Method and device for obtaining input of secure multi-party computing protocol
A technology for secure multi-party computation and protocol, applied in the field of cryptography, which can solve the problem of too many computing and storage resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0118] Embodiments of this specification will be described below with reference to the accompanying drawings.
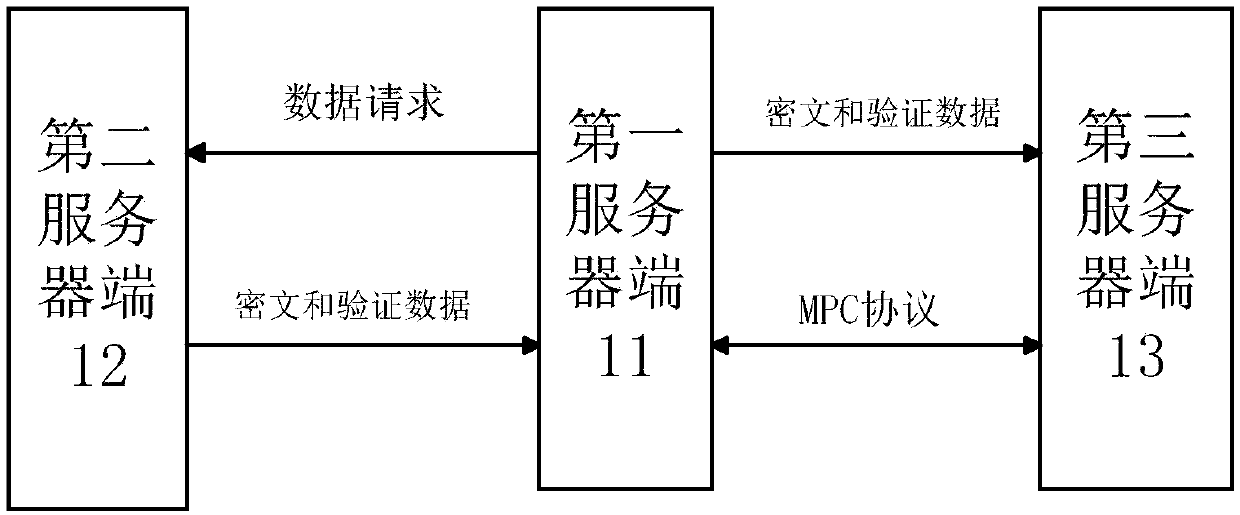
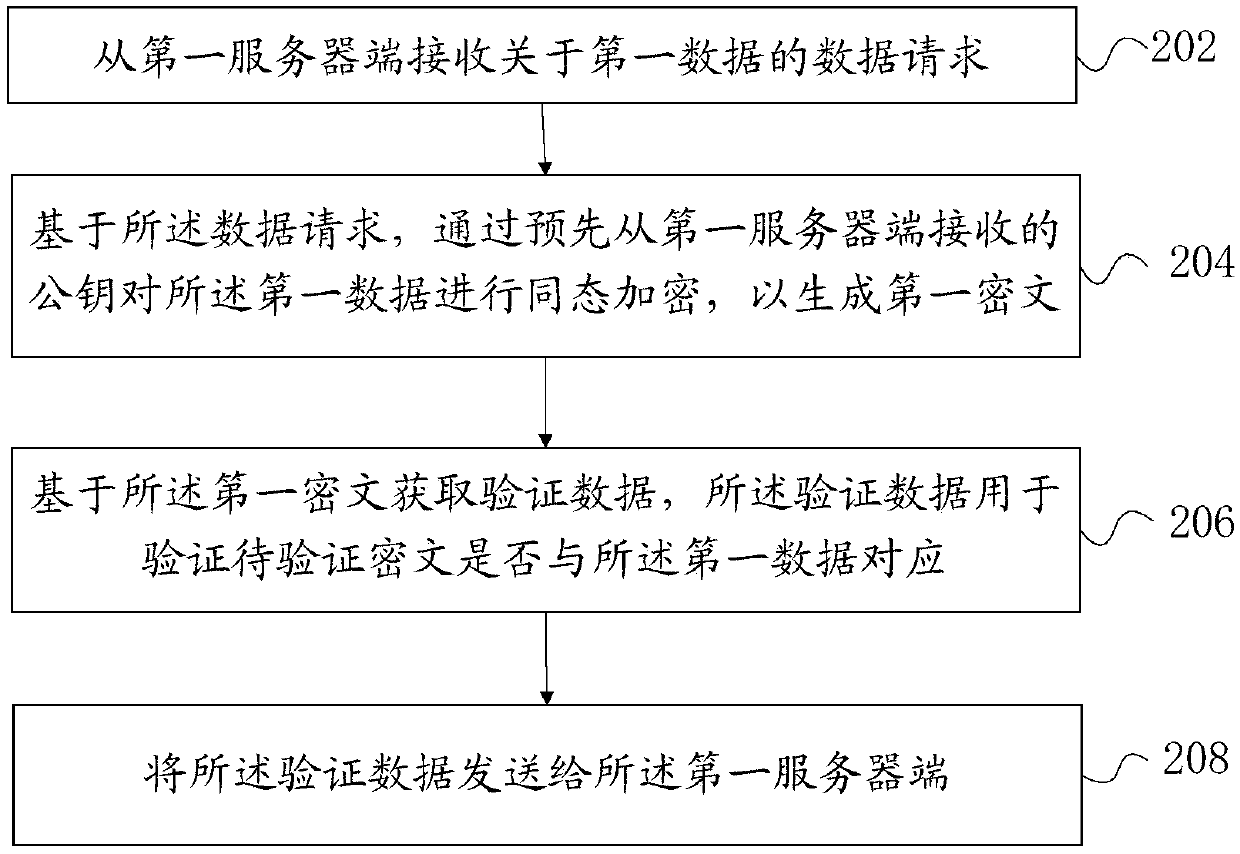
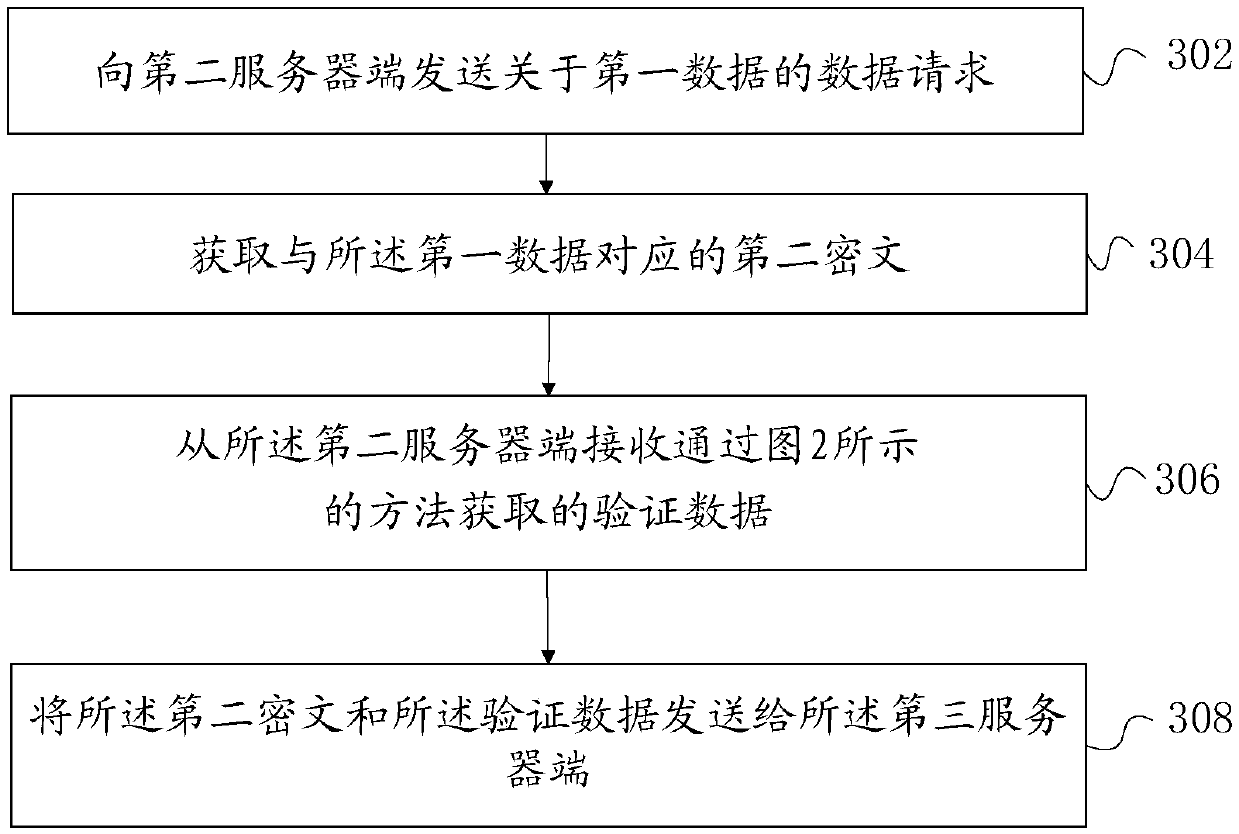
[0119] figure 1 A schematic diagram of a scenario of secure multi-party computing according to an embodiment of this specification is shown. Such as figure 1 As shown, the participants in the secure multi-party computing include a first server end 11 and a third server end 13, the first server end 11 is the prover server end, and the prover is, for example, an individual, an enterprise, an organization, etc., and the third server end 13 is On the verifier server side, the verifier can be an individual, enterprise, organization, etc. that provide services to the prover. This scenario also includes a second server end 12, which is, for example, a server end of an authoritative organization such as a bank or a tax bureau, in which the data of the certifying party is stored. Before the first server end 11 and the third server end 13 execute the secure multi-party comp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com