Phase-cut Fourier transform based image hiding method, image restoring method and image encrypted transmission method
A technology of Fourier transform and inverse Fourier transform, which is applied in the field of image encryption and information security research, can solve the problems of incomplete restoration of information and large amount of calculation, and achieve improved hiding and restoration efficiency, small amount of calculation, and increased The effect of practicality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
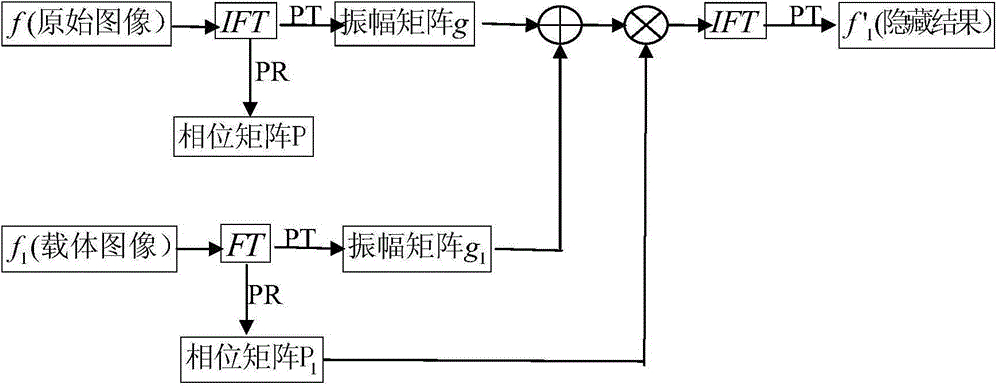
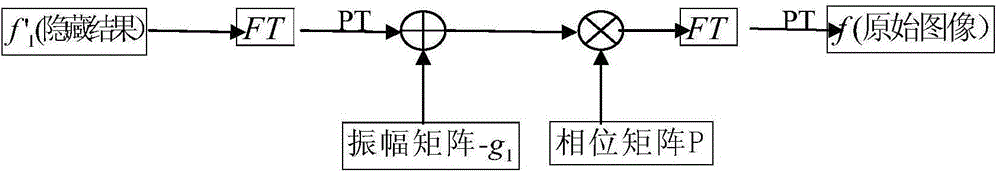
[0044] The image hiding method based on phase-cut Fourier transform in this embodiment can be found in figure 1 , including the following steps:
[0045] (1) Two grayscale images of known size M*N, the normalized grayscale value matrix is f, f respectively 1 , where f is the image to be hidden, f 1 as the carrier image.
[0046] (2) F(x,y)=IFT[f(u,v)] can be obtained from the image f(u,v) to be hidden through inverse Fourier transform, and F(x,y) is a complex value, which can be Expressed as Then after phase truncation (that is, extracting the amplitude matrix) and phase preservation (that is, extracting the phase matrix) to get:
[0047] g(x,y)=PT{IFT[f(u,v)]}=|F(x,y)|,
[0048]
[0049] Among them, g(x, y) is the amplitude after phase truncation, and P(x, y) is the retained phase, which is used as the decryption key when restoring.
[0050] (3) by the carrier image f 1 (x, y) after Fourier transform, can get F 1 (u,v)=FT[f 1 (x,y)], and then through phase trunca...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com