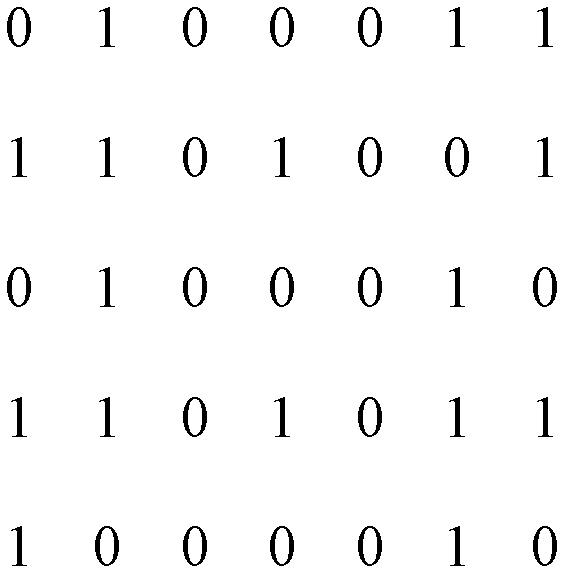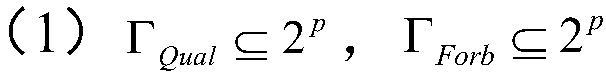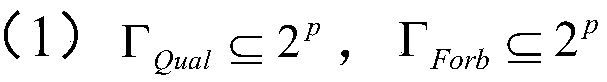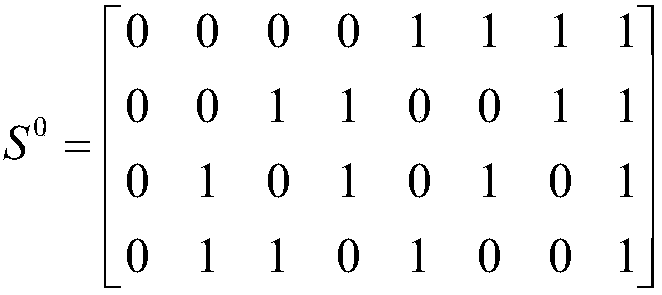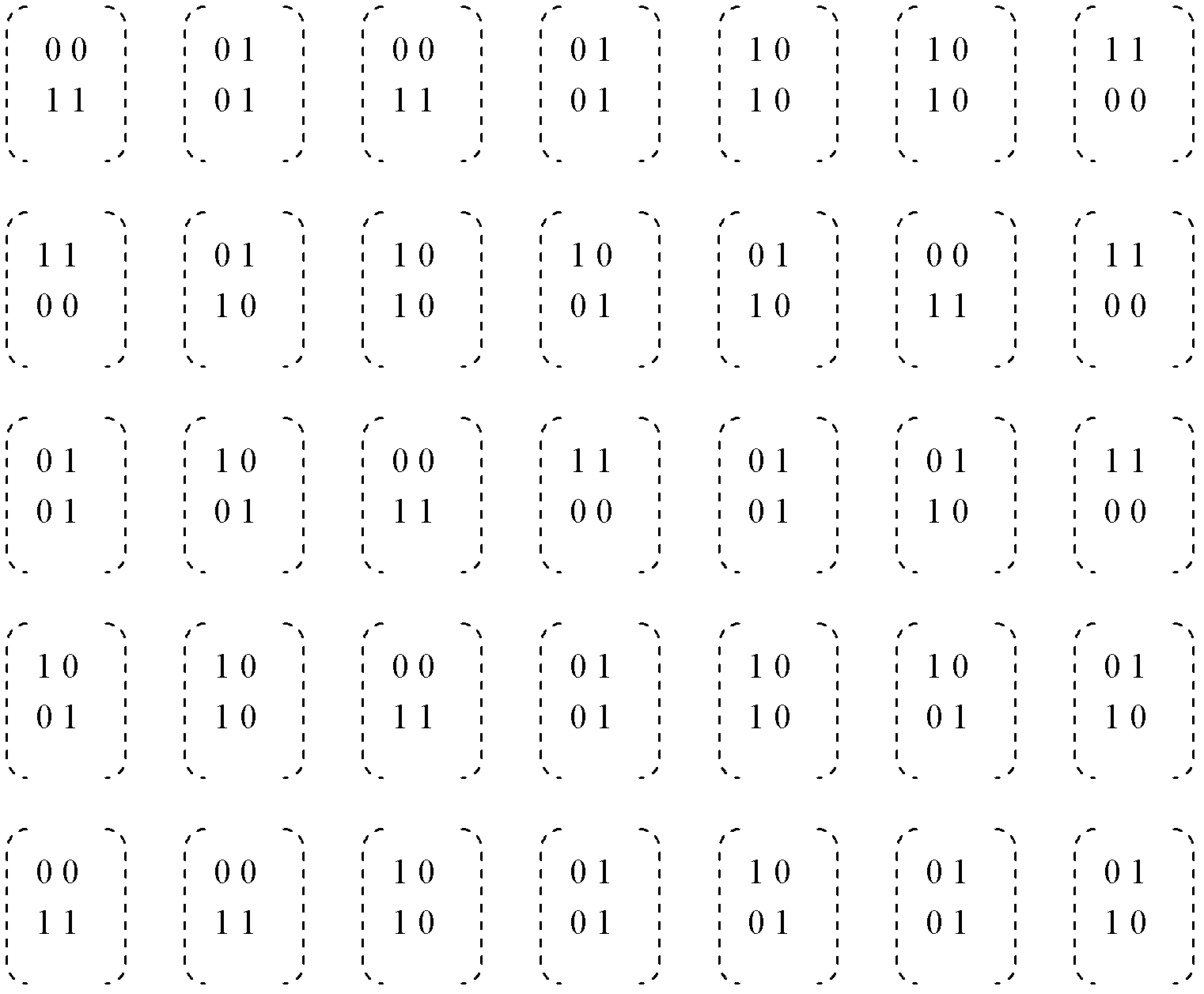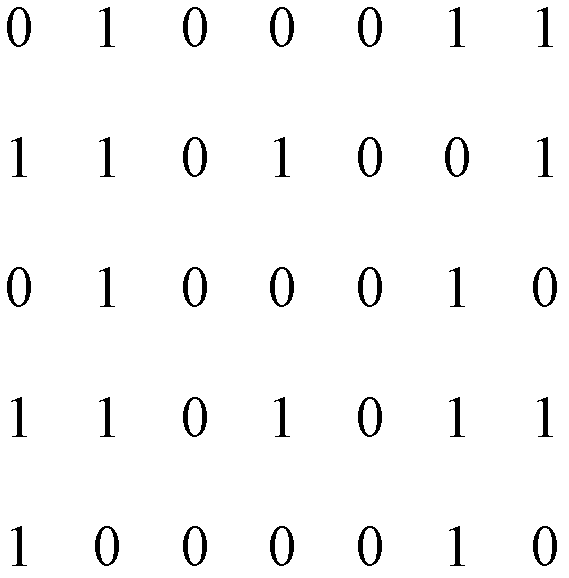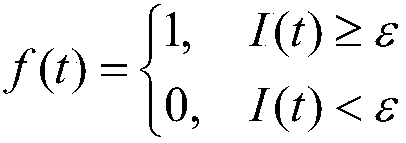Patents
Literature
40 results about "Visual cryptography" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
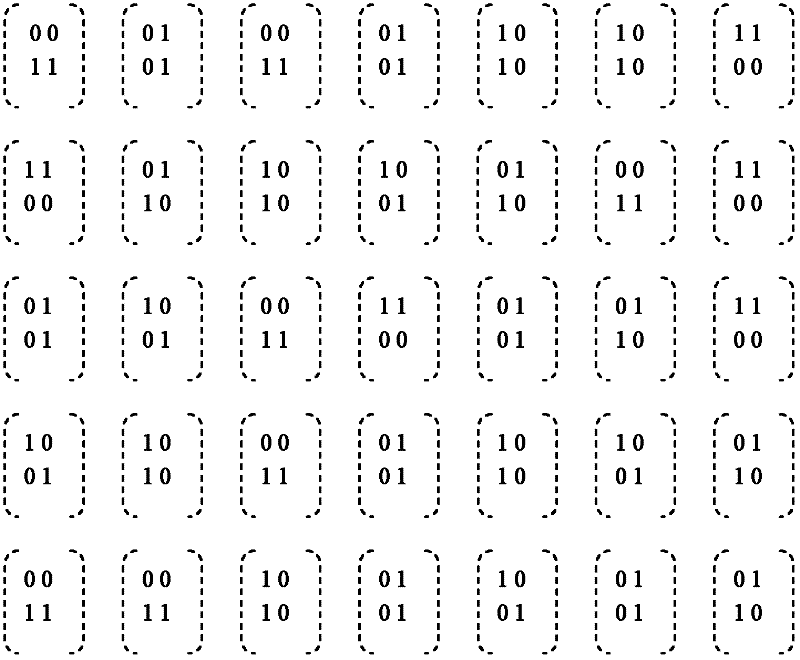
Visual cryptography is a cryptographic technique which allows visual information (pictures, text, etc.) to be encrypted in such a way that the decrypted information appears as a visual image. One of the best-known techniques has been credited to Moni Naor and Adi Shamir, who developed it in 1994. They demonstrated a visual secret sharing scheme, where an image was broken up into n shares so that only someone with all n shares could decrypt the image, while any n − 1 shares revealed no information about the original image. Each share was printed on a separate transparency, and decryption was performed by overlaying the shares. When all n shares were overlaid, the original image would appear. There are several generalizations of the basic scheme including k-out-of-n visual cryptography.
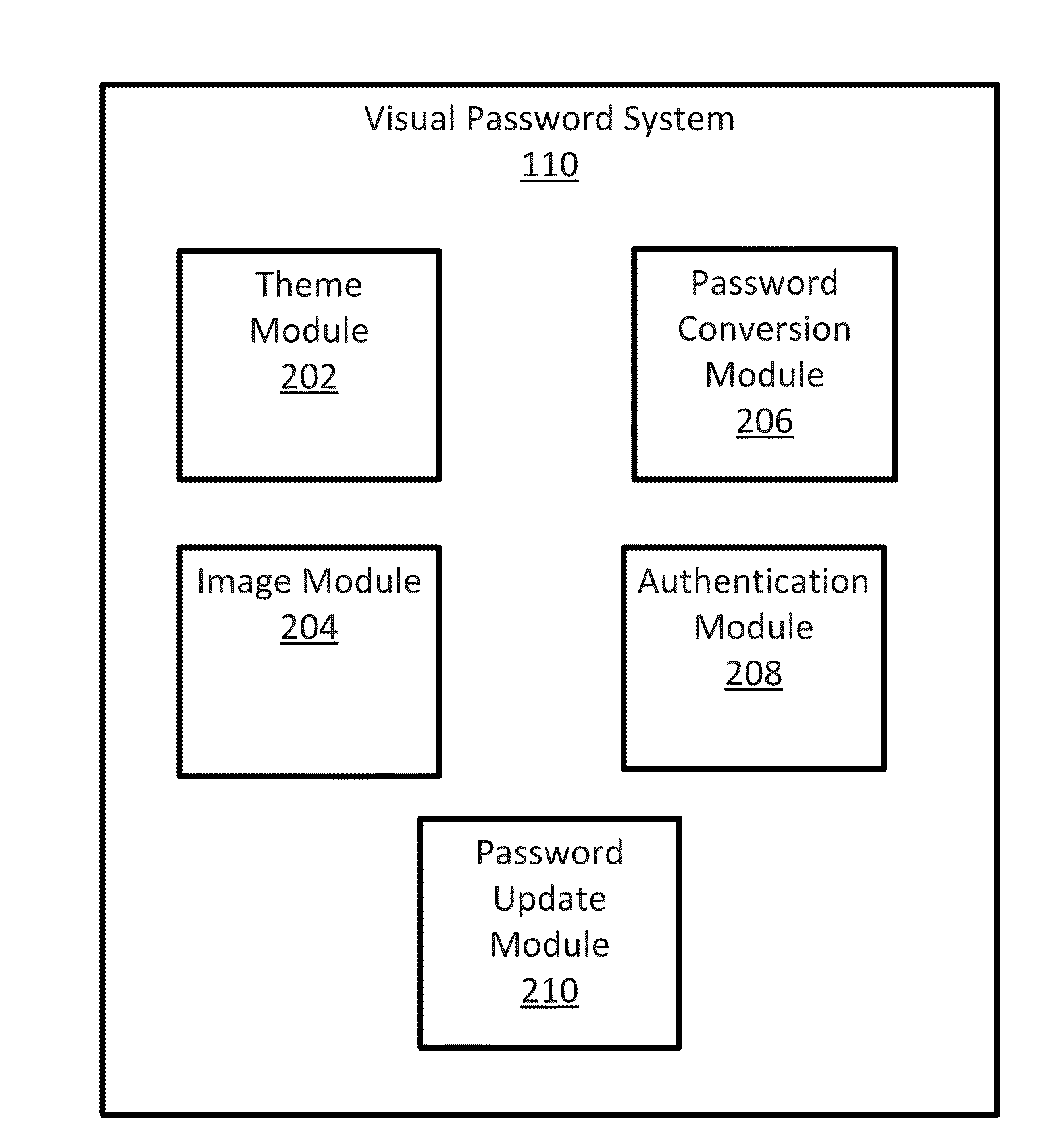
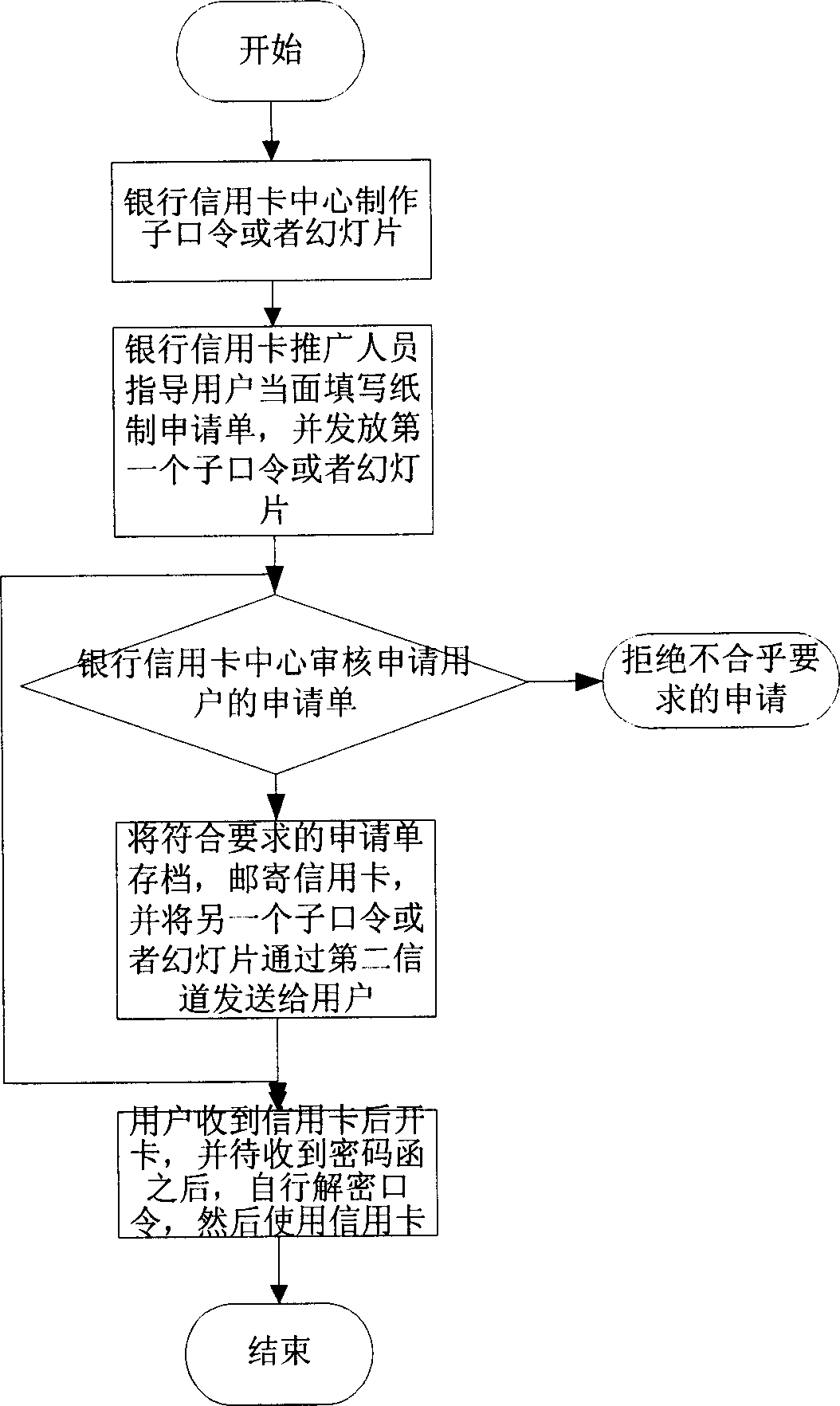
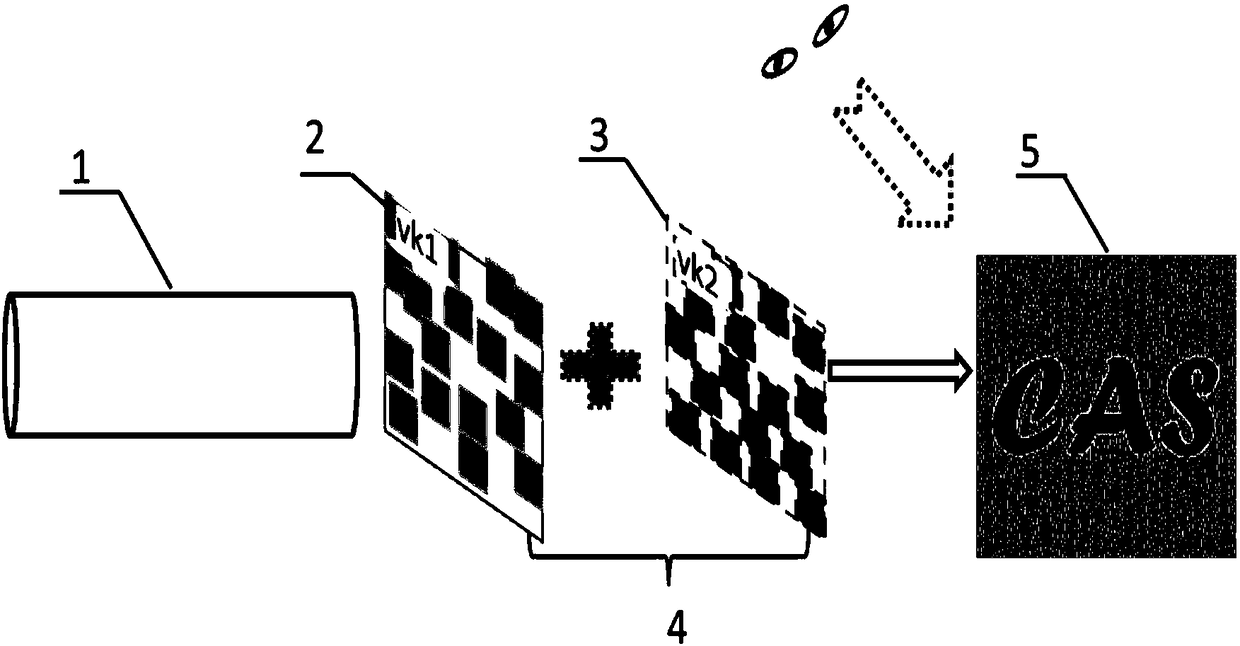
System For And Method Of Generating Visual Passwords
ActiveUS20150178490A1Digital data processing detailsMultiple digital computer combinationsGraphicsGraphical user interface
Systems and methods for creating a visual password are presented. A user having an account or profile is given the option to create a visual password via a graphical user interface. The interface displays a plurality of themes to the user, wherein each theme represents a category of images. The user selects a theme and is presented with a plurality of images within the category. The user selects one or more images in a certain order to create a visual password. The selected images and order of selection are saved as the user's visual password. When the user later attempts to electronically access his account, the user will be required to select the correct pictures in the correct sequence in order to access his account.
