QR code secret sharing method based on visual password
A secret sharing, two-dimensional code technology, applied in the field of two-dimensional code secret sharing based on visual password, can solve the security problems of secret sharing algorithm and other problems, and achieve the effect of good security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
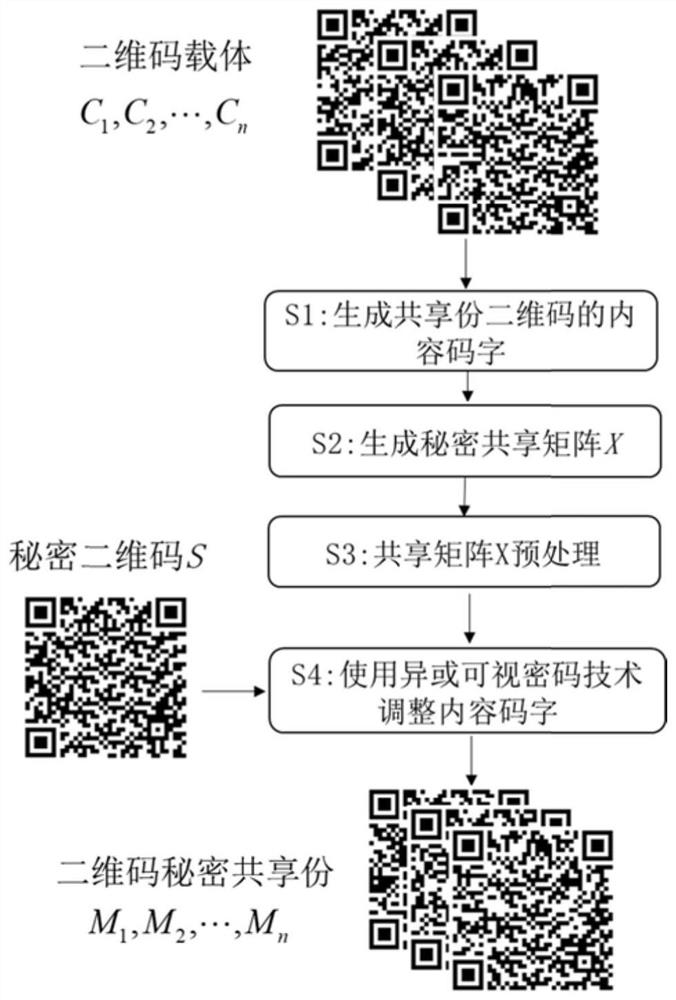
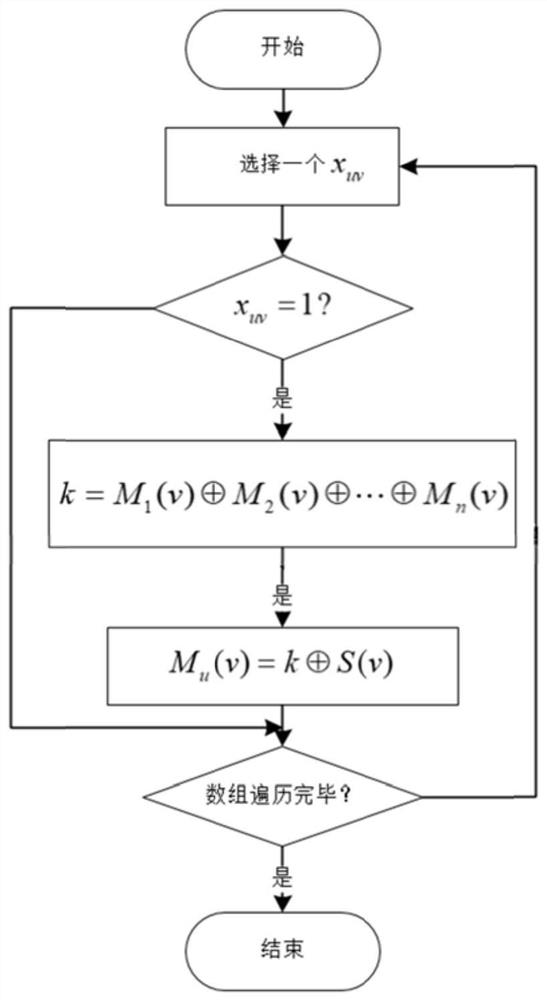
[0047] The specific embodiments of the present invention will be further described in detail below in conjunction with the accompanying drawings. The two-dimensional code secret sharing method based on visual password, its specific steps are described as follows figure 1 Shown in S1~S4. Wherein, the specific steps of the code word adjustment method based on visual password are described as follows: image 3 Shown:
[0048] Step 1: Read the carrier QR code C separately 1 ,C 2 ,...,C n information, and according to their version number and verification level, using the standard two-dimensional code coding process, through data analysis, data coding, redundant coding, code word filling and other operations, the M 1 , M 2 ,...,M n Content codeword.
