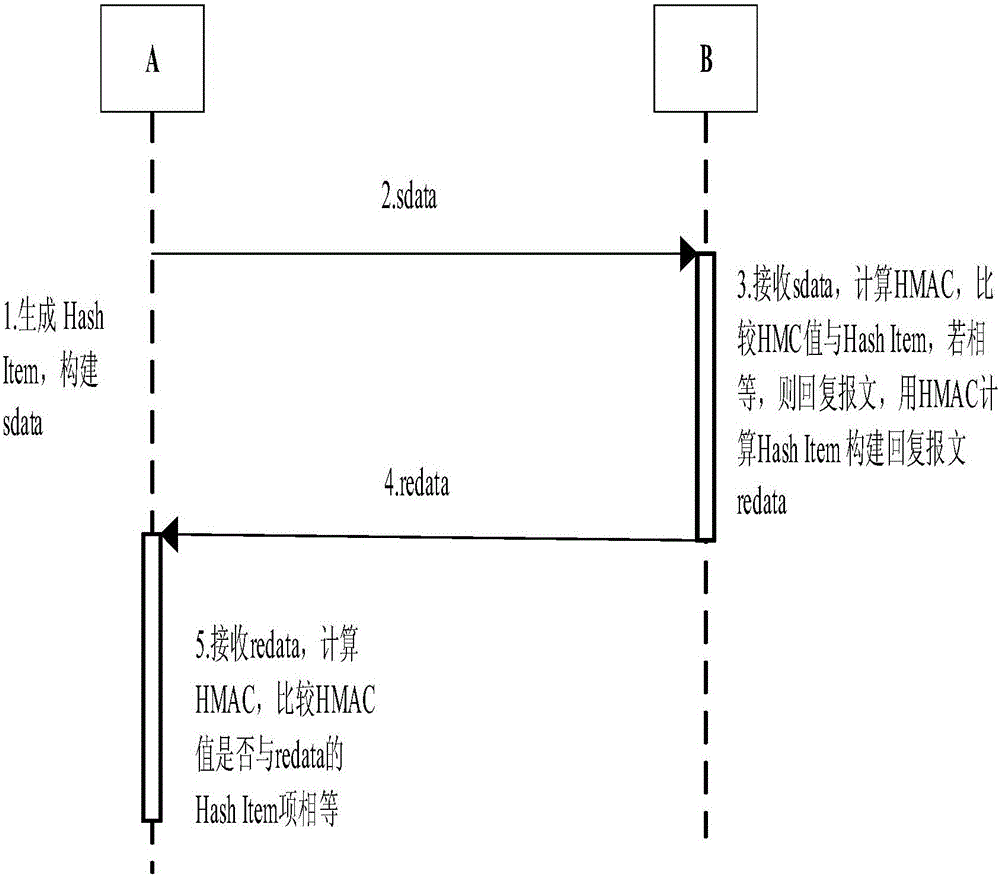
TPM-based Modbus/TCP security enhancement method
ActiveCN105721500AIntegrity guaranteedGuaranteed authenticityMultiple keys/algorithms usagePublic key for secure communicationCommunications securityOperational system
The invention provides a trusted platform module (TPM) based Modbus / TCP security enhancement method, and belongs to the industrial control field and the technical field of information. Security of an industrial control system concerns national security. In the existing security scheme, a problem of communication security certificate is not solved radically, and problems that a server is pseudo and secrete keys are stolen exist. According to the TPM-based Modbus / TCP security enhancement method, the idea of trusted computing is introduced, a TPM is added in a device, an identity authentication key of the TPM ensures that the identity of the device is trusted, and measurement information of an operating system and configuration software of the device ensures that the state of the device is trusted. With the participation of a trusted server, identity and state authentication of double parties is completed. Hash Item is added in a protocol format, so that the completeness of a message is ensured. TPM bound keys and authentication data PCR ensure the security of a key Kms in a generation process, and HMAC and the key Kms ensure the identity authentication of the double parties in a communication process.
Owner:BEIJING UNIV OF TECH
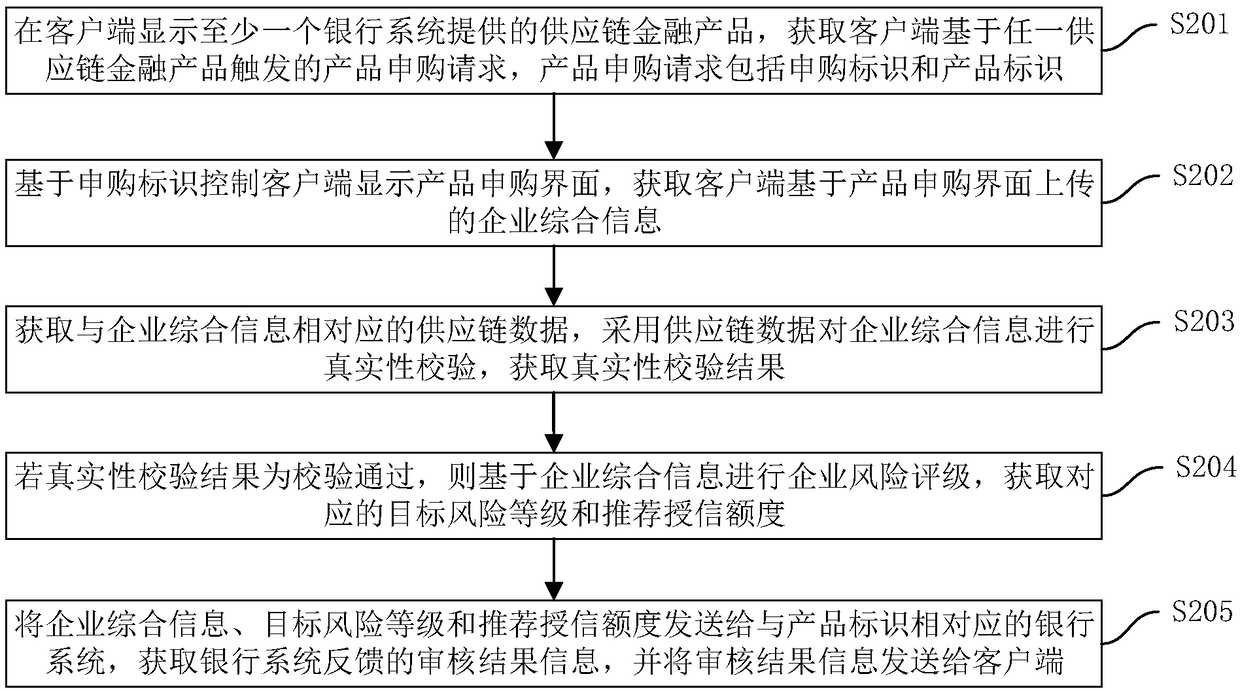
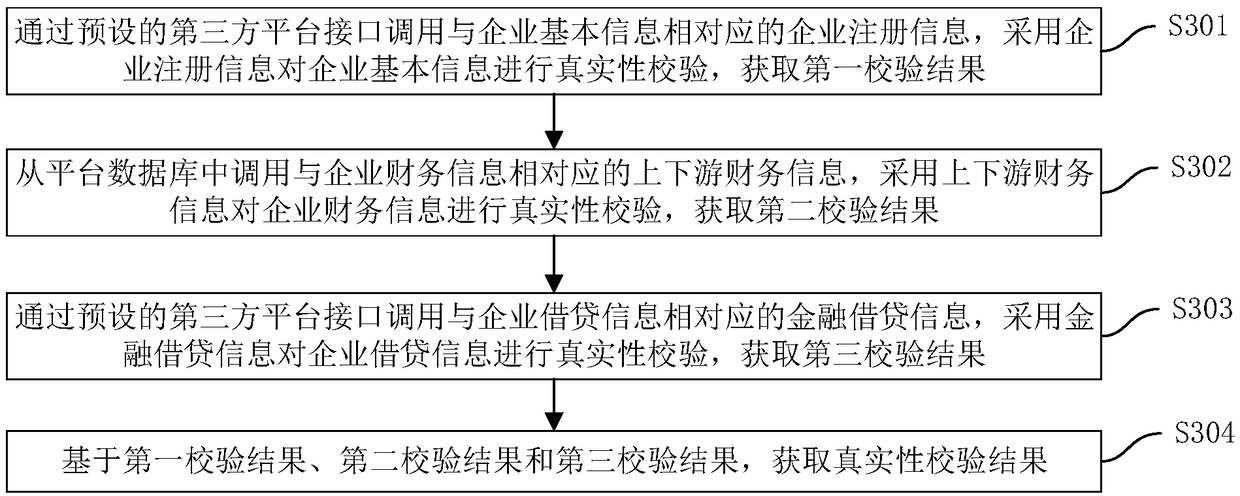
Supply chain financial service processing method, device, computer device and storage medium
The invention discloses a supply chain financial service processing method, a device, a computer device and a storage medium. The method comprises the following steps: displaying at least one supply chain financial product provided by a banking system on a client end, and obtaining a product purchase request triggered by the client end based on any supply chain financial product; Obtaining the comprehensive enterprise information uploaded by the client based on the product requisition interface; Acquiring the supply chain data corresponding to the comprehensive information of the enterprise, verifying the authenticity of the comprehensive information of the enterprise by using the supply chain data, and obtaining the authenticity verification results; If the authenticity verification result is passed, carrying out the enterprise risk rating based on the comprehensive information of the enterprise, and the target risk grade and the recommended credit line are obtained. The comprehensive information of the enterprise, the target risk grade and the recommended credit line are sent to the corresponding bank system of the product identification, and the review result information fed back by the bank system is sent to the client. This method can realize the information integration and enterprise qualification examination of supply chain financial products.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
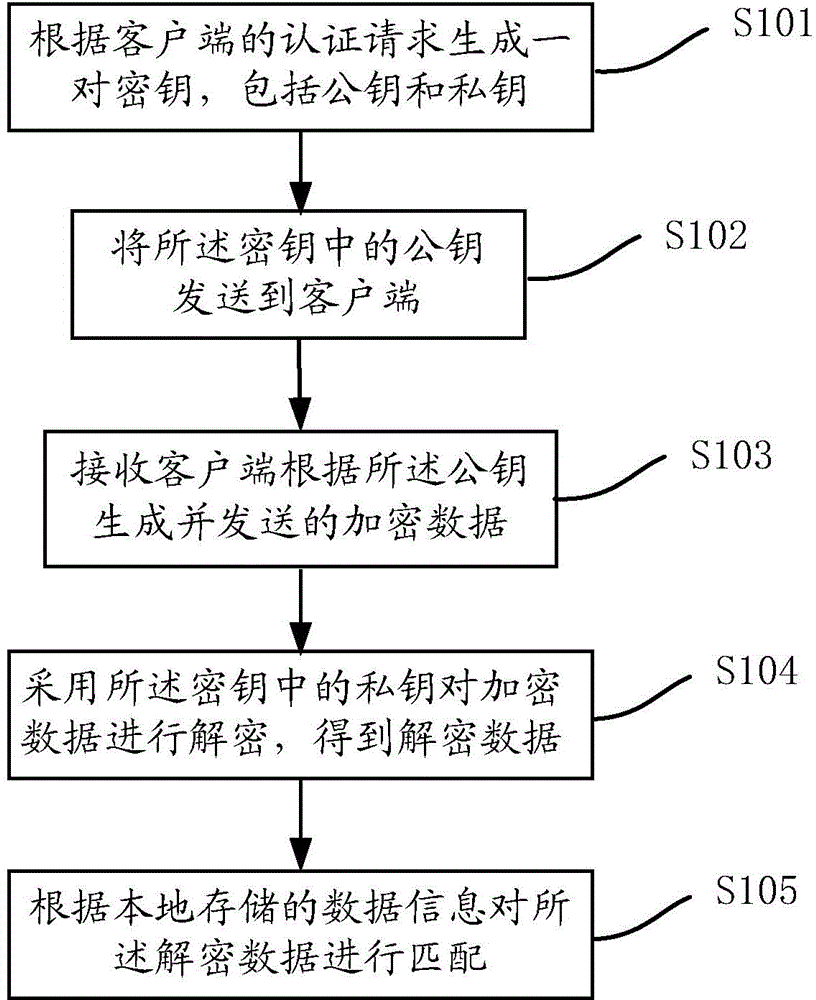
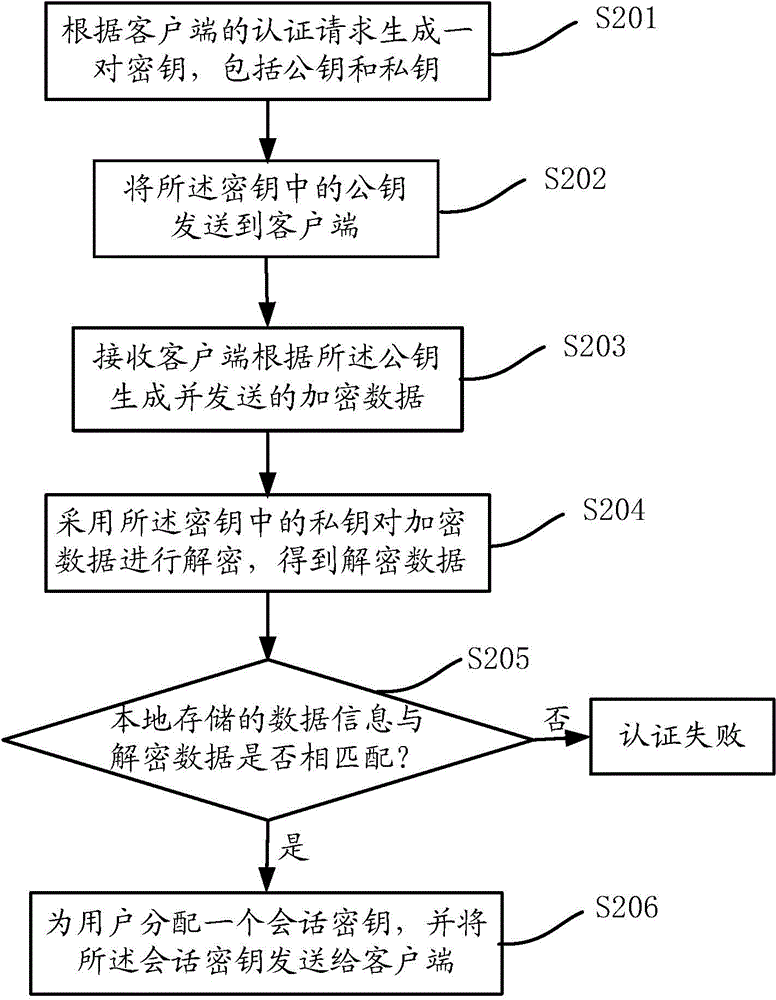
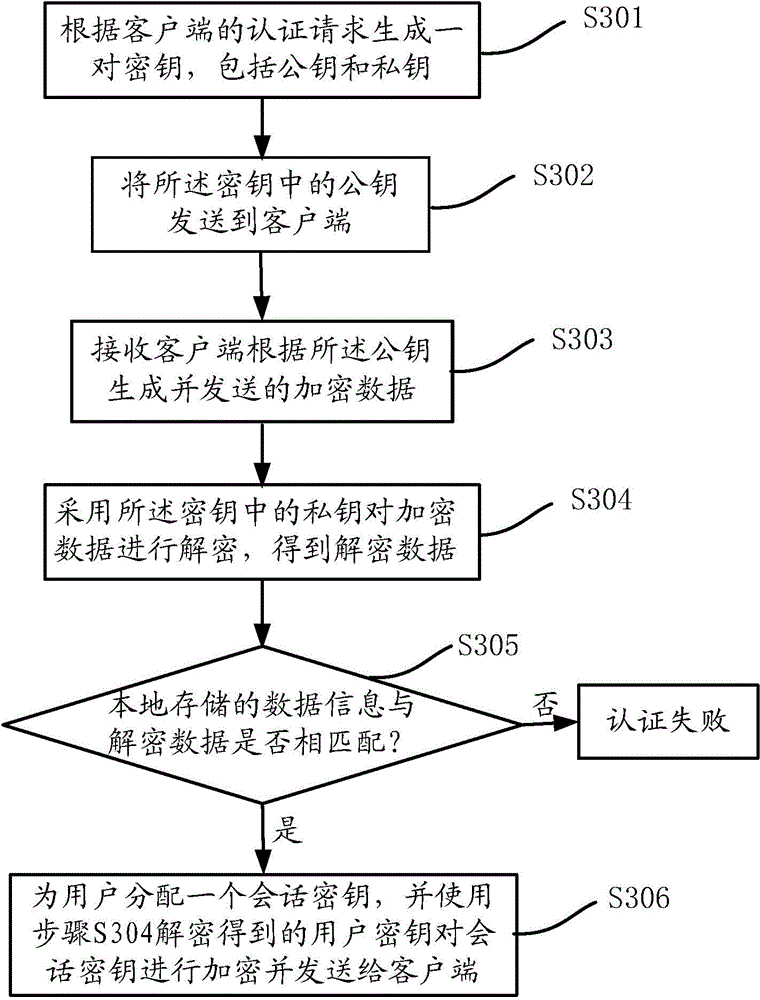
Fingerprint authentication method and system
InactiveCN105207776AEnsure safetyGuaranteed authenticityUser identity/authority verificationDigital data authenticationData informationFingerprint
The present invention discloses a fingerprint authentication method and a system. The method comprises an authentication step of generating a pair of keys according to the authentication request of a client, wherein the keys comprise a public key and a private key, a sending step of sending the public key to the client, a receiving step of receiving the encrypted data which is generated and sent by the client according to the public key, a decryption step of using the private key to decrypt the encrypted data to obtain decrypted data, and a matching step of matching the locally stored data information and the decrypted data. According to the fingerprint authentication method and the system, the stealing or interpolating of user data in a network transmission process can be prevented, and the safety and reliability of the user data in system certification are ensured.