Owner:CELLCO PARTNERSHIP INC +1
Method for visual cryptography and counterfeit prevention of patterns
InactiveCN101447071ADifficult to forgeEasy to identifyStampsLight effect designsExclusive orVisual perception
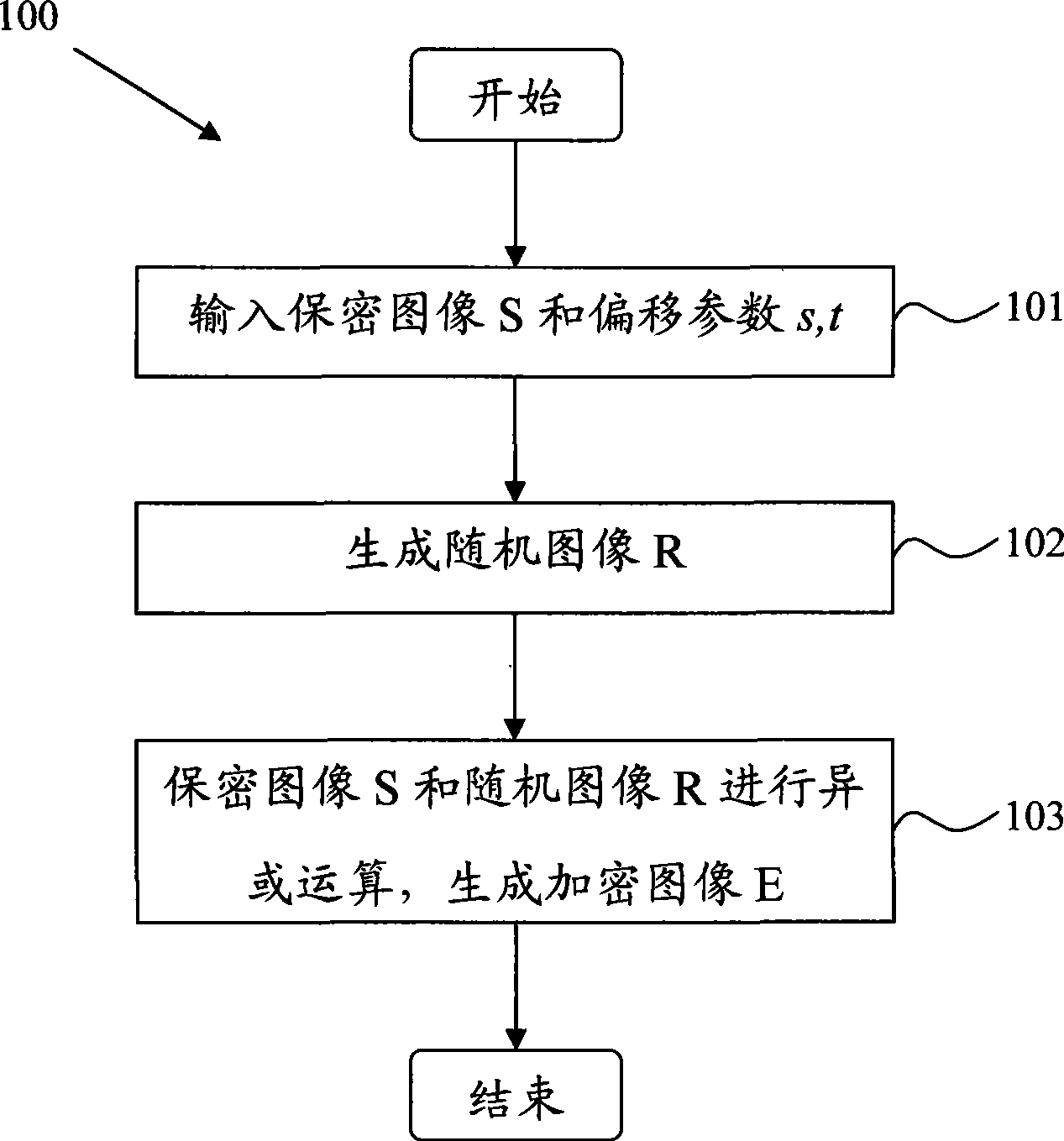
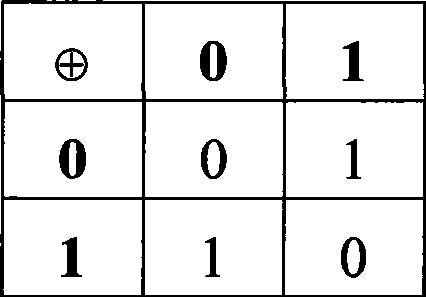
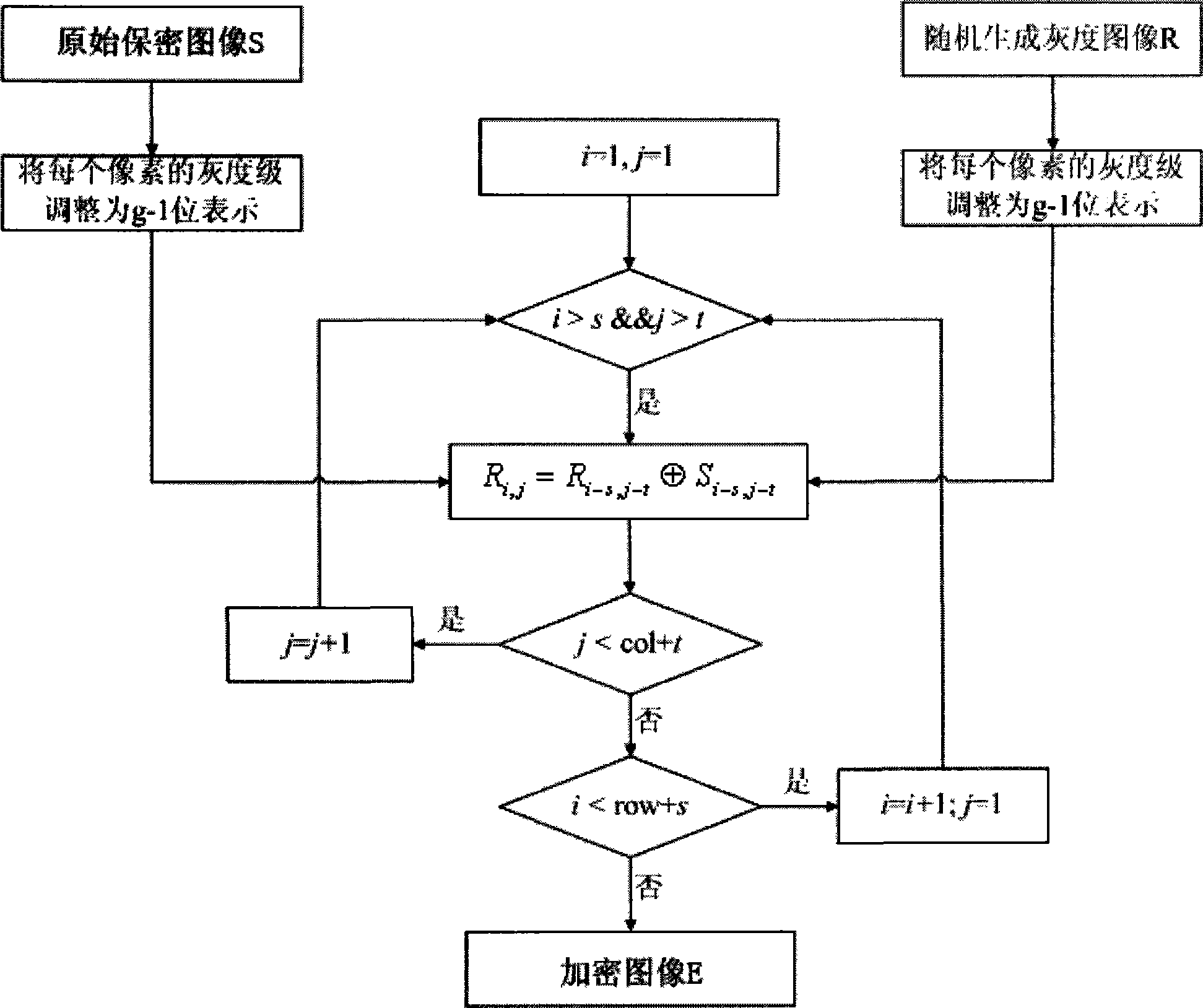
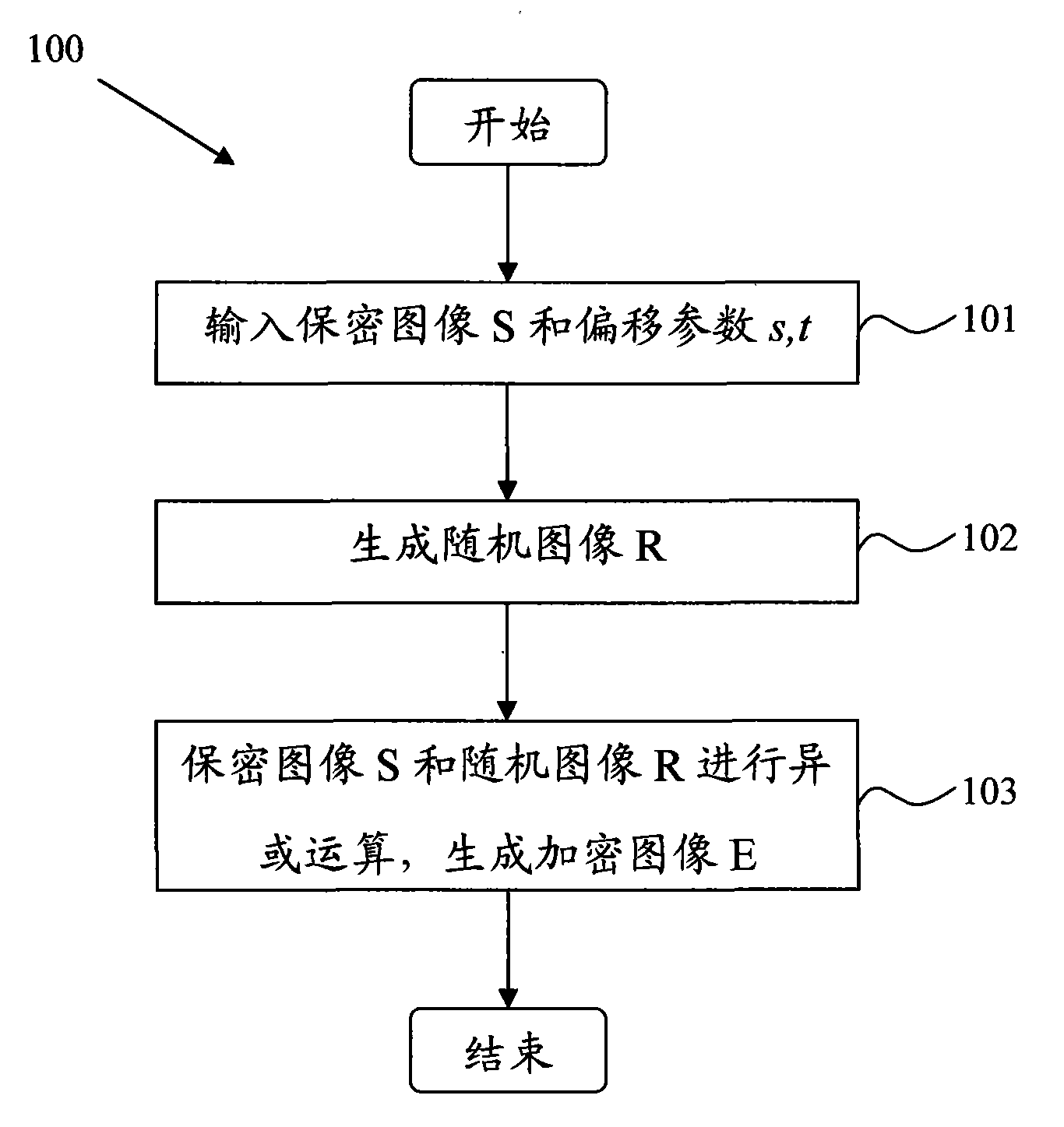
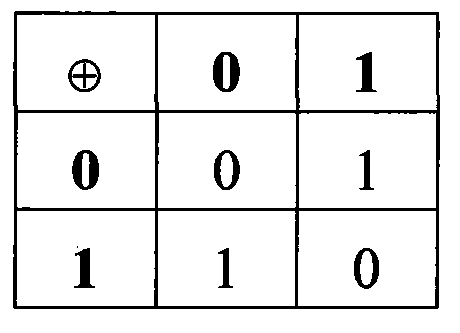
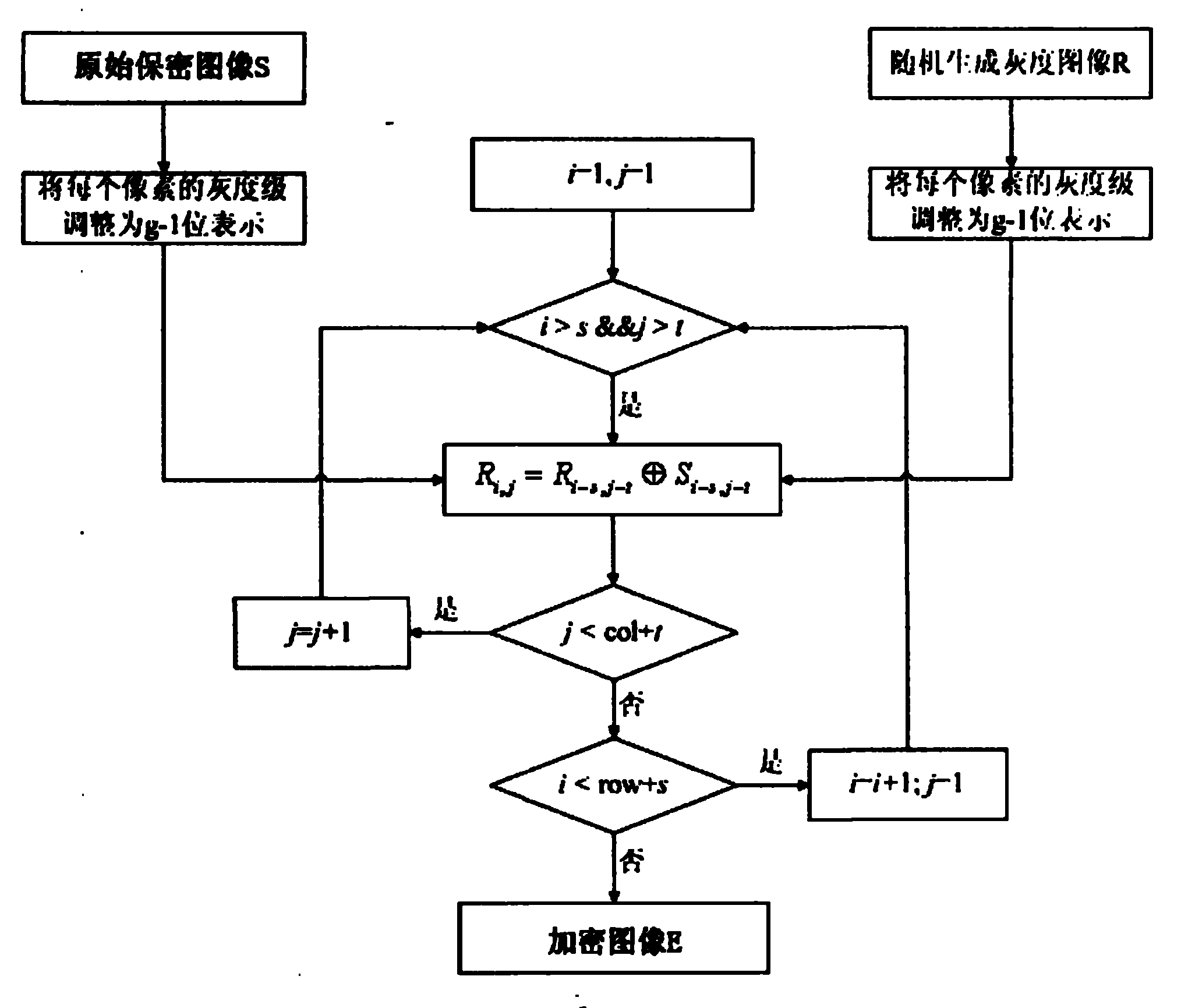
The invention discloses a visual cryptography and counterfeit prevention method for hiding and maintaining encrypted image information. The visual cryptography and counterfeit prevention method for patterns comprises the following steps: inputting a confidential image S and migration parameters s and t; randomly generating a grey image R; and subjecting the confidential image S and the random image R to the Exclusive-OR operation to generate an encrypted image E, wherein the encrypted image E contains information of the confidential image S. The confidential image S hidden in the encrypted images E is restored by superposing two encrypted images E, thereby achieving the effect of counterfeit prevention. The visual cryptography and counterfeit prevention method for patterns is incorporated with rectangular or arc-shaped anti-counterfeiting icons to form counterfeit-prevention elements which are applied to the data carriers such as counterfeit-prevention files and negotiable securities. The counterfeit-prevention algorithm has the characteristics of easy identification, high difficulty in counterfeiting and the like.
Owner:TSINGHUA UNIV
Display method and display device of peeping-preventing visible code
ActiveCN103177226AImprove satisfactionWaste less timeInternal/peripheral component protectionProgramming languageUser input
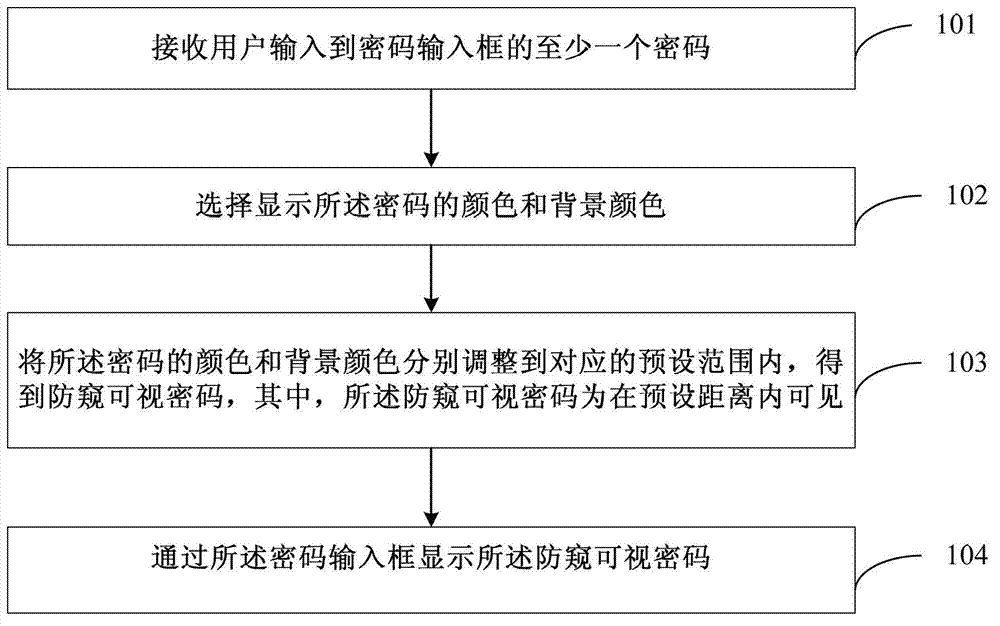
An embodiment of the invention discloses a display method and a display device of a peeping-preventing visible code. The method includes receiving at least one code input into a code input box by a user; selecting and displaying a color of the code and a background color; respectively adjusting the color of the code and the background color into a preset range, and obtaining the peeping-preventing visible code which is visible in a preset distance range; and displaying the peeping-preventing visible code through the code input box. As the user can see the correctness of the input code when inputting the code, if the user finds wrong inputting, the user can correct the code immediately, the problem that a wrong code is submitted to cause time waste is resolved, and meanwhile safety of the code is improved. Meanwhile, as the input code only can be seen at short range, and the code cannot be seen clearly at a long distance, a certain function of code peeping prevention is achieved.
Owner:ALIBABA (CHINA) CO LTD
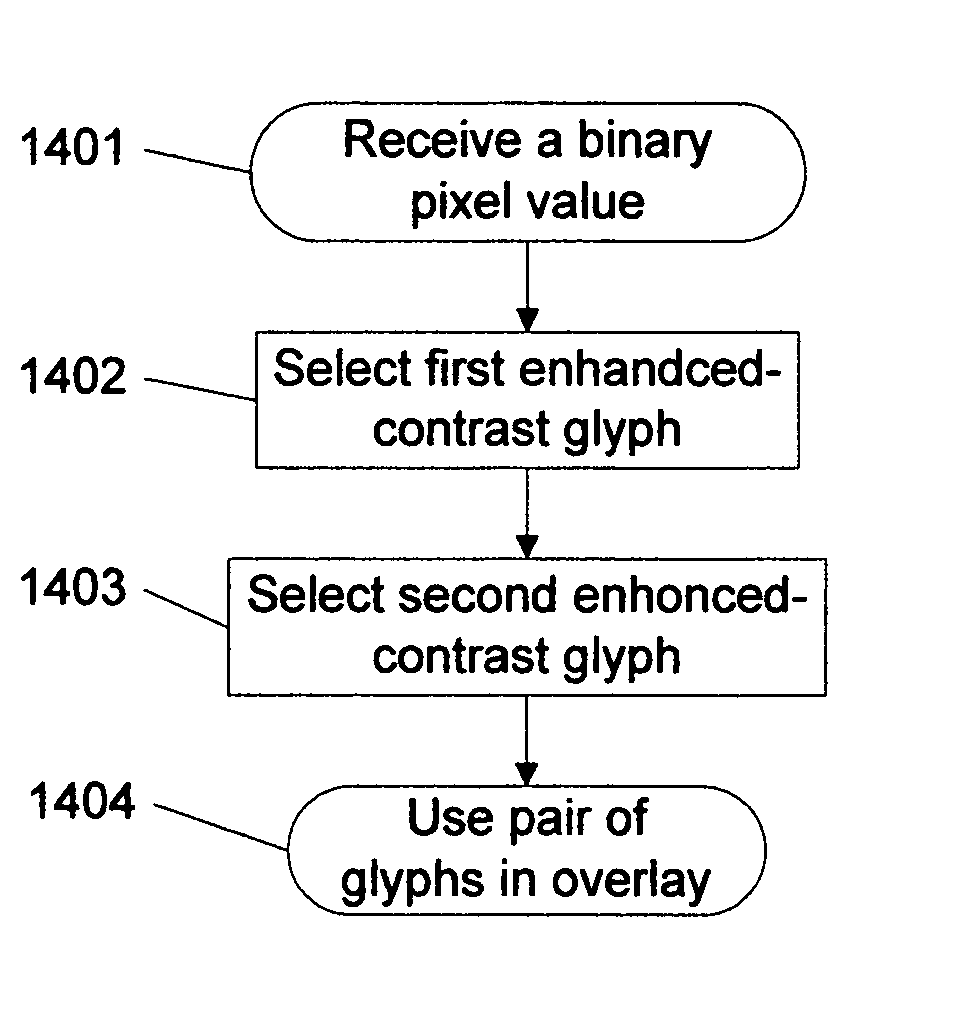
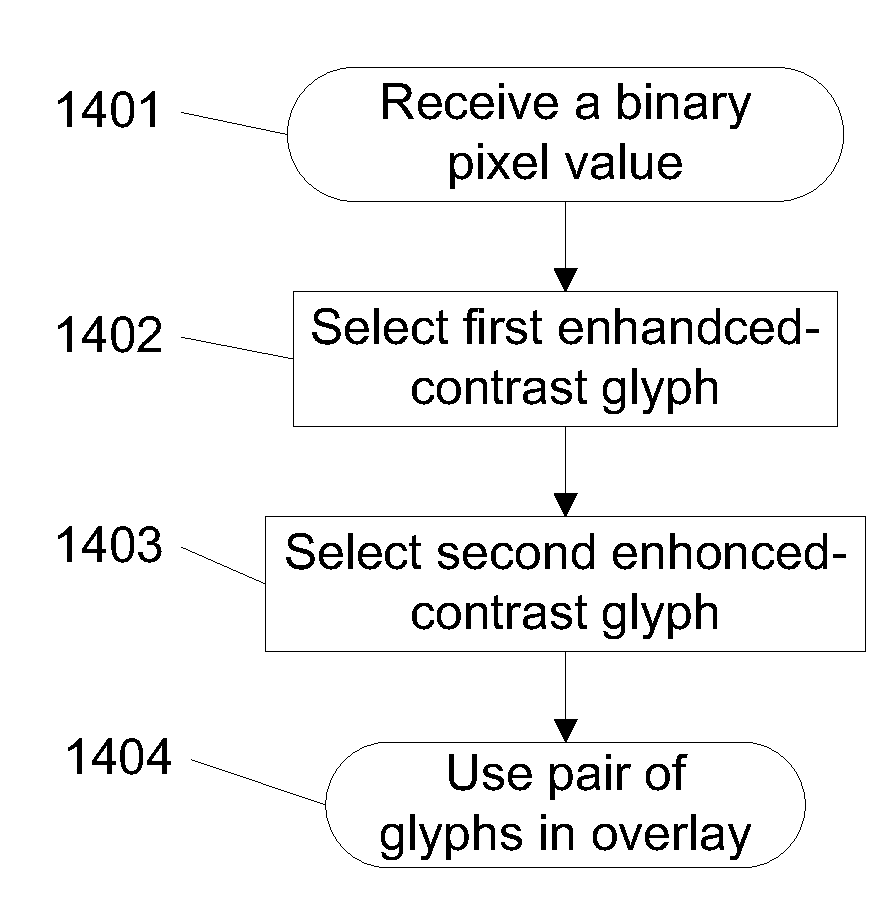
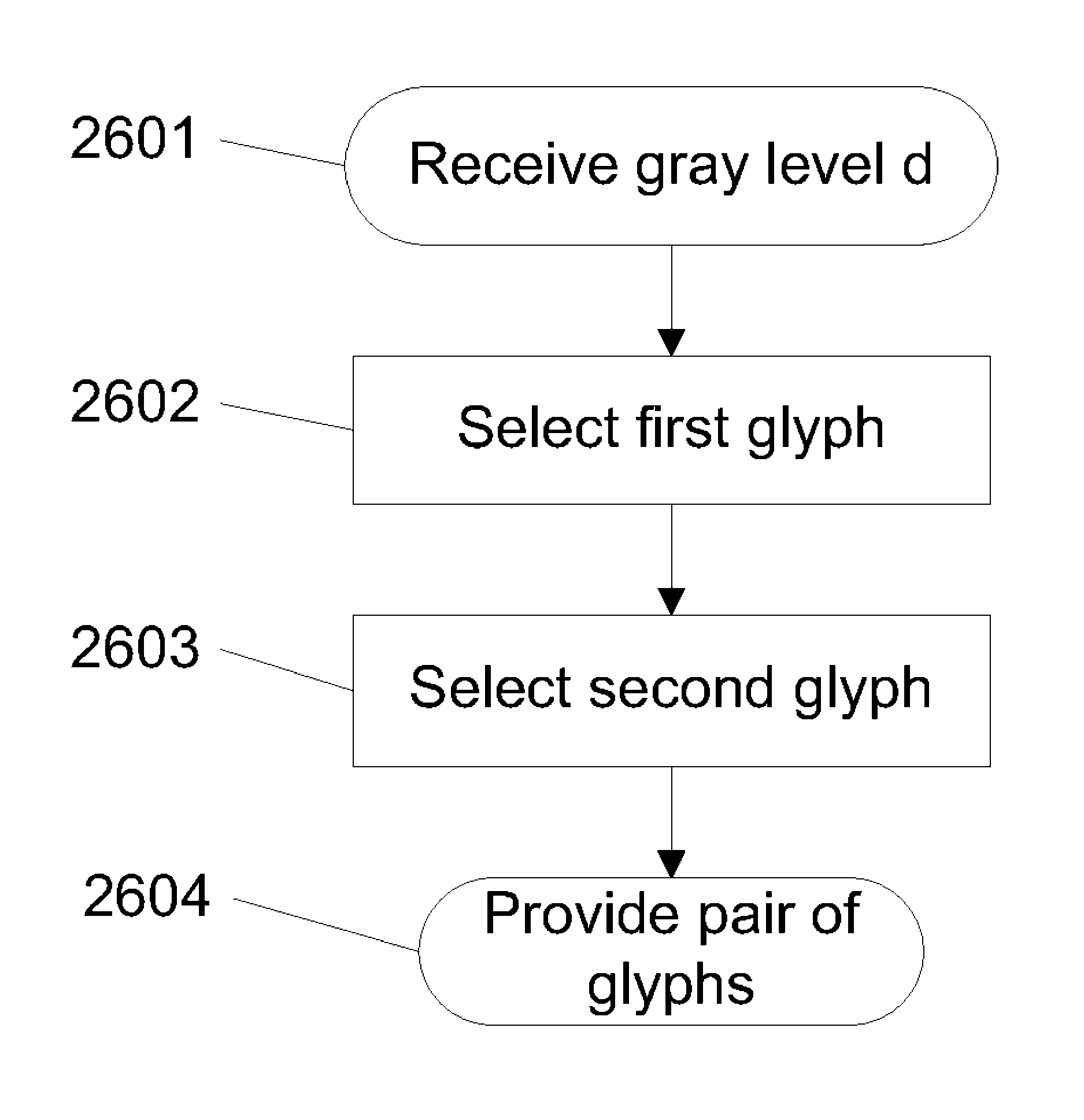
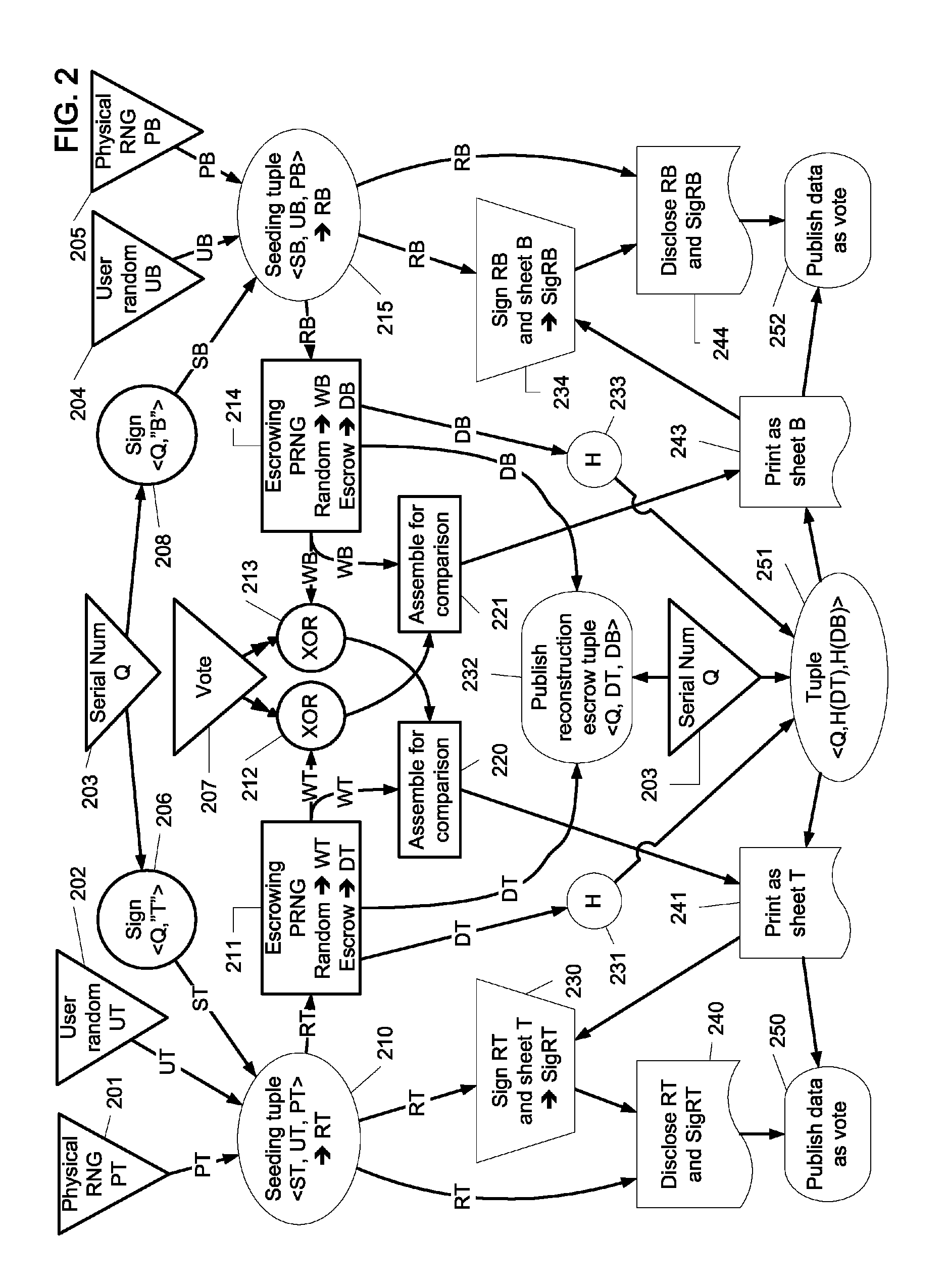
Visual cryptography and voting technology using a pair of enhanced contrast glyphs in overlay
In some embodiments, techniques for voting and visual cryptography may include various enhancements.
