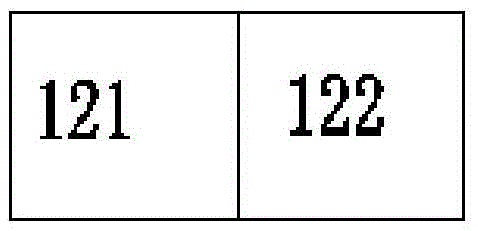End-to-end voice encryption communication method and device for mobile terminals
A voice encryption and mobile terminal technology, applied in the field of mobile communication, can solve problems such as wiretapping of calls, information leakage, fake base station fraud, etc., and achieve the effect of increasing privacy, simple structure and reasonable design
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
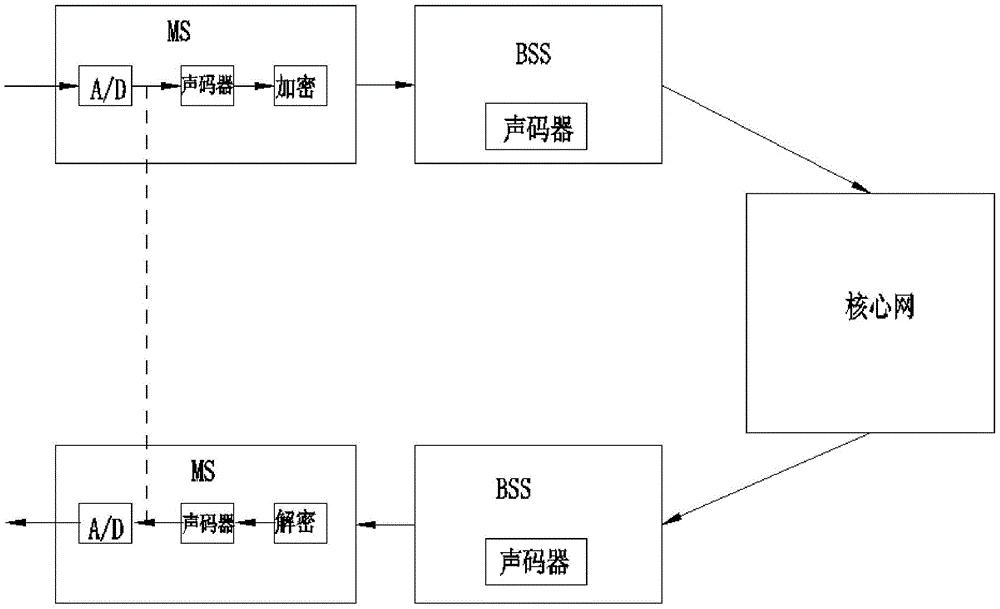
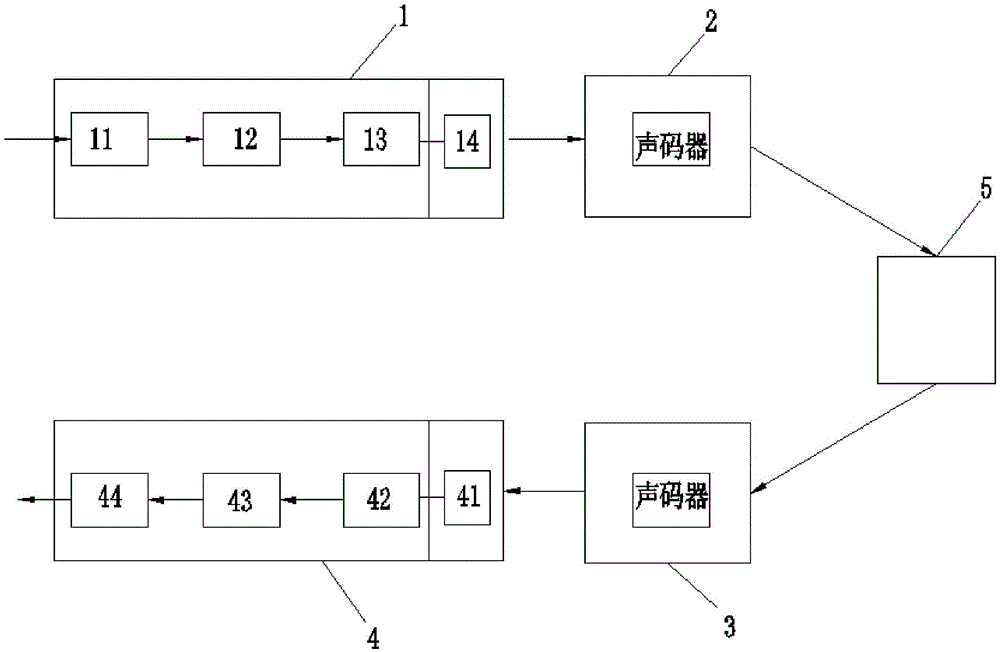
[0028] see Figure 2 to Figure 3 , the method for the mobile terminal end-to-end voice encryption call of the present embodiment, the steps are as follows:
[0029] 1) A / D data acquisition: the input voice call signal is converted by A / D, encoded by PCM, and divided into voice frames of fixed duration according to the mobile communication standard;
[0030] 2) Encryption: the key is dynamically obtained through the operation of the access station 121 (AP), and then the key is sent to the encryption unit 122 to encrypt the voice frame;
[0031] 3) Modulation: Design the modulator according to key parameters such as voicing judgment, gain, pitch frequency, and speech synthesis filter coefficient to synthesize encrypted data into speech signals;
[0032] 4) Vocoder processing and base station transmission: the mobile communication vocoder performs encoding, encryption and other processing on the synthesized voice signal, and transmits it from the terminal to the base station aft...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com