TPM-based Modbus/TCP security enhancement method
A protocol and security technology, applied in the field of industrial control, can solve problems such as server impersonation and key theft
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
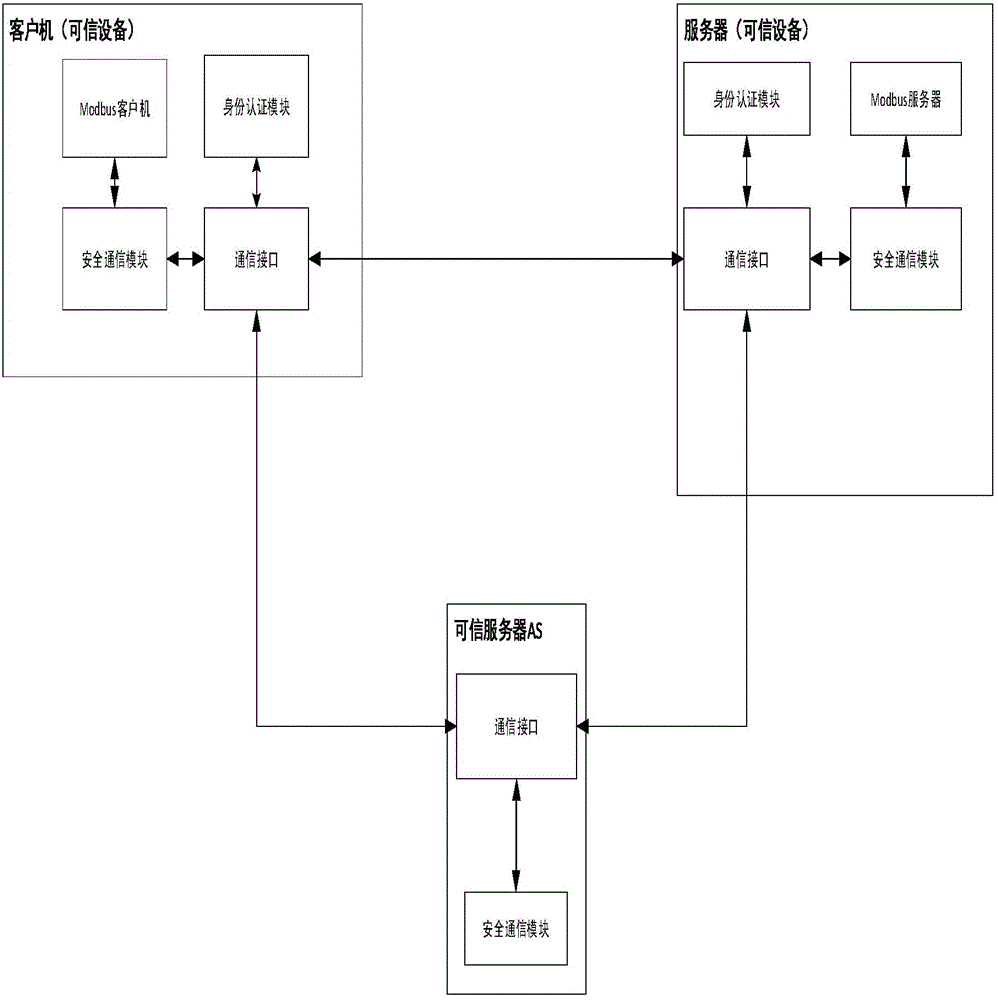
[0075] Any change in key information such as operating system key kernel modules and industrial control configuration software in a trusted device will change the trusted measurement value, that is, a change in device status information.