Owner:ROSKIND JAMES A DR
Extension visual encryption and decryption method
InactiveCN104574262ANot easy to attract attentionReduce computational complexityImage data processing detailsError diffusionImage sharing
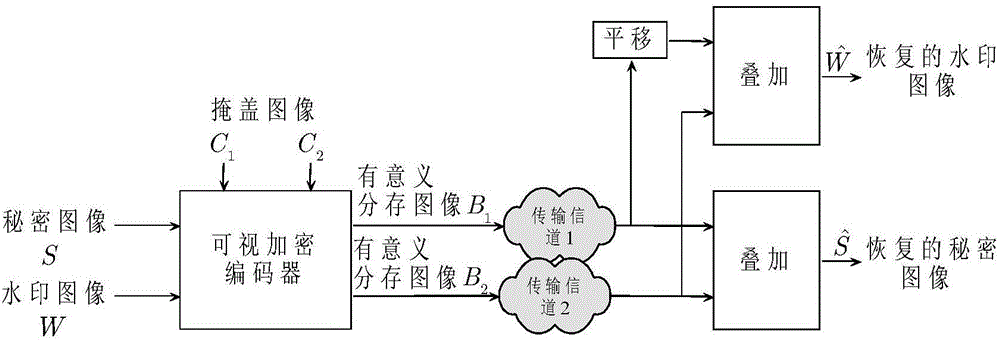
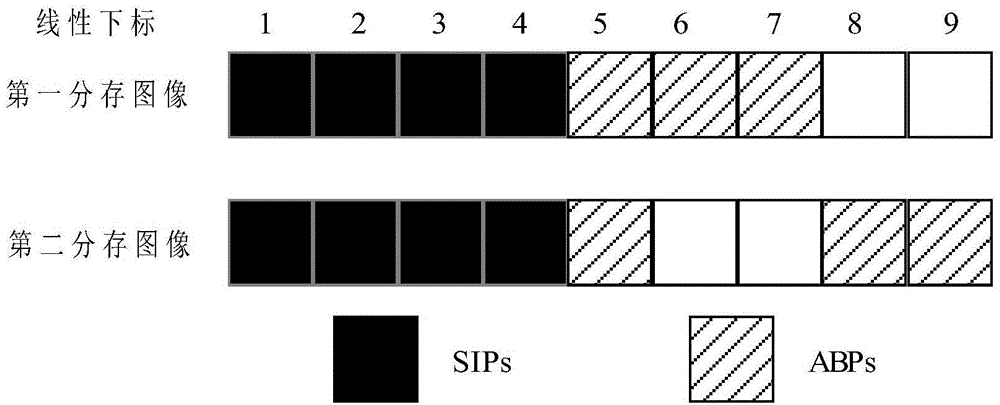
The invention discloses an extension visual encryption and decryption method. In the extension visual encryption process, a cover image is chunked first, and pixels in each block are divided into secret information pixels, auxiliary black pixels and common pixels; then (2,2) lines of a visual cryptography fundamental matrix are filled at the position of secret information, share images are divided into four areas, and secret images and watermark images are sequentially embedded into the four areas; at last, limited error diffusion is used for incorporating the characteristics of the cover image. In the extension visual decryption process, the two share images are overlaid in a staggered mode, and watermarks are recovered; then the two images align to each other to recover secret images. The extension visual encryption and decryption method has the advantages that image sharing is meaningful, the dimension is not extended, decryption does not need a computer, a tampering authentication function is achieved, and the recovered secrete images and the watermarks can be free of interference of the cover images at the same time.
Owner:SHANDONG UNIV OF SCI & TECH
Identity authentication method based on visual cryptography
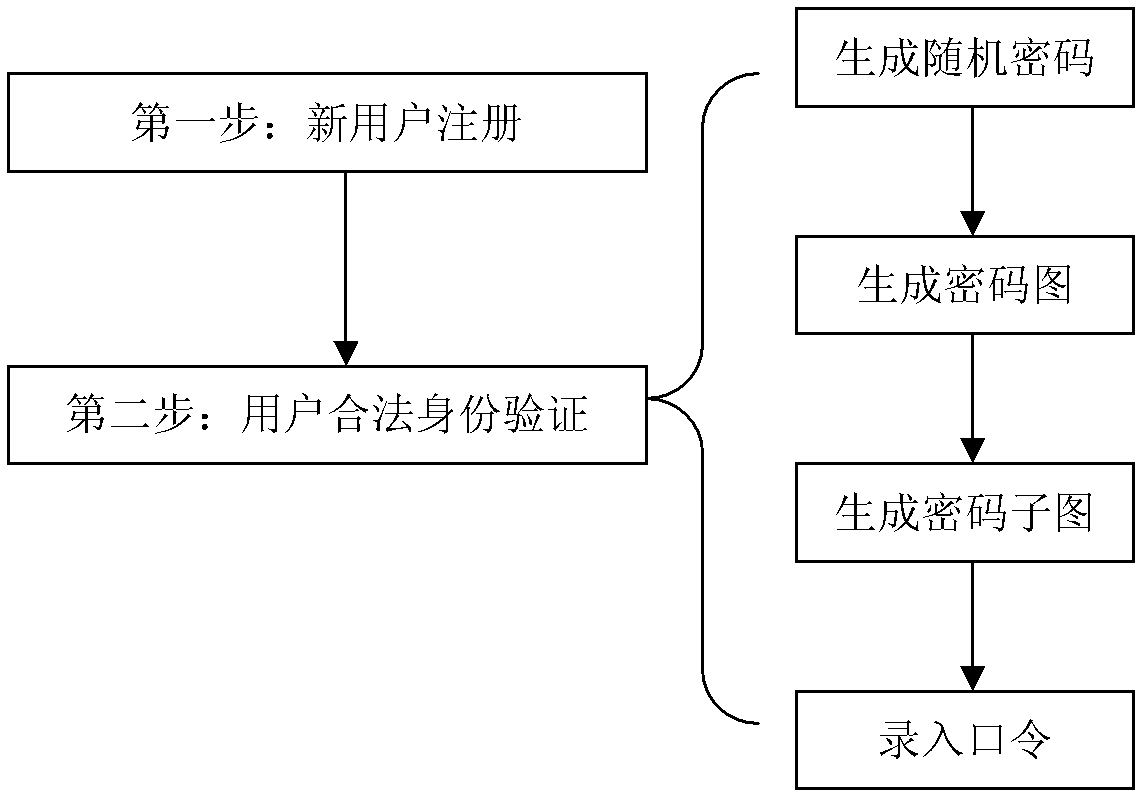
InactiveCN102340402ARealize dynamic passwordUncertainUser identity/authority verificationImage data processing detailsUser needsPassword
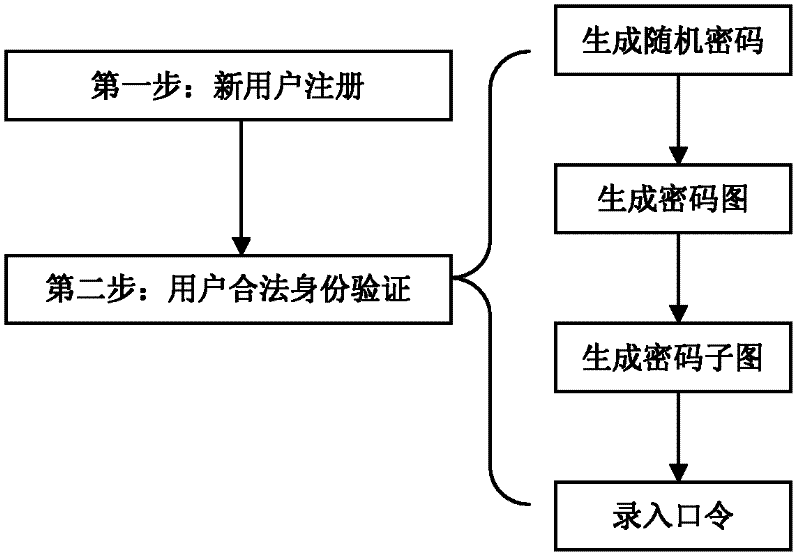
The invention provides an identity authentication method realizing a dynamic password encryption mode. The technical scheme comprises the following steps of: I, registering a new user, generating a mask picture M of the new user, and storing the other information and the mask picture M of the new user in a database as the registration information of the new user; II, authenticating the legal identity of the user; if the identity of any user needs authentication, executing the following steps: (1) generating a random cipher; (2) generating a cipher picture; (3) generating a cipher sub-picture;and (4) entering passwords to prove whether the user to be authenticated is a registered user. The invention has the beneficial effects that dynamic passwords can be realized, the decryption mode is simple, and the security is high. In spite of dynamic passwords, cipher transfer is not involved in the authentication process, thus the security is further improved.
Owner:NAT UNIV OF DEFENSE TECH
Picture delivering system based on visual cryptography and related computer program product
ActiveUS20140177836A1Improve securityImprove convenienceComputer security arrangementsCoding/ciphering apparatusComputer graphics (images)Display device
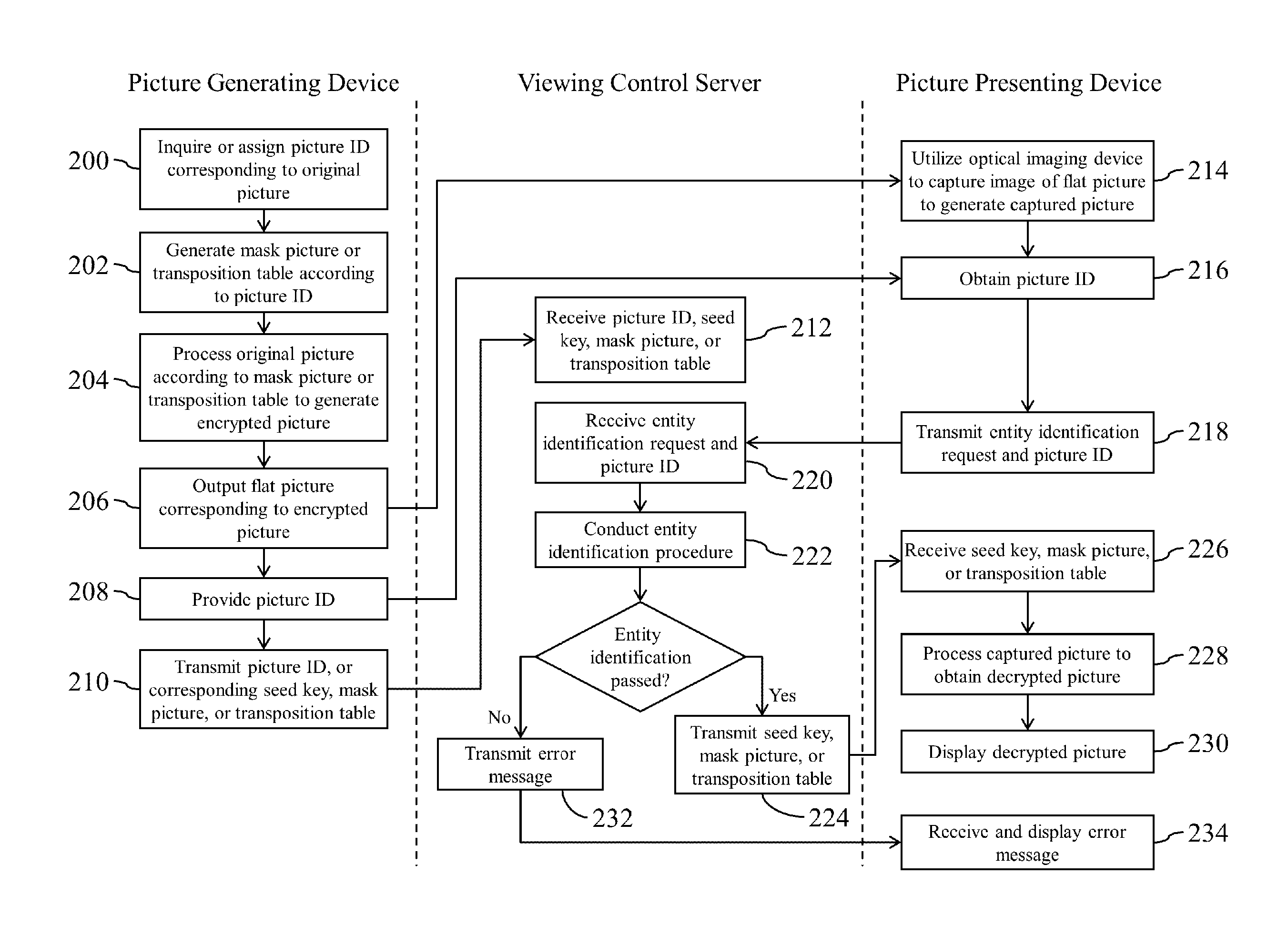
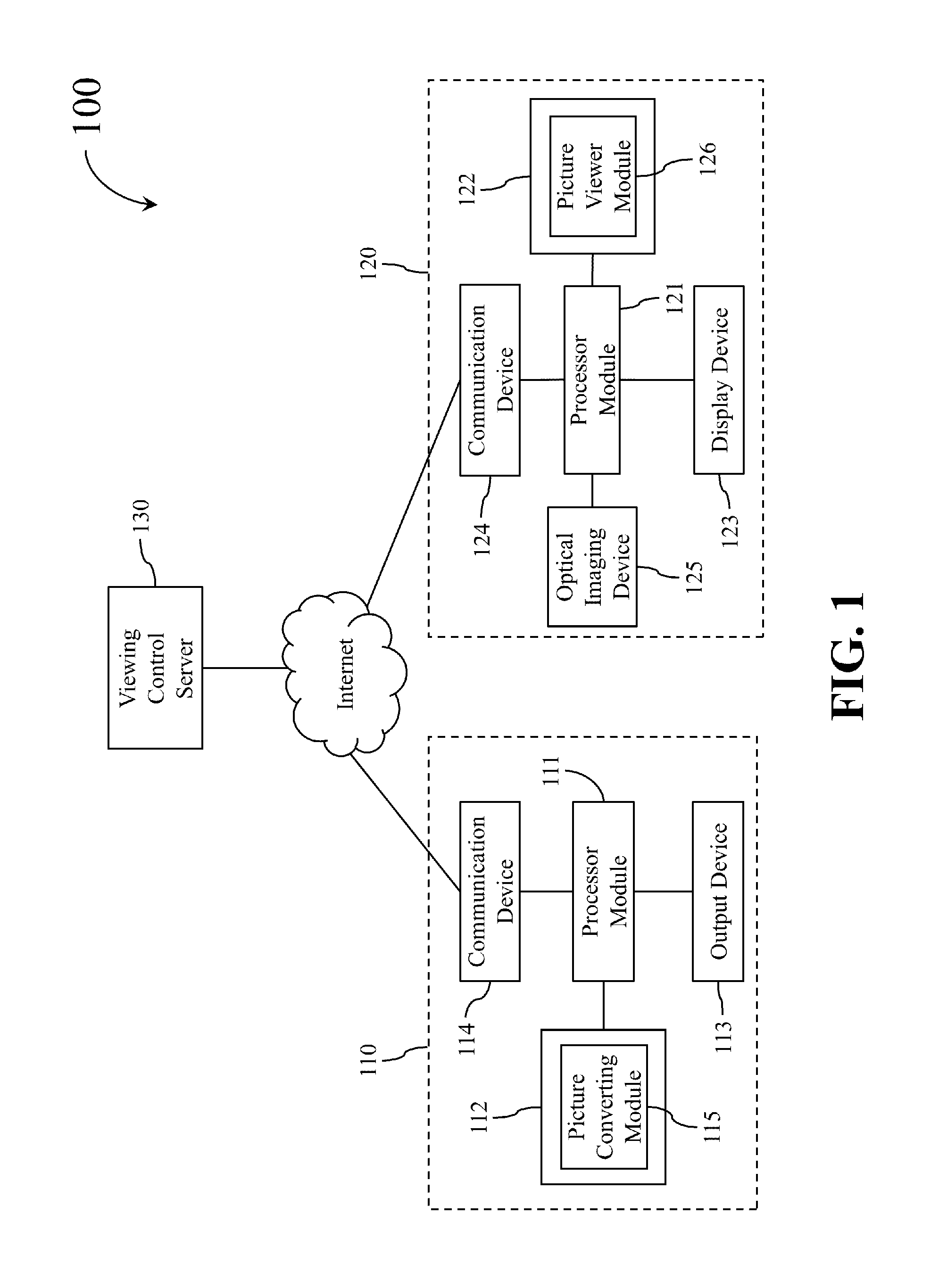
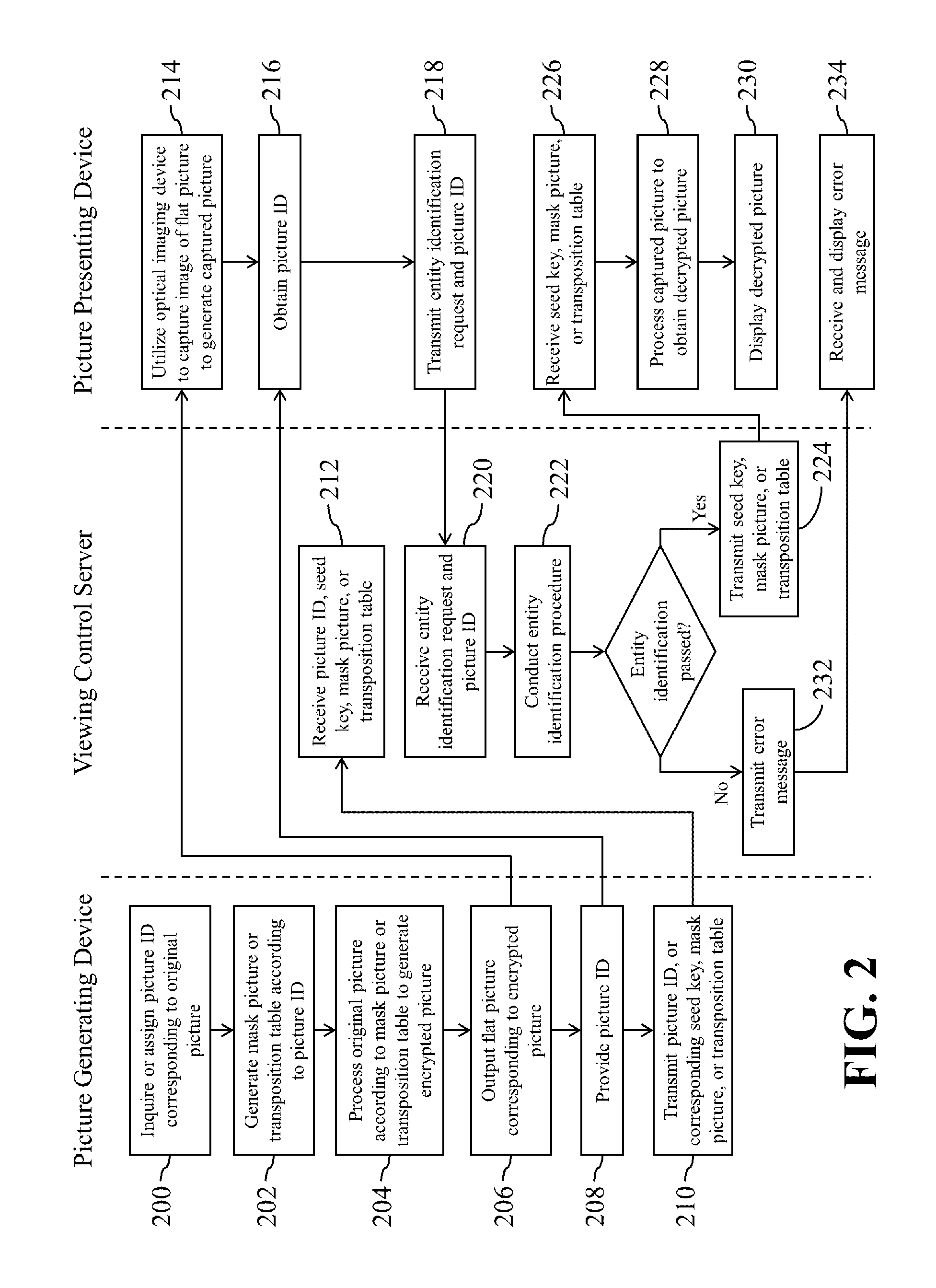
A picture delivering system is disclosed including: a picture generating device for outputting a flat picture corresponding to an encrypted picture and for providing a picture ID corresponding to the encrypted picture; and a picture presenting device for utilizing an optical imaging device to capture an image of the flat picture to generate a captured picture, for obtaining the picture ID, and for transmitting the picture ID to the picture generating device. When the picture presenting device passed an entity identification procedure, the picture presenting device obtains a decryption information, processes the captured picture according to the decryption information to obtain a decrypted picture, and then utilizes a display device to display the decrypted picture. The decryption information comprises at least one of a seed key, a mask picture, and a transposition table corresponding to the picture ID.
