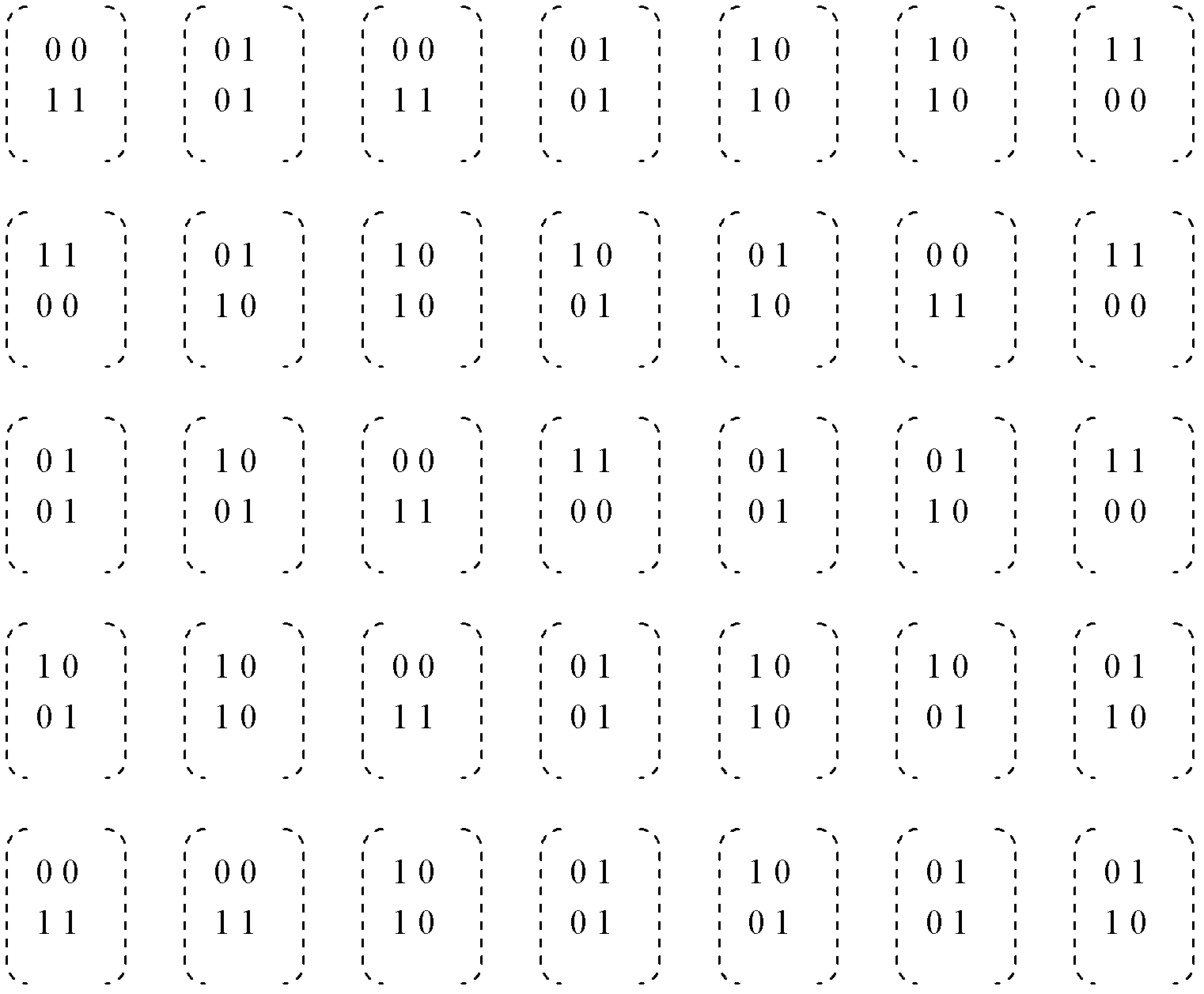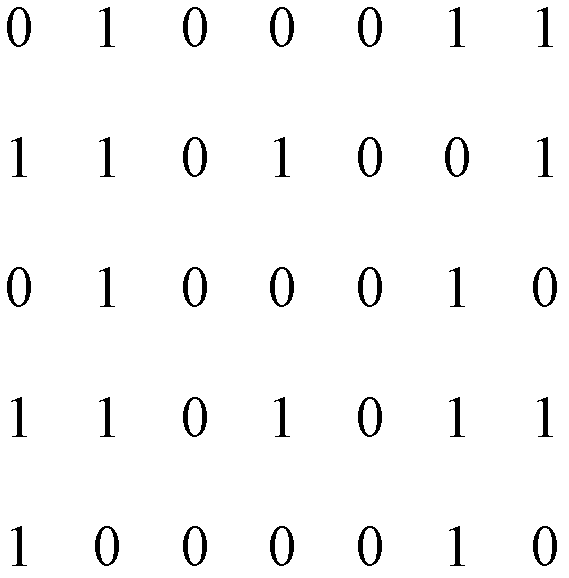Identity authentication method based on visual cryptography
A technology of identity authentication and visual cryptography, which is applied in the field of information security and can solve problems such as identity authentication methods that have not yet been discovered
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] The present invention will be described in detail below in conjunction with examples.