Owner:CHINA STANDARD SOFTWARE
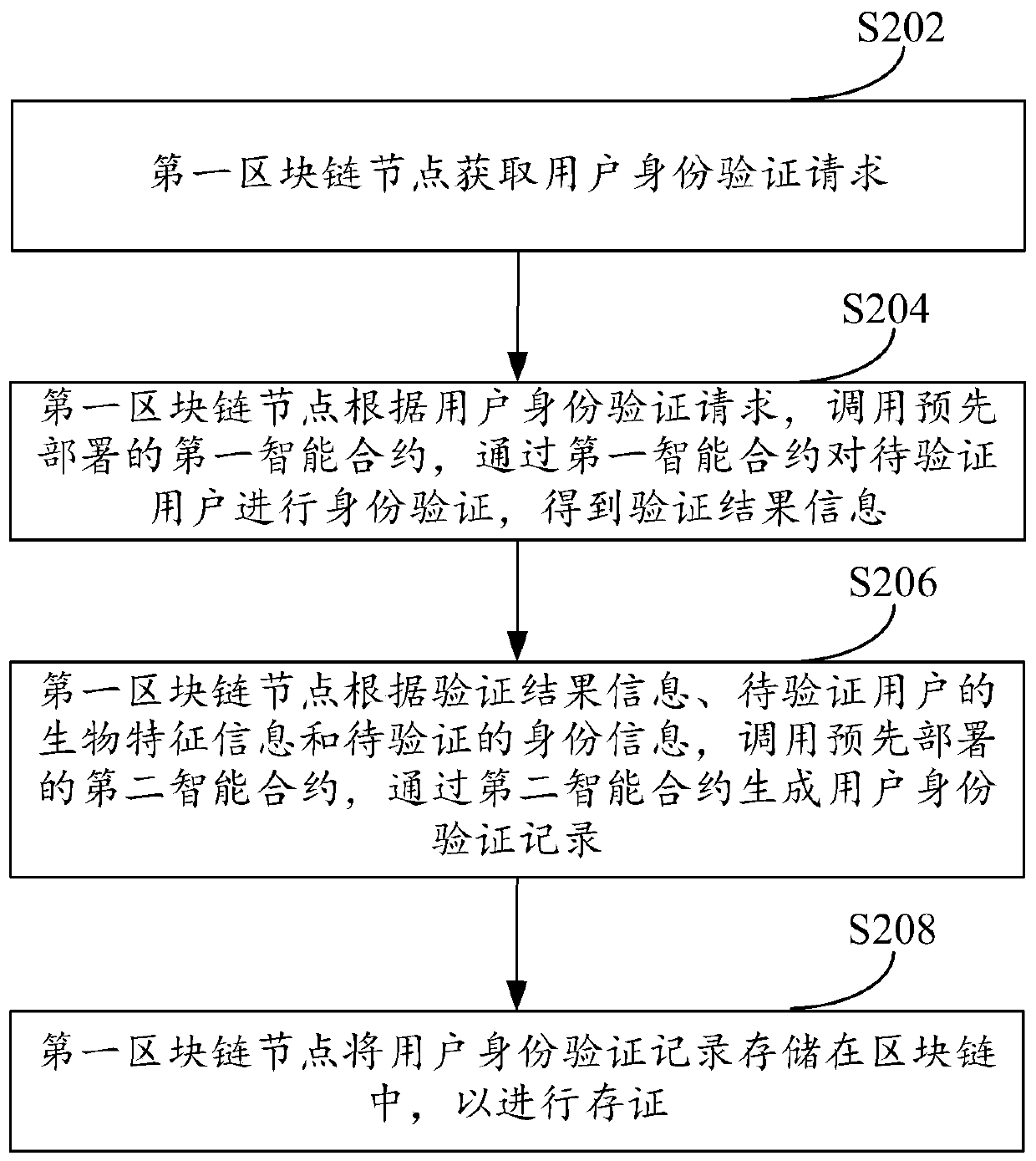
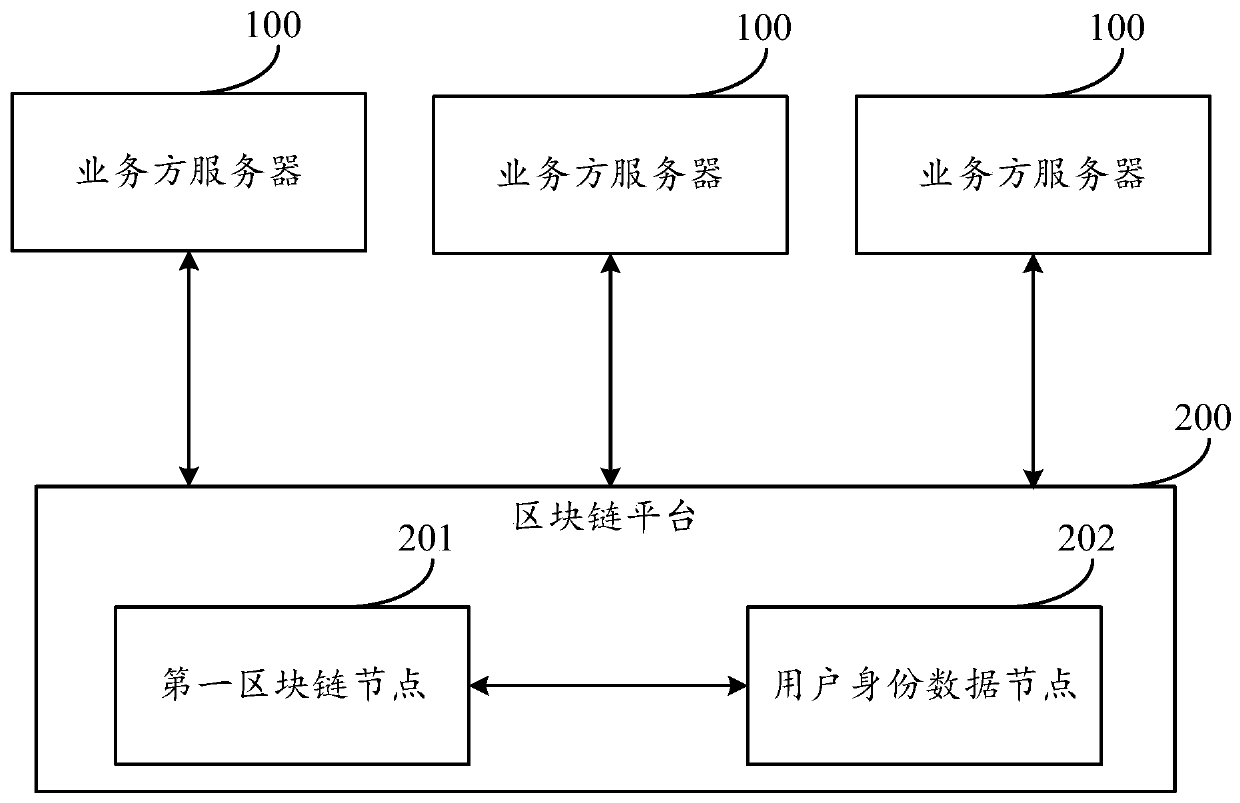
Identity verification method, device and equipment based on block chain
ActiveCN110555296AGuaranteed authenticityDigital data protectionDigital data authenticationUser authenticationSmart contract
The embodiment of the invention provides an identity authentication method, device and equipment based on a block chain, and the method comprises the steps that a first block chain node obtains a useridentity authentication request which comprises the biological feature information of a to-be-authenticated user and the to-be-authenticated identity information; the first blockchain node performs identity verification on the to-be-verified user through the first smart contract according to the user identity verification request to obtain verification result information; the first block chain node generates a user identity verification record through a second smart contract according to the verification result information, the biological characteristic information of the to-be-verified userand the to-be-verified identity information; and the first block chain node stores the user identity verification record in a block chain for evidence storage. According to the embodiment of the invention, the related information involved in the identity verification process can be stored in the block chain, and the true validity of the stored information is ensured based on the characteristic that the information in the block chain cannot be tampered.
Owner:ADVANCED NEW TECH CO LTD
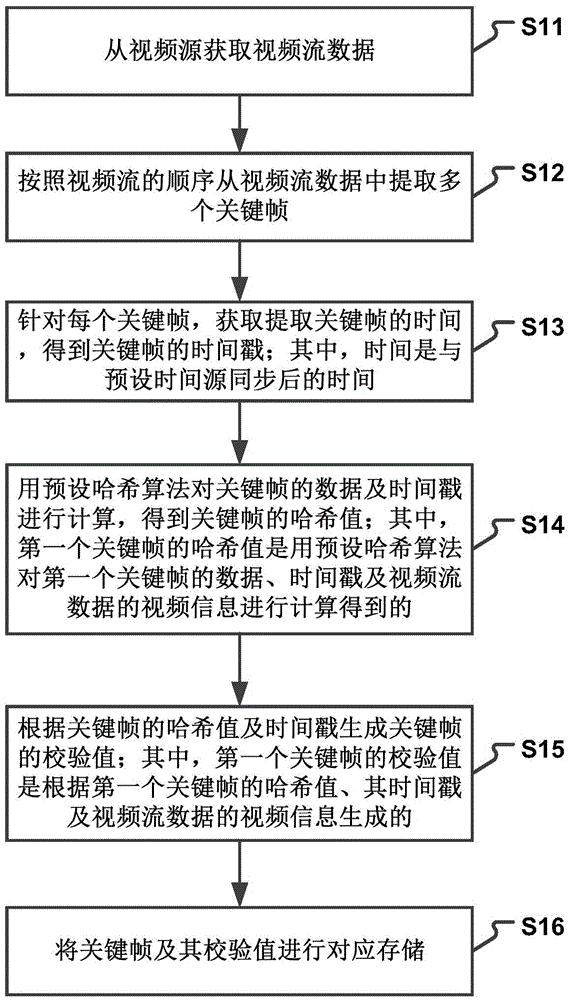
Video evidence preserving and verifying method and device
InactiveCN105611428AGuaranteed relevancePreservation is accurate and reliableSelective content distributionComputer hardwareHash table
The invention discloses a video evidence preserving and verifying method and device. The method comprises the following steps of obtaining video stream data from a video source; obtaining multiple key frames from the video stream data according to a sequence of video streams; for each key frame, obtaining the time for extracting the key frame, thus obtaining the time stamps of the key frames, wherein the time is time synchronized with a preset time source; calculating the data and the time stamps of the key frames through a preset hash algorithm, thus obtaining the hash values of the key frames, wherein the hash value of a first key frame is obtained by calculating the data and the time stamp of the first key frame and the video information of the video stream data through the preset hash algorithm; generating the verifying values of the key frames according to the hash values and the time stamps of the key frames, wherein the verifying value of the first key frame is generated according to the hash value and the time stamp of the first key frame and the video information of the video stream data; and correspondingly storing the key frames and the verifying values of the key frames.
Owner:BEIJING ANXUN NETWORK TECH CO LTD
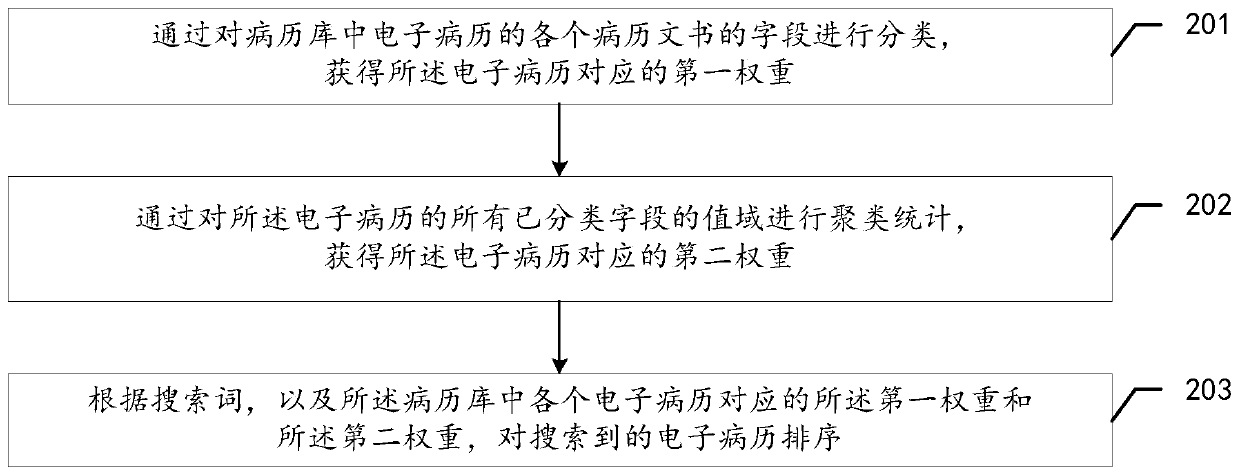
Medical record search result sorting method and related device
ActiveCN109753516AGuaranteed authenticityMeet prioritySemi-structured data retrievalSpecial data processing applicationsMedical recordDocument preparation
The invention discloses a medical record search result sorting method and a related device. The method comprises: fields of all medical record documents of electronic medical records in a medical record library are classified, and first weights corresponding to the electronic medical records are obtained; performing clustering statistics on the value domains of all classified fields of the electronic medical record to obtain a second weight corresponding to the electronic medical record; and finally, sorting the searched electronic medical records according to the search term and the first weight and the second weight corresponding to each electronic medical record in the medical record library. The method can be used based on an existing medical electronic medical record model, and therefore field classification in medical record documents can be conveniently, rapidly and efficiently achieved. In addition, the method is suitable for being combined with an existing correlation sortingalgorithm, the importance degree and the correlation degree of the electronic medical records are considered in the sorting process, the electronic medical records more conforming to the search wordsare arranged preferentially, and therefore the user satisfaction degree is improved, and the efficiency of the user for obtaining the electronic medical records expected by the user is improved.