Owner:JRSYS INT
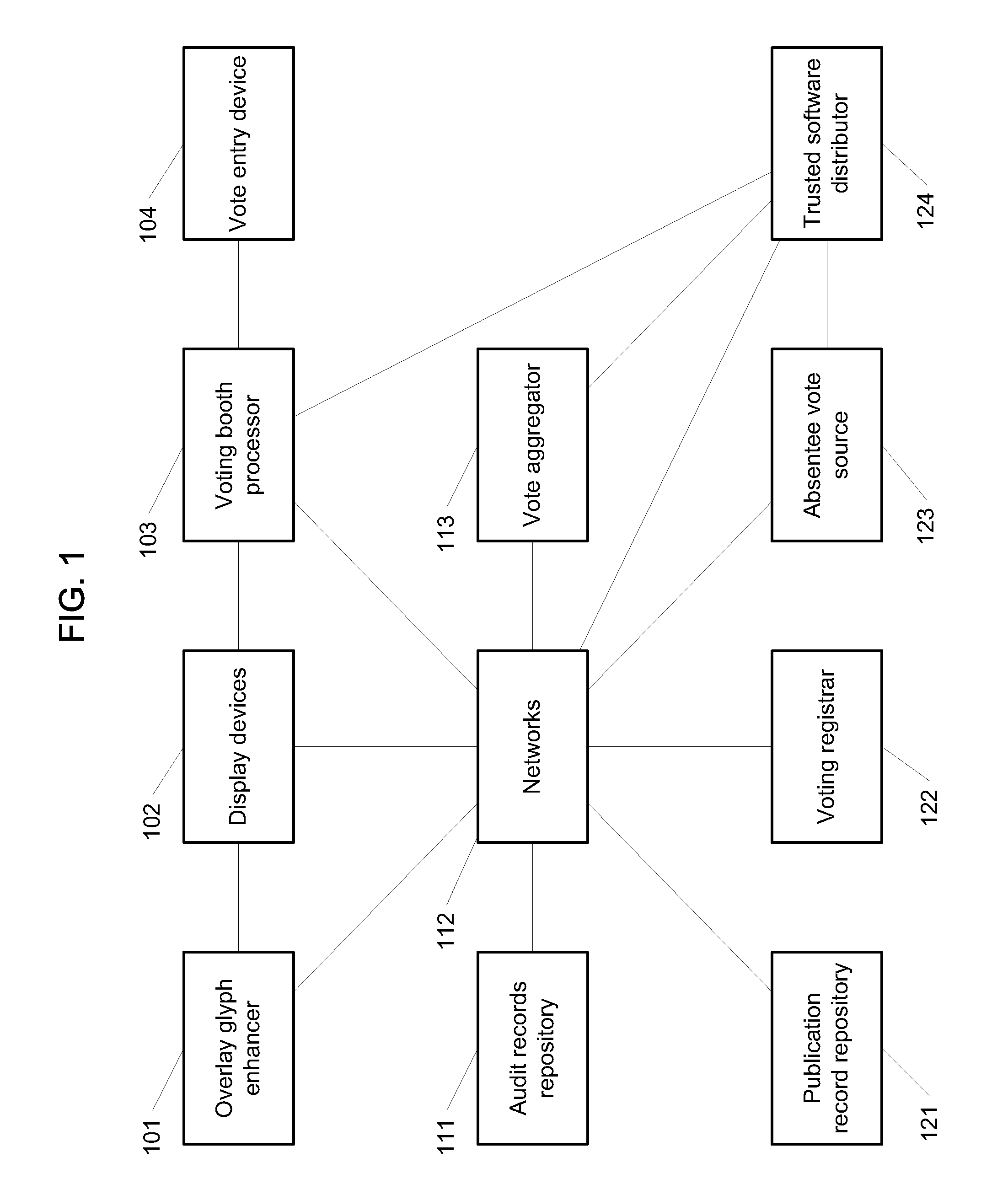
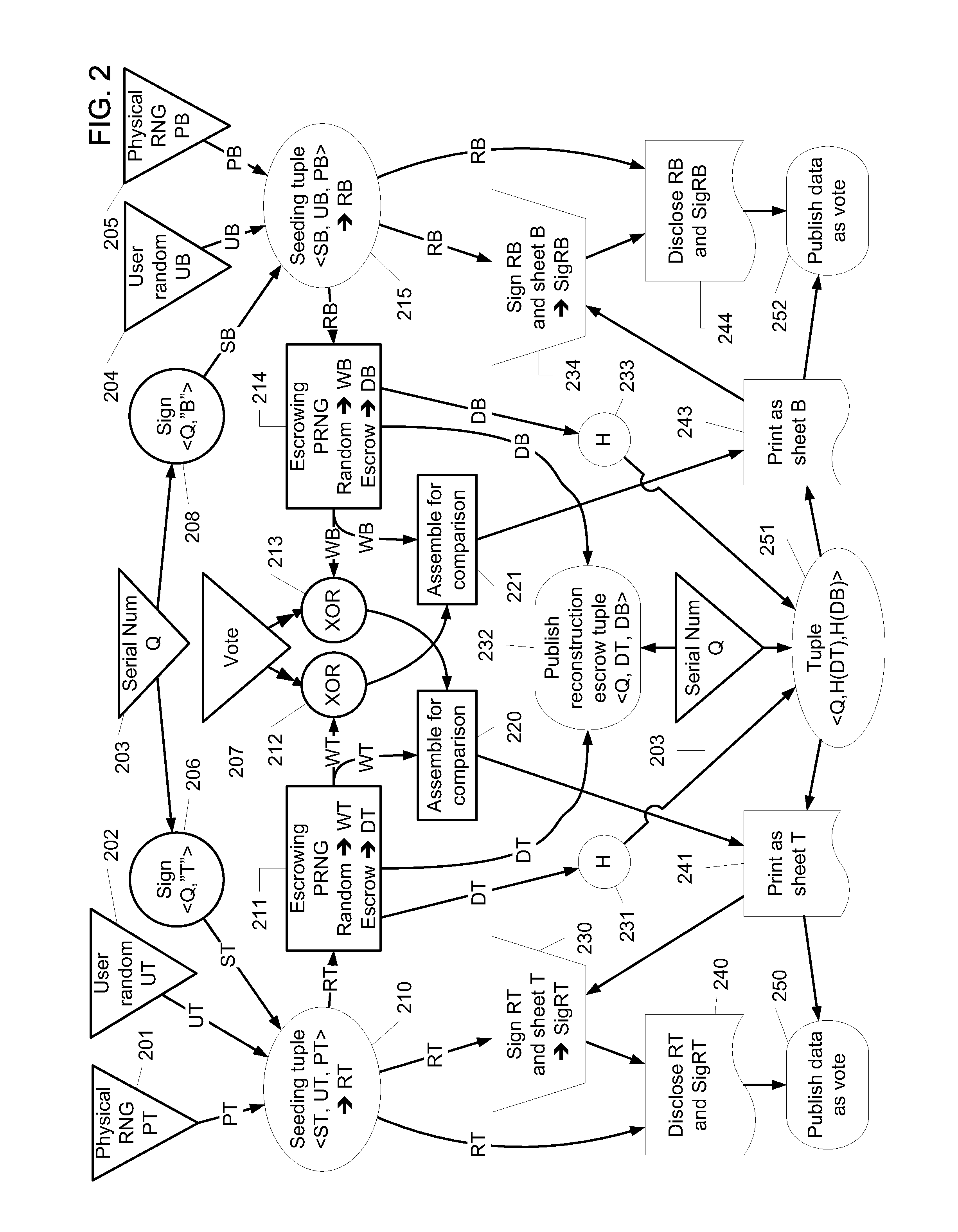
Visual cryptography and voting technology
ActiveUS20100142005A1Voting apparatusDigitally marking record carriersVisual perceptionComputer science
In some embodiments, techniques for voting and visual cryptography may include various enhancements.
Owner:ROSKIND JAMES A
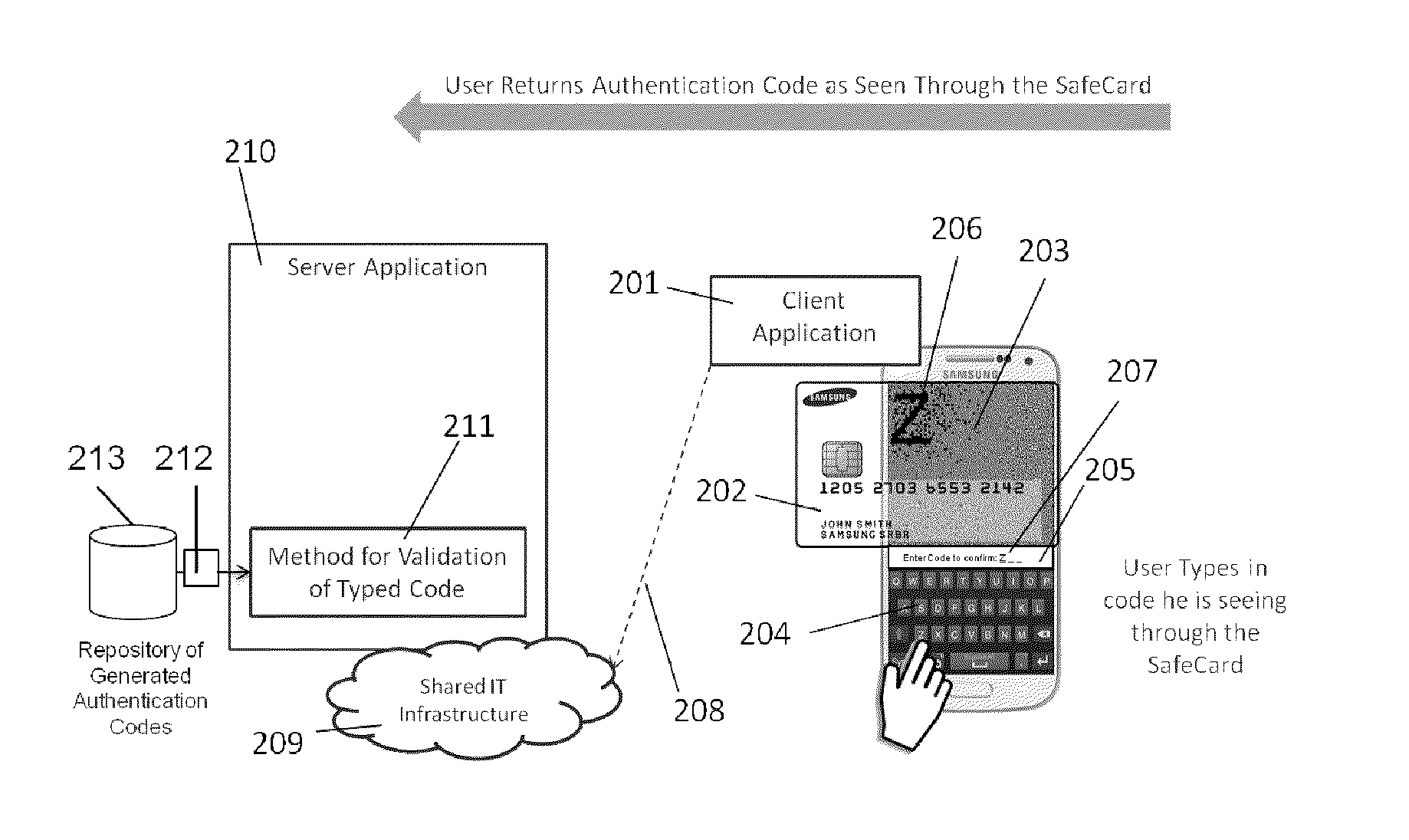
Method for authentication of mobile transactions using video encryption and method for video encryption
ActiveUS20150278807A1Improve experienceImprove user experienceAcutation objectsPayment protocolsMobile transactionMobile payment
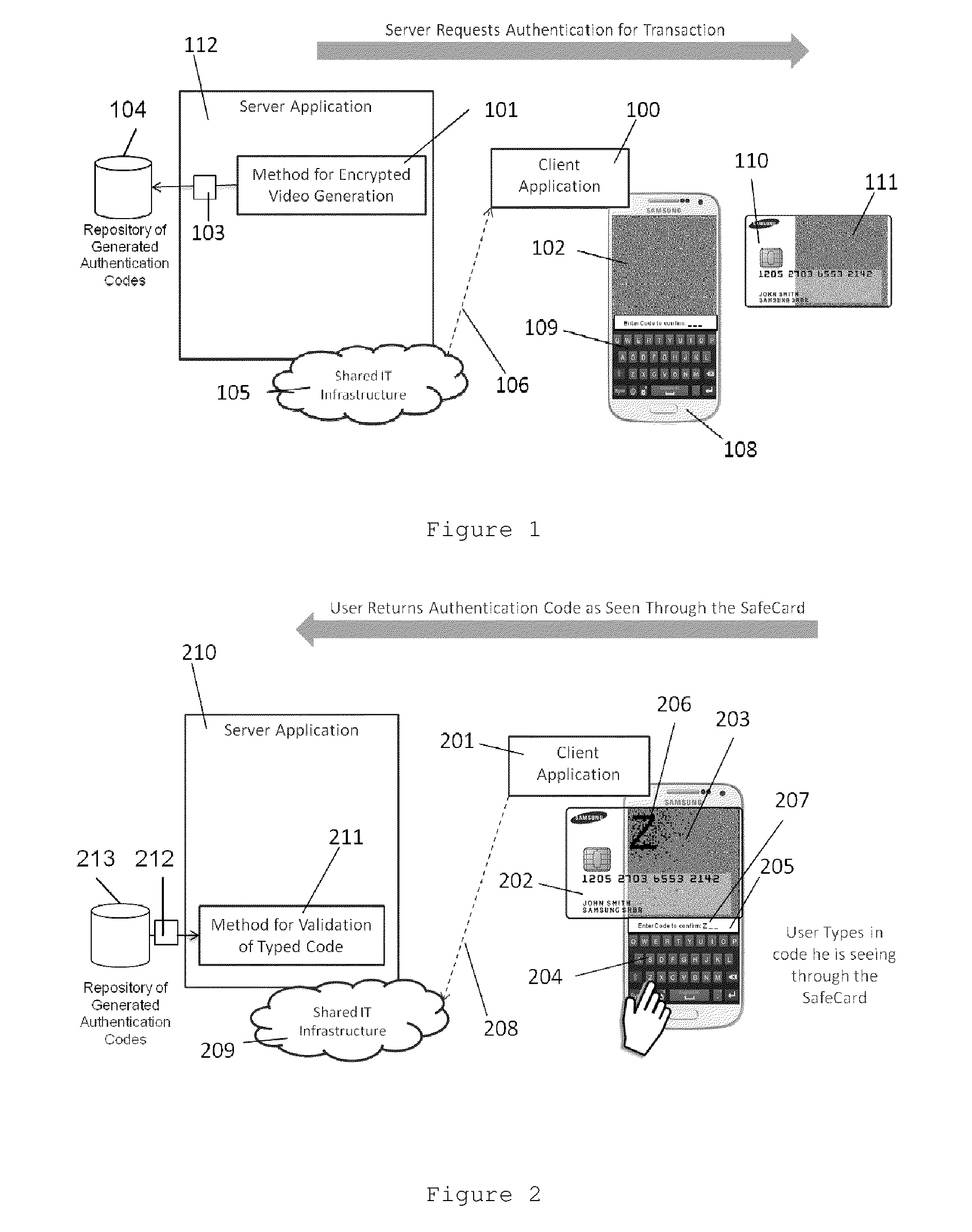
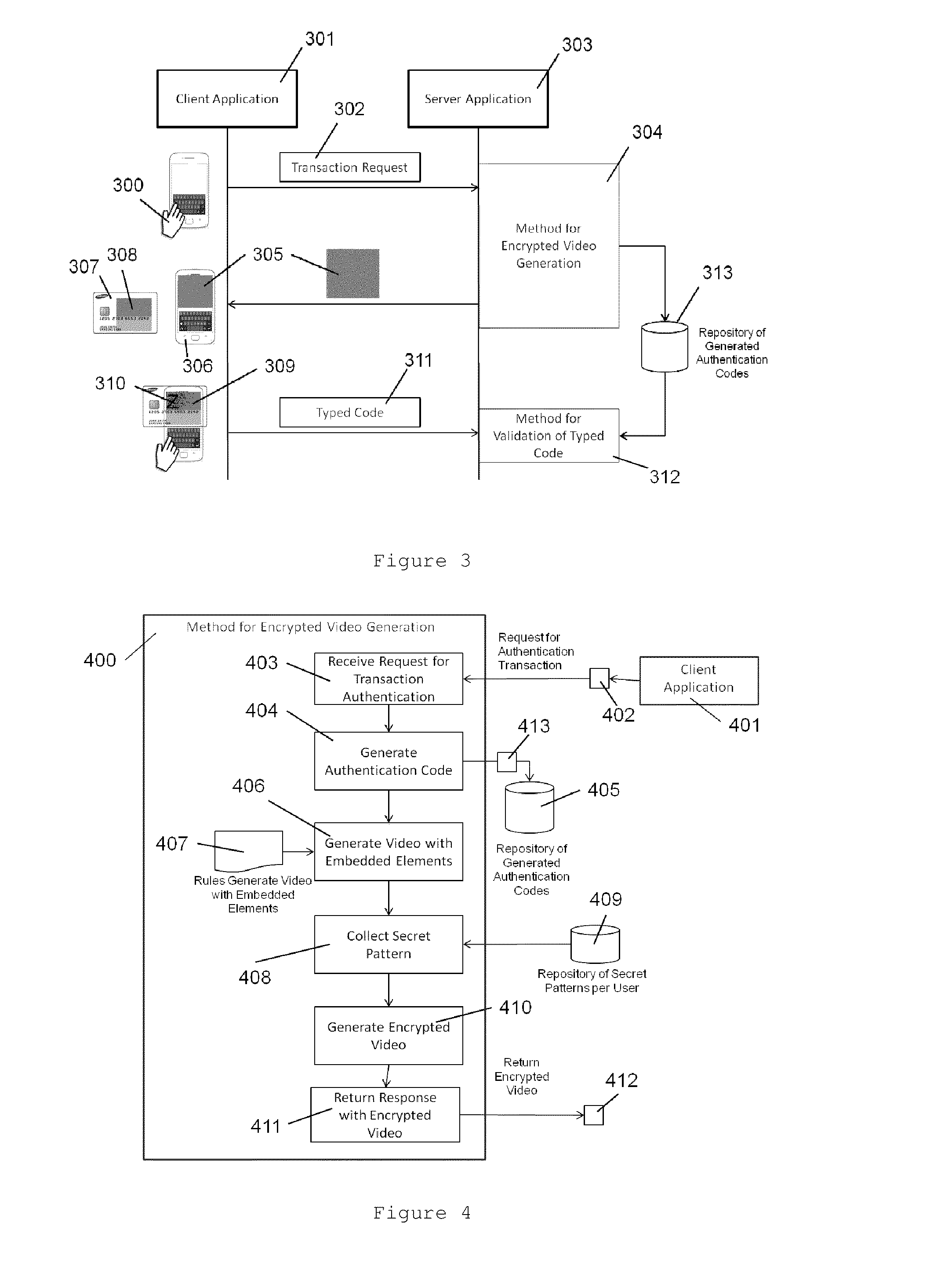
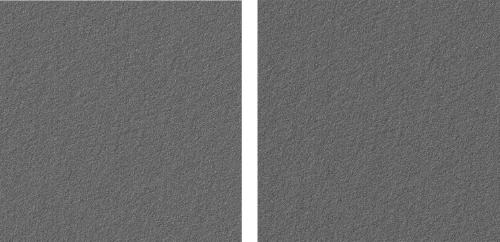
The present invention relates to a method which aims to improve data security in mobile payment transactions. To achieve this goal, we propose a highly secure method for transactions validation through video encryption and a new view of secrecy based on the combination of encrypted video (102, 203, 305) and a transparent safe card (110, 202, 307) with unique secret pattern (111, 308). This safe card (110, 202, 307) is shown as a translucent or transparent device capable of acting as “layer” or decoding mask using visual cryptography techniques. Additionally, it is proposed in one embodiment of the present invention a method for encryption of unencrypted video (602) through a frame analysis module (601) and a frame recomposition module (612).
Owner:SAMSUNG ELECTRONICSA AMAZONIA
Digital image encryption and decryption system based on visual password
InactiveCN111241554AReduced secrecy requirementsIncrease spawn rateImage codingDigital data protectionComputer graphics (images)Password
The invention discloses an image encryption and decryption method and an image encryption and decryption system based on a Visual Code and by adopting a Burch coding correction type off-axis referencelight computer generated hologram principle (CGH for short). The original image is encrypted by adopting a visual password technology, two encrypted sharing images are generated by using the originalimage, holograms corresponding to the two sharing images are obtained by using CGH during decryption, and light fields of the two holograms are respectively reconstructed and superposed to obtain a decrypted image. A novel secret sharing technology is adopted, and encryption safety and decryption reliability are enhanced for the condition that secret information is an image; meanwhile, differentfrom the traditional visual cryptography method, the hologram generated by the CGH cannot be directly superposed to obtain the original image, so that the confidentiality is further enhanced; experiments prove that the safety performance of encryption and decryption is excellent.
