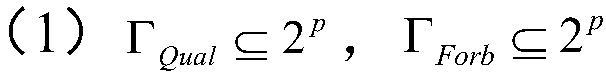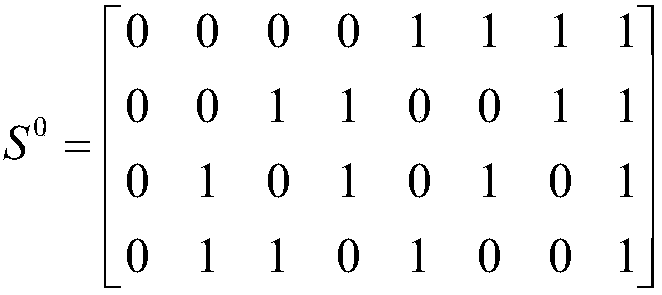A threshold visual cryptography matrix construction method
A visual password and threshold technology, applied in the field of secret sharing and visual passwords, can solve the problems of disorganized sharing and obtaining secret information, and achieve the effect of simple and efficient construction process and quality assurance.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0048] The (n, n) threshold scheme is illustrated below according to a specific embodiment:
[0049] If n=4, the number of rows of the basic matrix is 4, and the construction of the columns is according to S 0 Contains only 0, 2, 4 with even Hamming weight, S 1 The method that only includes 1 and 3 whose Hamming weight is an odd number is carried out, and the two base matrices are:
[0050]
[0051]
Embodiment 2
[0053] Let n=2, then the number of rows of the basic matrix is 2, and the structure of the columns is according to S 0 Contains only 0, 2, S with an even Hamming weight 1 The method that only includes 1s with an odd Hamming weight is performed, and the two basis matrices are:
[0054]
[0055] The following is the method for constructing the visual password matrix of any structure provided by the present invention by accumulating from the array.
[0056] The accumulation from the array is constructed on the basis of the above (n, n) threshold scheme. First build a cumulative array, the construction method of the cumulative array: construct a matrix CA of |P|×|T|, where |T|=|Γ ∞ |, if and only if , CA(i,j)=1, F is the set Γ ∞ collection of neutrons.
[0057] P is the set of participants in the visual cryptography scheme, and we consider the array P to be known. And T refers to the collection contained in the forbidden subset and the authorized subset; the collection...
Embodiment 3
[0067] The matrix construction method of the present invention is described below through the present embodiment:
[0068] Let n=4, P={1,2,3,4}, Γ 0 ={{1,2},{2,3},{3,4}},Γ ∞ ={{1,4},{1,3},{2,4}} can get F 1 = {1,4}, F 2 ={1,3},F 3 ={2,4}, then |T|=|Γ ∞ |=3, first construct the accumulative array, you can get:
[0069]
[0070] Then construct the basis matrix of the (3,3) threshold:
[0071]
[0072] At this time, observing CA can get col1={3}, col2={1,2}, col3={1,3}, col4={2}, from which the basis matrix can be calculated, as follows, col1=3, so S 0' and S 1' Line 3 of S as 0 and S 1 The first line of ; col2={1,2}, the S 0' and S 1' Lines 1 and 2 are ORed as S 0 and S 1 The second line of , so by analogy, the basis matrix can be obtained as follows:
[0073]
[0074]The method of the invention can realize the construction of the basic matrix of visual cryptography with any structure. As a visual cipher with hidden and shared secret technology, one of th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com