Multi-image optical hiding system based on visual password
A visual cryptography and multi-image technology, applied in the field of multi-image hiding systems, can solve the problems of high cost and high production cost of diffractive optical elements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] The present invention will be further described below in conjunction with the accompanying drawings and specific examples.
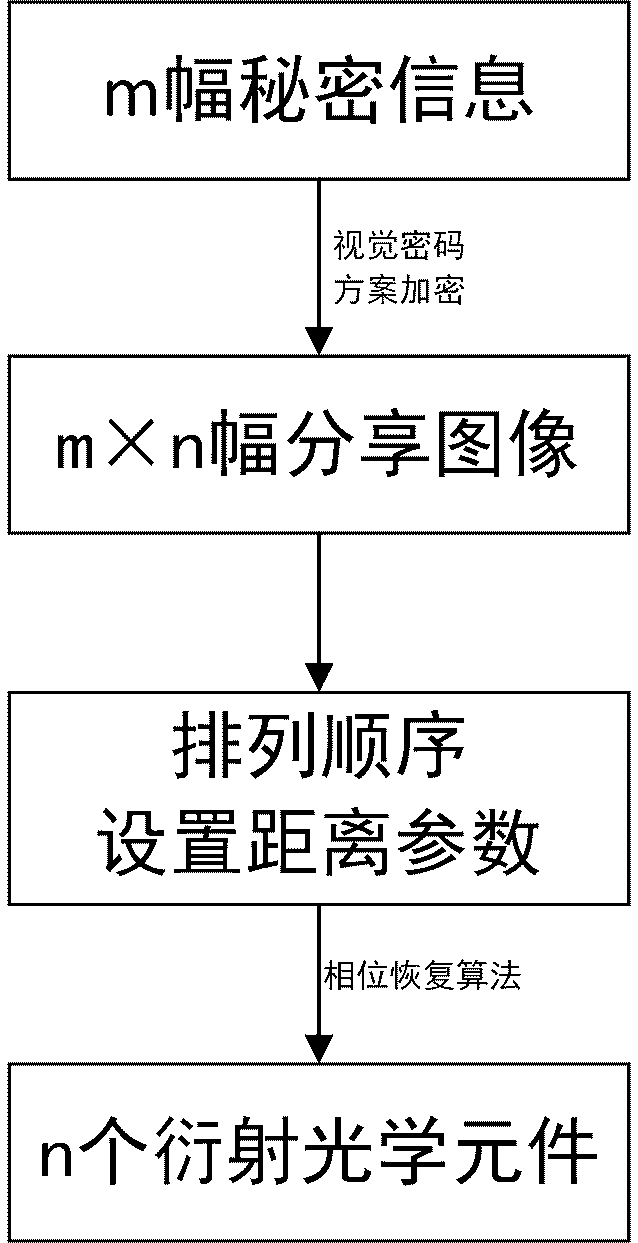
[0028] The four images in Figure 4 are used as secret information.
[0029] Use the visual cryptography scheme to encrypt the secret information. The visual cryptography scheme has a variety of encoding schemes. Here, the relatively simple "(2,2)-visual cryptography scheme" is used as an example to obtain 8 shared images, as shown in Figure 5.
[0030] Divide the shared images into two groups and sort them, and set the diffraction distance as z1=200mm, z2=400mm, z3=600mm, z4=800mm.