Owner:UNIVERSITY OF CHINESE ACADEMY OF SCIENCES
One-time pad password system based on visual cryptography
InactiveCN102394751ARealize dynamic passwordUncertainUser identity/authority verificationImage data processing detailsPasswordComputer module
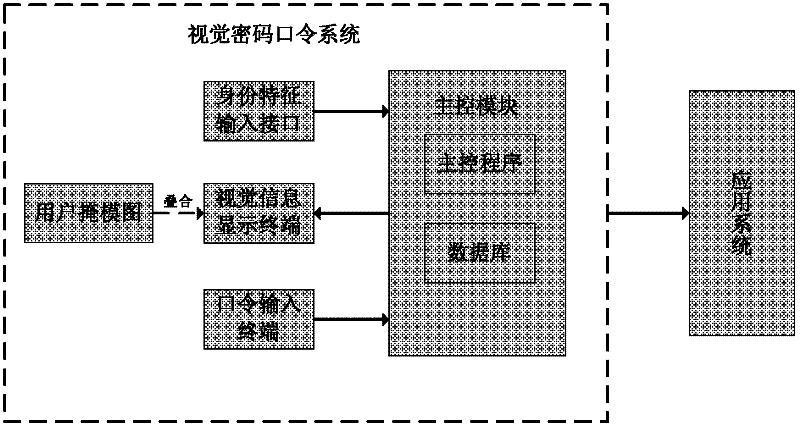
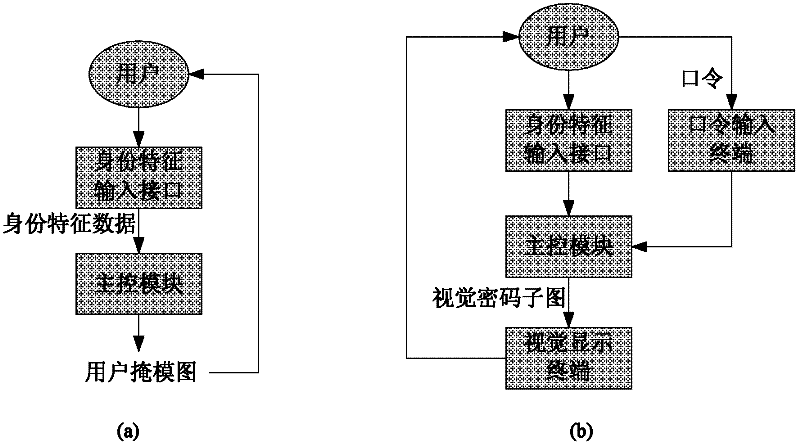
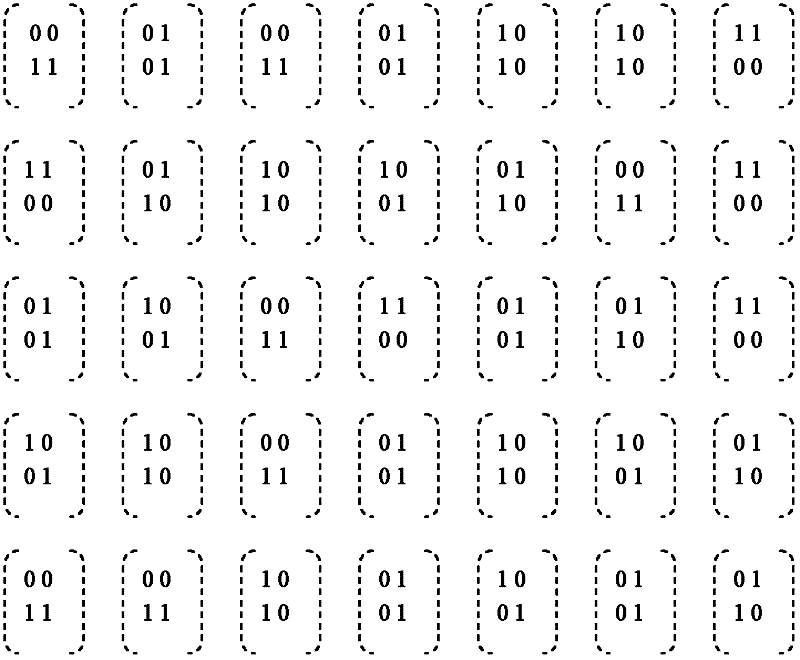
The invention provides a one-time pad password system based on visual cryptography. The technical scheme is that the one-time pad password system comprises a main-control module, an identity characteristic input interface, a visual information display terminal, a password input terminal and a plurality of subscriber masking pictures, wherein each subscriber masking picture corresponds to a subscriber; the identity characteristic input interface receives the identity characteristic data input of subscribers and sends the identity characteristic data input to the main-control module; the password input terminal receives the password input and sends the password input to the main-control module; the visual information display terminal receives visual cryptography subsidiary pictures sent by the main-control module and displays the visual cryptography subsidiary pictures to the subscribers; the subscribers place the possessed subscriber masking pictures on a first aligning frame to acquire the password P at the time; the main-control module comprises a master control program and a database; the main-control module takes a computer system as the platform and further comprises another master control program and another database to achieve subscriber register and authentication identification. The one-time pad password system provided by the invention can achieve safe, convenient andefficient subscriber identity authentication.
Owner:NAT UNIV OF DEFENSE TECH
A method for visual encryption of gray-scale image
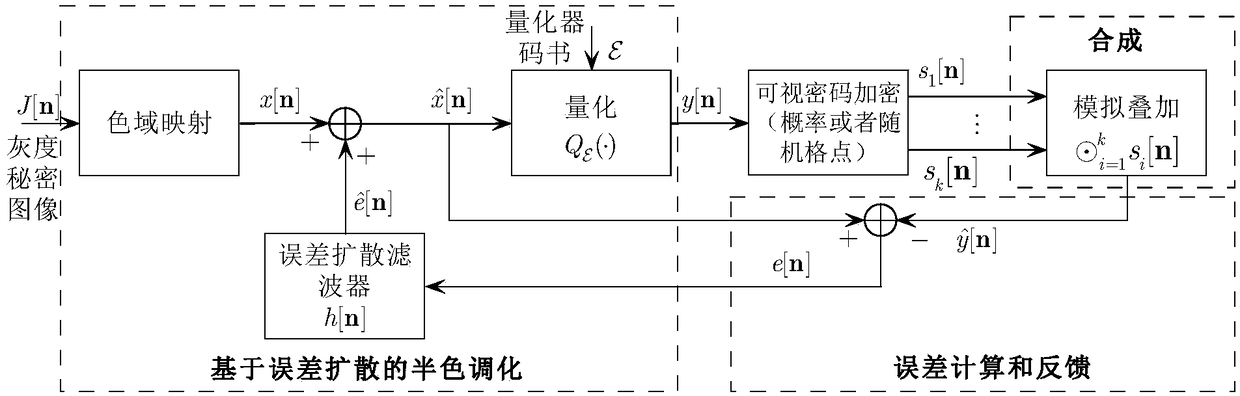
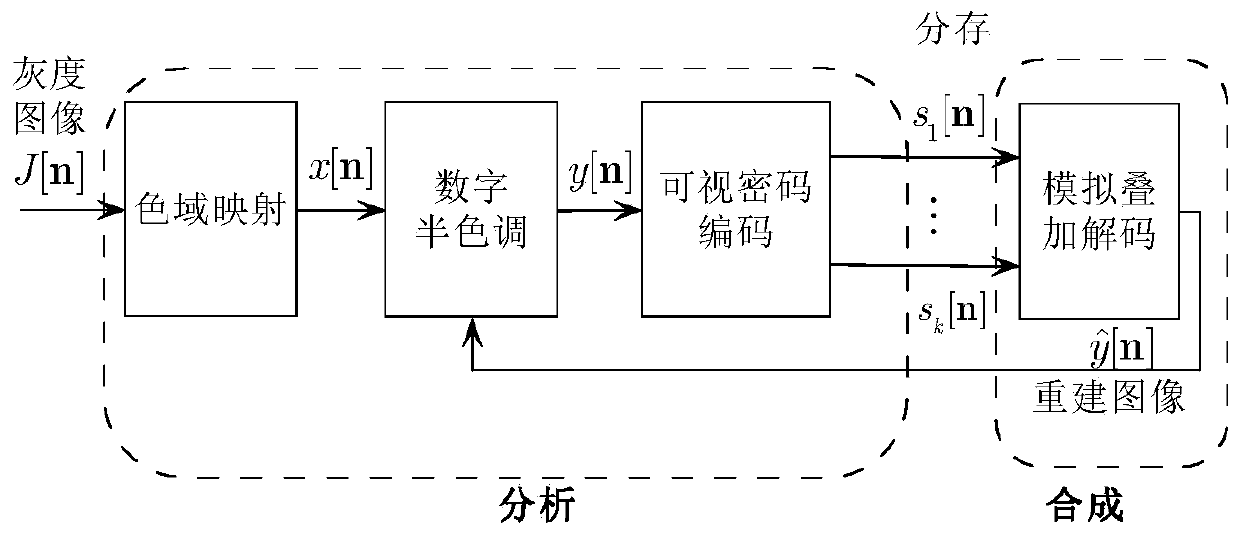
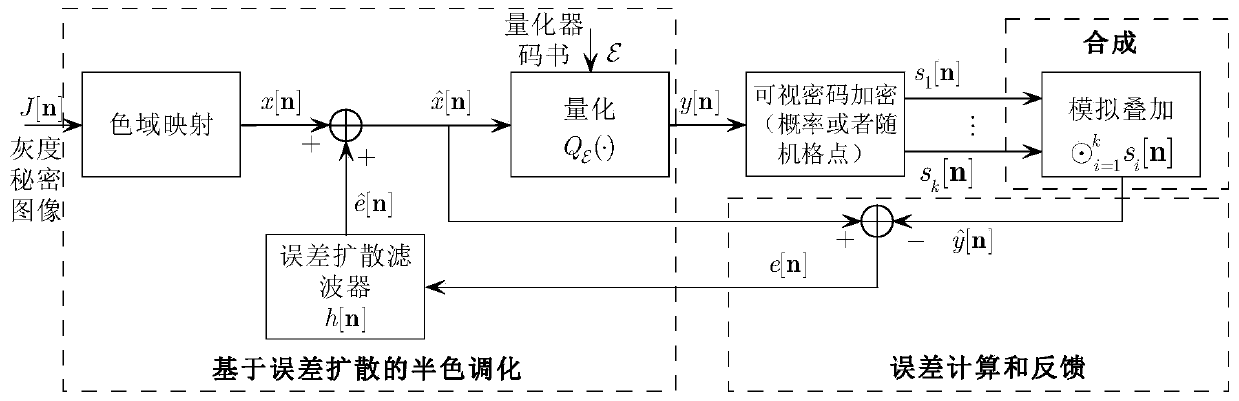
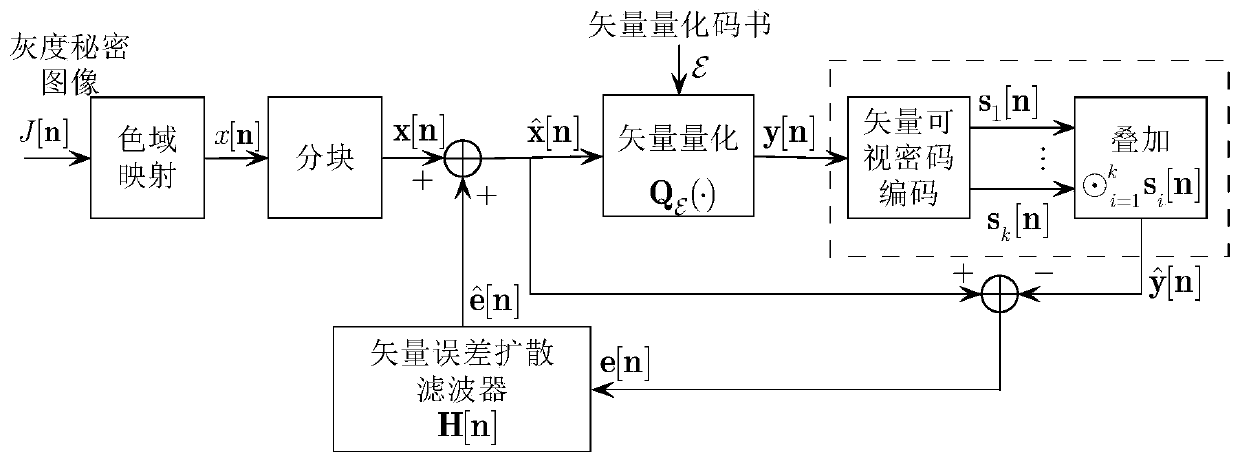
ActiveCN109214971AMeet the contrastTo meet the conditionsImage analysisEncryption apparatus with shift registers/memoriesError diffusionComputer vision
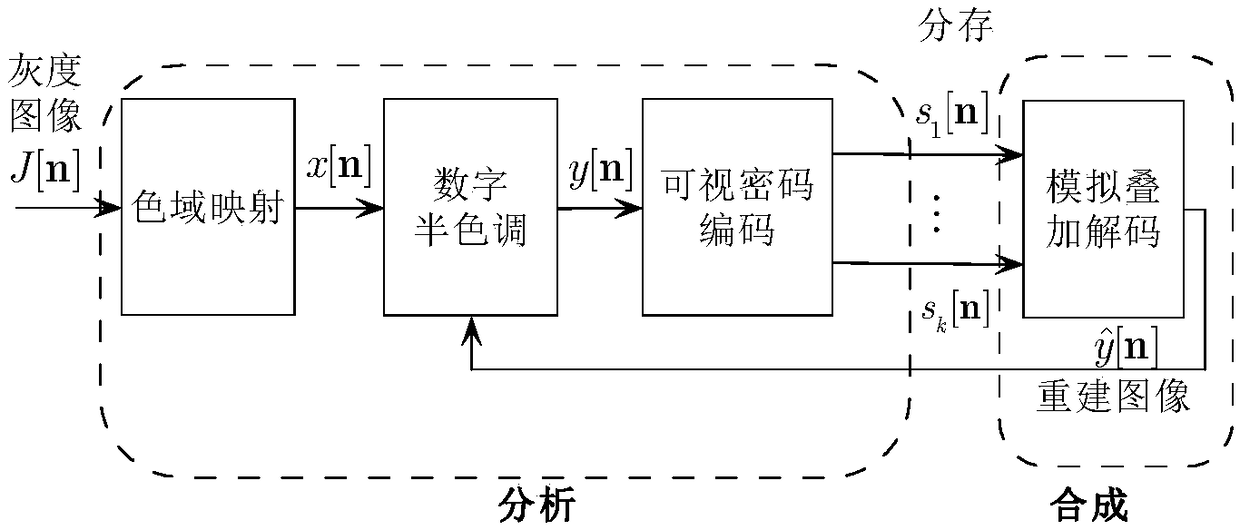
The invention discloses a gray image visual encryption method. In this method, two processes are placed in an error-diffusion feedback loop, which are the generation of split-memory image and the superposition decoding of visual cryptography. Which means, at the encoder end, each pixel or image block is sequentially processed in a scanning order, for each pixel or image block on the resulting split image, check its superposition decoding effect immediately, comparing the reconstructed target image obtained after superposition with the original secret image, obtaining the difference between thetwo, the contrast difference is fed back and diffused to surrounding pixels or image blocks that have not yet been quantized, so as to improve the quality of decoded and reconstructed secret images,wherein the analysis process corresponds to a process of generating a split image from the secret image and the synthesis process corresponds to a process of obtaining a target image from the split image, and the method of the invention places the synthesis in an analysis, that is, an analysis based on the synthesis.
Owner:SHANDONG UNIV OF SCI & TECH
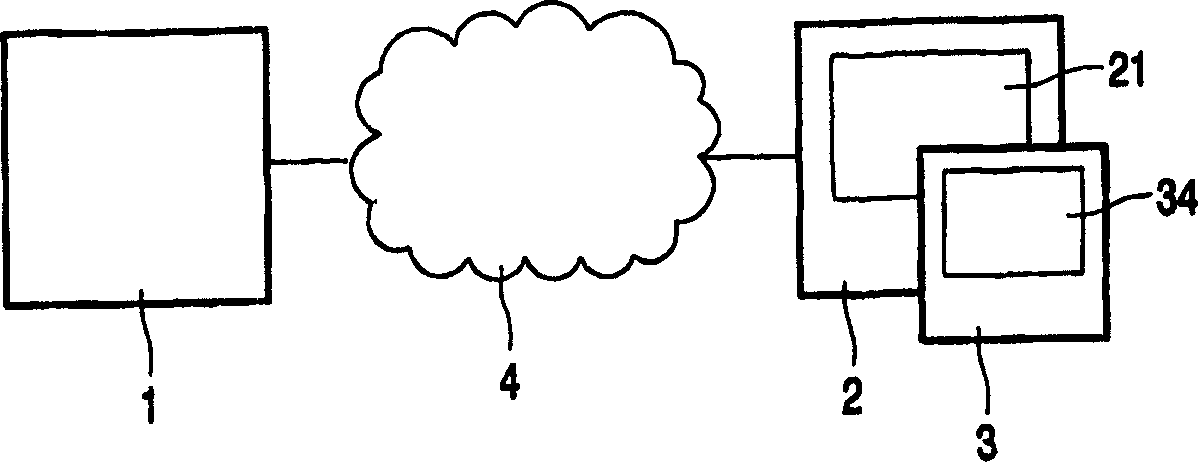
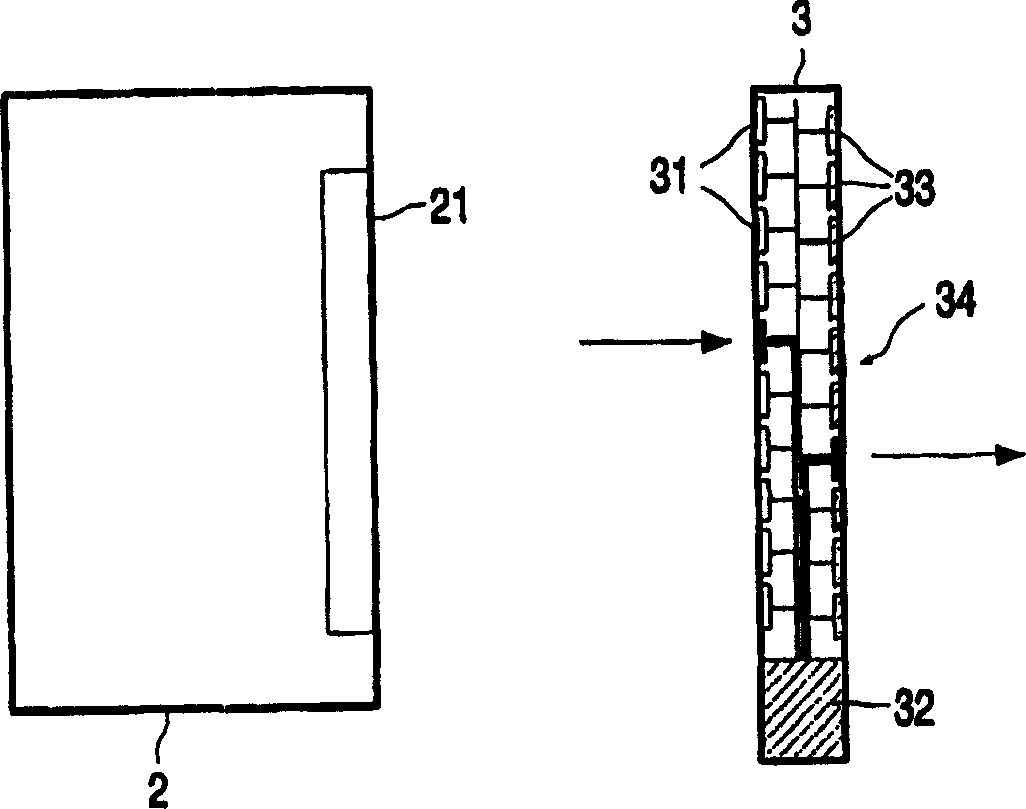
Key synchronization in a visual cryptographic system
InactiveCN1729495ASynchronising transmission/receiving encryption devicesMultiple keys/algorithms usageData synchronizationComputer terminal
A system for visual cryptography comprises a server (1) for encrypting a series of images using a set of keys, a terminal (2) for displaying the encrypted images, a transmission medium (4) for transmitting the encrypting images from the server to the terminal (2), and a decryption device (3) for decrypting the encrypted image displayed on the terminal. A key identification is produced by the server (1) and displayed by the terminal (2). The decryption device (3) senses the key identification and selects the corresponding key from its key set.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
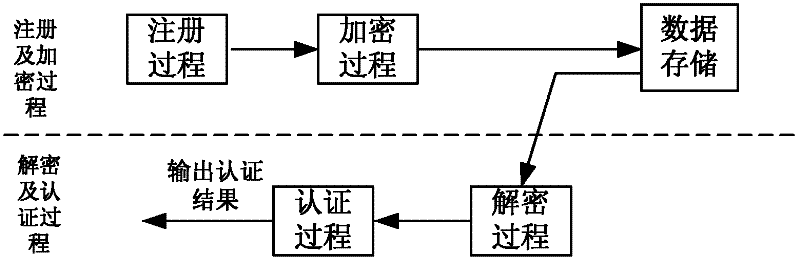
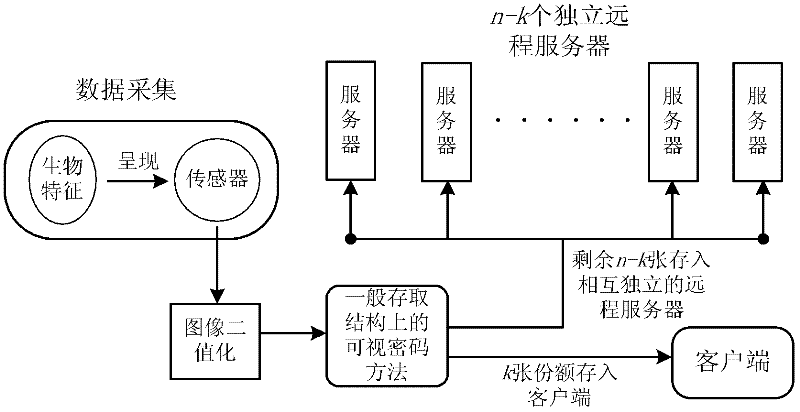
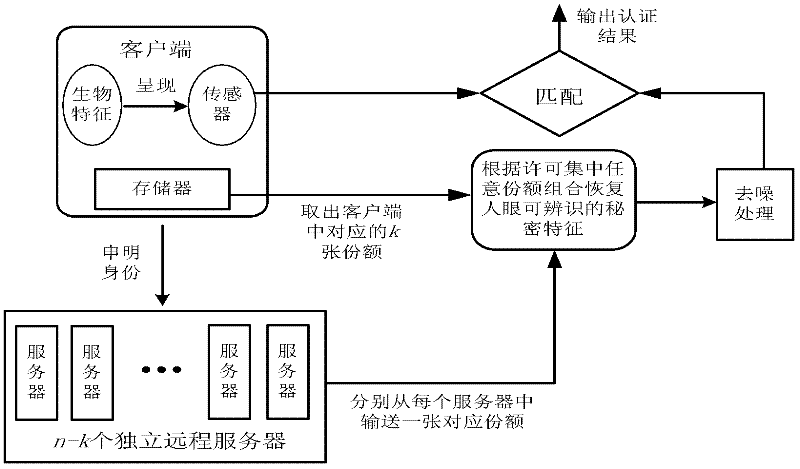
Biological characteristic remote authentication method based on visual codes
InactiveCN102413148AGuaranteed recoverabilityGuaranteed stabilityUser identity/authority verificationAccess structureSecret code
The invention provides a biological characteristic remote authentication method based on visual codes, which is used for solving potential security hazards in data storage and transmission in the traditional biological characteristic remote authentication system. The method comprises the following steps: registering a user; storing a registered biological characteristic image into multiple shares by a visual code method on a common access structure, defining a permission set of share images, and ensuring that only share combinations in the permission set can recover the registered biological characteristic image; superposing any share combinations in the permission set, and carrying out logic or operation to decrypt the registered biological characteristic image; and finally, authenticating the access user by using the decrypted registered biological characteristic images. The invention can ensure that the secret biological characteristic image can be recovered when any share images are damaged, and ensure no leakage of secret biological characteristic image information even if part of shares are thieved, thereby enhancing the data storage and transmission security in the biological characteristic remote authentication process.