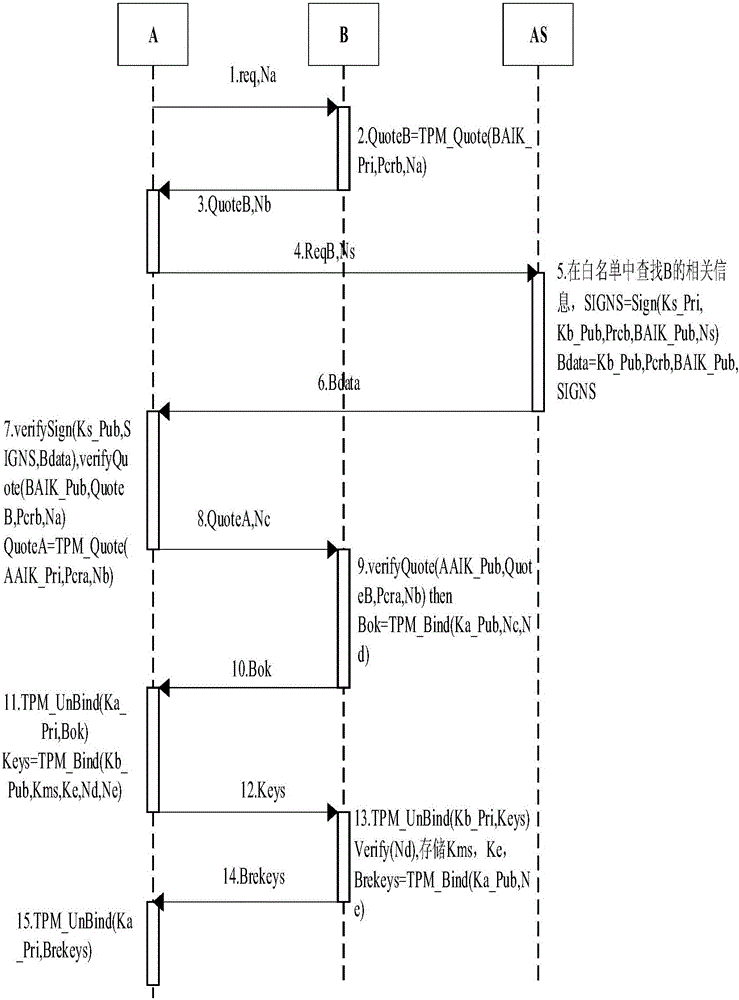
[0076] In order to make those skilled in the art better understand the present invention, the present invention will be further described below in conjunction with the accompanying drawings.
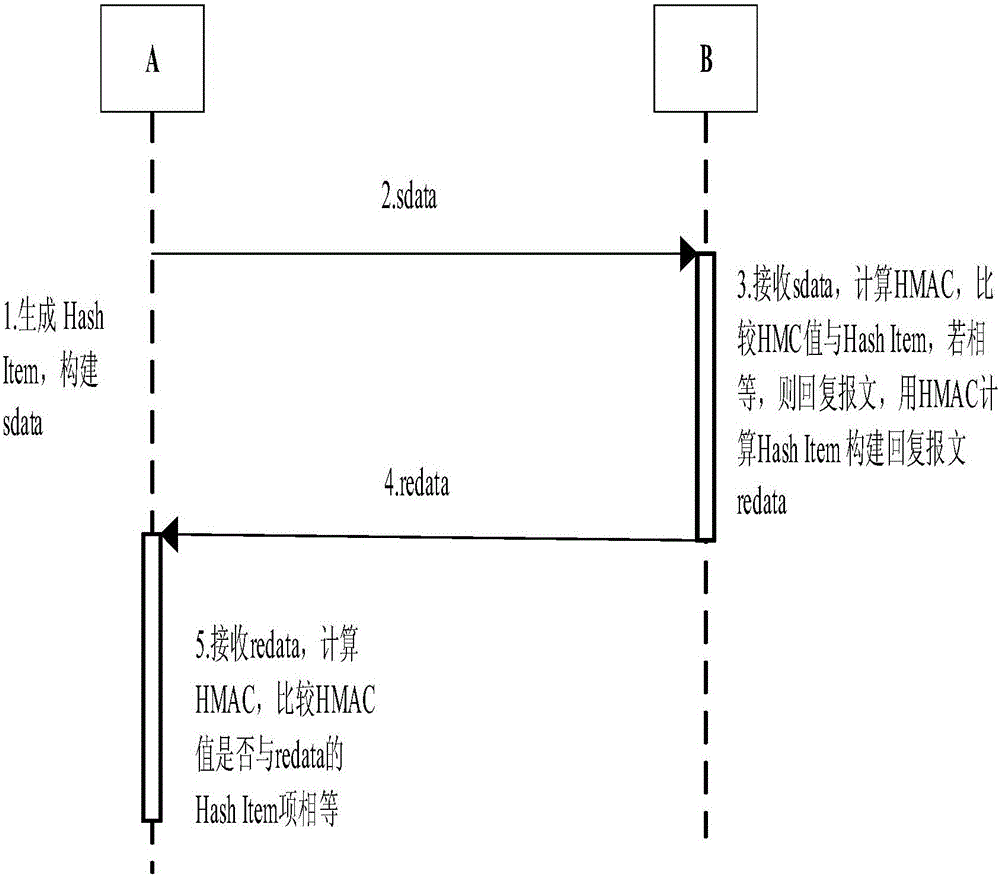
[0077] The trusted Modbus / TCP protocol format is shown in Table 1
[0078] Table 1: Trusted Modbus / TCP Formats
[0079]
[0080] MBAP: Header for Modbus / TCP.
[0081] HashAlgorithm: 1 byte, the hash algorithm is selected according to the computing capability of the device, and the two parties negotiate on the hash algorithm that can be used. The devices on both sides of the communication store the hash algorithm table. If this field is 1, it means SHA-1 is used, and if it is 2, MD5 is used.
[0082] HashItem: This item has a different number of byt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com