A Visual Encryption Method for Grayscale Image
A technology of grayscale image and encryption method, which is applied in image analysis, image data processing, image data processing, etc., can solve the problem of low detail resolution and achieve the effect of improving visual quality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0071] Basic idea of the present invention is as follows:
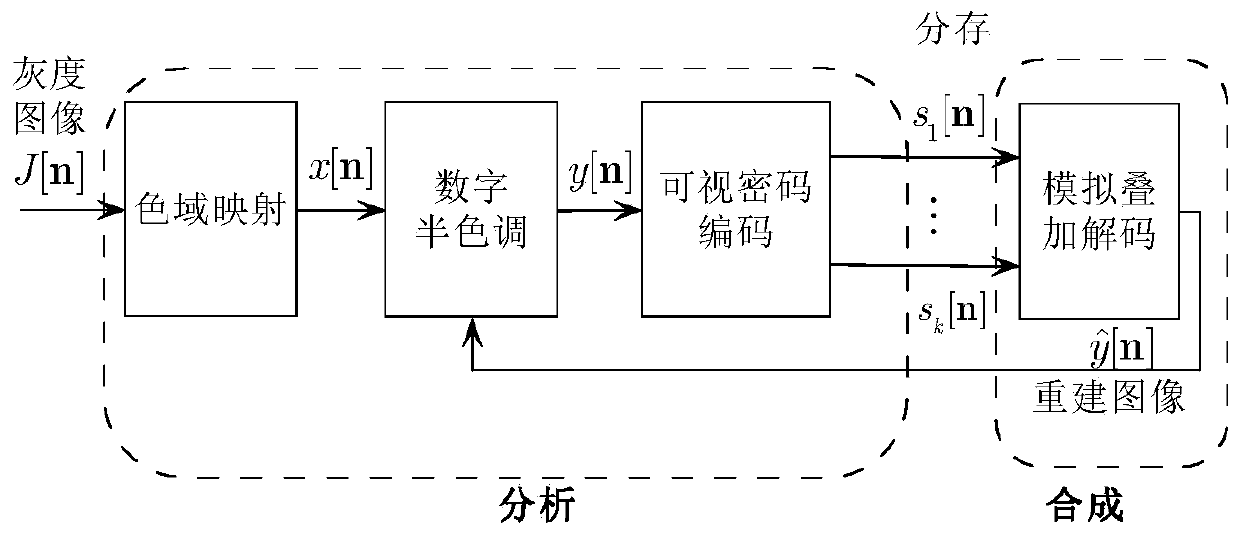
[0072] Such as figure 1 As shown, an cipher with a closed-loop feedback analysis-by-synthesis (Analysis-by-Synthesis, AbS) framework is proposed, and a visual cipher is designed from the perspective of analysis-synthesis, that is, the process of dividing the secret image into shared images is the analysis part; and the superposition of the shared image in the encryptor to generate the reconstructed image is the synthetic part.
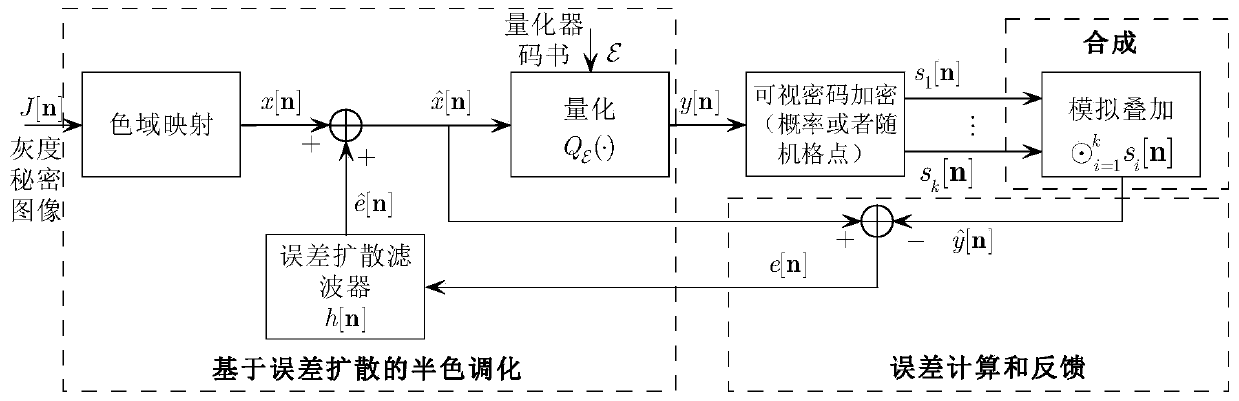
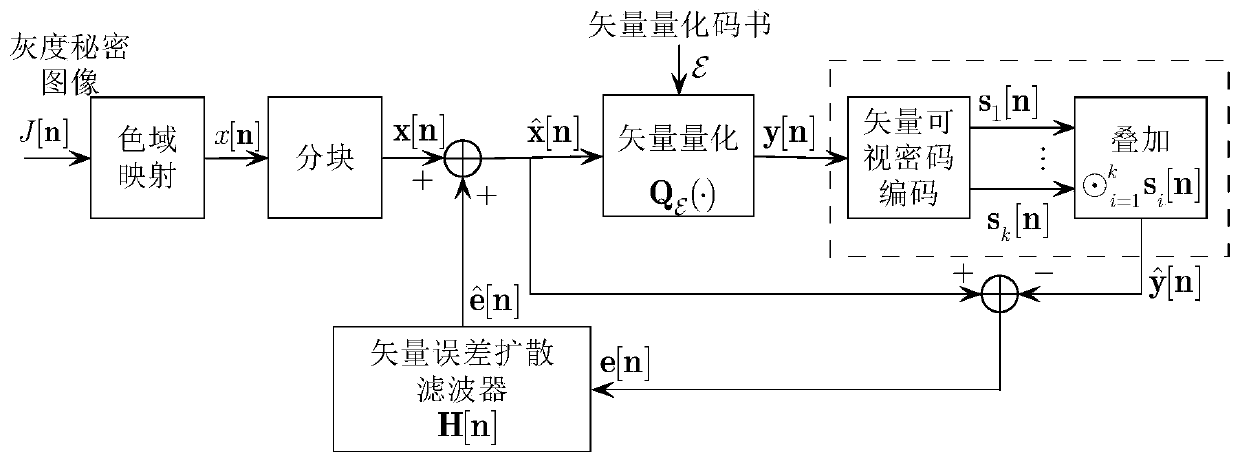
[0073] The basic meaning of AbS is to decode the shared image obtained by encryption in the encryptor (not in the decoder), and use the decoding result as the basis for optimizing the visual quality. Specifically, in this AbS framework, the reconstructed image synthesized by the encryptor is fed back to the analysis part to obtain the difference between the current reconstructed pixel (or image block) and the secret pixel (or image block), so that the halftoning process can This difference...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com