Owner:北京嘉和海森健康科技有限公司
Storage capacity predication method and storage capacity predication system
InactiveCN103903069AAccurate predictionImprove resource utilizationForecastingFailure rateSystems management
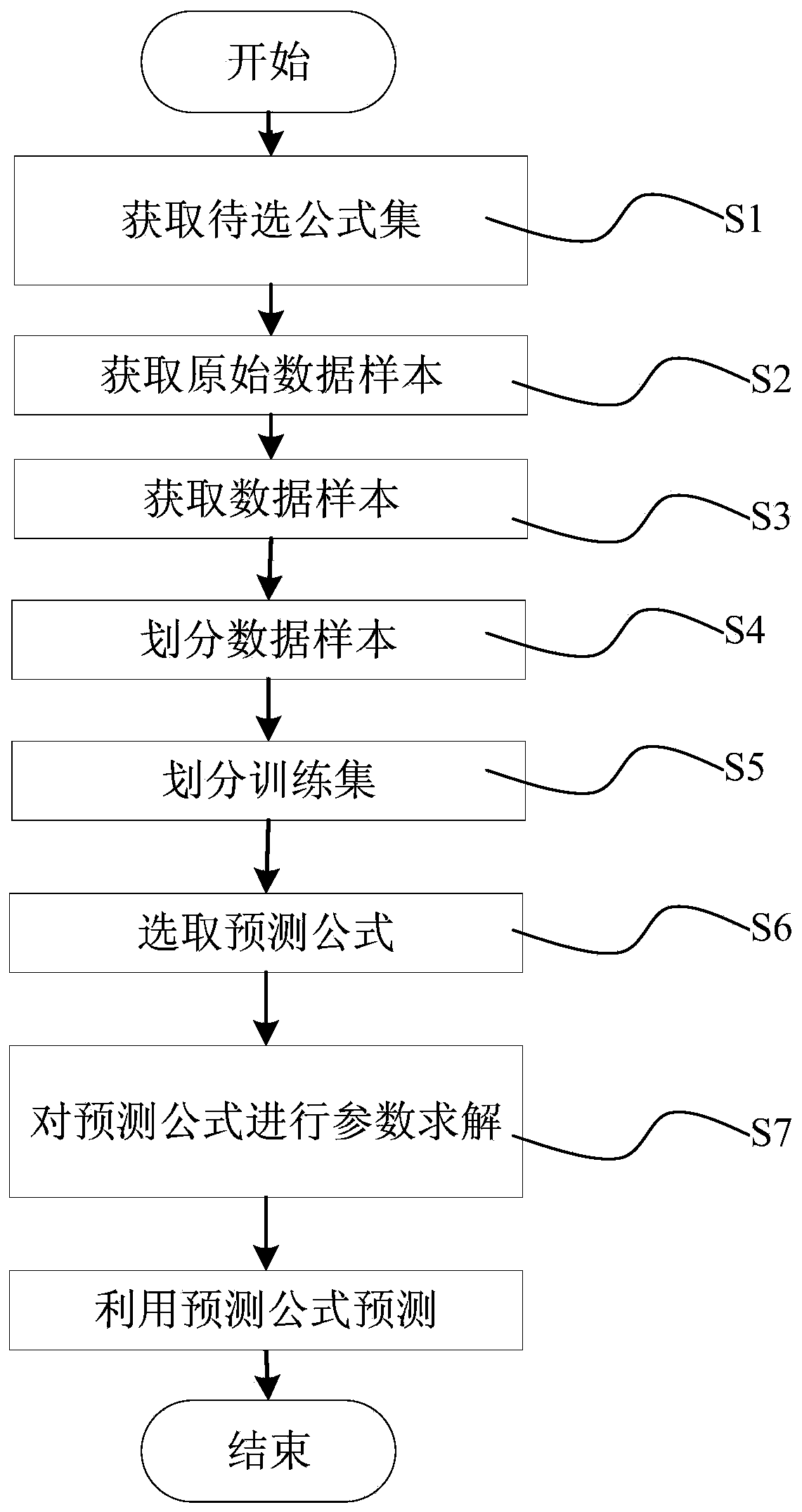
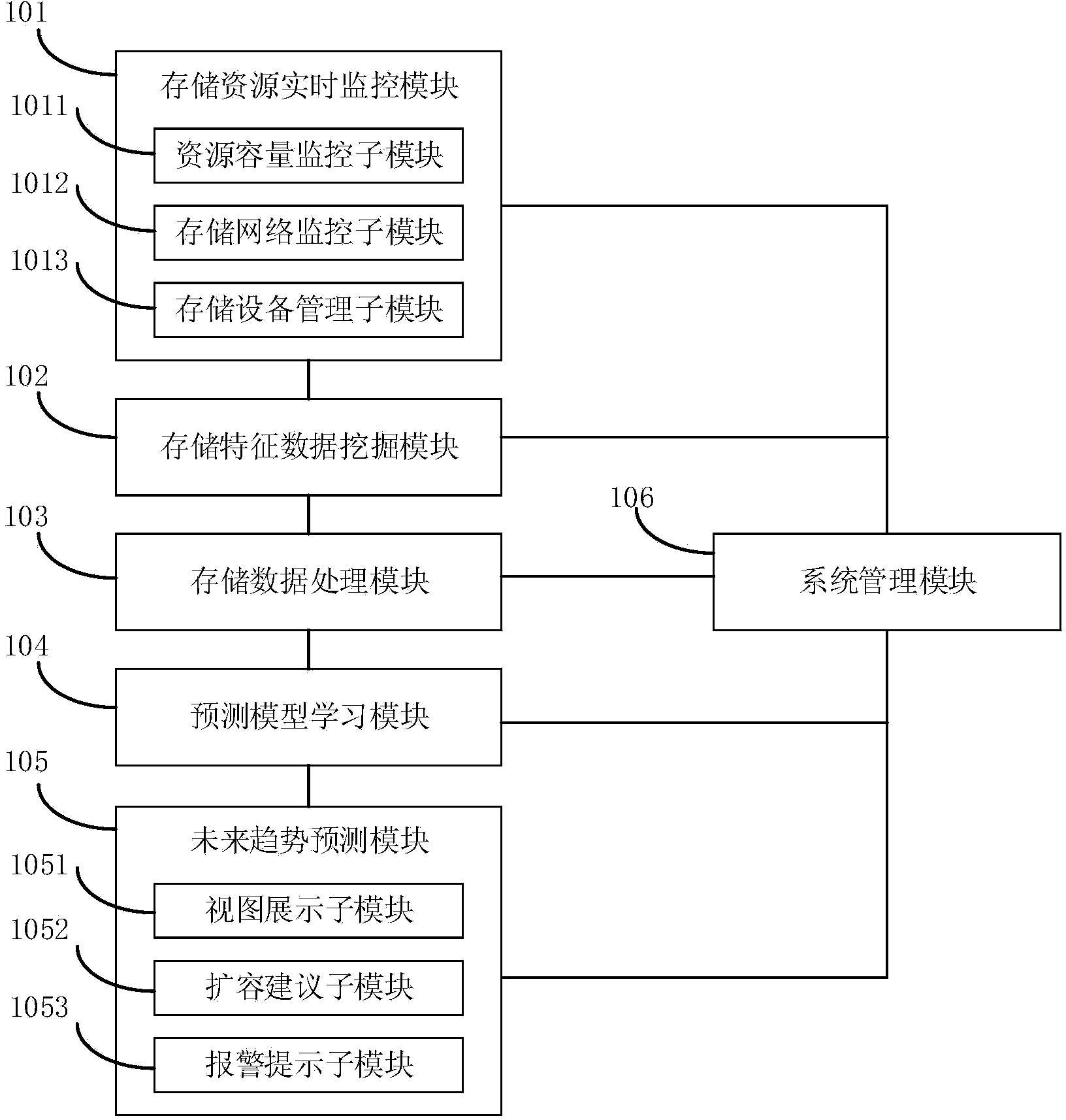
The invention relates to a storage capacity predication method which comprises the following steps that S1, a formulary to be selected is acquired; S2, an original data sample is acquired; S3, a data sample is acquired; S4, the data sample is divided; S5, a training set is divided; S6, a predictor formula is selected; S7, parameter solving is carried out on the predictor formula; S8, predication is carried out through the predictor formula. The invention further discloses a storage capacity predication system which comprises a system management module, a storage resource real-time monitoring module, a storage data processing module, a predication model study module and a future trend predication module. According to the technical scheme, the storage capacity of IT resources can be accurately predicated, and therefore the resource utilization rate is improved, the failure rate is reduced, and operation and maintenance quality is improved.
Owner:GUANGDONG POWER GRID CO LTD INFORMATION CENT +1
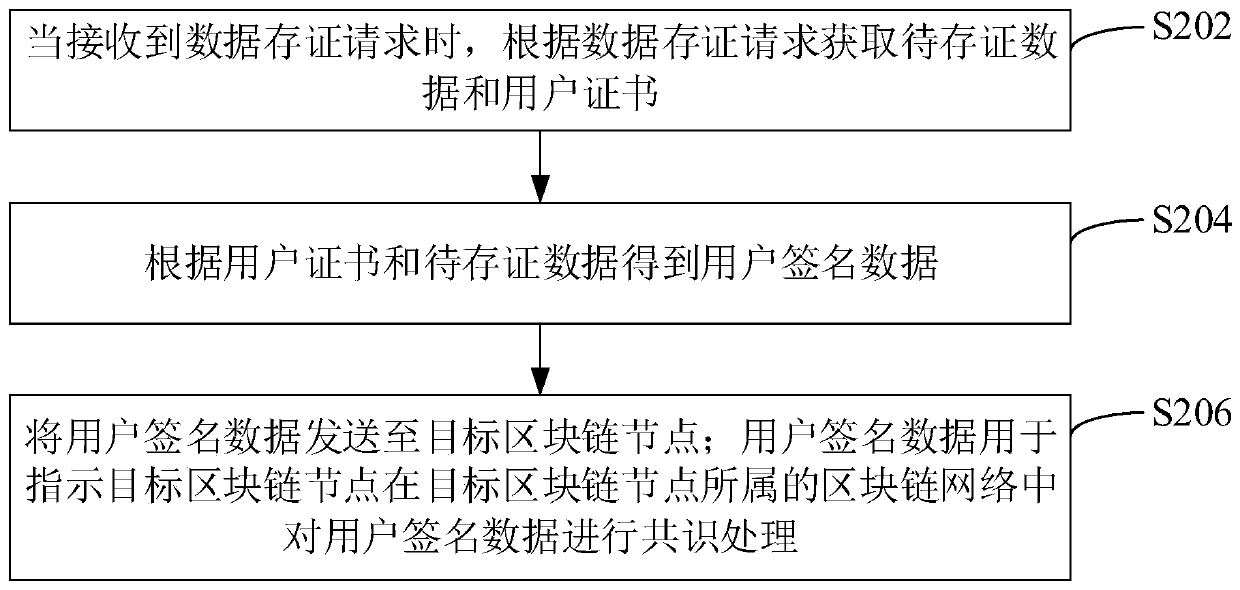
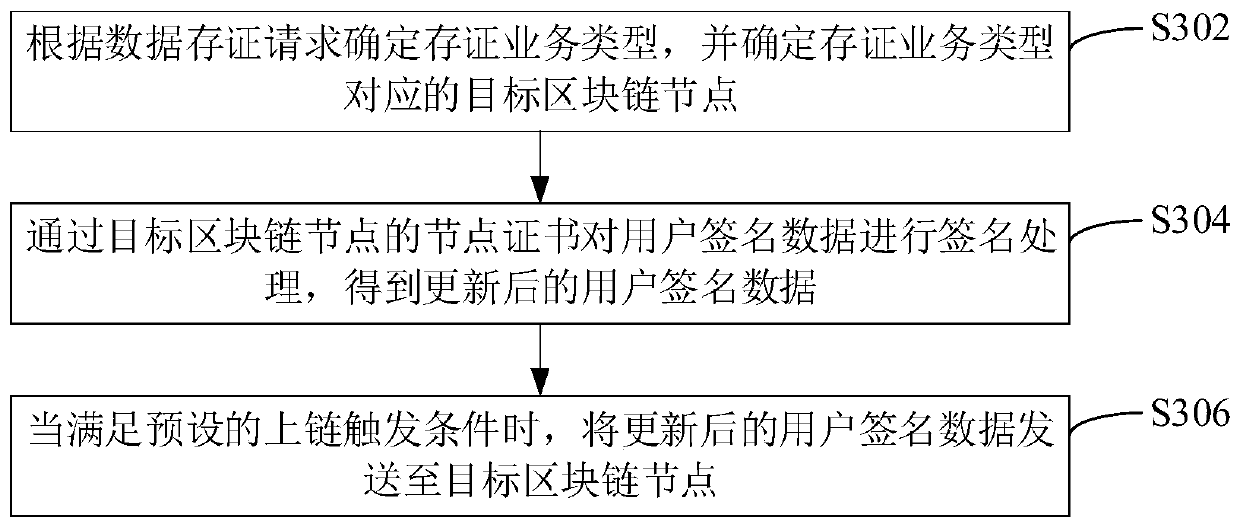
Data evidence storage method and device, computer equipment and storage medium
ActiveCN111010367AGuaranteed authenticityUser identity/authority verificationDigital data protectionEngineeringDatabase
The invention relates to a data evidence storage method and device, computer equipment and a storage medium. The method comprises the steps: obtaining to-be-stored data and a user certificate according to a data storage request when the data storage request is received; obtaining user signature data according to the user certificate and the to-be-stored data; sending the user signature data to a target blockchain node, wherein the user signature data is used for indicating the target blockchain node to perform consensus processing on the user signature data in a blockchain network to which thetarget blockchain node belongs. By adopting the method, the true reliability of the evidence storage data can be ensured.