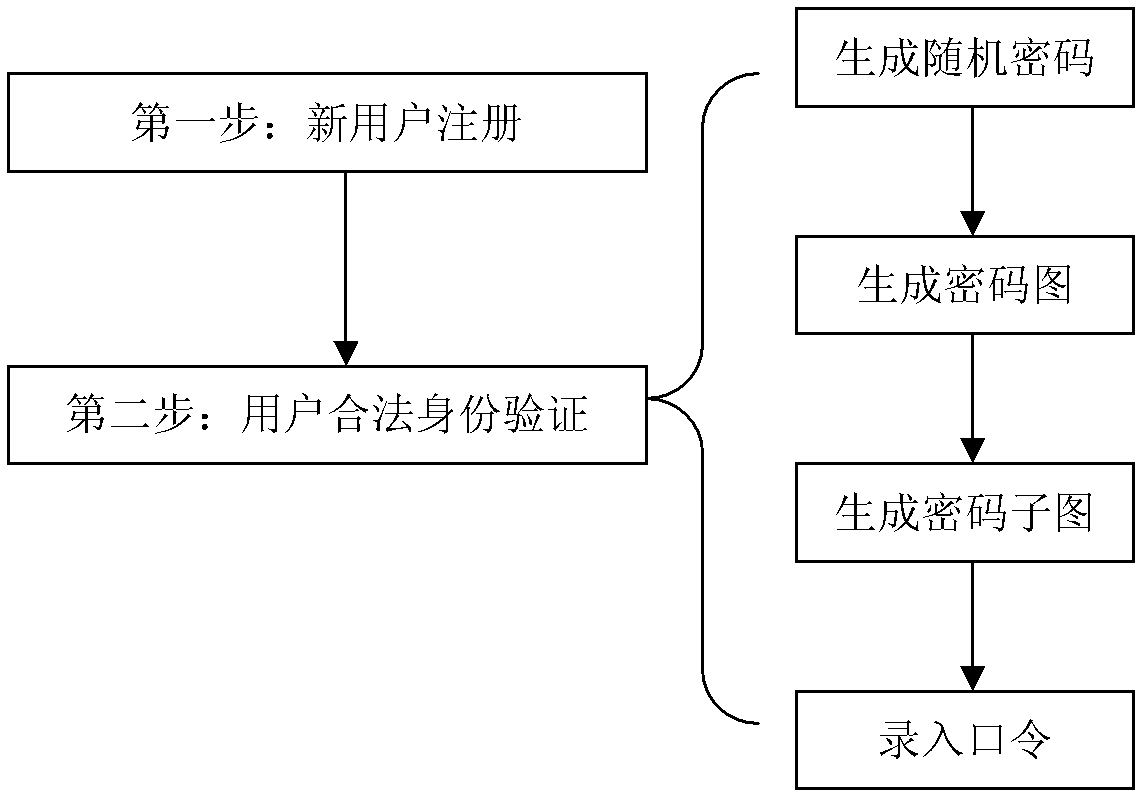
[0043] figure 1 It is a schematic flow chart of the principle of the present invention, Figure 2 to Figure 5 It is an example diagram of simulation experiment 1 carried out by using a specific embodiment of the present invention, Figure 6 to Figure 9 It is the result of the second simulation experiment using the specific embodiment of the present invention.
[0044] Such as figure 1 As shown, the present invention is divided into two steps, and the first step is the registration of a new user. Randomly select the basic map points composed of 2*2 pixels to arrange, generate a new user's mask map, distribute the mask map to the new user, and send other information of the new user (such as the user's name, valid certificate number and other user personal information) and the mask Figure 1 as the registration information of the new user and stored in the database. Such as figu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com