Owner:XIDIAN UNIV
QR code secret sharing method based on visual password
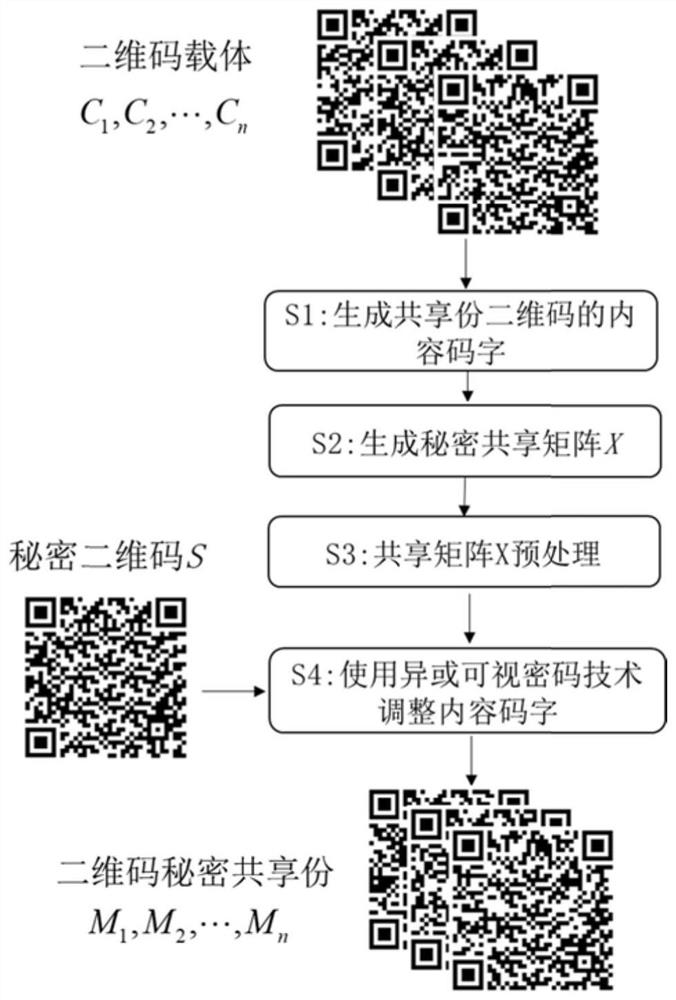
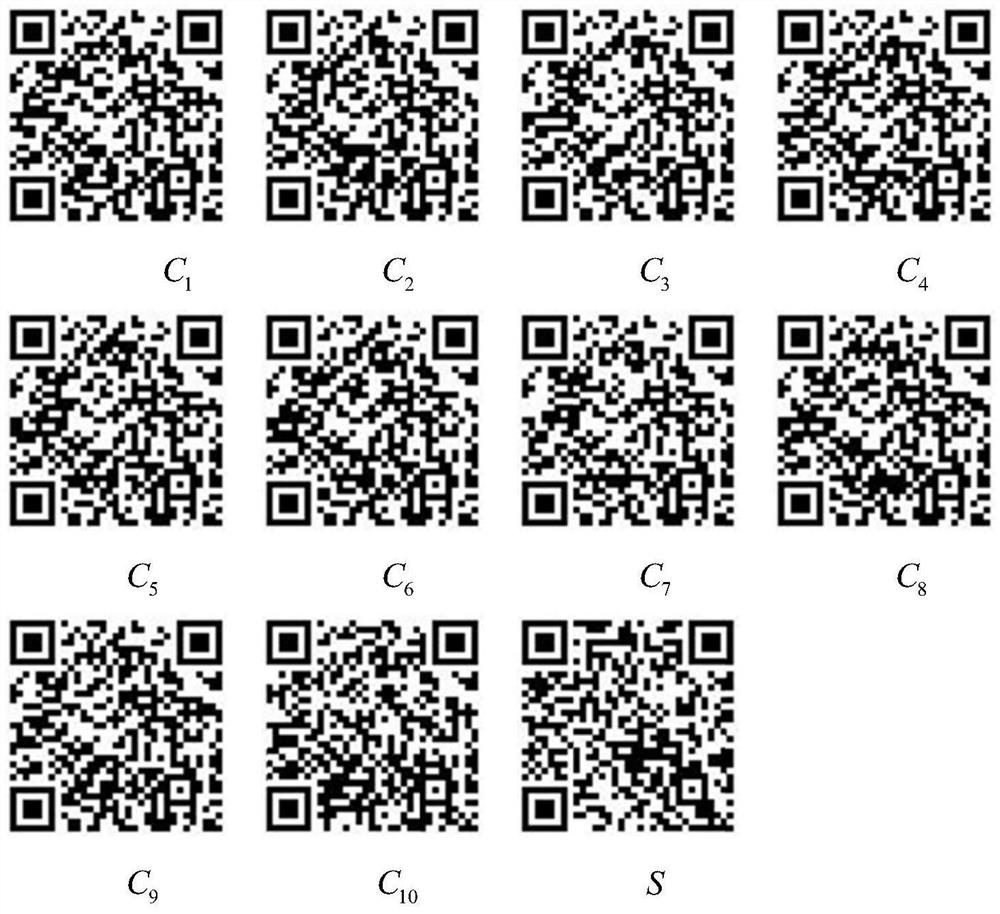
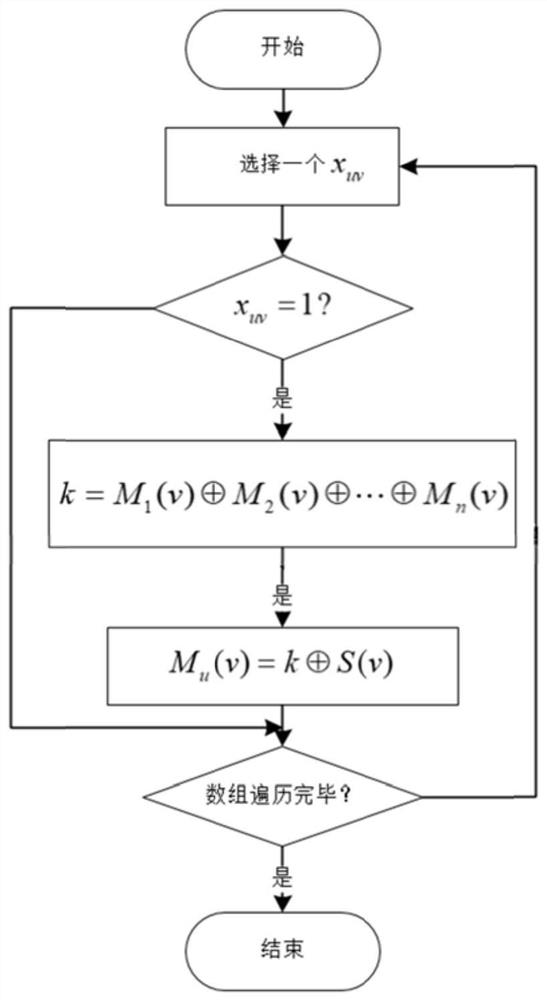
PendingCN111737713ARealize secret sharingImprove securityDigital data protectionCoding/ciphering apparatusAlgorithmPassword
The invention provides a QR code secret sharing method based on a visual password. The method comprises the steps: designing a 0-1 planning strategy by analyzing secret unrecoverable conditions of a shared subset, and then constructing a secret sharing matrix; based on the secret sharing matrix, adjusting the content code words of the carrier QR code by using an XOR visual password technology; andfinally, generating a secret sharing copy QR code according to the adjusted carrier QR code content code word, thereby realizing sharing of a secret QR code image. The method not only inherits the advantages of easy realization of visual cipher technology coding and low decoding calculation complexity, but also is superior to other existing methods in robustness, and the secret image has better security.
Owner:绍兴聚量数据技术有限公司 +1
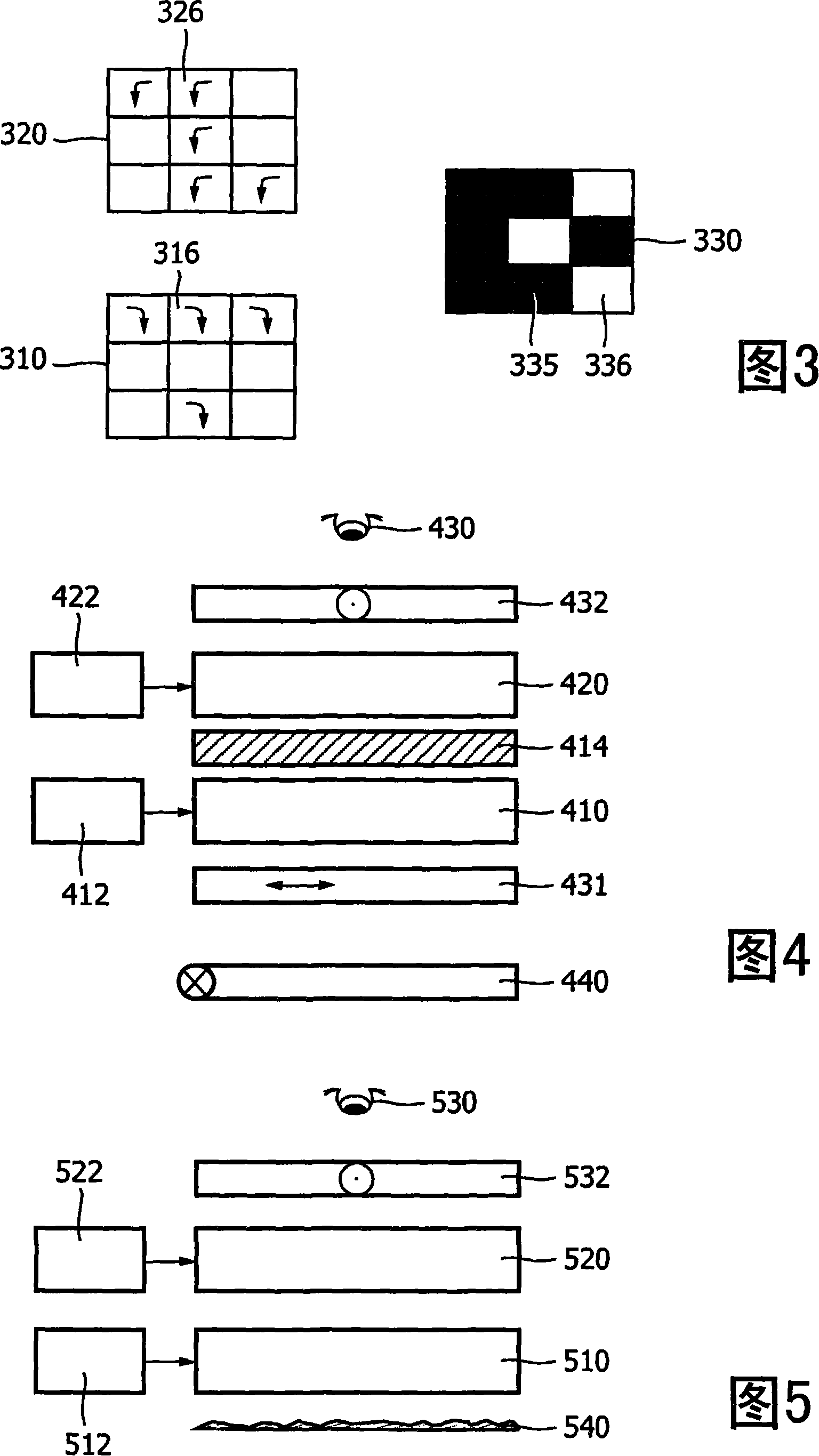
Display device for visually reconstructing an image
InactiveCN101084638AImprove image qualitySecret communicationCoding/ciphering apparatusLiquid crystallineImaging quality
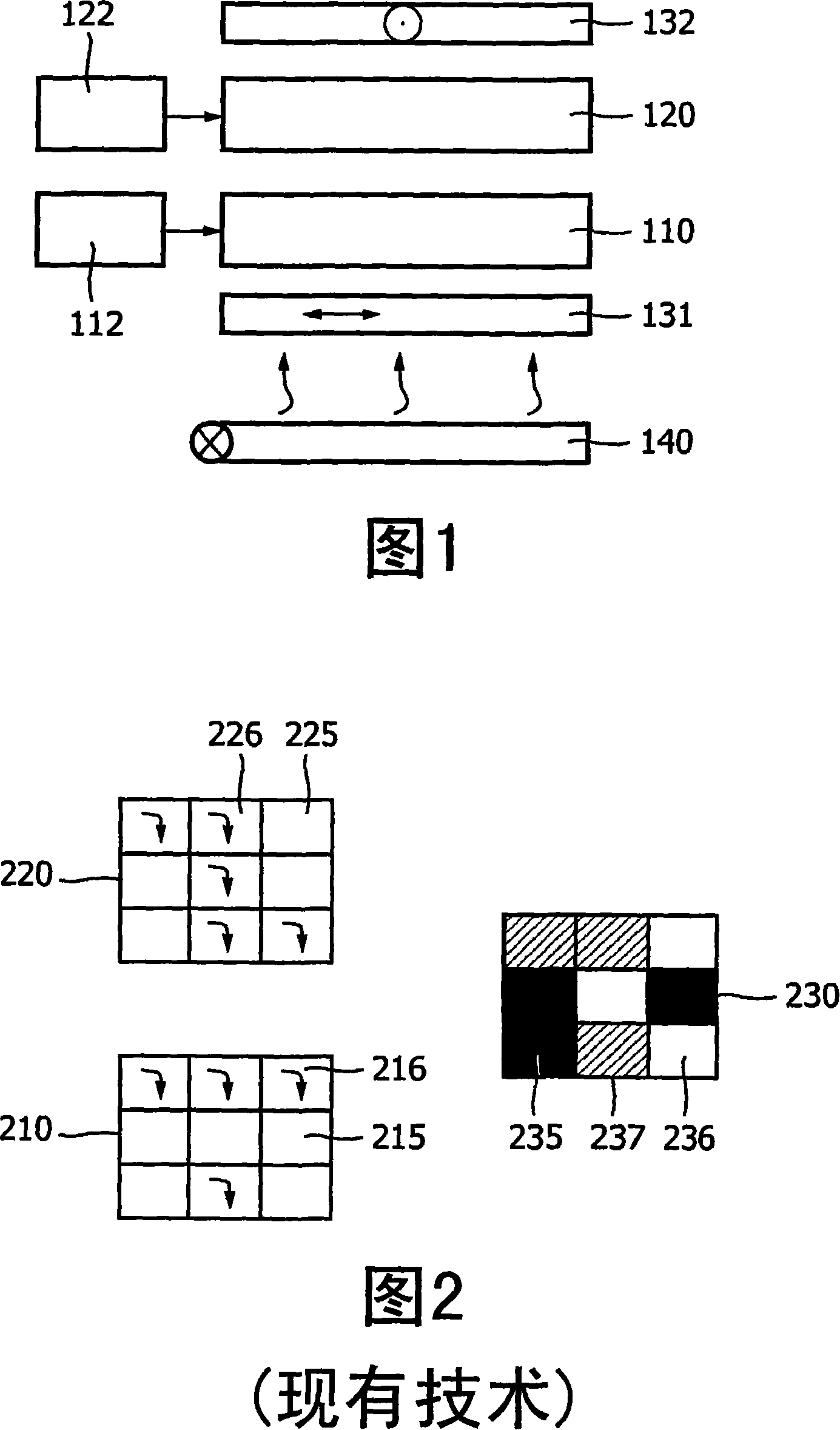
The invention relates to a display device for visually reconstructing an image (330) from an encoded image (320), such a device being particularly useful in the field of visual cryptography. The display device has two stacked liquid crystalline layers (410, 420) with individually addressable pixels. One layer (420) renders encoded image data together with a randomization pattern, and the other layer (410) only renders a randomization pattern. If the patterns match, the display device shows a visually reconstructed image (330) to a viewer. Means are provided for improving an optical match between the LC layers, such as a birefringent layer (414) between the two LC layers. Alternatively, two twisted nematic LC layers can be used having opposite twist directions. Such means were found to improve an image quality of the visually reconstructed image, and can in fact be advantageously applied in any display system including a plurality of LC layers cooperating for forming an image.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
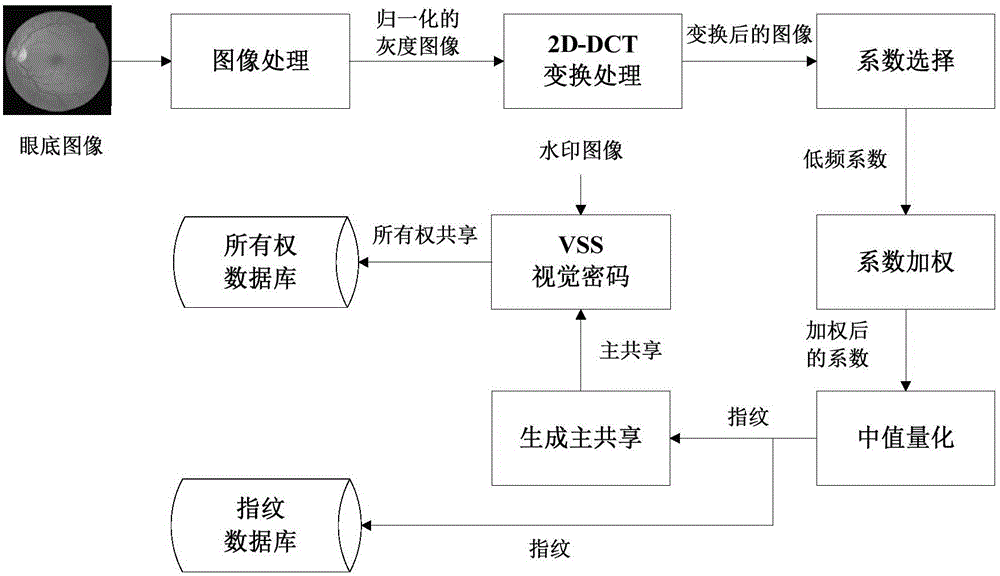
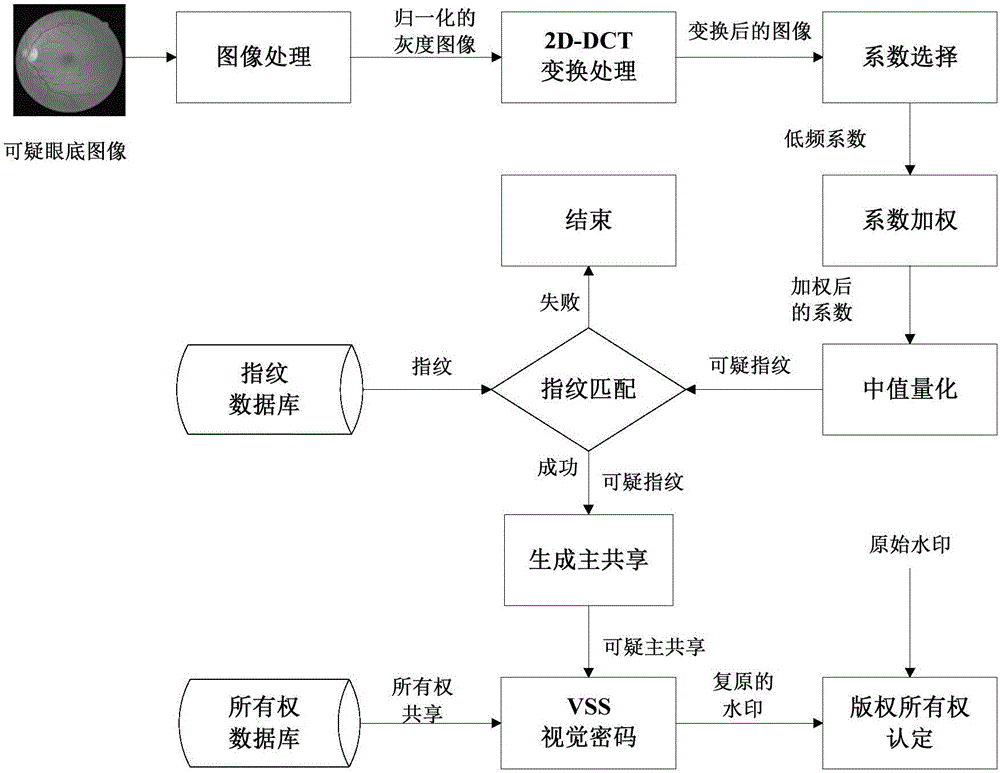
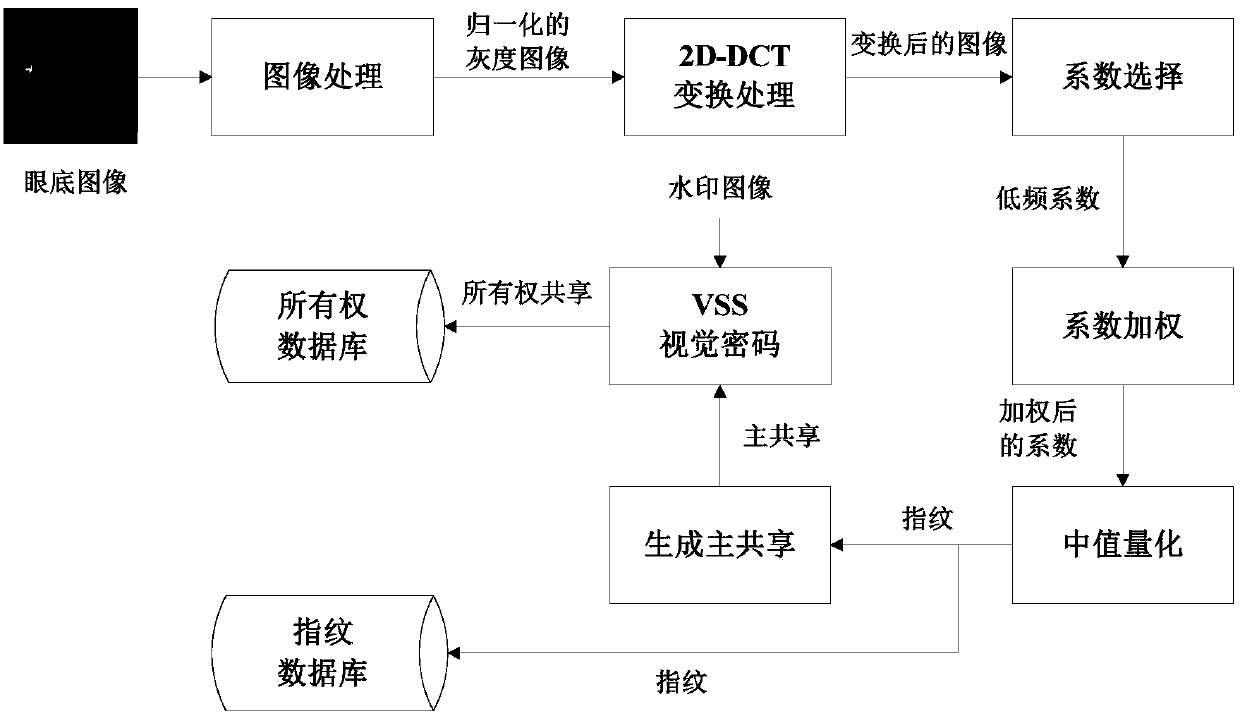
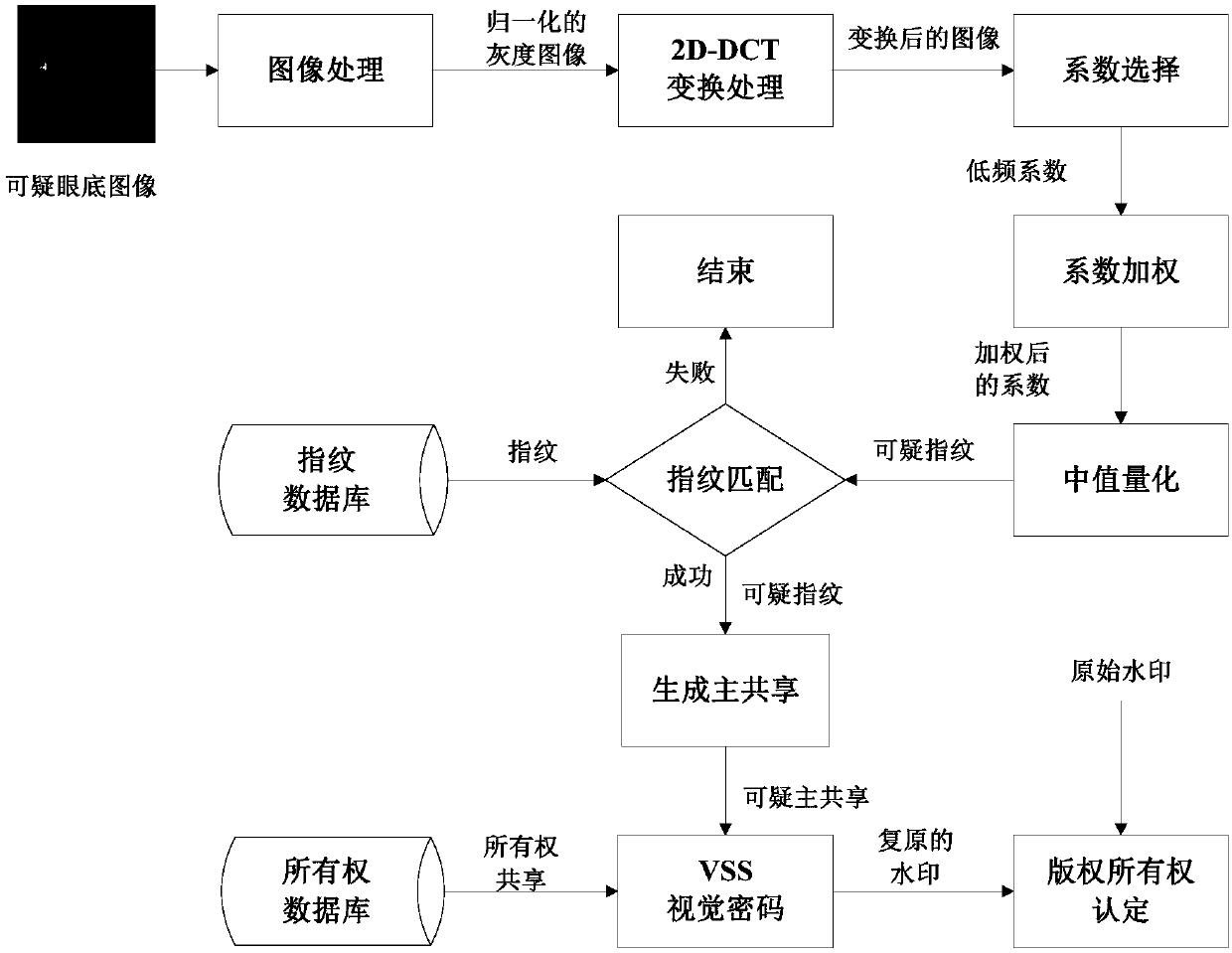
Eye fundus image nondestructive digital copyright management method based on fingerprint and zero-watermark mixed framework
InactiveCN106126978AImprove legibilityImprove robustnessCharacter and pattern recognitionImage data processing detailsDiseaseDigital rights management
The invention discloses an eye fundus image nondestructive digital copyright management method based on a fingerprint and zero-watermark mixed framework. The method comprises the following steps: firstly, performing 2D-DCT transformation on a normalized eye fundus image, setting different weights for coefficients obtained by transformation, extracting eye fundus image features with high identifiability and high robustness as fingerprints for content-based searching; and secondly, building a mapping relation between the fingerprints and watermarks according to a zero-watermark copyright protection method based on a VSS visual cryptography algorithm for copyright authentication. Compared with the conventional method, the method disclosed by the invention has the advantages that the whole process of the method is nondestructive and meets the requirement for accurate diagnosis; the method has the effect of protecting the copyright of the eye fundus image for a long time, and the problem of one-off copyright authentication based on digital watermarks; and the eye fundus image nondestructive digital copyright management method is applicable to digital copyright management of the eye fundus image, and has a certain clinical significance for auxiliary diagnosis of eye fundus-related diseases.