Owner:深圳市电子商务安全证书管理有限公司 +1
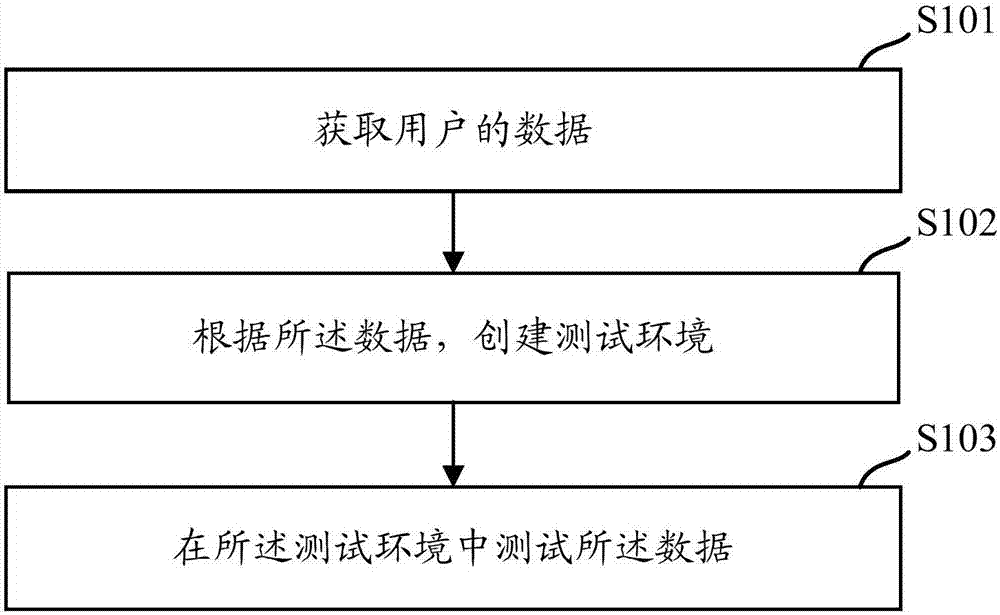
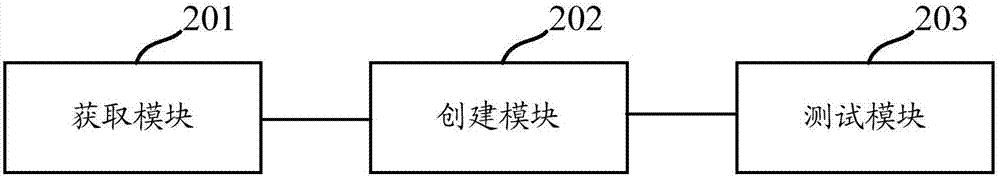
Testing method and device
Owner:ADVANCED NEW TECH CO LTD
Method for fixing and saving evidence of computer crime and device therefor
InactiveCN101017563AGuaranteed legalityGuaranteed relevanceData processing applicationsDigital data authenticationBIOSComputer science
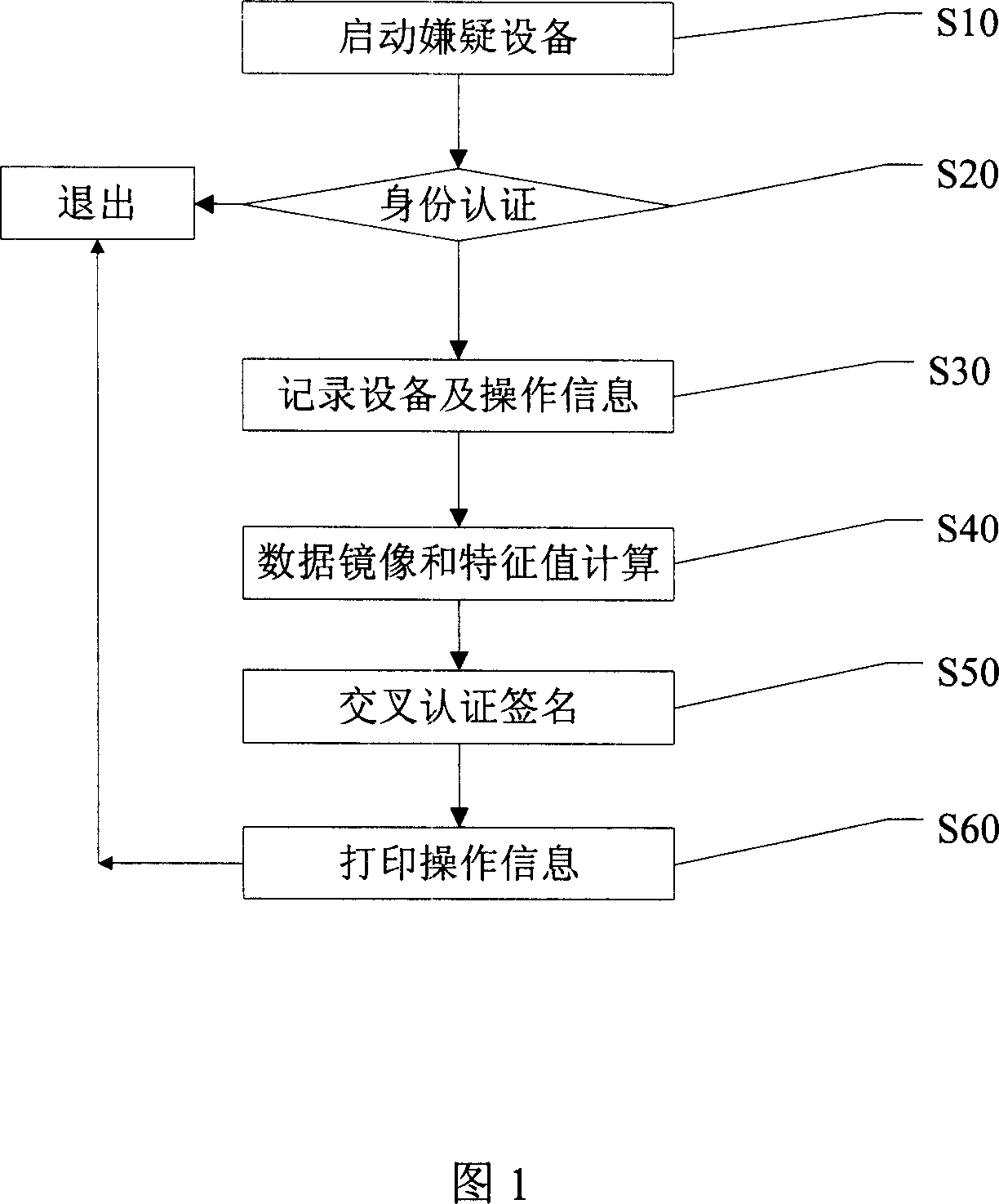
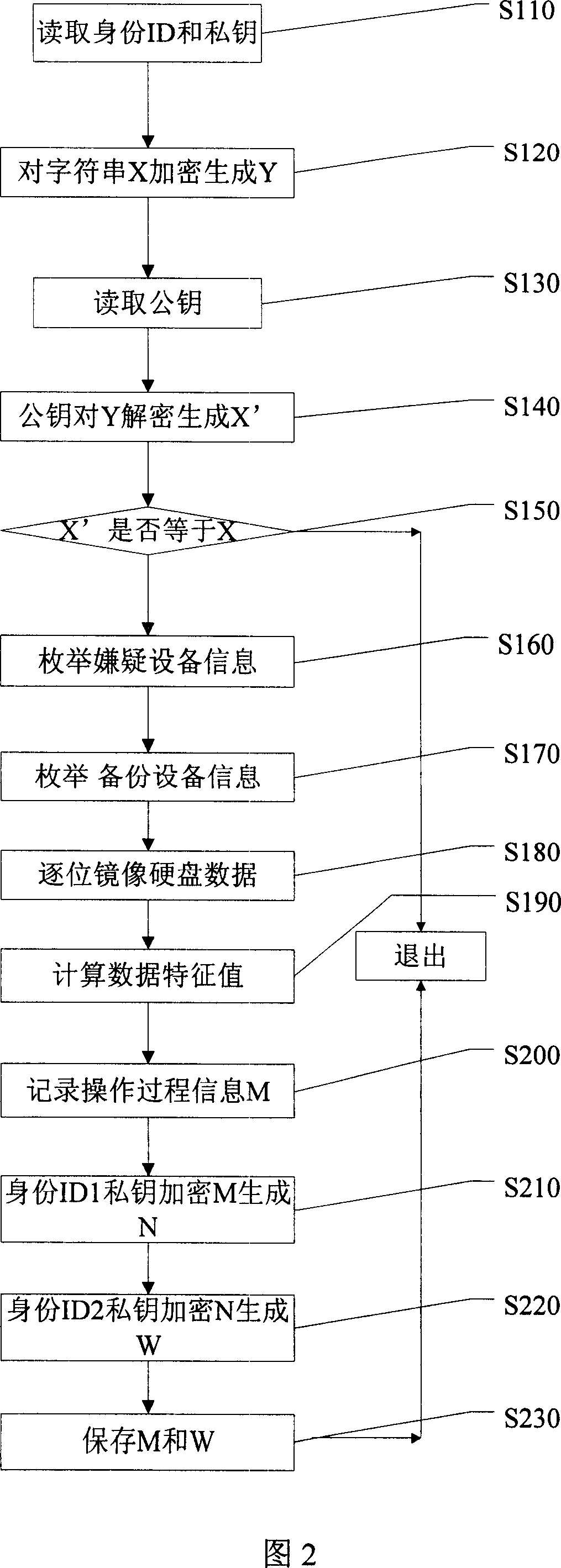
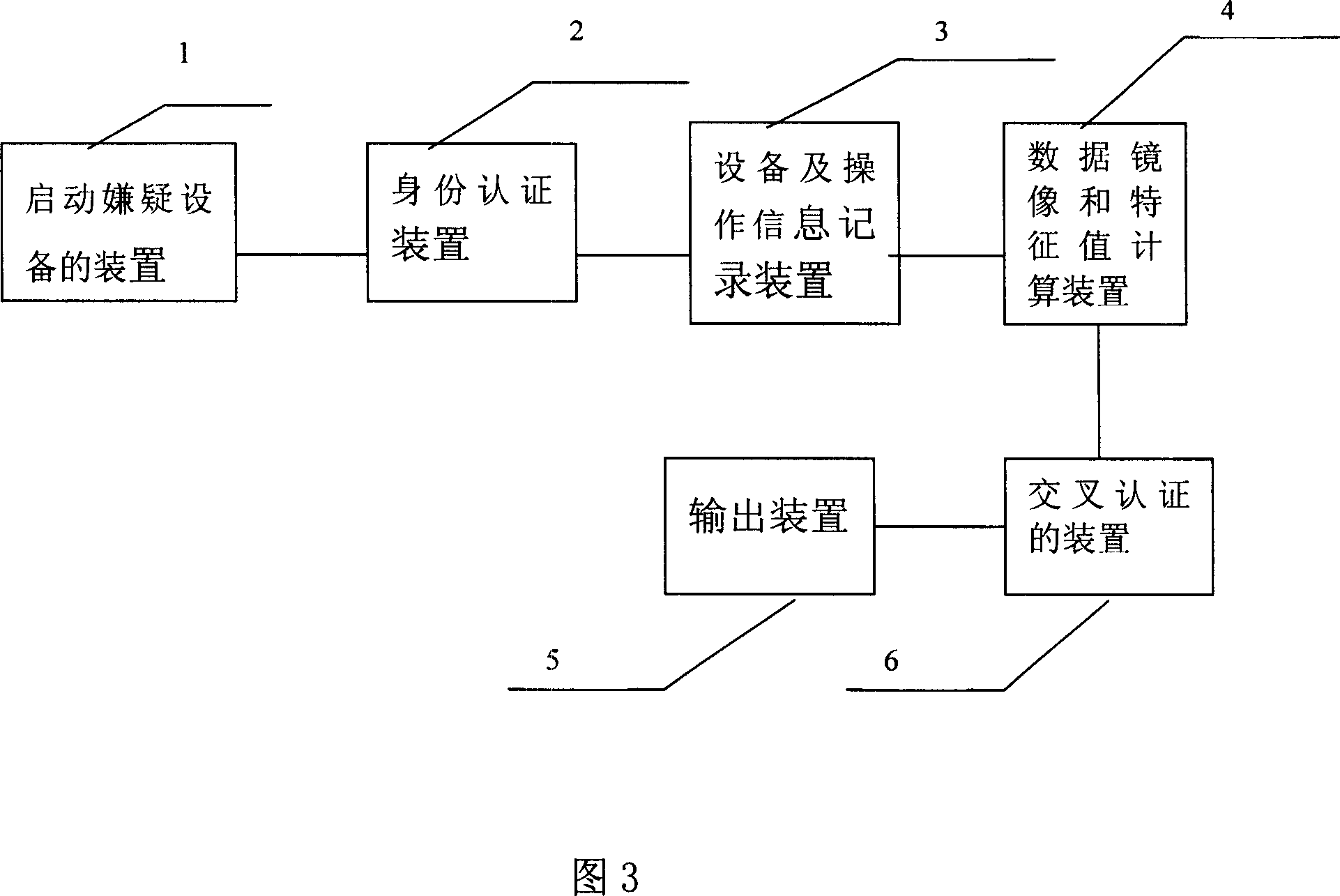
This invention provides one computer criminal evidence fix and ensuring method, which comprises the following steps: starting suspect devices to modify the suspect Bios set to primordially start the supportive disc; identification step to identify the person for electron evidence; recording device and operating information for evidence person, operation time and evidence medium; data images and property computing for property on the magnetic disc static memory medium for total images; crossly identifying according to fix result and process legality contract to ensure more than two legality evidence person on spot; printing the operation information and signature for final determination to fulfill electron signature and paper signature.
Owner:PEKING UNIV
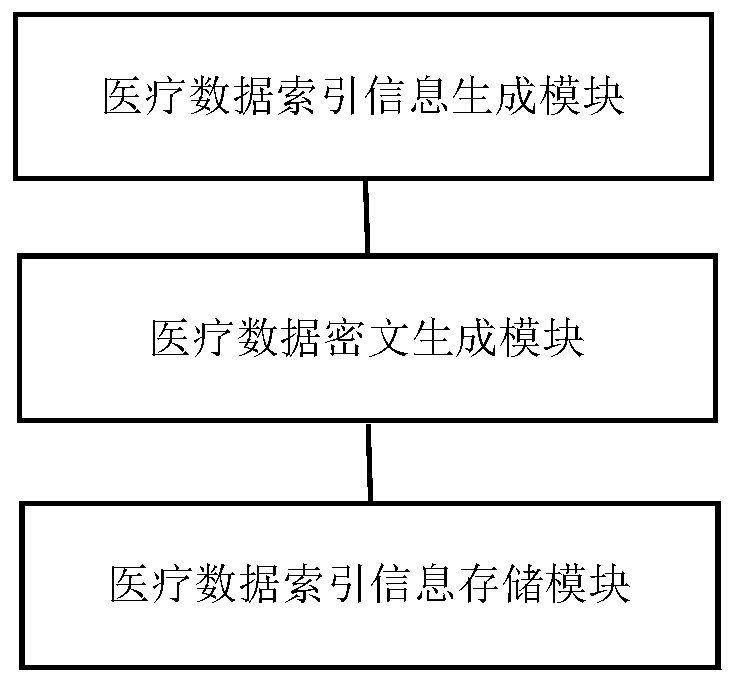
Medical data sharing method and device based on blockchain technology, electronic equipment and storage medium
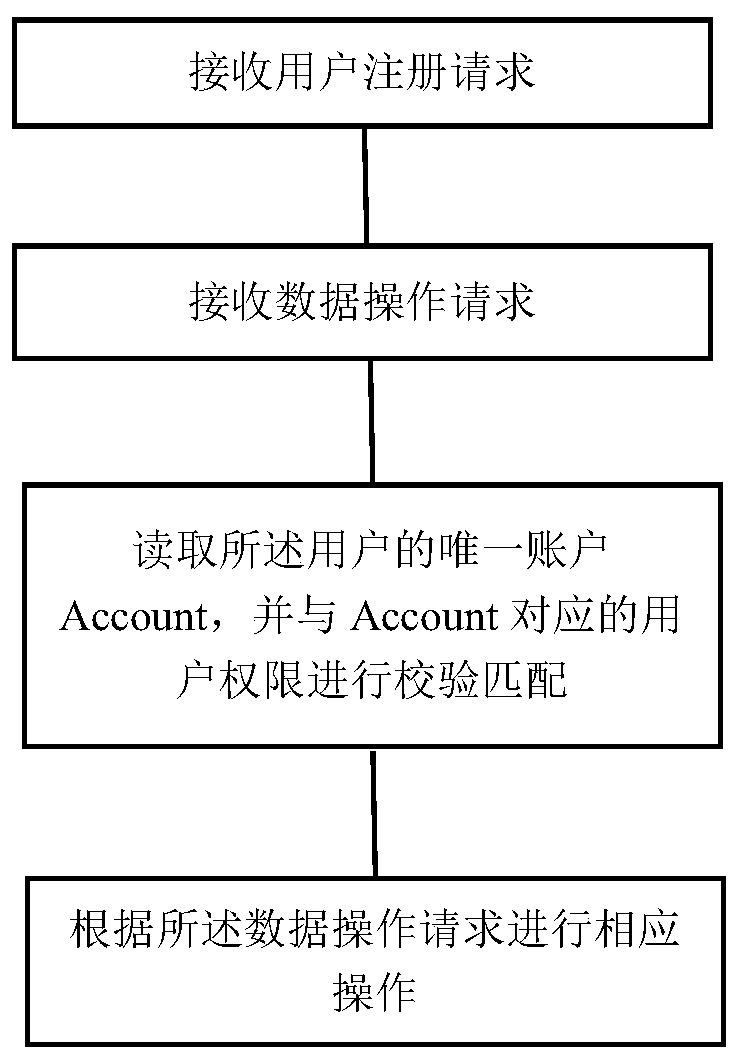
ActiveCN111261250AEnsure consistencyEnsure safetyMedical communicationInstrumentsThird partyUser Privilege
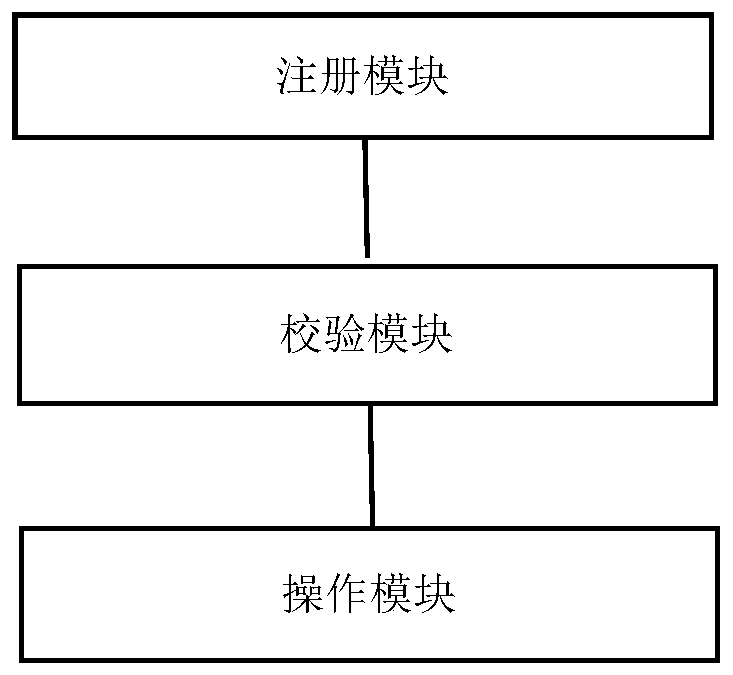
The invention discloses a medical data sharing method and device based on a block chain technology, electronic equipment and a storage medium. The method is applied to a medical alliance chain systemand comprises the steps: S1, receiving a user registration request, allocating a unique account Account (a user ID, a user type and user permission) to a user, generating a secret key K {k1, k2} for the user, k1 being a public key of the user in the medical alliance chain system, and k2 being a private key of the user; s2, receiving a data operation request; s3, reading the unique account Accountof the user according to the operation request, and performing verification matching with the user permission corresponding to the Account; and s4, after verification is passed, performing corresponding operation according to the data operation request, and sending, by the access node, the public key to a blockchain node. By means of the blockchain technology, a doctor is the only user capable ofmodifying the medical data content, the real reliability of data on the alliance blockchain is guaranteed, and the consistency of shared data is guaranteed; a patient has the authority of acquiring medical data and setting privacy, so that the safety of privacy information of the patient is ensured, and various problems caused by privacy leakage are avoided; and after the third-party institution passes the alliance authentication, the reliable medical data can be conveniently obtained, and the convenience is greatly improved.