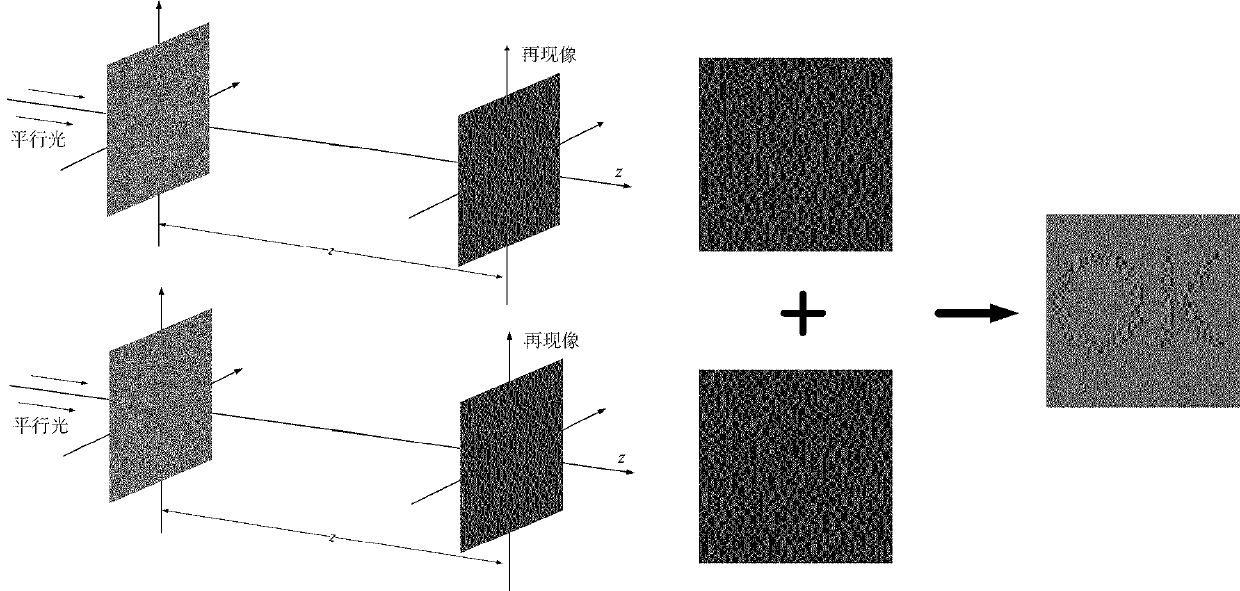
[0031] The phase information of the two diffractive optical elements is calculated using the GS algorithm, as shown in Figure 6.
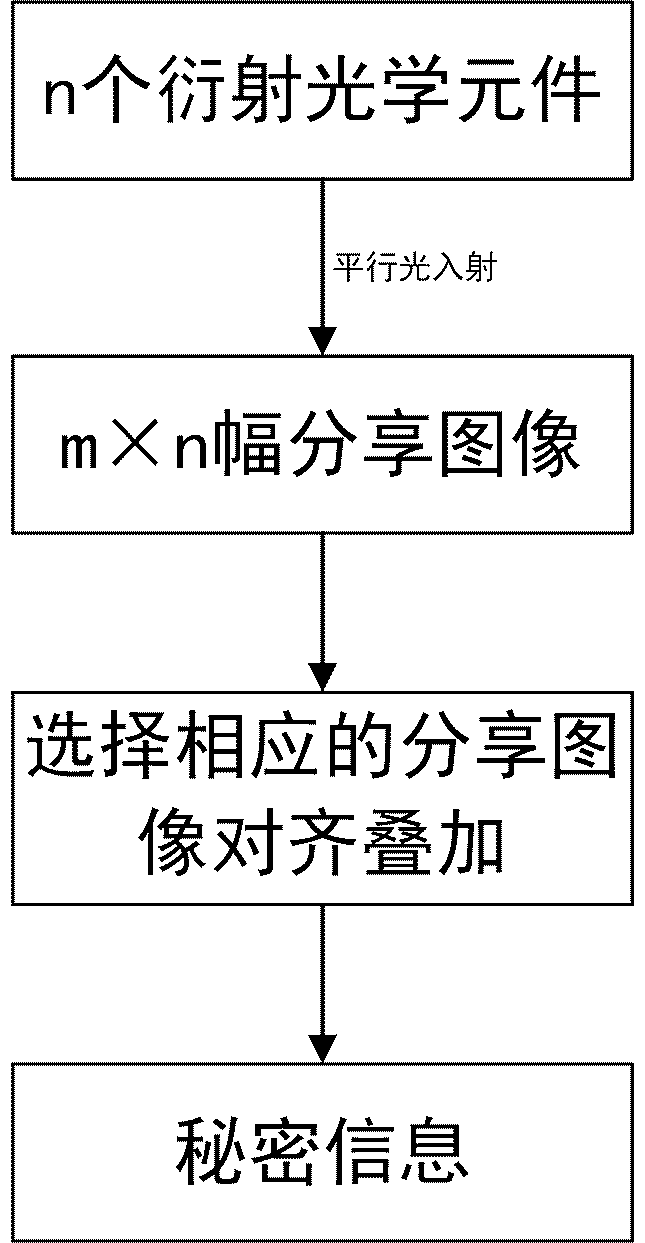
[0032] When decrypting, parallel light is used to irradiate two diffractive optical elements, and multiple shared images can be reproduced in the rear, as shown in Figure 7, and the corresponding shared images are aligned and superimposed...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com