Digital identity verification method, apparatus and system based on block chains
A digital identity and blockchain technology, applied in digital transmission systems, user identity/authority verification, transmission systems, etc., can solve problems such as increasing user thresholds and existing security risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
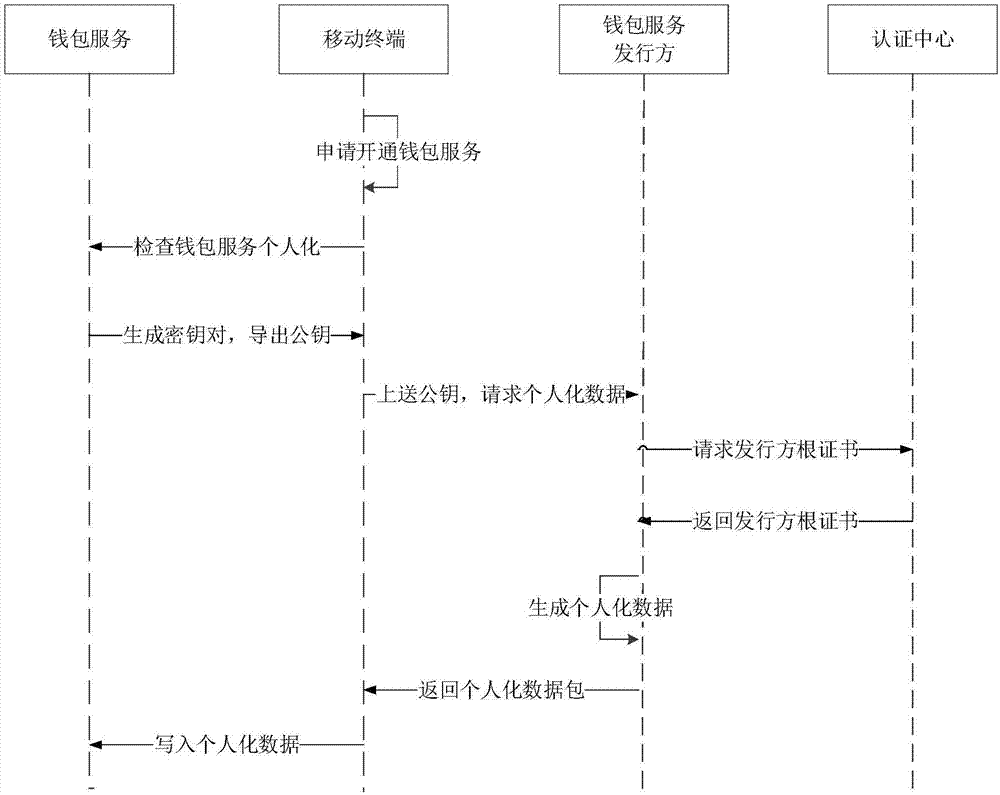
[0098] Based on the above embodiments, before the digital identity verification, a registration process of the wallet service may also be included. see image 3 , image 3 Schematic diagram of the process of registering for the wallet service. The specific technical solution is as follows:
[0099] S201: The mobile terminal receives a user name and a login key set by the user, and applies for opening a wallet service;
[0100] This step may be that the user logs in to the mobile terminal, initiates an application for opening a wallet service on the selection interface of the mobile application, and sets a user name and a login key. After receiving the user's registration application, user name, login key and other information, the mobile terminal applies for opening the wallet service.
[0101] S202: The mobile terminal sends a check instruction to check whether the wallet service is personalized;
[0102] The mobile terminal sends a check command to the wallet service acc...
Embodiment 3
[0116] Based on the above-mentioned embodiments, the method of digital identity verification based on block chain may also include the process of wallet certificate update, see Figure 4 , Figure 4 It is a schematic diagram of the wallet certificate update process, and the technical solution is as follows;
[0117] S301: When the wallet public key certificate is updated, the mobile terminal checks whether the wallet service is personalized;
[0118] When the wallet public key certificate needs to be updated, the mobile terminal checks whether the wallet service has been personalized, because there is no need to update the wallet certificate without a personalized wallet service.
[0119] S302: If yes, the mobile terminal receives the second key pair generated by the wallet service, and sends a certificate update request to the wallet service issuer;
[0120] When the wallet service has been personalized, the wallet service will regenerate a key pair, that is, a public key a...
Embodiment 4
[0128] Based on the above embodiments, the blockchain-based digital identity verification system can also include a password update process, see Figure 5 , the picture and text are the flow chart of the password update provided by the embodiment of this application, and the technical solution is as follows:
[0129] S401: When the password is updated, the mobile terminal receives the password modification application and the input old password and new password;
[0130] When the password is updated, usually when changing the password for the user, the user first logs in the mobile application through the user name and login key, and selects the interface to submit the application for modifying the password. At this time, a corresponding dialog box can appear on the interface of the mobile terminal to prompt the user to enter the old password. and new password. After receiving the password modification application, old password and new password, the mobile terminal sends rele...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com