Owner:JIANGSU HENGBAO INTELLIGENT SYST TECH CO LTD
Strength and rigidity testing fixture for aircraft draw bar and use method of strength and rigidity testing fixture
ActiveCN104865123AQuick installationGuaranteed authenticityStrength propertiesTest efficiencyHigh load
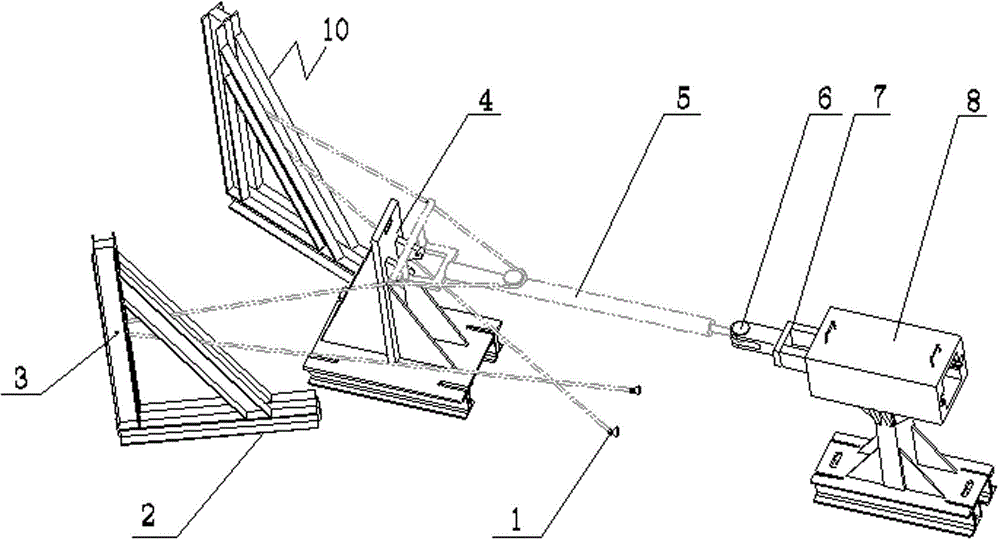
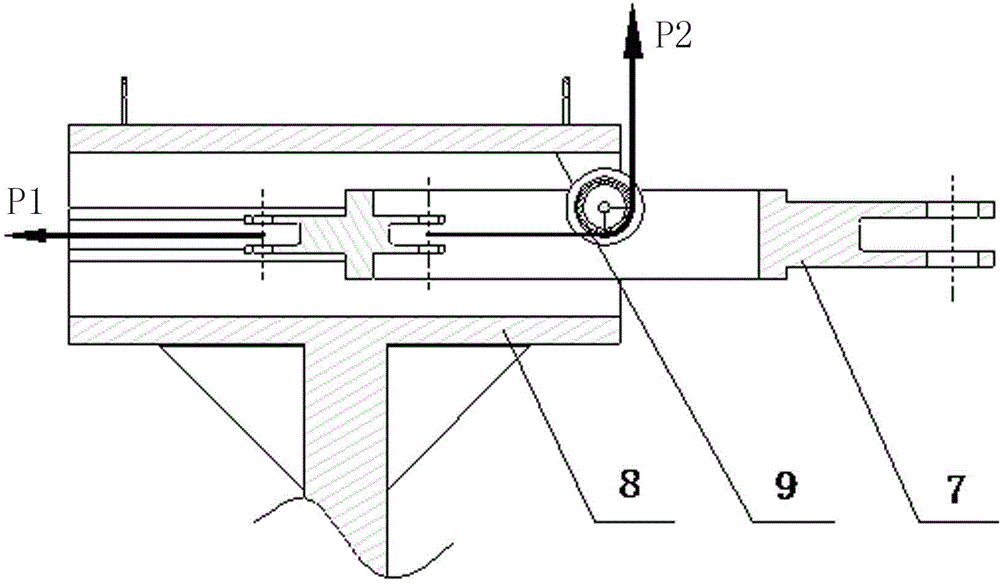
The invention relates to a strength and rigidity testing fixture for an aircraft draw bar. A front-end towing ring of a test piece is connected with one end of a main loading mechanism through a connecting pin, the main loading mechanism can slide freely in a guide rail of a slideway mechanism through a bearing per se, a fixed pulley I is arranged at the end part of the cavity of the slideway mechanism, two loading connectors in two directions are arranged at the other end of the main loading mechanism in the slideway mechanism and respectively connected two steel wire ropes, a rear-end connector of the test piece is connected with a simulative front undercarriage fixture, the steel wire ropes of the test piece bypass fixed pulleys II of load-bearing upright posts to be connected with a simulative main undercarriage fixture, and connectors adopting lug sheet forms at the tail end of the steel cable ropes can be directly connected with conventional fasteners. The testing fixture realize that the connecting mode and the strained condition of the test piece are consistent with the use state, the compression loading does not generate a lateral component force under the high-loaded condition, the occupied space is small, and the manufacturing cost is low. The test method is safe and reliable, the measured data are true and effective and the test efficiency is greatly improved.
Owner:SHENYANG AIRCRAFT CORP
Encrypted keyword search-based bidirectional anonymity trusted network debit and credit system and method
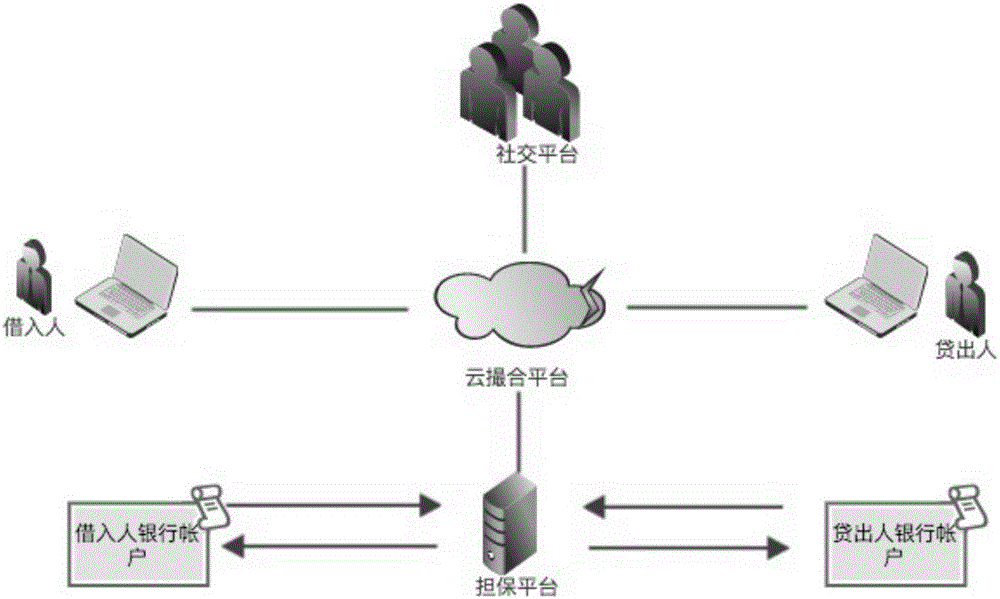
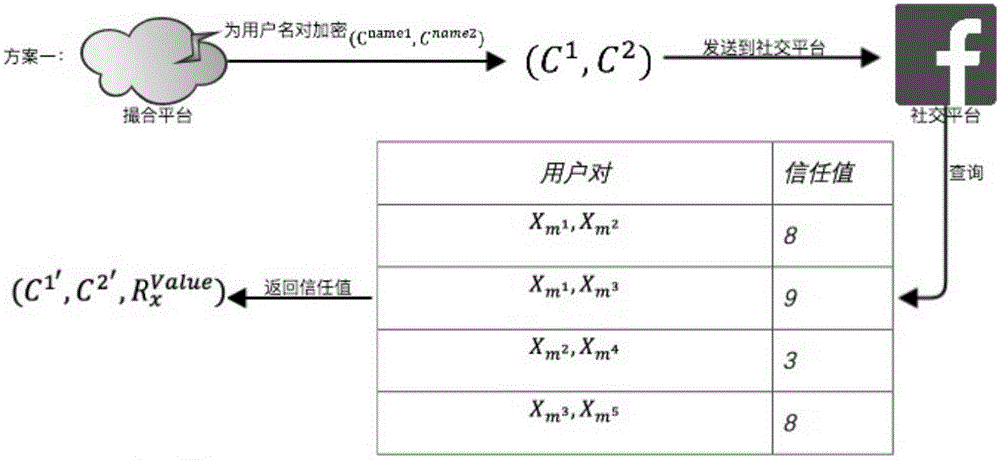
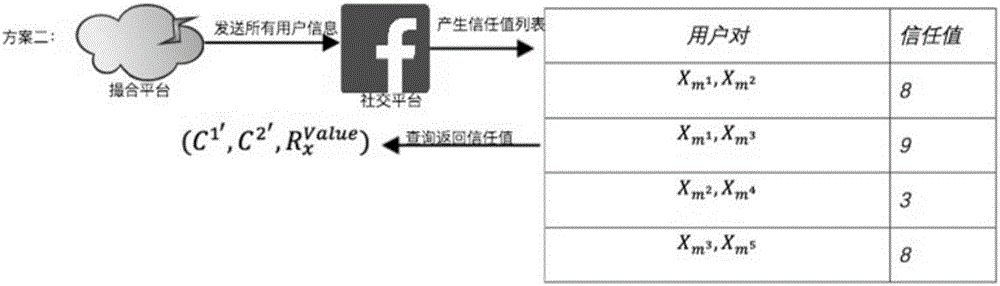
InactiveCN105825427AImprove security and privacyGuaranteed authenticityFinanceSocial platformAnonymity
The present invention discloses an encrypted keyword search-based bidirectional anonymity trusted network debit and credit system and method. The system is composed of a cloud matching platform and is communicated with a social platform and a guarantee platform to operate, the cloud matching platform matches a debit side and a credit side and analyzes the credit capability of the debit side, the guarantee platform is used to guarantee a financial transaction process, and the social platform is used to communicate with the cloud matching platform to obtain the acquaintance information data. The debit side is the initiator of a debit request, and the credit side is the provider of the credit fund. In the encrypted keyword search-based bidirectional anonymity trusted network debit and credit system of the present invention, the debit side does not need to publicize the personal information, and the system carries out the weighted calculation on the information provided by a user and the trust value obtained by the encrypted search on the social platform to obtain an acquaintance relationship index between the debit side and the credit side, thereby matching the debit and credit behaviors of the debit side and the credit side under the anonymity premise, and improving the privacy and the safety of the debit and credit behaviors.
Owner:SOUTH CHINA AGRI UNIV
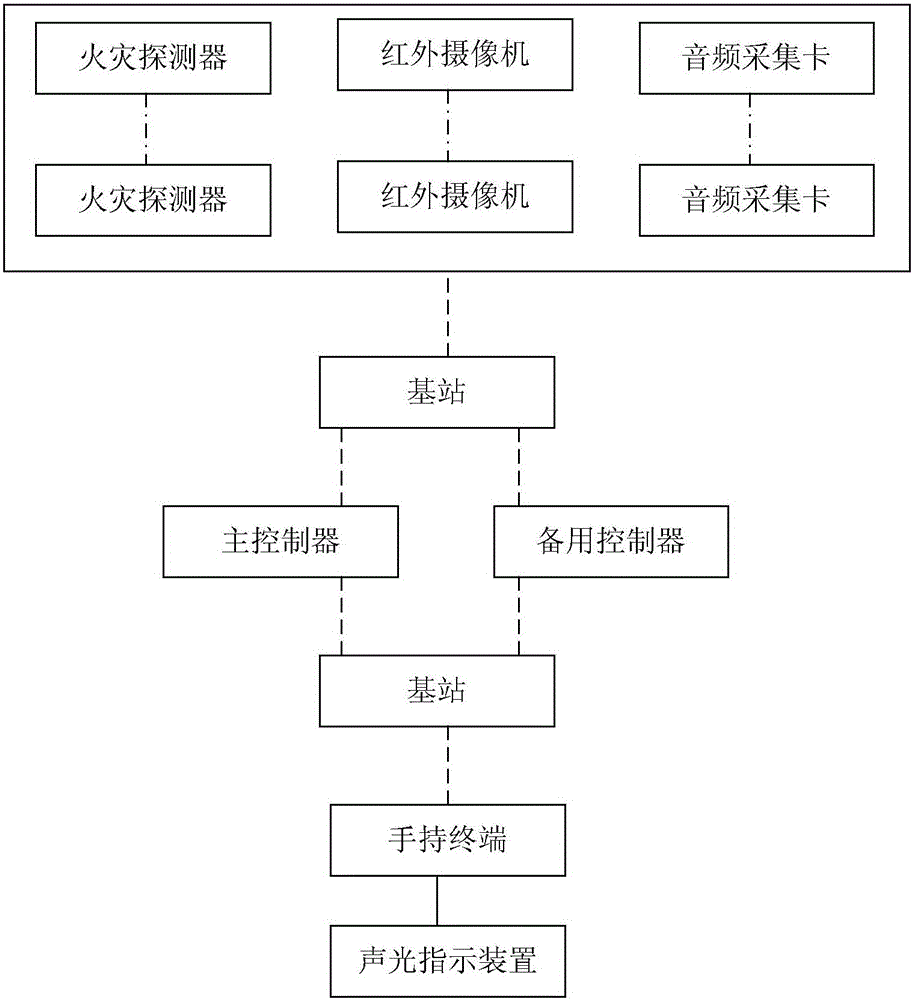
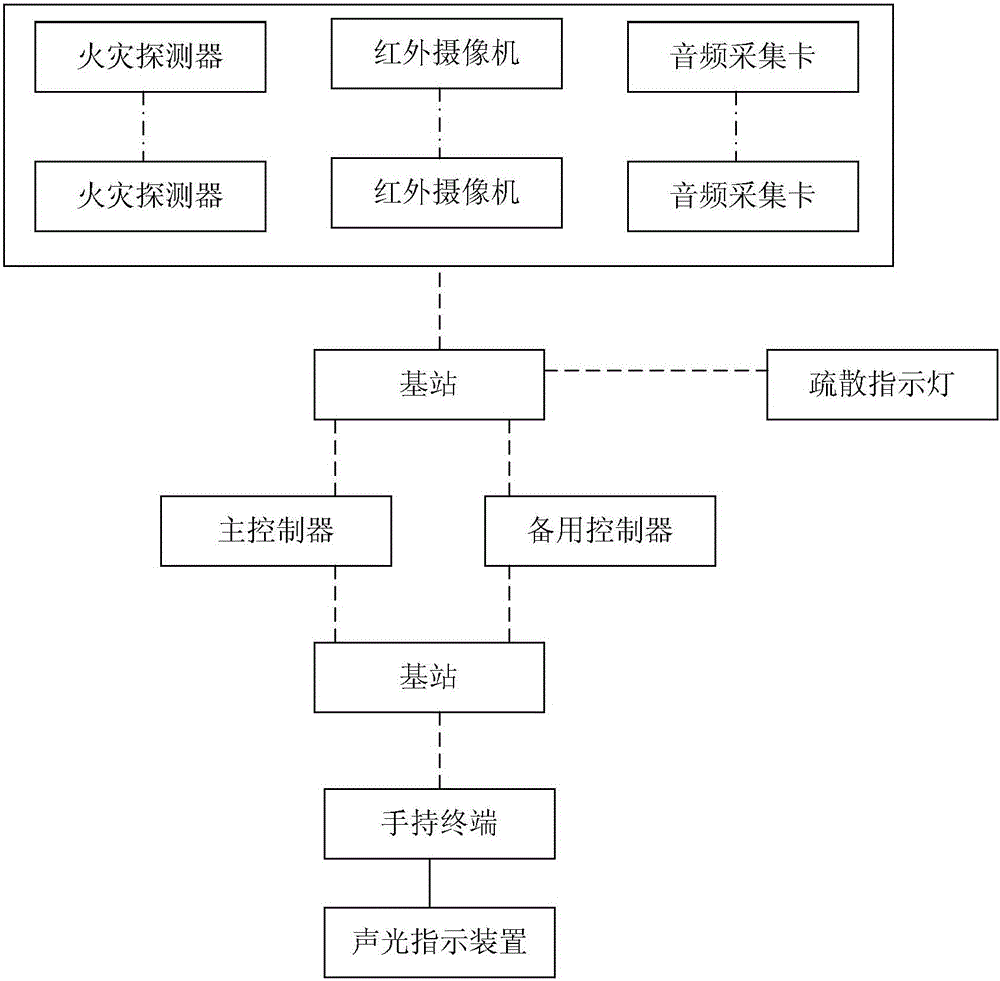
Smart fire scene escaping system and evacuating method for large-scale exhibition halls
InactiveCN106408807AAvoid enteringAvoid chokingSignalling system detailsElectric transmission signalling systemsFire detectorElectricity
The invention discloses a smart fire scene escaping system and evacuating method for large-scale exhibition halls. The system comprises a monitoring system for obtaining the onsite information of a fire scene; a handheld terminal and a sound-and-light indication device for guiding the escape of people; and a control terminal for receiving the data from the monitoring system and issuing escape routes to the handheld terminal. The monitoring system comprises M fire detectors, N infrared cameras, and L audio frequency acquisition cards. The handheld terminal comprises a processor pre-stored with the emergency channel map for the large-scale exhibition hall. The I / O disconnection interface of the processor is electrically connected with a positioning chip. The sound-and-light indication device comprises a sound-and-light alarming device and an audio player. Each door of the emergency channel is provided with at least one sound-and-light alarming device and one audio player. Each sound-and-light alarming device and each audio player are provided with a wireless communication module respectively. The processor is provided with a wireless communication module and a display module. The control terminal comprises a main controller and a standby controller.
