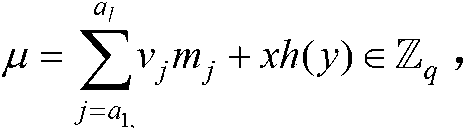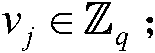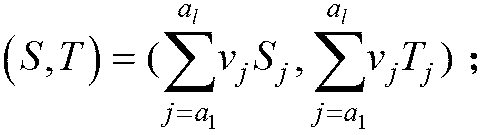Data safety audit method based on identification
A technology for data security and identity, applied in the field of information security, can solve the problems of inability to resist malicious cloud server attacks, complex maintenance and management of certificate systems, high computing and communication overhead, etc., to achieve effective auditing, ensure security and effectiveness, The effect of reducing computational complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The present invention will be further described below by taking cloud storage data security audit as an example.
[0025] The identity-based cloud storage data security audit method is as follows:
[0026] 1.1 Meaning of symbols used
[0027] F represents the file storing data, which consists of n data blocks composition, Represents the set of integer modulo q remainder classes, where q is a large prime number;
[0028] ID i ∈{0,1} * is the identity of user i, w∈{0,1} * The state parameters held by all users, in is an additive cyclic group of order prime q, Secret value held for PKG, {0,1} * represent a binary number,
[0029] S j , T j are data blocks m j The signature value and random tag value of S, T are the aggregated signature value and aggregated random tag value of the challenge data block respectively;
[0030] h 1 (·),H 2 ( ) all represent a one-way hash function, and the definition mapping is:
[0031] h( ) represents a one-way hash ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com