Method for fixing and saving evidence of computer crime and device therefor
A computer and evidence technology, applied in computer security devices, computing, program control devices, etc., to achieve the effect of ensuring legality, reliability, and good compatibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
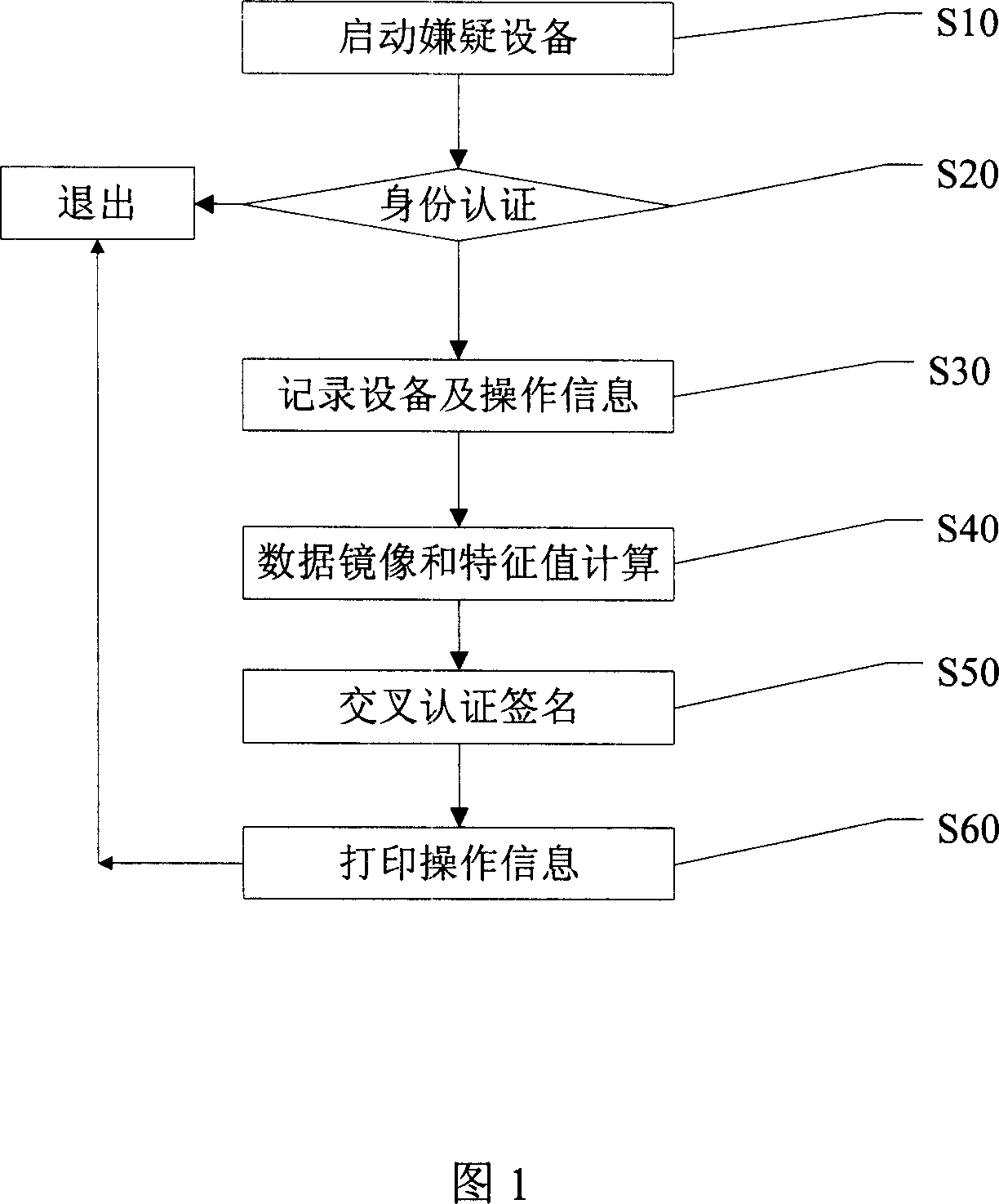
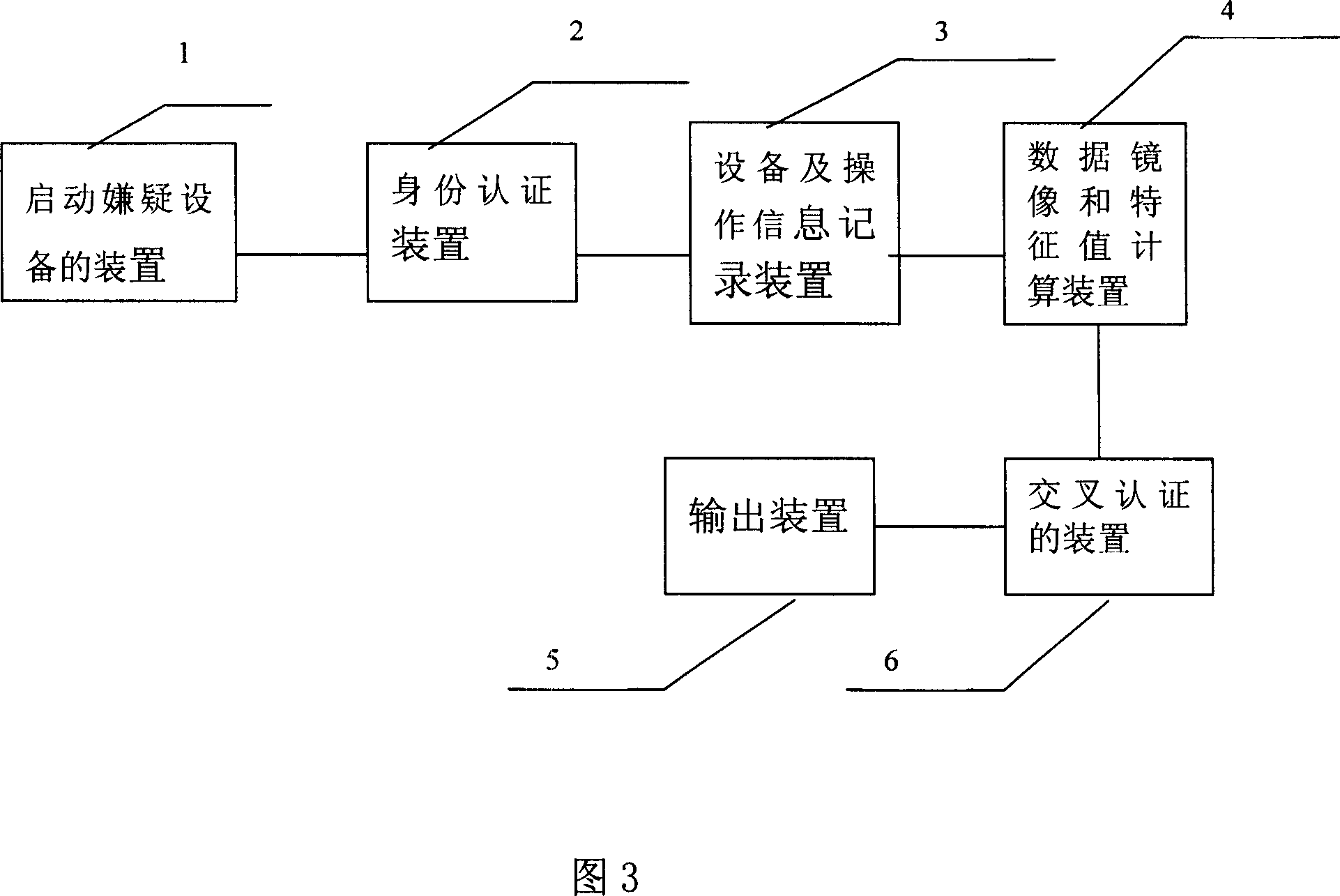
[0022] The specific embodiment of the present invention will be described in detail below with reference to the accompanying drawings. FIG. 1 is a flow chart of the computer crime evidence fixing and preservation method of the present invention.