Owner:TIAJIN JINGXIONG SCI & TECH ENG DEV CO LTD
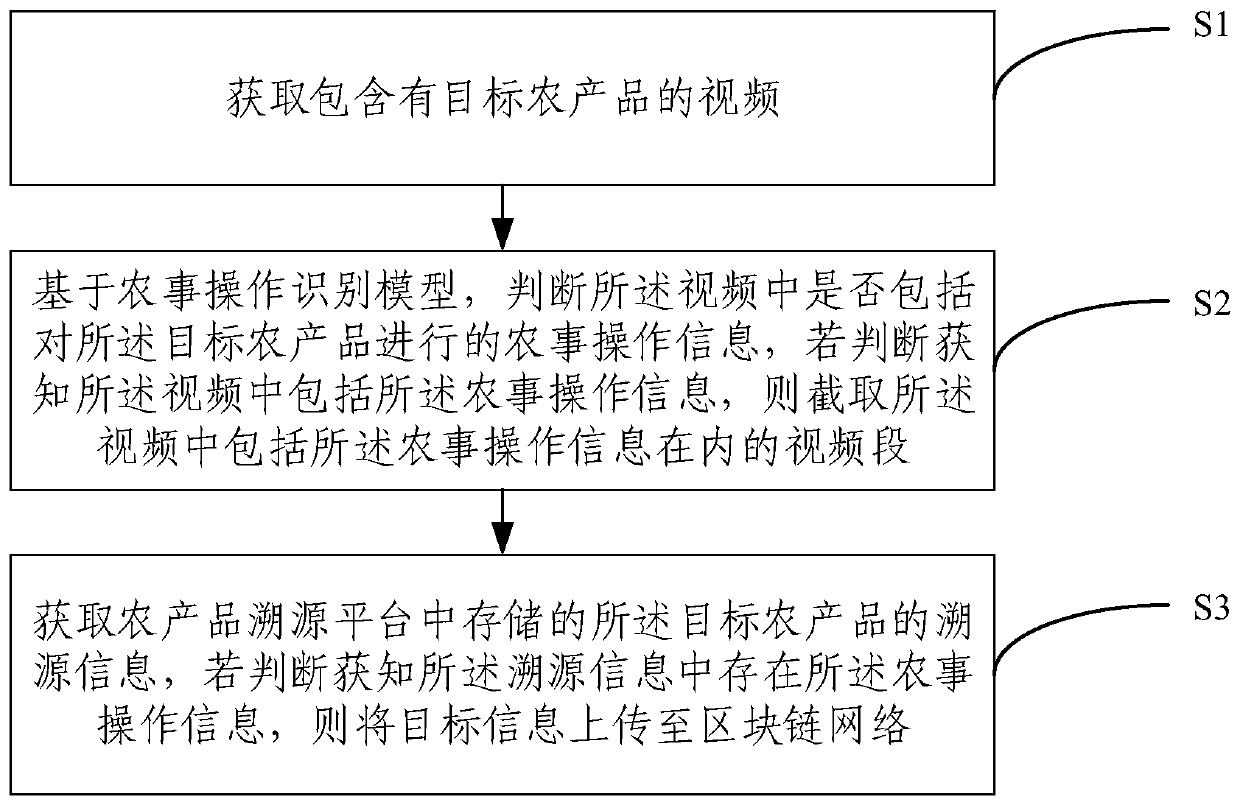
Agricultural product traceability storage method and traceability storage system based on block chain
The embodiment of the invention provides an agricultural product traceability storage method and traceability storage system based on a block chain, and the method comprises the steps: judging whethera video comprises agricultural product operation information of a target agricultural product through an agricultural product operation recognition model, and intercepting a video segment including the agricultural product operation information in the video if the video exists; when the agricultural product traceability information stored in the agricultural product traceability platform containsagricultural operation information, uploading the target information to the block chain network as a storage certificate. The whole process does not involve manual operation, the real reliability ofa block chain traceability system data source is guaranteed, effective data of video monitoring are efficiently utilized, and agricultural product traceability is more efficient and reliable.
Owner:BEIJING RES CENT FOR INFORMATION TECH & AGRI
Method for improving precision of numerically-controlled machine tool main shaft rotating thermal error measuring data
InactiveCN103801987AGuaranteed authenticityEnhanced Thermal Error Compensation and AccuracyMeasurement/indication equipmentsEngineeringSoftware programming
The invention discloses a method for improving precision of numerically-controlled machine tool main shaft rotating thermal error measuring data. The method comprises the steps of conducting theoretical analysis calculation on thermal errors, generated by rotating of the main shaft, in the X direction and the Y direction of a main shaft, obtaining more accurate real thermal error data, avoiding the theoretical errors in the prior art, obtaining the real machine tool main shaft thermal errors in the X direction and the Y direction, and ensuring that a mathematic model built based on the data has the higher precision. According to the method, theoretical defects in a traditional numerically-controlled machine tool main shaft rotating thermal error measuring data processing method are overcome, the precise machine tool main shaft thermal error measuring data are obtained, the defects of large difference existing between compensation simulation precision of a model built based on the theoretical defect data and the real compensation power are overcome, the real effectiveness of numerically-controlled machine tool thermal error compensation modeling precision is ensured, the thermal error compensation function and thermal error compensation precision are enhanced, online accurate measuring data can be obtained through software programming, and the practicability is achieved.
Owner:HEFEI UNIV OF TECH
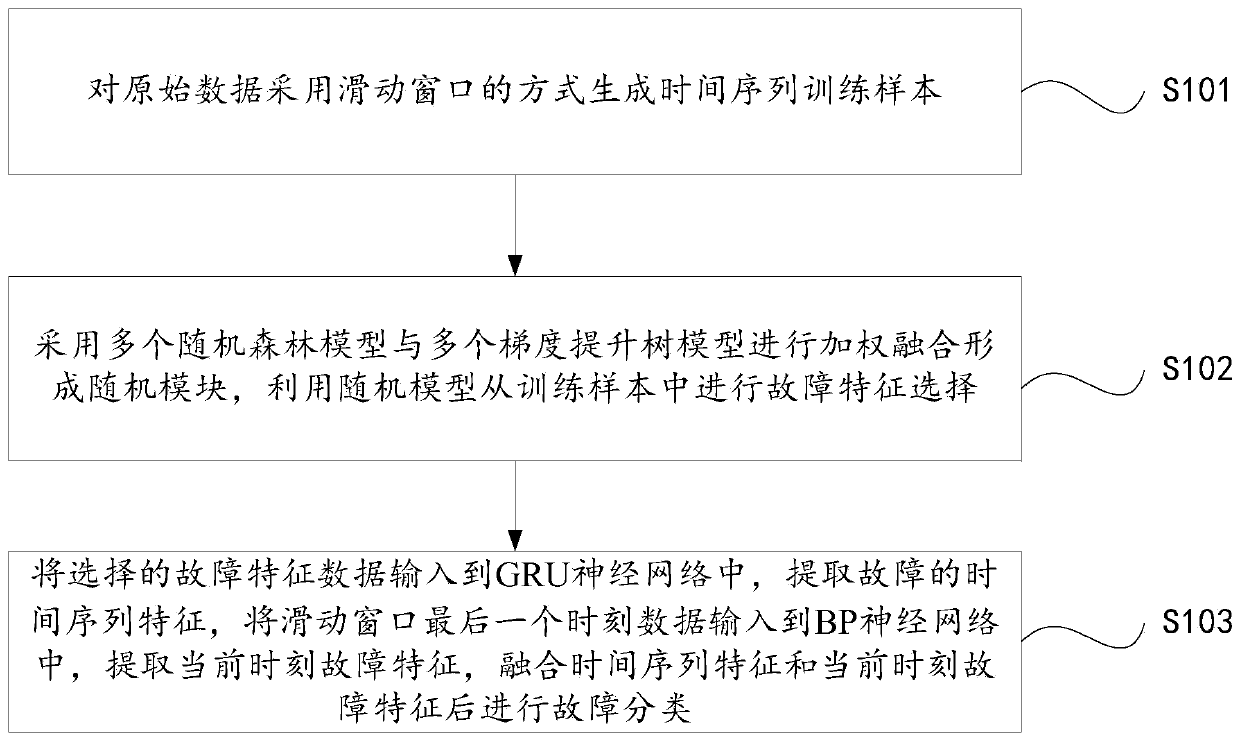
Service robot movement system fault diagnosis method and device based on time sequence characteristics
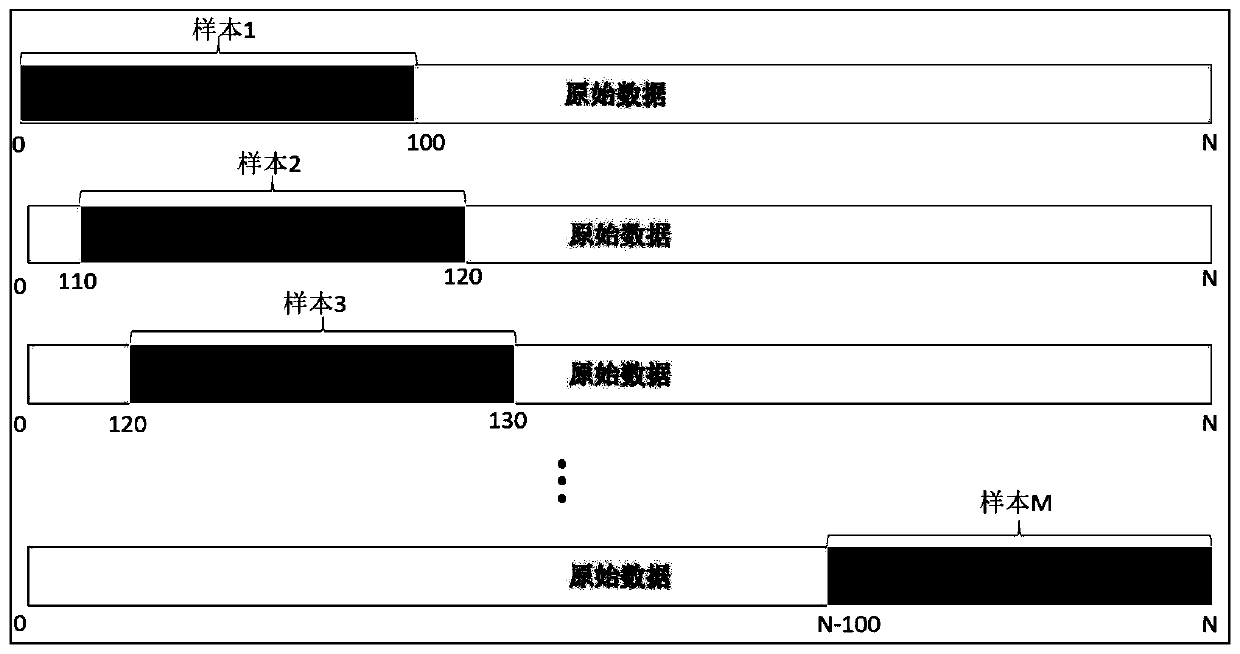
ActiveCN110231156AKeep valid featuresGuaranteed authenticityMachine part testingCharacter and pattern recognitionOriginal dataSlide window
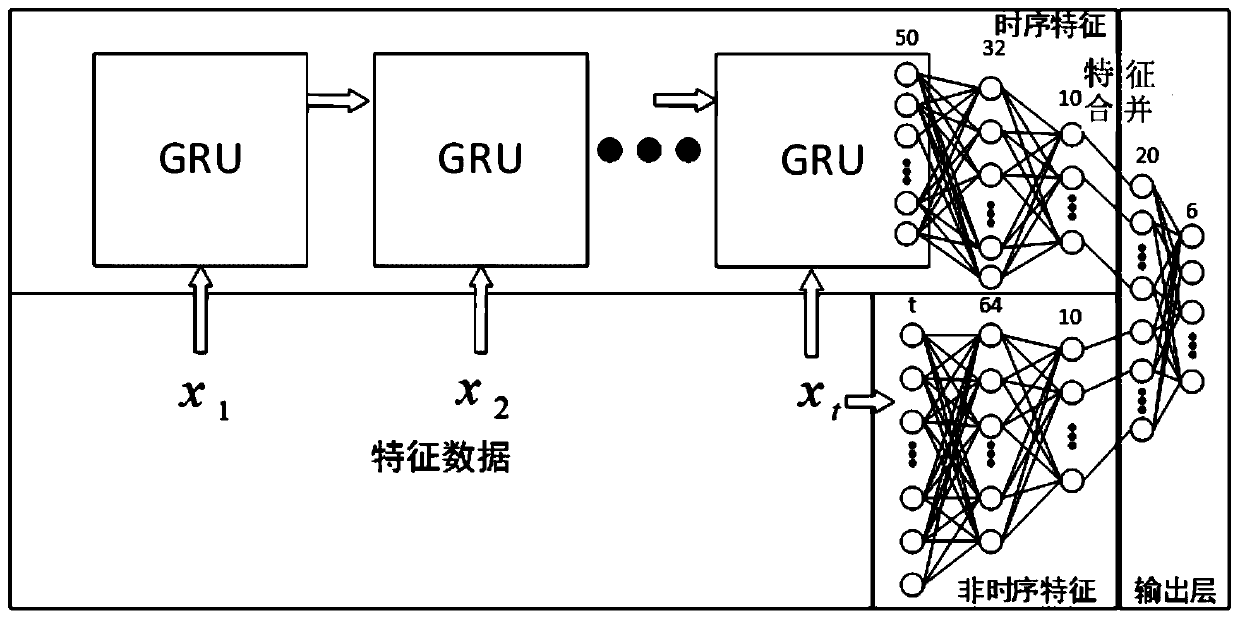
The invention provides a service robot movement system fault diagnosis method and device based on time sequence characteristics. The service robot movement system fault diagnosis method based on timesequence characteristics comprises the following steps that: adopting a sliding window way for original data to generate a time sequence training sample; adopting a plurality of random forest models and a plurality of gradient boosting tree models to carry out weighting fusion to form a random module, and utilizing a random model to carry out fault characteristic selection in the training sample;and inputting selected fault characteristic data into a GRU (Gated Recurrent Unit) neural network, extracting the time sequence characteristics of the fault, inputting the last moment data of the sliding window into a BP (Back Propagation) neural network, extracting the fault characteristics of a current moment, and carrying out fault classification after the time sequence characteristics and thefault characteristics of the current moment are combined.
