Data processing method and device for realizing privacy protection
A privacy protection and data processing technology, applied in the field of data security, can solve problems such as leakage of user privacy, leakage of user privacy, illegal raw sensor data, etc., and achieve the effects of ensuring user privacy security, high availability, and preventing leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The solutions provided in this specification will be described below in conjunction with the accompanying drawings.
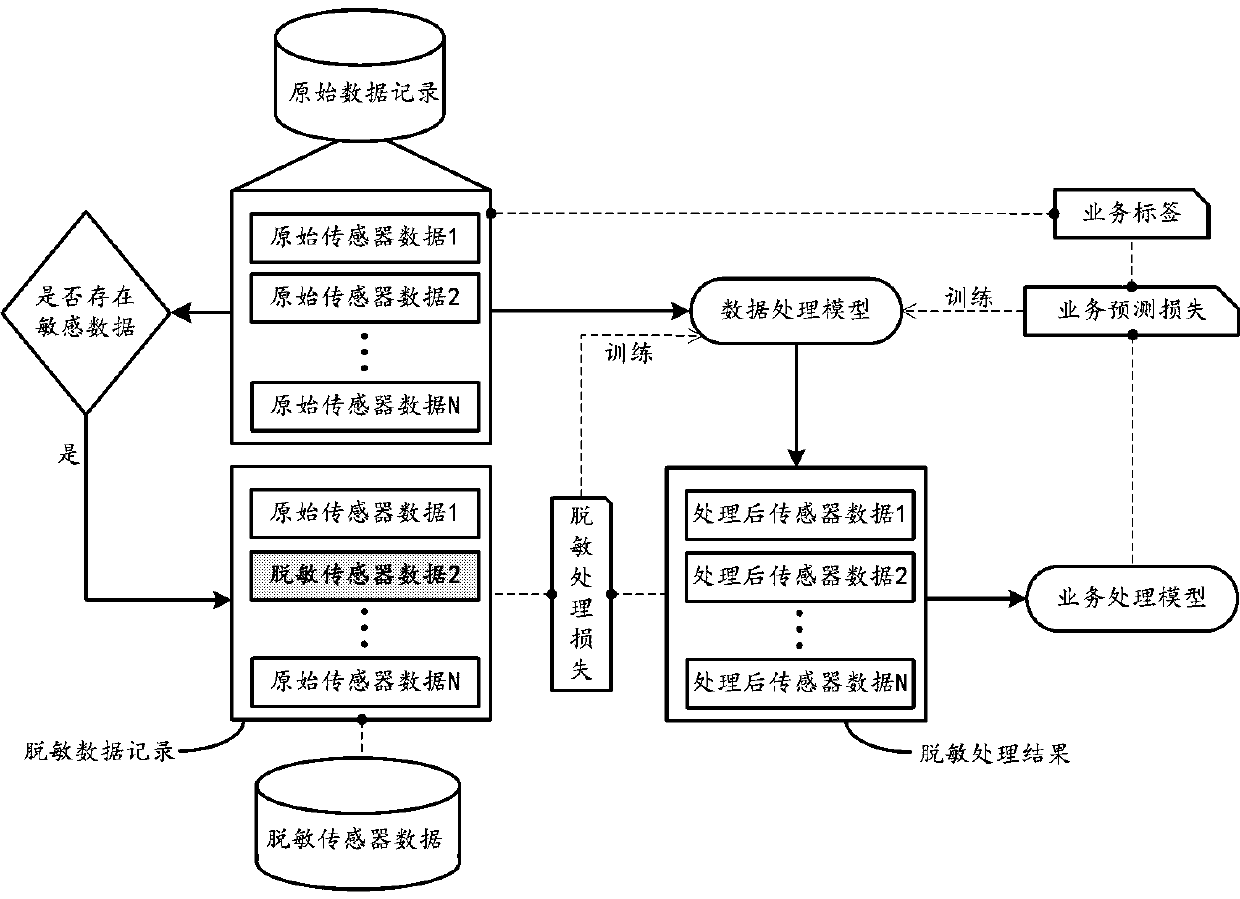
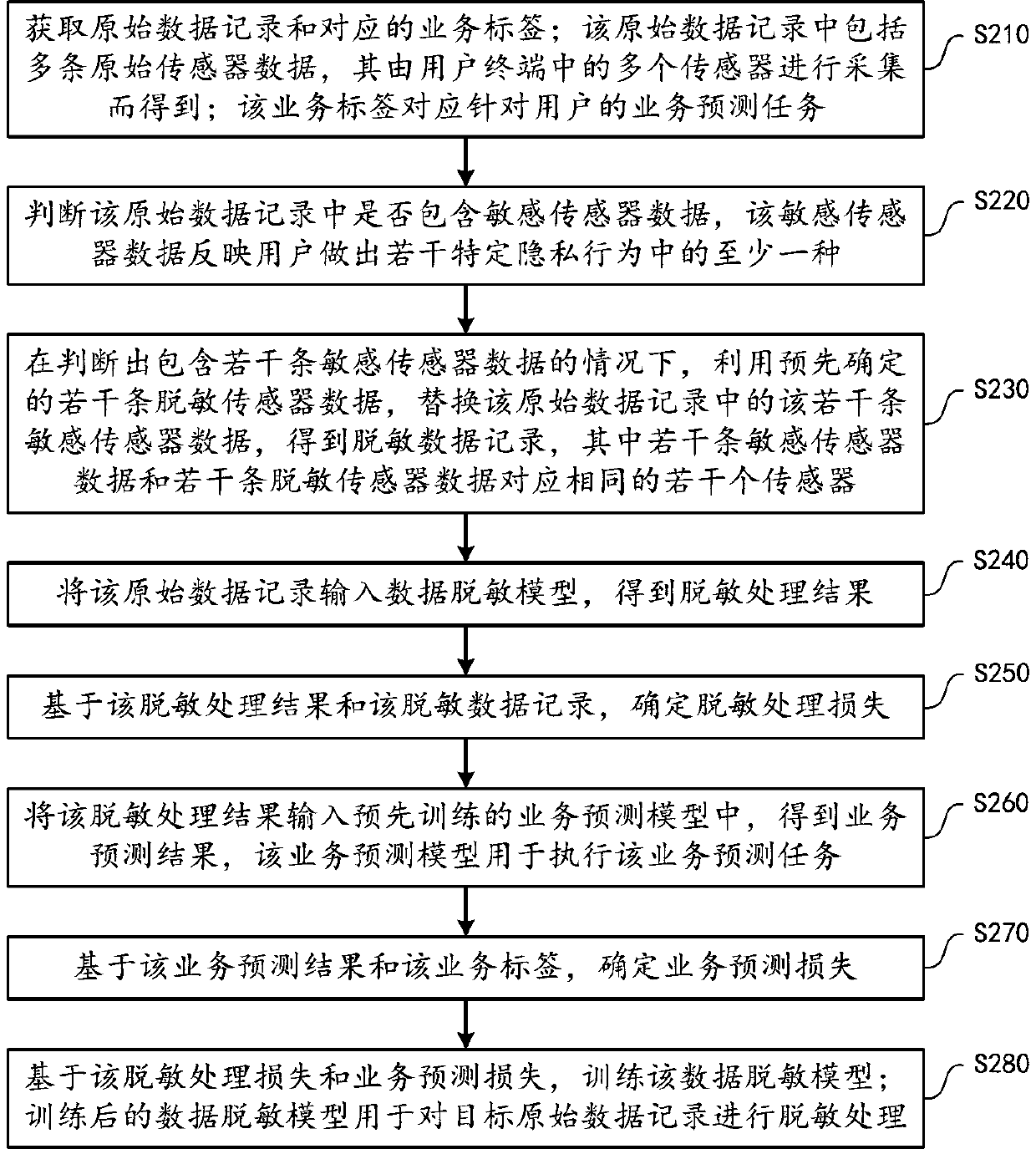
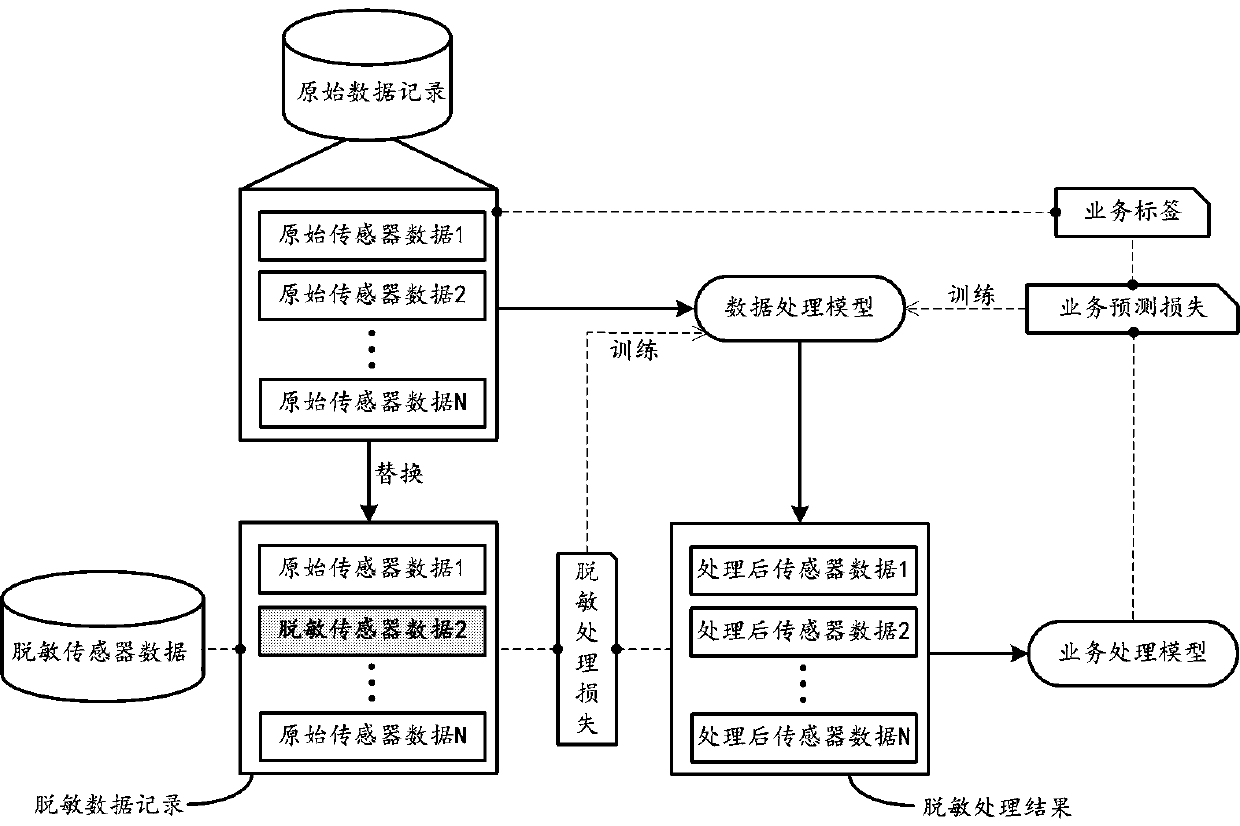
[0030] The embodiment of this specification discloses a data processing method for realizing privacy protection. By desensitizing raw sensor data, the protection of user-specific private information can be realized. Specifically, with the rise of machine learning, the inventor thought that machine learning technology can be applied to the technical field of data privacy and security, by training a machine learning model for desensitizing raw sensor data (hereinafter referred to as data desensitization sensitive model) to protect data privacy.
[0031] figure 1 A diagram showing a training implementation architecture diagram of a data desensitization model according to an embodiment, such as figure 1 As shown, for multiple sensors included in the user terminal ( figure 1 N is shown in , N is an integer greater than 1), each sensor performs data collect...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com