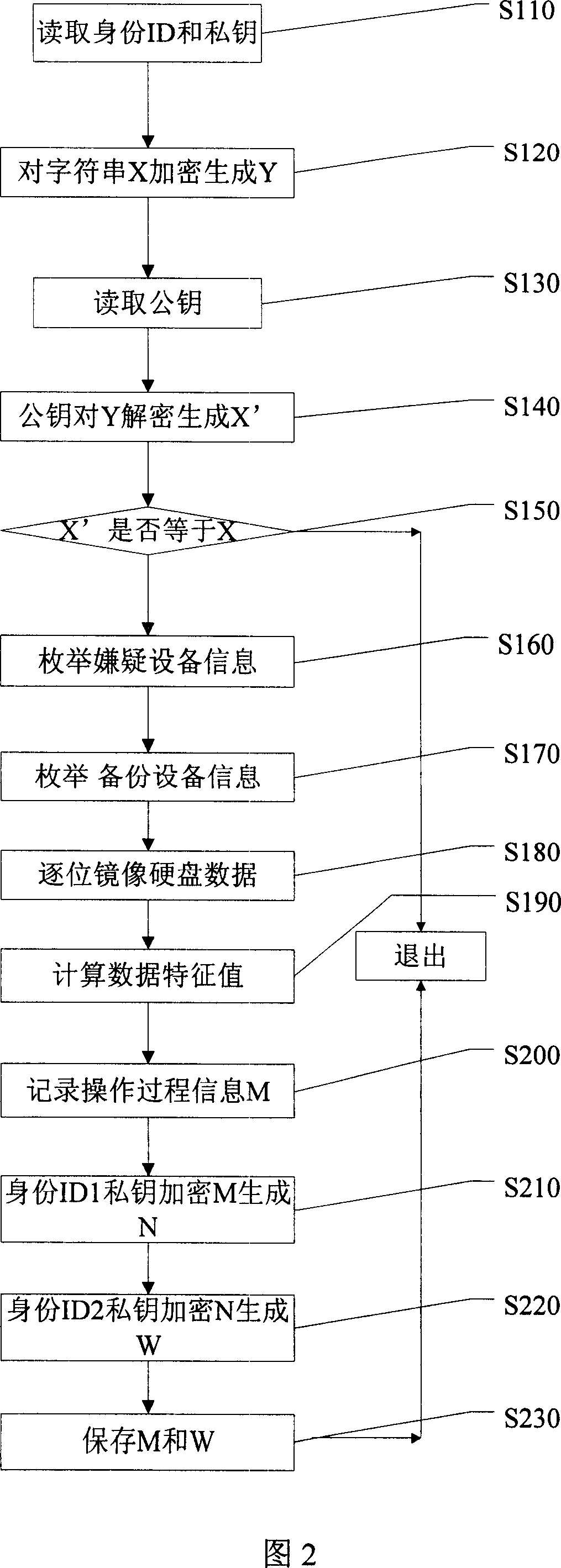
[0023] The method for fixing and preserving computer crime evidence of the present invention includes: step S10 of starting the suspect device: modifying the Bios setting of the suspect computer, so that the computer supports CD priority startup, and automatically guides the system to start the suspect computer; identity authentication step S20, by reading evidence Use the private key of the personnel, and encrypt a piece of data with the private key, and then use the public key of the forensic personnel built in the system to decrypt the content, compare the two sets of data obtained, if the two sets of data are the same, proceed to step S30, if The two sets of data are different, so exit the system. In addition, methods such as user...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com