Owner:SHANDONG UNIV
Webpage tamper-proofing device and method based on access control and directory protection
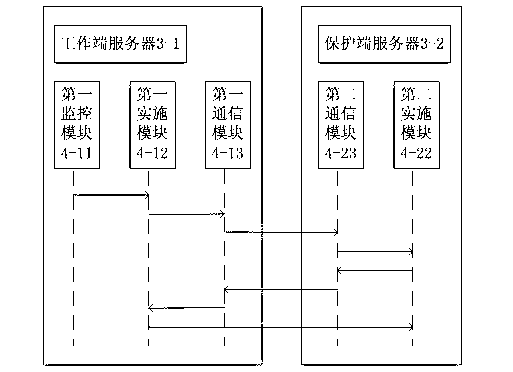
InactiveCN103236932APrevent tamperingTampering will notUser identity/authority verificationTamper resistanceMedia access control
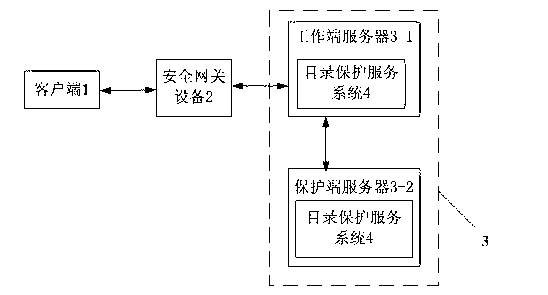
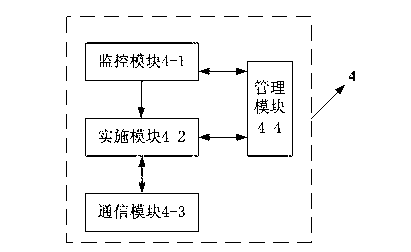
The invention provides a webpage tamper-proofing device and a webpage tamper-proofing method based on access control and directory protection. The webpage tamper-proofing device comprises a client end and a service end, wherein security gateway equipment is arranged between the client end and the service end, the service end comprises a work end server and a protecting end server, the work end server and the protecting end server are connected in an interactive manner, the work end server is communicated with the client end, and directory protection service systems are respectively arranged inside the work end server and the protecting end server. The webpage tamper-proofing device and the webpage tamper-proofing method comprise two parts that 1, the access control is realized through the security gateway equipment, an internal website and an external website are separated, the access authority of users is determined, and the users are prevented from illegally accessing and modifying application system and data; and 2, the directory protection function is realized through the directory protection service systems, the real-time deletion and recovery is realized, and the real reliability of files is ensured.
Owner:ANHUI HIGHGUARD NETWORKS TECH
Electronic contract storage method and device based on block chain, and electronic equipment
ActiveCN110351239AEasy to keepAvoid disclosureEncryption apparatus with shift registers/memoriesDigital data protectionElectronic contractsConfidentiality
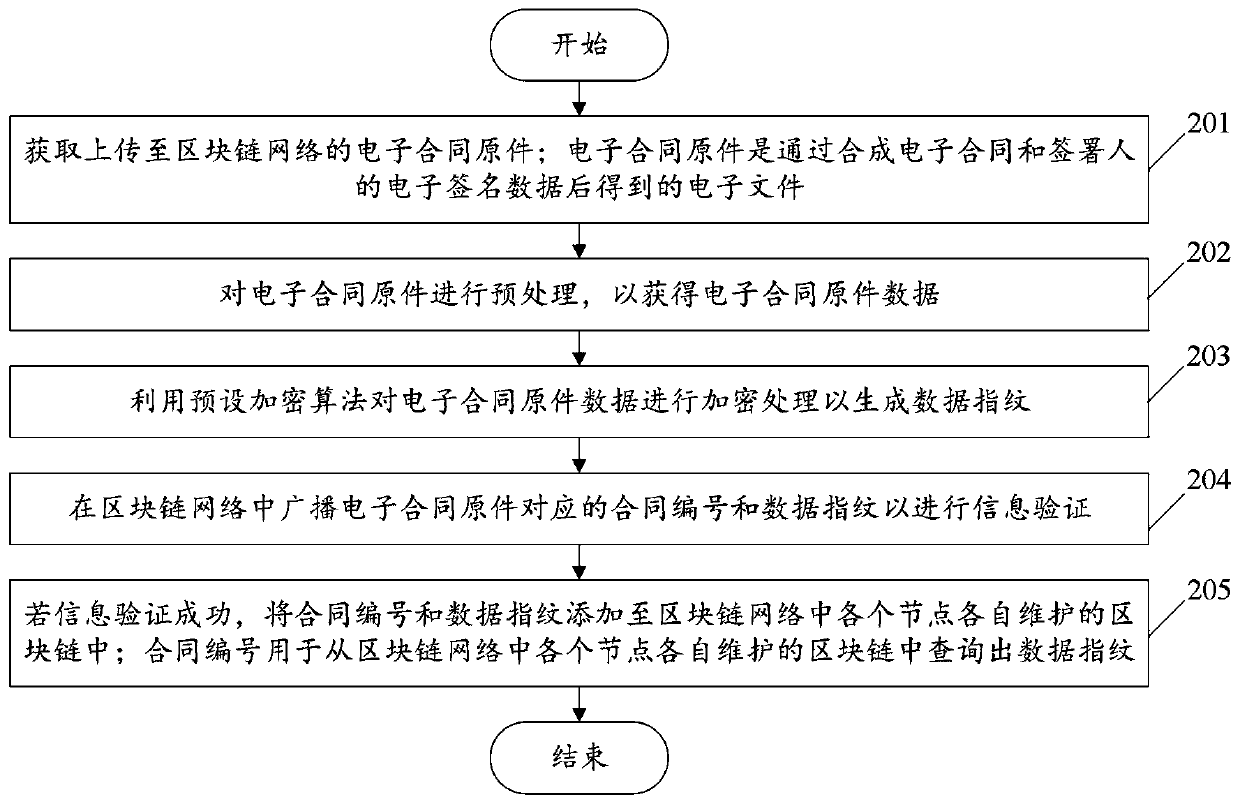
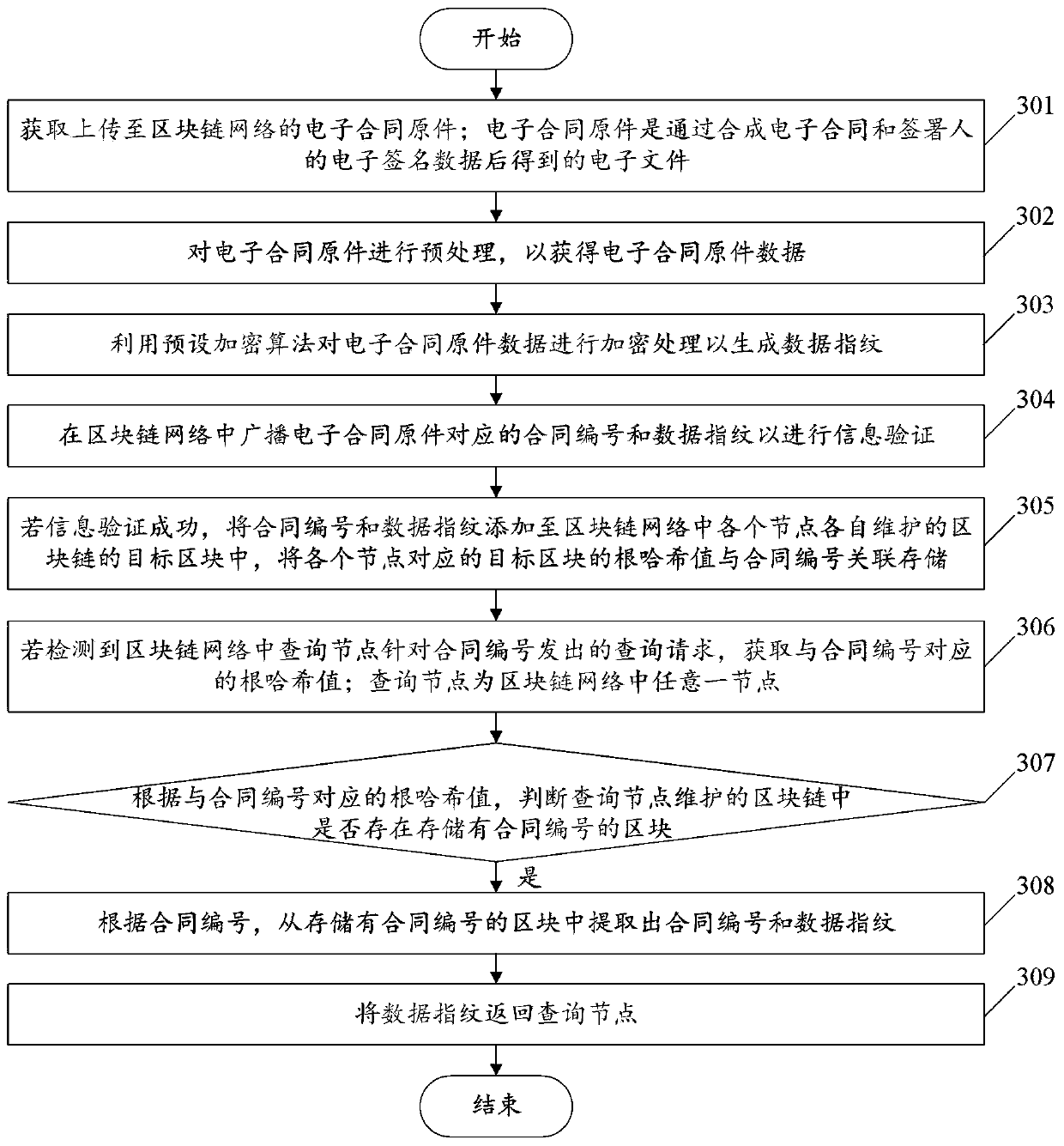
The invention relates to the technical field of block chains, and discloses an electronic contract storage method and a device based on a block chain, and electronic equipment, and the method comprises the steps: obtaining an electronic contract original uploaded to a block chain network, and enabling the electronic contract original to be an electronic file obtained through the synthesis of an electronic contract and the electronic signature data of a signer; preprocessing the electronic contract original to obtain electronic contract original data; performing encryption processing on the electronic contract original data by using a preset encryption algorithm to generate a data fingerprint; broadcasting a contract number and a data fingerprint corresponding to the electronic contract original in the blockchain network to perform information verification; and if the information verification succeeds, adding the contract number and the data fingerprint to the blockchain maintained by each node in the blockchain network, so that the electronic contract original can be prevented from being disclosed, the confidentiality of the electronic contract original can be improved, the electronic contract original data corresponding to the data fingerprint can be prevented from being tampered, and the real reliability of the data fingerprint can be ensured.
Owner:PINGAN PUHUI ENTERPRISE MANAGEMENT CO LTD
Long-distance high-spatial-resolution Raman temperature measurement sensor and realization method thereof
ActiveCN105973501AGuaranteed authenticityFilter out the DC componentThermometers using physical/chemical changesRaman amplifiersRadio frequency
The invention is mainly used for the optical fiber sensing temperature measurement field, and especially relates to a long-distance high-spatial-resolution Raman temperature measurement sensor and a realization method thereof. The long-distance high-spatial-resolution Raman temperature measurement sensor is characterized in that the long-distance high-spatial-resolution Raman temperature measurement sensor comprises an ultra-narrow-linewidth laser, a circulator, an acoustic-optic modulator, a reflector, a radio frequency generator, a 1*2 optical splitter (1:1), two wavelength division multiplexers, a Raman amplifier, an EDFA, two 2*1 couplers, a photoelectric detector, a signal processing and collection unit and a microprocessor unit. The beneficial effects are that the invention discloses the realization method of the long-distance high-spatial-resolution Raman temperature measurement sensor; the monitoring distance of the Raman temperature measurement sensor based on OTDR is generally smaller than 10 km, and spatial resolution is generally larger than 1 m; and the invention provides the realization method of the Raman temperature measurement sensor based on OFDR location technique, wherein the method can greatly improve measuring distance and spatial resolution index of the system, and the method can enable the monitoring distance of the Raman temperature sensor to reach 20 km, and spatial resolution index to reach the centimeter scale.