Owner:CENT SOUTH UNIV
Password encryption and multi-channel transmission method
This invention relates to one order transmission method by use of secret sharing or visual cryptography or multi-signal channel suitable for order transmission, which Uses secret sharing or visual cryptography to code the order into multiple sub orders to add the difficulty of stealing orders as the single order can not get secret order any information; the legal user owns all orders through simple computation or transparent film to get original order.
Owner:钱丽娜
Visual-cryptography-based visible anti-copying technique
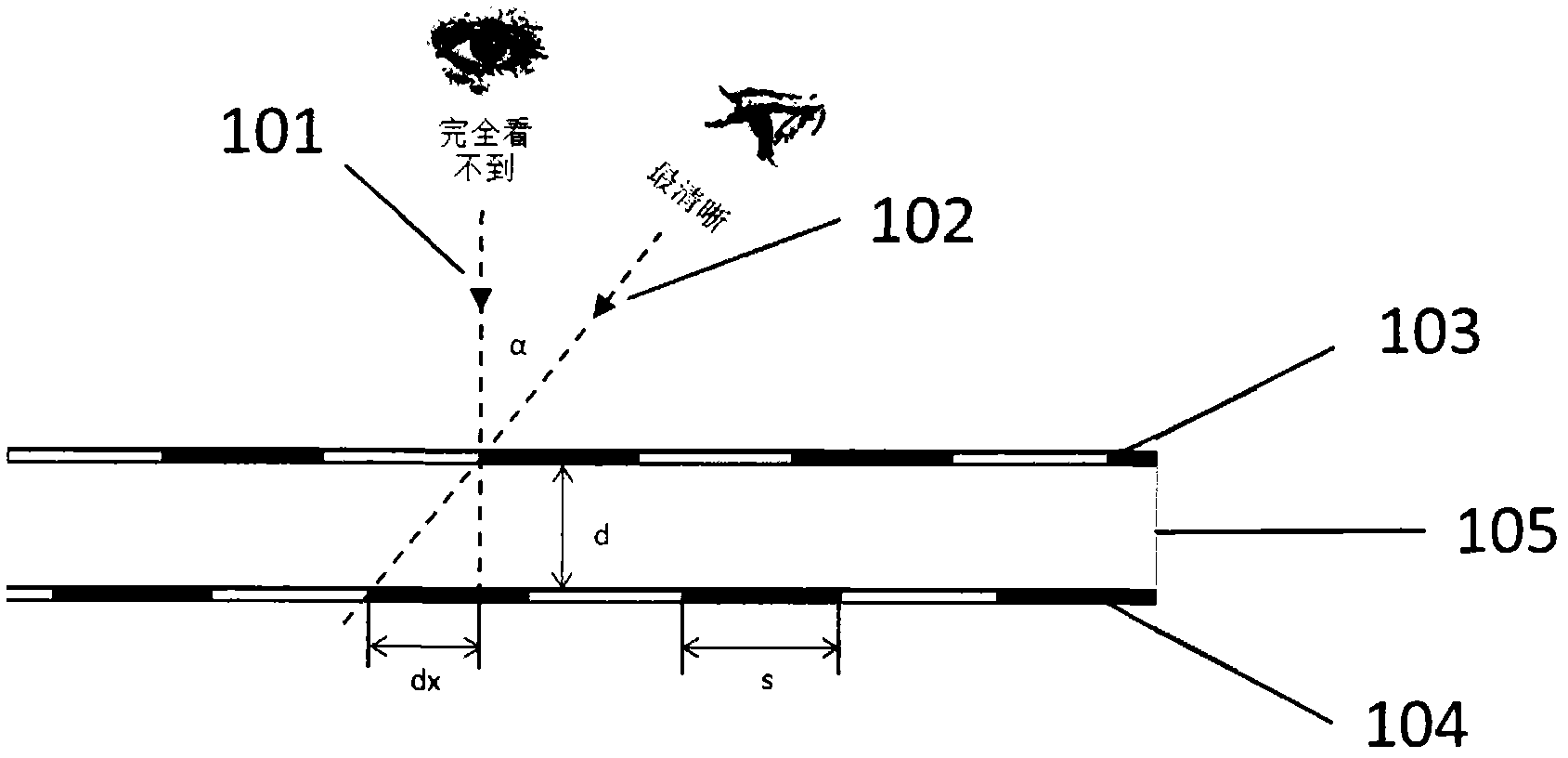
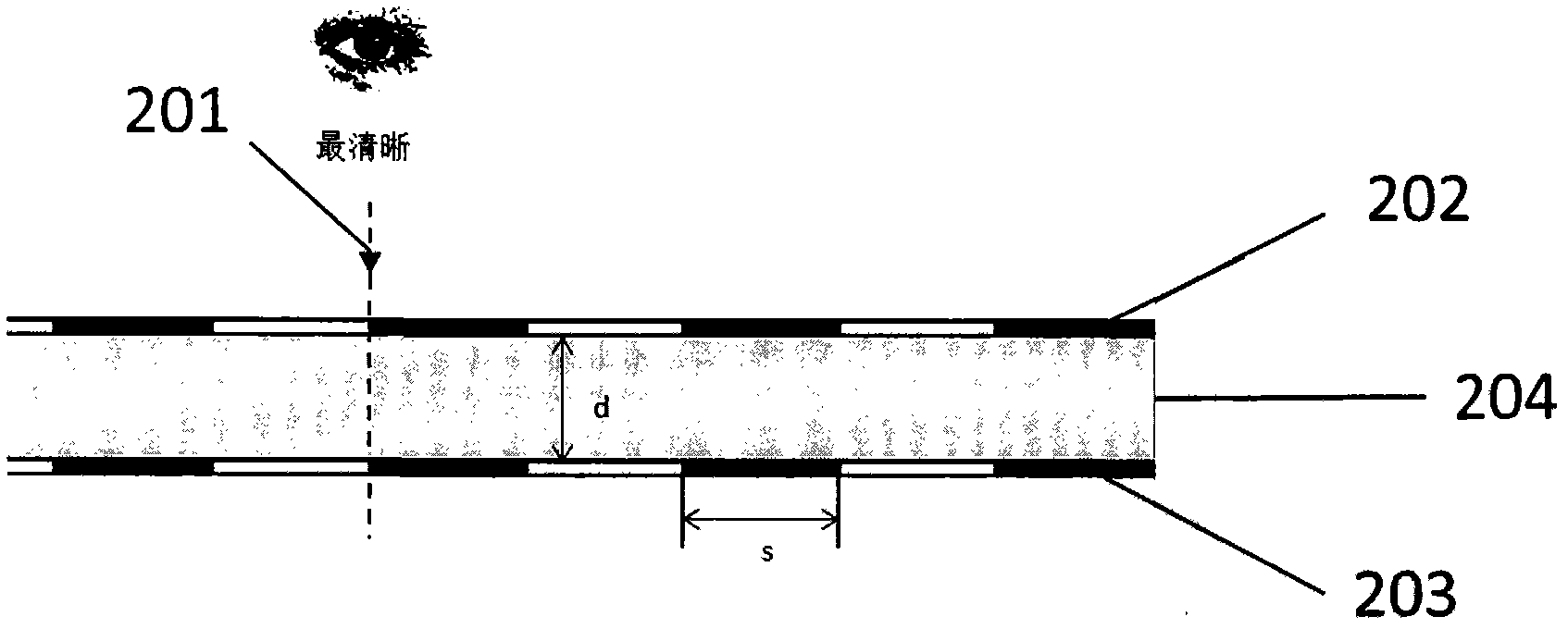
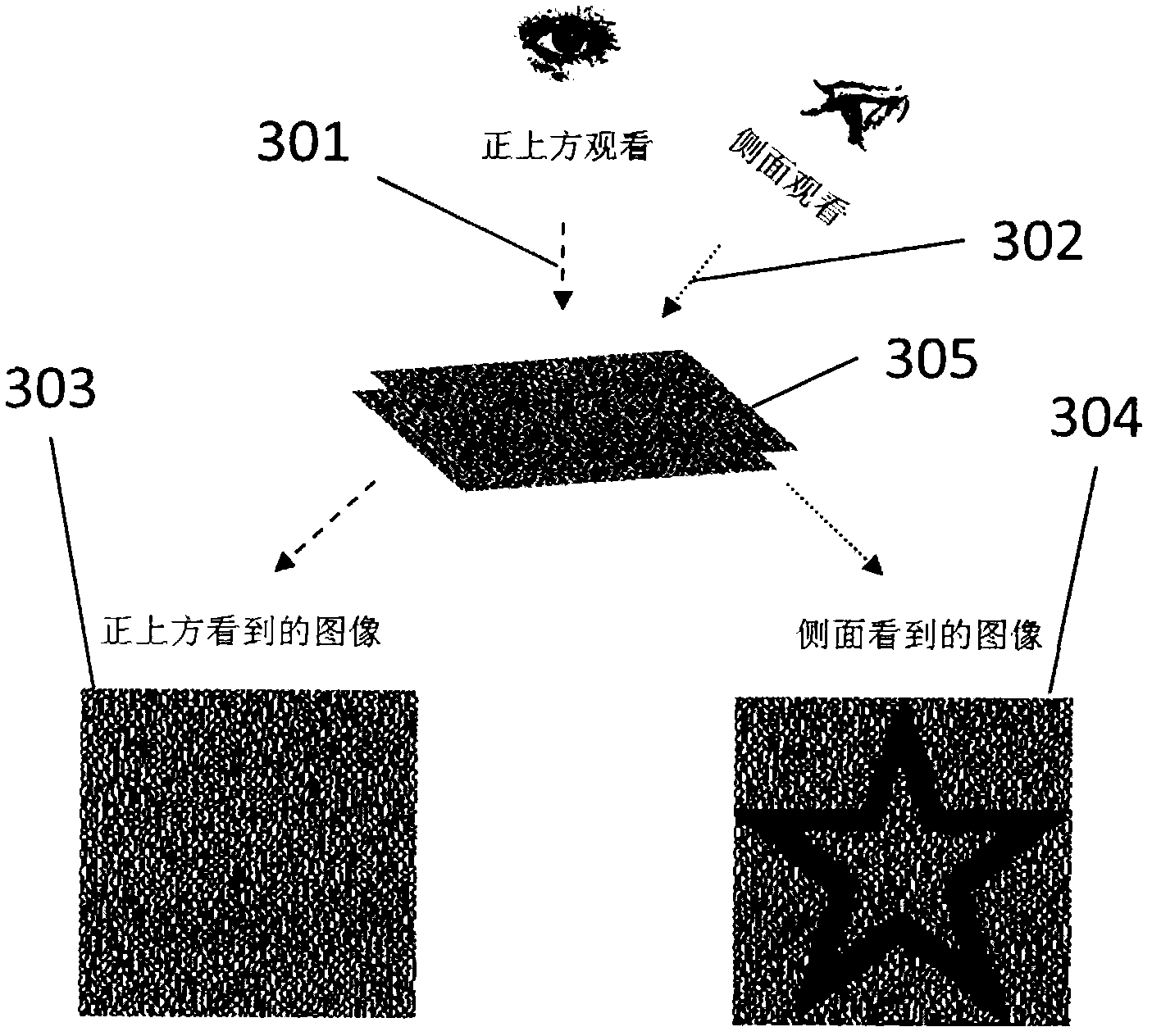
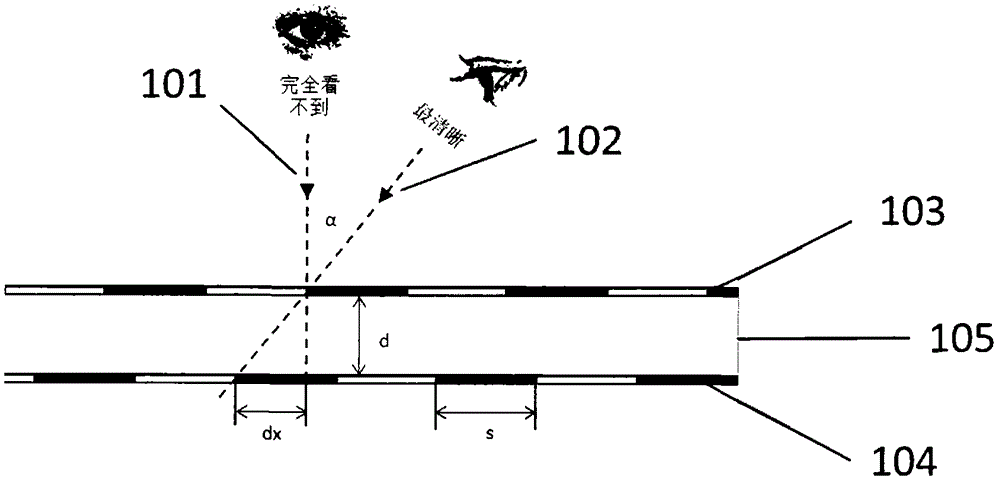
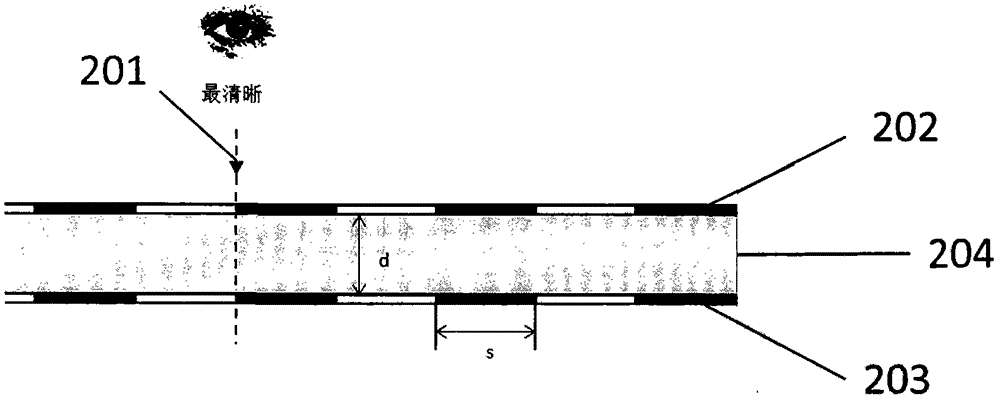
ActiveCN102658741ALow costPrevent copyingDuplicating/marking methodsPattern printingCredit cardVisual perception
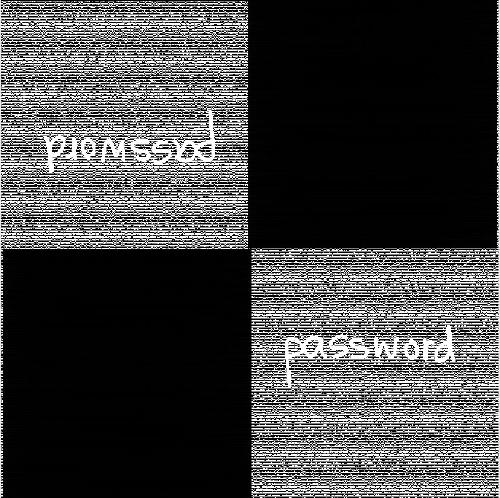
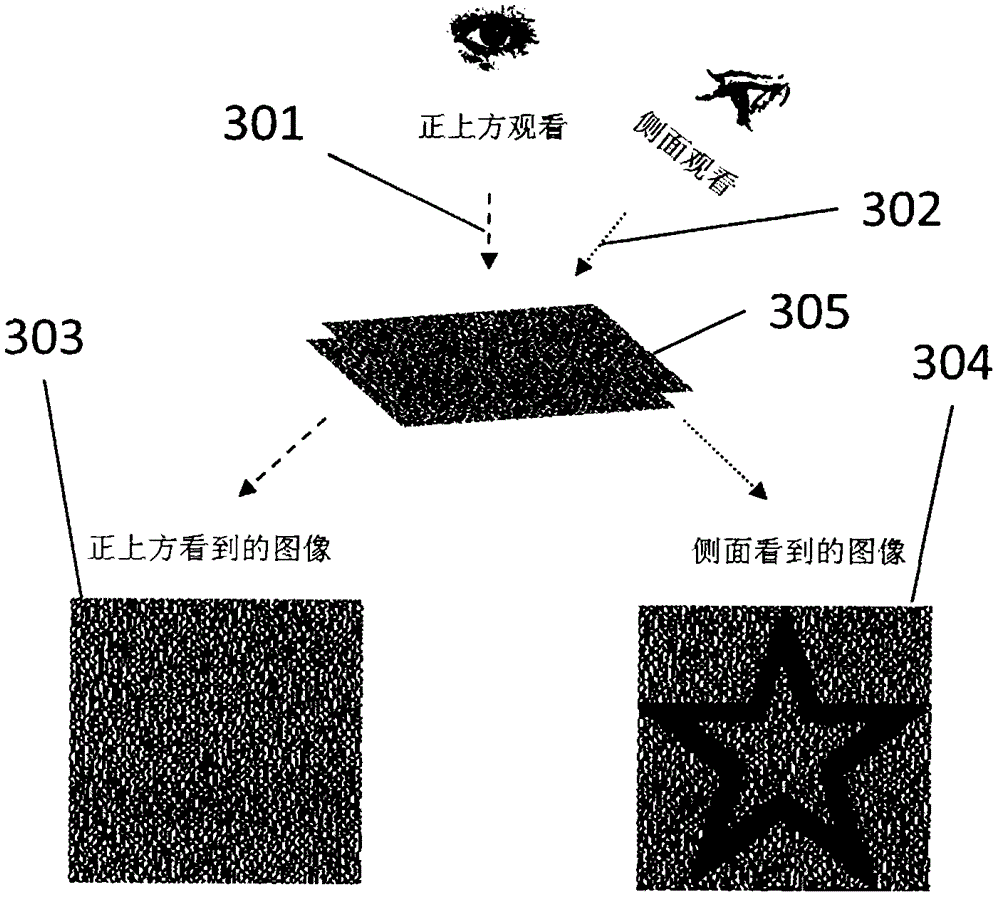
The invention provides an efficient and safe visible anti-copying technique which has low costs. The technique is based on the visual cryptography principles. By printing two sharing pictures of the visual cryptography program on a transparent film with a certain thickness according to a specific way, the cryptic pictures is visible from a certain offset angle instead of from the front of the paper, therefore preventing the pictures from being copied by equipments such as copying machines and scanners. As shown in the following picture, the pictures seen from right above and from the side of the anti-copying transparent film manufactured by the technique of the invention are totally different, wherein the picture can be clearly seen from the side face while the picture can not be seen or can be vaguely seen from the right above. The technique is applicable to the prevention of illegal copying of plane pictures and texts, therefore effectively avoiding forgery; to the prevention of intentionally or unintentionally peeping and covert photography, protecting privacy; and has low cost, applicable to extensively issued plane image-text carriers such as paper money, credit cards, negotiable securities, bills, identity cards and the like.
Owner:刘峰
A threshold visual cryptography matrix construction method
PendingCN109727294AQuality assuranceWill not affect the decryption effectImage codingArray data structureAlgorithm
The invention provides a threshold visual cryptography matrix construction method, which comprises the following steps of: constructing an accumulation counting group which consists of an | P | * | T| matrix CA; After the array P, the authorization subset and the forbidden subset are determined, determining F, wherein F is a set in Gamma infinity; Determining a set Gamma infinity, wherein the number of sets in the Gamma infinity is equal to that of the Gamma infinity; Constructing a matrix CA; Constructing basis matrixes S0'and S1 'of the accumulation array according to a (n, n) threshold scheme; Observing the distribution condition of the position with the Hamming weight of 1 in each line in the matrix CA, and taking the line sequence of the position with the Hamming weight of 1 in thematrix CA as the line sequence of the base matrixes S0 and S1; And so on, obtaining final basis matrixes S0 and S1. Due to the fact that the column number of the formed basis matrix is relatively small, the smaller the column number is, the smaller the pixel expansion degree is, the phenomenon that the decryption effect is affected due to the fact that an image is excessively stretched when secrets are recovered is avoided, and the quality of the decrypted image is guaranteed to a great extent.
Owner:CHENGDU UNIV OF INFORMATION TECH
Visual cryptography and voting technology
In some embodiments, techniques for voting and visual cryptography may include various enhancements.
