Password encryption and multi-channel transmission method
An encryption method and multi-channel technology, which is applied in the field of password encryption and multi-channel transmission, can solve the problem of not being able to obtain secret password information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
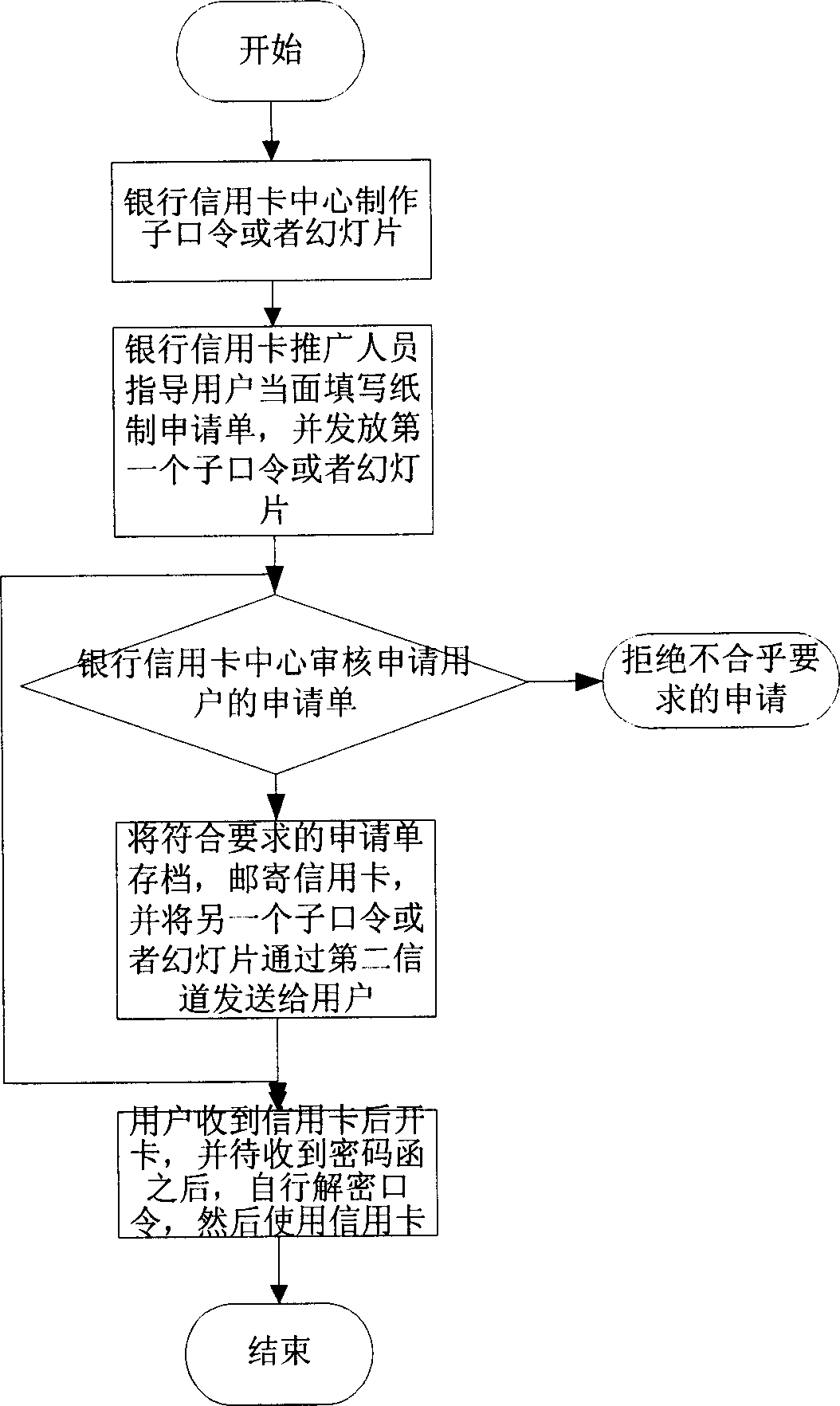
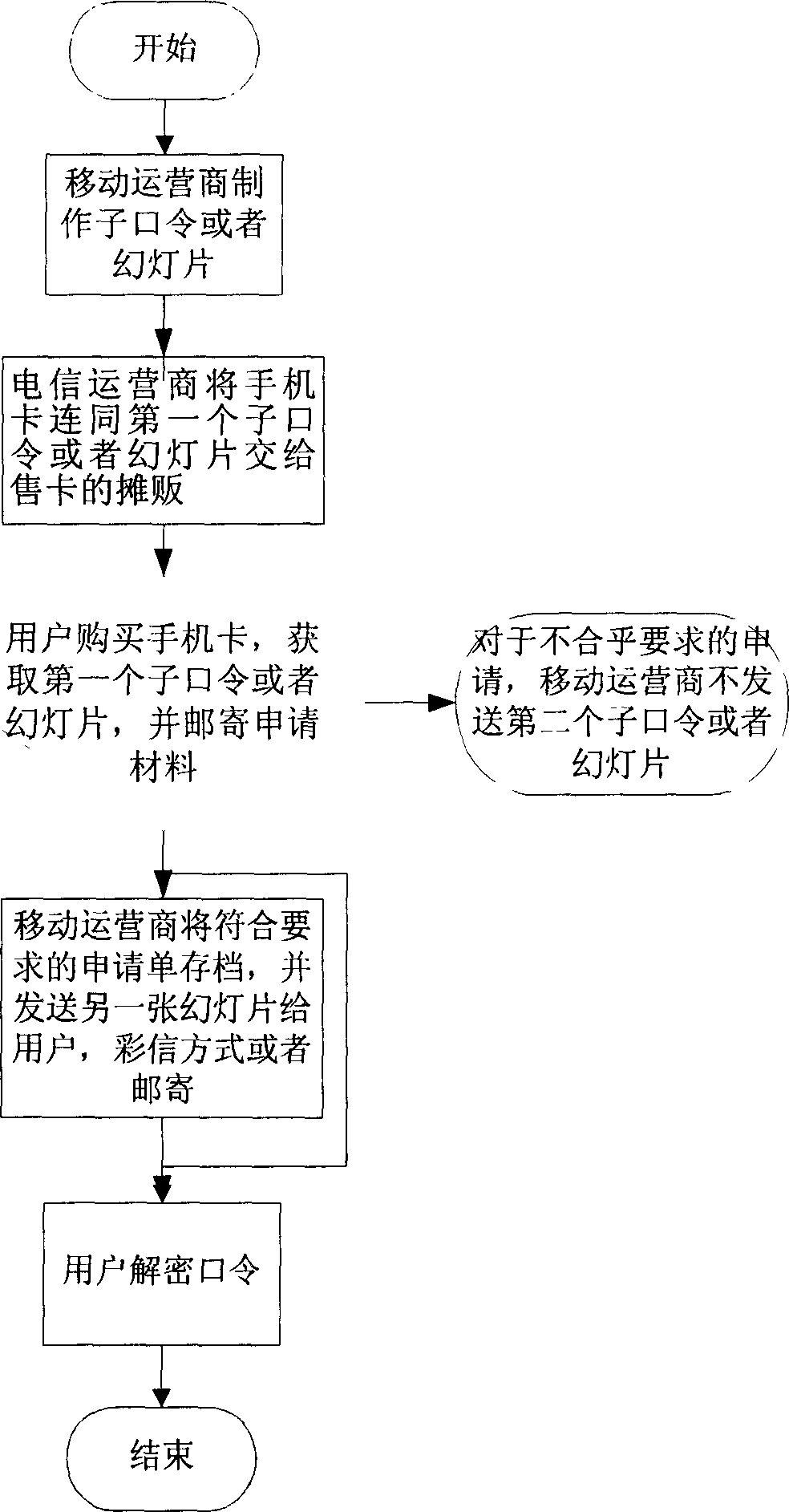
[0072] In the context of applying for a credit card service:
[0073] First: For applicants who apply for a credit card in the business hall, the sub-password or slides are made by the credit card center of the bank, and one of the sub-passwords or a slide is handed over to the staff in charge of business promotion of the bank, in step 1 Among them, the service applicant (520) and the service provider (510) are the user and the credit card center of the bank respectively, and the application form filled out by the user must be obtained from the bank staff, where the bank staff can be the credit card business promotion staff of the bank . In step 2, the credit card center reviews the user's application form and archives the paper application form. In step 3, the bank's credit card center directly mails the credit card and another sub-password or another slide to the user (or only mails the credit card, And send another sub-password or another slide by other means, such as SMS ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com