Owner:WEIHAI BEIYANG PHOTOELECTRIC INFORMATION TECH
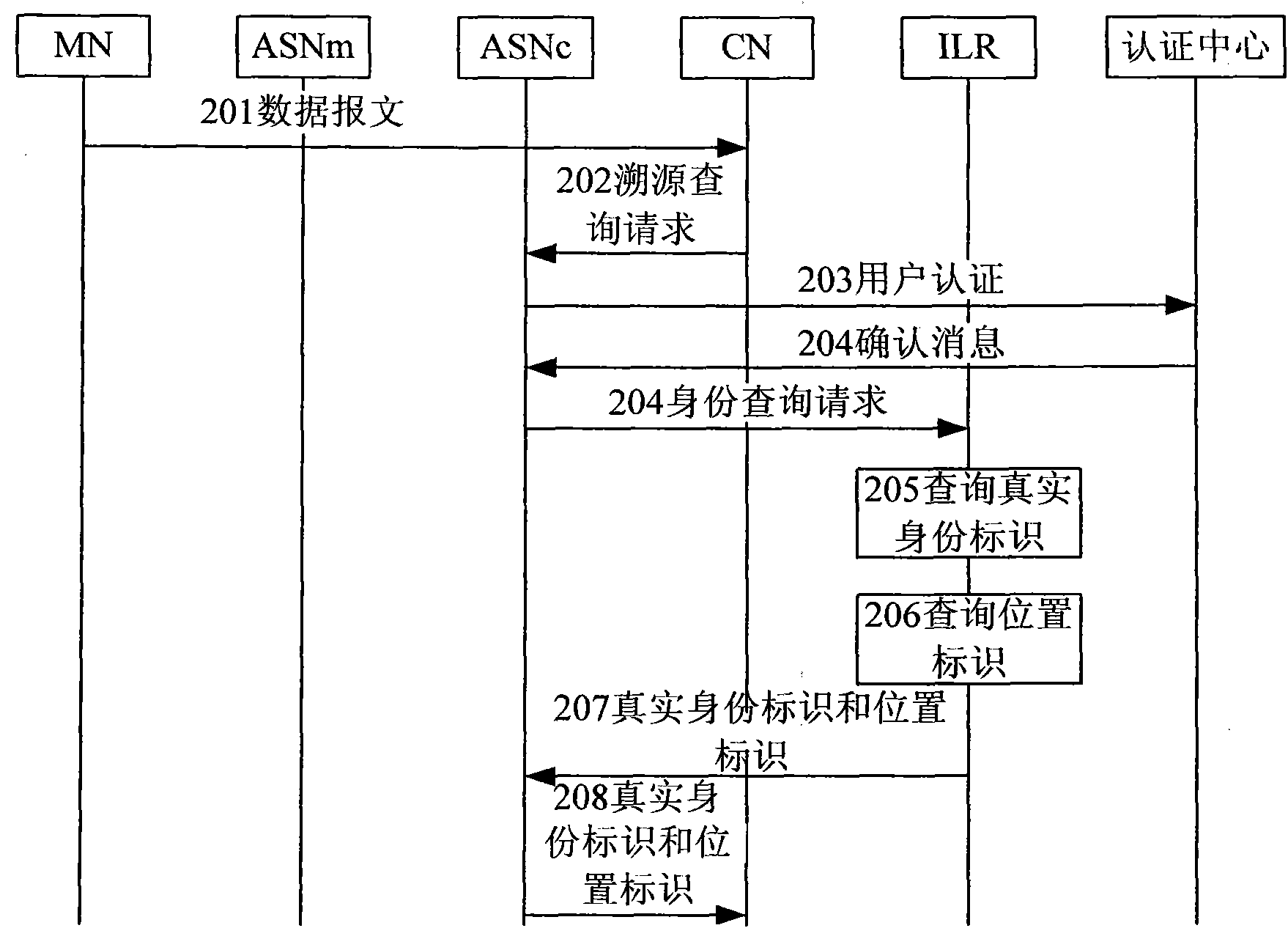
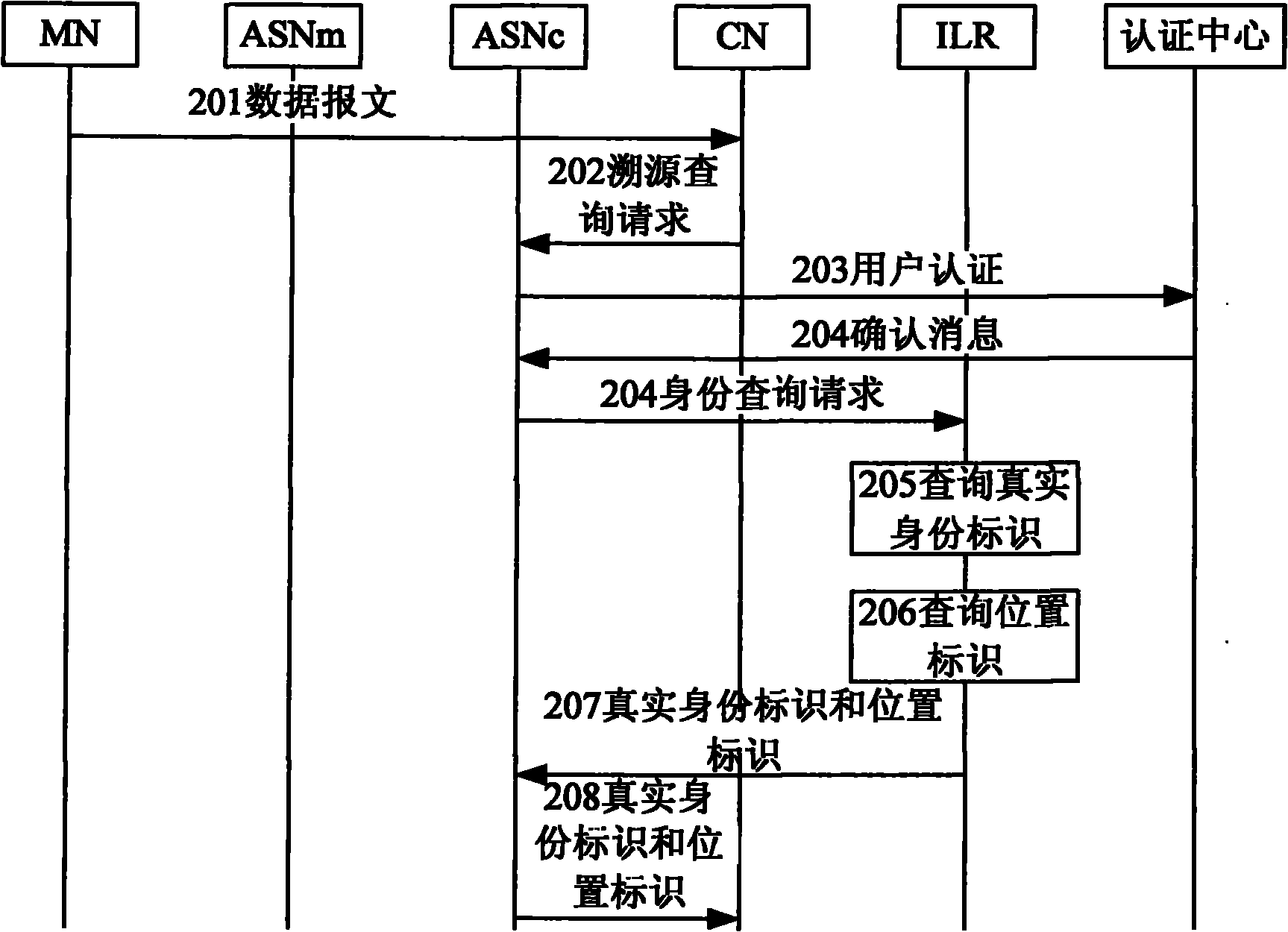
Source-tracing method and system for anonymous communication
InactiveCN102045163AGuaranteed authenticityUser identity/authority verificationIp addressApplication Identifier
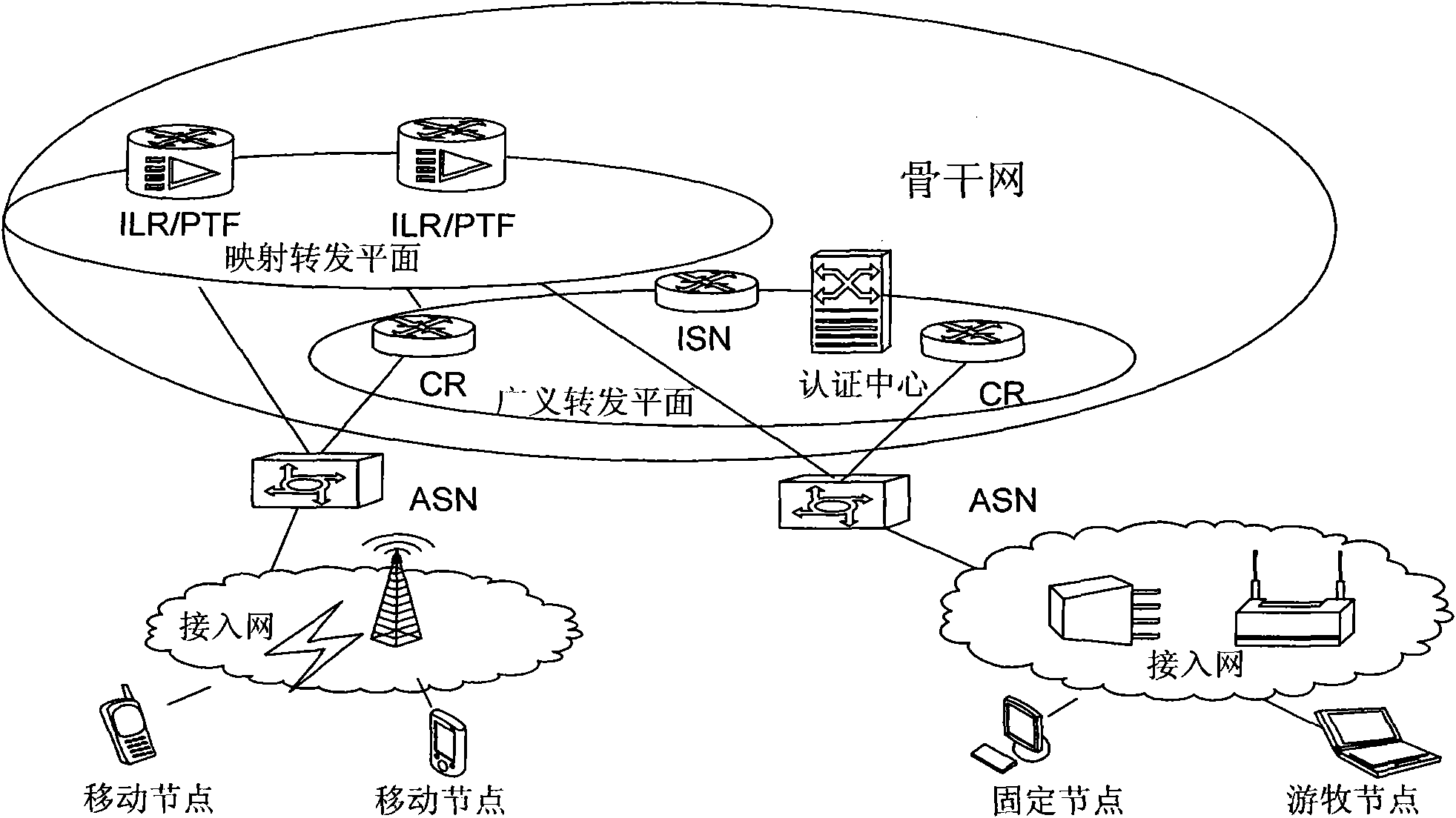
The invention discloses a source-tracing method for anonymous communication, which comprises the following steps of: sending a source-tracing inquiring request to an accessed access node by a node, and carrying an anonymous identity identifier in the source-tracing inquiring request; after the source-tracing inquiring request is received by the access node, inquiring a corresponding true identity identifier according to the anonymous identity identifier; and sending the inquired true identity identifier to the node. The invention considers that an IP (Internet Protocol) address can be dynamically allocated and can be juggled, and the source tracing of the IP address can not represent the positioning to a user; an AID (Application Identifier) is the true identity of the user, and wherever the user is located, the AID is unique, and the positioning to the AID is the positioning to the user; and an RID (Relative Identifier) is the position identifier of the user, an edge router accessed to the user is also identified, and the position of the user is inquired when the RID is positioned.
Owner:ZTE CORP
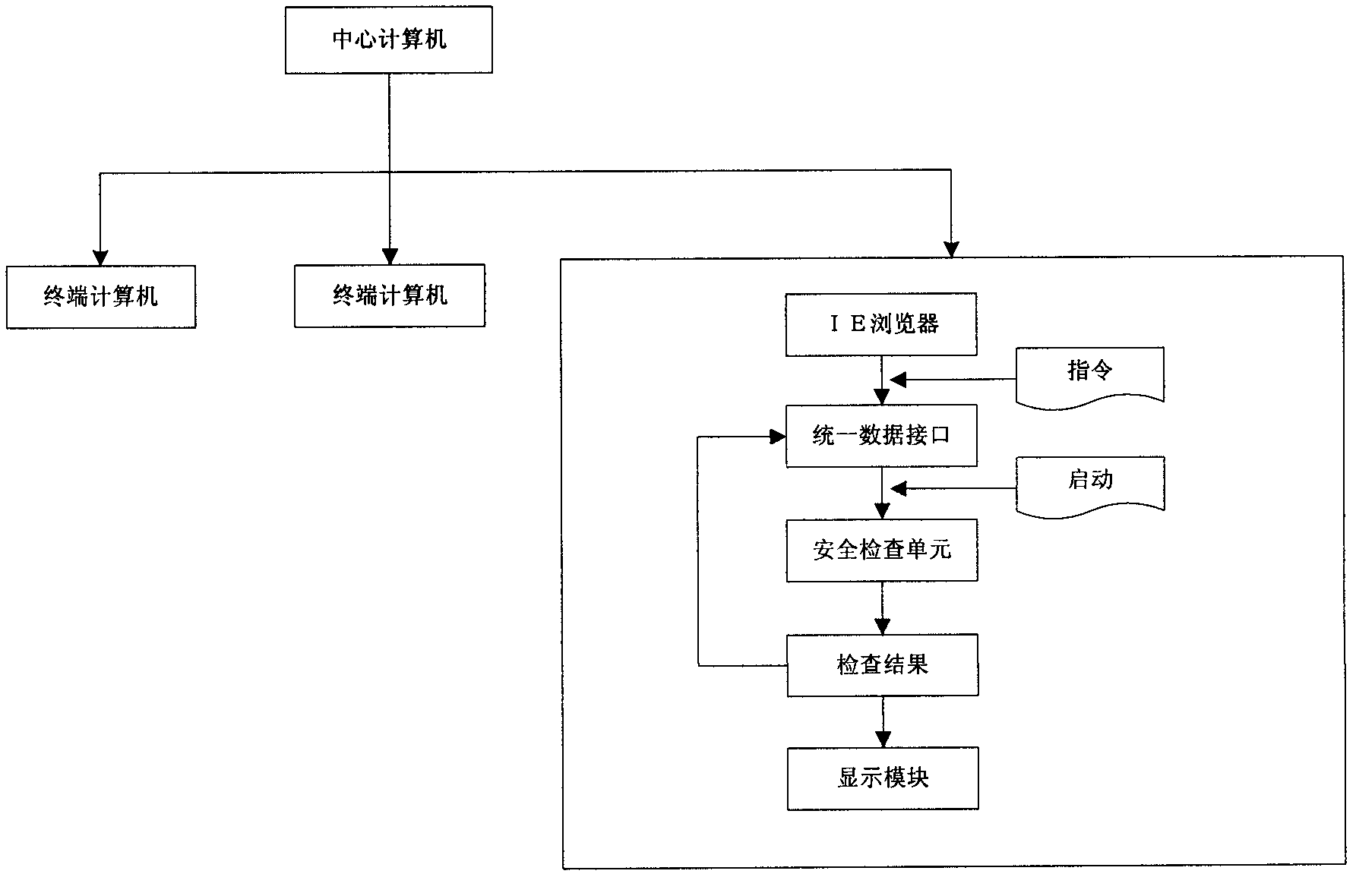
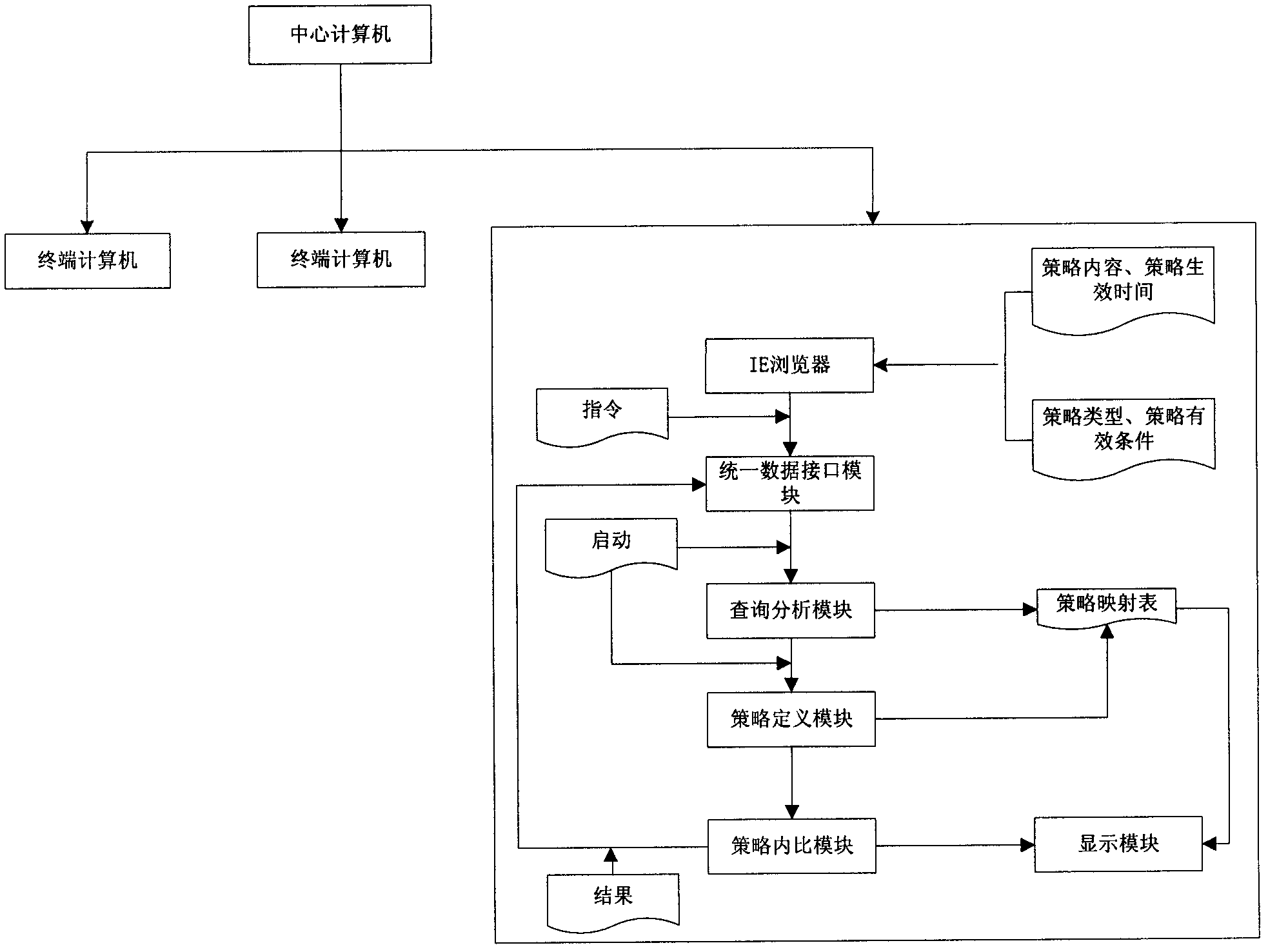
Safety online detecting system facing to terminal computers
ActiveCN102663298AAvoid defects that require on-site inspectionAvoid pitfalls of on-site inspectionPlatform integrity maintainanceNetwork onComputer security
A security online detecting system facing to terminal computers performs a centralized detection on all the terminal computers in network on a center computer on line. The system comprises a online detecting tool, a packaging module and the center computer, the online detecting tool is packed as CAB form and stored in the center computer by the packaging module, and the CAB is embedded into the IE browser by the center computer, the CAB is downloaded from the center computer to the terminal computer through the IE browser and automounted, a user can input a project command which expected to be detected and input information corresponding to the detected project by the IE browser on the center computer, the received project command and the input information corresponding to the detected project are send to a security detecting unit by a unified data interface module of every terminal computer, and the security detecting unit starts strategy security online detecting or patch security online detecting or hardware resource information security online detecting or software security online detecting according to the project command, and then the detecting results are displayed by a display module.
Owner:BEIJING INST OF SPACECRAFT SYST ENG +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com