Owner:ROSKIND JAMES A
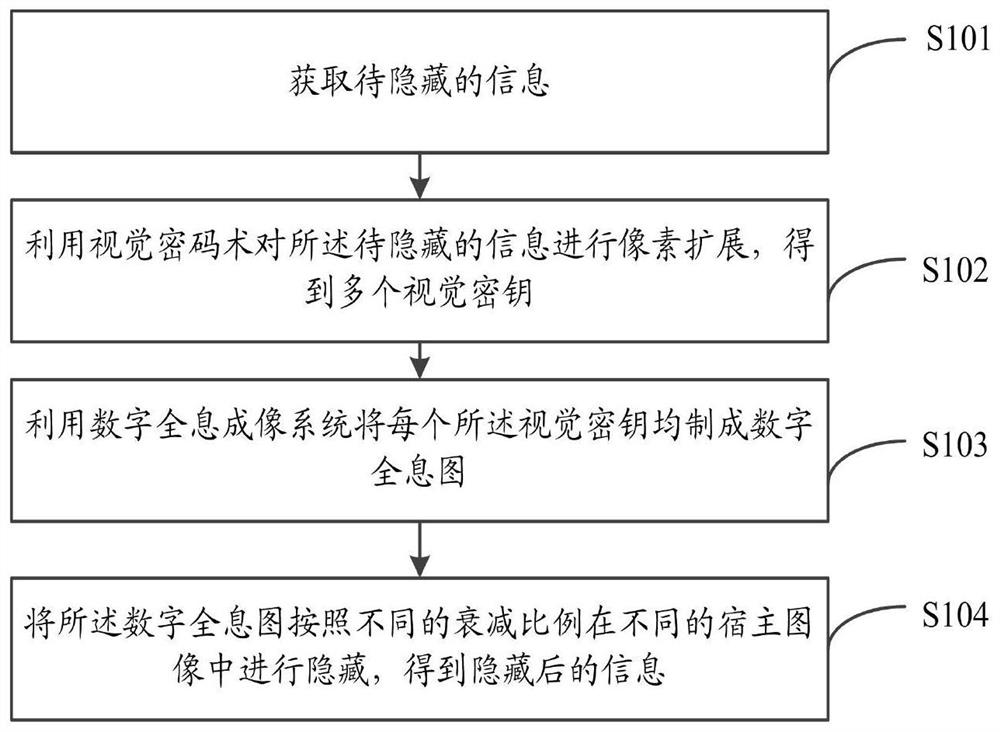
Digital holographic information hiding and extracting method and system
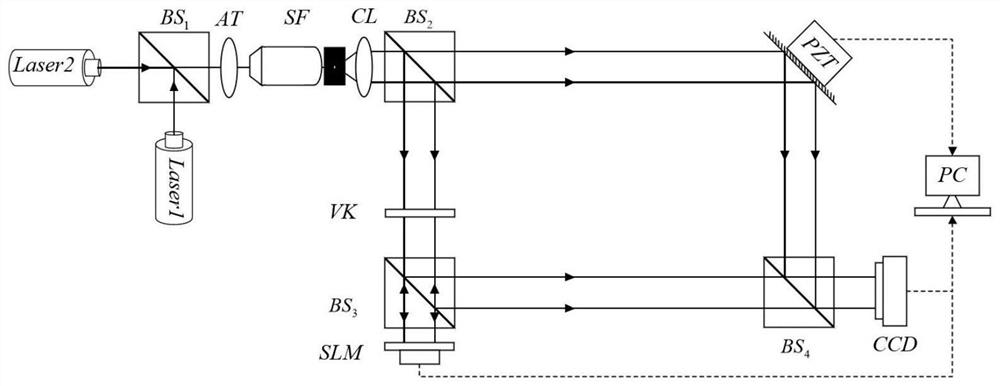
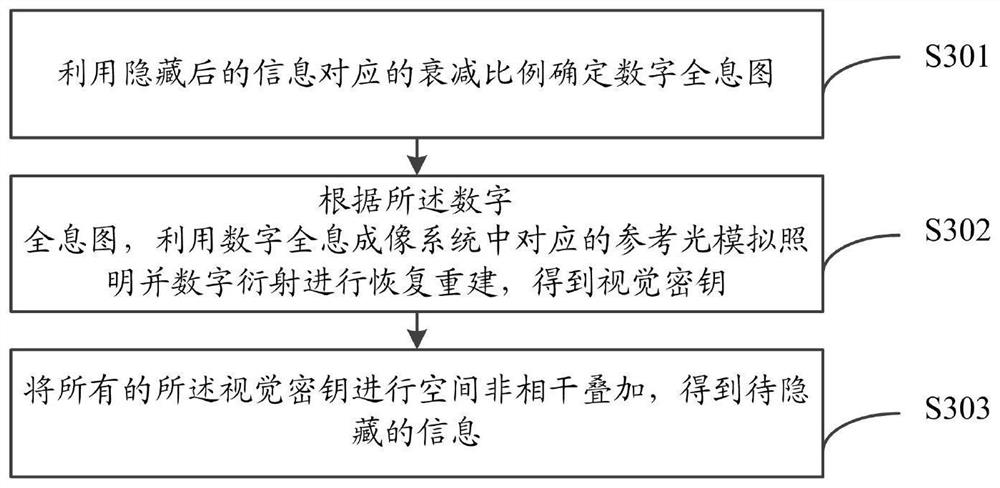
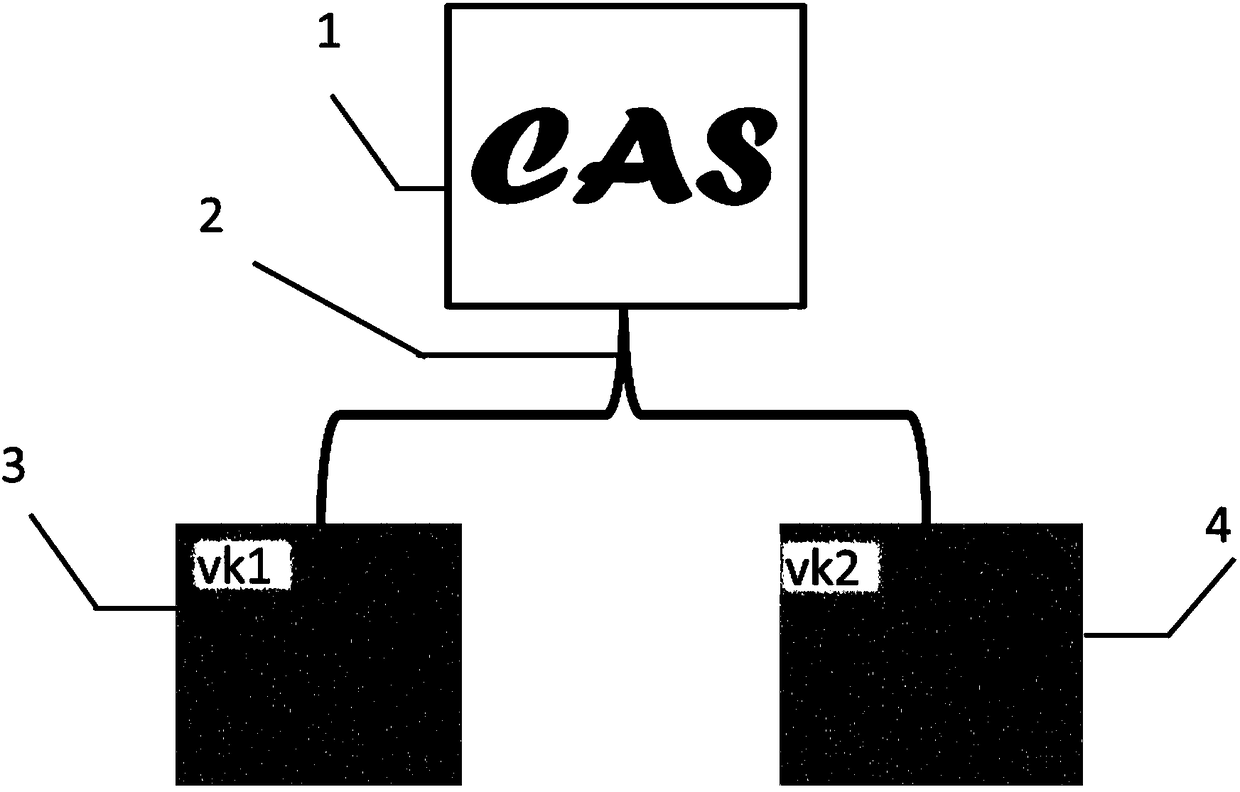
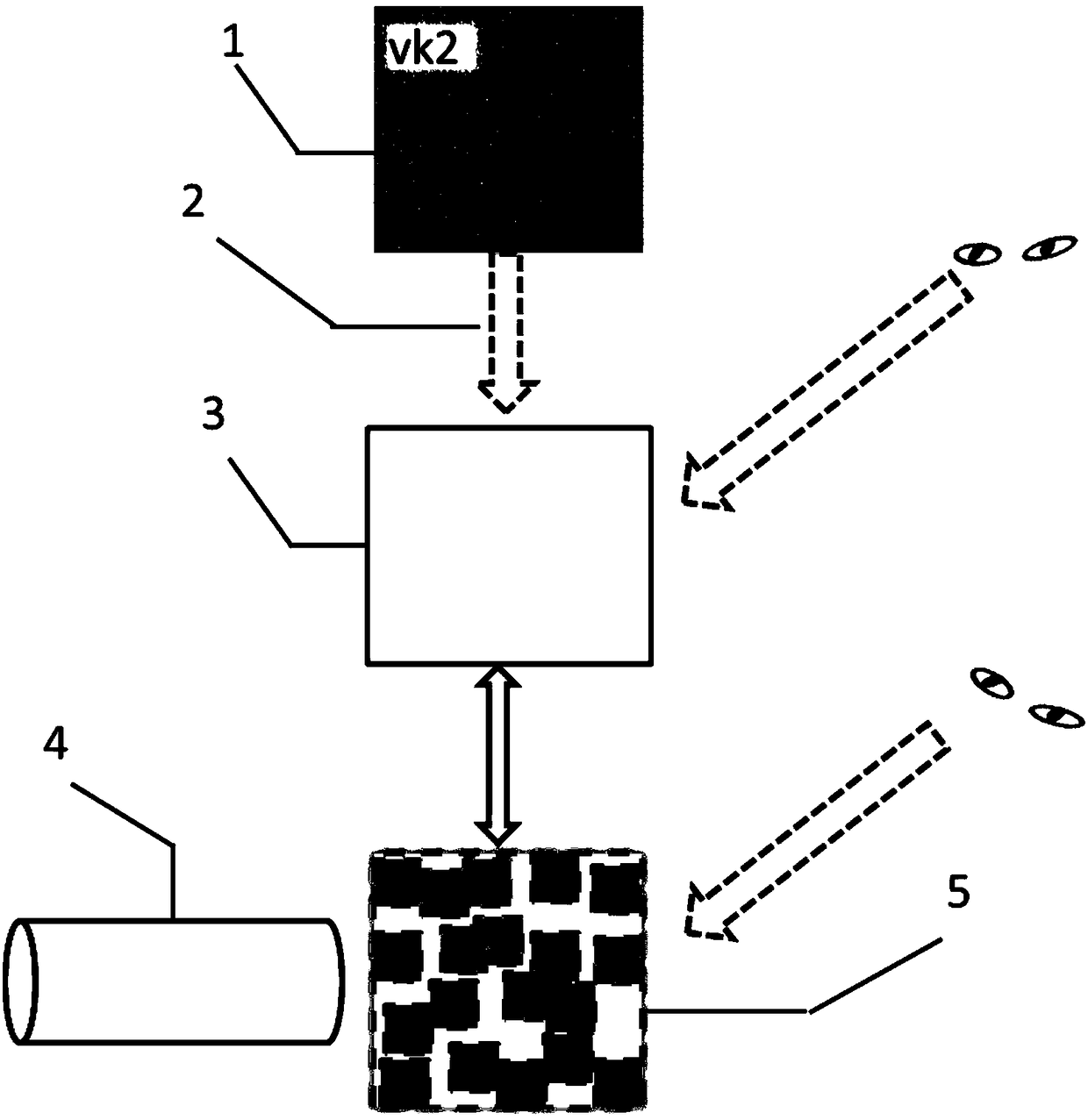
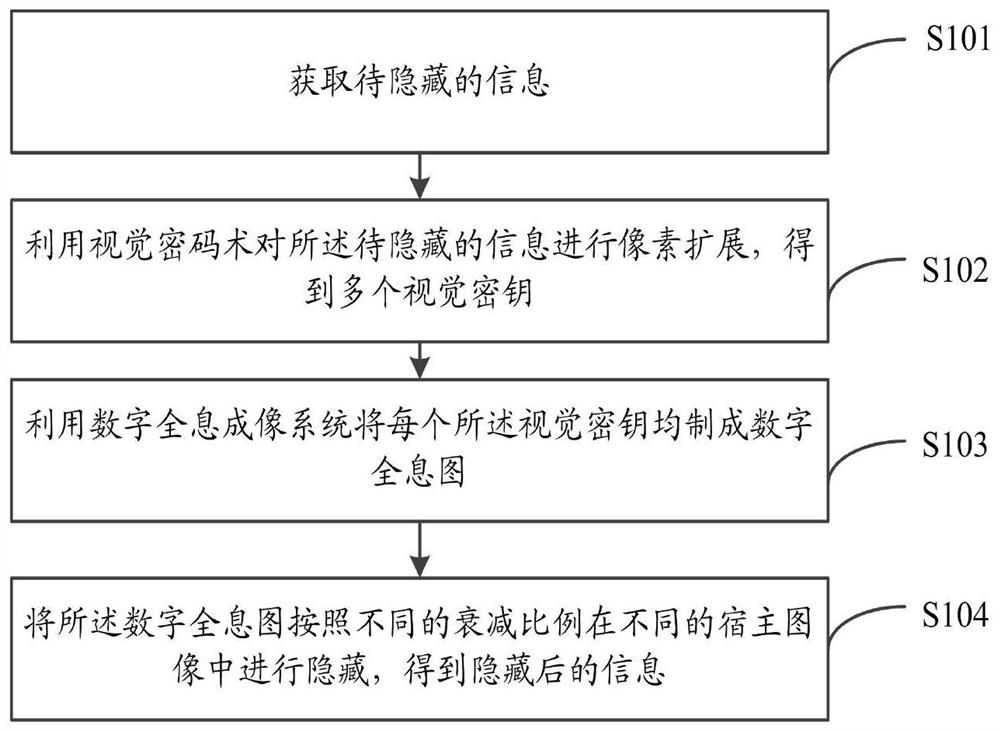
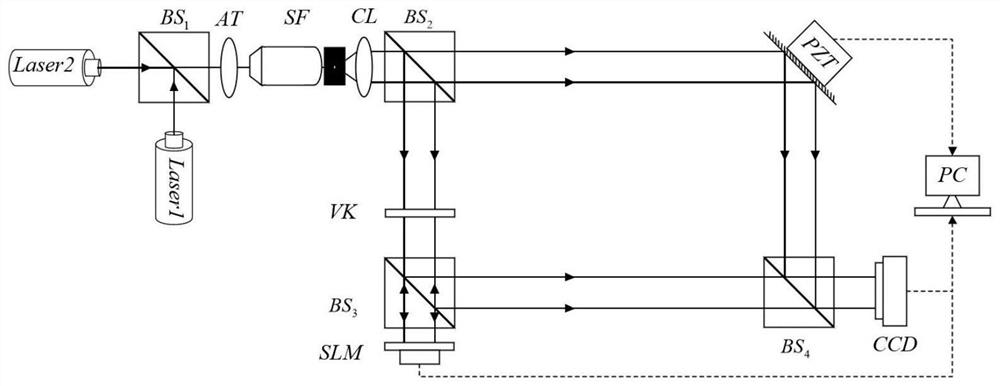
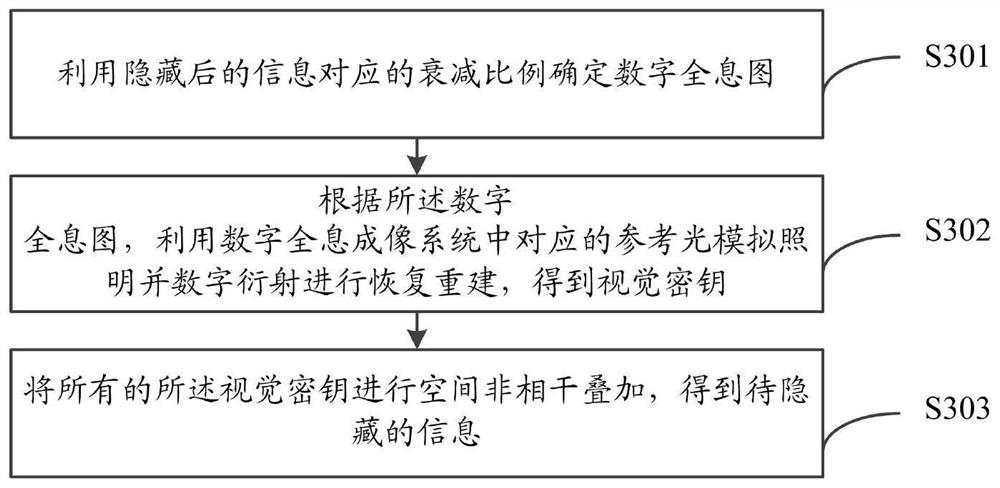
ActiveCN111897196AImprove securityImprove transmission efficiencyInstrumentsPattern recognitionInformation transmission
The invention relates to a digital holographic information hiding and extracting method and system. The hiding method comprises the steps of obtaining to-be-hidden information; performing pixel expansion on the to-be-hidden information by using visual cryptography to obtain a plurality of visual keys; utilizing a digital holographic imaging system to make each visual secret key into a digital hologram; and hiding the digital hologram in different host images according to different attenuation proportions to obtain hidden information. According to the digital holographic information hiding andextracting method and system provided by the invention, the safety and robustness in the information transmission process are improved.
Owner:UNIVERSITY OF CHINESE ACADEMY OF SCIENCES
Information security technology combining visual cryptography and photochromic material
The invention relates to an information security technology combining visual cryptography and a photochromic material. The technology is characterized in that the technology is based on the visual cryptography principle, one of information subgraphs generated by a visual cryptography scheme is printed into a certain substrate carrier through the photochromic material which has certain selectivityto laser parameters, another generated information subgraph is printed onto a transparent and visible carrier material, the transparent carrier material is calibrated and aligned with the substrate carrier, laser beams of specific parameters are used for illuminating, and finally original information can be decrypted and seen by human eyes. The technology has the advantages that the photochromic material is used for printing the image information of the visual cryptography, the safety and practicality of optical information are increased, and the technology is applicable to fields such as illegal copying preventing, copyright protection, information encryption and hiding and identity authentication.
Owner:UNIVERSITY OF CHINESE ACADEMY OF SCIENCES
System for and method of generating visual passwords
ActiveUS9171143B2Digital data processing detailsMultiple digital computer combinationsGraphicsGraphical user interface
Systems and methods for creating a visual password are presented. A user having an account or profile is given the option to create a visual password via a graphical user interface. The interface displays a plurality of themes to the user, wherein each theme represents a category of images. The user selects a theme and is presented with a plurality of images within the category. The user selects one or more images in a certain order to create a visual password. The selected images and order of selection are saved as the user's visual password. When the user later attempts to electronically access his account, the user will be required to select the correct pictures in the correct sequence in order to access his account.
Owner:CELLCO PARTNERSHIP INC +1
Identity authentication method based on visual cryptography
InactiveCN102340402BRealize dynamic passwordUncertainUser identity/authority verificationImage data processing detailsUser needsPassword
The invention provides an identity authentication method realizing a dynamic password encryption mode. The technical scheme comprises the following steps of: I, registering a new user, generating a mask picture M of the new user, and storing the other information and the mask picture M of the new user in a database as the registration information of the new user; II, authenticating the legal identity of the user; if the identity of any user needs authentication, executing the following steps: (1) generating a random cipher; (2) generating a cipher picture; (3) generating a cipher sub-picture;and (4) entering passwords to prove whether the user to be authenticated is a registered user. The invention has the beneficial effects that dynamic passwords can be realized, the decryption mode is simple, and the security is high. In spite of dynamic passwords, cipher transfer is not involved in the authentication process, thus the security is further improved.
Owner:NAT UNIV OF DEFENSE TECH
Method for visual cryptography and counterfeit prevention of patterns
InactiveCN101447071BDifficult to forgeEasy to identifyStampsLight effect designsExclusive orVisual perception
Owner:TSINGHUA UNIV
A Visual Anti-Copy Technology Based on Visual Password
The invention provides an efficient and safe visible anti-copying technique which has low costs. The technique is based on the visual cryptography principles. By printing two sharing pictures of the visual cryptography program on a transparent film with a certain thickness according to a specific way, the cryptic pictures is visible from a certain offset angle instead of from the front of the paper, therefore preventing the pictures from being copied by equipments such as copying machines and scanners. As shown in the following picture, the pictures seen from right above and from the side of the anti-copying transparent film manufactured by the technique of the invention are totally different, wherein the picture can be clearly seen from the side face while the picture can not be seen or can be vaguely seen from the right above. The technique is applicable to the prevention of illegal copying of plane pictures and texts, therefore effectively avoiding forgery; to the prevention of intentionally or unintentionally peeping and covert photography, protecting privacy; and has low cost, applicable to extensively issued plane image-text carriers such as paper money, credit cards, negotiable securities, bills, identity cards and the like.
Owner:刘峰
A method and system for hiding and extracting digital holographic information
ActiveCN111897196BImprove securityImprove transmission efficiencyInstrumentsInformation transmissionComputer graphics (images)
The invention relates to a method and system for hiding and extracting digital holographic information. The hiding method includes obtaining the information to be hidden; using visual cryptography to expand the pixels of the information to be hidden to obtain multiple visual keys; using a digital holographic imaging system to make each of the visual keys digital A hologram: hiding the digital hologram in different host images according to different attenuation ratios to obtain hidden information. The invention provides a method and system for hiding and extracting digital holographic information, which improves the security and robustness in the process of information transmission.
Owner:UNIVERSITY OF CHINESE ACADEMY OF SCIENCES
Non-destructive digital rights management method for fundus images based on hybrid architecture of fingerprint and zero watermark
InactiveCN106126978BImprove legibilityImprove robustnessCharacter and pattern recognitionImage data processing detailsPattern recognitionDigital rights management
The invention discloses a non-destructive digital copyright management method for fundus images based on a hybrid structure of fingerprints and zero watermarks. The method first performs 2D-DCT transformation on the normalized fundus images, and extracts features by setting different weights for the transformed coefficients. Highly Discriminative and Robust Fundus Image Features as Fingerprints for Content-Based Retrieval. Then the zero-watermark copyright protection method based on the VSS visual cryptography algorithm establishes the mapping relationship between fingerprints and watermarks for copyright identification. Compared with existing methods, this method has the following advantages: the whole process of the method is non-destructive and meets the requirements of accurate diagnosis; the copyright protection of fundus images is durable, avoiding the one-time problem of digital watermark copyright identification; it is suitable for fundus images The digital rights management method has certain clinical significance for the auxiliary diagnosis of fundus-related diseases.
Owner:CENT SOUTH UNIV
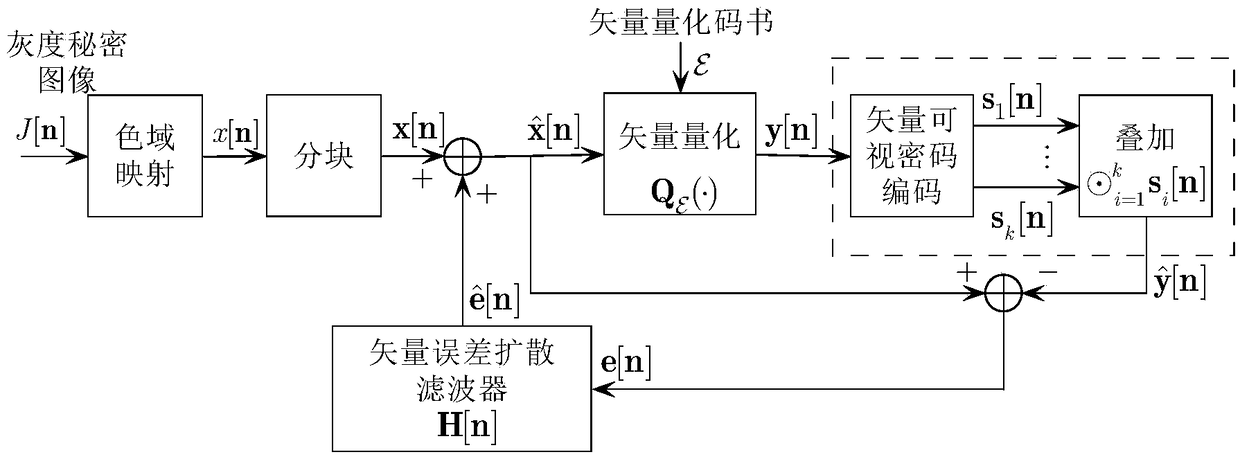
A Visual Encryption Method for Grayscale Image
ActiveCN109214971BImprove visual qualityImage analysisEncryption apparatus with shift registers/memoriesImaging qualityImage contrast
The invention discloses a grayscale image visual encryption method. In this method, the two processes of image generation and superposition decoding in visual cryptography are placed in an error diffusion feedback loop. That is to say, at the encoder side, each pixel or image block is sequentially processed according to a certain scanning order, and for each pixel or image block on the generated shared image, the superimposed decoding effect is checked immediately, and the superimposed obtained The reconstructed target image is compared with the original secret image to obtain the difference between the two, and the contrast difference is fed back and diffused to surrounding pixels or image blocks that have not been quantified, so as to improve the quality of the decoded and reconstructed secret image. The process of generating shared images, and the synthesis process corresponds to the process of obtaining target images from shared images, the method of the present invention puts synthesis in analysis, that is, analysis based on synthesis.
Owner:SHANDONG UNIV OF SCI & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com