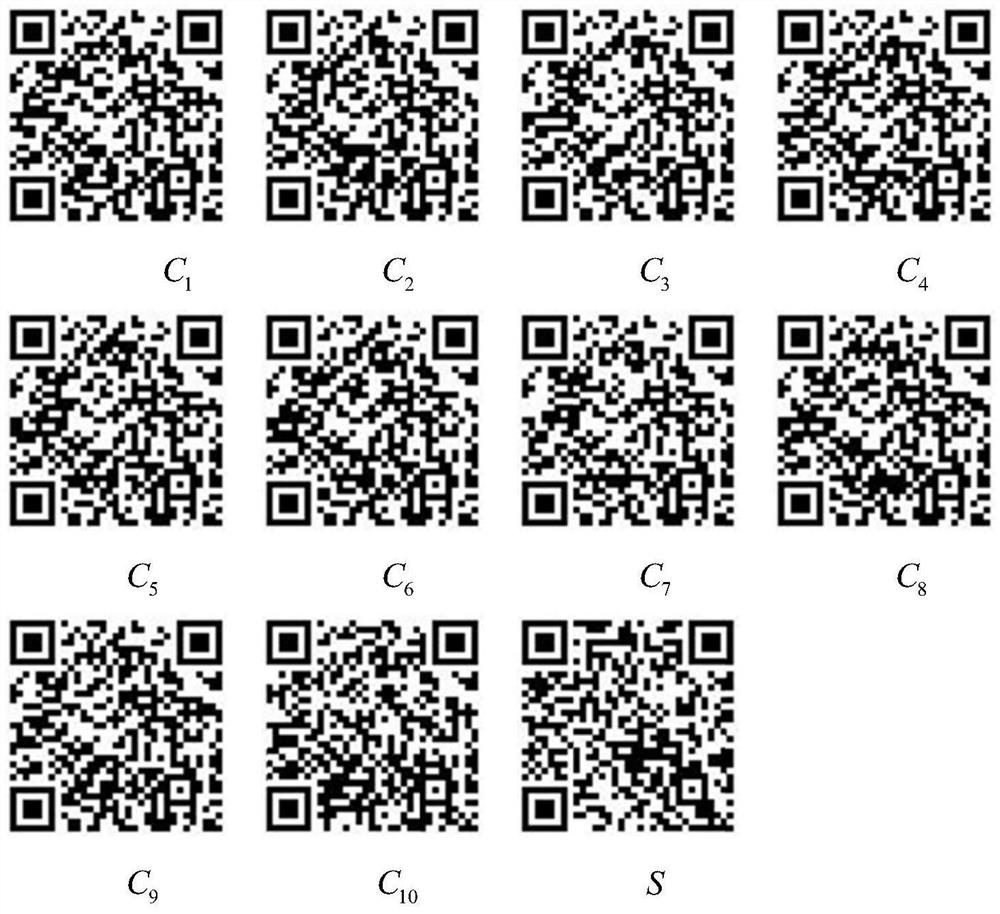
[0049] In this embodiment, set n=10, 10 carrier two-dimensional codes and secret two-dimensional code images refer to figure 2 . Among them, the versions of 10 QR codes are all 4-H, and they contain meaningful content infor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com